baacdaedfa445e9fa3cb1cdbbbc14873.ppt
- Количество слайдов: 68
 SEC 405 Wireless LAN Security with 802. 1 X, PEAP, and WPA Steve Riley Microsoft Corporation
SEC 405 Wireless LAN Security with 802. 1 X, PEAP, and WPA Steve Riley Microsoft Corporation
 Why? Huge fear of wireless Rooted in misunderstandings of security Wireless can be made secure Takes work Need to understand problem Need to plan for secure solution
Why? Huge fear of wireless Rooted in misunderstandings of security Wireless can be made secure Takes work Need to understand problem Need to plan for secure solution
 So what’s the problem? WEP is a euphemism Wired Equivalent Privacy Actually, it’s a lie It isn’t equivalent to “wired privacy” at all! How can you secure the air? So: WEP sucks http: //www. isaac. cs. berkeley. edu/isaac/wep-faq. html
So what’s the problem? WEP is a euphemism Wired Equivalent Privacy Actually, it’s a lie It isn’t equivalent to “wired privacy” at all! How can you secure the air? So: WEP sucks http: //www. isaac. cs. berkeley. edu/isaac/wep-faq. html
 Wired equivalent privacy
Wired equivalent privacy
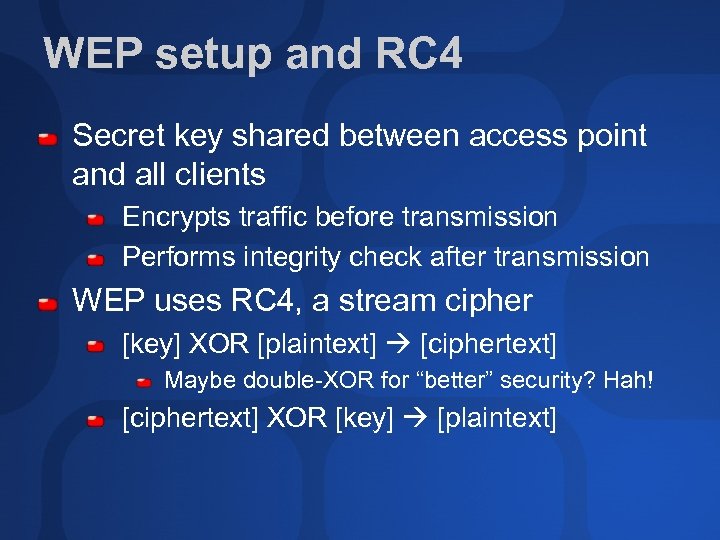 WEP setup and RC 4 Secret key shared between access point and all clients Encrypts traffic before transmission Performs integrity check after transmission WEP uses RC 4, a stream cipher [key] XOR [plaintext] [ciphertext] Maybe double-XOR for “better” security? Hah! [ciphertext] XOR [key] [plaintext]
WEP setup and RC 4 Secret key shared between access point and all clients Encrypts traffic before transmission Performs integrity check after transmission WEP uses RC 4, a stream cipher [key] XOR [plaintext] [ciphertext] Maybe double-XOR for “better” security? Hah! [ciphertext] XOR [key] [plaintext]
 Common attacks Bit-flipping (encryption ≠ integrity) Flipping bit n in cipertext flips same bit in plaintext Statistical attacks Multiple ciphertexts using same key permit determination of plaintext XOR Enables statistical attacks to recover plaintext More ciphertexts eases this Once one plaintext is known, recovering others is trivial
Common attacks Bit-flipping (encryption ≠ integrity) Flipping bit n in cipertext flips same bit in plaintext Statistical attacks Multiple ciphertexts using same key permit determination of plaintext XOR Enables statistical attacks to recover plaintext More ciphertexts eases this Once one plaintext is known, recovering others is trivial
 WEP’s “defenses” Integrity check (IC) field CRC-32 checksum, part of encrypted payload Not keyed Subject to bit-flipping can modify IC to make altered message appear valid Initialization vector (IV) added to key Alters key somewhat for each packet 24 -bit field; contained in plaintext portion Alas, this small keyspace guarantees reuse
WEP’s “defenses” Integrity check (IC) field CRC-32 checksum, part of encrypted payload Not keyed Subject to bit-flipping can modify IC to make altered message appear valid Initialization vector (IV) added to key Alters key somewhat for each packet 24 -bit field; contained in plaintext portion Alas, this small keyspace guarantees reuse
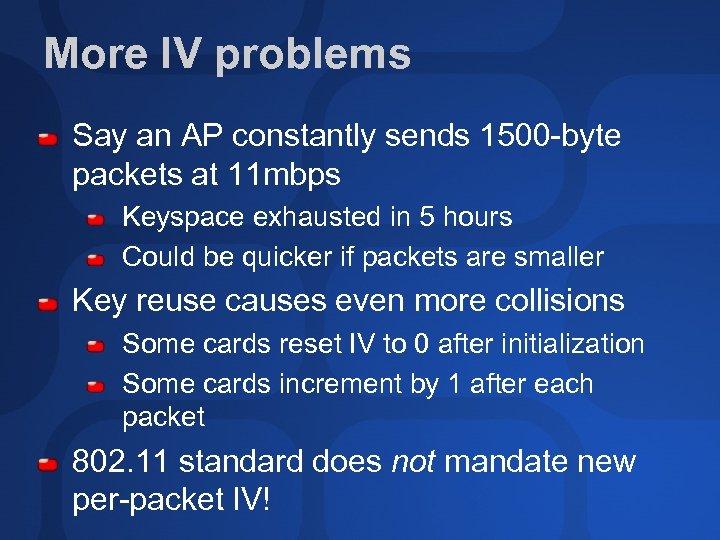 More IV problems Say an AP constantly sends 1500 -byte packets at 11 mbps Keyspace exhausted in 5 hours Could be quicker if packets are smaller Key reuse causes even more collisions Some cards reset IV to 0 after initialization Some cards increment by 1 after each packet 802. 11 standard does not mandate new per-packet IV!
More IV problems Say an AP constantly sends 1500 -byte packets at 11 mbps Keyspace exhausted in 5 hours Could be quicker if packets are smaller Key reuse causes even more collisions Some cards reset IV to 0 after initialization Some cards increment by 1 after each packet 802. 11 standard does not mandate new per-packet IV!
 Classes of attacks Key and IV reuse Known plaintext attack Partial known plaintext attack Weaknesses in RC 4 key scheduling algorithm Authentication forging Realtime decryption
Classes of attacks Key and IV reuse Known plaintext attack Partial known plaintext attack Weaknesses in RC 4 key scheduling algorithm Authentication forging Realtime decryption
 Tools WEPCrack—breaks 802. 11 keys http: //wepcrack. sourceforge. net/ Air. Snort—breaks 802. 11 keys Needs only 5 -10 million packets http: //airsnort. shmoo. com/ Net. Stumbler—access point reconnaissance http: //www. netstumbler. com
Tools WEPCrack—breaks 802. 11 keys http: //wepcrack. sourceforge. net/ Air. Snort—breaks 802. 11 keys Needs only 5 -10 million packets http: //airsnort. shmoo. com/ Net. Stumbler—access point reconnaissance http: //www. netstumbler. com
 WEP suckage Same key reused over and over again Per-packet IV isn’t enough Need to increase keyspace an attacker must analyze Generate new keys (not just IVs) periodically Use unique per-client keys These are our first requirements…
WEP suckage Same key reused over and over again Per-packet IV isn’t enough Need to increase keyspace an attacker must analyze Generate new keys (not just IVs) periodically Use unique per-client keys These are our first requirements…
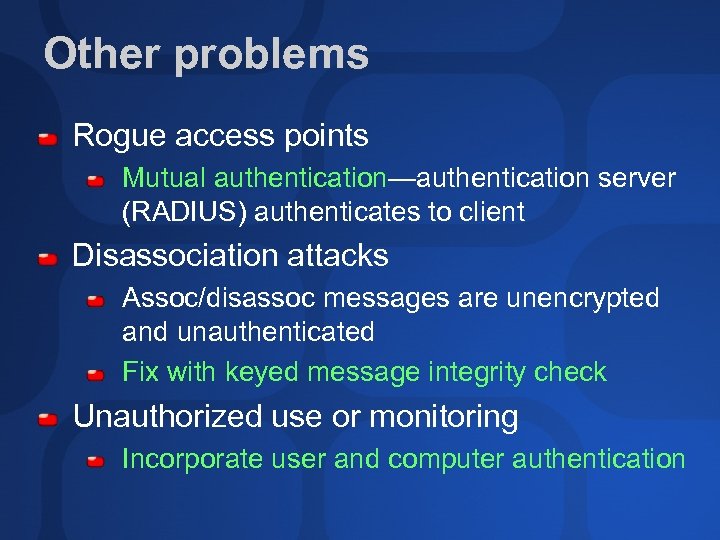 Other problems Rogue access points Mutual authentication—authentication server (RADIUS) authenticates to client Disassociation attacks Assoc/disassoc messages are unencrypted and unauthenticated Fix with keyed message integrity check Unauthorized use or monitoring Incorporate user and computer authentication
Other problems Rogue access points Mutual authentication—authentication server (RADIUS) authenticates to client Disassociation attacks Assoc/disassoc messages are unencrypted and unauthenticated Fix with keyed message integrity check Unauthorized use or monitoring Incorporate user and computer authentication
 Now what? Don’t fear wireless networks They can be secured. It just takes…technology! Our tasks today: understand how Key protection: 802. 1 X Authentication: EAP Enumerating and eliminating the vulnerabilities Verifying that we did the right thing
Now what? Don’t fear wireless networks They can be secured. It just takes…technology! Our tasks today: understand how Key protection: 802. 1 X Authentication: EAP Enumerating and eliminating the vulnerabilities Verifying that we did the right thing
 802. 1 x
802. 1 x
 Solution today: 802. 1 X Port-based access control mechanism defined by IEEE Works on anything, wired and wireless Access point must support 802. 1 X Allows choice of authentication methods using EAP Chosen by peers at authentication time Access point doesn’t care about EAP methods Manages keys automagically
Solution today: 802. 1 X Port-based access control mechanism defined by IEEE Works on anything, wired and wireless Access point must support 802. 1 X Allows choice of authentication methods using EAP Chosen by peers at authentication time Access point doesn’t care about EAP methods Manages keys automagically
 Is 802. 1 X enough? No It does solve: Key discovery by changing keys often and using different keys for each client Rogue APs and man-in-the-middle attacks by performing mutual device authentication Unauthorized access by authenticating users and computers It does not solve: Packet and disassociation spoofing because 802. 1 X doesn’t use a keyed MIC
Is 802. 1 X enough? No It does solve: Key discovery by changing keys often and using different keys for each client Rogue APs and man-in-the-middle attacks by performing mutual device authentication Unauthorized access by authenticating users and computers It does not solve: Packet and disassociation spoofing because 802. 1 X doesn’t use a keyed MIC
 Clarifying terminology 802. 11 is the specification for over-the-air wireless networks 802. 1 X is a PHY-independent specification for port-based access control Combining them makes sense There is no such thing as 802. 11 X But there is work on something called 802. 11 i
Clarifying terminology 802. 11 is the specification for over-the-air wireless networks 802. 1 X is a PHY-independent specification for port-based access control Combining them makes sense There is no such thing as 802. 11 X But there is work on something called 802. 11 i
 802. 1 X over 802. 11 Supplicant 802. 11 association Authenticator Access blocked EAPOL-start EAP-request/identity EAP-response/identity RADIUS-access-request EAP-request RADIUS-access-challenge EAP-response (credentials) RADIUS-access-request EAP-success RADIUS-access-accept EAPOW-key (WEP) Access allowed Authentication Server
802. 1 X over 802. 11 Supplicant 802. 11 association Authenticator Access blocked EAPOL-start EAP-request/identity EAP-response/identity RADIUS-access-request EAP-request RADIUS-access-challenge EAP-response (credentials) RADIUS-access-request EAP-success RADIUS-access-accept EAPOW-key (WEP) Access allowed Authentication Server
 Association and auth. N The 802. 11 association happens first Need to talk to the AP and get an IP address Open authentication—don’t have the WEP key yet Access beyond AP prohibited until auth. N succeeds AP drops non-EAPOL traffic After key is sent in EAPOW-key, access beyond AP is allowed Security conversation between supplicant and authentication server Wireless NIC and AP are passthrough devices
Association and auth. N The 802. 11 association happens first Need to talk to the AP and get an IP address Open authentication—don’t have the WEP key yet Access beyond AP prohibited until auth. N succeeds AP drops non-EAPOL traffic After key is sent in EAPOW-key, access beyond AP is allowed Security conversation between supplicant and authentication server Wireless NIC and AP are passthrough devices
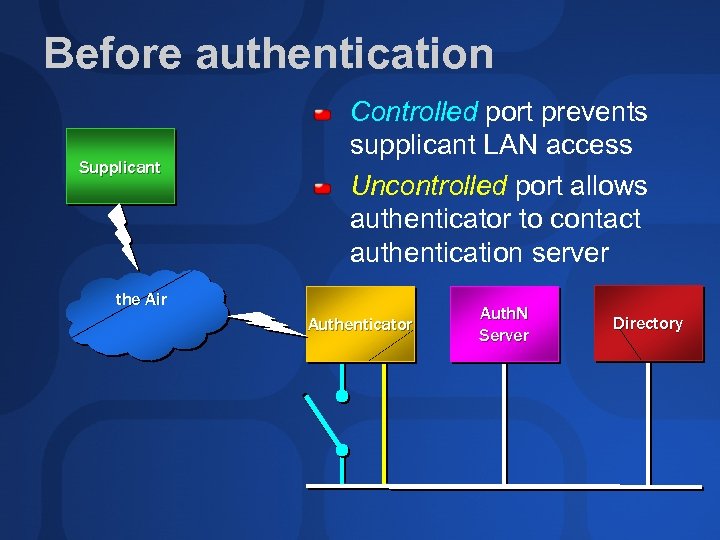 Before authentication Supplicant Controlled port prevents supplicant LAN access Uncontrolled port allows authenticator to contact authentication server the Air Authenticator Auth. N Server Directory
Before authentication Supplicant Controlled port prevents supplicant LAN access Uncontrolled port allows authenticator to contact authentication server the Air Authenticator Auth. N Server Directory
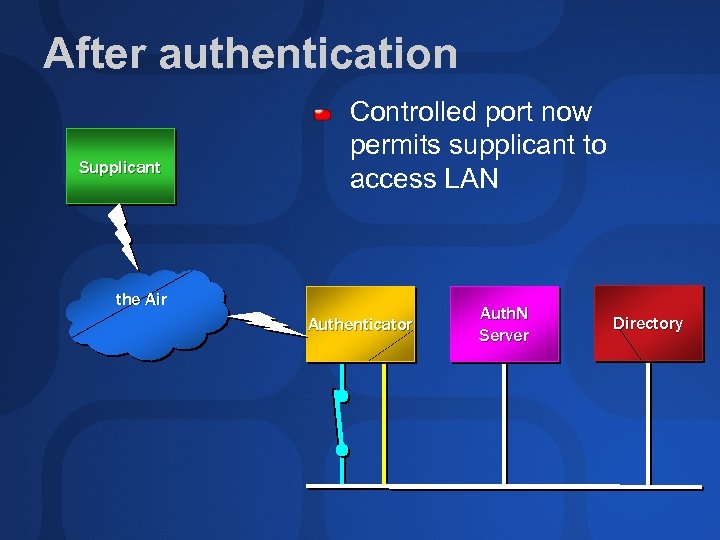 After authentication Supplicant Controlled port now permits supplicant to access LAN the Air Authenticator Auth. N Server Directory
After authentication Supplicant Controlled port now permits supplicant to access LAN the Air Authenticator Auth. N Server Directory
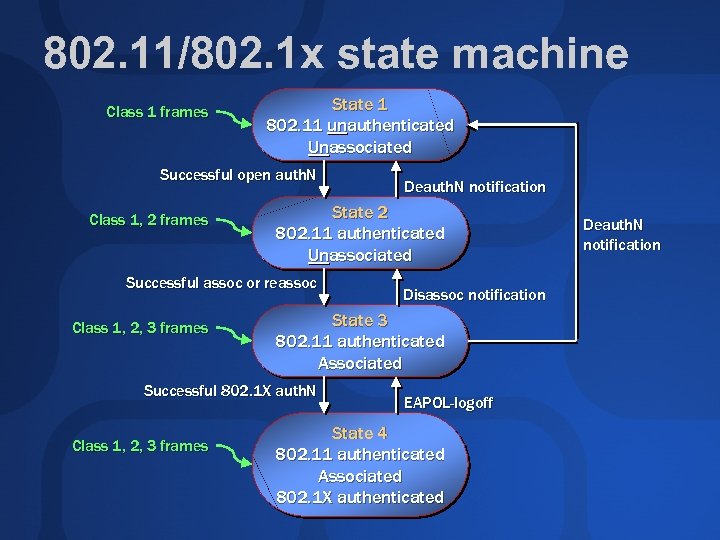 802. 11/802. 1 x state machine Class 1 frames State 1 802. 11 unauthenticated Unassociated Successful open auth. N Class 1, 2 frames State 2 802. 11 authenticated Unassociated Successful assoc or reassoc Class 1, 2, 3 frames Disassoc notification State 3 802. 11 authenticated Associated Successful 802. 1 X auth. N Class 1, 2, 3 frames Deauth. N notification EAPOL-logoff State 4 802. 11 authenticated Associated 802. 1 X authenticated Deauth. N notification
802. 11/802. 1 x state machine Class 1 frames State 1 802. 11 unauthenticated Unassociated Successful open auth. N Class 1, 2 frames State 2 802. 11 authenticated Unassociated Successful assoc or reassoc Class 1, 2, 3 frames Disassoc notification State 3 802. 11 authenticated Associated Successful 802. 1 X auth. N Class 1, 2, 3 frames Deauth. N notification EAPOL-logoff State 4 802. 11 authenticated Associated 802. 1 X authenticated Deauth. N notification
 Encryption keys Client and RADIUS server generate per-user session WEP keys Never sent over the air RADIUS server sends key to AP (encrypted with RADIUS shared secret) Access point has a global WEP key Used during AP authentication to client Sent in EAPOW-key message Encrypted with session key Session keys regenerated when… Key time exceeded (60 minute default) Client roams to new AP
Encryption keys Client and RADIUS server generate per-user session WEP keys Never sent over the air RADIUS server sends key to AP (encrypted with RADIUS shared secret) Access point has a global WEP key Used during AP authentication to client Sent in EAPOW-key message Encrypted with session key Session keys regenerated when… Key time exceeded (60 minute default) Client roams to new AP
 Extensible authentication protocol
Extensible authentication protocol
 EAP Link-layer security framework Simple encapsulation protocol for authentication mechanisms Runs over any link layer, lossy or lossless No built-in security Doesn’t assume physically secure link Authentication methods must incorporate their own security
EAP Link-layer security framework Simple encapsulation protocol for authentication mechanisms Runs over any link layer, lossy or lossless No built-in security Doesn’t assume physically secure link Authentication methods must incorporate their own security
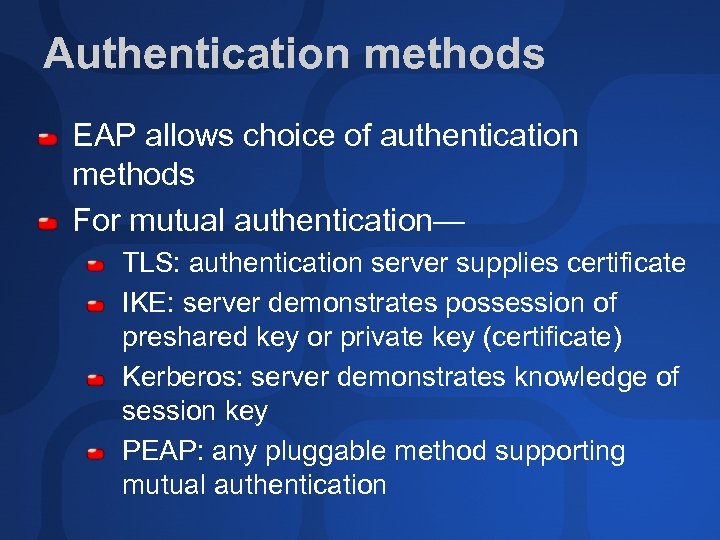 Authentication methods EAP allows choice of authentication methods For mutual authentication— TLS: authentication server supplies certificate IKE: server demonstrates possession of preshared key or private key (certificate) Kerberos: server demonstrates knowledge of session key PEAP: any pluggable method supporting mutual authentication
Authentication methods EAP allows choice of authentication methods For mutual authentication— TLS: authentication server supplies certificate IKE: server demonstrates possession of preshared key or private key (certificate) Kerberos: server demonstrates knowledge of session key PEAP: any pluggable method supporting mutual authentication
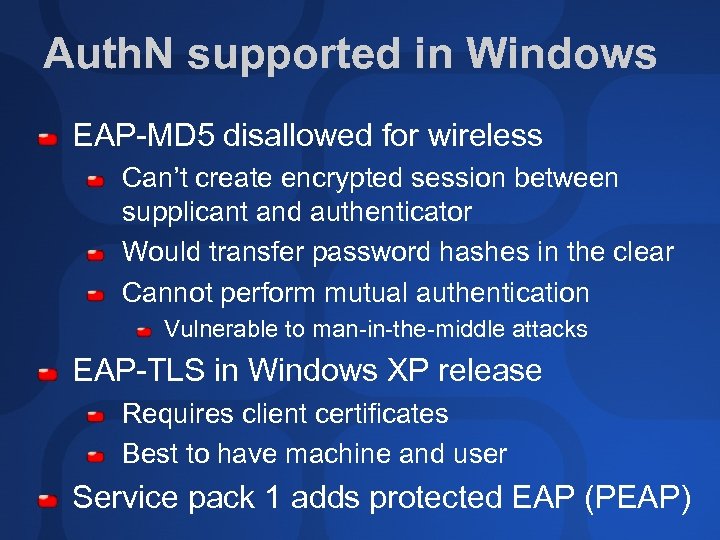 Auth. N supported in Windows EAP-MD 5 disallowed for wireless Can’t create encrypted session between supplicant and authenticator Would transfer password hashes in the clear Cannot perform mutual authentication Vulnerable to man-in-the-middle attacks EAP-TLS in Windows XP release Requires client certificates Best to have machine and user Service pack 1 adds protected EAP (PEAP)
Auth. N supported in Windows EAP-MD 5 disallowed for wireless Can’t create encrypted session between supplicant and authenticator Would transfer password hashes in the clear Cannot perform mutual authentication Vulnerable to man-in-the-middle attacks EAP-TLS in Windows XP release Requires client certificates Best to have machine and user Service pack 1 adds protected EAP (PEAP)
 Protected EAP (PEAP) Extension to EAP Allows use of any secure authentication mechanism for EAP No need to write individual EAP-enabled methods Windows PEAP allows: MS-CHAPv 2—passwords TLS (SSL channel)—certificates PEAP-TLS a little slower than EAP-TLS Secur. ID—but not tested/supported for
Protected EAP (PEAP) Extension to EAP Allows use of any secure authentication mechanism for EAP No need to write individual EAP-enabled methods Windows PEAP allows: MS-CHAPv 2—passwords TLS (SSL channel)—certificates PEAP-TLS a little slower than EAP-TLS Secur. ID—but not tested/supported for
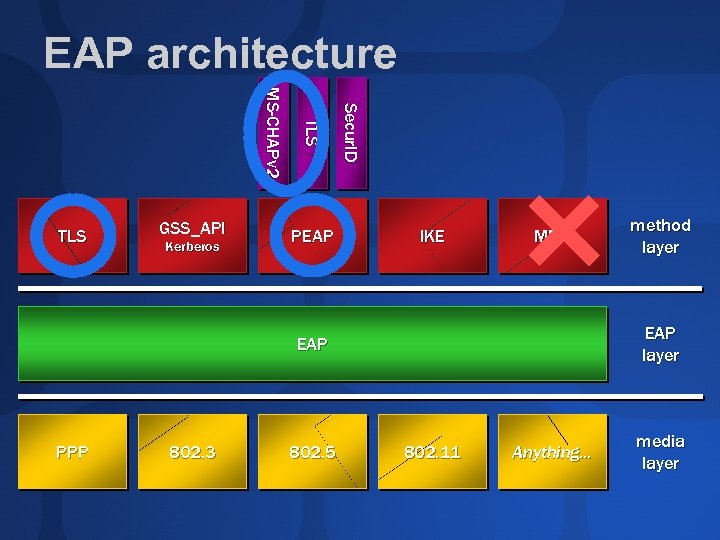 EAP architecture Kerberos PEAP Se c u r I D GSS_API TL S MS--CHAPv 2 M S C H AP v 2 TLS IKE MD 5 EAP layer EAP PPP 802. 3 802. 5 method layer 802. 11 Anything… media layer
EAP architecture Kerberos PEAP Se c u r I D GSS_API TL S MS--CHAPv 2 M S C H AP v 2 TLS IKE MD 5 EAP layer EAP PPP 802. 3 802. 5 method layer 802. 11 Anything… media layer
 How it works: The Windows logon process over PEAP with MS-CHAPv 2
How it works: The Windows logon process over PEAP with MS-CHAPv 2
 Security requirements, again Mutual device authentication Workstation and authentication server No rogue access points Prevents man-in-the-middle attacks Ensures key is transferred to correct entity User authentication No unauthorized access or interception WEP key uniqueness and regeneration Stop packet/disassociation spoofing
Security requirements, again Mutual device authentication Workstation and authentication server No rogue access points Prevents man-in-the-middle attacks Ensures key is transferred to correct entity User authentication No unauthorized access or interception WEP key uniqueness and regeneration Stop packet/disassociation spoofing
 Windows domain logon Two logons occur Machine User Machine accounts look like user accounts Certificate credential User ID/password/domain credential Take advantage of this
Windows domain logon Two logons occur Machine User Machine accounts look like user accounts Certificate credential User ID/password/domain credential Take advantage of this
 Windows PEAP authentication First phase—machine logon 802. 11 association Authenticate AP Authenticate computer Transition controlled port status For machine account access to authorized resources Second phase—user logon Authenticate user Transition controlled port status For user account access to authorized resources
Windows PEAP authentication First phase—machine logon 802. 11 association Authenticate AP Authenticate computer Transition controlled port status For machine account access to authorized resources Second phase—user logon Authenticate user Transition controlled port status For user account access to authorized resources
 Windows PEAP authentication First phase 1. Supplicant performs regular 802. 11 association 2. Supplicant sets up TLS channel with authenticator and requests authentication server’s certificate 3. Supplicant— Verifies name and dates on certificate Validates chain
Windows PEAP authentication First phase 1. Supplicant performs regular 802. 11 association 2. Supplicant sets up TLS channel with authenticator and requests authentication server’s certificate 3. Supplicant— Verifies name and dates on certificate Validates chain
 Our requirements so far Mutual device authentication Workstation and authentication server No rogue access points Only authorized APs are allowed to talk to authenticator Only authorized authenticators are allowed to talk to clients User authentication No unauthorized access or interception WEP key uniqueness and regeneration Packet/disassociation spoofing
Our requirements so far Mutual device authentication Workstation and authentication server No rogue access points Only authorized APs are allowed to talk to authenticator Only authorized authenticators are allowed to talk to clients User authentication No unauthorized access or interception WEP key uniqueness and regeneration Packet/disassociation spoofing
 Windows PEAP authentication First phase 4. Supplicant sends machine credentials to authenticator over previously-established TLS channel 5. Authenticator checks validity by contacting authentication server (RADIUS) 6. Authentication server contacts directory to verify credentials
Windows PEAP authentication First phase 4. Supplicant sends machine credentials to authenticator over previously-established TLS channel 5. Authenticator checks validity by contacting authentication server (RADIUS) 6. Authentication server contacts directory to verify credentials
 Windows PEAP authentication First phase 7. If valid, RADIUS generates WEP key 8. Authenticator delivers key to supplicant and transitions controlled port status to permit supplicant access to LAN (to resources allowed access through machine account only) 9. Computer logs on to domain
Windows PEAP authentication First phase 7. If valid, RADIUS generates WEP key 8. Authenticator delivers key to supplicant and transitions controlled port status to permit supplicant access to LAN (to resources allowed access through machine account only) 9. Computer logs on to domain
 Our requirements so far Mutual device authentication Workstation and authentication server No rogue access points User authentication No unauthorized access or interception WEP key uniqueness and regeneration Packet/disassociation spoofing
Our requirements so far Mutual device authentication Workstation and authentication server No rogue access points User authentication No unauthorized access or interception WEP key uniqueness and regeneration Packet/disassociation spoofing
 Windows PEAP authentication Second phase 1. Logon dialog appears 2. Supplicant sends user credentials to authenticator 3. Authenticator checks validity by contacting authentication server (RADIUS) 4. Authentication server contacts directory 5. If valid, authenticator extends controlled port status to permit supplicant full access to LAN
Windows PEAP authentication Second phase 1. Logon dialog appears 2. Supplicant sends user credentials to authenticator 3. Authenticator checks validity by contacting authentication server (RADIUS) 4. Authentication server contacts directory 5. If valid, authenticator extends controlled port status to permit supplicant full access to LAN
 Our requirements so far Mutual device authentication Workstation and authentication server No rogue access points User authentication No unauthorized access or interception WEP key uniqueness and regeneration Packet/disassociation spoofing
Our requirements so far Mutual device authentication Workstation and authentication server No rogue access points User authentication No unauthorized access or interception WEP key uniqueness and regeneration Packet/disassociation spoofing
 Why use machine accounts? Domain logon required for: Machine group policies Computer startup scripts Software installation settings When user account passwords expire Need associated WIC and transitioned controlled port for user notification and change dialog Machine account logon phase allows password expiration notices and changes to occur normally
Why use machine accounts? Domain logon required for: Machine group policies Computer startup scripts Software installation settings When user account passwords expire Need associated WIC and transitioned controlled port for user notification and change dialog Machine account logon phase allows password expiration notices and changes to occur normally
 Why passwords? Not all customers are ready for a PKI Managing user certificates stored on computer hard drives will always be painful Some personnel might roam among computers Smartcards solve this Technical and sociological issues can delay or prevent deployment PEAP enables (pretty) secure wireless now Allows easy migration to certificates and smartcards later
Why passwords? Not all customers are ready for a PKI Managing user certificates stored on computer hard drives will always be painful Some personnel might roam among computers Smartcards solve this Technical and sociological issues can delay or prevent deployment PEAP enables (pretty) secure wireless now Allows easy migration to certificates and smartcards later
 Remaining vulnerabilities
Remaining vulnerabilities
 Remaining vulnerabilities Two related vulnerabilities not addressed with 802. 1 X Bit flipping with known IVs packet spoofing Disassociation denials of service Simple addition to 802. 1 X will solve both
Remaining vulnerabilities Two related vulnerabilities not addressed with 802. 1 X Bit flipping with known IVs packet spoofing Disassociation denials of service Simple addition to 802. 1 X will solve both
 Bit-flipping attacks WEP doesn’t perform per-packet authentication IC is not a keyed message integrity check Flipped bits in WEP packet recalculated IC To spoof or replay: Flip bits in WEP packet where IV is known AP accepts packet Layer 3 device rejects, sends predictable response Build response database and derive key
Bit-flipping attacks WEP doesn’t perform per-packet authentication IC is not a keyed message integrity check Flipped bits in WEP packet recalculated IC To spoof or replay: Flip bits in WEP packet where IV is known AP accepts packet Layer 3 device rejects, sends predictable response Build response database and derive key
 Disassociation attacks 802. 11 associate/disassociate messages are unauthenticated and unencrypted Attacker can forge disassociation message Bothersome denials of service
Disassociation attacks 802. 11 associate/disassociate messages are unauthenticated and unencrypted Attacker can forge disassociation message Bothersome denials of service
 Solution: keyed IC Change behavior of WEP’s IC Derive key from seed value, source and destination MACs, payload Any change to these will alter the IC Include in every WEP packet
Solution: keyed IC Change behavior of WEP’s IC Derive key from seed value, source and destination MACs, payload Any change to these will alter the IC Include in every WEP packet
 WPA: Wi-Fi protected access
WPA: Wi-Fi protected access
 An interim until 802. 11 i Goals Require secure networking Solve WEP issues with software and firmware upgrades Provide secure wireless for SOHO No RADIUS needed Be forward compatible with 802. 11 i Be available today Wi-Fi Alliance began testing in February; will require WEP support for certification in August and beyond
An interim until 802. 11 i Goals Require secure networking Solve WEP issues with software and firmware upgrades Provide secure wireless for SOHO No RADIUS needed Be forward compatible with 802. 11 i Be available today Wi-Fi Alliance began testing in February; will require WEP support for certification in August and beyond
 Authentication 802. 1 X is required Still uses open authentication for initial 802. 11 association Supports pre-shared key if no RADIUS Same key configured on access point and on all wireless clients Initial unicast key derived from authentication process Verifies that AP and client have the same key
Authentication 802. 1 X is required Still uses open authentication for initial 802. 11 association Supports pre-shared key if no RADIUS Same key configured on access point and on all wireless clients Initial unicast key derived from authentication process Verifies that AP and client have the same key
 Key management TKIP replaces 802. 1 X key management Temporal key integrity protocol 128 -bit RC 4 combined with 128 -bit IV and client MAC address Changes unicast key every frame Has undergone thorough cryptanalysis Not actually a replacement for WEP More of a wrapper to work around weaknesses
Key management TKIP replaces 802. 1 X key management Temporal key integrity protocol 128 -bit RC 4 combined with 128 -bit IV and client MAC address Changes unicast key every frame Has undergone thorough cryptanalysis Not actually a replacement for WEP More of a wrapper to work around weaknesses
 Key protection Regenerates session and global keys 802. 1 X doesn’t regenerate global key used for multicast and broadcast traffic “Michael”: message integrity check 8 -byte MIC between payload and 4 -byte IC Encrypted along with everything else Encrypted frame counter prevents replay attacks Set to zero when key is set Incremented for every frame Receiver drops out-of-order frames
Key protection Regenerates session and global keys 802. 1 X doesn’t regenerate global key used for multicast and broadcast traffic “Michael”: message integrity check 8 -byte MIC between payload and 4 -byte IC Encrypted along with everything else Encrypted frame counter prevents replay attacks Set to zero when key is set Incremented for every frame Receiver drops out-of-order frames
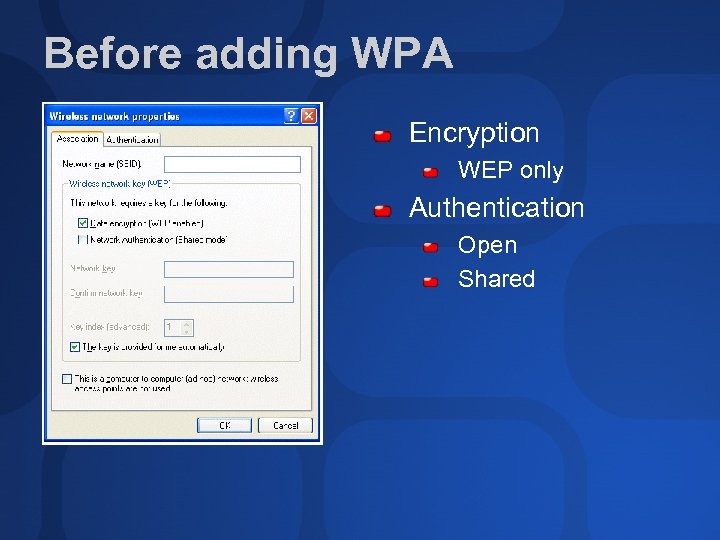 Before adding WPA Encryption WEP only Authentication Open Shared
Before adding WPA Encryption WEP only Authentication Open Shared
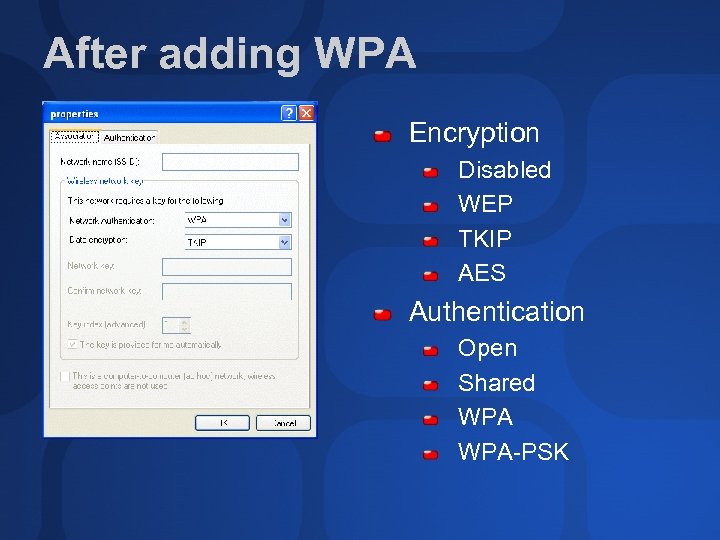 After adding WPA Encryption Disabled WEP TKIP AES Authentication Open Shared WPA-PSK
After adding WPA Encryption Disabled WEP TKIP AES Authentication Open Shared WPA-PSK
 Deployment
Deployment
 System requirements Client: Windows XP service pack 1 Server: Windows Server 2003 IAS Internet Authentication Service—our RADIUS server Certificate on IAS computer Backporting to Windows 2000 Client and IAS must have SP 3 No zero-config support in the client See KB article 313664 Supports only TLS and MS-CHAPv 2 Future EAP methods in XP and 2003 might not
System requirements Client: Windows XP service pack 1 Server: Windows Server 2003 IAS Internet Authentication Service—our RADIUS server Certificate on IAS computer Backporting to Windows 2000 Client and IAS must have SP 3 No zero-config support in the client See KB article 313664 Supports only TLS and MS-CHAPv 2 Future EAP methods in XP and 2003 might not
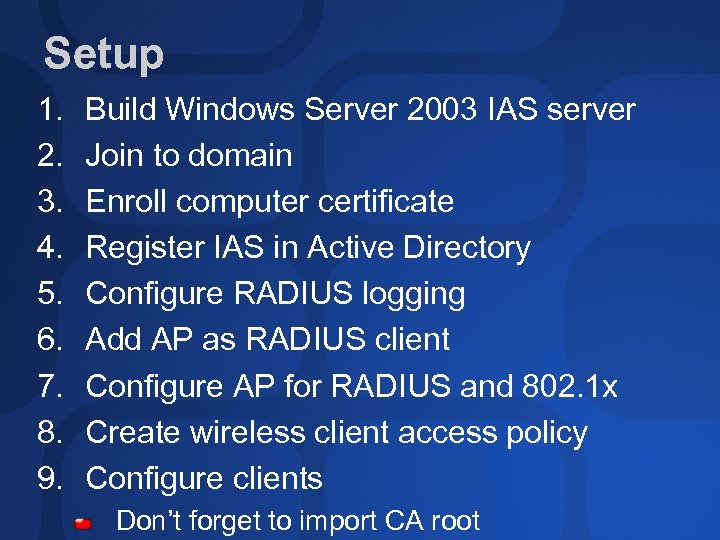 Setup 1. 2. 3. 4. 5. 6. 7. 8. 9. Build Windows Server 2003 IAS server Join to domain Enroll computer certificate Register IAS in Active Directory Configure RADIUS logging Add AP as RADIUS client Configure AP for RADIUS and 802. 1 x Create wireless client access policy Configure clients Don’t forget to import CA root
Setup 1. 2. 3. 4. 5. 6. 7. 8. 9. Build Windows Server 2003 IAS server Join to domain Enroll computer certificate Register IAS in Active Directory Configure RADIUS logging Add AP as RADIUS client Configure AP for RADIUS and 802. 1 x Create wireless client access policy Configure clients Don’t forget to import CA root
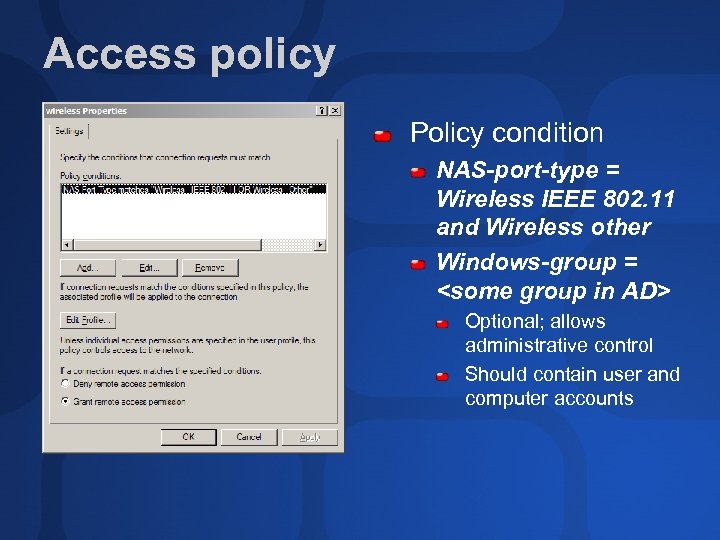 Access policy Policy condition NAS-port-type = Wireless IEEE 802. 11 and Wireless other Windows-group =
Access policy Policy condition NAS-port-type = Wireless IEEE 802. 11 and Wireless other Windows-group =
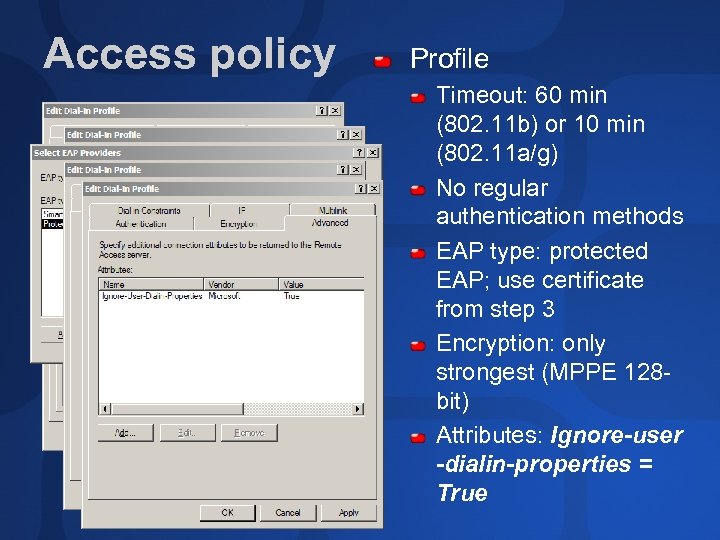 Access policy Profile Timeout: 60 min (802. 11 b) or 10 min (802. 11 a/g) No regular authentication methods EAP type: protected EAP; use certificate from step 3 Encryption: only strongest (MPPE 128 bit) Attributes: Ignore-user -dialin-properties = True
Access policy Profile Timeout: 60 min (802. 11 b) or 10 min (802. 11 a/g) No regular authentication methods EAP type: protected EAP; use certificate from step 3 Encryption: only strongest (MPPE 128 bit) Attributes: Ignore-user -dialin-properties = True
 What else?
What else?
 Interoperability PEAP standards authors Microsoft Cisco RSA Our implementation is version 0 Not compatible with version 1 Working towards interoperability PEAP allows servers and clients to support multiple versions
Interoperability PEAP standards authors Microsoft Cisco RSA Our implementation is version 0 Not compatible with version 1 Working towards interoperability PEAP allows servers and clients to support multiple versions
 The future—long term IEEE is working on 802. 11 i Replacement for WEP Includes TKIP, 802. 1 x, and keyed IC Mandatory AES (in WPA it’s optional) Addresses all currently known vulnerabilities and poor implementation decisions Need to be IEEE member to read work in progress Expected ratification in September 2003
The future—long term IEEE is working on 802. 11 i Replacement for WEP Includes TKIP, 802. 1 x, and keyed IC Mandatory AES (in WPA it’s optional) Addresses all currently known vulnerabilities and poor implementation decisions Need to be IEEE member to read work in progress Expected ratification in September 2003
 References Security of the WEP Algorithm http: //www. isaac. cs. berkeley. edu/isaac/wep-faq. html 802. 1 x--Port Based Network Access Control http: //www. ieee 802. org/1/pages/802. 1 x. html PPP Extensible Authentication Protocol http: //www. ietf. org/rfc 2284. txt PPP EAP-TLS Authentication Protocol http: //www. ietf. org/rfc 2176. txt Protected EAP Protocol ftp: //ftp. rfc-editor. org/in-notes/internet-drafts/draftjosefsson-pppext-eap-tls-eap-05. txt
References Security of the WEP Algorithm http: //www. isaac. cs. berkeley. edu/isaac/wep-faq. html 802. 1 x--Port Based Network Access Control http: //www. ieee 802. org/1/pages/802. 1 x. html PPP Extensible Authentication Protocol http: //www. ietf. org/rfc 2284. txt PPP EAP-TLS Authentication Protocol http: //www. ietf. org/rfc 2176. txt Protected EAP Protocol ftp: //ftp. rfc-editor. org/in-notes/internet-drafts/draftjosefsson-pppext-eap-tls-eap-05. txt
 Next steps Eliminate fear of wireless! Plan for wireless deployments where there’s a business case Conduct a site survey Radio engineering isn’t rocket science, but it isn’t a science fair project either Add appropriate technology Deploy a secure wireless network
Next steps Eliminate fear of wireless! Plan for wireless deployments where there’s a business case Conduct a site survey Radio engineering isn’t rocket science, but it isn’t a science fair project either Add appropriate technology Deploy a secure wireless network
 Community Resources http: //www. microsoft. com/communities/default. mspx Most Valuable Professional (MVP) http: //www. mvp. support. microsoft. com/ Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http: //www. microsoft. com/communities/newsgroups/default. mspx User Groups Meet and learn with your peers http: //www. microsoft. com/communities/usergroups/default. mspx
Community Resources http: //www. microsoft. com/communities/default. mspx Most Valuable Professional (MVP) http: //www. mvp. support. microsoft. com/ Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http: //www. microsoft. com/communities/newsgroups/default. mspx User Groups Meet and learn with your peers http: //www. microsoft. com/communities/usergroups/default. mspx
 Suggested Reading And Resources The tools you need to put technology to work! TITLE Deploying Secure 802. 11 Wireless Networks with Microsoft® Windows®: 0 -7356 -1939 -5 Available 8/13/03 Microsoft Press books are 20% off at the Tech. Ed Bookstore Also buy any TWO Microsoft Press books and get a FREE T-Shirt
Suggested Reading And Resources The tools you need to put technology to work! TITLE Deploying Secure 802. 11 Wireless Networks with Microsoft® Windows®: 0 -7356 -1939 -5 Available 8/13/03 Microsoft Press books are 20% off at the Tech. Ed Bookstore Also buy any TWO Microsoft Press books and get a FREE T-Shirt
 evaluations
evaluations
 © 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.


