76a7b27bb378d2c2093298d28d931cd6.ppt
- Количество слайдов: 64
 School of Computer Science and Mathematics It’s 2016: Why are we still being hacked ? Casimer De. Cusatis, Ph. D. The New York State Cloud Computing & Analytics Center at Marist College Poughkeepsie, NY (casimer. decusatis@marist. . edu @Dr_Casimer )
School of Computer Science and Mathematics It’s 2016: Why are we still being hacked ? Casimer De. Cusatis, Ph. D. The New York State Cloud Computing & Analytics Center at Marist College Poughkeepsie, NY (casimer. decusatis@marist. . edu @Dr_Casimer )
 Disclaimer • The security breach techniques discussed in this presentation should never be used on the Internet, or any public or private network. These examples are used for illustration purposes only. Your speaker and the college do not assume any liability if you practice these techniques on your own. • In other words, don’t try this at home !!!
Disclaimer • The security breach techniques discussed in this presentation should never be used on the Internet, or any public or private network. These examples are used for illustration purposes only. Your speaker and the college do not assume any liability if you practice these techniques on your own. • In other words, don’t try this at home !!!
 There are 2 kinds of companies… • Those that have been hacked • Those that don’t know they’ve been hacked yet There’s been a significant increase in hacking activity over the past few years…
There are 2 kinds of companies… • Those that have been hacked • Those that don’t know they’ve been hacked yet There’s been a significant increase in hacking activity over the past few years…
 What sort of companies were hacked in 2014? • August 2014
What sort of companies were hacked in 2014? • August 2014
 What sort of companies were hacked in 2014? • August 2014 • September 2014
What sort of companies were hacked in 2014? • August 2014 • September 2014
 What sort of companies were hacked in 2014? • August 2014 • September 2014 October 2014
What sort of companies were hacked in 2014? • August 2014 • September 2014 October 2014
 • Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
• Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
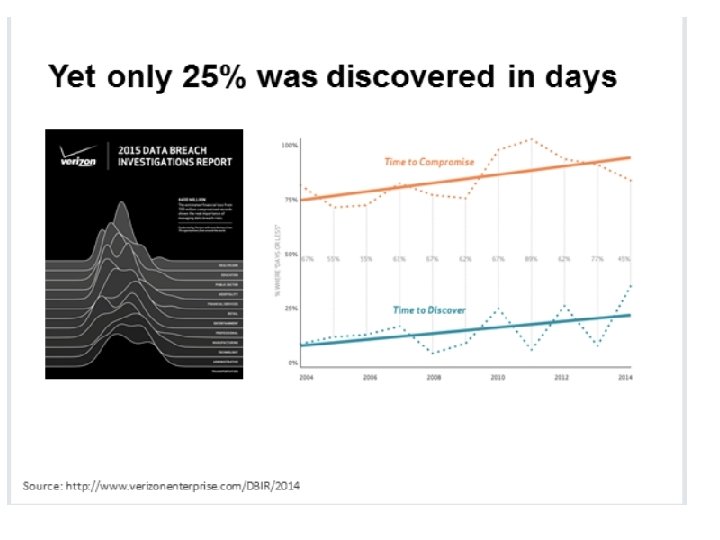
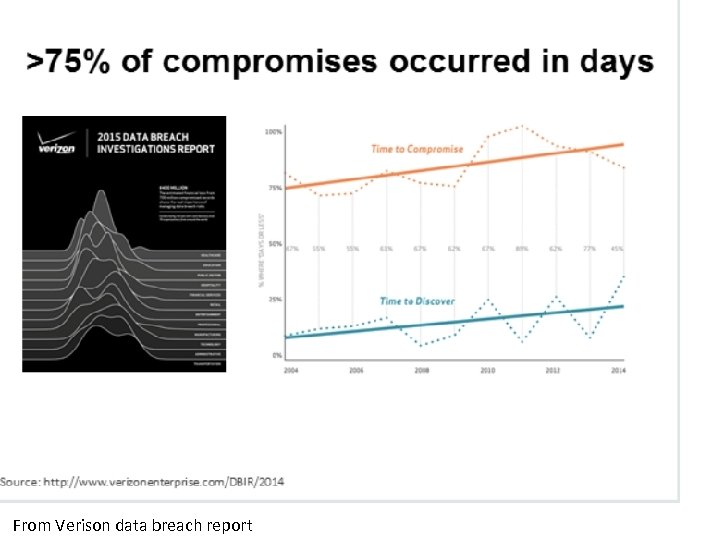 From Verison data breach report
From Verison data breach report
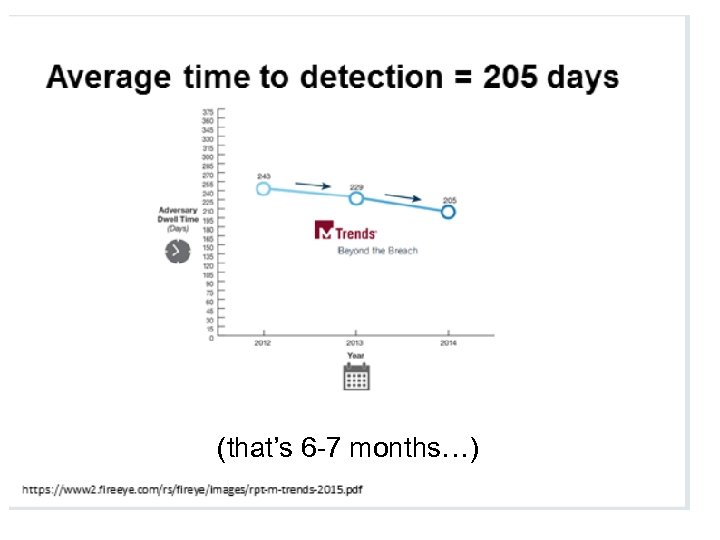 (that’s 6 -7 months…)
(that’s 6 -7 months…)
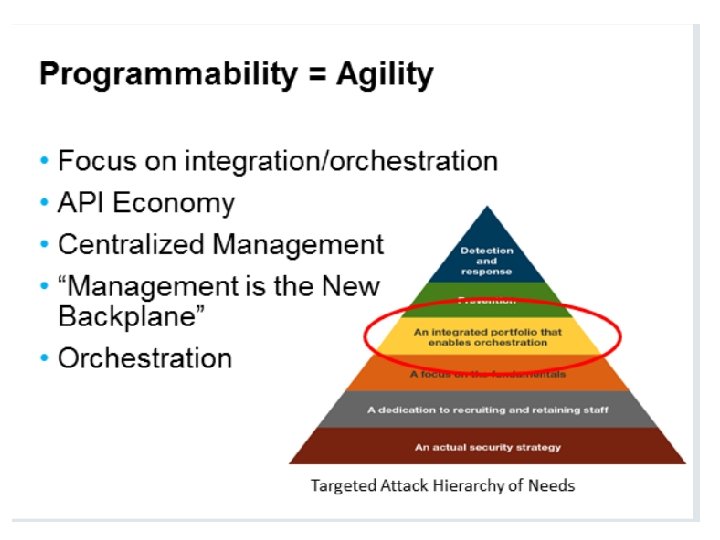
 Security Orchestration
Security Orchestration

 • Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies – In a typical year, large banks install 10 M patches they compile 500 M log files per day ! • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
• Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies – In a typical year, large banks install 10 M patches they compile 500 M log files per day ! • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
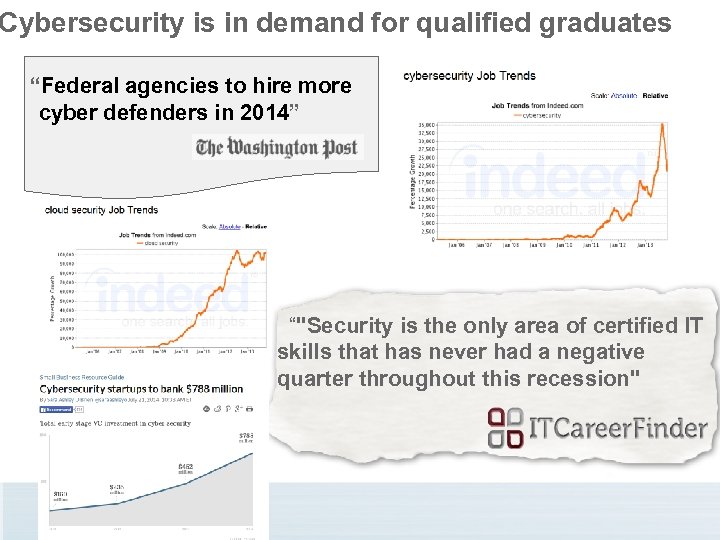 Cybersecurity is in demand for qualified graduates “Federal agencies to hire more cyber defenders in 2014” “"Security is the only area of certified IT skills that has never had a negative quarter throughout this recession"
Cybersecurity is in demand for qualified graduates “Federal agencies to hire more cyber defenders in 2014” “"Security is the only area of certified IT skills that has never had a negative quarter throughout this recession"
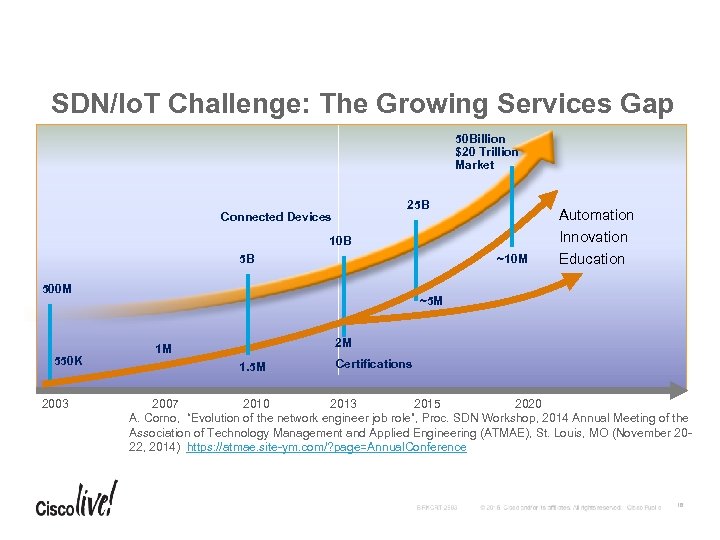 SDN/Io. T Challenge: The Growing Services Gap 50 Billion $20 Trillion Market 25 B Connected Devices 10 B 5 B ~10 M 500 M 550 K 2003 Automation Innovation Education ~5 M 2 M 1 M 1. 5 M Certifications 2007 2010 2013 2015 2020 A. Corno, “Evolution of the network engineer job role”, Proc. SDN Workshop, 2014 Annual Meeting of the Association of Technology Management and Applied Engineering (ATMAE), St. Louis, MO (November 2022, 2014) https: //atmae. site-ym. com/? page=Annual. Conference 18
SDN/Io. T Challenge: The Growing Services Gap 50 Billion $20 Trillion Market 25 B Connected Devices 10 B 5 B ~10 M 500 M 550 K 2003 Automation Innovation Education ~5 M 2 M 1 M 1. 5 M Certifications 2007 2010 2013 2015 2020 A. Corno, “Evolution of the network engineer job role”, Proc. SDN Workshop, 2014 Annual Meeting of the Association of Technology Management and Applied Engineering (ATMAE), St. Louis, MO (November 2022, 2014) https: //atmae. site-ym. com/? page=Annual. Conference 18
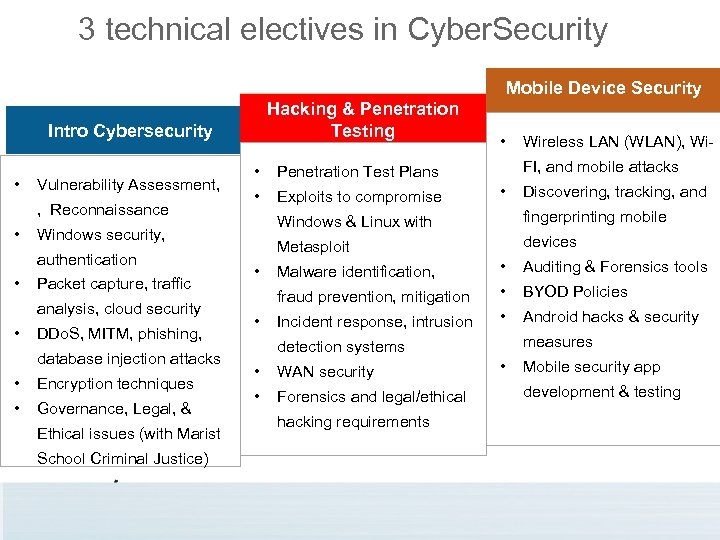 3 technical electives in Cyber. Security Mobile Device Security Hacking & Penetration Testing Intro Cybersecurity • Vulnerability Assessment, , Reconnaissance • Packet capture, traffic analysis, cloud security • • Exploits to compromise DDo. S, MITM, phishing, database injection attacks • Encryption techniques • Governance, Legal, & Ethical issues (with Marist School Criminal Justice) Wireless LAN (WLAN), Wi. FI, and mobile attacks Penetration Test Plans • Discovering, tracking, and Windows & Linux with fingerprinting mobile Metasploit Windows security, authentication • • • devices • Malware identification, • Auditing & Forensics tools fraud prevention, mitigation • • BYOD Policies Incident response, intrusion • Android hacks & security measures detection systems • WAN security • Forensics and legal/ethical hacking requirements • Mobile security app development & testing
3 technical electives in Cyber. Security Mobile Device Security Hacking & Penetration Testing Intro Cybersecurity • Vulnerability Assessment, , Reconnaissance • Packet capture, traffic analysis, cloud security • • Exploits to compromise DDo. S, MITM, phishing, database injection attacks • Encryption techniques • Governance, Legal, & Ethical issues (with Marist School Criminal Justice) Wireless LAN (WLAN), Wi. FI, and mobile attacks Penetration Test Plans • Discovering, tracking, and Windows & Linux with fingerprinting mobile Metasploit Windows security, authentication • • • devices • Malware identification, • Auditing & Forensics tools fraud prevention, mitigation • • BYOD Policies Incident response, intrusion • Android hacks & security measures detection systems • WAN security • Forensics and legal/ethical hacking requirements • Mobile security app development & testing
 • Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
• Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
 Attackers have more and better tools than ever before… and don’t consider collateral damage, update times, etc…
Attackers have more and better tools than ever before… and don’t consider collateral damage, update times, etc…
 Hacking your local power plant with Google • Supervisory Control And Data Acquisition • Runs electric power generation, nuclear plants, water treatment, sewage systems, oil and gas refineries, dams/hydroelectric, and other ICS systems – What is ICS ? Industrial Control Systems (these use industrial Ethernet switches, which have their own vulnerabilities) • SCADA standard says that these systems should never have public Internet access
Hacking your local power plant with Google • Supervisory Control And Data Acquisition • Runs electric power generation, nuclear plants, water treatment, sewage systems, oil and gas refineries, dams/hydroelectric, and other ICS systems – What is ICS ? Industrial Control Systems (these use industrial Ethernet switches, which have their own vulnerabilities) • SCADA standard says that these systems should never have public Internet access
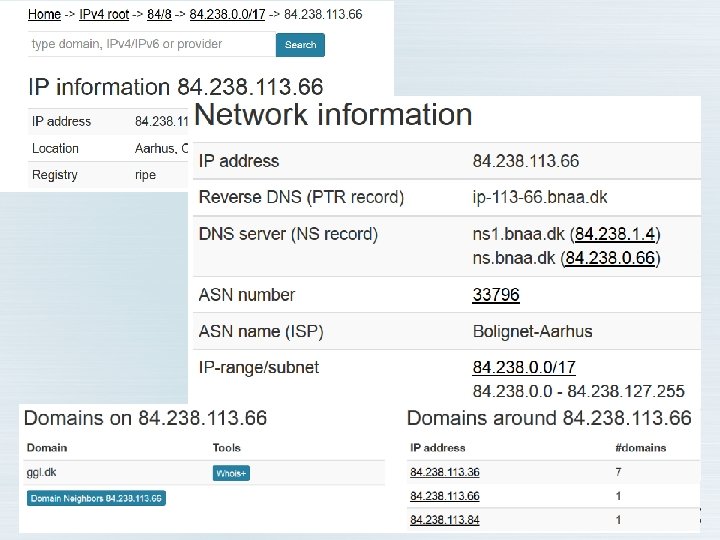
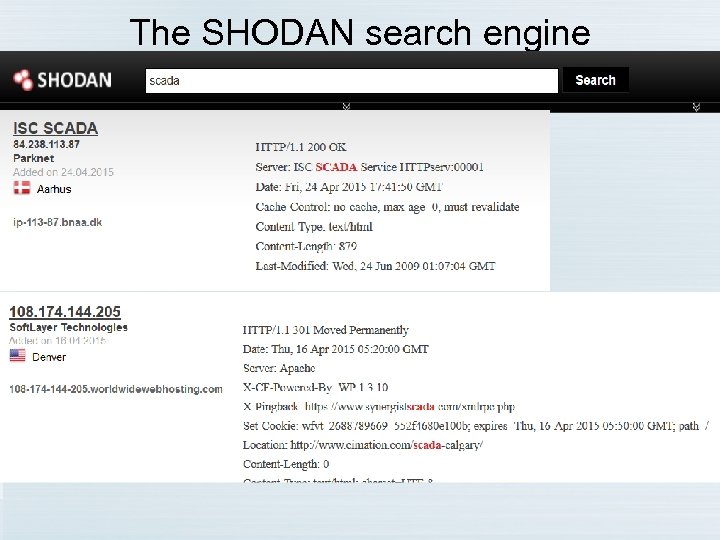 The SHODAN search engine Let’s search Google for Parknet Aarhus
The SHODAN search engine Let’s search Google for Parknet Aarhus
 What is the risk? • Let’s try a Google search and see what comes up
What is the risk? • Let’s try a Google search and see what comes up
 Well, at least they aren’t being exploited…
Well, at least they aren’t being exploited…
 List of SCADA recent hacks & vulnerabilities • 2007 – former nuclear plant engineer takes operating systems data to Iran • 2007 – hacker gains access to California power grid (despite warning authorities in advance) • 2009 – former IT consultant confesses to SCADA tampering at electric power plants source: S. Bosworth, Computer Security Handbook, 6 th edition
List of SCADA recent hacks & vulnerabilities • 2007 – former nuclear plant engineer takes operating systems data to Iran • 2007 – hacker gains access to California power grid (despite warning authorities in advance) • 2009 – former IT consultant confesses to SCADA tampering at electric power plants source: S. Bosworth, Computer Security Handbook, 6 th edition
 But that was a long time ago, right ?
But that was a long time ago, right ?
 List of SCADA recent hacks & vulnerabilities • 2014 – study identifies over 10, 000 small satellite dish uplinks used for SCADA vulnerable to attack • 2015 – security researchers find 60, 000 ICS systems with vulnerabilities controlling chemical plants, transportation systems, oil and gas refineries (including 150 zero day exploits) source: S. Gordeychik, presentation on SCADA Strangelove project, Chaos Communications Congress; see also D. Storm, Computer. World blog, January 2015 http: //www. computerworld. com/article/2475789/cybercrimehacking/hackers-exploit-scada-holes-to-take-full-control-of-criticalinfrastructure. html
List of SCADA recent hacks & vulnerabilities • 2014 – study identifies over 10, 000 small satellite dish uplinks used for SCADA vulnerable to attack • 2015 – security researchers find 60, 000 ICS systems with vulnerabilities controlling chemical plants, transportation systems, oil and gas refineries (including 150 zero day exploits) source: S. Gordeychik, presentation on SCADA Strangelove project, Chaos Communications Congress; see also D. Storm, Computer. World blog, January 2015 http: //www. computerworld. com/article/2475789/cybercrimehacking/hackers-exploit-scada-holes-to-take-full-control-of-criticalinfrastructure. html
 The NRC has been hacked 3 times in the past 3 years alone • In the first attack, hackers made use of a common phishing email to trick US Nuclear Regulatory Commission staff into handing over their sign-in details. The mail directed them to a Google spreadsheet for which they needed to log in. A total of 215 staff member were targeted, but only 12 fell victim. • Another attack hit victims with an embedded URL hosting malware. This time, the attackers used the flagship cloud service from Microsoft, otherwise known as Sky. Drive. • The third attack made use of a personal email account of an NRC employee, which had all of its 16 co-worker contacts infected with a PDF attachment containing an evil javascript. • http: //www. bestvpnservice. com/blog/us-nuclear-regulatorycommission-hacked-thrice-in-three-years/
The NRC has been hacked 3 times in the past 3 years alone • In the first attack, hackers made use of a common phishing email to trick US Nuclear Regulatory Commission staff into handing over their sign-in details. The mail directed them to a Google spreadsheet for which they needed to log in. A total of 215 staff member were targeted, but only 12 fell victim. • Another attack hit victims with an embedded URL hosting malware. This time, the attackers used the flagship cloud service from Microsoft, otherwise known as Sky. Drive. • The third attack made use of a personal email account of an NRC employee, which had all of its 16 co-worker contacts infected with a PDF attachment containing an evil javascript. • http: //www. bestvpnservice. com/blog/us-nuclear-regulatorycommission-hacked-thrice-in-three-years/
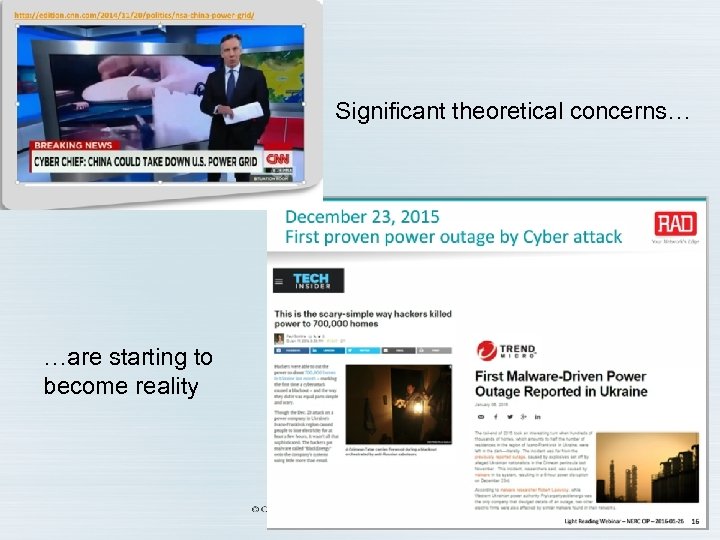 Significant theoretical concerns… …are starting to become reality
Significant theoretical concerns… …are starting to become reality
 PG&E Substation, Metcalf, CA • http: //www. wsj. com/articles/SB 1000142405270230 4851104579359141941621778 • http: //www. ksg. harvard. edu/hepg/Papers/2014/San doval_HEPGJune 2014. pdf
PG&E Substation, Metcalf, CA • http: //www. wsj. com/articles/SB 1000142405270230 4851104579359141941621778 • http: //www. ksg. harvard. edu/hepg/Papers/2014/San doval_HEPGJune 2014. pdf
 Metcalf Incident • April 16, 2014, around 1 AM – first known coordinated physical attack on a U. S. electrical power station (PG&E Metcalf, California substation) • Attackers first cut 6 optical fiber cables in an underground conduit near the station off Highway 101 (damaging them so repair would be difficult) – Level 3 ISP cables were also cut • A group of snipers armed with high power rifles opened fire on the plant for 20 minutes – Surgically knocked out 17 transformers supplying power to silicon valley – Oil-filled cooling systems leaked 52, 000 gallons of oil – Over 100 shell casings from AK-47 s found at the scene (no fingerprints) – Escaped before police arrived on the scene (officers initially arrived then left because there was no sign of a disturbance) • Emergency power rerouting avoided most blackouts – 27 days and $15 M before the station was fully operational again – Led to the so-called “ 7 bullet theory”
Metcalf Incident • April 16, 2014, around 1 AM – first known coordinated physical attack on a U. S. electrical power station (PG&E Metcalf, California substation) • Attackers first cut 6 optical fiber cables in an underground conduit near the station off Highway 101 (damaging them so repair would be difficult) – Level 3 ISP cables were also cut • A group of snipers armed with high power rifles opened fire on the plant for 20 minutes – Surgically knocked out 17 transformers supplying power to silicon valley – Oil-filled cooling systems leaked 52, 000 gallons of oil – Over 100 shell casings from AK-47 s found at the scene (no fingerprints) – Escaped before police arrived on the scene (officers initially arrived then left because there was no sign of a disturbance) • Emergency power rerouting avoided most blackouts – 27 days and $15 M before the station was fully operational again – Led to the so-called “ 7 bullet theory”

 • Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
• Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
 The Fazio Mechanical Services breach
The Fazio Mechanical Services breach
 The Fazio Mechanical Services breach better known as The Target Breach
The Fazio Mechanical Services breach better known as The Target Breach
 The Target Breach • • Christmas Season 2013 Black. POS malware “scrapes” transaction data Debit/credit transactions of 40 million customers In separate attack, information stolen on 70 million Target customers • Largest retail hack in U. S. history so far • Sales losses, stock decline, technology officer fired, CEO fired – Target spent over $65 M so far recoverying – Target profit down 46% for the holiday season – March 2015 – Target offers $10 M to settle class action suit (one of 90 such suites), case is ongoing… Copyright © 2015 Pearson Education, Inc. 3 -39
The Target Breach • • Christmas Season 2013 Black. POS malware “scrapes” transaction data Debit/credit transactions of 40 million customers In separate attack, information stolen on 70 million Target customers • Largest retail hack in U. S. history so far • Sales losses, stock decline, technology officer fired, CEO fired – Target spent over $65 M so far recoverying – Target profit down 46% for the holiday season – March 2015 – Target offers $10 M to settle class action suit (one of 90 such suites), case is ongoing… Copyright © 2015 Pearson Education, Inc. 3 -39
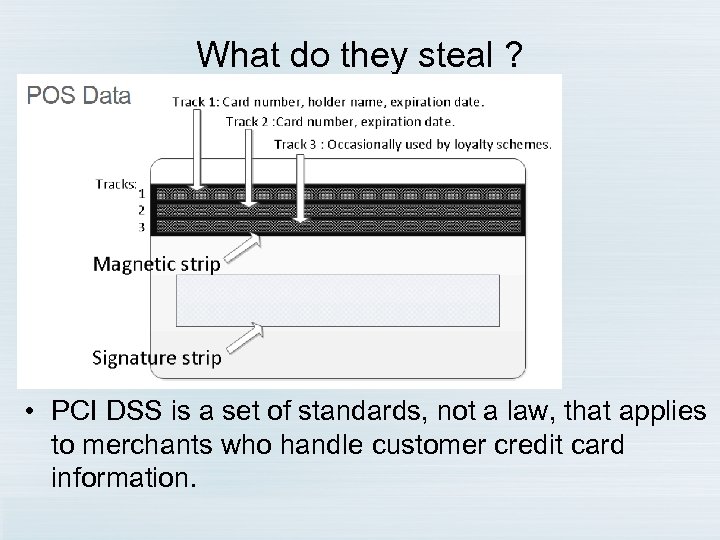 What do they steal ? • PCI DSS is a set of standards, not a law, that applies to merchants who handle customer credit card information. • Payment Card Industry Data Security Standard
What do they steal ? • PCI DSS is a set of standards, not a law, that applies to merchants who handle customer credit card information. • Payment Card Industry Data Security Standard
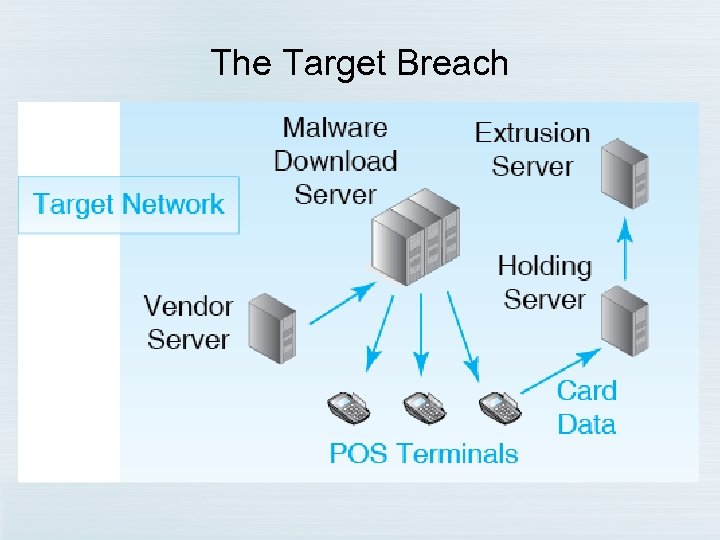 The Target Breach Copyright © 2015 Pearson Education, Inc. 3 -42
The Target Breach Copyright © 2015 Pearson Education, Inc. 3 -42
 Was it preventable? • Hacker’s install of the exfiltration system (a maze of dummy U. S. sites which then linked to sites in Russia), Target’s Bangalore security office (which monitors their systems 24 x 7) saw and flagged the hack attempt. • Target HQ in Minneapolis was duly notified. And then nothing happened. Other alarms from Nov 30 and Dec 2 were also ignored
Was it preventable? • Hacker’s install of the exfiltration system (a maze of dummy U. S. sites which then linked to sites in Russia), Target’s Bangalore security office (which monitors their systems 24 x 7) saw and flagged the hack attempt. • Target HQ in Minneapolis was duly notified. And then nothing happened. Other alarms from Nov 30 and Dec 2 were also ignored
 • Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
• Dire shortage of security professionals • Attackers have more and better tools than ever before • Security is really, really hard – Attackers only need to know 1 vulnerability – Defenders need to understand test everything (computers, storage, LAN, WAN, optical networks) – As well as keep up with the pace of new technologies that make everything a moving target (cloud, SDN, smart phones…) • Who can you trust…even established companies are getting into trouble • Attackers have gotten much better organized, often with nation state backing • The Internet of Things is coming…
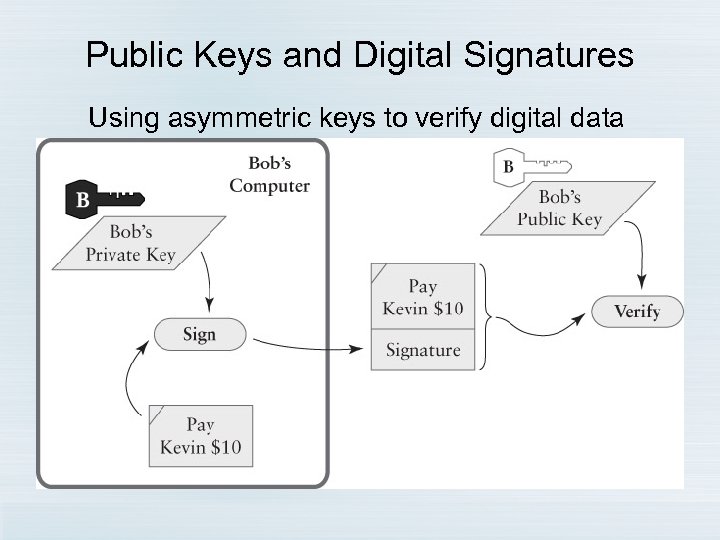 Public Keys and Digital Signatures Using asymmetric keys to verify digital data
Public Keys and Digital Signatures Using asymmetric keys to verify digital data
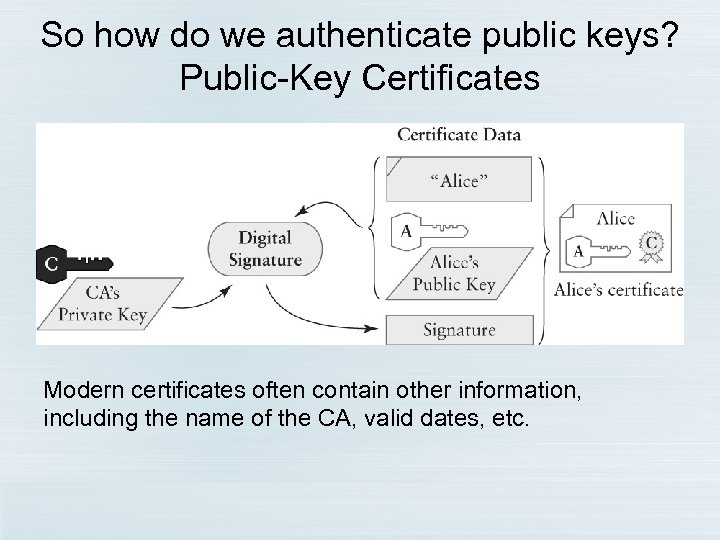 So how do we authenticate public keys? Public-Key Certificates Modern certificates often contain other information, including the name of the CA, valid dates, etc.
So how do we authenticate public keys? Public-Key Certificates Modern certificates often contain other information, including the name of the CA, valid dates, etc.
 Who signs a public key ? • A certificate authority provides outside validation that a security document—a digital certificate— sent by a server was properly issued to someone who controls that server's domain name. • A CA that gets hijacked or otherwise misused can issue documents for any domain anywhere that will be accepted as valid. • This allows attacks in which it's impossible to detect anything has gone wrong.
Who signs a public key ? • A certificate authority provides outside validation that a security document—a digital certificate— sent by a server was properly issued to someone who controls that server's domain name. • A CA that gets hijacked or otherwise misused can issue documents for any domain anywhere that will be accepted as valid. • This allows attacks in which it's impossible to detect anything has gone wrong.
 Lenovo • Founded 1984 • World’s biggest personal computer maker (now diversifying into smart phones) • Global concern doing business in every major country worldwide • $46. 3 Billion revenue last year
Lenovo • Founded 1984 • World’s biggest personal computer maker (now diversifying into smart phones) • Global concern doing business in every major country worldwide • $46. 3 Billion revenue last year
 Super. Fish • Lenovo laptops sold between September 2014 and January 2015 have pre-installed adware called Super. Fish which comes from a third party that has its own certificate authority – Lenovo claims no enterprise-class machines (Thinkpads) had this software, and that the software image was limited to the dates above. • All encrypted data on the laptop Is routed through this one CA and protected by a single password
Super. Fish • Lenovo laptops sold between September 2014 and January 2015 have pre-installed adware called Super. Fish which comes from a third party that has its own certificate authority – Lenovo claims no enterprise-class machines (Thinkpads) had this software, and that the software image was limited to the dates above. • All encrypted data on the laptop Is routed through this one CA and protected by a single password
 How does it work ? • Super. Fish monitors your web traffic while you’re shopping and then shows you similar products to the images that pop up in your browser. • But how can it do this when you’re securely connected to a website with an address beginning with https ? • Superfish intercepts traffic from the site and makes it searchable by tinkering with the Windows operating system and granting itself the ability to masquerade as any web site on the internet. • It’s so poorly designed that anyone can masquerade in the same way – if you have the password
How does it work ? • Super. Fish monitors your web traffic while you’re shopping and then shows you similar products to the images that pop up in your browser. • But how can it do this when you’re securely connected to a website with an address beginning with https ? • Superfish intercepts traffic from the site and makes it searchable by tinkering with the Windows operating system and granting itself the ability to masquerade as any web site on the internet. • It’s so poorly designed that anyone can masquerade in the same way – if you have the password
 But you’d need the password, right? • The password was cracked in February 2015 It was stored in Super. Fish’s active memory and was “trivial to extract” (took about 3 hours) • The password is “komodia, ” which happens to be the Greek goddess of happiness and amusement, and the name of a company that writes software that intercepts secure web traffic – Published by Wired magazine and many others
But you’d need the password, right? • The password was cracked in February 2015 It was stored in Super. Fish’s active memory and was “trivial to extract” (took about 3 hours) • The password is “komodia, ” which happens to be the Greek goddess of happiness and amusement, and the name of a company that writes software that intercepts secure web traffic – Published by Wired magazine and many others
 Lenovo response (Feb. 2015) • Lenovo said the company had "thoroughly investigated this technology and [does] not find any evidence to substantiate security concerns. "
Lenovo response (Feb. 2015) • Lenovo said the company had "thoroughly investigated this technology and [does] not find any evidence to substantiate security concerns. "
 So we’re cool, right ? • Wired business: “Lenovo’s response to its dangerous adware is astonishingly clueless” • Extreme Tech: “a mixture of tone deaf and defiant”…”an evolving message and a very deep hole” • BBC, Cnet, others…”Superfish screw-up highlights biggest problem in software” • Lenovo followup statement: “Super. Fish was included in some consumer notebooks shipped in late 2014. User feedback was not positive. ”
So we’re cool, right ? • Wired business: “Lenovo’s response to its dangerous adware is astonishingly clueless” • Extreme Tech: “a mixture of tone deaf and defiant”…”an evolving message and a very deep hole” • BBC, Cnet, others…”Superfish screw-up highlights biggest problem in software” • Lenovo followup statement: “Super. Fish was included in some consumer notebooks shipped in late 2014. User feedback was not positive. ”
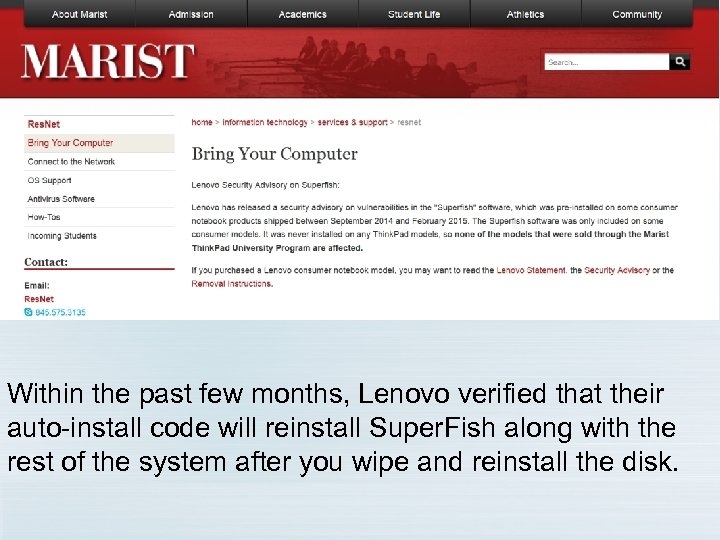 Within the past few months, Lenovo verified that their auto-install code will reinstall Super. Fish along with the rest of the system after you wipe and reinstall the disk.
Within the past few months, Lenovo verified that their auto-install code will reinstall Super. Fish along with the rest of the system after you wipe and reinstall the disk.
 Juniper’s Back Door • December 2015 – researchers find 2 back doors in Juniper firewalls, one of which allows you to decrypt information in a VPN when using Juniper Net. Screen firewalls http: //www. wired. com/2015/12/researchers-solve-the -juniper-mystery-and-they-say-its-partially-the-nsasfault/
Juniper’s Back Door • December 2015 – researchers find 2 back doors in Juniper firewalls, one of which allows you to decrypt information in a VPN when using Juniper Net. Screen firewalls http: //www. wired. com/2015/12/researchers-solve-the -juniper-mystery-and-they-say-its-partially-the-nsasfault/
 Juniper’s Back Door • Researchers suspect this vulnerability repurposes a back door initially implemented or suggested by the NSA – Or possibly one of its partners (like the UK) – Or possibly someone else entirely (Russia, China, …) • NSA allegedly placed weaknesses in a government approved encryption standard called Dual EC (a pseudorandom number generator) combined with a flaw in Juniper’s own code
Juniper’s Back Door • Researchers suspect this vulnerability repurposes a back door initially implemented or suggested by the NSA – Or possibly one of its partners (like the UK) – Or possibly someone else entirely (Russia, China, …) • NSA allegedly placed weaknesses in a government approved encryption standard called Dual EC (a pseudorandom number generator) combined with a flaw in Juniper’s own code
 Juniper’s Back Door • Weakness in Dual EC (Elliptic Curve) have been known since at least 2007, when Microsoft first discovered them • Dual EC was one of four random number generators approved by NIST for encrypting government documents • Problems with Dual EC make it possible to predict the output of the random number generator after viewing only 32 bytes of the output, making the code susceptible to cracking • It was widely debated whether the NSA selected the constraints for Dual EC to make it easier to break
Juniper’s Back Door • Weakness in Dual EC (Elliptic Curve) have been known since at least 2007, when Microsoft first discovered them • Dual EC was one of four random number generators approved by NIST for encrypting government documents • Problems with Dual EC make it possible to predict the output of the random number generator after viewing only 32 bytes of the output, making the code susceptible to cracking • It was widely debated whether the NSA selected the constraints for Dual EC to make it easier to break
 Juniper’s Back Door • Juniper claimed that they had implement their own constraint (rather than the NSA version) and also implemented a second ANSI random number generator which operated on the output of the Dual EC generator • Except their code had a bug. The second random number generator and other features were never used • According to security researchers, “What’s happening is they managed to screw it up in all the firmware, such that the ANSI code is there but it’s never used…That’s a catastrophic fail. ”
Juniper’s Back Door • Juniper claimed that they had implement their own constraint (rather than the NSA version) and also implemented a second ANSI random number generator which operated on the output of the Dual EC generator • Except their code had a bug. The second random number generator and other features were never used • According to security researchers, “What’s happening is they managed to screw it up in all the firmware, such that the ANSI code is there but it’s never used…That’s a catastrophic fail. ”
 Juniper’s Back Door • But at least Juniper generated their own constraints, right? • Well…yes, but…the constraint point on their software was apparently changed recently • Juniper apparently didn’t anticipate hackers getting access to their source code and changing the constraint point to something more easily broken
Juniper’s Back Door • But at least Juniper generated their own constraints, right? • Well…yes, but…the constraint point on their software was apparently changed recently • Juniper apparently didn’t anticipate hackers getting access to their source code and changing the constraint point to something more easily broken
 Juniper’s Back Door • Matthew Green, a cryptographer and professor at Johns Hopkins University, says that the ANSI failure raises additional questions about Juniper. “I don’t want to say that Juniper did this on purpose. But if you wanted to create a deliberate backdoor based on Dual_EC and make it look safe, while also having it be vulnerable, this is the way you’d do it. The best backdoor is a backdoor that looks like a bug, where you look at the thing and say, ‘Whoops, someone forgot a line of code or got a symbol wrong. ’ … It makes it deniable. But this bug happens to be sitting there right next to this incredibly dangerous NSA-designed random number generator, and it makes that generator actually dangerous where it might not have been otherwise. ”
Juniper’s Back Door • Matthew Green, a cryptographer and professor at Johns Hopkins University, says that the ANSI failure raises additional questions about Juniper. “I don’t want to say that Juniper did this on purpose. But if you wanted to create a deliberate backdoor based on Dual_EC and make it look safe, while also having it be vulnerable, this is the way you’d do it. The best backdoor is a backdoor that looks like a bug, where you look at the thing and say, ‘Whoops, someone forgot a line of code or got a symbol wrong. ’ … It makes it deniable. But this bug happens to be sitting there right next to this incredibly dangerous NSA-designed random number generator, and it makes that generator actually dangerous where it might not have been otherwise. ”
 OK, so at least now we can fix this • Juniper has released a patch, but all it does is reset the constraint point • So if anyone changes the constraint point again, we’re right back where we started • Juniper did NOT choose to enable the second ANSI random number generator for some reason • Further, Juniper did not release information on how it generated the new constraint point (so we can verify it’s truly random) or whether they had generated their own secret key for the constraint they did implement (again, back to where we started)
OK, so at least now we can fix this • Juniper has released a patch, but all it does is reset the constraint point • So if anyone changes the constraint point again, we’re right back where we started • Juniper did NOT choose to enable the second ANSI random number generator for some reason • Further, Juniper did not release information on how it generated the new constraint point (so we can verify it’s truly random) or whether they had generated their own secret key for the constraint they did implement (again, back to where we started)
 OK, so now we can fix this ? • Quoting security researchers, “It now depends on whether you trust them to have generated this point randomly or not. I would probably not do that at this point, ” • “There’s no legitimate reason to put Dual_EC in a product, ” he says. “There never was. This is an incredibly powerful and dangerous code and you put it in your system and it creates a capability that would not have been there otherwise. There’s no way to use it safely. ”
OK, so now we can fix this ? • Quoting security researchers, “It now depends on whether you trust them to have generated this point randomly or not. I would probably not do that at this point, ” • “There’s no legitimate reason to put Dual_EC in a product, ” he says. “There never was. This is an incredibly powerful and dangerous code and you put it in your system and it creates a capability that would not have been there otherwise. There’s no way to use it safely. ”
 Conclusions • Security is really, really hard • What can we do ? – Train the next generation of security experts • Knowledge is power. Arm yourself. • Automate wherever you can. – Take threat seriously – Develop better open source tools & analytics – Research new ways to counteract wellorganized attackers with unlimited resources (work smarter, not harder) – Get ready for the Internet of Things
Conclusions • Security is really, really hard • What can we do ? – Train the next generation of security experts • Knowledge is power. Arm yourself. • Automate wherever you can. – Take threat seriously – Develop better open source tools & analytics – Research new ways to counteract wellorganized attackers with unlimited resources (work smarter, not harder) – Get ready for the Internet of Things
 School of Computer Science and Mathematics QUESTIONS ? Follow @Dr_Casimer or http: //www. ofcconference. org/en-us/home/about/ofc-blog/
School of Computer Science and Mathematics QUESTIONS ? Follow @Dr_Casimer or http: //www. ofcconference. org/en-us/home/about/ofc-blog/
 School of Computer Science and Mathematics Recent Research Publications • C. De. Cusatis, J. Ziskin, T. Bundy, “The rise of SDN optical networks; has automated provisioning arrived? “, invited presentation, Pacific Telecom Conference, Honolulu, Hawaii (January 2014) • C. De. Cusatis, R. Cannistra, B. Carle, M. Johnson, J. Kapadia, Z. Meath, M. Miller, D. Young, T. Bundy , G. Zussman, K. Bergman, A. Carranza, C. Sher-De. Cusatis, A. Pletch, R. Ransom, “Dynamic orchestration test bed for SDN and NFV at the New York State Center for Cloud Computing & Analytics”, OFC 2014 annual meeting, San Francisco, CA (accepted & to be published, March 2014) • C. De. Cusatis et. al. , “Developing a software defined networking curriculum through industry partnership”, Proc. ASEE Annual Meeting, Hartford, CT (April 3 -5, 2014) ** named among top 10 conference papers ** http: //aseene. org/proceedings/2014/index. htm • Internet 2 Global Summit, April 6 -10, 2014, Denver, Colorado http: //meetings. internet 2. edu/2014 -global-summit/detail/10003109/ • C. De. Cusatis, “SDN, NFV, and the cloud disruption: the next generation open data center interoperable network (ODIN)”, Bright. Talk webinar, April 17, 2014 https: //www. brighttalk. com/search? q=De. Cusatis • C. De. Cusatis, R. Cannistra, T. Bundy, “Software Defined Environments and Next Generation Networks: a tutorial”, Proc. Keystone Initiative for Network Based Education and Research (KINBER) 2014 annual meeting (an Internet 2 affiliate), Harrisburg, PA, April 23 -25, 2014 • C. De. Cusatis and L. Miano, “Cloud computing and software defined environments”, Pace University college of computer science and engineering seminar series, April 30, 2014 • C. De. Cusatis and R. Cannistra, “Dynamic management and provisioning of software defined cloud data centers”, Proc. NSF Enterprise Computing Conference (ECC), paper SC 3101, June 8 -10, Marist College, Poughkeepsie, NY (2014) 66
School of Computer Science and Mathematics Recent Research Publications • C. De. Cusatis, J. Ziskin, T. Bundy, “The rise of SDN optical networks; has automated provisioning arrived? “, invited presentation, Pacific Telecom Conference, Honolulu, Hawaii (January 2014) • C. De. Cusatis, R. Cannistra, B. Carle, M. Johnson, J. Kapadia, Z. Meath, M. Miller, D. Young, T. Bundy , G. Zussman, K. Bergman, A. Carranza, C. Sher-De. Cusatis, A. Pletch, R. Ransom, “Dynamic orchestration test bed for SDN and NFV at the New York State Center for Cloud Computing & Analytics”, OFC 2014 annual meeting, San Francisco, CA (accepted & to be published, March 2014) • C. De. Cusatis et. al. , “Developing a software defined networking curriculum through industry partnership”, Proc. ASEE Annual Meeting, Hartford, CT (April 3 -5, 2014) ** named among top 10 conference papers ** http: //aseene. org/proceedings/2014/index. htm • Internet 2 Global Summit, April 6 -10, 2014, Denver, Colorado http: //meetings. internet 2. edu/2014 -global-summit/detail/10003109/ • C. De. Cusatis, “SDN, NFV, and the cloud disruption: the next generation open data center interoperable network (ODIN)”, Bright. Talk webinar, April 17, 2014 https: //www. brighttalk. com/search? q=De. Cusatis • C. De. Cusatis, R. Cannistra, T. Bundy, “Software Defined Environments and Next Generation Networks: a tutorial”, Proc. Keystone Initiative for Network Based Education and Research (KINBER) 2014 annual meeting (an Internet 2 affiliate), Harrisburg, PA, April 23 -25, 2014 • C. De. Cusatis and L. Miano, “Cloud computing and software defined environments”, Pace University college of computer science and engineering seminar series, April 30, 2014 • C. De. Cusatis and R. Cannistra, “Dynamic management and provisioning of software defined cloud data centers”, Proc. NSF Enterprise Computing Conference (ECC), paper SC 3101, June 8 -10, Marist College, Poughkeepsie, NY (2014) 66


