64aef0b748702a1a64130927cb4e4212.ppt
- Количество слайдов: 25

SAP and Novell Collaborate on Comprehensive, Integrated Governance, Risk, and Compliance Solutions re ictu p or a slide f ple itle sam the t in

Agenda • Addressing today’s GRC challenges • Demo • Real-World Insights
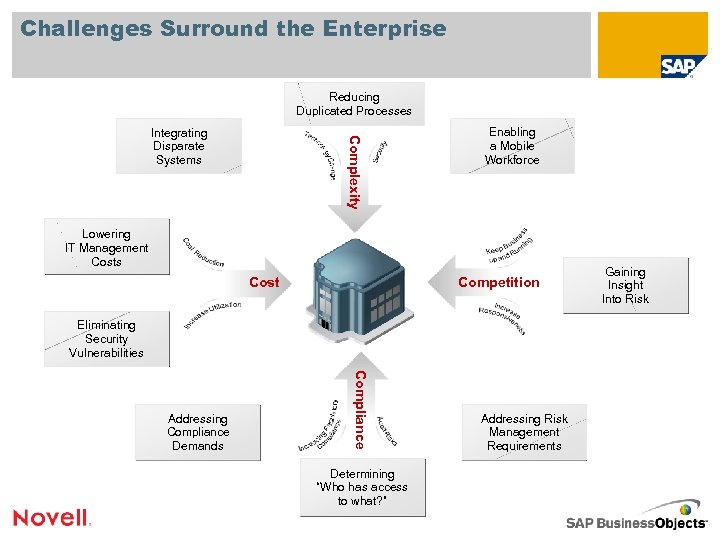
Challenges Surround the Enterprise Reducing Duplicated Processes Complexity Integrating Disparate Systems Enabling a Mobile Workforce Lowering IT Management Costs Competition Cost Eliminating Security Vulnerabilities Compliance Addressing Compliance Demands Determining “Who has access to what? ” Addressing Risk Management Requirements Gaining Insight Into Risk
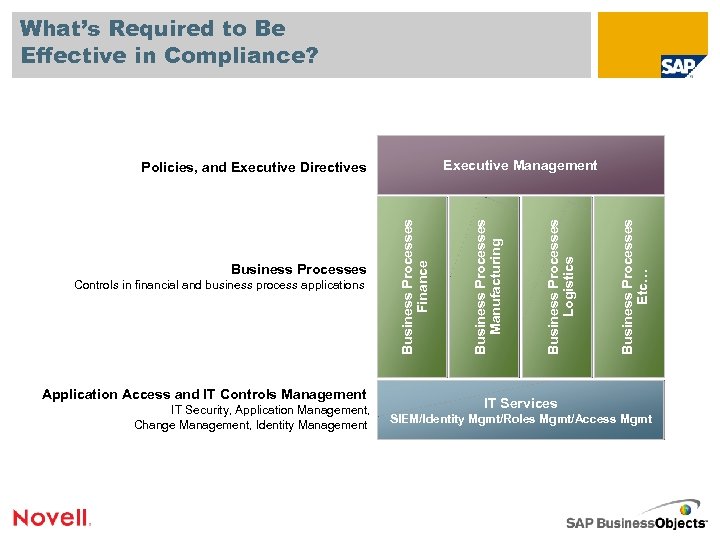
What’s Required to Be Effective in Compliance? Application Access and IT Controls Management IT Security, Application Management, Change Management, Identity Management Business Processes Etc… Business Processes Logistics Controls in financial and business process applications Business Processes Finance Business Processes Manufacturing Executive Management Policies, and Executive Directives IT Services SIEM/Identity Mgmt/Roles Mgmt/Access Mgmt
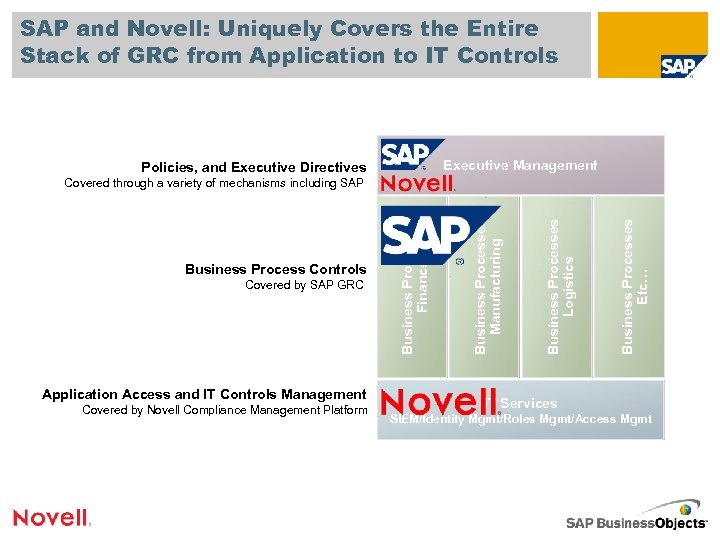
SAP and Novell: Uniquely Covers the Entire Stack of GRC from Application to IT Controls Executive Management Policies, and Executive Directives Application Access and IT Controls Management Covered by Novell Compliance Management Platform Business Processes Etc… Business Processes Logistics Covered by SAP GRC Business Processes Manufacturing Business Process Controls Business Processes Finance Covered through a variety of mechanisms including SAP IT Services SIEM/Identity Mgmt/Roles Mgmt/Access Mgmt
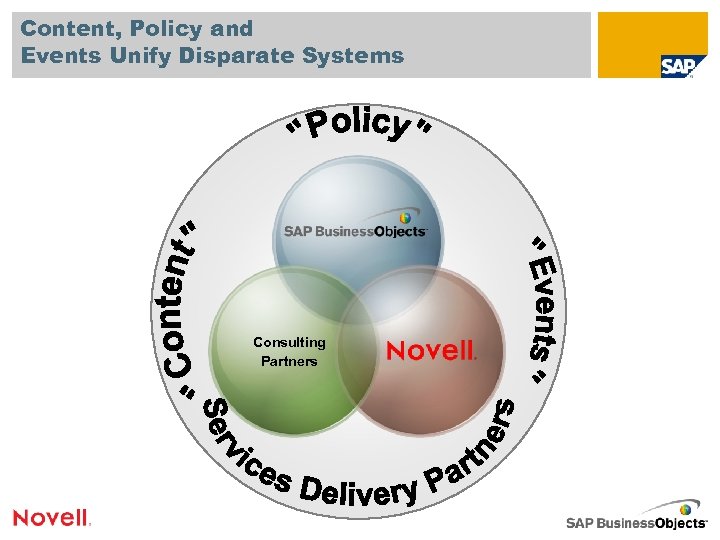
Content, Policy and Events Unify Disparate Systems Consulting Partners
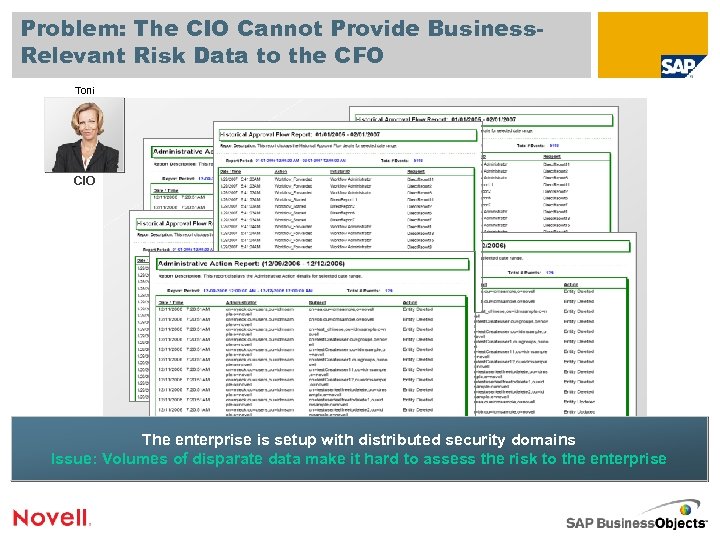
Problem: The CIO Cannot Provide Business. Relevant Risk Data to the CFO Toni CIO The enterprise is setup with distributed security domains Issue: Volumes of disparate data make it hard to assess the risk to the enterprise
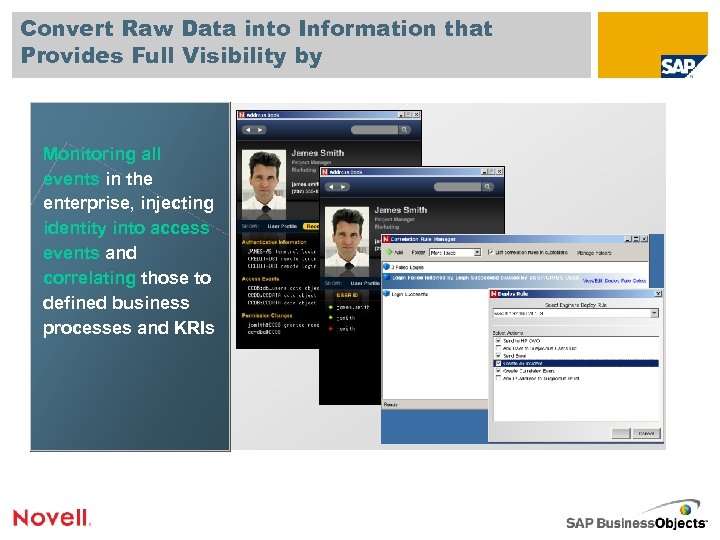
Convert Raw Data into Information that Provides Full Visibility by Monitoring all events in the enterprise, injecting identity into access events and correlating those to defined business processes and KRIs
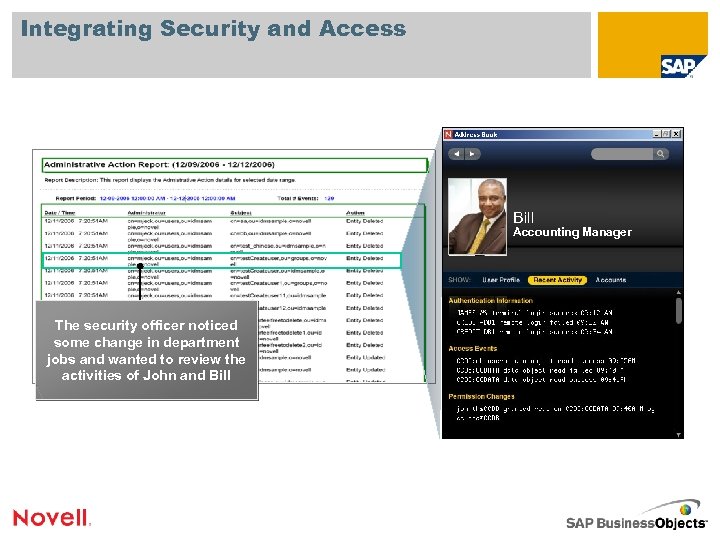
Integrating Security and Access Bill Accounting Manager The security officer noticed some change in department jobs and wanted to review the activities of John and Bill
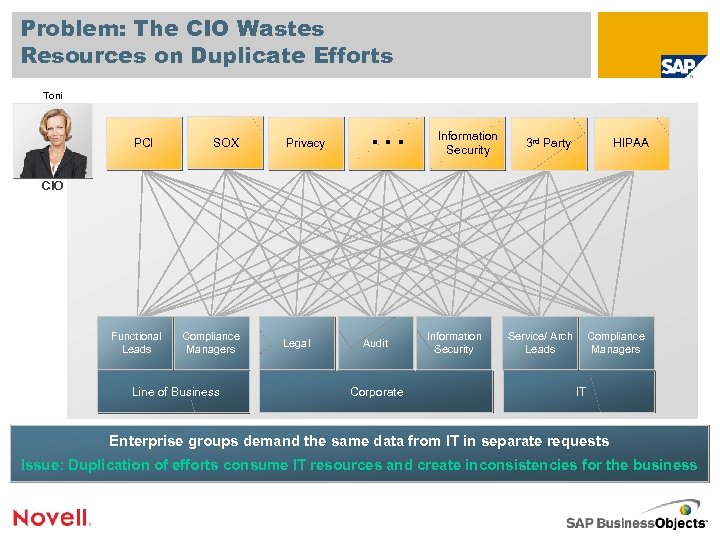
Problem: The CIO Wastes Resources on Duplicate Efforts Toni PCI SOX Privacy … Information Security 3 rd Party HIPAA CIO Functional Leads Compliance Managers Line of Business Legal Audit Corporate Information Security Service/ Arch Leads Compliance Managers IT Enterprise groups demand the same data from IT in separate requests Issue: Duplication of efforts consume IT resources and create inconsistencies for the business
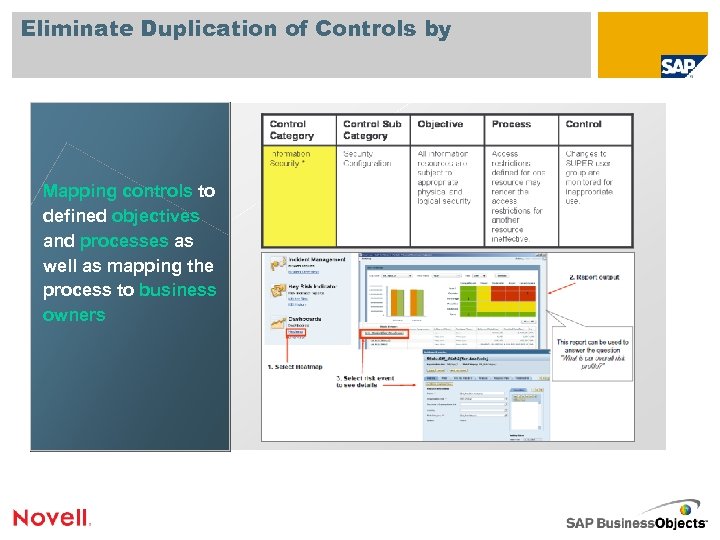
Eliminate Duplication of Controls by Mapping controls to defined objectives and processes as well as mapping the process to business owners
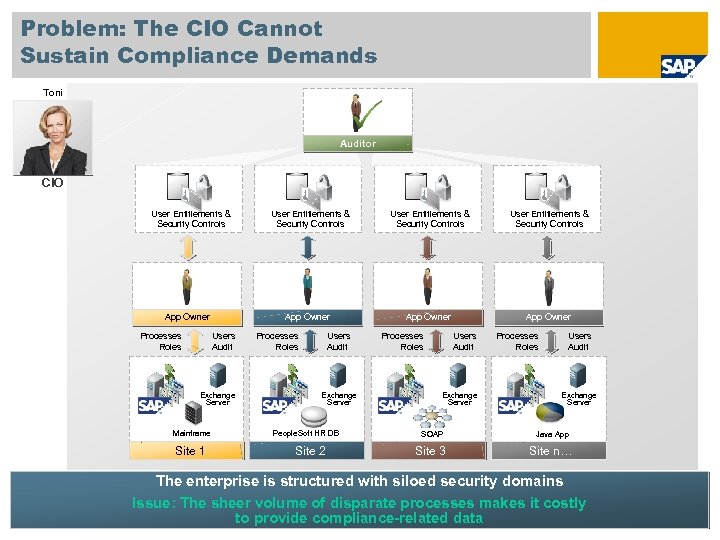
Problem: The CIO Cannot Sustain Compliance Demands Toni Auditor CIO User Entitlements & Security Controls Users Audit Processes Roles Exchange Server Mainframe Site 1 User Entitlements & Security Controls App Owner Users Audit Processes Roles Exchange Server People. Soft HR DB Site 2 Users Audit Processes Roles Exchange Server SOAP Java App Site 3 Site n… The enterprise is structured with siloed security domains Issue: The sheer volume of disparate processes makes it costly to provide compliance-related data
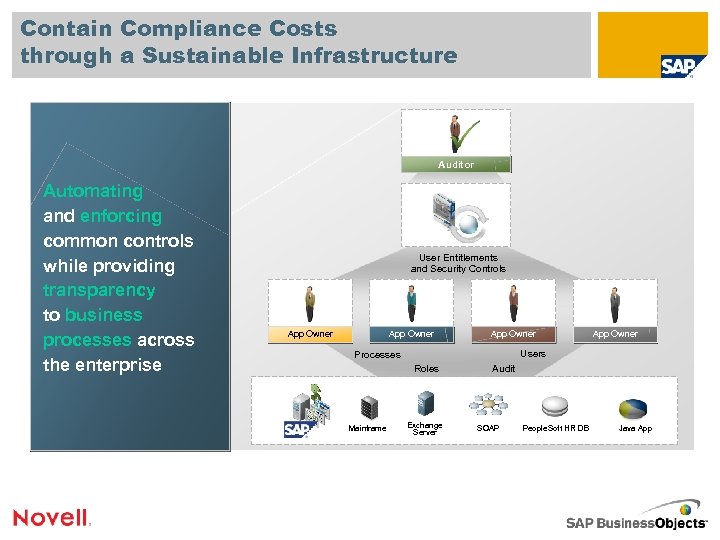
Contain Compliance Costs through a Sustainable Infrastructure Auditor Automating and enforcing common controls while providing transparency to business processes across the enterprise User Entitlements and Security Controls App Owner Users Processes Roles Mainframe App Owner Exchange Server Audit SOAP People. Soft HR DB Java App
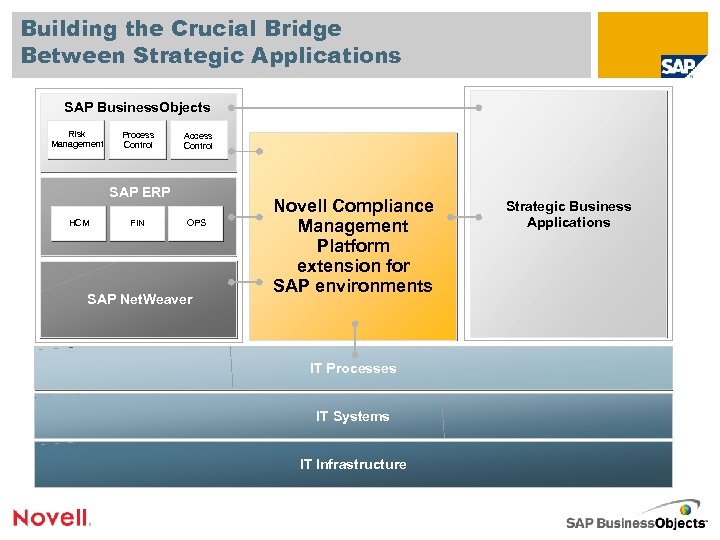
Building the Crucial Bridge Between Strategic Applications SAP Business. Objects Risk Management Process Control Access Control SAP ERP HCM FIN OPS SAP Net. Weaver Novell Compliance Management Platform extension for SAP environments IT Processes IT Systems IT Infrastructure Strategic Business Applications
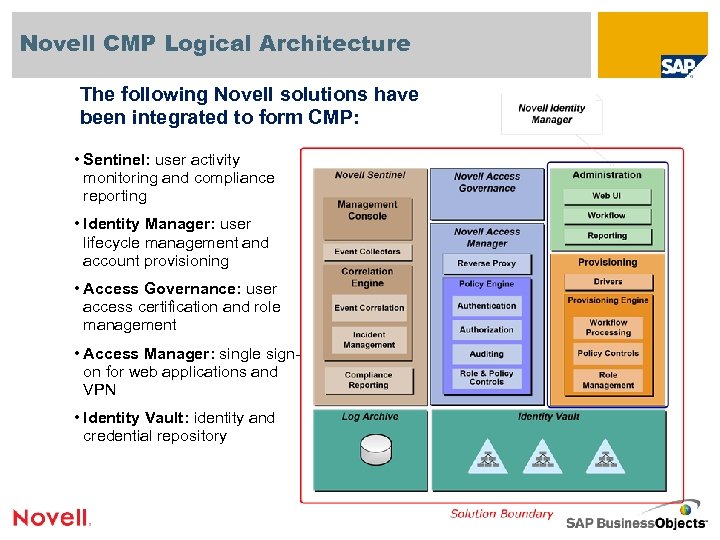
Novell CMP Logical Architecture The following Novell solutions have been integrated to form CMP: • Sentinel: user activity monitoring and compliance reporting • Identity Manager: user lifecycle management and account provisioning • Access Governance: user access certification and role management • Access Manager: single signon for web applications and VPN • Identity Vault: identity and credential repository
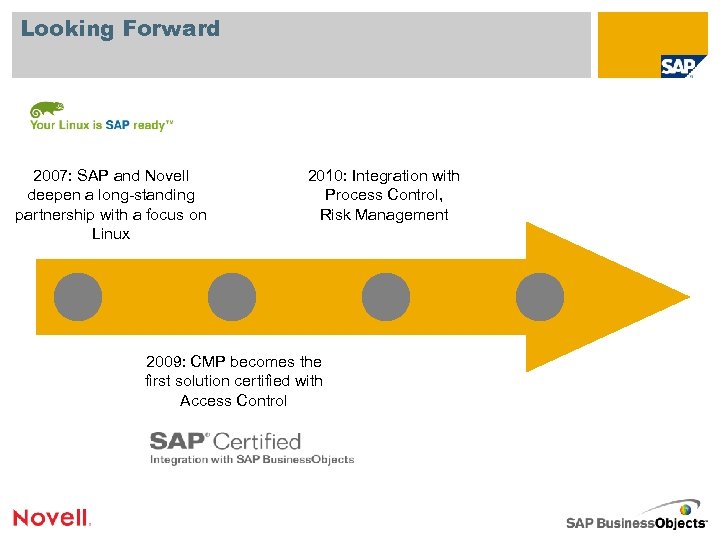
Looking Forward 2007: SAP and Novell deepen a long-standing partnership with a focus on Linux 2010: Integration with Process Control, Risk Management 2009: CMP becomes the first solution certified with Access Control

DEMO

Real-World Insights
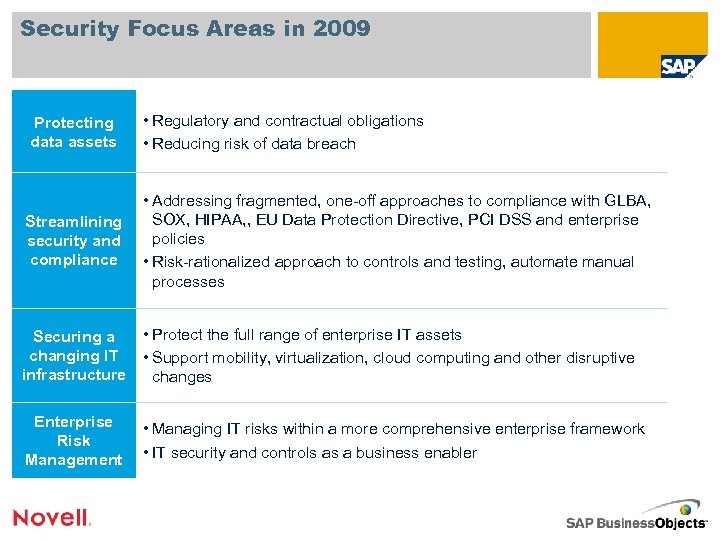
Security Focus Areas in 2009 Protecting data assets • Regulatory and contractual obligations • Reducing risk of data breach Streamlining security and compliance • Addressing fragmented, one-off approaches to compliance with GLBA, SOX, HIPAA, , EU Data Protection Directive, PCI DSS and enterprise policies • Risk-rationalized approach to controls and testing, automate manual processes Securing a changing IT infrastructure • Protect the full range of enterprise IT assets • Support mobility, virtualization, cloud computing and other disruptive changes Enterprise Risk Management • Managing IT risks within a more comprehensive enterprise framework • IT security and controls as a business enabler
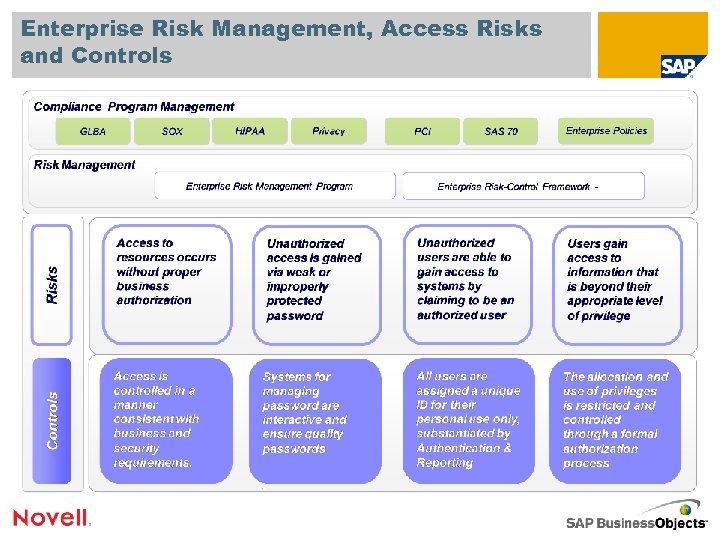
Enterprise Risk Management, Access Risks and Controls
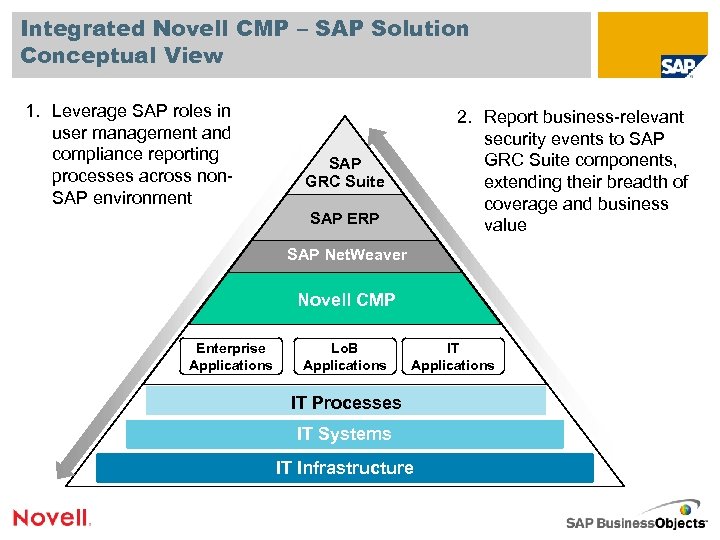
Integrated Novell CMP – SAP Solution Conceptual View 1. Leverage SAP roles in user management and compliance reporting processes across non. SAP environment 2. Report business-relevant security events to SAP GRC Suite components, extending their breadth of coverage and business value SAP GRC Suite SAP ERP SAP Net. Weaver Novell CMP Enterprise Applications Lo. B Applications IT Processes IT Systems IT Infrastructure
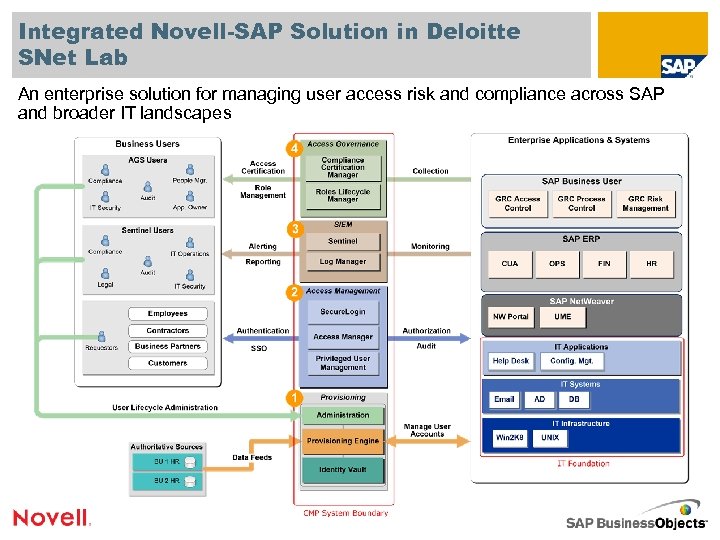
Integrated Novell-SAP Solution in Deloitte SNet Lab An enterprise solution for managing user access risk and compliance across SAP and broader IT landscapes
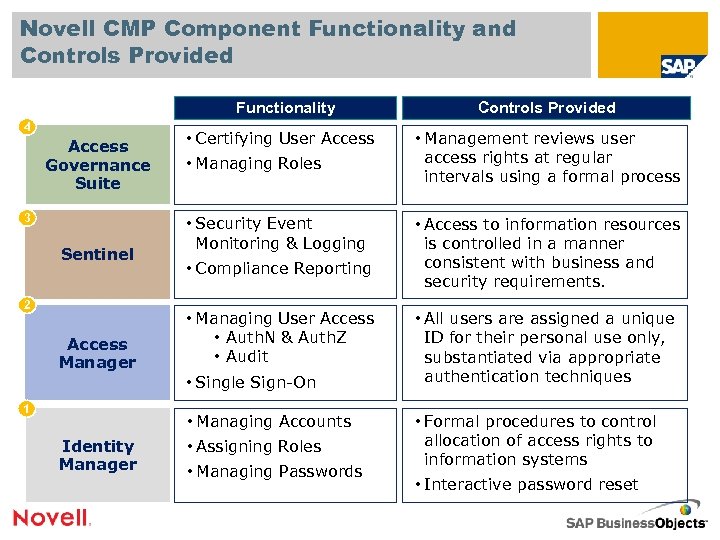
Novell CMP Component Functionality and Controls Provided Functionality 4 Access Governance Suite 3 Sentinel 2 Access Manager • Certifying User Access • Managing Roles • Security Event Monitoring & Logging • Compliance Reporting • Managing User Access • Auth. N & Auth. Z • Audit • Single Sign-On 1 • Managing Accounts Identity Manager • Assigning Roles • Managing Passwords Controls Provided • Management reviews user access rights at regular intervals using a formal process • Access to information resources is controlled in a manner consistent with business and security requirements. • All users are assigned a unique ID for their personal use only, substantiated via appropriate authentication techniques • Formal procedures to control allocation of access rights to information systems • Interactive password reset
© SAP 2008 / Page 25 Geoffrey Coulehan, SAP Market Development Questions?

Contact Information • Jay Roxe (jroxe@novell. com) • Rick Wagner (rwagner@novell. com) • Ranga Bodla (ranga. bodla@sap. com) • Eli Fisk (efisk@deloitte. com)
64aef0b748702a1a64130927cb4e4212.ppt