6b8731d9f31b4673b7ca89a12c61ed7b.ppt
- Количество слайдов: 83
 SEC 407 ISA Server Internals and Infrastructure Design Zachary Gutt and Steve Riley Product Managers Security Business Unit Microsoft Corporation
SEC 407 ISA Server Internals and Infrastructure Design Zachary Gutt and Steve Riley Product Managers Security Business Unit Microsoft Corporation
 Why? Firewalls are “geeky” toys Administrators typically are geeks Intimate knowledge of firewall packet handling is often necessary to fully understand how to secure a protocol ISA Server documentation lacks sufficient detail Session’s content discusses many common questions on the newsgroups
Why? Firewalls are “geeky” toys Administrators typically are geeks Intimate knowledge of firewall packet handling is often necessary to fully understand how to secure a protocol ISA Server documentation lacks sufficient detail Session’s content discusses many common questions on the newsgroups
 Agenda Packet flows in publishing DMZ scenarios SSL handing in web publishing Packet filters and filtering Client-type things Authentication, protocol handling, DNS ISA Server vs. RRAS IPSec and NAT
Agenda Packet flows in publishing DMZ scenarios SSL handing in web publishing Packet filters and filtering Client-type things Authentication, protocol handling, DNS ISA Server vs. RRAS IPSec and NAT
 Credits DNS Jim Harrison, Microsoft ISA Server vs. RRAS and Q 310888 Craig Nelson, Avanade Some extensibility info Ronald Beekelaar, Beekelaar Consultancy Interesting design alternative Tom Schinder
Credits DNS Jim Harrison, Microsoft ISA Server vs. RRAS and Q 310888 Craig Nelson, Avanade Some extensibility info Ronald Beekelaar, Beekelaar Consultancy Interesting design alternative Tom Schinder
 Packet flows and publishing
Packet flows and publishing
 Packet flows in publishing Server publishing Simple one-to-one mapping between outside address and LAT member over one particular protocol “Half-NAT” Web publishing Multiple servers and sites with one external IP address Use URLs to direct traffic “Full-NAT”
Packet flows in publishing Server publishing Simple one-to-one mapping between outside address and LAT member over one particular protocol “Half-NAT” Web publishing Multiple servers and sites with one external IP address Use URLs to direct traffic “Full-NAT”
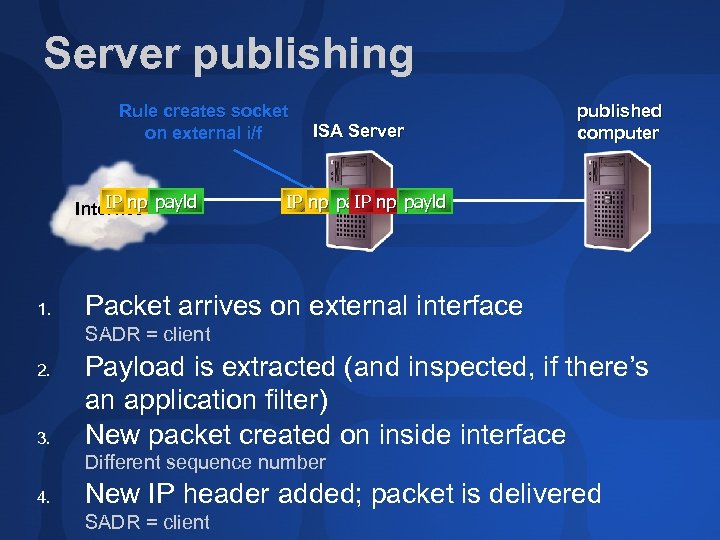 Server publishing Rule creates socket on external i/f IP np Internet payld 1. ISA Server published computer IP np payld IP Packet arrives on external interface SADR = client 2. 3. Payload is extracted (and inspected, if there’s an application filter) New packet created on inside interface Different sequence number 4. New IP header added; packet is delivered SADR = client
Server publishing Rule creates socket on external i/f IP np Internet payld 1. ISA Server published computer IP np payld IP Packet arrives on external interface SADR = client 2. 3. Payload is extracted (and inspected, if there’s an application filter) New packet created on inside interface Different sequence number 4. New IP header added; packet is delivered SADR = client
 Server publishing Multiple servers Remember: socket = {IPAddr, port, protocol} Different protocols Can reuse same external IP address; port number will be different {IPAddr, port 1, prot. A} {IPAddr, port 2, prot. B} Same protocols Must use additional external IP address; port numbers will be same {IPAddr 1, port, prot. A} {IPAddr 2, port, prot. A}
Server publishing Multiple servers Remember: socket = {IPAddr, port, protocol} Different protocols Can reuse same external IP address; port number will be different {IPAddr, port 1, prot. A} {IPAddr, port 2, prot. B} Same protocols Must use additional external IP address; port numbers will be same {IPAddr 1, port, prot. A} {IPAddr 2, port, prot. A}
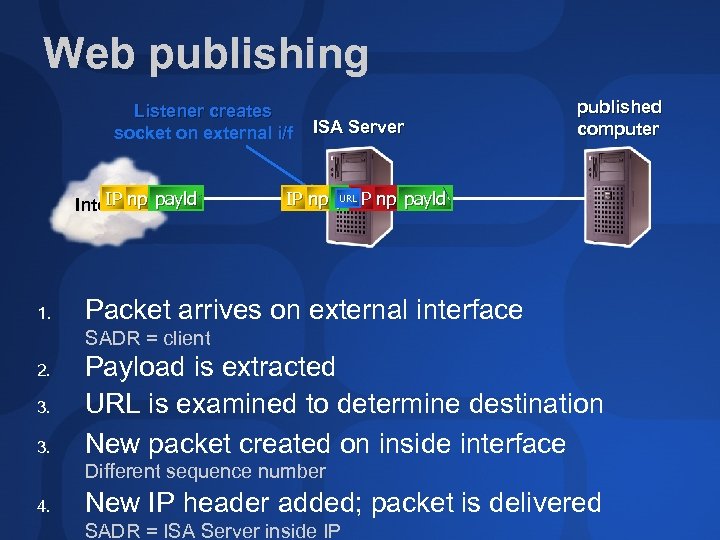 Web publishing Listener creates socket on external i/f IP np Internet payld 1. ISA Server published computer URL IP np payld IP Packet arrives on external interface SADR = client 2. 3. 3. Payload is extracted URL is examined to determine destination New packet created on inside interface Different sequence number 4. New IP header added; packet is delivered SADR = ISA Server inside IP
Web publishing Listener creates socket on external i/f IP np Internet payld 1. ISA Server published computer URL IP np payld IP Packet arrives on external interface SADR = client 2. 3. 3. Payload is extracted URL is examined to determine destination New packet created on inside interface Different sequence number 4. New IP header added; packet is delivered SADR = ISA Server inside IP
 Web publishing Multiple servers The listener creates the socket Can have multiple listeners on different external IPs for varying auth. N needs Use separate DNS names for each The rule directs the request Destination sets indicate which rule Set contains URL entered in browser
Web publishing Multiple servers The listener creates the socket Can have multiple listeners on different external IPs for varying auth. N needs Use separate DNS names for each The rule directs the request Destination sets indicate which rule Set contains URL entered in browser
 Web publishing Multiple auth. N needs Requirements www. example. com is public my. example. com has no auth. N in app Use ISA Server for auth. N; basic over HTTPS Components Two DNS “A” records Two listeners Two destination sets Two publishing rules Trusted computer certificate
Web publishing Multiple auth. N needs Requirements www. example. com is public my. example. com has no auth. N in app Use ISA Server for auth. N; basic over HTTPS Components Two DNS “A” records Two listeners Two destination sets Two publishing rules Trusted computer certificate
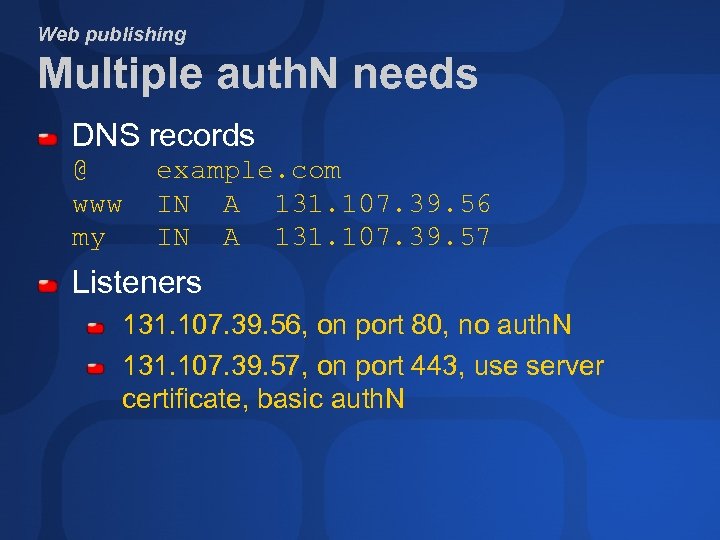 Web publishing Multiple auth. N needs DNS records @ www my example. com IN A 131. 107. 39. 56 IN A 131. 107. 39. 57 Listeners 131. 107. 39. 56, on port 80, no auth. N 131. 107. 39. 57, on port 443, use server certificate, basic auth. N
Web publishing Multiple auth. N needs DNS records @ www my example. com IN A 131. 107. 39. 56 IN A 131. 107. 39. 57 Listeners 131. 107. 39. 56, on port 80, no auth. N 131. 107. 39. 57, on port 443, use server certificate, basic auth. N
 Web publishing Multiple auth. N needs Destination sets DSPublic: www. example. com DSPrivate: my. example. com Publishing rules WWW: send to inside-web-name for DSPublic MY: send to inside-internal-name for DSPrivate
Web publishing Multiple auth. N needs Destination sets DSPublic: www. example. com DSPrivate: my. example. com Publishing rules WWW: send to inside-web-name for DSPublic MY: send to inside-internal-name for DSPrivate
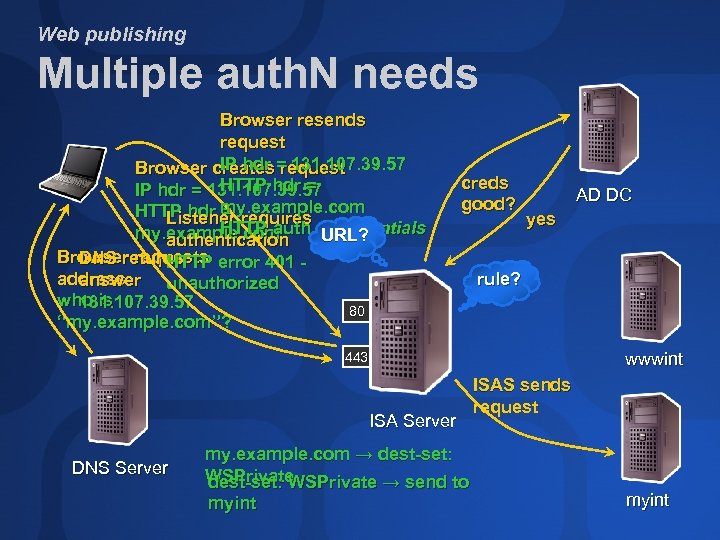 Web publishing Multiple auth. N needs Browser resends request IP hdr request Browser creates = 131. 107. 39. 57 HTTP hdr = IP hdr = 131. 107. 39. 57 HTTP hdr my. example. com = Listener requires HTTP-auth = credentials my. example. com URL? authentication Browser requests error 401 DNS returns HTTP address answer unauthorized who is 131. 107. 39. 57 80 “my. example. com”? creds good? AD DC yes rule? wwwint 443 ISA Server DNS Server my. example. com → dest-set: WSPrivate → send to myint ISAS sends request myint
Web publishing Multiple auth. N needs Browser resends request IP hdr request Browser creates = 131. 107. 39. 57 HTTP hdr = IP hdr = 131. 107. 39. 57 HTTP hdr my. example. com = Listener requires HTTP-auth = credentials my. example. com URL? authentication Browser requests error 401 DNS returns HTTP address answer unauthorized who is 131. 107. 39. 57 80 “my. example. com”? creds good? AD DC yes rule? wwwint 443 ISA Server DNS Server my. example. com → dest-set: WSPrivate → send to myint ISAS sends request myint
 DMZ scenarios
DMZ scenarios
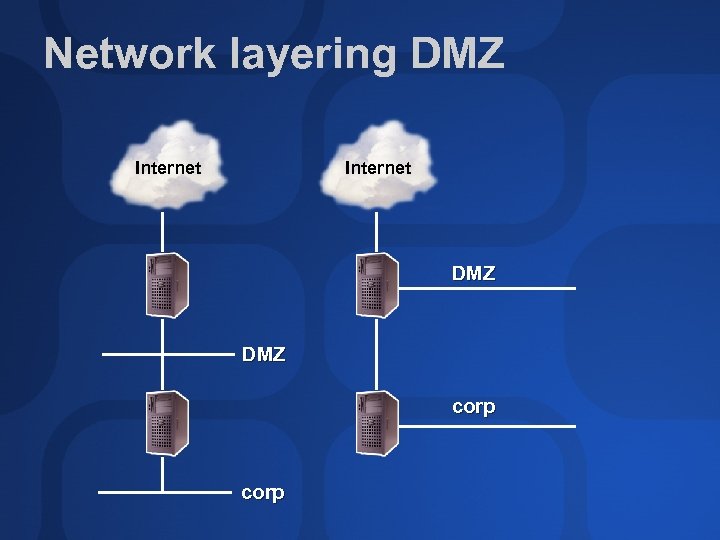
 DMZ Scenarios The two traditional kinds Disadvantages of using “DMZ” interfaces in ISA Server Best way to design layered networks
DMZ Scenarios The two traditional kinds Disadvantages of using “DMZ” interfaces in ISA Server Best way to design layered networks
 Network layering DMZ Internet DMZ corp
Network layering DMZ Internet DMZ corp
 Layered DMZ characteristics Multiple firewalls Each firewall protects its own network Sometimes use different brands Heterogeneity can be costly, though Looks like the world’s only political DMZ
Layered DMZ characteristics Multiple firewalls Each firewall protects its own network Sometimes use different brands Heterogeneity can be costly, though Looks like the world’s only political DMZ
 Screened subnet “DMZ” Internet DMZ corp
Screened subnet “DMZ” Internet DMZ corp
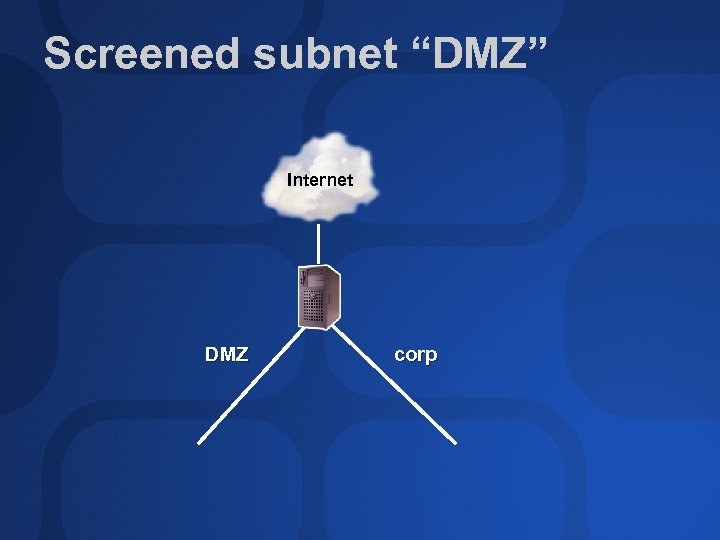
 Screened subnet characteristics Not really a DMZ More complex to build Too many rules to wrap your brain around Opportunities for misconfiguration Performance problems
Screened subnet characteristics Not really a DMZ More complex to build Too many rules to wrap your brain around Opportunities for misconfiguration Performance problems
 ISA Server DMZs ISA Server calls them “perimeter networks” Types Back-to-back (regular DMZ) Three-homed (screened subnet) Interesting undocumented third choice Pretty easy to choose which But first…
ISA Server DMZs ISA Server calls them “perimeter networks” Types Back-to-back (regular DMZ) Three-homed (screened subnet) Interesting undocumented third choice Pretty easy to choose which But first…
 Network interfaces Two kinds Internal External Two flavors of external Internet-facing DMZ
Network interfaces Two kinds Internal External Two flavors of external Internet-facing DMZ
 Internal interfaces Can have more than one Defined by the LAT Any interface whose IP address is in LAT is an internal interface
Internal interfaces Can have more than one Defined by the LAT Any interface whose IP address is in LAT is an internal interface
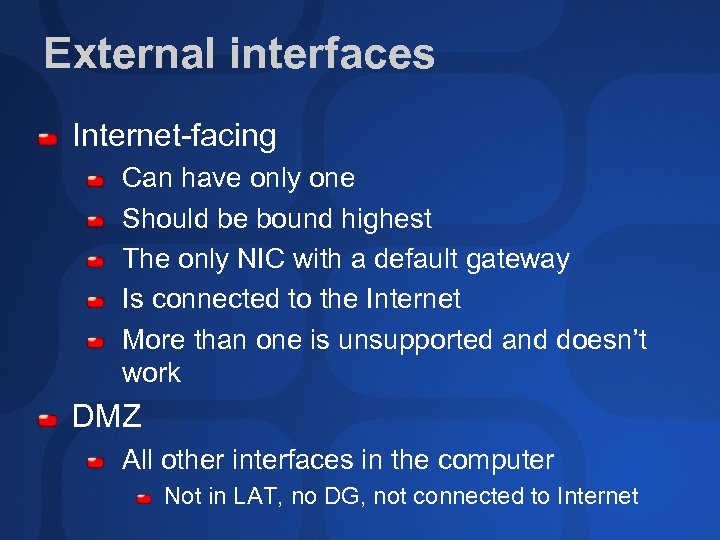 External interfaces Internet-facing Can have only one Should be bound highest The only NIC with a default gateway Is connected to the Internet More than one is unsupported and doesn’t work DMZ All other interfaces in the computer Not in LAT, no DG, not connected to Internet
External interfaces Internet-facing Can have only one Should be bound highest The only NIC with a default gateway Is connected to the Internet More than one is unsupported and doesn’t work DMZ All other interfaces in the computer Not in LAT, no DG, not connected to Internet
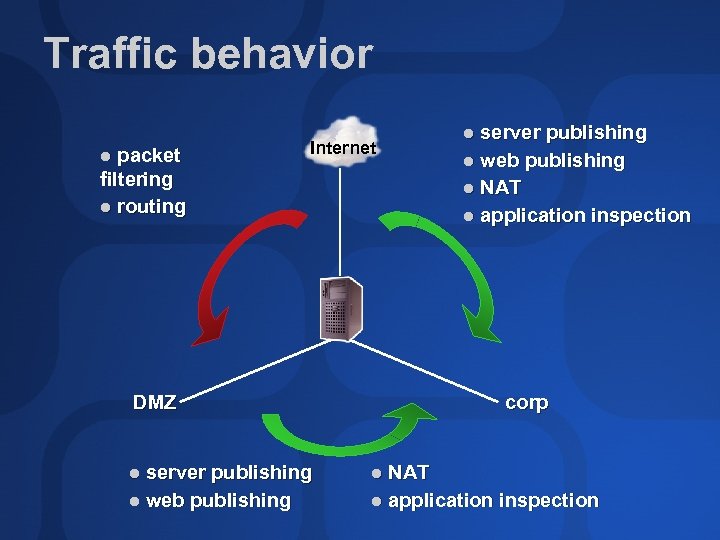 Traffic behavior packet filtering routing Internet DMZ server publishing web publishing NAT application inspection corp NAT application inspection
Traffic behavior packet filtering routing Internet DMZ server publishing web publishing NAT application inspection corp NAT application inspection
 Suboptimal design Traffic into and out of DMZ interfaces isn’t well-protected Basic packet filtering is just like any other firewall Has no knowledge of application protocols Can’t inspect for conformance Doesn’t use web or application filters Recommendation— Don’t use three-homed design
Suboptimal design Traffic into and out of DMZ interfaces isn’t well-protected Basic packet filtering is just like any other firewall Has no knowledge of application protocols Can’t inspect for conformance Doesn’t use web or application filters Recommendation— Don’t use three-homed design
 Proper design Back-to-back ISA Servers LATs Outside: IP address range(s) of DMZ net Inside: IP address range(s) of corp net Achieve inspection everywhere Internet to DMZ to corp net It’s this inspection that’s the value
Proper design Back-to-back ISA Servers LATs Outside: IP address range(s) of DMZ net Inside: IP address range(s) of corp net Achieve inspection everywhere Internet to DMZ to corp net It’s this inspection that’s the value
 Back-to-back publishing In DMZ Normal publishing method In corp net Publish resource on inside ISA Server Publish inside ISA Server on outside ISA Server Use SSL offload cards for HTTPS http: //www. microsoft. com/isaserver/partners/ ssl. asp AEP Crypto—fast and cheap!
Back-to-back publishing In DMZ Normal publishing method In corp net Publish resource on inside ISA Server Publish inside ISA Server on outside ISA Server Use SSL offload cards for HTTPS http: //www. microsoft. com/isaserver/partners/ ssl. asp AEP Crypto—fast and cheap!
 Interesting alternative Three-homed design No “DMZ” interface Two internal interfaces Application inspection between Internet and all internal interfaces Need to protect cross-interface communications—how? Good for constrained budgets
Interesting alternative Three-homed design No “DMZ” interface Two internal interfaces Application inspection between Internet and all internal interfaces Need to protect cross-interface communications—how? Good for constrained budgets
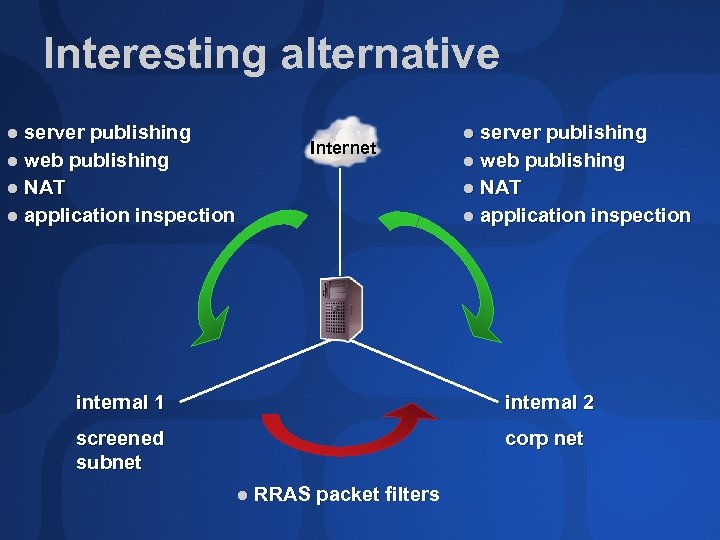 Interesting alternative server publishing web publishing NAT application inspection Internet server publishing web publishing NAT application inspection internal 1 internal 2 screened subnet corp net RRAS packet filters
Interesting alternative server publishing web publishing NAT application inspection Internet server publishing web publishing NAT application inspection internal 1 internal 2 screened subnet corp net RRAS packet filters
 RRAS filters Use RRAS filtering to control communications between nets Think securely! Block all from 1 to 2… …except that which is necessary Block all from 2 to 1… …except that which is necessary Don’t allow everything from corp to screened Not concerned with VPN protocols here RRAS is just providing the filtering
RRAS filters Use RRAS filtering to control communications between nets Think securely! Block all from 1 to 2… …except that which is necessary Block all from 2 to 1… …except that which is necessary Don’t allow everything from corp to screened Not concerned with VPN protocols here RRAS is just providing the filtering
 SSL handling and certificates
SSL handling and certificates
 SSL handling Three options “Passthrough” or “tunneling” “Termination” “Regeneration” 2 and 3 sometimes referred to as bridging —but which kind?
SSL handling Three options “Passthrough” or “tunneling” “Termination” “Regeneration” 2 and 3 sometimes referred to as bridging —but which kind?
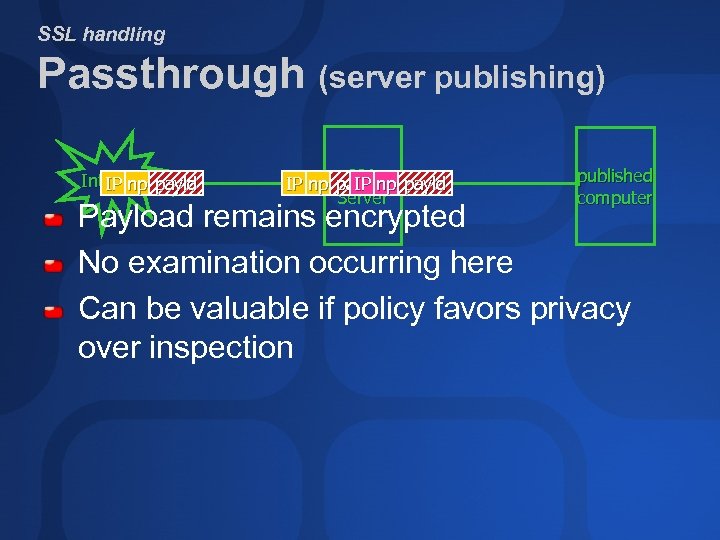 SSL handling Passthrough (server publishing) Internet payld IP np ISA IP np payld IP Server published computer Payload remains encrypted No examination occurring here Can be valuable if policy favors privacy over inspection
SSL handling Passthrough (server publishing) Internet payld IP np ISA IP np payld IP Server published computer Payload remains encrypted No examination occurring here Can be valuable if policy favors privacy over inspection
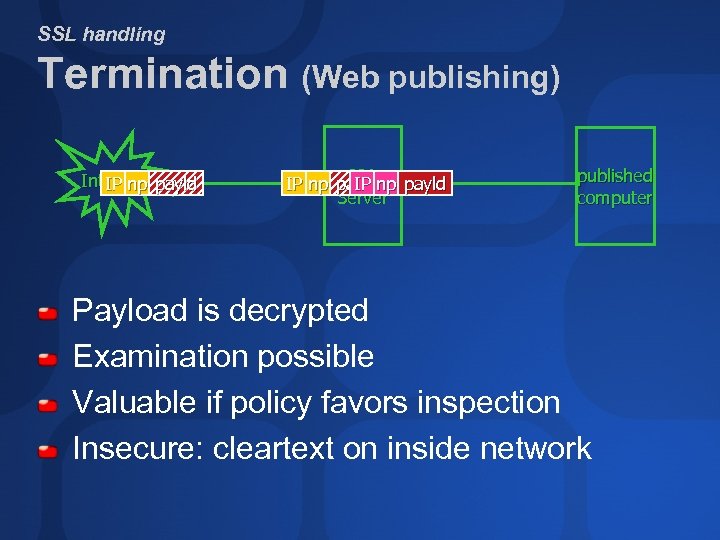 SSL handling Termination (Web publishing) Internet payld IP np ISA IP np payld IP Server published computer Payload is decrypted Examination possible Valuable if policy favors inspection Insecure: cleartext on inside network
SSL handling Termination (Web publishing) Internet payld IP np ISA IP np payld IP Server published computer Payload is decrypted Examination possible Valuable if policy favors inspection Insecure: cleartext on inside network
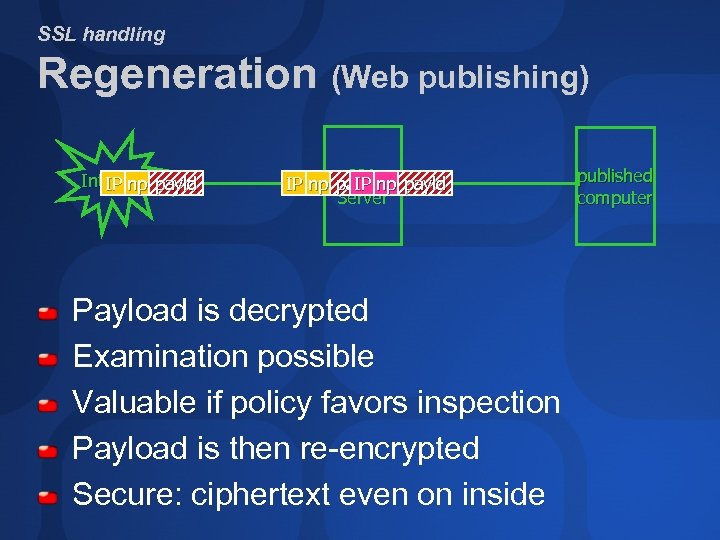 SSL handling Regeneration (Web publishing) Internet payld IP np ISA IP np payld IP Server Payload is decrypted Examination possible Valuable if policy favors inspection Payload is then re-encrypted Secure: ciphertext even on inside published computer
SSL handling Regeneration (Web publishing) Internet payld IP np ISA IP np payld IP Server Payload is decrypted Examination possible Valuable if policy favors inspection Payload is then re-encrypted Secure: ciphertext even on inside published computer
 Certificates Server certificates When ISA Server is an HTTPS server Obtain from public CA Choose on the listener tab Client certificates When published server requires client certs for auth. N Obtain from internal CA Choose on the listener tab Certs for published web servers Issued from internal CA Add internal root to ISA Server
Certificates Server certificates When ISA Server is an HTTPS server Obtain from public CA Choose on the listener tab Client certificates When published server requires client certs for auth. N Obtain from internal CA Choose on the listener tab Certs for published web servers Issued from internal CA Add internal root to ISA Server
 Packet filters, packet filtering and IP routing
Packet filters, packet filtering and IP routing
 Does this hurt?
Does this hurt?
 Traffic passing LAT ↔ external is well-understood Protocol rules: getting out Publishing rules: getting in But… What are packet filters? What happens when you turn on packet filtering? What is IP routing?
Traffic passing LAT ↔ external is well-understood Protocol rules: getting out Publishing rules: getting in But… What are packet filters? What happens when you turn on packet filtering? What is IP routing?
 Access policy Packet filters allow traffic into and out of the external interface Are independent of protocol and publishing rules Should always enable packet filtering to protect ISA Server computer Blocks nearly everything except… Some ICMP, outbound DNS questions
Access policy Packet filters allow traffic into and out of the external interface Are independent of protocol and publishing rules Should always enable packet filtering to protect ISA Server computer Blocks nearly everything except… Some ICMP, outbound DNS questions
 Packet filters From/to ISA Server computer Not recommended! (It’s a firewall, not a workstation) External ↔ DMZ Need a filter for each protocol allowed into the DMZ Don’t need response rules LAT ↔ external/DMZ Only for non-TCP/UDP protocols
Packet filters From/to ISA Server computer Not recommended! (It’s a firewall, not a workstation) External ↔ DMZ Need a filter for each protocol allowed into the DMZ Don’t need response rules LAT ↔ external/DMZ Only for non-TCP/UDP protocols
 IP routing Needed for non-TCP/UDP access by secure. NAT clients Improves performance by enabling the kernel mode data pump! Huh? Checkbox has a completely different meaning than what’s implied by “IP routing”
IP routing Needed for non-TCP/UDP access by secure. NAT clients Improves performance by enabling the kernel mode data pump! Huh? Checkbox has a completely different meaning than what’s implied by “IP routing”
 Secondary connections “Data channels” negotiated and opened while primary connection still exists Examples St(r)eaming media Audio/video conferencing FTP
Secondary connections “Data channels” negotiated and opened while primary connection still exists Examples St(r)eaming media Audio/video conferencing FTP
 KMDP If: A protocol has secondary connections There is no application filter that wants to inspect the data stream Then: Enabling IP routing sends secondary connections through the KMDP Big performance boost Works with All client types Filters that are KMDP-aware
KMDP If: A protocol has secondary connections There is no application filter that wants to inspect the data stream Then: Enabling IP routing sends secondary connections through the KMDP Big performance boost Works with All client types Filters that are KMDP-aware
 A bad configuration If you: Enable packet filtering Write packet filters for TCP, UDP, and other IP protocols Enable routing Have no protocol or publishing rules You have a basic, stupid layer 3/layer 4 stateful inspection firewall
A bad configuration If you: Enable packet filtering Write packet filters for TCP, UDP, and other IP protocols Enable routing Have no protocol or publishing rules You have a basic, stupid layer 3/layer 4 stateful inspection firewall
 Clients
Clients
 Client types Secure. NAT Crazy name—there is no client software or configuration Handled by firewall service HTTP requests redirected to web proxy service if redirector is enabled Firewall client Handled by firewall service HTTP requests redirected to web proxy service if redirector is enabled Web proxy client Handled by web proxy service
Client types Secure. NAT Crazy name—there is no client software or configuration Handled by firewall service HTTP requests redirected to web proxy service if redirector is enabled Firewall client Handled by firewall service HTTP requests redirected to web proxy service if redirector is enabled Web proxy client Handled by web proxy service
 “All protocols” Means different things Secure. NAT Only those where a (simple) protocol definition exists Need application filter for complex Firewall client Literally everything Web proxy client Web protocols
“All protocols” Means different things Secure. NAT Only those where a (simple) protocol definition exists Need application filter for complex Firewall client Literally everything Web proxy client Web protocols
 Authentication Secure. NAT No user authentication; only IP addresses can be used in client address sets Firewall client Carries user credentials Authenticates for all protocols There’s an exception… Web proxy client Carries user credentials
Authentication Secure. NAT No user authentication; only IP addresses can be used in client address sets Firewall client Carries user credentials Authenticates for all protocols There’s an exception… Web proxy client Carries user credentials
 Firewall client authentication Exemption Scenario User is FW client only HTTP redirector filter is on Sends FW client HTTP requests to web proxy User credentials are lost Firewall service doesn’t forward Logs will show anonymous ID Solution Configure redirector to reject HTTP requests from FW and Secure. NAT clients
Firewall client authentication Exemption Scenario User is FW client only HTTP redirector filter is on Sends FW client HTTP requests to web proxy User credentials are lost Firewall service doesn’t forward Logs will show anonymous ID Solution Configure redirector to reject HTTP requests from FW and Secure. NAT clients
 Firewall client operation Intercepts all Win. Sock API calls—calls to external addresses are redirected to ISA Server Layered service provider; works with all IP protocols Supports user authentication; can set permissions by protocol and port No need for address editing
Firewall client operation Intercepts all Win. Sock API calls—calls to external addresses are redirected to ISA Server Layered service provider; works with all IP protocols Supports user authentication; can set permissions by protocol and port No need for address editing
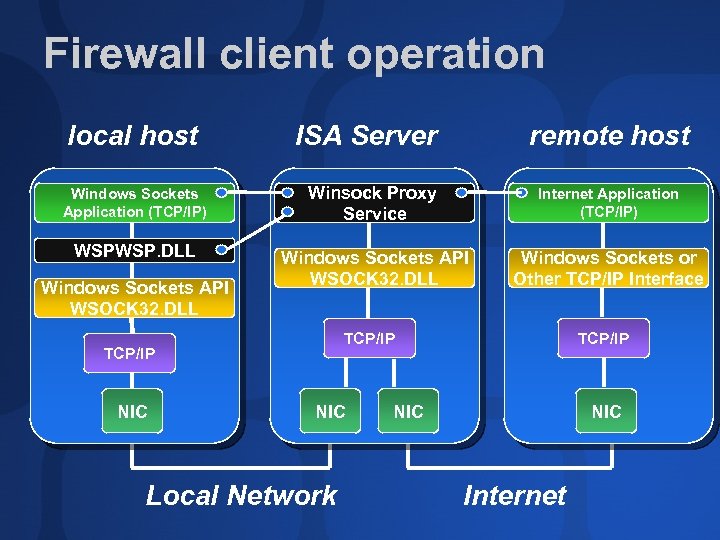 Firewall client operation local host ISA Server remote host Windows Sockets Application (TCP/IP) Winsock Proxy Service Internet Application (TCP/IP) WSPWSP. DLL Windows Sockets API WSOCK 32. DLL Windows Sockets or Other TCP/IP Interface Windows Sockets API WSOCK 32. DLL TCP/IP NIC Local Network TCP/IP NIC Internet
Firewall client operation local host ISA Server remote host Windows Sockets Application (TCP/IP) Winsock Proxy Service Internet Application (TCP/IP) WSPWSP. DLL Windows Sockets API WSOCK 32. DLL Windows Sockets or Other TCP/IP Interface Windows Sockets API WSOCK 32. DLL TCP/IP NIC Local Network TCP/IP NIC Internet
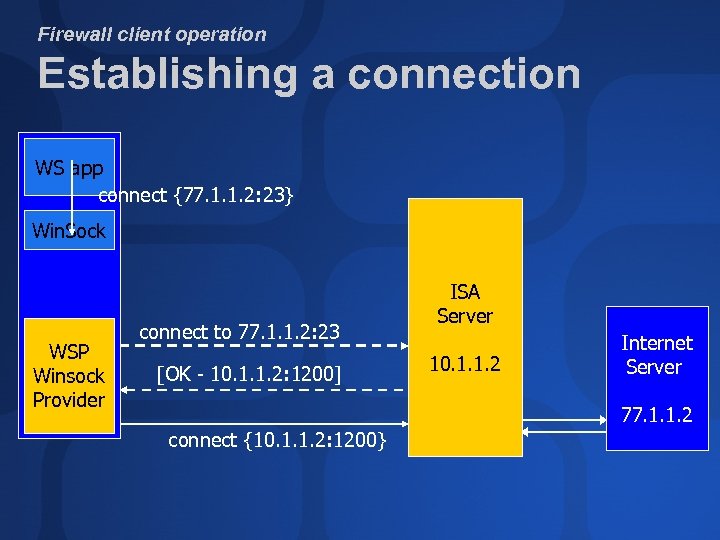 Firewall client operation Establishing a connection WS app connect {77. 1. 1. 2: 23} Win. Sock WSP Winsock Provider connect to 77. 1. 1. 2: 23 [OK - 10. 1. 1. 2: 1200] ISA Server 10. 1. 1. 2 Internet Server 77. 1. 1. 2 connect {10. 1. 1. 2: 1200}
Firewall client operation Establishing a connection WS app connect {77. 1. 1. 2: 23} Win. Sock WSP Winsock Provider connect to 77. 1. 1. 2: 23 [OK - 10. 1. 1. 2: 1200] ISA Server 10. 1. 1. 2 Internet Server 77. 1. 1. 2 connect {10. 1. 1. 2: 1200}
 Firewall client operation Port usage 1745/TCP: configuration refreshes MSPCLNT. INI and MSPLAT. TXT 1745/UDP: control connection Negotiation of data channel Ephemeral: data connection
Firewall client operation Port usage 1745/TCP: configuration refreshes MSPCLNT. INI and MSPLAT. TXT 1745/UDP: control connection Negotiation of data channel Ephemeral: data connection
 DNS Secure. NAT Must have access to DNS server—ISA Server won’t proxy DNS Need DNS protocol rule Firewall client ISA Server or the client perform DNS Depends on settings in MSPCLNT. INI Web proxy client ISA Server performs DNS
DNS Secure. NAT Must have access to DNS server—ISA Server won’t proxy DNS Need DNS protocol rule Firewall client ISA Server or the client perform DNS Depends on settings in MSPCLNT. INI Web proxy client ISA Server performs DNS
 DNS configuration Must have proper DNS configuration ON ISA Server external interface if no DNS forwarding available On inside interface if server in LAT can forward to Internet Bind NIC with DNS settings higher http: //isaserver. org/pages/article. asp? id=239 Incorrect defaults for DNS cache http: //isaserver. org/pages/article. asp? id=238 Firewall clients are “special”…
DNS configuration Must have proper DNS configuration ON ISA Server external interface if no DNS forwarding available On inside interface if server in LAT can forward to Internet Bind NIC with DNS settings higher http: //isaserver. org/pages/article. asp? id=239 Incorrect defaults for DNS cache http: //isaserver. org/pages/article. asp? id=238 Firewall clients are “special”…
 DNS configuration Firewall client Resolution obeys setting for each application in MSPCLNT. INI Local or proxied “Common configuration” is local Just like Secure. NAT Error 14120 Occurs if FW client is accessing a published server Traffic leaves then re-enters ISA Server http: //isaserver. org/pages/article. asp? id=236 http: //isaserver. org/pages/article. asp? id=353
DNS configuration Firewall client Resolution obeys setting for each application in MSPCLNT. INI Local or proxied “Common configuration” is local Just like Secure. NAT Error 14120 Occurs if FW client is accessing a published server Traffic leaves then re-enters ISA Server http: //isaserver. org/pages/article. asp? id=236 http: //isaserver. org/pages/article. asp? id=353
 ISA Server vs. RRAS
ISA Server vs. RRAS
 Terminology Remote access VPN Client on Internet connects to VPN server Network VPN Two networks create VPN over Internet Gateway server on each network Often called “site-to-site VPN” IPSec Transport mode: used in L 2 TP+IPSec remote access and network VPNs Tunnel mode: designed for network VPNs
Terminology Remote access VPN Client on Internet connects to VPN server Network VPN Two networks create VPN over Internet Gateway server on each network Often called “site-to-site VPN” IPSec Transport mode: used in L 2 TP+IPSec remote access and network VPNs Tunnel mode: designed for network VPNs
 RRAS handles all VPN work ISA Server’s wizard simplifies configuration for typical scenarios Inbound remote-access Network Doesn’t eliminate need to understand RRAS
RRAS handles all VPN work ISA Server’s wizard simplifies configuration for typical scenarios Inbound remote-access Network Doesn’t eliminate need to understand RRAS
 ISA Server Can— Originate and terminate PPTP and L 2 TP+IPSec VPNs For remote access and network Permit outbound PPTP Can’t— Terminate IPSec tunnel mode VPNs Permit outbound L 2 TP+IPSec Server-publish any VPN protocol NAT-T improves situation; stay tuned
ISA Server Can— Originate and terminate PPTP and L 2 TP+IPSec VPNs For remote access and network Permit outbound PPTP Can’t— Terminate IPSec tunnel mode VPNs Permit outbound L 2 TP+IPSec Server-publish any VPN protocol NAT-T improves situation; stay tuned
 Enabling outbound PPTP UI: packet filter properties
Enabling outbound PPTP UI: packet filter properties
 Enabling inbound VPN ISA Server terminates incoming VPN connections Can’t server-publish any VPN protocol Enables PPTP and L 2 TP+IPSec Configures RRAS Enforces authentication and encryption Opens packet filters
Enabling inbound VPN ISA Server terminates incoming VPN connections Can’t server-publish any VPN protocol Enables PPTP and L 2 TP+IPSec Configures RRAS Enforces authentication and encryption Opens packet filters
 Inbound VPN packet filters Allow IKE (Internet Key Exchange) any-ip: 500/udp ↔ external-ip: 500/udp Allow L 2 TP any-ip: 1701/udp ↔ external-ip: 1701/udp Application filters handle PPTP “PPTP receive”: accepts inbound PPTP “PPTP call”: allows responses IP protocol 47, both directions
Inbound VPN packet filters Allow IKE (Internet Key Exchange) any-ip: 500/udp ↔ external-ip: 500/udp Allow L 2 TP any-ip: 1701/udp ↔ external-ip: 1701/udp Application filters handle PPTP “PPTP receive”: accepts inbound PPTP “PPTP call”: allows responses IP protocol 47, both directions
 RRAS configuration Both routing and remote access MS-CHAP and MS-CHAPv 2 auth. N Disable MS-CHAP on RRAS and in policy profile DHCP address assignment 128 PPTP and 128 L 2 TP ports No RRAS packet filtering 40 -, 56 -, and 128 -bit encryption Change policy profile to allow only “Strongest” = 128 -bit
RRAS configuration Both routing and remote access MS-CHAP and MS-CHAPv 2 auth. N Disable MS-CHAP on RRAS and in policy profile DHCP address assignment 128 PPTP and 128 L 2 TP ports No RRAS packet filtering 40 -, 56 -, and 128 -bit encryption Change policy profile to allow only “Strongest” = 128 -bit
 Recall the limitations Can’t— Terminate IPSec tunnel mode VPNs Permit outbound L 2 TP+IPSec Server-publish any VPN protocol Various architectural and protocol reasons But first…
Recall the limitations Can’t— Terminate IPSec tunnel mode VPNs Permit outbound L 2 TP+IPSec Server-publish any VPN protocol Various architectural and protocol reasons But first…
 IPSec background Security association (SA) Alice and Bob have a secure “channel” between their computers Authenticates and optionally encrypts Transport mode SA between two nodes Tunnel mode SA between two gateways Node-to-node is secure because it passes through gateways
IPSec background Security association (SA) Alice and Bob have a secure “channel” between their computers Authenticates and optionally encrypts Transport mode SA between two nodes Tunnel mode SA between two gateways Node-to-node is secure because it passes through gateways
 IPSec background IPSec alone not sufficient for remote access VPNs No user authentication No endpoint address assignment L 2 TP performs these functions IPSec protects traffic Authenticates machines Encrypts L 2 TP
IPSec background IPSec alone not sufficient for remote access VPNs No user authentication No endpoint address assignment L 2 TP performs these functions IPSec protects traffic Authenticates machines Encrypts L 2 TP
 IPSec background L 2 TP+IPSec suitable for both remote access and network VPNs Supported in product Well-documented Compare to pure IPSec tunnel mode Supported only for network VPNs Difficult to configure No routable interfaces in RRAS Not possible today with ISA Server
IPSec background L 2 TP+IPSec suitable for both remote access and network VPNs Supported in product Well-documented Compare to pure IPSec tunnel mode Supported only for network VPNs Difficult to configure No routable interfaces in RRAS Not possible today with ISA Server
 L 2 TP+IPSec packet behavior When an L 2 TP+IPSec VPN server receives traffic— 1. 2. 3. 4. 5. 6. IPSec packet arrives at ISA Server Packet filter driver hands to IPSec decrypts then reinjects L 2 TP into receive path Packet filter driver sees L 2 TP and accepts Packet goes to L 2 TP driver in RRAS Packet decapsulated
L 2 TP+IPSec packet behavior When an L 2 TP+IPSec VPN server receives traffic— 1. 2. 3. 4. 5. 6. IPSec packet arrives at ISA Server Packet filter driver hands to IPSec decrypts then reinjects L 2 TP into receive path Packet filter driver sees L 2 TP and accepts Packet goes to L 2 TP driver in RRAS Packet decapsulated
 L 2 TP+IPSec packet behavior Say we tried pure IPSec tunnel mode 1. 2. 3. Packet arrives at ISA Server Packet filter driver hands to IPSec decrypts and passes up the stack Packet has destination IP address other than ISA server’s own, so— 1. 2. Packet placed on stack’s send path—this is normal Windows behavior Packet goes back out ISA Server, rather than delivered to client behind
L 2 TP+IPSec packet behavior Say we tried pure IPSec tunnel mode 1. 2. 3. Packet arrives at ISA Server Packet filter driver hands to IPSec decrypts and passes up the stack Packet has destination IP address other than ISA server’s own, so— 1. 2. Packet placed on stack’s send path—this is normal Windows behavior Packet goes back out ISA Server, rather than delivered to client behind
 L 2 TP+IPSec limitations Therefore: can’t use IPSec tunnel mode Can’t also allow outbound L 2 TP+IPSec at all NAT issue; see NAT-T info later
L 2 TP+IPSec limitations Therefore: can’t use IPSec tunnel mode Can’t also allow outbound L 2 TP+IPSec at all NAT issue; see NAT-T info later
 VPN server publishing Not possible in current version of ISA Server publishing understands only TCP and UDP VPNs use other IP protocols PPTP: 47, generic routing encapsulation IPSec ESP: 50, encapsulated security payload IPSec AH: 51, authenticated header
VPN server publishing Not possible in current version of ISA Server publishing understands only TCP and UDP VPNs use other IP protocols PPTP: 47, generic routing encapsulation IPSec ESP: 50, encapsulated security payload IPSec AH: 51, authenticated header
 Q 310888 RRAS “Internal” interface is server-side tunnel termination point Can NAT this interface to treat incoming tunnels as private interfaces NATing them allows easy outbound access either back through RRAS or through some other firewall Also allows NATing between RRAS sites Article explains how to set this up
Q 310888 RRAS “Internal” interface is server-side tunnel termination point Can NAT this interface to treat incoming tunnels as private interfaces NATing them allows easy outbound access either back through RRAS or through some other firewall Also allows NATing between RRAS sites Article explains how to set this up
 Functionality issue ISA Server replaces RRAS’s NAT driver RRAS “Internal” interface can no longer be NATed Breaks Q 310888 RRAS NAT GUI makes no sense NETSH NAT settings ignored Do you want VPN users to be able to get back out to the Internet? Yes: need separate RRAS and ISA Server computers
Functionality issue ISA Server replaces RRAS’s NAT driver RRAS “Internal” interface can no longer be NATed Breaks Q 310888 RRAS NAT GUI makes no sense NETSH NAT settings ignored Do you want VPN users to be able to get back out to the Internet? Yes: need separate RRAS and ISA Server computers
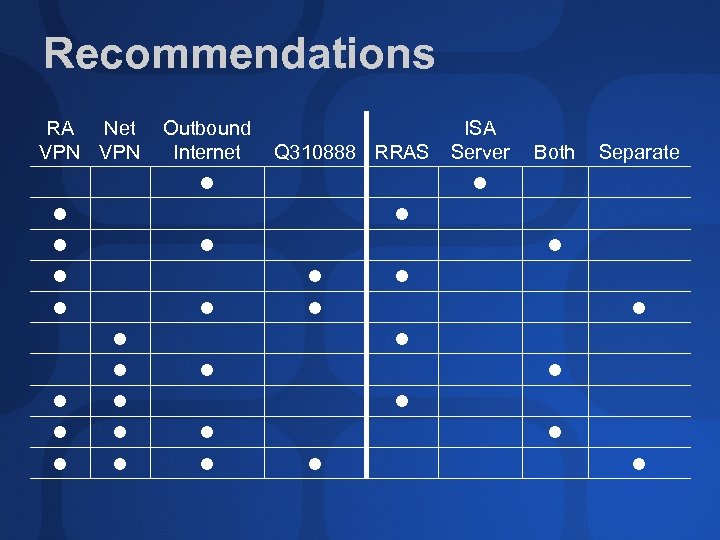 Recommendations RA Net VPN Outbound Internet Q 310888 RRAS ISA Server Both Separate
Recommendations RA Net VPN Outbound Internet Q 310888 RRAS ISA Server Both Separate
 RRAS security Don’t forget RRAS packet filters if using RRAS alone External interface— PPTP: from any: any to ext-ip: 1723/tcp L 2 TP: from any: any to ext-ip: 1701/udp LAN interface— PPTP: from lan-ip: 1723/tcp to any: any L 2 TP: from lan-ip: 1701/udp to any: any No IPSec filterspecs needed Traffic is L 2 TP once RRAS sees it
RRAS security Don’t forget RRAS packet filters if using RRAS alone External interface— PPTP: from any: any to ext-ip: 1723/tcp L 2 TP: from any: any to ext-ip: 1701/udp LAN interface— PPTP: from lan-ip: 1723/tcp to any: any L 2 TP: from lan-ip: 1701/udp to any: any No IPSec filterspecs needed Traffic is L 2 TP once RRAS sees it
 Next Steps Complete the evaluation of ISA Server that you’ve already been doing Right? Consider where adding application-aware inspection can increase security Exchange RPC Outlook Web Access Share. Point Servers of various flavors Anything built on any web server Deploy it!
Next Steps Complete the evaluation of ISA Server that you’ve already been doing Right? Consider where adding application-aware inspection can increase security Exchange RPC Outlook Web Access Share. Point Servers of various flavors Anything built on any web server Deploy it!
 Suggested Reading And Resources The tools you need to put technology to work! TITLE Microsoft® Internet Security and Acceleration (ISA) Server 2000 Administrator's Pocket Consultant: 0 -7356 -1442 -3 Writing Secure Code, Second Edition: 0 -7356 -1722 -8 Available Today Microsoft Press books are 20% off at the Tech. Ed Bookstore Also buy any TWO Microsoft Press books and get a FREE T-Shirt
Suggested Reading And Resources The tools you need to put technology to work! TITLE Microsoft® Internet Security and Acceleration (ISA) Server 2000 Administrator's Pocket Consultant: 0 -7356 -1442 -3 Writing Secure Code, Second Edition: 0 -7356 -1722 -8 Available Today Microsoft Press books are 20% off at the Tech. Ed Bookstore Also buy any TWO Microsoft Press books and get a FREE T-Shirt
 Community Resources http: //www. microsoft. com/communities/default. mspx Most Valuable Professional (MVP) http: //www. mvp. support. microsoft. com/ Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http: //www. microsoft. com/communities/newsgroups/default. mspx User Groups Meet and learn with your peers http: //www. microsoft. com/communities/usergroups/default. mspx
Community Resources http: //www. microsoft. com/communities/default. mspx Most Valuable Professional (MVP) http: //www. mvp. support. microsoft. com/ Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http: //www. microsoft. com/communities/newsgroups/default. mspx User Groups Meet and learn with your peers http: //www. microsoft. com/communities/usergroups/default. mspx
 evaluations
evaluations
 © 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.


