6430b43bb2385982ca518c37a2a4ffcf.ppt
- Количество слайдов: 16
 Secure Electronic Transaction (SET) Shervin Erfani Electrical and Computer Engineering Department University of Windsor December 2003 Reference: Chapter 7 of the Text, pp. 234 -247 December 2, 2003 ECE Dept. – University of Windsor 1
Secure Electronic Transaction (SET) Shervin Erfani Electrical and Computer Engineering Department University of Windsor December 2003 Reference: Chapter 7 of the Text, pp. 234 -247 December 2, 2003 ECE Dept. – University of Windsor 1
 Overview of SET • • What is SET Protocol? What is the Goal of SET? How does it work? What does SET provide? December 2, 2003 ECE Dept. – University of Windsor 2
Overview of SET • • What is SET Protocol? What is the Goal of SET? How does it work? What does SET provide? December 2, 2003 ECE Dept. – University of Windsor 2
 SET Protocol • The current version, SETv 1, is a set of security protocol and formats to establish credit card transactions on the Internet. • Provides a secure communication channel among all parties involved in an E-commerce transaction • Provides trust by the use of X. 509 v 3 digital certificates • Ensures privacy December 2, 2003 ECE Dept. – University of Windsor 3
SET Protocol • The current version, SETv 1, is a set of security protocol and formats to establish credit card transactions on the Internet. • Provides a secure communication channel among all parties involved in an E-commerce transaction • Provides trust by the use of X. 509 v 3 digital certificates • Ensures privacy December 2, 2003 ECE Dept. – University of Windsor 3
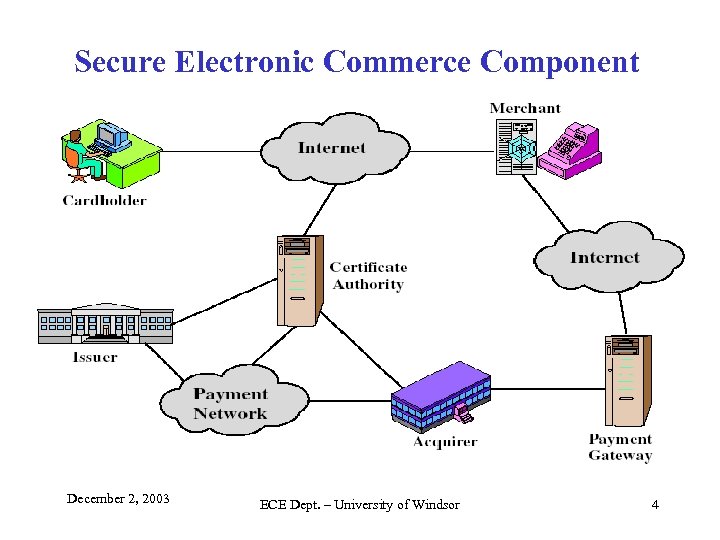 Secure Electronic Commerce Component December 2, 2003 ECE Dept. – University of Windsor 4
Secure Electronic Commerce Component December 2, 2003 ECE Dept. – University of Windsor 4
 Participants in the SET System • CARDHOLDER – Consumers and corporate purchasers using the Internet to Merchants • MERCHANT – An organization that offers goods or services over the Internet • ISSUER – A financial institution or bank providing the cardholder with the payment card • ACQUIRER – A financial institution that processes payment card authorizations and payments on behalf of the merchant • PAYMENT GATEWAT – A security interface function to process merchant payment messages for the Acquirer • CERTIFICATION AUTHORITY (CA) – A trusted entity 3 rd party issuing X. 509 v 3 public-key certificates for cardholder, merchants, and payment gateways. December 2, 2003 ECE Dept. – University of Windsor 5
Participants in the SET System • CARDHOLDER – Consumers and corporate purchasers using the Internet to Merchants • MERCHANT – An organization that offers goods or services over the Internet • ISSUER – A financial institution or bank providing the cardholder with the payment card • ACQUIRER – A financial institution that processes payment card authorizations and payments on behalf of the merchant • PAYMENT GATEWAT – A security interface function to process merchant payment messages for the Acquirer • CERTIFICATION AUTHORITY (CA) – A trusted entity 3 rd party issuing X. 509 v 3 public-key certificates for cardholder, merchants, and payment gateways. December 2, 2003 ECE Dept. – University of Windsor 5
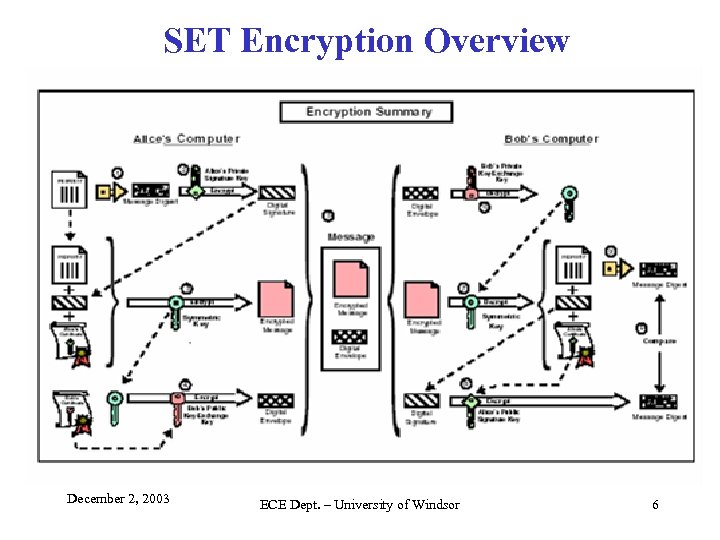 SET Encryption Overview December 2, 2003 ECE Dept. – University of Windsor 6
SET Encryption Overview December 2, 2003 ECE Dept. – University of Windsor 6
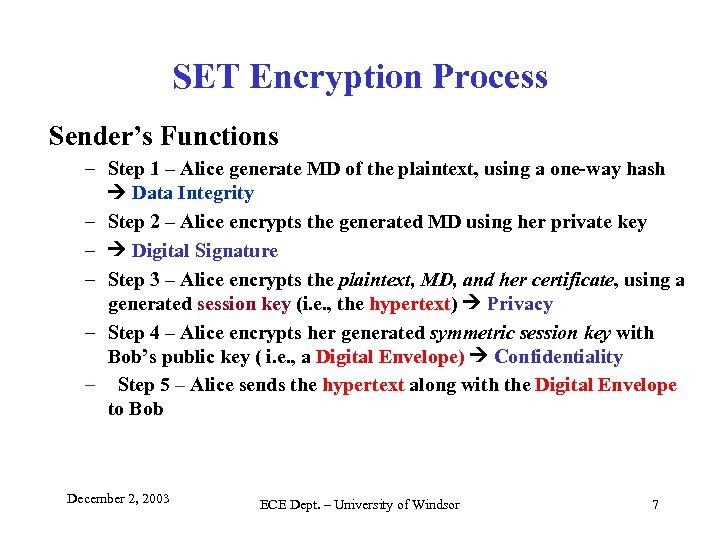 SET Encryption Process Sender’s Functions – Step 1 – Alice generate MD of the plaintext, using a one-way hash Data Integrity – Step 2 – Alice encrypts the generated MD using her private key – Digital Signature – Step 3 – Alice encrypts the plaintext, MD, and her certificate, using a generated session key (i. e. , the hypertext) Privacy – Step 4 – Alice encrypts her generated symmetric session key with Bob’s public key ( i. e. , a Digital Envelope) Confidentiality – Step 5 – Alice sends the hypertext along with the Digital Envelope to Bob December 2, 2003 ECE Dept. – University of Windsor 7
SET Encryption Process Sender’s Functions – Step 1 – Alice generate MD of the plaintext, using a one-way hash Data Integrity – Step 2 – Alice encrypts the generated MD using her private key – Digital Signature – Step 3 – Alice encrypts the plaintext, MD, and her certificate, using a generated session key (i. e. , the hypertext) Privacy – Step 4 – Alice encrypts her generated symmetric session key with Bob’s public key ( i. e. , a Digital Envelope) Confidentiality – Step 5 – Alice sends the hypertext along with the Digital Envelope to Bob December 2, 2003 ECE Dept. – University of Windsor 7
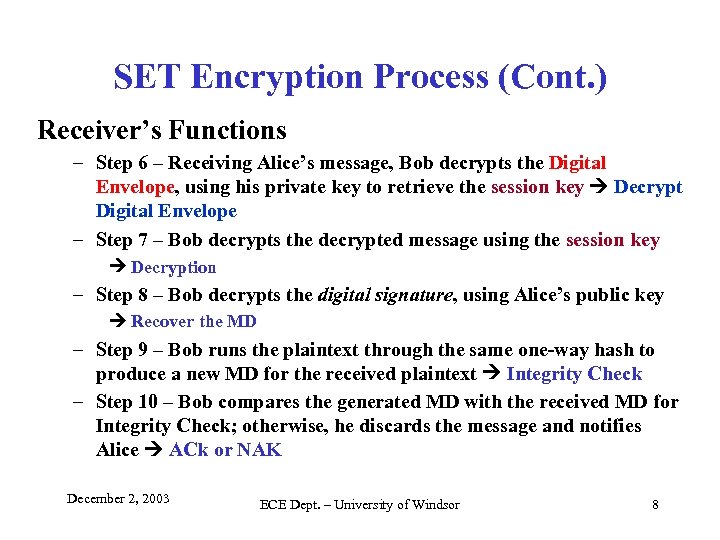 SET Encryption Process (Cont. ) Receiver’s Functions – Step 6 – Receiving Alice’s message, Bob decrypts the Digital Envelope, using his private key to retrieve the session key Decrypt Digital Envelope – Step 7 – Bob decrypts the decrypted message using the session key Decryption – Step 8 – Bob decrypts the digital signature, using Alice’s public key Recover the MD – Step 9 – Bob runs the plaintext through the same one-way hash to produce a new MD for the received plaintext Integrity Check – Step 10 – Bob compares the generated MD with the received MD for Integrity Check; otherwise, he discards the message and notifies Alice ACk or NAK December 2, 2003 ECE Dept. – University of Windsor 8
SET Encryption Process (Cont. ) Receiver’s Functions – Step 6 – Receiving Alice’s message, Bob decrypts the Digital Envelope, using his private key to retrieve the session key Decrypt Digital Envelope – Step 7 – Bob decrypts the decrypted message using the session key Decryption – Step 8 – Bob decrypts the digital signature, using Alice’s public key Recover the MD – Step 9 – Bob runs the plaintext through the same one-way hash to produce a new MD for the received plaintext Integrity Check – Step 10 – Bob compares the generated MD with the received MD for Integrity Check; otherwise, he discards the message and notifies Alice ACk or NAK December 2, 2003 ECE Dept. – University of Windsor 8
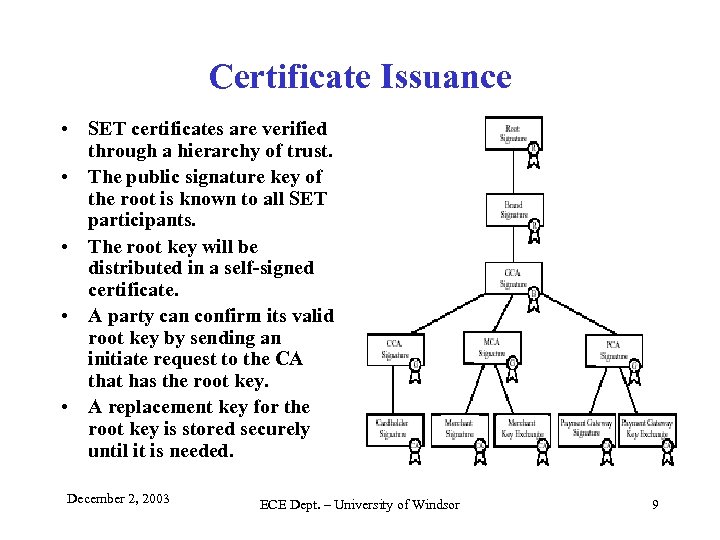 Certificate Issuance • SET certificates are verified through a hierarchy of trust. • The public signature key of the root is known to all SET participants. • The root key will be distributed in a self-signed certificate. • A party can confirm its valid root key by sending an initiate request to the CA that has the root key. • A replacement key for the root key is stored securely until it is needed. December 2, 2003 ECE Dept. – University of Windsor 9
Certificate Issuance • SET certificates are verified through a hierarchy of trust. • The public signature key of the root is known to all SET participants. • The root key will be distributed in a self-signed certificate. • A party can confirm its valid root key by sending an initiate request to the CA that has the root key. • A replacement key for the root key is stored securely until it is needed. December 2, 2003 ECE Dept. – University of Windsor 9
 SET Payment Processing SET defines a variety of transaction protocols to securely conduct E-Commerce: v. Cardholder Registration v. Merchant Registration v. Purchase Request v. Payment Authorization v. Payment Capture December 2, 2003 ECE Dept. – University of Windsor 10
SET Payment Processing SET defines a variety of transaction protocols to securely conduct E-Commerce: v. Cardholder Registration v. Merchant Registration v. Purchase Request v. Payment Authorization v. Payment Capture December 2, 2003 ECE Dept. – University of Windsor 10
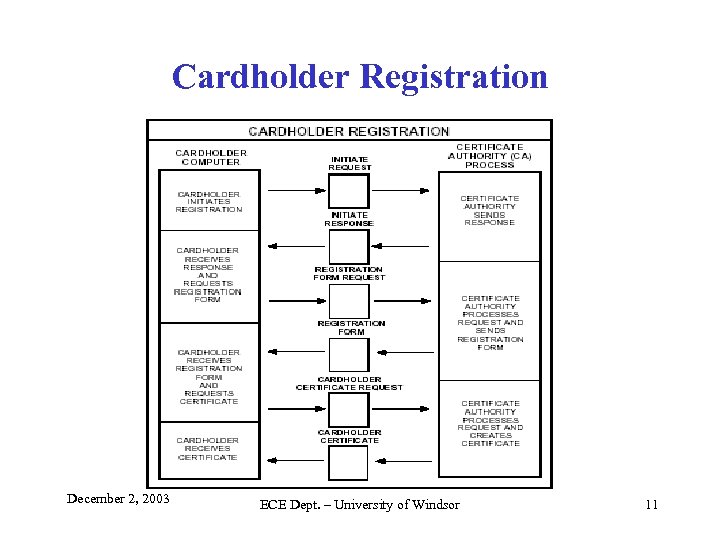 Cardholder Registration December 2, 2003 ECE Dept. – University of Windsor 11
Cardholder Registration December 2, 2003 ECE Dept. – University of Windsor 11
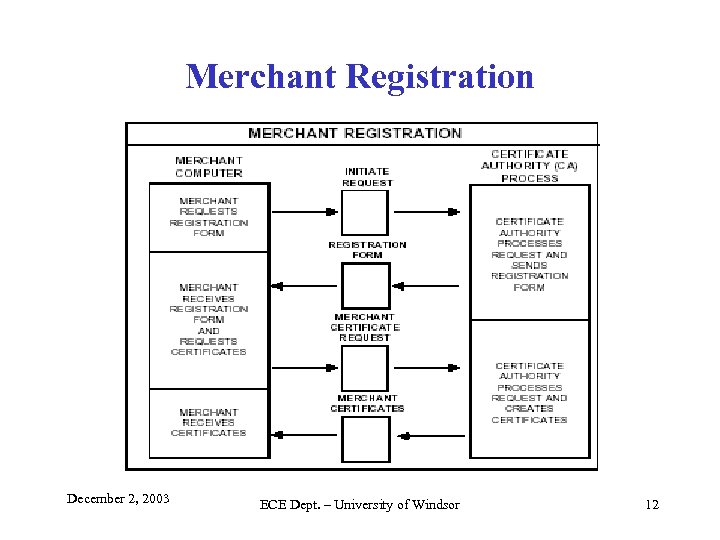 Merchant Registration December 2, 2003 ECE Dept. – University of Windsor 12
Merchant Registration December 2, 2003 ECE Dept. – University of Windsor 12
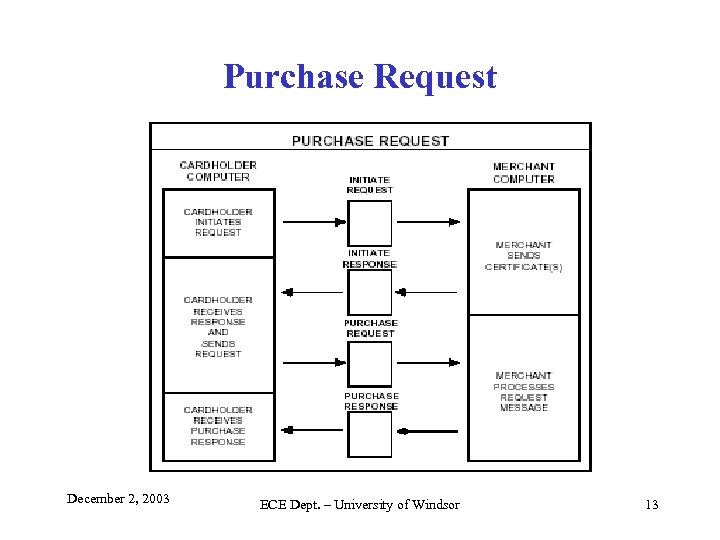 Purchase Request December 2, 2003 ECE Dept. – University of Windsor 13
Purchase Request December 2, 2003 ECE Dept. – University of Windsor 13
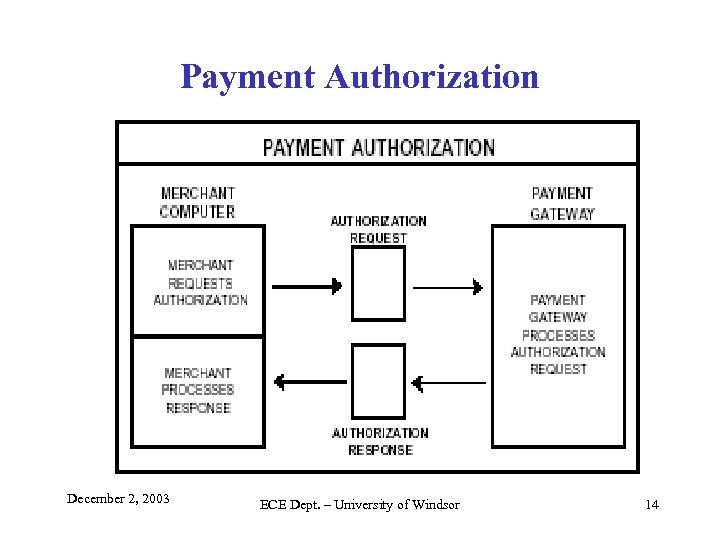 Payment Authorization December 2, 2003 ECE Dept. – University of Windsor 14
Payment Authorization December 2, 2003 ECE Dept. – University of Windsor 14
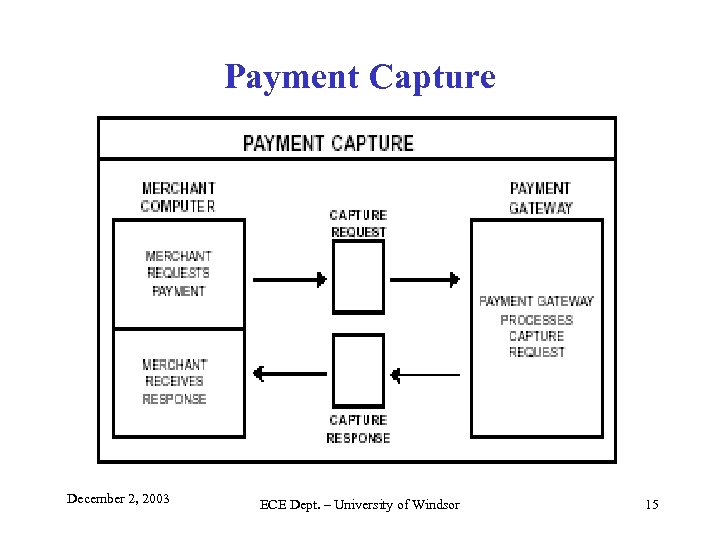 Payment Capture December 2, 2003 ECE Dept. – University of Windsor 15
Payment Capture December 2, 2003 ECE Dept. – University of Windsor 15
 What Does SET Provide? • Confidentiality of Information: Conventional encryption such as DES is used for passing Cardholder account and payment information. • Integrity of Data: RSA digital signature using SHA-1 hash codes are used. • Cardholder Account Authentication: using X. 509 v 3 digital certificates with RSA signatures. • Merchant Authentication: SET uses X. 509 v 3 digital certificates with RSA signatures December 2, 2003 ECE Dept. – University of Windsor 16
What Does SET Provide? • Confidentiality of Information: Conventional encryption such as DES is used for passing Cardholder account and payment information. • Integrity of Data: RSA digital signature using SHA-1 hash codes are used. • Cardholder Account Authentication: using X. 509 v 3 digital certificates with RSA signatures. • Merchant Authentication: SET uses X. 509 v 3 digital certificates with RSA signatures December 2, 2003 ECE Dept. – University of Windsor 16


