3d115ebb88dc84f9ccf9eca2067e981a.ppt
- Количество слайдов: 33

. SE Signed since September 2005 What’s it like 7 months later? Anne-Marie Eklund Löwinder, amel@iis. se www. iis. se

What is. se? • • • The Kingdom of Sweden TLD operated by II-stiftelsen ~442 446 domains (2006 -04 -25) A daily growth with ~500 domains 7 unicast servers + 2 anycast clusters www. iis. se
Why? • Increase integrity of the DNS • Increase security for. SE domain holders and their users. ‣ A countermeasure against pharming and other DNS MITM ‣ ‣ attacks. An infrastructure strengthening technique. A contemplated use of DNSSEC is for authenticated distribution of public keys for other security schemes. • Called upon by the authorities (the Swedish Post and • • Telecom Agency, PTS). New applications ENUM www. iis. se

When? • First workshop in February 1999 • Testing since January 2003 • Public testing since January 2004 • RFC 4033, 4034 & 4035 (aka DNSSEC bis) were published in March 2005. • September 13 th 2005, . se started to distribute the signed. se zone. • Signed delegations for early adopters from mid. November 2005. • More extensive tests started February 1 st, 2006. www. iis. se
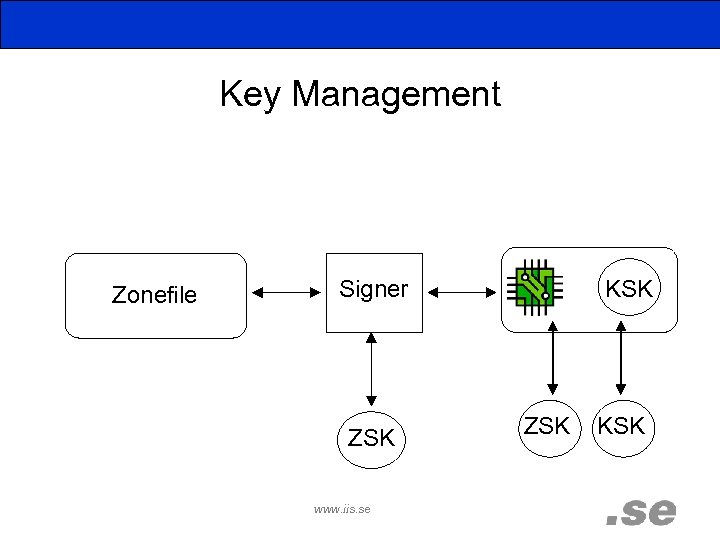
Key Management Zonefile Signer ZSK www. iis. se KSK ZSK KSK
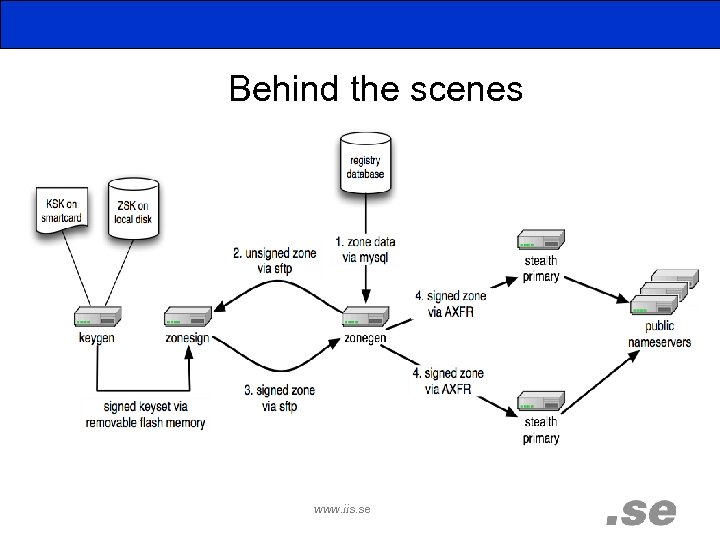
Behind the scenes www. iis. se

Distribution • All. SE name servers has been • • DNSSEC enabled since June 2005. Servers are running BIND or NSD. Different platforms and operating systems: ‣Free. BSD, Net. BSD, Linux, Solaris ‣Sparc, Alpha, x 86 www. iis. se
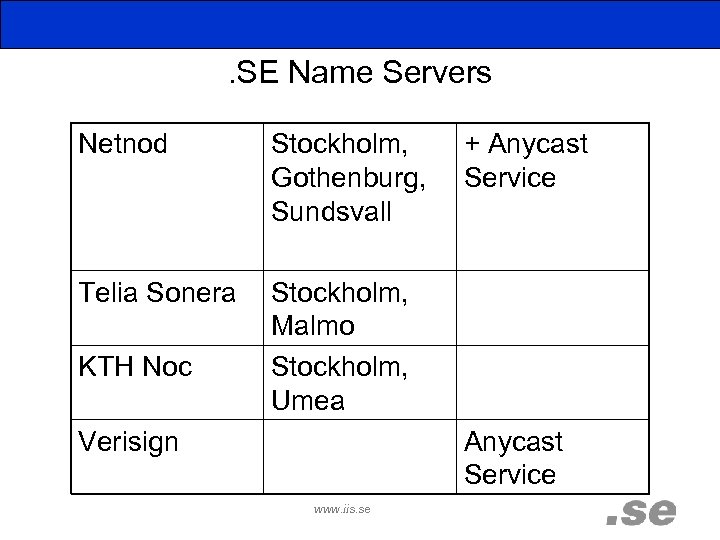
. SE Name Servers Netnod Stockholm, Gothenburg, Sundsvall Telia Sonera Stockholm, Malmo Stockholm, Umea KTH Noc Verisign + Anycast Service www. iis. se

Monitoring • Nagios has been extended to perform basic DNSSEC checks – Warn for signatures soon to expire – Test for correct DNSSEC additional processing – Check the integrity of some signatures www. iis. se
Signing childs – secured delegations • The domain must be a sub domain of. SE. • The domain holder must sign a limitation of liability statement with IIS. • The domain holder must provide IIS with a technical contact person. • IIS must be able to authenticate the technical contact person using a certificate signed by a certificate authority trusted by. SE’s key management tool KEYMAN. • The domain must be delegated to one or more name servers, all of them supporting DNSSEC according to RFC 4033, 4034 and 4035. www. iis. se

Child Key Management • KEYMAN is used for early adopters • New registry & registrar system with integrated DNSSEC planned for Q 4 2006 www. iis. se

New Registry • Todays registry model in. se is “confusing” • No clear relation between registrar and registrant • New registry service will be EPP based, and have a purer Registry – Registrar relationship • Registrars will handle DNSSEC through EPP • Requirements for DNSSEC? (Probably some extra paragraphs in the registrar agreement) • Authentication of registrants? www. iis. se

Certificate Authorities trusted by. SE • • • Posten Sverige AB SIS ID CA v 1 (The Swedish Post) Telia e-id CA CAcert. org Thawte Personal Freemail Sw. UPKI CA (Swedish Universities PKI CA) If someone think that their favourite CA is not in the list, they may contact us, and we will consider adding it. www. iis. se
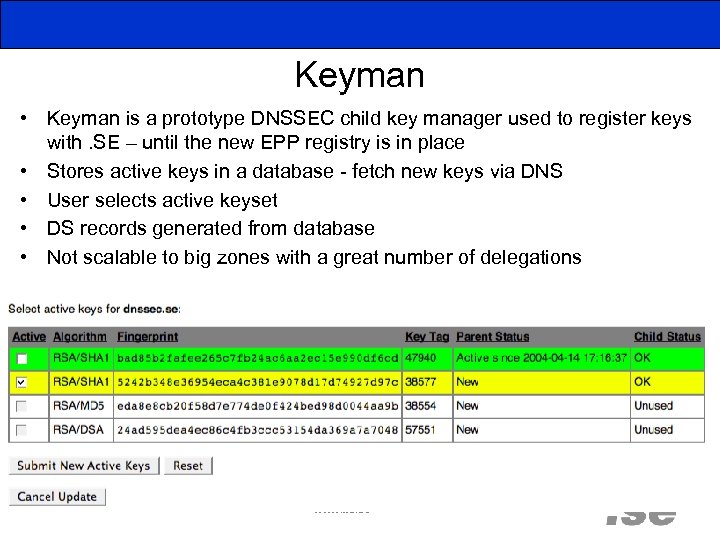
Keyman • Keyman is a prototype DNSSEC child key manager used to register keys with. SE – until the new EPP registry is in place • Stores active keys in a database - fetch new keys via DNS • User selects active keyset • DS records generated from database • Not scalable to big zones with a great number of delegations www. iis. se
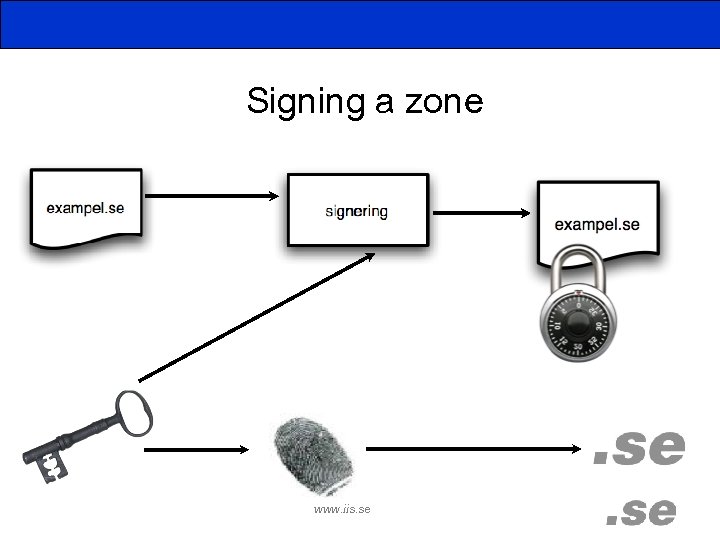
Signing a zone www. iis. se
Lessons learned • Stating the obvious… ØYou might be aware of this already Ø If not, you probably will be www. iis. se

Do not run BIND 8. www. iis. se

Make sure your firewall can handle EDNS. www. iis. se

Separate authoritative and recursive name servers. www. iis. se
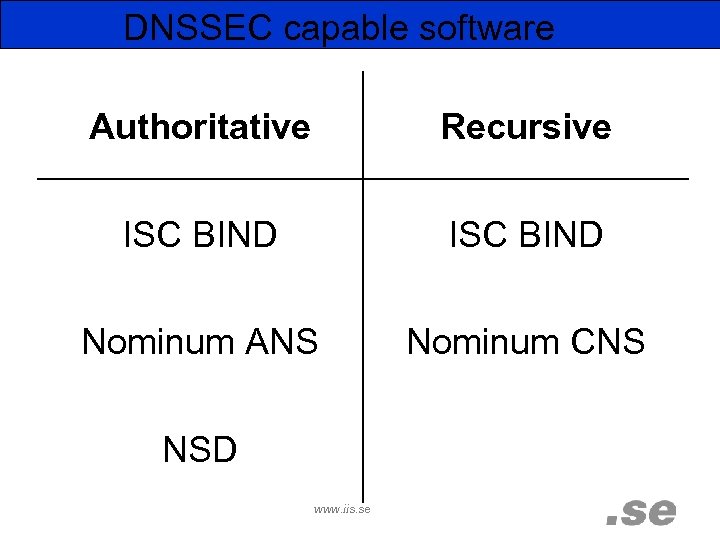
DNSSEC capable software Authoritative Recursive ISC BIND Nominum ANS Nominum CNS NSD www. iis. se

Performance - resolving • We are measuring to get a picture of what DNSSEC does to performance in the DNS environment. • A report will be published very soon. • From what we experience there are no big differences running without DNSSEC or with DNSSEC enabled. www. iis. se

What is the performance hit on a typical ISP resolver if they would enable DNSSEC validadtion for. se today? www. iis. se
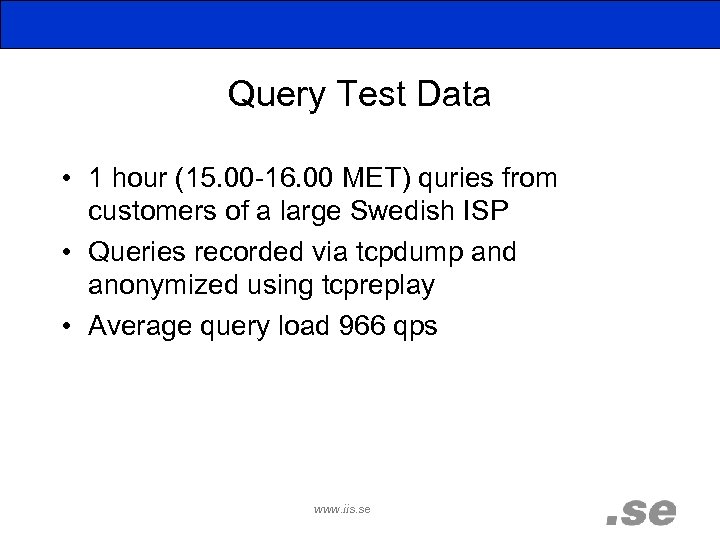
Query Test Data • 1 hour (15. 00 -16. 00 MET) quries from customers of a large Swedish ISP • Queries recorded via tcpdump and anonymized using tcpreplay • Average query load 966 qps www. iis. se
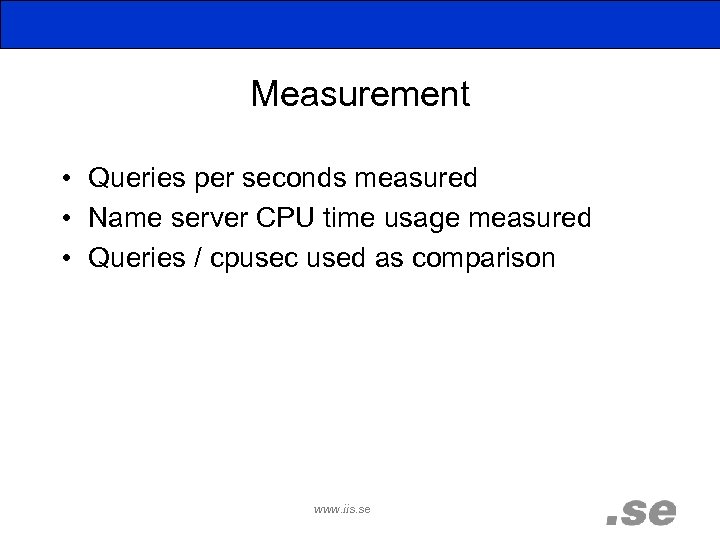
Measurement • Queries per seconds measured • Name server CPU time usage measured • Queries / cpusec used as comparison www. iis. se

Public resolvers • . SE provides public resolvers for testing purposes: ‣bind. dnssec. se ‣cns. dnssec. se • http: //dnssec. nic. se/recursive/ www. iis. se
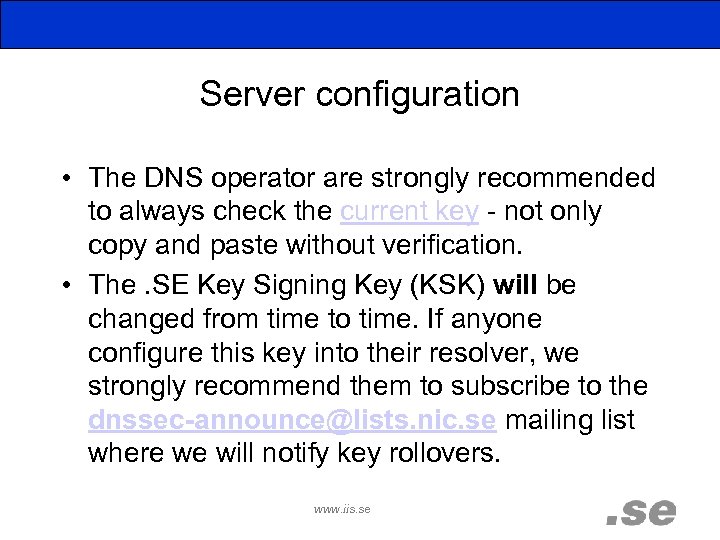
Server configuration • The DNS operator are strongly recommended to always check the current key - not only copy and paste without verification. • The. SE Key Signing Key (KSK) will be changed from time to time. If anyone configure this key into their resolver, we strongly recommend them to subscribe to the dnssec-announce@lists. nic. se mailing list where we will notify key rollovers. www. iis. se
Tests - Phase 1 • • Friendly users 18 zones and 11 different domain holders Short period of time Some test participants failed to update their signatures before expiration date • No other problems reported www. iis. se

Tests phase 2 • • Extended test population New agreement on Limitation of Liability Running for 12 months Now 27 zones and 20 different domain holders • Planning to send out a survey to get some idea about the participants experiences so far www. iis. se

Zone walking • What about it ? • The whois service for. se only shows registration status and delegation information • Extended information on domain names are only available via web interface and protected by CAPTCHA. • We’ve noticed some - but no alarming –activity • Working very actively with the development of NSEC 3 www. iis. se

Costs? • 2004 – Project budget 350. 000 SEK (appr. 35. 000 Euros) • 2005 – Project budget 950. 000 SEK (appr. 95. 000 Euros) • 2006 – Project budget appr. 100. 000 Euros www. iis. se
To do list - 2006 • Tests Phase 2 – Extended tests with more users ending in January 2007 • Enable DNSSEC validation at ISP’s - Information – Conference co-arranged with PTS. Try to reach ISP: s to convince them to enable DNSSEC on resolvers for their broadband customers. • Sign important DNS infrastructure - Education – 1 ½ day sponsored ”hands on” tutorial, participants from registrars, DNS service providers for banks, government agencies, large media companies, ISP: s. • Sharing the. se model - Documentation – ”DPS”, technical descriptions, code distribution, administrative routines. www. iis. se

Documentation & Policy • • • DNSSEC Policy and Practice Statement DNSSEC Limitation of Liability DNSSEC Environment description Deployment information for other TLDs Internal technical and administrative documentation www. iis. se

Thank you! Questions? dnssec-info@iis. se http: //dnssec. iis. se/ www. iis. se
3d115ebb88dc84f9ccf9eca2067e981a.ppt