b38edc7ed61f7b693a7a0f0b24d98223.ppt
- Количество слайдов: 20
 Sania: Syntactic and Semantic Analysis for Automated Testing against SQL Injection Yuji Kosuga, Kenji Kono, Miyuki Hanaoka Keio University Miho Hishiyama, Yu Takahama IX Knowledge Inc. 2007 Annual Computer Security Applications Conference (ACSAC) 1
Sania: Syntactic and Semantic Analysis for Automated Testing against SQL Injection Yuji Kosuga, Kenji Kono, Miyuki Hanaoka Keio University Miho Hishiyama, Yu Takahama IX Knowledge Inc. 2007 Annual Computer Security Applications Conference (ACSAC) 1
 OUTLINE 1. 2. 3. 4. 5. 6. Introduction Related Work Design of Sania Implementation Experiments Conclusion 2
OUTLINE 1. 2. 3. 4. 5. 6. Introduction Related Work Design of Sania Implementation Experiments Conclusion 2
 1. Introduction Databases are threatened by SQL injection attacks. Sanitizing SELECT * FROM users WHERE name = 'xxx' AND password = '' or "1"="1' '" '1'='1' Discovering SQL injection vulnerabilities are based on a penetration testing. 3
1. Introduction Databases are threatened by SQL injection attacks. Sanitizing SELECT * FROM users WHERE name = 'xxx' AND password = '' or "1"="1' '" '1'='1' Discovering SQL injection vulnerabilities are based on a penetration testing. 3
 1. Introduction (cont. ) Sania Automatically identifies potentially vulnerable spots in the SQL queries. ³ Generates attack requests. ³ Comparing the parse trees of the SQL queries between innocent HTTP request and attack request. ³ 4
1. Introduction (cont. ) Sania Automatically identifies potentially vulnerable spots in the SQL queries. ³ Generates attack requests. ³ Comparing the parse trees of the SQL queries between innocent HTTP request and attack request. ³ 4
 2. Related Work Framework Support A validator prohibits an input from including meta-characters. ³ To transform the dangerous characters to safe ones. ³ 5
2. Related Work Framework Support A validator prohibits an input from including meta-characters. ³ To transform the dangerous characters to safe ones. ³ 5
 2. Related Work (cont. ) Prepare Statement ³ separates the values in a query from the structure of SQL Prepared. Statement stmt = conn. prepare. Statement( "INSERT INTO message VALUES(? , ? )"); stmt. set. String(1, “razor"); stmt. set. String(2, “razor@mail. com"); stmt. execute. Update(); stmt. clear. Parameters(); ³ All the legacy web applications must be rewritten. 6
2. Related Work (cont. ) Prepare Statement ³ separates the values in a query from the structure of SQL Prepared. Statement stmt = conn. prepare. Statement( "INSERT INTO message VALUES(? , ? )"); stmt. set. String(1, “razor"); stmt. set. String(2, “razor@mail. com"); stmt. execute. Update(); stmt. clear. Parameters(); ³ All the legacy web applications must be rewritten. 6
 2. Related Work (cont. ) Combined Static and Dynamic Analysis Uses a static analysis to build the models of the SQL queries. ³ Intercepts all the SQL queries before they are sent to the database. ³ Checks each query against the statically built models. ³ 7
2. Related Work (cont. ) Combined Static and Dynamic Analysis Uses a static analysis to build the models of the SQL queries. ³ Intercepts all the SQL queries before they are sent to the database. ³ Checks each query against the statically built models. ³ 7
 2. Related Work (cont. ) Machine Learning Approach An intrusion detection system (IDS) based on a machine learning technique. ³ The overall IDS quality depends on the quality of the training set. ³ It cannot thoroughly check all the vulnerable spots like the traditional penetration testing. ³ 8
2. Related Work (cont. ) Machine Learning Approach An intrusion detection system (IDS) based on a machine learning technique. ³ The overall IDS quality depends on the quality of the training set. ³ It cannot thoroughly check all the vulnerable spots like the traditional penetration testing. ³ 8
 2. Related Work (cont. ) Instruction-Set Randomization ³ To create SQL queries using randomized keywords instead of the normal SQL keywords. 9
2. Related Work (cont. ) Instruction-Set Randomization ³ To create SQL queries using randomized keywords instead of the normal SQL keywords. 9
 3. Design of Sania Specifying Vulnerable Spots The vulnerable spots have the potential to be security holes of SQL injection. HTTP request includes id=555&cat=book ³ Generated SQL query SELECT * FROM users WHERE user id=555 10
3. Design of Sania Specifying Vulnerable Spots The vulnerable spots have the potential to be security holes of SQL injection. HTTP request includes id=555&cat=book ³ Generated SQL query SELECT * FROM users WHERE user id=555 10
 3. Design of Sania (cont. ) Crafting Attack Requests ³ Linear attack ® ³ Sania inserts an attack code to a single vulnerable spot. Combination attack ® Sania inserts attack codes in two or more vulnerable spots at the same time. 11
3. Design of Sania (cont. ) Crafting Attack Requests ³ Linear attack ® ³ Sania inserts an attack code to a single vulnerable spot. Combination attack ® Sania inserts attack codes in two or more vulnerable spots at the same time. 11
 3. Design of Sania (cont. ) Linear attack ³ Each attack code represented as a four-element tuple: (user. Input, meta. Character, parentheses, inserted. SQL). (λ | ε, ’ | ", true, or ’ 1’=’ 1 | or "1"="1 | or 1=1 -- | or 1=1; -- | or 1=1/*). SELECT id, xxx from users (λ, ε, false, from yyy-- | from yyy; -- | from yyy/*). ³ SELECT id, xxx from yyy--from users ³ 12
3. Design of Sania (cont. ) Linear attack ³ Each attack code represented as a four-element tuple: (user. Input, meta. Character, parentheses, inserted. SQL). (λ | ε, ’ | ", true, or ’ 1’=’ 1 | or "1"="1 | or 1=1 -- | or 1=1; -- | or 1=1/*). SELECT id, xxx from users (λ, ε, false, from yyy-- | from yyy; -- | from yyy/*). ³ SELECT id, xxx from yyy--from users ³ 12
 3. Design of Sania (cont. ) Combination Attack A combination attack exploits two or more vulnerable spots at the same time to inject an SQL query. ³ SELECT * FROM users WHERE name=’ø 1’ and password=’ø 2’ (øi: vulnerable spot). ³ SELECT * FROM users WHERE name=’’ and password=’ or 1=1 --’ ³ 13
3. Design of Sania (cont. ) Combination Attack A combination attack exploits two or more vulnerable spots at the same time to inject an SQL query. ³ SELECT * FROM users WHERE name=’ø 1’ and password=’ø 2’ (øi: vulnerable spot). ³ SELECT * FROM users WHERE name=’’ and password=’ or 1=1 --’ ³ 13
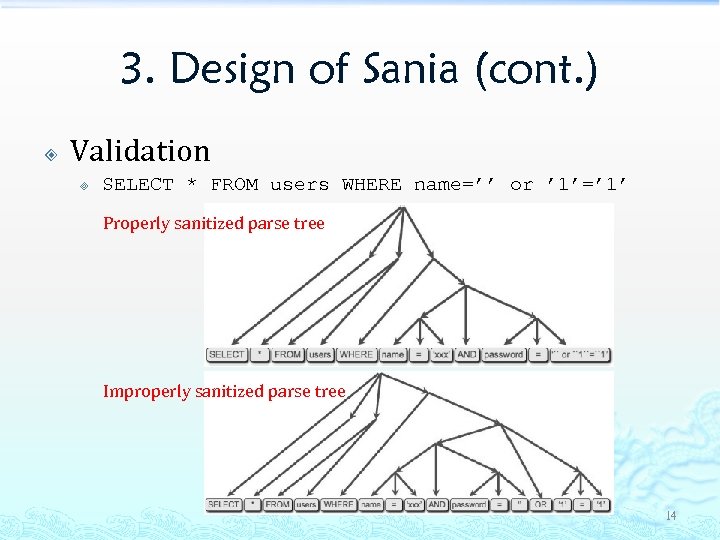 3. Design of Sania (cont. ) Validation ³ SELECT * FROM users WHERE name=’’ or ’ 1’=’ 1’ Properly sanitized parse tree Improperly sanitized parse tree 14
3. Design of Sania (cont. ) Validation ³ SELECT * FROM users WHERE name=’’ or ’ 1’=’ 1’ Properly sanitized parse tree Improperly sanitized parse tree 14
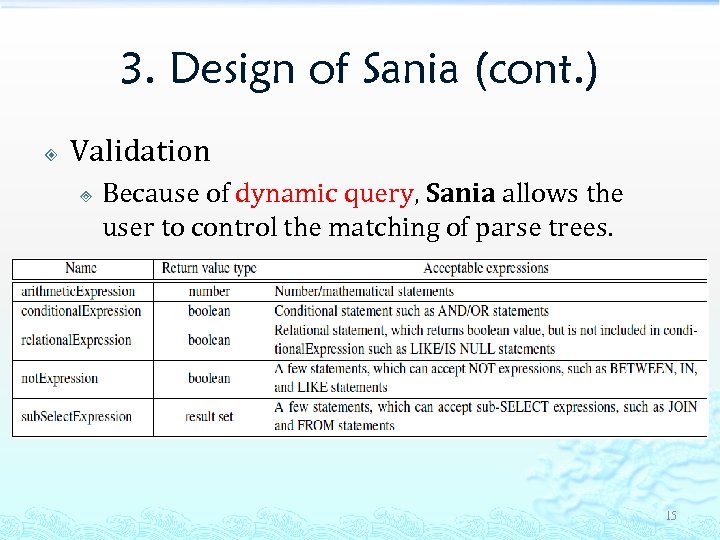 3. Design of Sania (cont. ) Validation ³ Because of dynamic query, Sania allows the user to control the matching of parse trees. 15
3. Design of Sania (cont. ) Validation ³ Because of dynamic query, Sania allows the user to control the matching of parse trees. 15
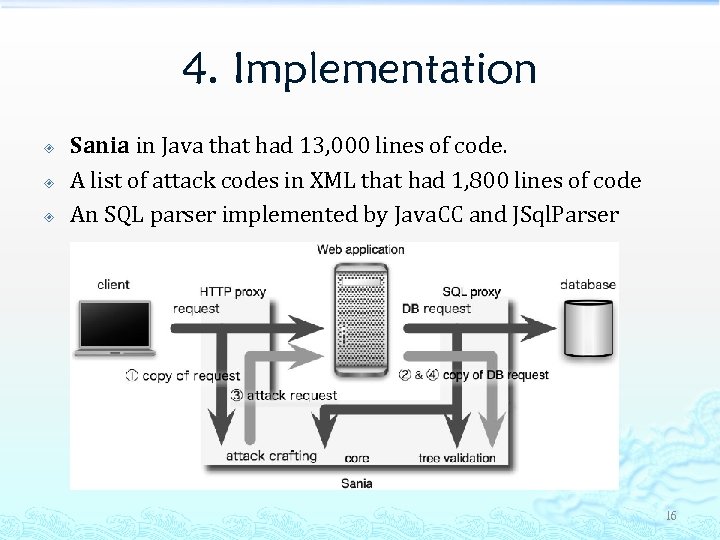 4. Implementation Sania in Java that had 13, 000 lines of code. A list of attack codes in XML that had 1, 800 lines of code An SQL parser implemented by Java. CC and JSql. Parser 16
4. Implementation Sania in Java that had 13, 000 lines of code. A list of attack codes in XML that had 1, 800 lines of code An SQL parser implemented by Java. CC and JSql. Parser 16
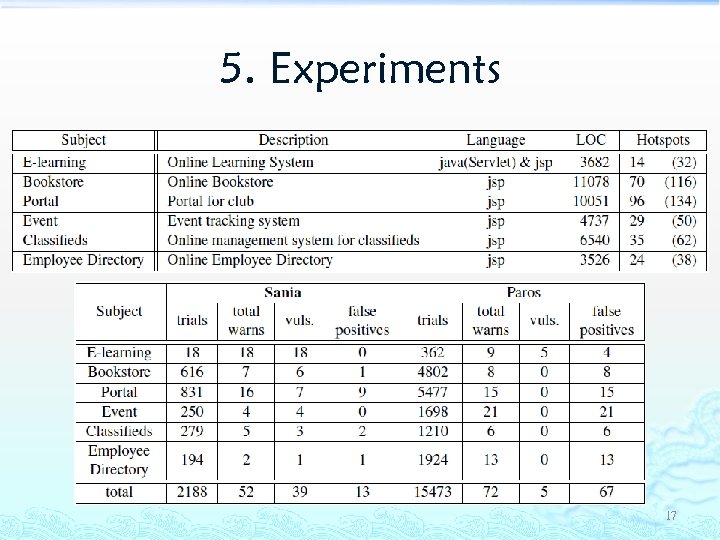 5. Experiments 17
5. Experiments 17
 5. Experiments (cont. ) This result reveals that Sania can: Execute precise linear attacks. ³ Execute powerful combination attacks. ³ 18
5. Experiments (cont. ) This result reveals that Sania can: Execute precise linear attacks. ³ Execute powerful combination attacks. ³ 18
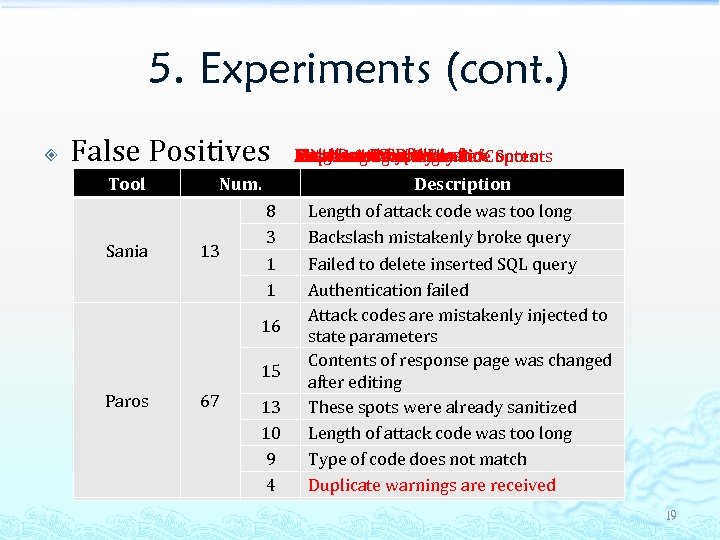 5. Experiments (cont. ) False Positives Tool Sania Num. 13 8 3 1 1 16 15 Paros 67 13 10 9 4 Database Record Error Contents Misallocated of Dynamic Length and. Conflict Safe Spots Field Data. Warnings Attacking Potentially Mishandling Backslash Duplicate Type Conflict Description Length of attack code was too long Backslash mistakenly broke query Failed to delete inserted SQL query Authentication failed Attack codes are mistakenly injected to state parameters Contents of response page was changed after editing These spots were already sanitized Length of attack code was too long Type of code does not match Duplicate warnings are received 19
5. Experiments (cont. ) False Positives Tool Sania Num. 13 8 3 1 1 16 15 Paros 67 13 10 9 4 Database Record Error Contents Misallocated of Dynamic Length and. Conflict Safe Spots Field Data. Warnings Attacking Potentially Mishandling Backslash Duplicate Type Conflict Description Length of attack code was too long Backslash mistakenly broke query Failed to delete inserted SQL query Authentication failed Attack codes are mistakenly injected to state parameters Contents of response page was changed after editing These spots were already sanitized Length of attack code was too long Type of code does not match Duplicate warnings are received 19
 6. Conclusion Sania, which is designed to check for SQL injection vulnerabilities in the development and debugging phases. Sania has been proved effective; it found 39 SQL injection vulnerabilities and incurred only 13 false positives. 20
6. Conclusion Sania, which is designed to check for SQL injection vulnerabilities in the development and debugging phases. Sania has been proved effective; it found 39 SQL injection vulnerabilities and incurred only 13 false positives. 20


