e8619b1a2daa97119f28bbb363920007.ppt
- Количество слайдов: 22
 Secure communication in cellular and ad hoc environments Bharat Bhargava bb@cs. purdue. edu Department of Computer Sciences, Purdue University This is supported by Motorola Communication Research Lab & National Science Foundation
Secure communication in cellular and ad hoc environments Bharat Bhargava bb@cs. purdue. edu Department of Computer Sciences, Purdue University This is supported by Motorola Communication Research Lab & National Science Foundation
 Team at Motorola: Jeff Bonta George Calcev Benetido Fouseca Trefor Delve Team at Purdue University: X. Wu Research scientist (receives his Ph. D from UC-Davis) Y. Lu Ph. D student G. Ding Ph. D student W. Wang Ph. D student
Team at Motorola: Jeff Bonta George Calcev Benetido Fouseca Trefor Delve Team at Purdue University: X. Wu Research scientist (receives his Ph. D from UC-Davis) Y. Lu Ph. D student G. Ding Ph. D student W. Wang Ph. D student
 Problem statement How to provide secure, continuous, and efficient connectivity for a mobile unit in a structured (cellular based) or unstructured (ad hoc) network environment? 3
Problem statement How to provide secure, continuous, and efficient connectivity for a mobile unit in a structured (cellular based) or unstructured (ad hoc) network environment? 3
 Challenges • Dynamic topology – Movement, node failure, energy • Heterogeneous and decentralized control • Limited resources – Bandwidth, processing ability, energy • Unfriendly environment – Selfish nodes, malicious attackers 4
Challenges • Dynamic topology – Movement, node failure, energy • Heterogeneous and decentralized control • Limited resources – Bandwidth, processing ability, energy • Unfriendly environment – Selfish nodes, malicious attackers 4
 Research contributions • Combining advantages of cellular systems and ad hoc networks to enable a more secure network structure and better performance • Designing routing protocols for ad hoc networks that adapt to both network topology and traffic congestion • Designing intruder identification protocols in ad hoc networks • Conducting experimental studies in heterogeneous wireless environments and evaluating our protocols 5
Research contributions • Combining advantages of cellular systems and ad hoc networks to enable a more secure network structure and better performance • Designing routing protocols for ad hoc networks that adapt to both network topology and traffic congestion • Designing intruder identification protocols in ad hoc networks • Conducting experimental studies in heterogeneous wireless environments and evaluating our protocols 5
 Research directions • Cellular-aided Mobile Ad Hoc Network (CAMA) • Adaptive and Heterogeneous Mobile Wireless Networks • Intruder Identification in Ad Hoc Networks 6
Research directions • Cellular-aided Mobile Ad Hoc Network (CAMA) • Adaptive and Heterogeneous Mobile Wireless Networks • Intruder Identification in Ad Hoc Networks 6
 Cellular-aided Mobile Ad Hoc Network (CAMA) Problem statement: How to realize commercial peer-to-peer applications over mobile wireless ad hoc networks? Papers: “Integrating Heterogeneous Wireless Technologies: Cellular-Aided Mobile Wireless Ad hoc Networks (CAMA)”, submitted to ACM Special Issues of the Journal on Special Topics in Mobile Networking and Applications (MONET). 7
Cellular-aided Mobile Ad Hoc Network (CAMA) Problem statement: How to realize commercial peer-to-peer applications over mobile wireless ad hoc networks? Papers: “Integrating Heterogeneous Wireless Technologies: Cellular-Aided Mobile Wireless Ad hoc Networks (CAMA)”, submitted to ACM Special Issues of the Journal on Special Topics in Mobile Networking and Applications (MONET). 7
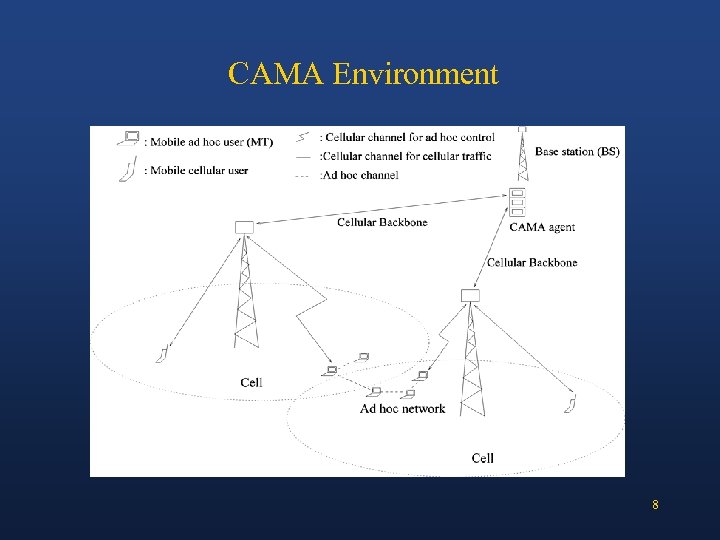 CAMA Environment 8
CAMA Environment 8
 Research with Motorola • Evaluate CAMA routing in different environments by varying: radio environment, node mobility, node density, traffic pattern, and the accuracy of position information • Authentication • Key distribution • Intrusion detection 9
Research with Motorola • Evaluate CAMA routing in different environments by varying: radio environment, node mobility, node density, traffic pattern, and the accuracy of position information • Authentication • Key distribution • Intrusion detection 9
 Adaptive and Heterogeneous Mobile Wireless Networks Problem statement: How to provide continuous connectivity for a mobile unit to a network in which every node is moving? Papers: “Secure Wireless Network with Movable Base Stations”, being revised for IEICE/IEEE Joint Special Issue on Assurance Systems and Networks. “Study of Distance Vector Routing Protocols for Mobile Ad Hoc Networks”, in Proceedings of IEEE International Conference on Pervasive Computing and Communications (Per. Com), 2003. 10
Adaptive and Heterogeneous Mobile Wireless Networks Problem statement: How to provide continuous connectivity for a mobile unit to a network in which every node is moving? Papers: “Secure Wireless Network with Movable Base Stations”, being revised for IEICE/IEEE Joint Special Issue on Assurance Systems and Networks. “Study of Distance Vector Routing Protocols for Mobile Ad Hoc Networks”, in Proceedings of IEEE International Conference on Pervasive Computing and Communications (Per. Com), 2003. 10
 Research questions in mobile ad hoc networks • Development of ad hoc routing protocols that adapt to traffic load and network congestion. – Identify the network parameters that impact the performance of routing protocols. – Determine the appropriateness of on-demand proactive approaches (given specific routing requirements and network parameters). – Identify features of ad hoc networks that can be used to improve routing. 11
Research questions in mobile ad hoc networks • Development of ad hoc routing protocols that adapt to traffic load and network congestion. – Identify the network parameters that impact the performance of routing protocols. – Determine the appropriateness of on-demand proactive approaches (given specific routing requirements and network parameters). – Identify features of ad hoc networks that can be used to improve routing. 11
 Ongoing research • Study of proactive and on-demand approaches • Congestion-aware distance vector routing protocol • Packet loss study 12
Ongoing research • Study of proactive and on-demand approaches • Congestion-aware distance vector routing protocol • Packet loss study 12
 Characteristics of wireless networks with movable base stations • • • Large scale Heterogeneity Autonomous sub-nets Base stations have more resources Base stations take more responsibilities 13
Characteristics of wireless networks with movable base stations • • • Large scale Heterogeneity Autonomous sub-nets Base stations have more resources Base stations take more responsibilities 13
 Research questions • How to organize the network? – Minimize the effect of motion – Minimize the involvement of mobile host • How to build routing protocol? – IP-compliant – Cooperate with various intra-subnet routing protocols • How to secure communications? – Authenticate – Maintain authentication when a host is roaming 14
Research questions • How to organize the network? – Minimize the effect of motion – Minimize the involvement of mobile host • How to build routing protocol? – IP-compliant – Cooperate with various intra-subnet routing protocols • How to secure communications? – Authenticate – Maintain authentication when a host is roaming 14
 Intruder Identification in Ad Hoc Networks Problem statement: Intruder identification in ad hoc networks is the procedure of identifying the user or host that conducts the inappropriate, incorrect, or anomalous activities that threaten the connectivity or reliability of the networks and the authenticity of the data traffic in the networks. Papers: “On Security Study of Two Distance Vector Routing Protocols for Mobile Ad Hoc Networks”, in Proceedings of IEEE International Conference on Pervasive Computing and Communications (Per. Com), 2003. “On Vulnerability and Protection of Ad Hoc On-demand Distance Vector Protocol”, in Proceedings of 10 th IEEE International Conference on Telecommunication (ICT), 2003. 15
Intruder Identification in Ad Hoc Networks Problem statement: Intruder identification in ad hoc networks is the procedure of identifying the user or host that conducts the inappropriate, incorrect, or anomalous activities that threaten the connectivity or reliability of the networks and the authenticity of the data traffic in the networks. Papers: “On Security Study of Two Distance Vector Routing Protocols for Mobile Ad Hoc Networks”, in Proceedings of IEEE International Conference on Pervasive Computing and Communications (Per. Com), 2003. “On Vulnerability and Protection of Ad Hoc On-demand Distance Vector Protocol”, in Proceedings of 10 th IEEE International Conference on Telecommunication (ICT), 2003. 15
 Research Motivation • Two types of attacks target Ad Hoc network – External attacks – Internal attacks • Why intrusion detection itself is not enough – Detecting intrusion without removing the malicious host leaves the protection in a passive mode – Identifying the source of the attack may accelerate the detection of other attacks 16
Research Motivation • Two types of attacks target Ad Hoc network – External attacks – Internal attacks • Why intrusion detection itself is not enough – Detecting intrusion without removing the malicious host leaves the protection in a passive mode – Identifying the source of the attack may accelerate the detection of other attacks 16
 Evaluation Criteria • Accuracy – False coverage: Number of normal hosts that are incorrectly marked as suspected. – False exclusion: Number of malicious hosts that are not identified as such. • Overhead – Overhead measures the increases in control packets and computation costs for identifying the attackers (e. g. verifying signed packets, updating blacklists). – Workload of identifying the malicious hosts in multiple rounds 17
Evaluation Criteria • Accuracy – False coverage: Number of normal hosts that are incorrectly marked as suspected. – False exclusion: Number of malicious hosts that are not identified as such. • Overhead – Overhead measures the increases in control packets and computation costs for identifying the attackers (e. g. verifying signed packets, updating blacklists). – Workload of identifying the malicious hosts in multiple rounds 17
 Evaluation Criteria • Effectiveness – Effectiveness: Increase in the performance of ad hoc networks after the malicious hosts are identified and isolated. Metrics include the increase of the packet delivery ratio, the decrease of average delay, or the decrease of normalized protocol overhead (control packets/delivered packets). • Robustness – Robustness of the algorithm: Its ability to resist different kinds of attacks. 18
Evaluation Criteria • Effectiveness – Effectiveness: Increase in the performance of ad hoc networks after the malicious hosts are identified and isolated. Metrics include the increase of the packet delivery ratio, the decrease of average delay, or the decrease of normalized protocol overhead (control packets/delivered packets). • Robustness – Robustness of the algorithm: Its ability to resist different kinds of attacks. 18
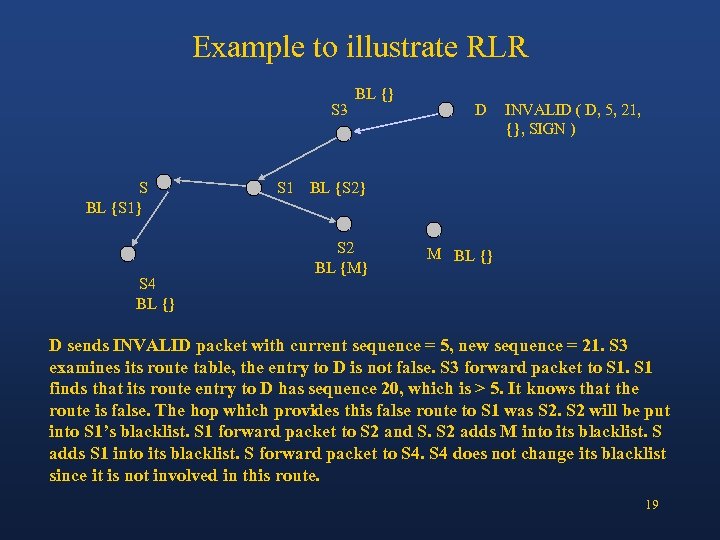 Example to illustrate RLR S 3 S BL {S 1} S 4 BL {} D INVALID ( D, 5, 21, {}, SIGN ) S 1 BL {S 2} S 2 BL {M} M BL {} D sends INVALID packet with current sequence = 5, new sequence = 21. S 3 examines its route table, the entry to D is not false. S 3 forward packet to S 1 finds that its route entry to D has sequence 20, which is > 5. It knows that the route is false. The hop which provides this false route to S 1 was S 2 will be put into S 1’s blacklist. S 1 forward packet to S 2 and S. S 2 adds M into its blacklist. S adds S 1 into its blacklist. S forward packet to S 4 does not change its blacklist since it is not involved in this route. 19
Example to illustrate RLR S 3 S BL {S 1} S 4 BL {} D INVALID ( D, 5, 21, {}, SIGN ) S 1 BL {S 2} S 2 BL {M} M BL {} D sends INVALID packet with current sequence = 5, new sequence = 21. S 3 examines its route table, the entry to D is not false. S 3 forward packet to S 1 finds that its route entry to D has sequence 20, which is > 5. It knows that the route is false. The hop which provides this false route to S 1 was S 2 will be put into S 1’s blacklist. S 1 forward packet to S 2 and S. S 2 adds M into its blacklist. S adds S 1 into its blacklist. S forward packet to S 4 does not change its blacklist since it is not involved in this route. 19
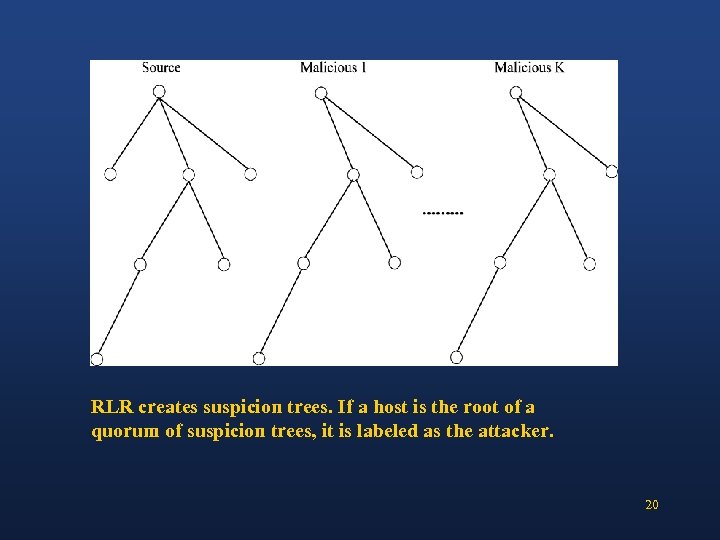 RLR creates suspicion trees. If a host is the root of a quorum of suspicion trees, it is labeled as the attacker. 20
RLR creates suspicion trees. If a host is the root of a quorum of suspicion trees, it is labeled as the attacker. 20
 Securing Ad Hoc networks -- Establish trust relationship in open environments • Evaluate known knowledge – Known knowledge: • Interpretations of observations • Recommendations – An algorithm that evaluates trust among hosts is being developed – A host’s trustworthiness affects the trust toward the hosts on the route • Predict of trustworthiness of a host – Current approach uses the result of evaluation as prediction. 21
Securing Ad Hoc networks -- Establish trust relationship in open environments • Evaluate known knowledge – Known knowledge: • Interpretations of observations • Recommendations – An algorithm that evaluates trust among hosts is being developed – A host’s trustworthiness affects the trust toward the hosts on the route • Predict of trustworthiness of a host – Current approach uses the result of evaluation as prediction. 21
 Securing Ad Hoc networks -- Establish trust relationship in open environments • What trust information is needed when adding/ removing suspicious host from blacklist? – The trust opinion of S 1 towards an entity S 2 in a certain context R • What characteristics of trust need to be included in the model? – Dependability: combination of competence, benevolence, and integrity – Predictability 22
Securing Ad Hoc networks -- Establish trust relationship in open environments • What trust information is needed when adding/ removing suspicious host from blacklist? – The trust opinion of S 1 towards an entity S 2 in a certain context R • What characteristics of trust need to be included in the model? – Dependability: combination of competence, benevolence, and integrity – Predictability 22


