 Scanning Determining if the system is alive IP Scanning Port Scanning War Dialing
Scanning Determining if the system is alive IP Scanning Port Scanning War Dialing
 PING Sweeps • PING is used to send ICMP Echo type 8 packets to determined if a Type 0 reply is received indicating the system is alive. • Type 0 Echo Reply • Type 3 Destination unreachable • Type 4 Source Quench • Type 8 Echo • Type 11 Time exceeded • Type 13 Timestamp Reply • Type 15 Info Request • Type 16 Info Reply
PING Sweeps • PING is used to send ICMP Echo type 8 packets to determined if a Type 0 reply is received indicating the system is alive. • Type 0 Echo Reply • Type 3 Destination unreachable • Type 4 Source Quench • Type 8 Echo • Type 11 Time exceeded • Type 13 Timestamp Reply • Type 15 Info Request • Type 16 Info Reply
 FPING • Fping for unix systems, can read the contents of a file listing a range of IP addresses • Fping –a –f in. txt
FPING • Fping for unix systems, can read the contents of a file listing a range of IP addresses • Fping –a –f in. txt
 NMAP • NMAP –Sp 192. 168. 1. 0/24 www. insecure. org/nmap
NMAP • NMAP –Sp 192. 168. 1. 0/24 www. insecure. org/nmap
 Superscan for Windows • www. foundstone. com
Superscan for Windows • www. foundstone. com
 Port Scanning • Determining what services are running or listening by connecting to TCP and UDP ports
Port Scanning • Determining what services are running or listening by connecting to TCP and UDP ports
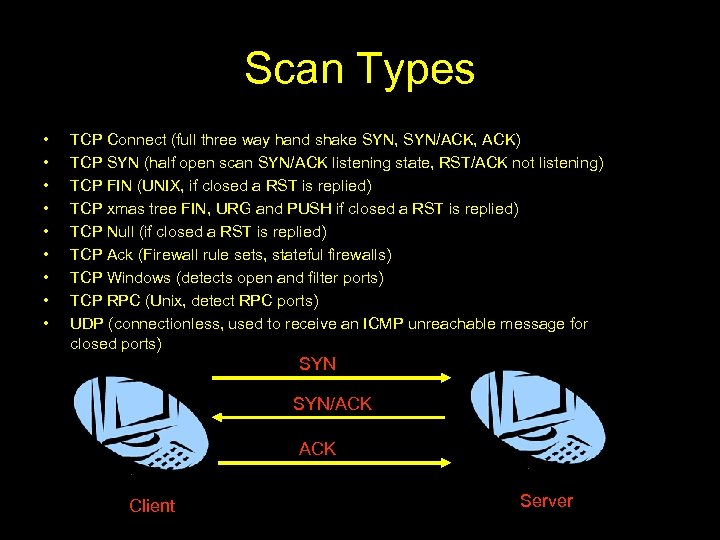 Scan Types • • • TCP Connect (full three way hand shake SYN, SYN/ACK, ACK) TCP SYN (half open scan SYN/ACK listening state, RST/ACK not listening) TCP FIN (UNIX, if closed a RST is replied) TCP xmas tree FIN, URG and PUSH if closed a RST is replied) TCP Null (if closed a RST is replied) TCP Ack (Firewall rule sets, stateful firewalls) TCP Windows (detects open and filter ports) TCP RPC (Unix, detect RPC ports) UDP (connectionless, used to receive an ICMP unreachable message for closed ports) SYN/ACK Client Server
Scan Types • • • TCP Connect (full three way hand shake SYN, SYN/ACK, ACK) TCP SYN (half open scan SYN/ACK listening state, RST/ACK not listening) TCP FIN (UNIX, if closed a RST is replied) TCP xmas tree FIN, URG and PUSH if closed a RST is replied) TCP Null (if closed a RST is replied) TCP Ack (Firewall rule sets, stateful firewalls) TCP Windows (detects open and filter ports) TCP RPC (Unix, detect RPC ports) UDP (connectionless, used to receive an ICMP unreachable message for closed ports) SYN/ACK Client Server
 Netcat • Nc –v –x –w 2 192. 168. 1. 1 1 -140
Netcat • Nc –v –x –w 2 192. 168. 1. 1 1 -140
 Nmap • Unix based • Nmap –Ss 192. 168. 1. 1
Nmap • Unix based • Nmap –Ss 192. 168. 1. 1
 Port Scanners Unix Strobe Tcp_scan Nmap Netcat Windows Netcat Superscan Winscan ip. Eye WUPS Scan. Line
Port Scanners Unix Strobe Tcp_scan Nmap Netcat Windows Netcat Superscan Winscan ip. Eye WUPS Scan. Line
 Banner Grabbing • Banner Grabbing is the act of connecting to a network available service or application • Ports 135, 139, 445: generally denotes a Windows system • Ports 512 -514: Unix ‘r’ commands
Banner Grabbing • Banner Grabbing is the act of connecting to a network available service or application • Ports 135, 139, 445: generally denotes a Windows system • Ports 512 -514: Unix ‘r’ commands
 Banner Grabbing • Nmap –O 192. 168. 1. 10 port state Protocol Service 21 Open tcp ftp We could also use packet filtering to grab information!
Banner Grabbing • Nmap –O 192. 168. 1. 10 port state Protocol Service 21 Open tcp ftp We could also use packet filtering to grab information!
 Banner Grabbing • Automated discovery tools give graphical displays of networks such as • Tkined, cheops and Scotty
Banner Grabbing • Automated discovery tools give graphical displays of networks such as • Tkined, cheops and Scotty
 War Dialing • Used to dial Telephone numbers searching for remote access/modem connections
War Dialing • Used to dial Telephone numbers searching for remote access/modem connections
 Countermeasures • Detect a potential attack early • Use an IDS such as www. snort. org or Genius at www. indiesoft. com • Filter ICMP traffic through Firewall • Use ACLs
Countermeasures • Detect a potential attack early • Use an IDS such as www. snort. org or Genius at www. indiesoft. com • Filter ICMP traffic through Firewall • Use ACLs
 Exercise • Download an IP scanner, port scanner and network IDS in groups of three perform scans, banner grabbing and NID
Exercise • Download an IP scanner, port scanner and network IDS in groups of three perform scans, banner grabbing and NID