f3639b25d43cf4ed2535740c59b69b69.ppt
- Количество слайдов: 29

Safeguarding Enterprise Data with Continuous, Real-Time Database Security, Monitoring & Compliance Fakhreddine El Mourabiti – Data Governance / Europe fmourabiti@be. ibm. com 1 © 2012 IBM Corporation

IBM Security Systems You know? you can do this online now. © 2012 IBM Corporation 2 CONFIDENTIAL © 2012 IBM Corporation
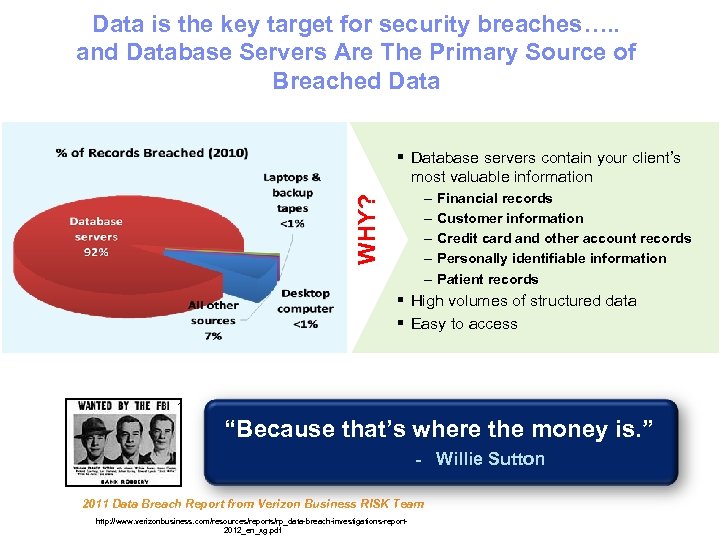
Data is the key target for security breaches…. . and Database Servers Are The Primary Source of Breached Data § Database servers contain your client’s most valuable information WHY? – – – Financial records Customer information Credit card and other account records Personally identifiable information Patient records § High volumes of structured data § Easy to access “Because that’s where the money is. ” - Willie Sutton 2011 Data Breach Report from Verizon Business RISK Team http: //www. verizonbusiness. com/resources/reports/rp_data-breach-investigations-report 2012_en_xg. pdf

The Goals Continuously monitor access to sensitive data in databases, data warehouses, Hadoop big data environments and file shares to: 1 Prevent data breaches – Mitigate external and internal threats 2 Ensure the integrity of sensitive data – Prevent unauthorized changes to data, data infrastructure, configuration files and logs 3 Reduce cost of compliance - Automate and centralize controls • Across heterogeneous environments such as databases, applications, data warehouses and Big Data platforms like Hadoop • Across diverse regulations, such as PCI DSS, data privacy regulations, HIPAA/HITECH etc. Simplify the audit review processes - Simplify audit review processes 4 CONFIDENTIAL © 2012 IBM Corporation
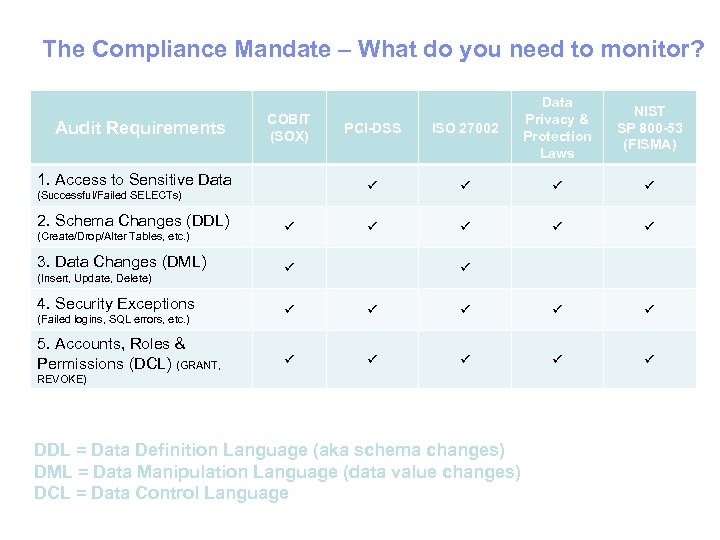
The Compliance Mandate – What do you need to monitor? Audit Requirements 1. Access to Sensitive Data (Successful/Failed SELECTs) 2. Schema Changes (DDL) (Create/Drop/Alter Tables, etc. ) 3. Data Changes (DML) (Insert, Update, Delete) 4. Security Exceptions (Failed logins, SQL errors, etc. ) 5. Accounts, Roles & Permissions (DCL) (GRANT, PCI-DSS ISO 27002 COBIT (SOX) Data Privacy & Protection Laws NIST SP 800 -53 (FISMA) REVOKE) DDL = Data Definition Language (aka schema changes) DML = Data Manipulation Language (data value changes) DCL = Data Control Language
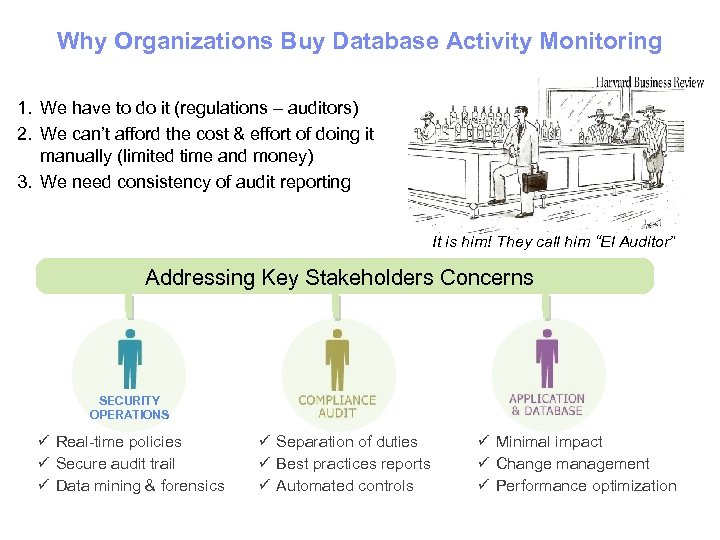
Why Organizations Buy Database Activity Monitoring 1. We have to do it (regulations – auditors) 2. We can’t afford the cost & effort of doing it manually (limited time and money) 3. We need consistency of audit reporting It is him! They call him “El Auditor” Addressing Key Stakeholders Concerns SECURITY OPERATIONS Real-time policies Secure audit trail Data mining & forensics Separation of duties Best practices reports Automated controls Minimal impact Change management Performance optimization
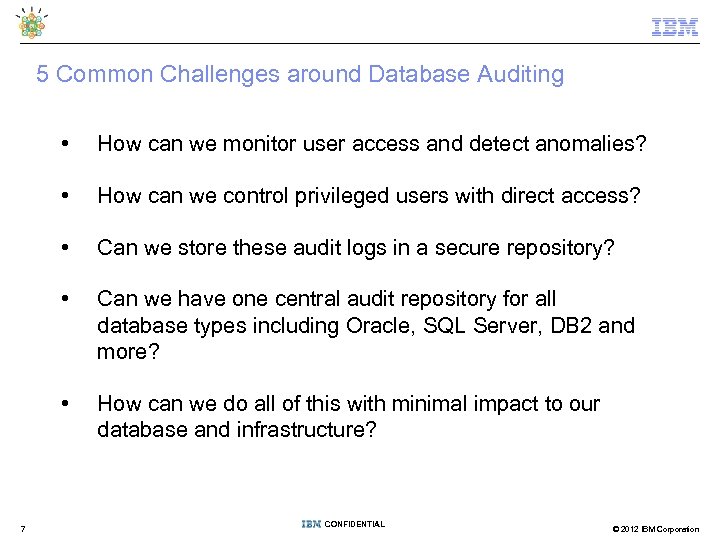
5 Common Challenges around Database Auditing • • How can we control privileged users with direct access? • Can we store these audit logs in a secure repository? • Can we have one central audit repository for all database types including Oracle, SQL Server, DB 2 and more? • 7 How can we monitor user access and detect anomalies? How can we do all of this with minimal impact to our database and infrastructure? CONFIDENTIAL © 2012 IBM Corporation
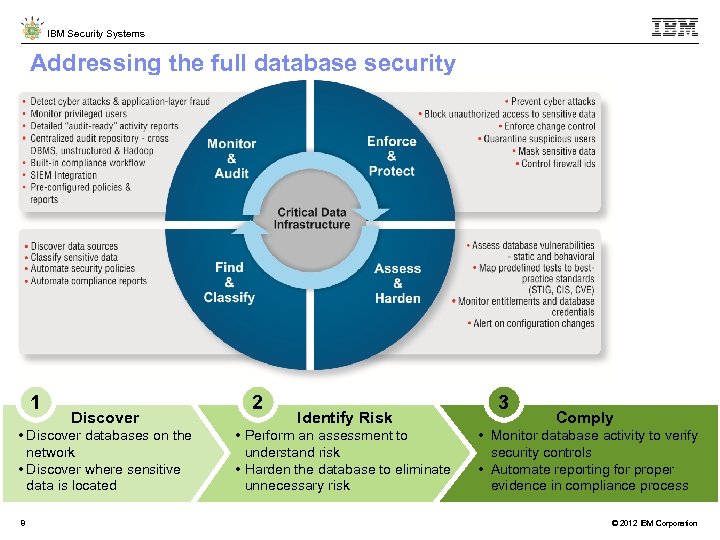
IBM Security Systems Addressing the full database security lifecycle 1 Discover • Discover databases on the network • Discover where sensitive data is located 8 2 Identify Risk • Perform an assessment to understand risk • Harden the database to eliminate unnecessary risk 3 Comply • Monitor database activity to verify security controls • Automate reporting for proper evidence in compliance process © 2012 IBM Corporation
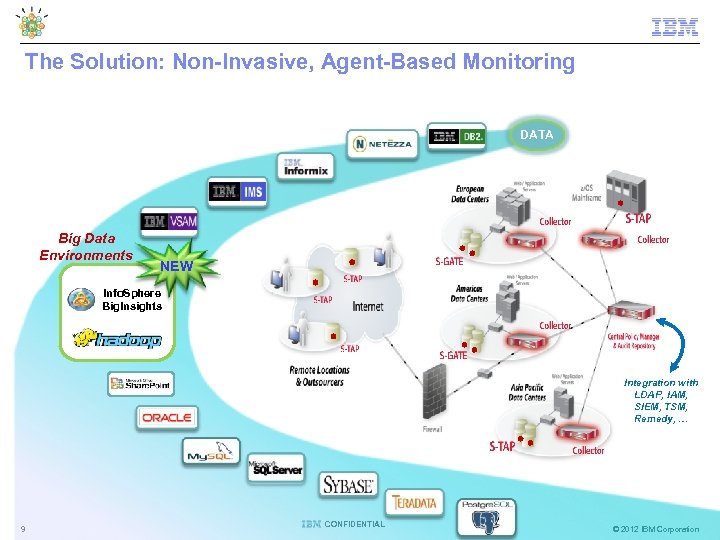
The Solution: Non-Invasive, Agent-Based Monitoring DATA Big Data Environments NEW Info. Sphere Big. Insights Integration with LDAP, IAM, SIEM, TSM, Remedy, … 9 CONFIDENTIAL © 2012 IBM Corporation
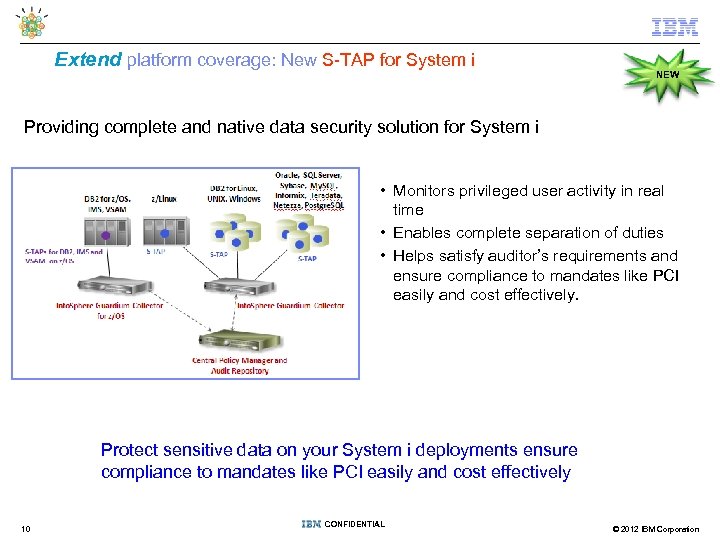
Extend platform coverage: New S-TAP for System i NEW Providing complete and native data security solution for System i • Monitors privileged user activity in real time • Enables complete separation of duties • Helps satisfy auditor’s requirements and ensure compliance to mandates like PCI easily and cost effectively. Protect sensitive data on your System i deployments ensure compliance to mandates like PCI easily and cost effectively 10 CONFIDENTIAL © 2012 IBM Corporation
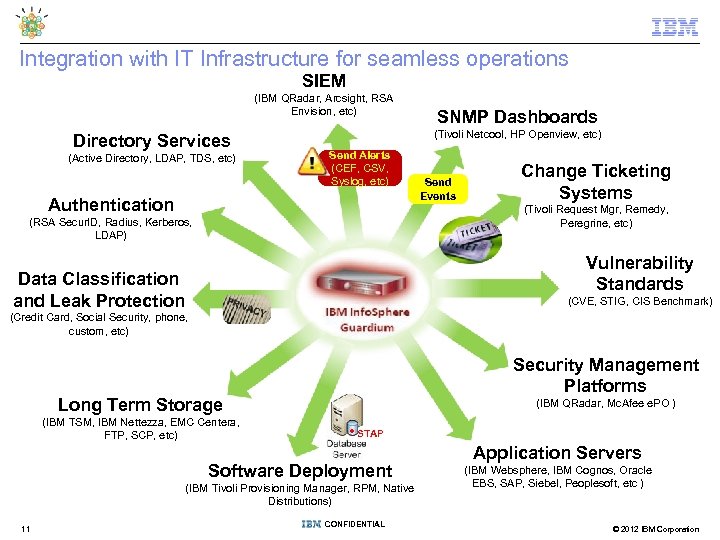
Integration with IT Infrastructure for seamless operations SIEM (IBM QRadar, Arcsight, RSA Envision, etc) Directory Services (Active Directory, LDAP, TDS, etc) SNMP Dashboards (Tivoli Netcool, HP Openview, etc) Send Alerts (CEF, CSV, Syslog, etc) Authentication Send Events Change Ticketing Systems (Tivoli Request Mgr, Remedy, Peregrine, etc) (RSA Secur. ID, Radius, Kerberos, LDAP) Vulnerability Standards Data Classification and Leak Protection (CVE, STIG, CIS Benchmark) (Credit Card, Social Security, phone, custom, etc) Security Management Platforms Long Term Storage (IBM TSM, IBM Nettezza, EMC Centera, FTP, SCP, etc) (IBM QRadar, Mc. Afee e. PO ) • STAP Software Deployment (IBM Tivoli Provisioning Manager, RPM, Native Distributions) 11 CONFIDENTIAL Application Servers (IBM Websphere, IBM Cognos, Oracle EBS, SAP, Siebel, Peoplesoft, etc ) © 2012 IBM Corporation
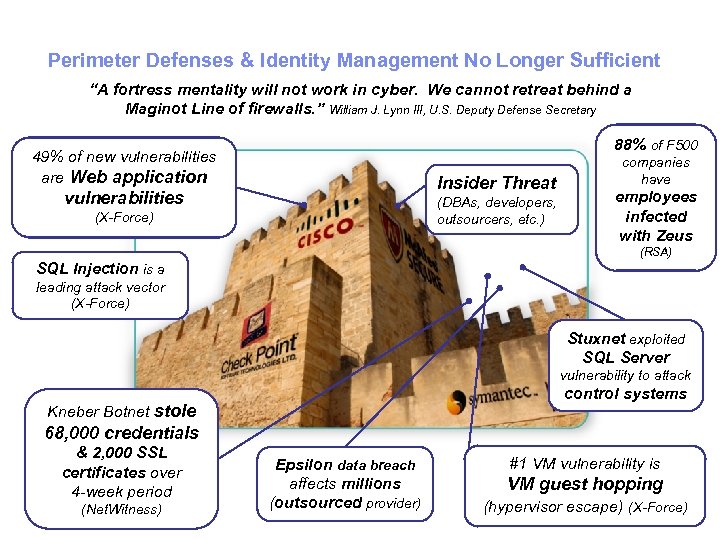
Perimeter Defenses & Identity Management No Longer Sufficient “A fortress mentality will not work in cyber. We cannot retreat behind a Maginot Line of firewalls. ” William J. Lynn III, U. S. Deputy Defense Secretary 88% of F 500 49% of new vulnerabilities are Web application Insider Threat vulnerabilities (DBAs, developers, outsourcers, etc. ) (X-Force) companies have employees infected with Zeus (RSA) SQL Injection is a leading attack vector (X-Force) Stuxnet exploited SQL Server vulnerability to attack control systems Kneber Botnet stole 68, 000 credentials & 2, 000 SSL certificates over 4 -week period (Net. Witness) Epsilon data breach affects millions (outsourced provider) #1 VM vulnerability is VM guest hopping (hypervisor escape) (X-Force)
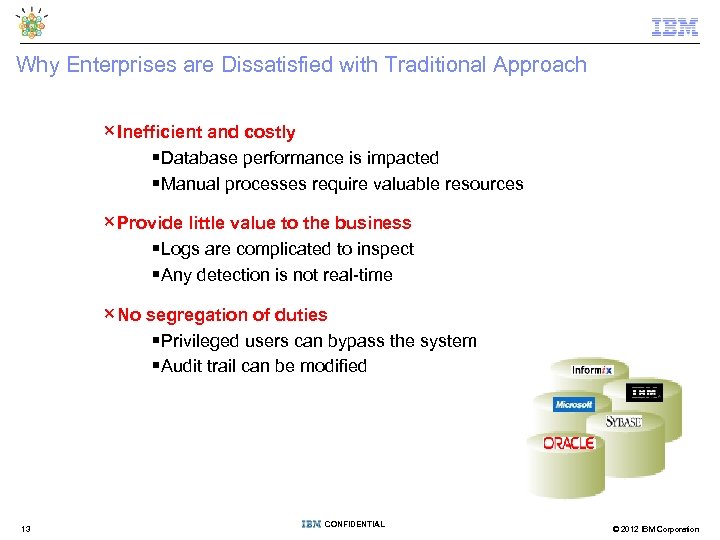
Why Enterprises are Dissatisfied with Traditional Approach ×Inefficient and costly §Database performance is impacted §Manual processes require valuable resources ×Provide little value to the business §Logs are complicated to inspect §Any detection is not real-time ×No segregation of duties §Privileged users can bypass the system §Audit trail can be modified 13 CONFIDENTIAL © 2012 IBM Corporation
Secure Settings Activity Monitoring M DA Observation Towers / Turret VA E AT SG Arrow Loop Walls Moat E AT SG Gate Guards 14 CONFIDENTIAL © 2012 IBM Corporation
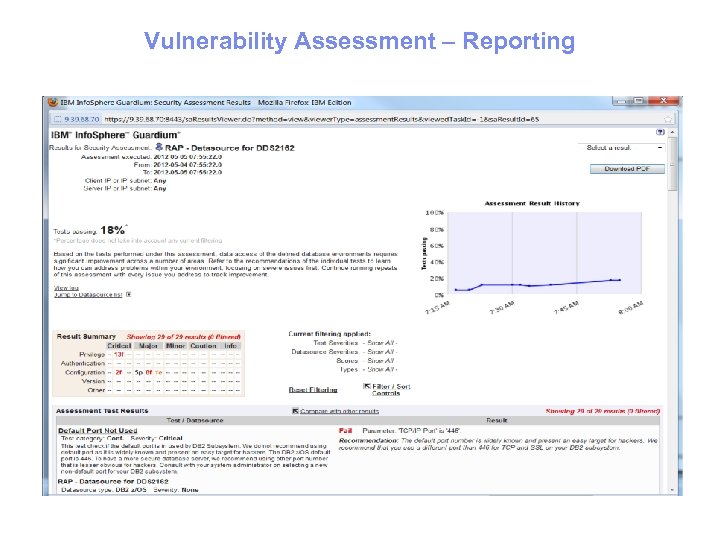
Vulnerability Assessment – Reporting 15
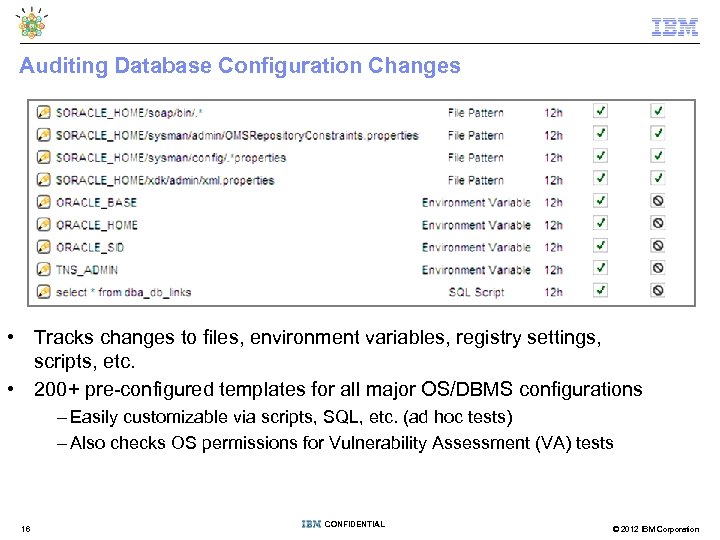
Auditing Database Configuration Changes • Tracks changes to files, environment variables, registry settings, scripts, etc. • 200+ pre-configured templates for all major OS/DBMS configurations – Easily customizable via scripts, SQL, etc. (ad hoc tests) – Also checks OS permissions for Vulnerability Assessment (VA) tests 16 CONFIDENTIAL © 2012 IBM Corporation
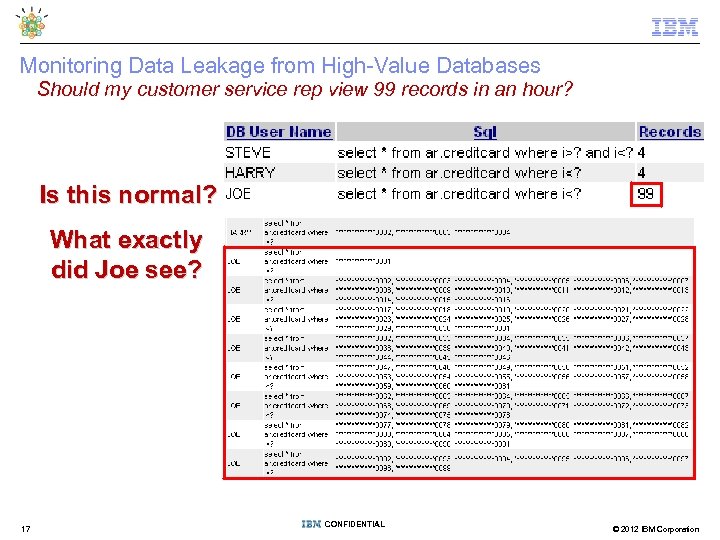
Monitoring Data Leakage from High-Value Databases Should my customer service rep view 99 records in an hour? Is this normal? What exactly did Joe see? 17 CONFIDENTIAL © 2012 IBM Corporation
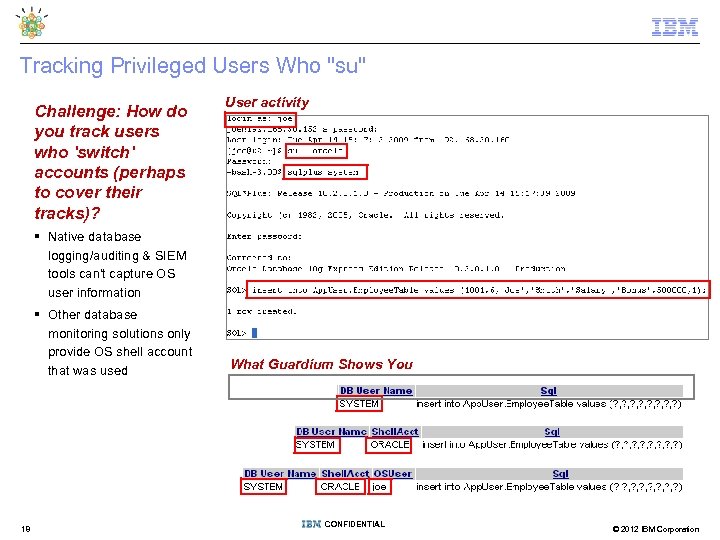
Tracking Privileged Users Who "su" Challenge: How do you track users who 'switch' accounts (perhaps to cover their tracks)? User activity § Native database logging/auditing & SIEM tools can't capture OS user information § Other database monitoring solutions only provide OS shell account that was used 18 What Guardium Shows You CONFIDENTIAL © 2012 IBM Corporation
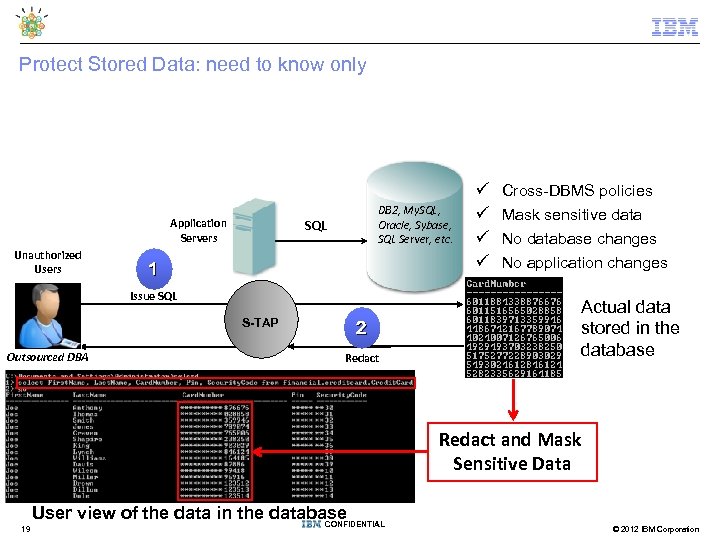
Protect Stored Data: need to know only Application Servers Unauthorized Users DB 2, My. SQL, Oracle, Sybase, SQL Server, etc. SQL 1 Issue SQL S-TAP Outsourced DBA 2 Redact Cross-DBMS policies Mask sensitive data No database changes No application changes Actual data stored in the database Redact and Mask Sensitive Data 19 User view of the data in the database CONFIDENTIAL © 2012 IBM Corporation
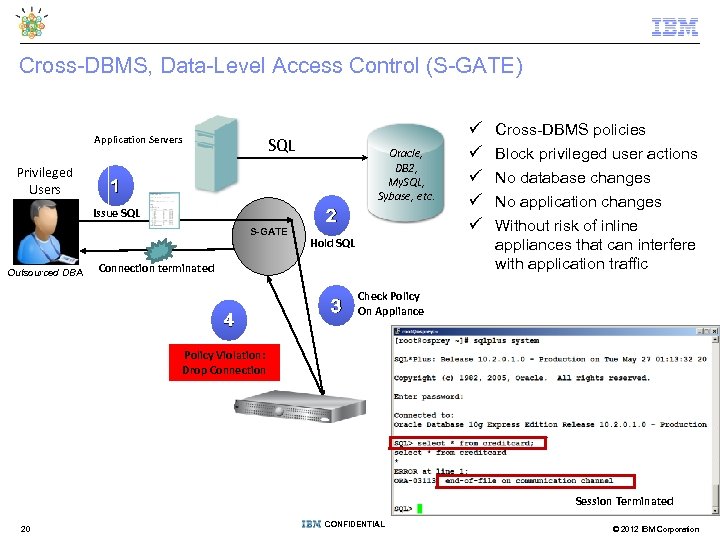
Cross-DBMS, Data-Level Access Control (S-GATE) Application Servers Privileged Users SQL 1 Issue SQL S-GATE Outsourced DBA Oracle, DB 2, My. SQL, Sybase, etc. 2 Hold SQL Connection terminated 4 3 Cross-DBMS policies Block privileged user actions No database changes No application changes Without risk of inline appliances that can interfere with application traffic Check Policy On Appliance Policy Violation: Drop Connection Session Terminated 20 CONFIDENTIAL © 2012 IBM Corporation
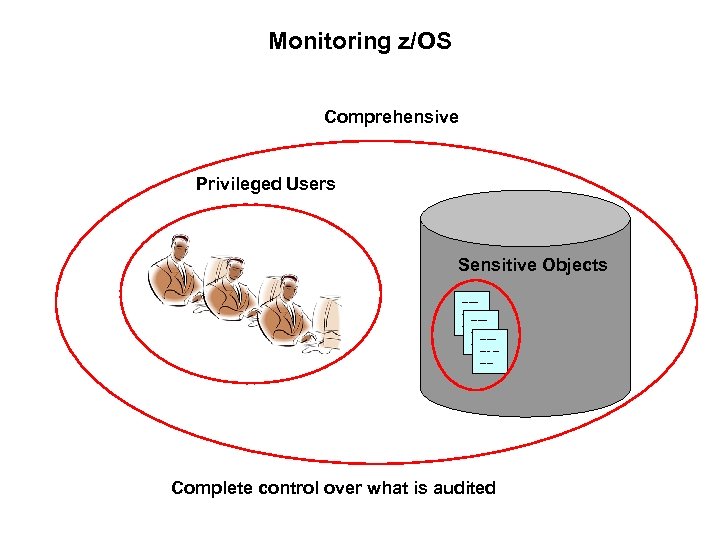
Monitoring z/OS Comprehensive Privileged Users Sensitive Objects ----------- ----- Complete control over what is audited
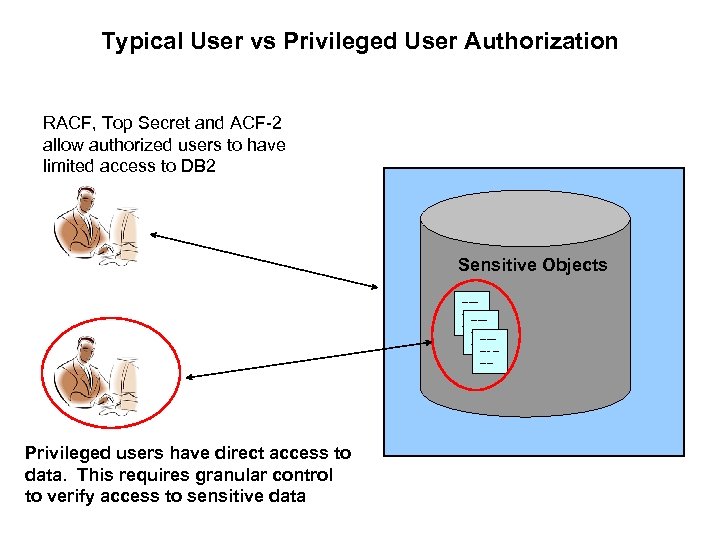
Typical User vs Privileged User Authorization RACF, Top Secret and ACF-2 allow authorized users to have limited access to DB 2 Sensitive Objects ----------- ----- Privileged users have direct access to data. This requires granular control to verify access to sensitive data
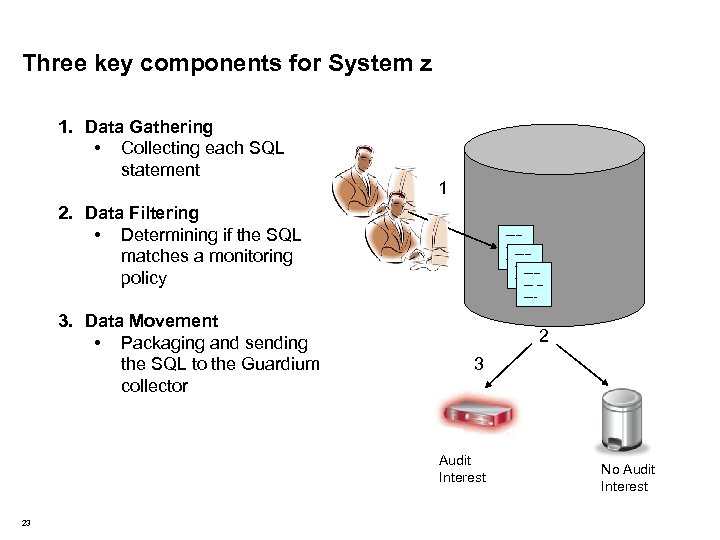
Three key components for System z 1. Data Gathering • Collecting each SQL statement 1 2. Data Filtering • Determining if the SQL matches a monitoring policy 3. Data Movement • Packaging and sending the SQL to the Guardium collector ----------- ----- 2 3 Audit Interest 23 No Audit Interest
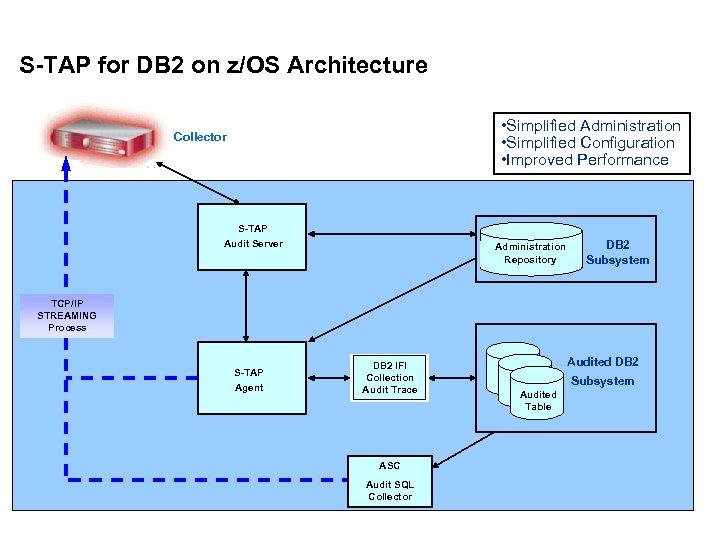
S-TAP for DB 2 on z/OS Architecture • Simplified Administration • Simplified Configuration • Improved Performance Collector S-TAP Audit Server Administration Repository DB 2 Subsystem TCP/IP STREAMING Process S-TAP Agent DB 2 IFI Collection Audit Trace ASC Audit SQL Collector Audited DB 2 Subsystem Audited Table
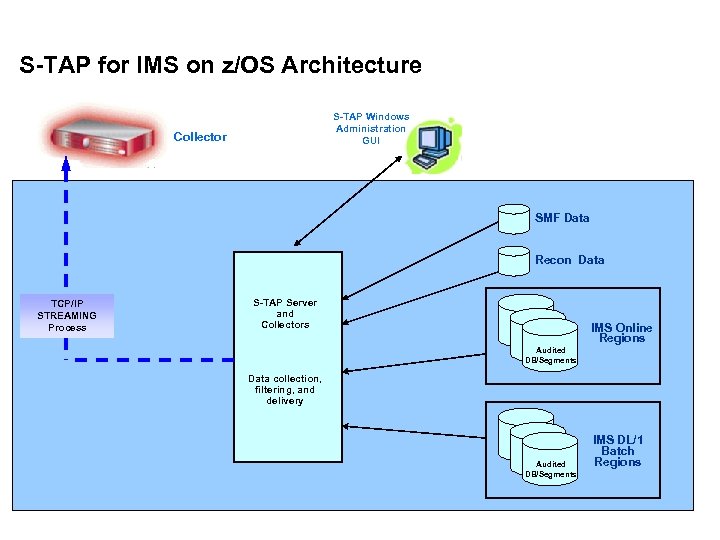
S-TAP for IMS on z/OS Architecture S-TAP Windows Administration GUI Collector SMF Data Recon Data TCP/IP STREAMING Process S-TAP Server and Collectors IMS Online Regions Audited DB/Segments Data collection, filtering, and delivery Audited DB/Segments IMS DL/1 Batch Regions
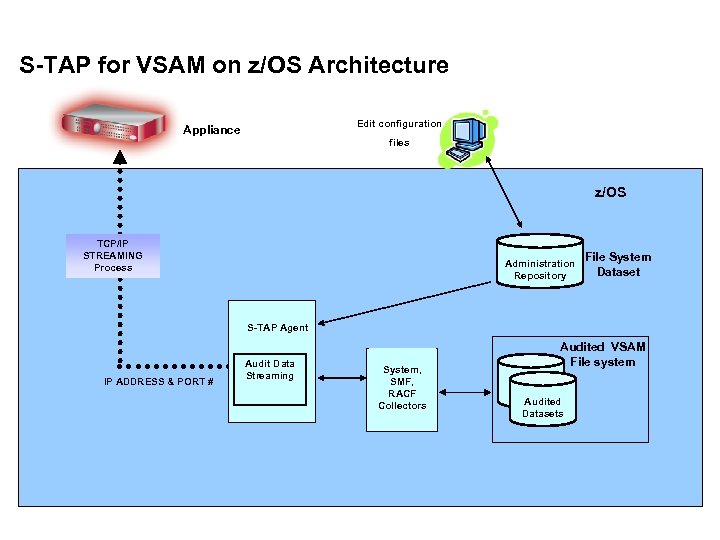
S-TAP for VSAM on z/OS Architecture Edit configuration Appliance files z/OS TCP/IP STREAMING Process Administration Repository File System Dataset S-TAP Agent IP ADDRESS & PORT # Audit Data Streaming System, SMF, RACF Collectors Audited VSAM File system Audited Tables Audited Datasets
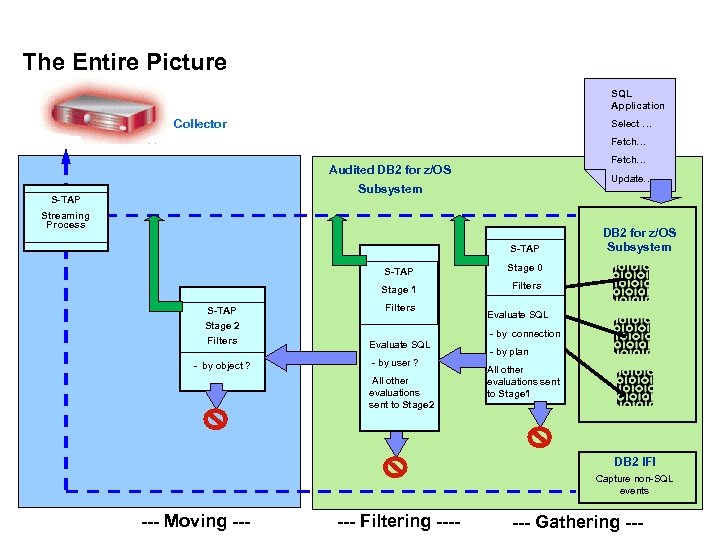
The Entire Picture SQL Application Collector Select … Fetch… Audited DB 2 for z/OS Update… Subsystem S-TAP Streaming Process S-TAP Stage 0 Stage 1 Filters Stage 2 Filters - by object ? DB 2 for z/OS Subsystem Evaluate SQL - by user ? All other evaluations sent to Stage 2 Evaluate SQL - by connection - by plan All other evaluations sent to Stage 1 DB 2 IFI Capture non-SQL events --- Moving --- Filtering ---- Gathering ---
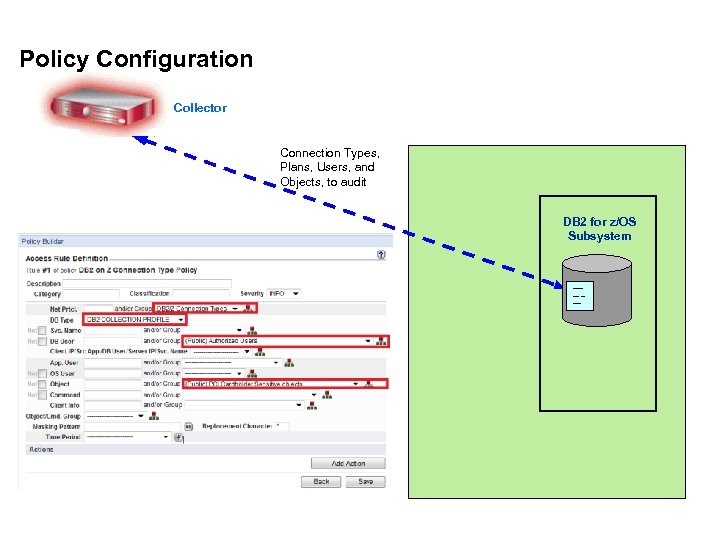
Policy Configuration Collector Connection Types, Plans, Users, and Objects, to audit DB 2 for z/OS Subsystem -------

ibm. com/guardium
f3639b25d43cf4ed2535740c59b69b69.ppt