59e2f1212272c339cddab575a97e76bf.ppt
- Количество слайдов: 14
 Safe. Net Key. Secure with Luna HSM Management © Safe. Net Confidential and Proprietary 1
Safe. Net Key. Secure with Luna HSM Management © Safe. Net Confidential and Proprietary 1
 Why Is Centralized Key Management Needed? The Unmanageable Cost of Diverse Encryption Systems According to Gartner: “by 2015, 30% of organizations under regulatory mandates will not have deployed some form of encryption to secure data assets, and 50% will suffer data loss and/or experience regulatory sanctions”. * Challenges: à Time: Managing diverse encryption systems manually, decreases operational effectiveness while increasing risks à Data Loss / Operational Disruptions: Up to 39 percent of organizations who have experienced key loss also lose data permanently or disrupt business operations. à Proof of Compliance: Demonstrate which appliances, devices, applications are using encryption keys and where they are geographically located à Maintenance Costs: à Heterogeneous systems mean no economy of scale for maintenance costs. Each encryption system and key management solution could have 15 -20% annual maintenance fees. * Source: trust catalyst, 2009 Encryption & Key Management Industry Benchmark Report 2
Why Is Centralized Key Management Needed? The Unmanageable Cost of Diverse Encryption Systems According to Gartner: “by 2015, 30% of organizations under regulatory mandates will not have deployed some form of encryption to secure data assets, and 50% will suffer data loss and/or experience regulatory sanctions”. * Challenges: à Time: Managing diverse encryption systems manually, decreases operational effectiveness while increasing risks à Data Loss / Operational Disruptions: Up to 39 percent of organizations who have experienced key loss also lose data permanently or disrupt business operations. à Proof of Compliance: Demonstrate which appliances, devices, applications are using encryption keys and where they are geographically located à Maintenance Costs: à Heterogeneous systems mean no economy of scale for maintenance costs. Each encryption system and key management solution could have 15 -20% annual maintenance fees. * Source: trust catalyst, 2009 Encryption & Key Management Industry Benchmark Report 2
 Pain Points of Decentralization “…organizations should exert significant pressure on cryptographic solution vendors to support the cryptographic keys in their systems being open to management by third-party OASIS-KMIP-compliant key managers. Without this, organizations will continue to have a siloed key management approach with each and every encryption deployment. ” à Limited Administrative Transparency Fragmented policy and fragmented key management Differing hardware, policies, devices in different business units within the enterprise No clear view of keys and key states on the HSM à Operational Inefficiencies Key management is an after-thought Manual audit reviews Require different administrative functions for key management – admin skill sets à Multiple key vaults in multiple locations Audit Deficiencies & Failures Irregular key rotation à Compliance (NIST 800 -57, PCI-DSS, etc. ) 3
Pain Points of Decentralization “…organizations should exert significant pressure on cryptographic solution vendors to support the cryptographic keys in their systems being open to management by third-party OASIS-KMIP-compliant key managers. Without this, organizations will continue to have a siloed key management approach with each and every encryption deployment. ” à Limited Administrative Transparency Fragmented policy and fragmented key management Differing hardware, policies, devices in different business units within the enterprise No clear view of keys and key states on the HSM à Operational Inefficiencies Key management is an after-thought Manual audit reviews Require different administrative functions for key management – admin skill sets à Multiple key vaults in multiple locations Audit Deficiencies & Failures Irregular key rotation à Compliance (NIST 800 -57, PCI-DSS, etc. ) 3
 Why Should Customers Choose Safe. Net? “To date, only one major cryptographic vendor that possesses its own key manager offering has suggested as part of a road map discussion that it would tentatively support a third-party OASIS KMIPcompliant key manager managing its cryptographic keys. ”~ Eric Ouellet, Analyst, Gartner Only Safe. Net Key. Secue can provide OASIS KMIP integration with Luna SA/PCI and other KMIP based platforms. Safe. Net Key. Secure manages a diverse range of cryptographic key types. Our solution is application agnostic, meaning applications do not need to be tailored to work with Key. Secure. In addition to HSM management, Key. Secure features comprehensive coverage for storage and archive encryption. Key. Secure benefits from a clear vision leading to full support of KMIP which will enable management of a large number of encryption solutions and vendors. 4
Why Should Customers Choose Safe. Net? “To date, only one major cryptographic vendor that possesses its own key manager offering has suggested as part of a road map discussion that it would tentatively support a third-party OASIS KMIPcompliant key manager managing its cryptographic keys. ”~ Eric Ouellet, Analyst, Gartner Only Safe. Net Key. Secue can provide OASIS KMIP integration with Luna SA/PCI and other KMIP based platforms. Safe. Net Key. Secure manages a diverse range of cryptographic key types. Our solution is application agnostic, meaning applications do not need to be tailored to work with Key. Secure. In addition to HSM management, Key. Secure features comprehensive coverage for storage and archive encryption. Key. Secure benefits from a clear vision leading to full support of KMIP which will enable management of a large number of encryption solutions and vendors. 4
 Drivers for Our Success in the HSM Space COST Offer cost-effective hardware solutions that can secure keys for multiple concurrent applications on a single appliance USABILITY Provide distinct operational roles and remote management capabilities for maximum flexibility in a wide range of organizations Mitigate RISK with a defense in depth approach to hardware and system design Helping customers successfully achieve the correct balance of risk mitigation, cost effectiveness and usability 5
Drivers for Our Success in the HSM Space COST Offer cost-effective hardware solutions that can secure keys for multiple concurrent applications on a single appliance USABILITY Provide distinct operational roles and remote management capabilities for maximum flexibility in a wide range of organizations Mitigate RISK with a defense in depth approach to hardware and system design Helping customers successfully achieve the correct balance of risk mitigation, cost effectiveness and usability 5
 Key. Secure in HSM Environments Key. Secure provides a centralized view of all the keys in an enterprise including the association between encryption keys and the applications using these keys as well as key metadata such as creation date of the key. COST Offer solutions that enable our customers to manage and monitor their existing HSM centrally, for reduced administrative costs USABILITY Provide a streamlined and intuitive user interface that facilitates HSM management, and simplifies the audit process Mitigate RISK by empowering a centralized administrative team with tools that provide a real time view of the infrastructure and ensures consistent security policy enforcement Helping customers successfully achieve the correct balance of risk mitigation, cost effectiveness and usability 6
Key. Secure in HSM Environments Key. Secure provides a centralized view of all the keys in an enterprise including the association between encryption keys and the applications using these keys as well as key metadata such as creation date of the key. COST Offer solutions that enable our customers to manage and monitor their existing HSM centrally, for reduced administrative costs USABILITY Provide a streamlined and intuitive user interface that facilitates HSM management, and simplifies the audit process Mitigate RISK by empowering a centralized administrative team with tools that provide a real time view of the infrastructure and ensures consistent security policy enforcement Helping customers successfully achieve the correct balance of risk mitigation, cost effectiveness and usability 6
 Mapping the Feature Set of Key. Secure 7
Mapping the Feature Set of Key. Secure 7
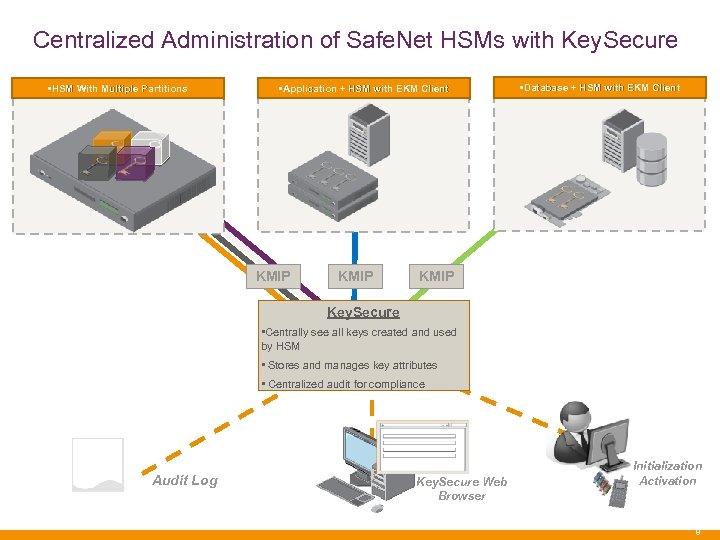 Centralized Administration of Safe. Net HSMs with Key. Secure • HSM With Multiple Partitions • Application + HSM with EKM Client KMIP • Database + HSM with EKM Client KMIP Key. Secure K • Centrally see all keys created and used Se ey by HSM c ur e • Stores and manages key attributes • Centralized audit for compliance Audit Log Key. Secure Web Browser Initialization Activation 8
Centralized Administration of Safe. Net HSMs with Key. Secure • HSM With Multiple Partitions • Application + HSM with EKM Client KMIP • Database + HSM with EKM Client KMIP Key. Secure K • Centrally see all keys created and used Se ey by HSM c ur e • Stores and manages key attributes • Centralized audit for compliance Audit Log Key. Secure Web Browser Initialization Activation 8
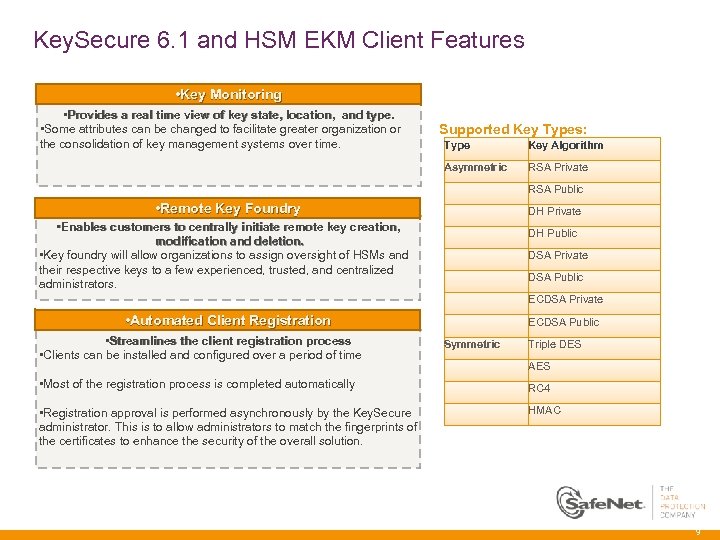 Key. Secure 6. 1 and HSM EKM Client Features • Key Monitoring • Provides a real time view of key state, location, and type. • Some attributes can be changed to facilitate greater organization or the consolidation of key management systems over time. Supported Key Types: Type Key Algorithm Asymmetric RSA Private RSA Public • Remote Key Foundry DH Private • Enables customers to centrally initiate remote key creation, modification and deletion. • Key foundry will allow organizations to assign oversight of HSMs and their respective keys to a few experienced, trusted, and centralized administrators. DH Public DSA Private DSA Public ECDSA Private • Automated Client Registration • Streamlines the client registration process • Clients can be installed and configured over a period of time ECDSA Public Symmetric Triple DES AES • Most of the registration process is completed automatically RC 4 • Registration approval is performed asynchronously by the Key. Secure administrator. This is to allow administrators to match the fingerprints of the certificates to enhance the security of the overall solution. HMAC 9
Key. Secure 6. 1 and HSM EKM Client Features • Key Monitoring • Provides a real time view of key state, location, and type. • Some attributes can be changed to facilitate greater organization or the consolidation of key management systems over time. Supported Key Types: Type Key Algorithm Asymmetric RSA Private RSA Public • Remote Key Foundry DH Private • Enables customers to centrally initiate remote key creation, modification and deletion. • Key foundry will allow organizations to assign oversight of HSMs and their respective keys to a few experienced, trusted, and centralized administrators. DH Public DSA Private DSA Public ECDSA Private • Automated Client Registration • Streamlines the client registration process • Clients can be installed and configured over a period of time ECDSA Public Symmetric Triple DES AES • Most of the registration process is completed automatically RC 4 • Registration approval is performed asynchronously by the Key. Secure administrator. This is to allow administrators to match the fingerprints of the certificates to enhance the security of the overall solution. HMAC 9
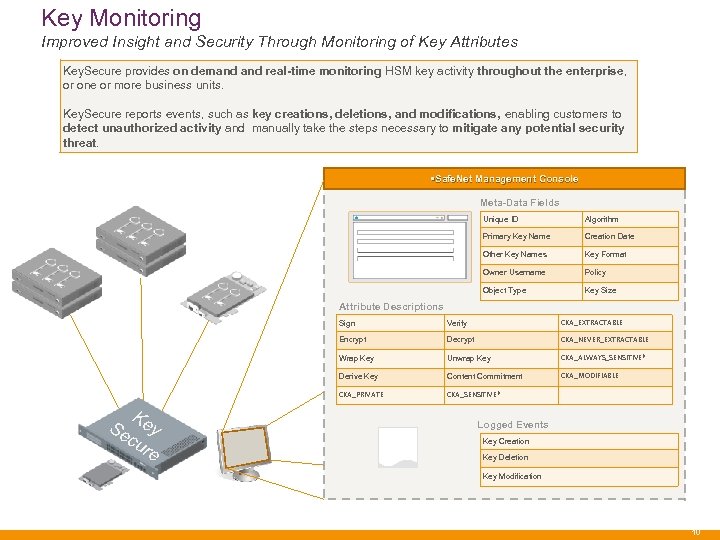 Key Monitoring Improved Insight and Security Through Monitoring of Key Attributes Key. Secure provides on demand real-time monitoring HSM key activity throughout the enterprise, or one or more business units. Key. Secure reports events, such as key creations, deletions, and modifications, enabling customers to detect unauthorized activity and manually take the steps necessary to mitigate any potential security threat. • Safe. Net Management Console Meta-Data Fields Unique ID Algorithm Primary Key Name Creation Date Other Key Names Key Format Owner Username Policy Object Type Key Size Attribute Descriptions Sign CKA_EXTRACTABLE Encrypt Decrypt CKA_NEVER_EXTRACTABLE Wrap Key Unwrap Key CKA_ALWAYS_SENSITIVE* Derive Key Content Commitment CKA_MODIFIABLE CKA_PRIVATE K Se ey cu re Verify CKA_SENSITIVE* Logged Events Key Creation Key Deletion Key Modification 10
Key Monitoring Improved Insight and Security Through Monitoring of Key Attributes Key. Secure provides on demand real-time monitoring HSM key activity throughout the enterprise, or one or more business units. Key. Secure reports events, such as key creations, deletions, and modifications, enabling customers to detect unauthorized activity and manually take the steps necessary to mitigate any potential security threat. • Safe. Net Management Console Meta-Data Fields Unique ID Algorithm Primary Key Name Creation Date Other Key Names Key Format Owner Username Policy Object Type Key Size Attribute Descriptions Sign CKA_EXTRACTABLE Encrypt Decrypt CKA_NEVER_EXTRACTABLE Wrap Key Unwrap Key CKA_ALWAYS_SENSITIVE* Derive Key Content Commitment CKA_MODIFIABLE CKA_PRIVATE K Se ey cu re Verify CKA_SENSITIVE* Logged Events Key Creation Key Deletion Key Modification 10
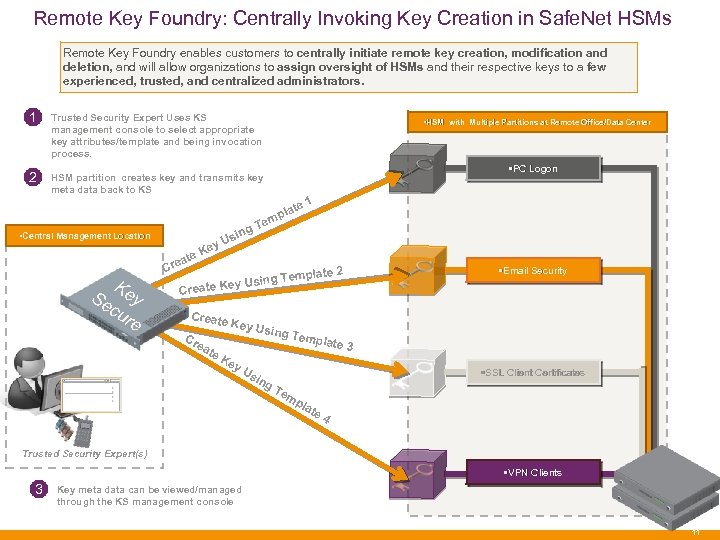 Remote Key Foundry: Centrally Invoking Key Creation in Safe. Net HSMs Remote Key Foundry enables customers to centrally initiate remote key creation, modification and deletion, and will allow organizations to assign oversight of HSMs and their respective keys to a few experienced, trusted, and centralized administrators. 1 Trusted Security Expert Uses KS management console to select appropriate key attributes/template and being invocation process. 2 HSM partition creates key and transmits key meta data back to KS • Central Management Location K Se ey cu re g sin • HSM with Multiple Partitions at Remote Office/Data Center • PC Logon la mp te 1 Te y. U Ke ate Cre emplate 2 y Using T e Create K Create Cr ea te Key U Ke sing T y. U • Email Security sin empla te 3 • SSL Client Certificates g. T em pla te 4 Trusted Security Expert(s) • VPN Clients 3 Key meta data can be viewed/managed through the KS management console 11
Remote Key Foundry: Centrally Invoking Key Creation in Safe. Net HSMs Remote Key Foundry enables customers to centrally initiate remote key creation, modification and deletion, and will allow organizations to assign oversight of HSMs and their respective keys to a few experienced, trusted, and centralized administrators. 1 Trusted Security Expert Uses KS management console to select appropriate key attributes/template and being invocation process. 2 HSM partition creates key and transmits key meta data back to KS • Central Management Location K Se ey cu re g sin • HSM with Multiple Partitions at Remote Office/Data Center • PC Logon la mp te 1 Te y. U Ke ate Cre emplate 2 y Using T e Create K Create Cr ea te Key U Ke sing T y. U • Email Security sin empla te 3 • SSL Client Certificates g. T em pla te 4 Trusted Security Expert(s) • VPN Clients 3 Key meta data can be viewed/managed through the KS management console 11
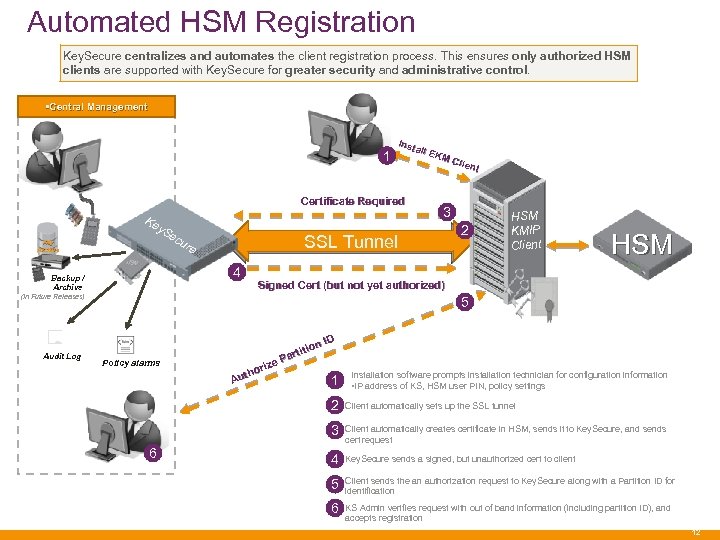 Automated HSM Registration Key. Secure centralizes and automates the client registration process. This ensures only authorized HSM clients are supported with Key. Secure for greater security and administrative control. • Central Management 1 Inst all E KM Clie nt Certificate Required Ke y. S Key Archive ec SSL Tunnel ure 4 Backup / Archive 2 HSM KMIP Client HSM Signed Cert (but not yet authorized) (In Future Releases) Audit Log 3 5 Policy alarms n ID itio t Par rize tho Au 1 Installation software prompts installation technician for configuration information • IP address of KS, HSM user PIN, policy settings 2 3 6 Client automatically sets up the SSL tunnel Client automatically creates certificate in HSM, sends it to Key. Secure, and sends cert request 4 Key. Secure sends a signed, but unauthorized cert to client 5 Client sends the an authorization request to Key. Secure along with a Partition ID for identification 6 KS Admin verifies request with out of band information (including partition ID), and accepts registration 12
Automated HSM Registration Key. Secure centralizes and automates the client registration process. This ensures only authorized HSM clients are supported with Key. Secure for greater security and administrative control. • Central Management 1 Inst all E KM Clie nt Certificate Required Ke y. S Key Archive ec SSL Tunnel ure 4 Backup / Archive 2 HSM KMIP Client HSM Signed Cert (but not yet authorized) (In Future Releases) Audit Log 3 5 Policy alarms n ID itio t Par rize tho Au 1 Installation software prompts installation technician for configuration information • IP address of KS, HSM user PIN, policy settings 2 3 6 Client automatically sets up the SSL tunnel Client automatically creates certificate in HSM, sends it to Key. Secure, and sends cert request 4 Key. Secure sends a signed, but unauthorized cert to client 5 Client sends the an authorization request to Key. Secure along with a Partition ID for identification 6 KS Admin verifies request with out of band information (including partition ID), and accepts registration 12
 Key. Secure Enhances this Balance! RISK MITIGATION § Empower a Centralized Administrative Team § Ensure consistent security policy application across an enterprise EASE OF USE § Centralized view of HSMs, keys and Key States § GUI Interface § Reduced Dependency on PED Devices LOWER TOTAL COST OF OWNERSHIP § Reduced administrative costs § Streamlined HSM setup process § More efficient audit process Helping customers successfully achieve the correct balance of risk mitigation, cost effectiveness and usability 13
Key. Secure Enhances this Balance! RISK MITIGATION § Empower a Centralized Administrative Team § Ensure consistent security policy application across an enterprise EASE OF USE § Centralized view of HSMs, keys and Key States § GUI Interface § Reduced Dependency on PED Devices LOWER TOTAL COST OF OWNERSHIP § Reduced administrative costs § Streamlined HSM setup process § More efficient audit process Helping customers successfully achieve the correct balance of risk mitigation, cost effectiveness and usability 13
 Thank You! 14
Thank You! 14


