a71a45a8eb3547d4da16f2934102d3f6.ppt
- Количество слайдов: 30
 Scope project presentation SCientific inn. Ovation Product conc. Ept 2009 -2011 4. 12. 2009
Scope project presentation SCientific inn. Ovation Product conc. Ept 2009 -2011 4. 12. 2009
 Time schedule for Scope presentations 10: 15 10: 30 10: 45 11: 00 11: 15 - 10: 30 10: 45 11: 00 11: 15 12: 00 WP 1: DATA ANOMALY DETECTION IN MOBILE NETWORKS AND INTERNET WP 2: PERSONAL SECURITY AND SMART MOBILE SYSTEMS WP 3: CENTRALIZED LOGISTICS MONITORING VIA MOBILE COMMUNICATION WP 4: DATA PLATFORM ARCHITECTURE FOR PUBLIC SAFETY Arjen mobiilipalvelut
Time schedule for Scope presentations 10: 15 10: 30 10: 45 11: 00 11: 15 - 10: 30 10: 45 11: 00 11: 15 12: 00 WP 1: DATA ANOMALY DETECTION IN MOBILE NETWORKS AND INTERNET WP 2: PERSONAL SECURITY AND SMART MOBILE SYSTEMS WP 3: CENTRALIZED LOGISTICS MONITORING VIA MOBILE COMMUNICATION WP 4: DATA PLATFORM ARCHITECTURE FOR PUBLIC SAFETY Arjen mobiilipalvelut
 Jy. U Tekes Programs in Nutshell • • Two different programs 1. Scope – innovative product concepts 2. Personal Mobile Space – mobile applications for learning and well-being Key targets: – Identify new business and job opportunities for Jyväskylä area by combining competences of experienced Nokia R&D people, Jy. U researchers and students – Focus to industries where Central Finland has existing regional business infrastructure (security, logistics, software…). – Strengthen the Jy. U academic infrastructure by establishing international collaboration with the main academic centers in Europe and the US.
Jy. U Tekes Programs in Nutshell • • Two different programs 1. Scope – innovative product concepts 2. Personal Mobile Space – mobile applications for learning and well-being Key targets: – Identify new business and job opportunities for Jyväskylä area by combining competences of experienced Nokia R&D people, Jy. U researchers and students – Focus to industries where Central Finland has existing regional business infrastructure (security, logistics, software…). – Strengthen the Jy. U academic infrastructure by establishing international collaboration with the main academic centers in Europe and the US.
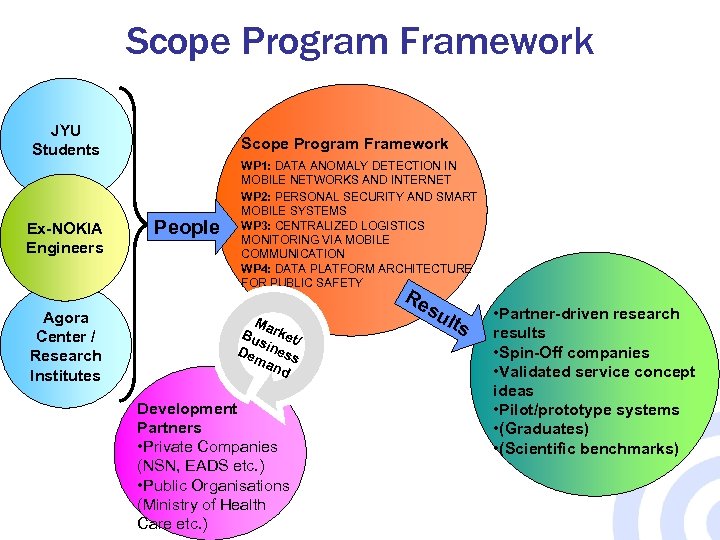 Scope Program Framework JYU Students Ex-NOKIA Engineers Agora Center / Research Institutes Scope Program Framework People WP 1: DATA ANOMALY DETECTION IN MOBILE NETWORKS AND INTERNET WP 2: PERSONAL SECURITY AND SMART MOBILE SYSTEMS WP 3: CENTRALIZED LOGISTICS MONITORING VIA MOBILE COMMUNICATION WP 4: DATA PLATFORM ARCHITECTURE FOR PUBLIC SAFETY Re Ma Bu rket/ s De iness ma nd Development Partners • Private Companies (NSN, EADS etc. ) • Public Organisations (Ministry of Health Care etc. ) su lts • Partner-driven research results • Spin-Off companies • Validated service concept ideas • Pilot/prototype systems • (Graduates) • (Scientific benchmarks)
Scope Program Framework JYU Students Ex-NOKIA Engineers Agora Center / Research Institutes Scope Program Framework People WP 1: DATA ANOMALY DETECTION IN MOBILE NETWORKS AND INTERNET WP 2: PERSONAL SECURITY AND SMART MOBILE SYSTEMS WP 3: CENTRALIZED LOGISTICS MONITORING VIA MOBILE COMMUNICATION WP 4: DATA PLATFORM ARCHITECTURE FOR PUBLIC SAFETY Re Ma Bu rket/ s De iness ma nd Development Partners • Private Companies (NSN, EADS etc. ) • Public Organisations (Ministry of Health Care etc. ) su lts • Partner-driven research results • Spin-Off companies • Validated service concept ideas • Pilot/prototype systems • (Graduates) • (Scientific benchmarks)
 WP 1: Data anomaly detection in mobile networks and internet 4. 12. 2009
WP 1: Data anomaly detection in mobile networks and internet 4. 12. 2009
 Intrusion Detection Systems (IDS) IDS is a network security device that monitors network and/or system activities for malicious attacks. Traditional IDS is based on signatures: • Looks for signatures of specific attack type that has already been documented 6
Intrusion Detection Systems (IDS) IDS is a network security device that monitors network and/or system activities for malicious attacks. Traditional IDS is based on signatures: • Looks for signatures of specific attack type that has already been documented 6
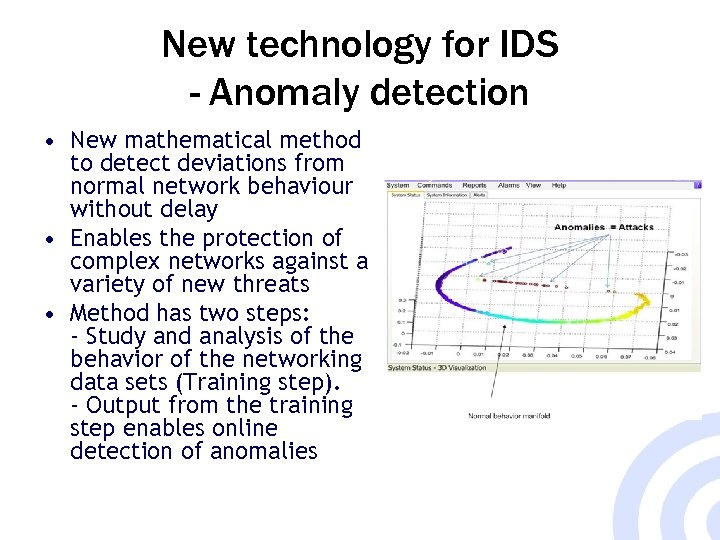 New technology for IDS - Anomaly detection • New mathematical method to detect deviations from normal network behaviour without delay • Enables the protection of complex networks against a variety of new threats • Method has two steps: - Study and analysis of the behavior of the networking data sets (Training step). - Output from the training step enables online detection of anomalies
New technology for IDS - Anomaly detection • New mathematical method to detect deviations from normal network behaviour without delay • Enables the protection of complex networks against a variety of new threats • Method has two steps: - Study and analysis of the behavior of the networking data sets (Training step). - Output from the training step enables online detection of anomalies
 Use of the new method in mobile networks • Prove that the method can be applied to find anomalies from IP traffic in mobile networks • Steps to go – Sample data collection from Nokia Test Network (NTN), validate the usability of the data – Collect data from NTN for training steps – Implement the anomaly detection system into NTN – Create malware into NTN – Detect the anomalies • For the implementation of the anomaly detection system into NTN we need SW designers – Matlab, Wireshark, Editcap, Python, C++
Use of the new method in mobile networks • Prove that the method can be applied to find anomalies from IP traffic in mobile networks • Steps to go – Sample data collection from Nokia Test Network (NTN), validate the usability of the data – Collect data from NTN for training steps – Implement the anomaly detection system into NTN – Create malware into NTN – Detect the anomalies • For the implementation of the anomaly detection system into NTN we need SW designers – Matlab, Wireshark, Editcap, Python, C++
 WP 2: Personal Security via Smart Mobile Technology WP 2 a: Personalized Mobile Notification Channel 4. 12. 2009
WP 2: Personal Security via Smart Mobile Technology WP 2 a: Personalized Mobile Notification Channel 4. 12. 2009
 Emergency Notification During crises and emergencies, individuals at risk need accurate and timely information in order to take protective measures. Traditional means of public warning, such as broadcast media and outdoor warning sirens, have demonstrated repeatedly that they do not reach all members of a population at risk, nor do they result in behavioral compliance by all those who do receive emergency directives. 10
Emergency Notification During crises and emergencies, individuals at risk need accurate and timely information in order to take protective measures. Traditional means of public warning, such as broadcast media and outdoor warning sirens, have demonstrated repeatedly that they do not reach all members of a population at risk, nor do they result in behavioral compliance by all those who do receive emergency directives. 10
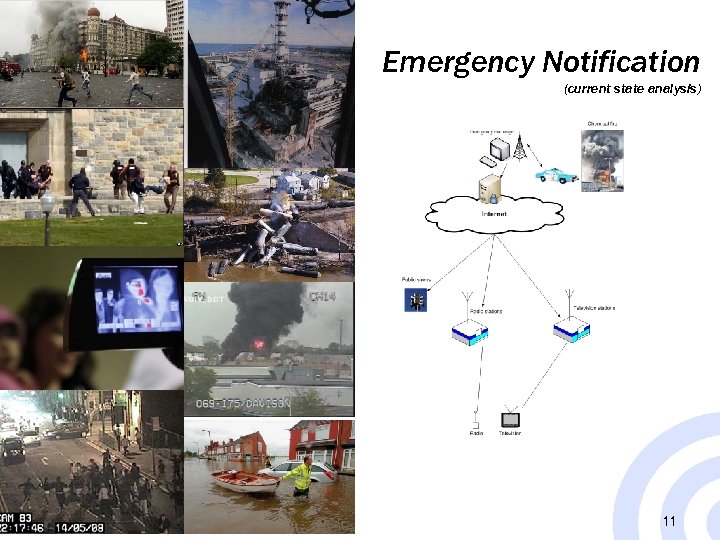 Emergency Notification (current state analysis) 11
Emergency Notification (current state analysis) 11
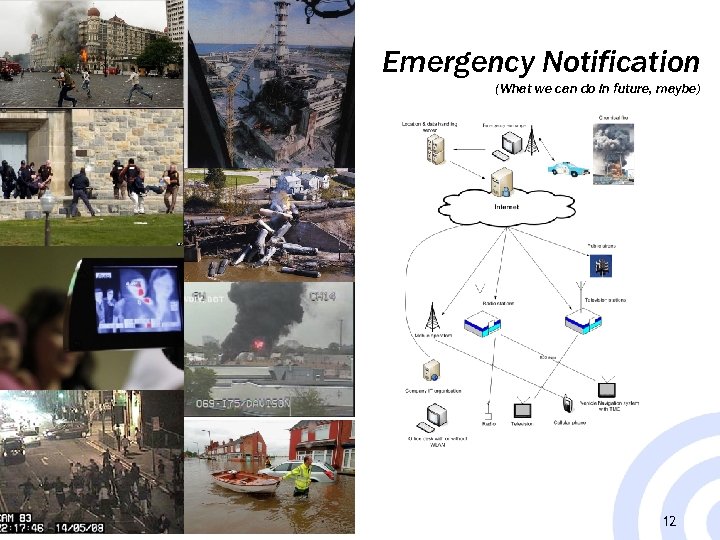 Emergency Notification (What we can do in future, maybe) 12
Emergency Notification (What we can do in future, maybe) 12
 Public Notification is a global challenge • Whether natural disaster, terrorism, civil unrest, industrial accidents, etc. , authorities must secure the safety of public • National notification strategies in many countries --weather, tsunami, “all hazard – all warning” • Multi-channel alerts: 13
Public Notification is a global challenge • Whether natural disaster, terrorism, civil unrest, industrial accidents, etc. , authorities must secure the safety of public • National notification strategies in many countries --weather, tsunami, “all hazard – all warning” • Multi-channel alerts: 13
 Why wireless technology? • 4, 1 billion mobiles phones globally • Effective notification technologies must address handset capabilities (from feature-less phone to smart phone) • Customer can be individual, service provider, enterprise, government (local, regional, national) 3 G Multimedia Web MMS SMS Global Market 14
Why wireless technology? • 4, 1 billion mobiles phones globally • Effective notification technologies must address handset capabilities (from feature-less phone to smart phone) • Customer can be individual, service provider, enterprise, government (local, regional, national) 3 G Multimedia Web MMS SMS Global Market 14
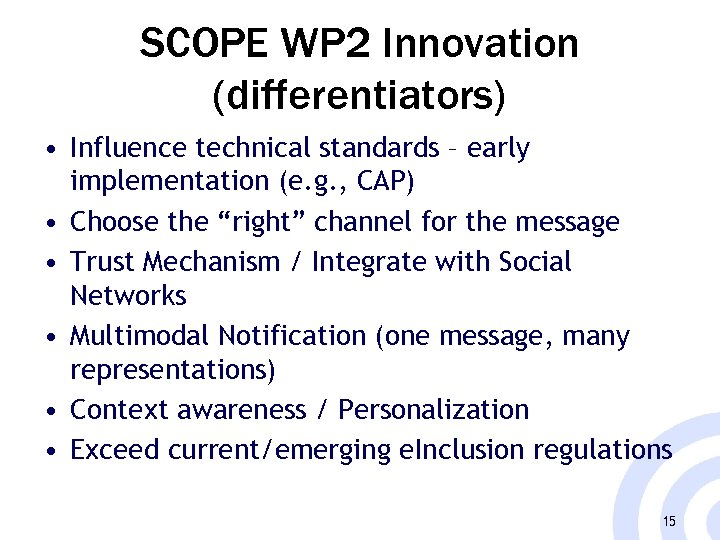 SCOPE WP 2 Innovation (differentiators) • Influence technical standards – early implementation (e. g. , CAP) • Choose the “right” channel for the message • Trust Mechanism / Integrate with Social Networks • Multimodal Notification (one message, many representations) • Context awareness / Personalization • Exceed current/emerging e. Inclusion regulations 15
SCOPE WP 2 Innovation (differentiators) • Influence technical standards – early implementation (e. g. , CAP) • Choose the “right” channel for the message • Trust Mechanism / Integrate with Social Networks • Multimodal Notification (one message, many representations) • Context awareness / Personalization • Exceed current/emerging e. Inclusion regulations 15
 SCOPE WP 2 examples • • • Understanding of new technologies User personalization Usability Context awareness understanding of different software platforms and limitations • C++, Java, Python, QT, Symbian etc… project management skills quality awareness end user point of view (ie. Performance) software module design and intergration software testing skills (results, analysis and improvement ideas 16
SCOPE WP 2 examples • • • Understanding of new technologies User personalization Usability Context awareness understanding of different software platforms and limitations • C++, Java, Python, QT, Symbian etc… project management skills quality awareness end user point of view (ie. Performance) software module design and intergration software testing skills (results, analysis and improvement ideas 16
 WP 3: Centralized Mobile Logistics Optimization System Mika Rantaniva
WP 3: Centralized Mobile Logistics Optimization System Mika Rantaniva
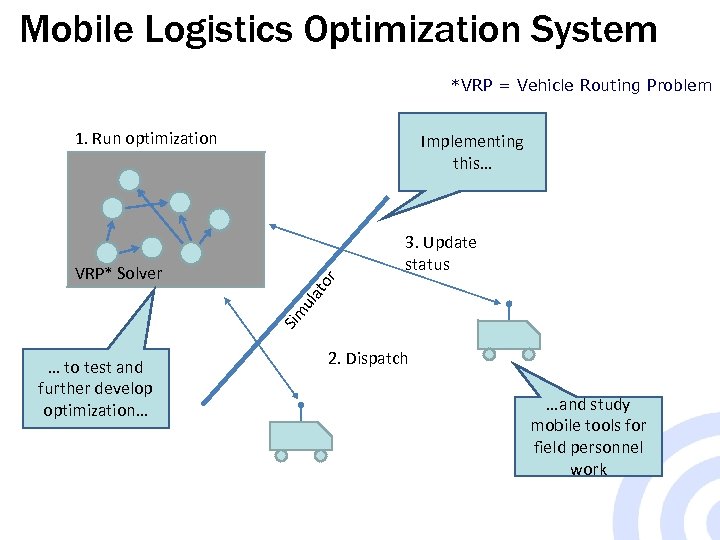 Mobile Logistics Optimization System *VRP = Vehicle Routing Problem 1. Run optimization Implementing this… 3. Update status Sim ula to r VRP* Solver … to test and further develop optimization… 2. Dispatch …and study mobile tools for field personnel work
Mobile Logistics Optimization System *VRP = Vehicle Routing Problem 1. Run optimization Implementing this… 3. Update status Sim ula to r VRP* Solver … to test and further develop optimization… 2. Dispatch …and study mobile tools for field personnel work
 The VRP algorithm core is based on worldclass scientific research • Prof. Olli Bräysy belongs to top three researchers globally in Vehicle Routing Problem (VRP) area • Applications & Innoroad References – – – Transportation services (Transpoint, Neste Oil) Waste management (L&T) Newspaper and mail delivery (Keskisuomalainen) Home care and meal delivery (City of Jyväskylä) Public transport (School transportation) Etc.
The VRP algorithm core is based on worldclass scientific research • Prof. Olli Bräysy belongs to top three researchers globally in Vehicle Routing Problem (VRP) area • Applications & Innoroad References – – – Transportation services (Transpoint, Neste Oil) Waste management (L&T) Newspaper and mail delivery (Keskisuomalainen) Home care and meal delivery (City of Jyväskylä) Public transport (School transportation) Etc.
 Key competence needs • Simulator / other VRP related research – Programming skills (Java, C, C++) – Optimisation, simulation and operation research studies benefit – Longer-term interest to academic research – More information: Olli Bräysy 044 -3591974 • Mobile tools for service personnel – Application programming skills (e. g. Java) – Cognitive studies (usability/end-user view) – This part depends on company funding
Key competence needs • Simulator / other VRP related research – Programming skills (Java, C, C++) – Optimisation, simulation and operation research studies benefit – Longer-term interest to academic research – More information: Olli Bräysy 044 -3591974 • Mobile tools for service personnel – Application programming skills (e. g. Java) – Cognitive studies (usability/end-user view) – This part depends on company funding
 SCOPE WG 4 “Tactical platform architecture to enchance development of Public Safety situation awareness systems”
SCOPE WG 4 “Tactical platform architecture to enchance development of Public Safety situation awareness systems”
 Target of the work: – Define • “Universal PMR Gateway” to connect TETRA network to exisisting and future applications and services by using standardized/de facto protocols • some future applications based on the customer requirements – Build demonstrator environment (e. g. Gateway + Java application) – Verify • Build demostrator to show functionality both of the application and gateway
Target of the work: – Define • “Universal PMR Gateway” to connect TETRA network to exisisting and future applications and services by using standardized/de facto protocols • some future applications based on the customer requirements – Build demonstrator environment (e. g. Gateway + Java application) – Verify • Build demostrator to show functionality both of the application and gateway
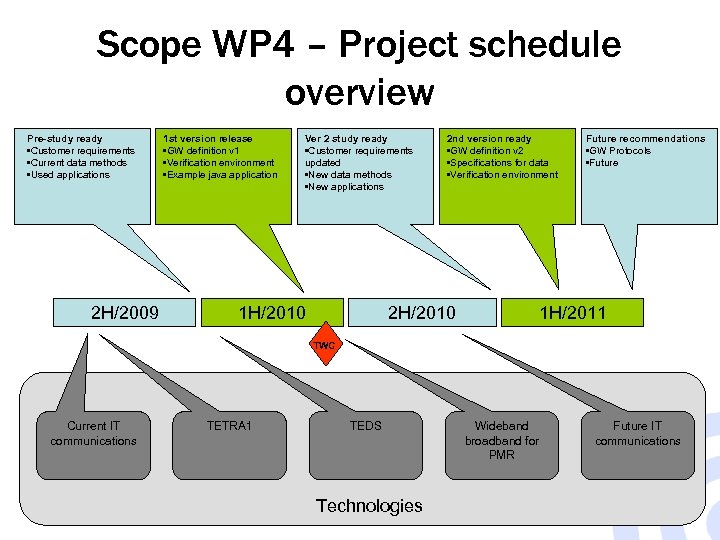 Scope WP 4 – Project schedule overview Pre-study ready • Customer requirements • Current data methods • Used applications 2 H/2009 1 st version release • GW definition v 1 • Verification environment • Example java application Ver 2 study ready • Customer requirements updated • New data methods • New applications 1 H/2010 2 nd version ready • GW definition v 2 • Specifications for data • Verification environment 2 H/2010 Future recommendations • GW Protocols • Future 1 H/2011 TWC Current IT communications TETRA 1 TEDS Technologies Wideband broadband for PMR Future IT communications
Scope WP 4 – Project schedule overview Pre-study ready • Customer requirements • Current data methods • Used applications 2 H/2009 1 st version release • GW definition v 1 • Verification environment • Example java application Ver 2 study ready • Customer requirements updated • New data methods • New applications 1 H/2010 2 nd version ready • GW definition v 2 • Specifications for data • Verification environment 2 H/2010 Future recommendations • GW Protocols • Future 1 H/2011 TWC Current IT communications TETRA 1 TEDS Technologies Wideband broadband for PMR Future IT communications
 Applications needs for TETRA terminals 1. Emergency notification system – Based on Java ME application on EADS terminal • Java MIDP 2. 0 (JSR 118) platform • XHTML browser • Integrated GPS receiver – Work to be done: • Specification of the application – features – UI – Usability • Coding • Testing • Documentation Kaasuvaroitus koko Jyväskylän alueella.
Applications needs for TETRA terminals 1. Emergency notification system – Based on Java ME application on EADS terminal • Java MIDP 2. 0 (JSR 118) platform • XHTML browser • Integrated GPS receiver – Work to be done: • Specification of the application – features – UI – Usability • Coding • Testing • Documentation Kaasuvaroitus koko Jyväskylän alueella.
 Applications needs for TETRA terminals 2. Police Blog - Some ideas: 1. With EADS TETRA terminals - Java based application - TETRA SDS service is used 2. With External portable devices (e. g. Win CE, i. Phone, Symbian, Android) - Sw platforms and tools to be selected accordingly - TETRA SDS service is used 3. With external portable PC - Emulate current police tactical information system - Sw platforms and tools to be selected accordingly
Applications needs for TETRA terminals 2. Police Blog - Some ideas: 1. With EADS TETRA terminals - Java based application - TETRA SDS service is used 2. With External portable devices (e. g. Win CE, i. Phone, Symbian, Android) - Sw platforms and tools to be selected accordingly - TETRA SDS service is used 3. With external portable PC - Emulate current police tactical information system - Sw platforms and tools to be selected accordingly
 Work to be done: • Specification of the applications – – Creation of concept features UI Usabiliity • Coding • Testing • Documentation
Work to be done: • Specification of the applications – – Creation of concept features UI Usabiliity • Coding • Testing • Documentation
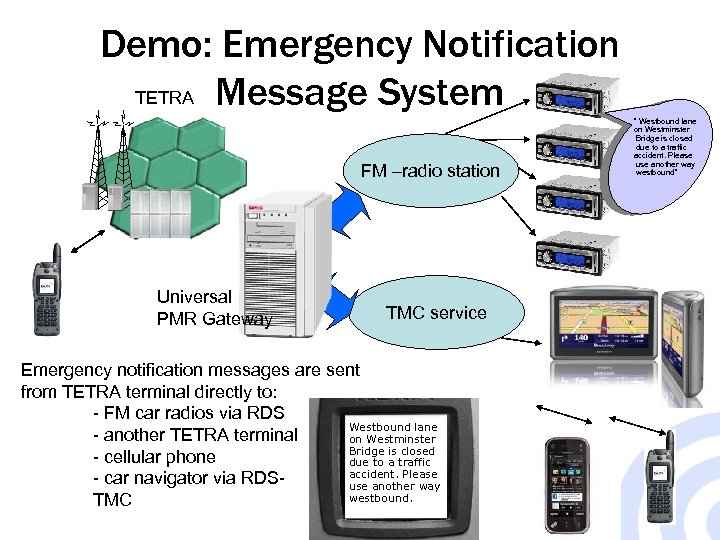 Demo: Emergency Notification TETRA Message System FM –radio station Universal PMR Gateway TMC service Emergency notification messages are sent from TETRA terminal directly to: - FM car radios via RDS Westbound lane - another TETRA terminal on Westminster Bridge is closed - cellular phone due to a traffic accident. Please - car navigator via RDSuse another way westbound. TMC ” Westbound lane on Westminster Bridge is closed due to a traffic accident. Please use another way westbound”
Demo: Emergency Notification TETRA Message System FM –radio station Universal PMR Gateway TMC service Emergency notification messages are sent from TETRA terminal directly to: - FM car radios via RDS Westbound lane - another TETRA terminal on Westminster Bridge is closed - cellular phone due to a traffic accident. Please - car navigator via RDSuse another way westbound. TMC ” Westbound lane on Westminster Bridge is closed due to a traffic accident. Please use another way westbound”
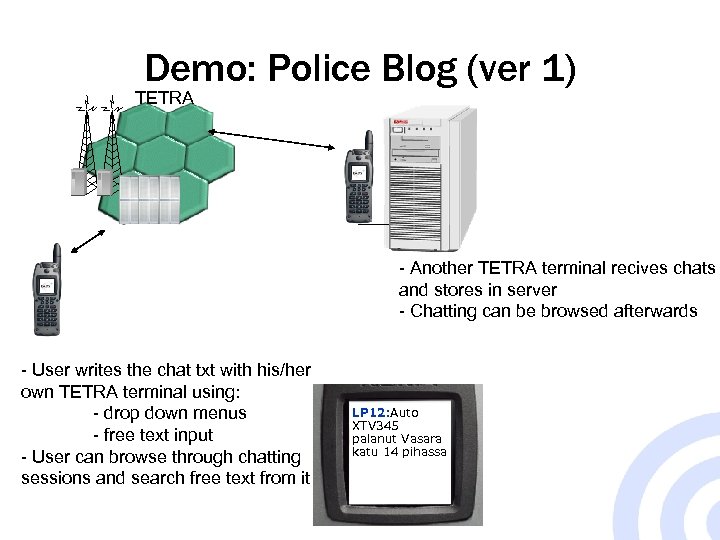 Demo: Police Blog (ver 1) TETRA - Another TETRA terminal recives chats and stores in server - Chatting can be browsed afterwards - User writes the chat txt with his/her own TETRA terminal using: - drop down menus - free text input - User can browse through chatting sessions and search free text from it LP 12: Auto XTV 345 palanut Vasara katu 14 pihassa
Demo: Police Blog (ver 1) TETRA - Another TETRA terminal recives chats and stores in server - Chatting can be browsed afterwards - User writes the chat txt with his/her own TETRA terminal using: - drop down menus - free text input - User can browse through chatting sessions and search free text from it LP 12: Auto XTV 345 palanut Vasara katu 14 pihassa
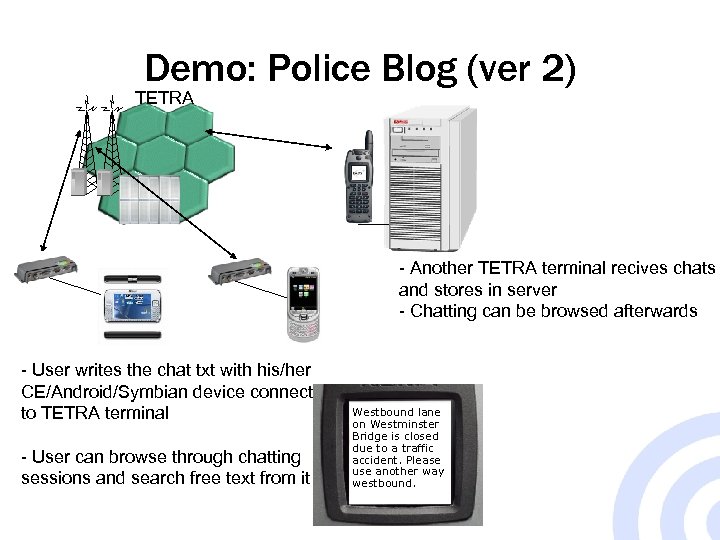 Demo: Police Blog (ver 2) TETRA - Another TETRA terminal recives chats and stores in server - Chatting can be browsed afterwards - User writes the chat txt with his/her CE/Android/Symbian device connected to TETRA terminal - User can browse through chatting sessions and search free text from it Westbound lane on Westminster Bridge is closed due to a traffic accident. Please use another way westbound.
Demo: Police Blog (ver 2) TETRA - Another TETRA terminal recives chats and stores in server - Chatting can be browsed afterwards - User writes the chat txt with his/her CE/Android/Symbian device connected to TETRA terminal - User can browse through chatting sessions and search free text from it Westbound lane on Westminster Bridge is closed due to a traffic accident. Please use another way westbound.
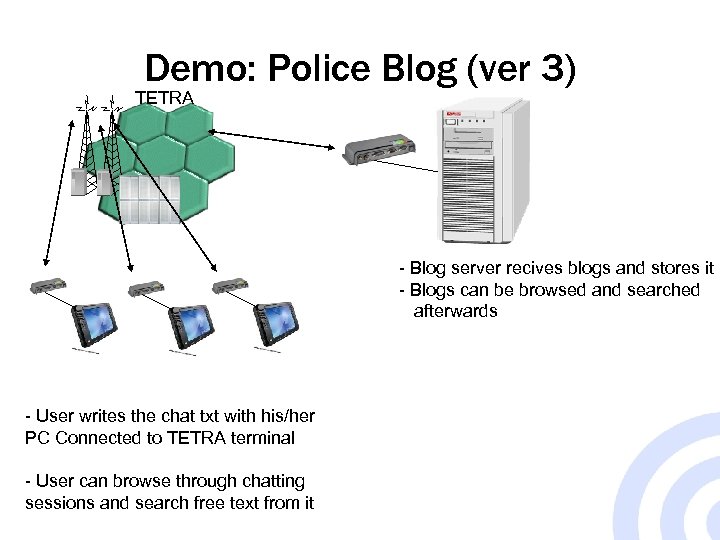 Demo: Police Blog (ver 3) TETRA - Blog server recives blogs and stores it - Blogs can be browsed and searched afterwards - User writes the chat txt with his/her PC Connected to TETRA terminal - User can browse through chatting sessions and search free text from it
Demo: Police Blog (ver 3) TETRA - Blog server recives blogs and stores it - Blogs can be browsed and searched afterwards - User writes the chat txt with his/her PC Connected to TETRA terminal - User can browse through chatting sessions and search free text from it


