be2eb40a045c67b607082ac4a5b9f719.ppt
- Количество слайдов: 15
 SEC-2016 -0193 MAF&MEF Interface Specification discussion of the next steps Group Name: SEC WG Source: Qualcomm Inc. , Phil Hawkes, Wolfgang Granzow Meeting Date: SEC#26, 2016 -12 -02 Agenda Item: WI-0057 -TEF_interface
SEC-2016 -0193 MAF&MEF Interface Specification discussion of the next steps Group Name: SEC WG Source: Qualcomm Inc. , Phil Hawkes, Wolfgang Granzow Meeting Date: SEC#26, 2016 -12 -02 Agenda Item: WI-0057 -TEF_interface
 Objective • At TP#24 the WI-0057 “TEF Interface” was agreed • From this WI, the stage-3 details of the interface between AEs and CSEs with M 2 M Authentication Function (MAF) and M 2 M Enrolment Function (MEF) shall result – Trust Enabling Function (TEF) is a generic term used for MAF and MEF • Discussion paper SEC-2016 -0165 R 01 was presented at TP#25 – 3 reference architecture options were proposed: 1) separate reference points for MAF and MEF 2) single new reference point for TEF 3) define TEF as a new CSF, then MAF and MEF become CSEs and new reference point is not required, i. e. Mca/Mcc applies – No agreement on the way forward was achieved at TP#25 2
Objective • At TP#24 the WI-0057 “TEF Interface” was agreed • From this WI, the stage-3 details of the interface between AEs and CSEs with M 2 M Authentication Function (MAF) and M 2 M Enrolment Function (MEF) shall result – Trust Enabling Function (TEF) is a generic term used for MAF and MEF • Discussion paper SEC-2016 -0165 R 01 was presented at TP#25 – 3 reference architecture options were proposed: 1) separate reference points for MAF and MEF 2) single new reference point for TEF 3) define TEF as a new CSF, then MAF and MEF become CSEs and new reference point is not required, i. e. Mca/Mcc applies – No agreement on the way forward was achieved at TP#25 2
 Proposal • Let‘s begin developing MAF and MEF interfaces separately, i. e. Mmef and Mmaf, and independent of Mca and Mcc • Even if MAF and MEF would be regarded as special types of CSEs, it would still make sense to use a distinct name for the reference points – We also use different names Mca and Mcc although the protocols used on these reference points are essentially identical • Alternatively we could use notation Ma and Me – There was discussion on using a one- or two-character index 3
Proposal • Let‘s begin developing MAF and MEF interfaces separately, i. e. Mmef and Mmaf, and independent of Mca and Mcc • Even if MAF and MEF would be regarded as special types of CSEs, it would still make sense to use a distinct name for the reference points – We also use different names Mca and Mcc although the protocols used on these reference points are essentially identical • Alternatively we could use notation Ma and Me – There was discussion on using a one- or two-character index 3
 Title of the new specification • When avoiding the term “TEF”, what should be the title of the new specification to be developed under WI-0057 “TEF Interface”? • New working title could be one of the following: – MAF and MEF Interface Specification (suggested here) – Credential Management Specification – Trust Enabling Architecture 4
Title of the new specification • When avoiding the term “TEF”, what should be the title of the new specification to be developed under WI-0057 “TEF Interface”? • New working title could be one of the following: – MAF and MEF Interface Specification (suggested here) – Credential Management Specification – Trust Enabling Architecture 4
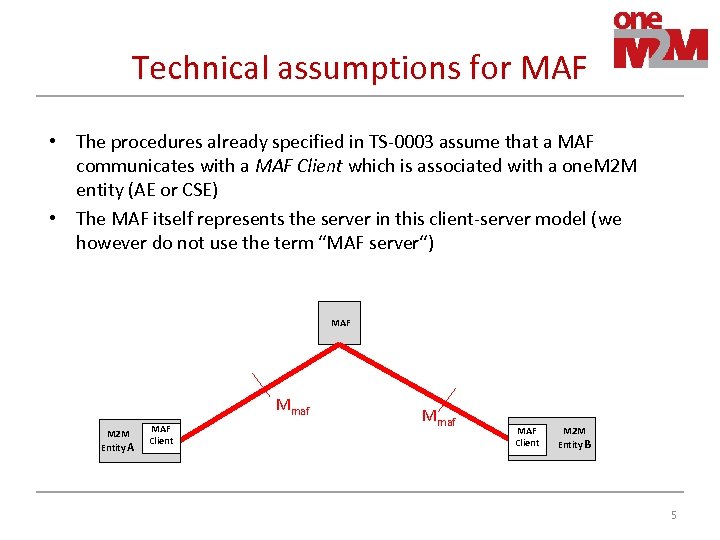 Technical assumptions for MAF • The procedures already specified in TS-0003 assume that a MAF communicates with a MAF Client which is associated with a one. M 2 M entity (AE or CSE) • The MAF itself represents the server in this client-server model (we however do not use the term “MAF server“) MAF Mmaf M 2 M Entity A MAF Client Mmaf MAF Client M 2 M Entity B 5
Technical assumptions for MAF • The procedures already specified in TS-0003 assume that a MAF communicates with a MAF Client which is associated with a one. M 2 M entity (AE or CSE) • The MAF itself represents the server in this client-server model (we however do not use the term “MAF server“) MAF Mmaf M 2 M Entity A MAF Client Mmaf MAF Client M 2 M Entity B 5
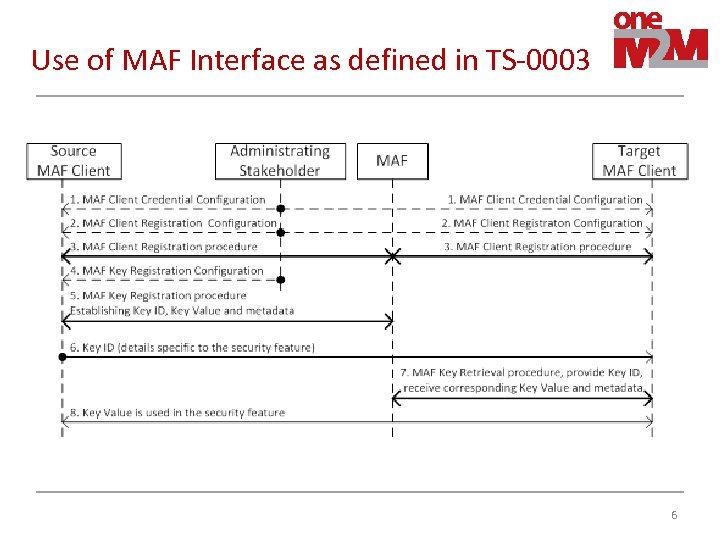 Use of MAF Interface as defined in TS-0003 6
Use of MAF Interface as defined in TS-0003 6
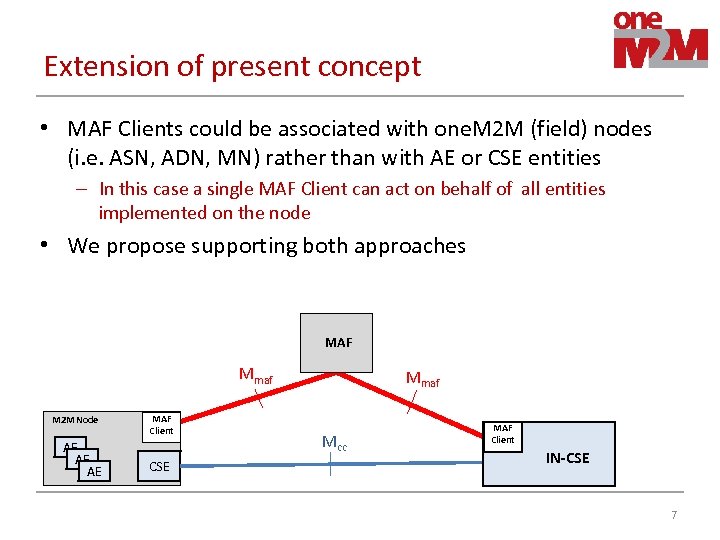 Extension of present concept • MAF Clients could be associated with one. M 2 M (field) nodes (i. e. ASN, ADN, MN) rather than with AE or CSE entities – In this case a single MAF Client can act on behalf of all entities implemented on the node • We propose supporting both approaches MAF Mmaf M 2 M Node AE AE AE MAF Client CSE Mmaf Mcc MAF Client IN-CSE 7
Extension of present concept • MAF Clients could be associated with one. M 2 M (field) nodes (i. e. ASN, ADN, MN) rather than with AE or CSE entities – In this case a single MAF Client can act on behalf of all entities implemented on the node • We propose supporting both approaches MAF Mmaf M 2 M Node AE AE AE MAF Client CSE Mmaf Mcc MAF Client IN-CSE 7
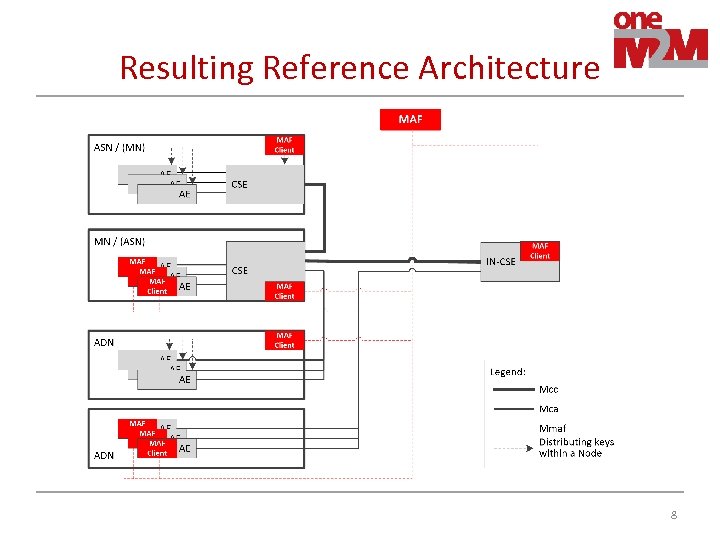 Resulting Reference Architecture 8
Resulting Reference Architecture 8
 Definitions (to be included into the new spec) • MAF Client: – functionality for performing MAF procedures on behalf of an associated CSE or AE, or on behalf of CSE or AE(s) present on an associated Node. Note: the existing definition in TS-0003 needs to be updated accordingly • MEF Client: – functionality for performing MEF procedures on behalf of an associated CSE or AE, or on behalf of CSE or AE(s) present on an associated Node. • MAF interface: – Communication interface between a MAF and a MAF Client identified by reference point Mmaf • MEF interface: – Communication interface between a MEF and a MEF Client identified by reference point Mmef 9
Definitions (to be included into the new spec) • MAF Client: – functionality for performing MAF procedures on behalf of an associated CSE or AE, or on behalf of CSE or AE(s) present on an associated Node. Note: the existing definition in TS-0003 needs to be updated accordingly • MEF Client: – functionality for performing MEF procedures on behalf of an associated CSE or AE, or on behalf of CSE or AE(s) present on an associated Node. • MAF interface: – Communication interface between a MAF and a MAF Client identified by reference point Mmaf • MEF interface: – Communication interface between a MEF and a MEF Client identified by reference point Mmef 9
 Proposed communication scheme on Mmaf • Reusing one. M 2 M RESTful protocol as applied on Mca and Mcc reference points • Reusing existing request and response primitives – many optional Mcc/Mca primitive parameters/features not required on Mmaf and. Mmef (not eliminating future extensions) • Blocking-mode access to server only (non-blocking may be defined in future release) 10
Proposed communication scheme on Mmaf • Reusing one. M 2 M RESTful protocol as applied on Mca and Mcc reference points • Reusing existing request and response primitives – many optional Mcc/Mca primitive parameters/features not required on Mmaf and. Mmef (not eliminating future extensions) • Blocking-mode access to server only (non-blocking may be defined in future release) 10
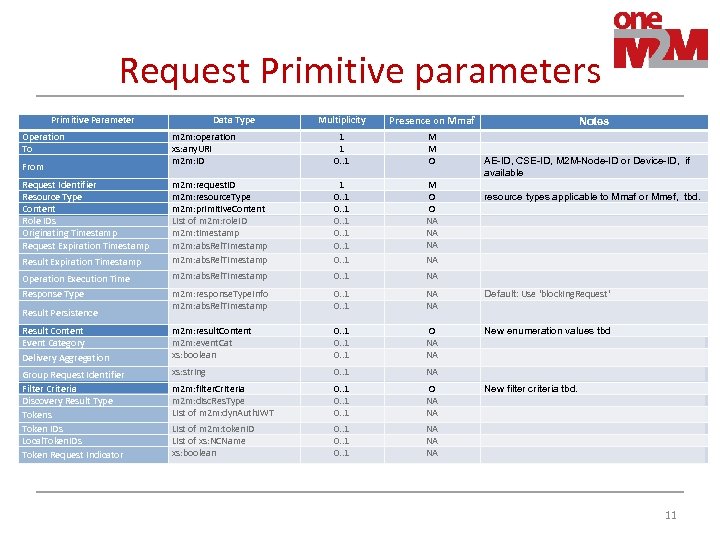 Request Primitive parameters Multiplicity Presence on Mmaf m 2 m: operation xs: any. URI m 2 m: ID 1 1 0. . 1 M M O m 2 m: request. ID m 2 m: resource. Type m 2 m: primitive. Content List of m 2 m: role. ID m 2 m: timestamp m 2 m: abs. Rel. Timestamp 1 0. . 1 M O O NA NA NA m 2 m: abs. Rel. Timestamp 0. . 1 NA m 2 m: response. Type. Info m 2 m: abs. Rel. Timestamp 0. . 1 NA NA Default: Use 'blocking. Request' Result Content Event Category Delivery Aggregation m 2 m: result. Content m 2 m: event. Cat xs: boolean 0. . 1 O NA NA New enumeration values tbd Group Request Identifier Filter Criteria Discovery Result Type Tokens Token IDs Local. Token. IDs Token Request Indicator xs: string 0. . 1 NA m 2 m: filter. Criteria m 2 m: disc. Res. Type List of m 2 m: dyn. Auth. JWT 0. . 1 O NA NA New filter criteria tbd. List of m 2 m: token. ID List of xs: NCName xs: boolean 0. . 1 NA NA NA Primitive Parameter Operation To From Request Identifier Resource Type Content Role IDs Originating Timestamp Request Expiration Timestamp Result Expiration Timestamp Operation Execution Time Response Type Result Persistence Data Type Notes AE-ID, CSE-ID, M 2 M-Node-ID or Device-ID, if available resource types applicable to Mmaf or Mmef, tbd. NA 11
Request Primitive parameters Multiplicity Presence on Mmaf m 2 m: operation xs: any. URI m 2 m: ID 1 1 0. . 1 M M O m 2 m: request. ID m 2 m: resource. Type m 2 m: primitive. Content List of m 2 m: role. ID m 2 m: timestamp m 2 m: abs. Rel. Timestamp 1 0. . 1 M O O NA NA NA m 2 m: abs. Rel. Timestamp 0. . 1 NA m 2 m: response. Type. Info m 2 m: abs. Rel. Timestamp 0. . 1 NA NA Default: Use 'blocking. Request' Result Content Event Category Delivery Aggregation m 2 m: result. Content m 2 m: event. Cat xs: boolean 0. . 1 O NA NA New enumeration values tbd Group Request Identifier Filter Criteria Discovery Result Type Tokens Token IDs Local. Token. IDs Token Request Indicator xs: string 0. . 1 NA m 2 m: filter. Criteria m 2 m: disc. Res. Type List of m 2 m: dyn. Auth. JWT 0. . 1 O NA NA New filter criteria tbd. List of m 2 m: token. ID List of xs: NCName xs: boolean 0. . 1 NA NA NA Primitive Parameter Operation To From Request Identifier Resource Type Content Role IDs Originating Timestamp Request Expiration Timestamp Result Expiration Timestamp Operation Execution Time Response Type Result Persistence Data Type Notes AE-ID, CSE-ID, M 2 M-Node-ID or Device-ID, if available resource types applicable to Mmaf or Mmef, tbd. NA 11
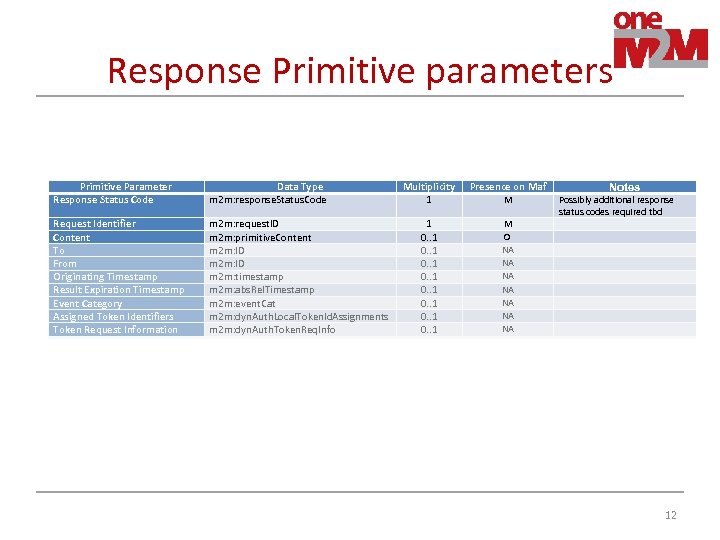 Response Primitive parameters Primitive Parameter Response Status Code Data Type m 2 m: response. Status. Code Request Identifier Content To From Originating Timestamp Result Expiration Timestamp Event Category Assigned Token Identifiers Token Request Information m 2 m: request. ID m 2 m: primitive. Content m 2 m: ID m 2 m: timestamp m 2 m: abs. Rel. Timestamp m 2 m: event. Cat m 2 m: dyn. Auth. Local. Token. Id. Assignments m 2 m: dyn. Auth. Token. Req. Info Multiplicity 1 Presence on Maf 1 0. . 1 M O NA NA M Notes Possibly additional response status codes required tbd 12
Response Primitive parameters Primitive Parameter Response Status Code Data Type m 2 m: response. Status. Code Request Identifier Content To From Originating Timestamp Result Expiration Timestamp Event Category Assigned Token Identifiers Token Request Information m 2 m: request. ID m 2 m: primitive. Content m 2 m: ID m 2 m: timestamp m 2 m: abs. Rel. Timestamp m 2 m: event. Cat m 2 m: dyn. Auth. Local. Token. Id. Assignments m 2 m: dyn. Auth. Token. Req. Info Multiplicity 1 Presence on Maf 1 0. . 1 M O NA NA M Notes Possibly additional response status codes required tbd 12
 MAF Interface Stage 3 Details in the new spec • Use similar specification approach as currently applied for specification of Mcc/Mca stage 3 details: – Define request and response primitives with parameters applicable on Mmaf – Define new resource types hosted by the MAF, structure and data types as defined in TS-0004 • Describe generic procedures at the MAF and MAF Client • Describe procedures specific to new resource types – Reuse bindings to application layer transport protocols • TS-0008/9/20 (HTTP/1. 1, Co. AP, Web. Socket; MQTT not suitable) • Specify “delta” relative to TS-0008/9/20 (if there is any) 13
MAF Interface Stage 3 Details in the new spec • Use similar specification approach as currently applied for specification of Mcc/Mca stage 3 details: – Define request and response primitives with parameters applicable on Mmaf – Define new resource types hosted by the MAF, structure and data types as defined in TS-0004 • Describe generic procedures at the MAF and MAF Client • Describe procedures specific to new resource types – Reuse bindings to application layer transport protocols • TS-0008/9/20 (HTTP/1. 1, Co. AP, Web. Socket; MQTT not suitable) • Specify “delta” relative to TS-0008/9/20 (if there is any) 13
 MAF and MEF Procedures defined in TS-0003 • Remote Security Provisioning Frameworks (RSPF) – Clause 8. 3 in TS-0003 – Certificate Enrolment currently part of this functionality but only partly specified right now • MAF-based security frameworks – – Clause 8. 8 in TS-0003 Clause 8. 2. 2. 3 for MAF-based SAEF Clause 8. 4. 2 for MAF-based ESPrim Currently no text for MAF-based ESData • Remote security frameworks for E 2 E security – Clause 8. 6 in TS-0003 – Referenced on Clause 8. 5. 2. 2. 3 for ESData 14
MAF and MEF Procedures defined in TS-0003 • Remote Security Provisioning Frameworks (RSPF) – Clause 8. 3 in TS-0003 – Certificate Enrolment currently part of this functionality but only partly specified right now • MAF-based security frameworks – – Clause 8. 8 in TS-0003 Clause 8. 2. 2. 3 for MAF-based SAEF Clause 8. 4. 2 for MAF-based ESPrim Currently no text for MAF-based ESData • Remote security frameworks for E 2 E security – Clause 8. 6 in TS-0003 – Referenced on Clause 8. 5. 2. 2. 3 for ESData 14
 Summary of proposed way forward • Start development of the new specification under the working title “MAF and MEF Interface Specification” at TP#26: – Proposed skeleton: SEC-2016 -0166 R 01 – Proposed scope: SEC-2016 -0167 R 01 – Proposed main body: SEC-2016 -0168 R 01 (addressing MAF interface only) • Add parts which were dropped from SEC-2016 -0138 (short names) into the new specification (can be postponed to SEC#26. x telcos) • More details on procedures need to be added in TS-0003 – Mapping between MAF/MEF procedures to CRUD procedures defined in the new MAF and MEF Interface Specification (i. e. follow-up on SEC-2016 -0137) • Add definition of new reference points to TS-0001 when the new specification has become stable 15
Summary of proposed way forward • Start development of the new specification under the working title “MAF and MEF Interface Specification” at TP#26: – Proposed skeleton: SEC-2016 -0166 R 01 – Proposed scope: SEC-2016 -0167 R 01 – Proposed main body: SEC-2016 -0168 R 01 (addressing MAF interface only) • Add parts which were dropped from SEC-2016 -0138 (short names) into the new specification (can be postponed to SEC#26. x telcos) • More details on procedures need to be added in TS-0003 – Mapping between MAF/MEF procedures to CRUD procedures defined in the new MAF and MEF Interface Specification (i. e. follow-up on SEC-2016 -0137) • Add definition of new reference points to TS-0001 when the new specification has become stable 15


