eeaad94bf32166b91fbcd43e6979e89f.ppt
- Количество слайдов: 40

Secure Networking for Business Continuity © 2002, Cisco Systems, Inc. All rights reserved.

Agenda • Business Resilience • Security Issues • Legacy vs. Network Security • Cisco’s SAFE Blueprint • Cisco Security Development • Predictions and Summary
Drivers of the Internet Race Survival Global Competition New Revenue Empowered Workforce Educated Leaders Internet Economy 2002 New Competition Competitive Advantage Profits, Cash Flow, Productivity Organization Structure

Today’s Internet Business Environment E-Commerce Customer Care E-Learning Workforce Optimization Supply Chain
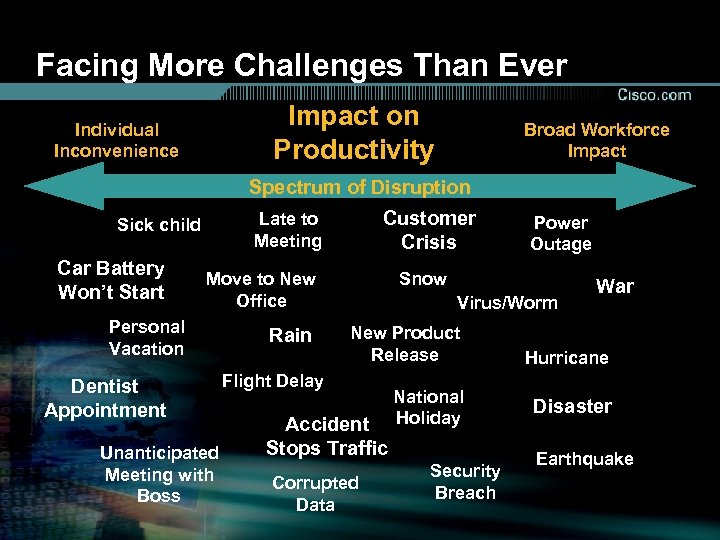
Facing More Challenges Than Ever Impact on Productivity Individual Inconvenience Broad Workforce Impact Spectrum of Disruption Car Battery Won’t Start Customer Crisis Late to Meeting Sick child Move to New Office Personal Vacation Dentist Appointment Unanticipated Meeting with Boss Rain Power Outage Snow Virus/Worm New Product Release Flight Delay Accident Stops Traffic Corrupted Data National Holiday Security Breach War Hurricane Disaster Earthquake
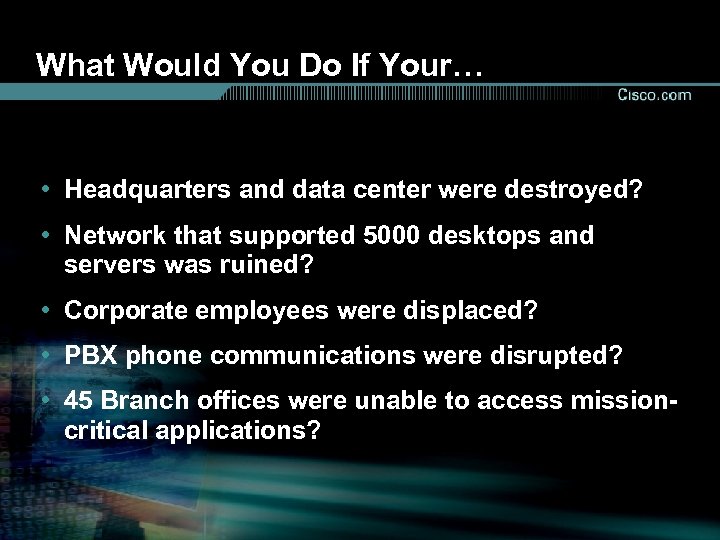
What Would You Do If Your… • Headquarters and data center were destroyed? • Network that supported 5000 desktops and servers was ruined? • Corporate employees were displaced? • PBX phone communications were disrupted? • 45 Branch offices were unable to access missioncritical applications?
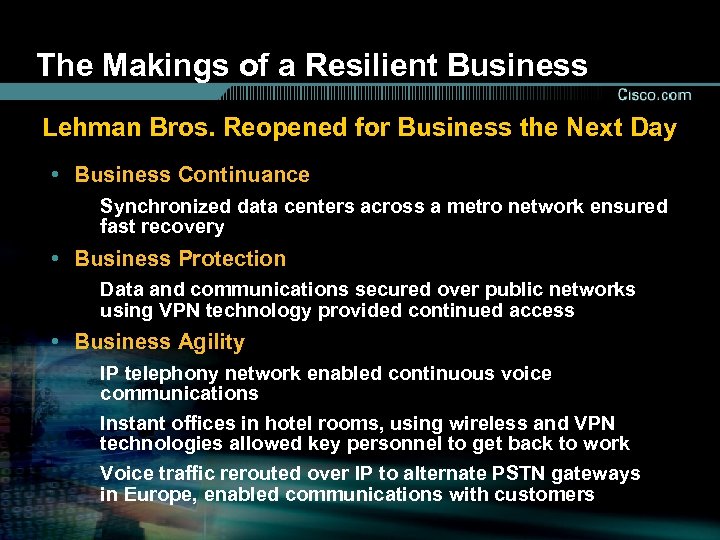
The Makings of a Resilient Business Lehman Bros. Reopened for Business the Next Day • Business Continuance Synchronized data centers across a metro network ensured fast recovery • Business Protection Data and communications secured over public networks using VPN technology provided continued access • Business Agility IP telephony network enabled continuous voice communications Instant offices in hotel rooms, using wireless and VPN technologies allowed key personnel to get back to work Voice traffic rerouted over IP to alternate PSTN gateways in Europe, enabled communications with customers

In the Event of Disruption, Can You … • Ensure critical systems and networks are continuously available? • Restore mission critical applications? • Provide uninterrupted workforce productivity with a secure instant office?

How Much Down-Time Can You Afford? Industry Sector Revenue/Hour • Revenue loss Energy $2, 817, 846 • Customer dissatisfaction Telecommunications $2, 066, 245 Manufacturing $1, 610. 654 Financial Institutions $1, 495, 134 Information Technology $1, 344, 461 Insurance $1, 202, 444 Retail $1, 107, 274 • Lost productivity • Brand dilution • Legal liability • Financial performance Source: Meta Group 11/2000

Achieving Stability in an Unpredictable World Business Resilience re·sil·ience (ri-zil’-yens)—Injecting security, protection and recovery into dispersed and far-flung organizations so that they can bounce back from any kind of setback, whether a natural disaster, a hostile economic change, a competitive onslaught, cyber-espionage or a terrorist attack. Gartner, January 2002
Business Resilience Objectives Networked Virtual Organizations are Agile • Predictable performance • Non-stop e-business • Disaster recovery and asset protection • Decentralized and mobilized resources • Flexible communications

Security. . Critical Enabler for Business Resilience E-Commerce Supply Chain Management Customer Care Workforce Optimization E-Learning • Requires Defense-in-Depth • Requires multiple components • Integration into e-business infrastructure • Requires comprehensive blueprint
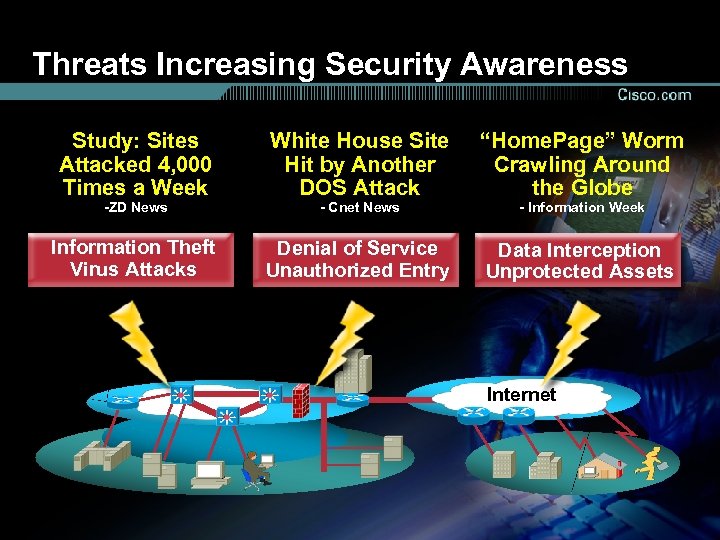
Threats Increasing Security Awareness Study: Sites Attacked 4, 000 Times a Week White House Site Hit by Another DOS Attack “Home. Page” Worm Crawling Around the Globe Information Theft Virus Attacks Denial of Service Unauthorized Entry Data Interception Unprotected Assets -ZD News - Cnet News - Information Week Internet
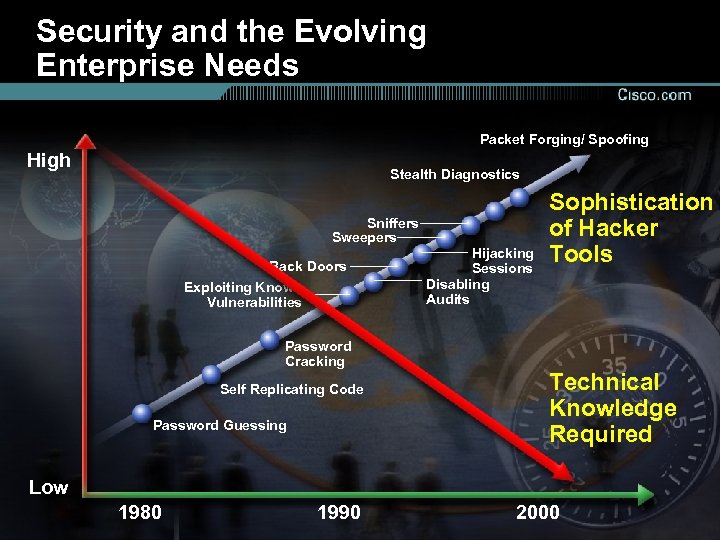
Security and the Evolving Enterprise Needs Packet Forging/ Spoofing High Stealth Diagnostics Sniffers Sweepers Back Doors Exploiting Known Vulnerabilities Hijacking Sessions Disabling Audits Sophistication of Hacker Tools Password Cracking Self Replicating Code Password Guessing Technical Knowledge Required Low 1980 1990 2000

Outsider / External Breaches % of Respondents Experiencing These Security Breaches 89% 80% 48% 37% 24% Source: Goldman Sachs 39% 25% 21%

What’s the Impact of Not Properly Securing Your Network ? • Cost—directly affects bottom line 186 organizations* reported hack attempts totaling nearly $378 million. Average loss per respondent nearly $2, 000 • Credibility—end-user perception Can your end-user trust your network? • Productivity—ability to use your system Downtime is lost time and revenue • Viability—can ultimately affect your business Where will your company be in 1 year… 5 years? • Liability—are you responsible? If you don’t take actions to stop outbound attacks, are you liable for damages inflicted on others? * FBI and Computer Security Institute(CSI)― 2001

It’s About “Business Continuity” “ We security folks have got to stop treating security like it’s a separate problem from network management. Error detection, intrusion detection, and link outages – these are all aspects of the same network management problem. ” Marcus Ranum CEO, Network Flight Recorder One of the Fathers of the Modern Firewall
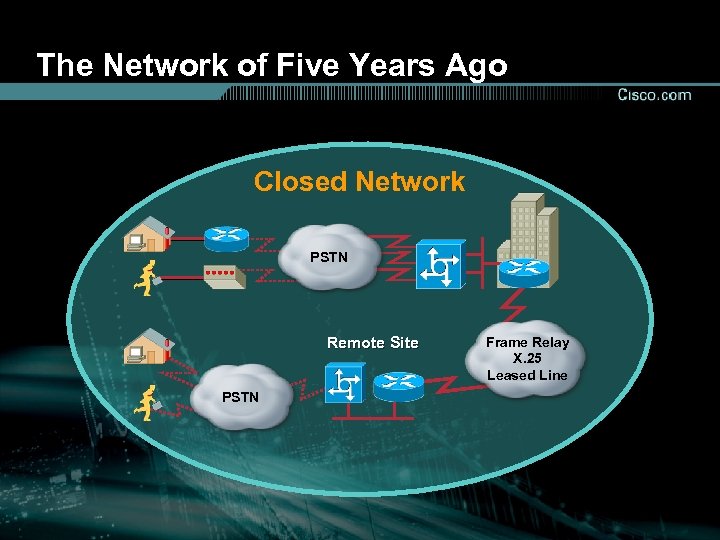
The Network of Five Years Ago Closed Network PSTN Remote Site PSTN Frame Relay X. 25 Leased Line

Legacy Security Solutions • Most security designed when networks were simple and static • Primarily single-point products (accesscontrol) with no network integration or intelligence • Such legacy products are still seen as default security solutions (a “cure-all”) • Today, there are serious drawbacks to relying on such “overlay” security to protect sophisticated networks and services

Case in Point… Internet connections have dramatically increased as a frequent point of attack (from 59% in 2000 to 70% in 2001. ) Of those organizations reporting attacks, we learn: § 27% say they don't know if there had been unauthorized access or misuse § 21% reported from two to five incidents in one year § 58% reported ten or more incidents in a single year – something isn’t working! Computer Security Institute & FBI Report March, 2001

Code Red and Nimda Worm Impacts • Rapid penetration and propagation through existing security solutions • Extensive impact; expensive recovery • Exploited existing and known vulnerabilities, and bypassed legacy security devices • Could be prevented and mitigated

Impact of Recent Worms • Major Computer Company. . . Code Red/Nimda $9 million for remediation 12, 000 IT hours for Code Red 6, 500 IT hours for Nimda • Multibillion dollar financial institution. . . Nimda 75% of core routers down at any given time Lost trading server for half day ($13 million impact) Important Lesson Learned: Security Needs to Be Designed and Implemented Around, In and Through the Network
The Network Today

Today’s Threats • Attackers are taking advantage of complex networks and sophisticated Internet services • In this environment, everything is a target: Routers, Switches, Hosts, Networks (local and remote), Applications, Operating Systems, Security Devices, Remote Users, Business Partners, Extranets, etc. • Threats to today’s networks are not addressed by most legacy security products • In fact, there is no single security device which can protect all of these targets
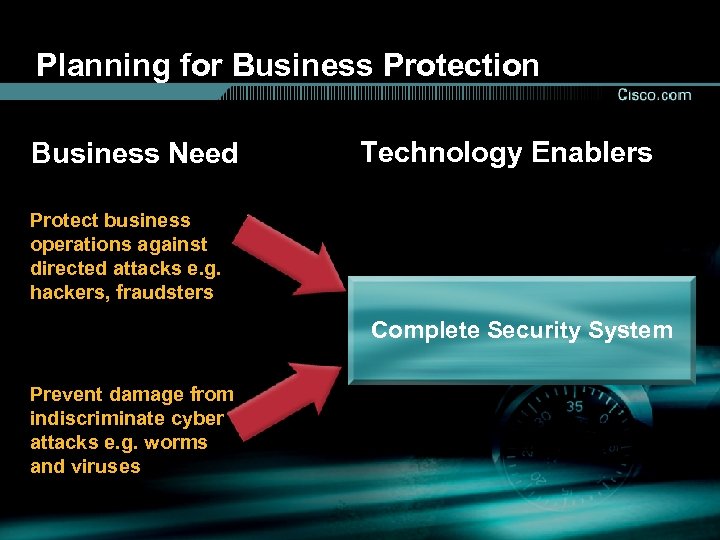
Planning for Business Protection Business Need Technology Enablers Protect business operations against directed attacks e. g. hackers, fraudsters Complete Security System Prevent damage from indiscriminate cyber attacks e. g. worms and viruses

What Customers Want A Network-based “Intelligent” Solution • Integration of security into all processes Bridge gap between Network Ops and Security Ops • Security foundation for current technology • Security foundation for new technology – no “fork -lift” upgrades Integrated Voice, Video, and Data traffic Support for Wireless and Remote Access Qo. S for differentiated handling of network traffic • Defense in depth Build security into the network, not just the perimeter • End-to-end networking solution

Cisco Security Directions Mission • Accelerate deployment of security and e -business infrastructures Strategy • Embrace integration into e-business infrastructure and technology initiatives • Provide most comprehensive security/ VPN solution • Utilize solutions and services ecosystems/partners
An Integrated System-Wide Approach • End-to-end coordinated network+security system approach Defense in depth Protects hosts and networks • Scalable system-wide security management policy, configuration, administration, monitoring Appliance and Router Firewalls, IDS, VPNs • Single point of contact for network and security technical assistance, support and professional services Fast problem resolution Lower cost of ownership

SAFE Security Blueprint • Integrates security and network issues • Includes specific configurations for Cisco and partner solutions • Based on existing, shipping capabilities • Over 3, 000 hours of lab testing • Currently, five SAFE white papers: SAFE for Enterprise, SAFE for SMB, SAFE Blueprint for IP Telephony, Wireless LAN Security in Depth, Combating Internet Worms
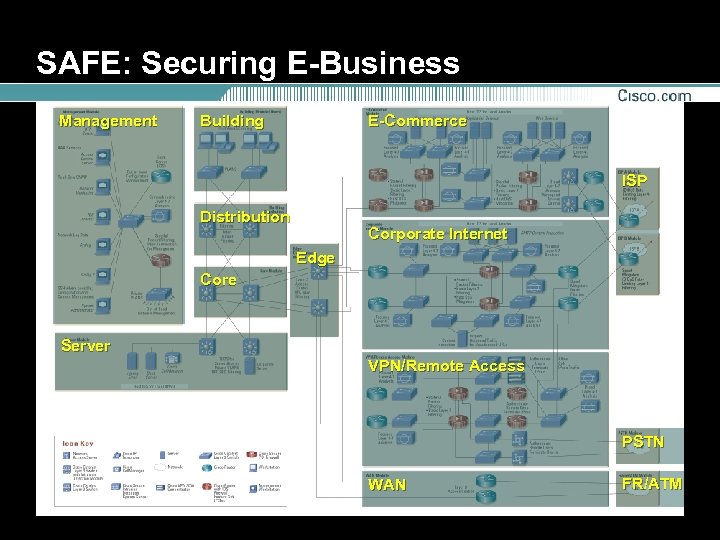
SAFE: Securing E-Business Management Building E-Commerce ISP Distribution Corporate Internet Edge Core Server VPN/Remote Access PSTN WAN FR/ATM
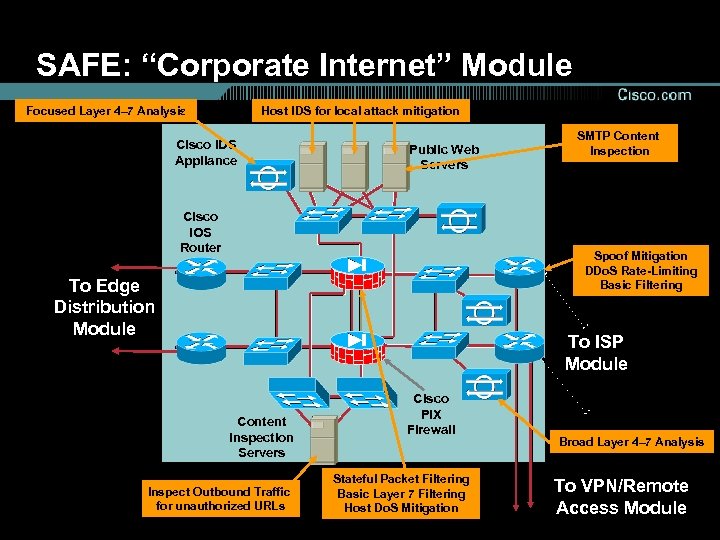
SAFE: “Corporate Internet” Module Focused Layer 4– 7 Analysis Host IDS for local attack mitigation Cisco IDS Appliance Public Web Servers Cisco IOS Router SMTP Content Inspection Spoof Mitigation DDo. S Rate-Limiting Basic Filtering To Edge Distribution Module To ISP Module Content Inspection Servers Inspect Outbound Traffic for unauthorized URLs Cisco PIX Firewall Stateful Packet Filtering Basic Layer 7 Filtering Host Do. S Mitigation Broad Layer 4– 7 Analysis To VPN/Remote Access Module
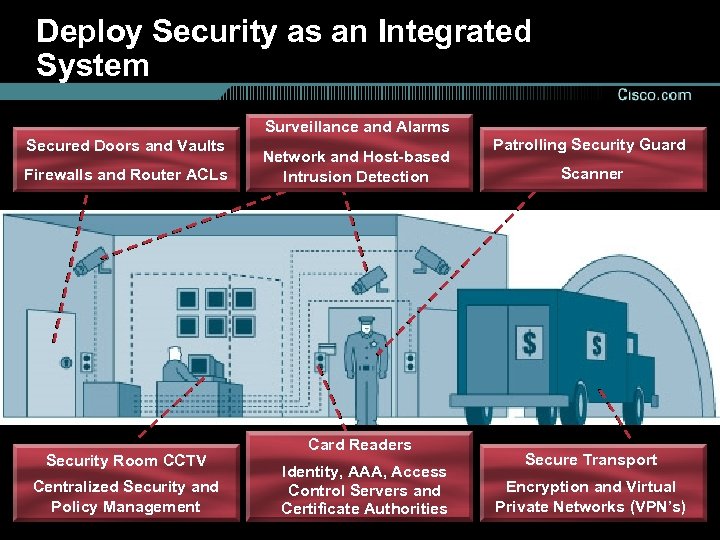
Deploy Security as an Integrated System Surveillance and Alarms Secured Doors and Vaults Firewalls and Router ACLs Security Room CCTV Centralized Security and Policy Management Network and Host-based Intrusion Detection Card Readers Identity, AAA, Access Control Servers and Certificate Authorities Patrolling Security Guard Scanner Secure Transport Encryption and Virtual Private Networks (VPN’s)
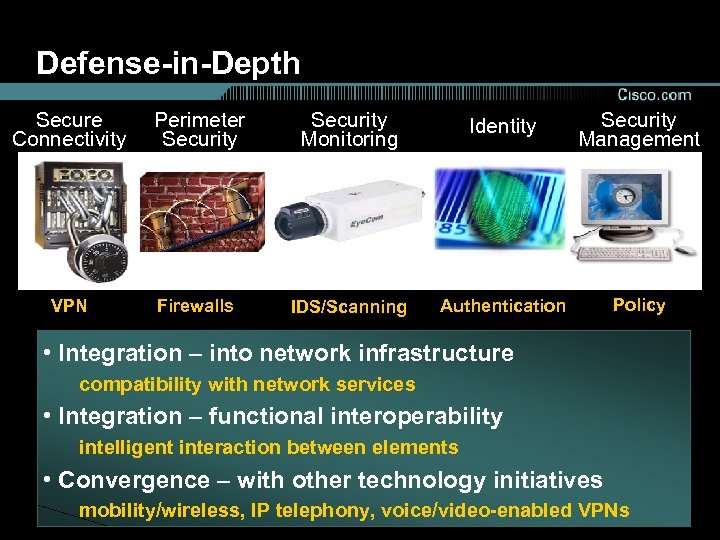
Defense-in-Depth Secure Connectivity Perimeter Security Monitoring Identity Security Management VPN Firewalls IDS/Scanning Authentication Policy • Integration – into network infrastructure compatibility with network services • Integration – functional interoperability intelligent interaction between elements • Convergence – with other technology initiatives mobility/wireless, IP telephony, voice/video-enabled VPNs

Action Plan: Implementing a Process 1. Develop a comprehensive security policy Based on assessment of assets, threats, vulnerabilities 2. Implement it Focus on key exposures Build defense in depth Security and network experts engage In-source or out-source 3. Monitor and audit It’s what you don’t know. . . Be selective 4. React—according to plan Recovery needs to be rapid and organized Involve partners—in advance 5. Repeat Cycle! Continuous improvement to address new threats

Trends / Predictions • Security is going Mainstream Fundamental to e-business—not an afterthought • Security is going to Main Street Every small business will be an e-business Increased outsourcing of solutions and services • Security extends everywhere The Internet home and the Mobile Office • The Bar will continue to be raised Criticality of e-business applications Increased regulation • Comprehensive solutions will win Security integrated into voice, video, wireless infrastructures

Prediction 2002. . . IT Security Prediction: • Organizations will reset their IT security plans in 2002 Rationale: • Organizations rethinking security after September 11 • Focus of IT security will shift from the “Three As” (authentication, authorization, administration) to business continuity • Physical and IT security will be integrated Source: IDC 2001; * Security Authorization, Authentication, Administration

Cisco’s Leadership Obligation • Leading provider of networking equipment • Leading provider of Security/VPN solutions • SAFE network security blueprint brings networking and Security/VPN together • Development efforts focused on networkintelligent Security/VPN solutions • Strong partnership program around Security/VPN solutions

In Summary. . . • Internet Vital to Core of Business/ Government • Security Fundamental to Health of Internet • Attacks Increasing Dramatically – Targeted at New Network and Internet Services • Security Must be Part of Network Infrastructure • Partnership (Business and Government) Critical to a Global Security Strategy • We Want to Partner With You
More Information • www. cisco. com/go/security • www. cisco. com/go/safe • www. cisco. com/go/evpn • www. cisco. com/go/securitypartners • www. cisco. com/go/csec • www. cisco. com/go/netpro • www. cisco. com/go/securitytrng • www. cert. org • www. happyhacker. org • www. infosecuritymag. com

© 2001, Cisco Systems, Inc. All rights reserved. 40
eeaad94bf32166b91fbcd43e6979e89f.ppt