9a45307f5485b484cb9e104fa6d2d15c.ppt
- Количество слайдов: 9

SEC-2017 -0017 DM-Based MEF Group Name: SEC WG Source: Qualcomm Inc. , Wolfgang Granzow, Phil Hawkes, Josef Blanz Meeting Date: SEC#27, 2017 -02 -13 Agenda Item: MAF/MEF Interface
Motivation • Enrolment is providing a MEF Client (CSE, AE or Node – to be formally defined) with credentials needed for operational phase – MEF Client may need occasional re-enrolling to obtain fresh credentials or to obtain credentials for use with other CSE/AE/Nodes • This is remote management – management of credentials • High Level Proposal: DM-based MEF, comprising – DM functionality for configuring credential objects currently in TS 0022 • Move those <mgmt. Obj> to TS-0032 – Use <mgmt. Cmd> to trigger operations • MEF equivalent of MAF <symm. Key. Reg> Creation for registering symm keys • Certificate Enrolment using EST (RFC 7030), with MEF acting as EST Server (an RA)

<mgmt. Obj> from TS-0022 • TS-0022 (See MAS-2017 -0022 Rxx) – Delete [Symm. Key. Cred], [my. Cert. File. Cred], [my. Cert. Fingerprint. Cred], [my. Cert. Issuer. DNCred], [public. Key. IDCred], [MAFKey. Reg. Cred] – Minor update to [trust. Anchor. Cred] (see MAS-2015 -0005 R 03) • Identify using cert fingerprint, and add URL for retrieving file. • Managed entity only needs to retrieve file once, even if in multiple [auth. Profile] • Associate with [auth. Profile] by configuring as a child of [auth. Profile] – Minor update to [auth. Profile] (see MAS-2015 -0005 R 03) • mgmt. Links to Credential Objects are replaced with either – parameters from those Credential Objects, or – credential identifiers that were in Credential Object specializations. • TS-0022 becomes independent of these Credential Objects (and TS-0032). • TS-0032 – Incorporate [Symm. Key. Cred], with minor change – Incorporate [my. Cert. File. Cred] – no change – Add [my. ESTProvisioned. Cert. Info] providing information about EST provisioned certs
![[authentication. Profile] in TS-0022 [authentication. Profile] //see MAS-2016 -0022 Rxx • SUID • TLSCiphersuites [authentication. Profile] in TS-0022 [authentication. Profile] //see MAS-2016 -0022 Rxx • SUID • TLSCiphersuites](https://present5.com/presentation/9a45307f5485b484cb9e104fa6d2d15c/image-4.jpg)
[authentication. Profile] in TS-0022 [authentication. Profile] //see MAS-2016 -0022 Rxx • SUID • TLSCiphersuites • symm. Key. ID [0. . 1] • MAFFQDN • MAFDuration • my. Cert. Fingerprint [0. . 1] // includes hash function ID + hash value • raw. Pub. Key. ID [0. . 1] //as above • [trust. Anchors] 0. . n // Configured to be child(ren) of [auth’n. Profile] – cert. URL – Cert. Fingerprint // URL for retrieving trust anchor cert from DM Server // include hash function ID + hash value
![TS-0032: [symm. Key. Cred] • Common <mgmt. Obj> attributes not shown • [symm. Key. TS-0032: [symm. Key. Cred] • Common <mgmt. Obj> attributes not shown • [symm. Key.](https://present5.com/presentation/9a45307f5485b484cb9e104fa6d2d15c/image-5.jpg)
TS-0032: [symm. Key. Cred] • Common <mgmt. Obj> attributes not shown • [symm. Key. Cred] //Not recommended. Should use <symm. Key. Reg> over Mcc/Mca – SUIDs – symm. Key. Issuer //symm. Key. Issuer is implicitly set to DM Server FQDN – symm. Key. Rel. ID – symm. Key. Value //Set ACL to prevent all further access once configured 5

TS-0032 Certificate mgmt. Objs • Common <mgmt. Obj> attributes not shown • EST is the recommended mechanism for provisioning certificates • [my. ESTProvisioned. Cert. Info] //Info about EST-provisioned cert. – SUIDs – Issuer. Name – Cert. Fingerprint. Algo – Cert. Fingerprint. Value • [my. Cert. File. Cred] //Direct configuration of certificates. No Certificate Signing Request. – SUIDs – my. Cert. File. Format – my. Cert. File. Content 6
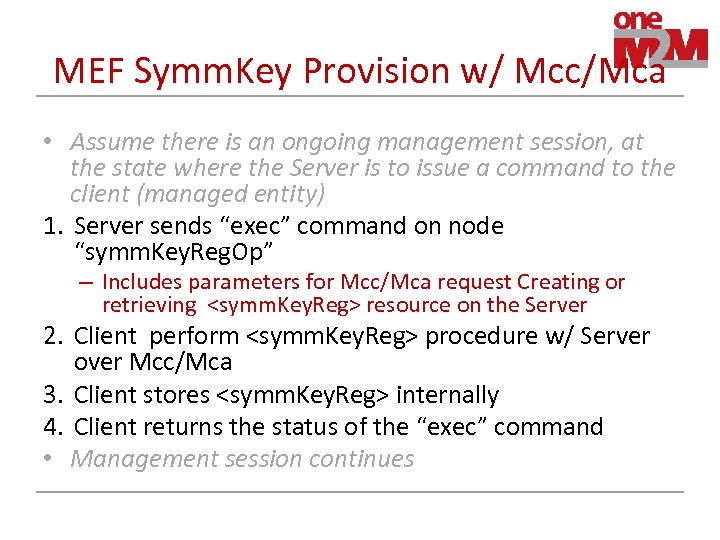
MEF Symm. Key Provision w/ Mcc/Mca • Assume there is an ongoing management session, at the state where the Server is to issue a command to the client (managed entity) 1. Server sends “exec” command on node “symm. Key. Reg. Op” – Includes parameters for Mcc/Mca request Creating or retrieving <symm. Key. Reg> resource on the Server 2. Client perform <symm. Key. Reg> procedure w/ Server over Mcc/Mca 3. Client stores <symm. Key. Reg> internally 4. Client returns the status of the “exec” command • Management session continues
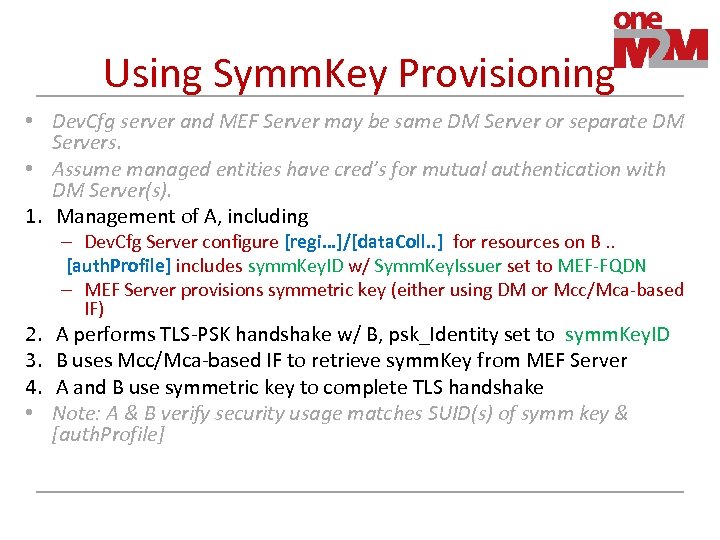
Using Symm. Key Provisioning • Dev. Cfg server and MEF Server may be same DM Server or separate DM Servers. • Assume managed entities have cred’s for mutual authentication with DM Server(s). 1. Management of A, including 2. 3. 4. • – Dev. Cfg Server configure [regi…]/[data. Coll. . ] for resources on B. . [auth. Profile] includes symm. Key. ID w/ Symm. Key. Issuer set to MEF-FQDN – MEF Server provisions symmetric key (either using DM or Mcc/Mca-based IF) A performs TLS-PSK handshake w/ B, psk_Identity set to symm. Key. ID B uses Mcc/Mca-based IF to retrieve symm. Key from MEF Server A and B use symmetric key to complete TLS handshake Note: A & B verify security usage matches SUID(s) of symm key & [auth. Profile]
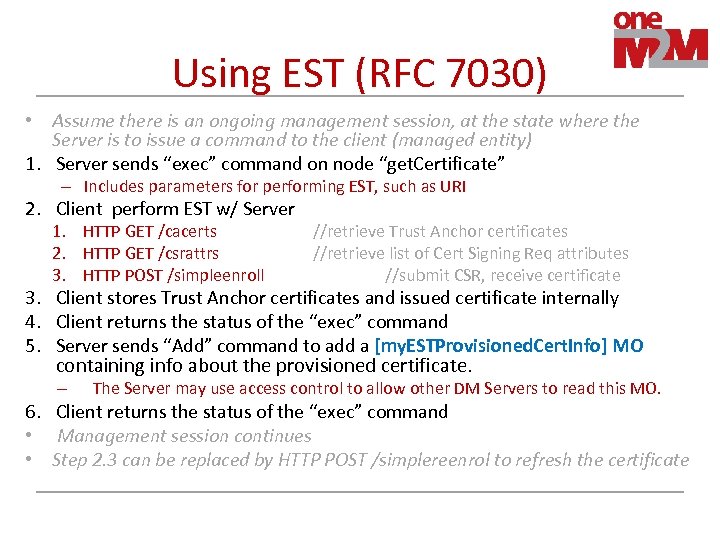
Using EST (RFC 7030) • Assume there is an ongoing management session, at the state where the Server is to issue a command to the client (managed entity) 1. Server sends “exec” command on node “get. Certificate” – Includes parameters for performing EST, such as URI 2. Client perform EST w/ Server 1. HTTP GET /cacerts 2. HTTP GET /csrattrs 3. HTTP POST /simpleenroll //retrieve Trust Anchor certificates //retrieve list of Cert Signing Req attributes //submit CSR, receive certificate 3. Client stores Trust Anchor certificates and issued certificate internally 4. Client returns the status of the “exec” command 5. Server sends “Add” command to add a [my. ESTProvisioned. Cert. Info] MO containing info about the provisioned certificate. – The Server may use access control to allow other DM Servers to read this MO. 6. Client returns the status of the “exec” command • Management session continues • Step 2. 3 can be replaced by HTTP POST /simplereenrol to refresh the certificate
9a45307f5485b484cb9e104fa6d2d15c.ppt