54e881d1c3734fd8d406dfc4e35628f2.ppt
- Количество слайдов: 34
Safe Browsing Copyright 2007 © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http: //www. owasp. org

Safe Browsing: Class Outline Web Browsers – How they work generally speaking. Over view of how browsers work How many think they work vs how they really work Live group participation demo - maybe Browsers – What's available out there? Current state of affairs Cornucopia of browsers Outlook = IE? ? Making browsing safer, better and more anonymous. Online hazards overview BHO and other add-ons Browser Security Checks Multiple browser ninjutsu Tor – hiding in plain sight (well sort of) OWASP
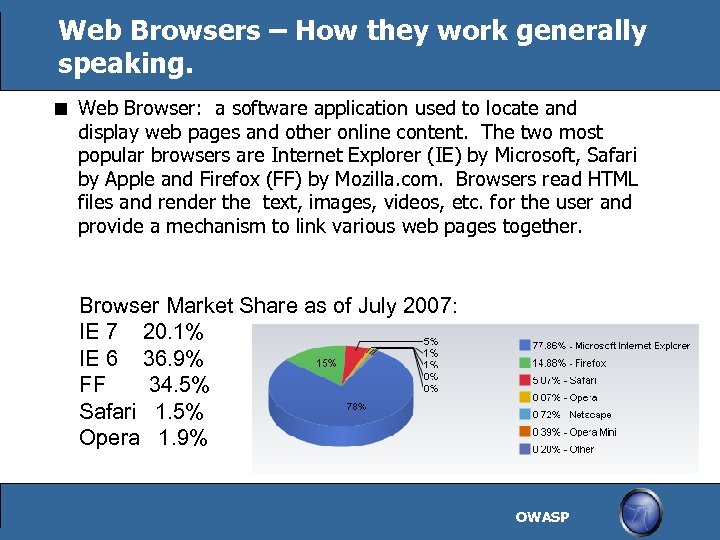
Web Browsers – How they work generally speaking. Web Browser: a software application used to locate and display web pages and other online content. The two most popular browsers are Internet Explorer (IE) by Microsoft, Safari by Apple and Firefox (FF) by Mozilla. com. Browsers read HTML files and render the text, images, videos, etc. for the user and provide a mechanism to link various web pages together. Browser Market Share as of July 2007: IE 7 20. 1% IE 6 36. 9% FF 34. 5% Safari 1. 5% Opera 1. 9% OWASP
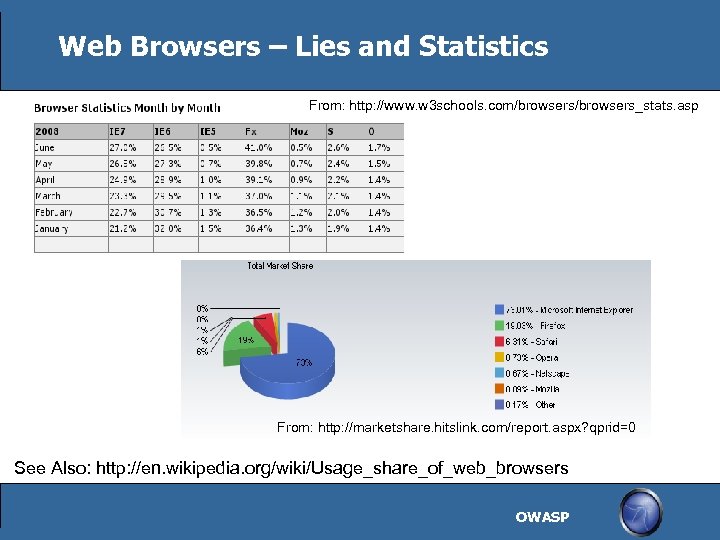
Web Browsers – Lies and Statistics From: http: //www. w 3 schools. com/browsers_stats. asp From: http: //marketshare. hitslink. com/report. aspx? qprid=0 See Also: http: //en. wikipedia. org/wiki/Usage_share_of_web_browsers OWASP
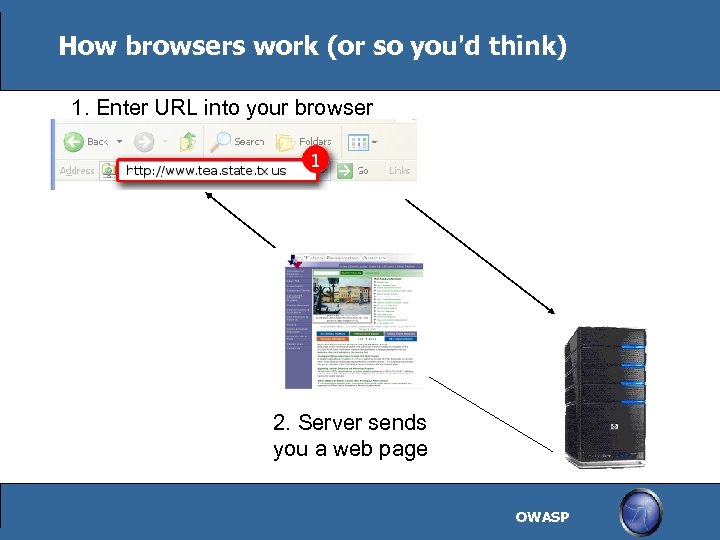
How browsers work (or so you'd think) 1. Enter URL into your browser 2. Server sends you a web page OWASP

How browsers really work Enter a URL into a browser Breaks the URL into a host + path Asks a DNS server for an IP address for the host DNS server returns a IP address for that host Browser sends a request to the IP address If no port is given, port 80 is used Path is used to determine what file to send Server replies to the request – usually sends a HTML file Browser reads the HTML file and asks for all the files referenced in the original HTML file These additional files could be images, more HTML, or other types on content. Additional files could reside on different hosts requiring more DNS requests After browser gets all the pieces, it renders a single “page” OWASP

What is this IP business anyway? Every computer on the Internet (or any network) will have a special number associated with it called the IP address. By using this number, network traffic can be directed from its origin to the destination. How can I tell what my IP address is? IP Chicken! http: //www. ipchicken. com OWASP
Browsers: What's out there? Even though Windows XP will label IE “Internet”, there are many, many ways to view the web OWASP

OK, so who are the real contenders? IE and FF are the two leaders in the web browser space as they account for somewhere slightly greater then 90% of web browsers, depending on who you ask. An independent researcher compared IE to FF looking at how many days each browser had a known vulnerability and there wasn't a patch available. 98% unsafe or there we only 7 days in 2006 where IE was vulnerability free 15% unsafe (7% unsafe on Windows) or there were 309 days in 2006 where FF was vulnerability free (30 days were Mac only) OWASP
Hurray, FF 3! Mozilla. com just released Firefox version 3! http: //www. mozilla. com/en-US/firefox/features/ http: //www. mozilla. com/en-US/firefox/security/ OWASP
Don't forget about third party candidates. Opera is a really nice browser as well Doesn't have the market share of the big 2 (that could be a good thing) Runs on Windows / Mac / Linux Has a ton of unique features Doesn't have as many plugins/add ons as FF Good track record on security patching Speed dial is pretty slick Becoming a favorite of mine for 'general browsing' OWASP
So, should I switch? How painful will that be? OWASP
Which is which? OWASP
By the way. . . Outlook = IE (more in our Email security class) OWASP

Making browsing a better place Quick Review: Browsers work by asking a server for files and then rendering the end result of the request(s). There a ton of browsers out there with IE and FF the most popular. FF edges out IE historically for features and security. Opera is a good option too. So now we know about browsers, what's next Making browsing safer, better and more anonymous. Online hazards overview BHO and other add-ons Browser Security Checks Multiple browser ninjutsu Tor – hiding in plain sight (well sort of) OWASP

SSL: Browsers security issues solved Not really. . . HTTP vs HTTPS HTTP is very similar to email in its evolution HTTP is by design insecure, particularly to eavesdropping and interception/modification of content HTTPS was developed to mitigate this risk HTTPS does Keeps communication between browser and server hidden from view Provides some verification of the server you are talking to HTTPS doesn't Stop malicious traffic from passing between browsers and servers Stop XSS, XSRF, SQL-I, application logic flaws. . OWASP
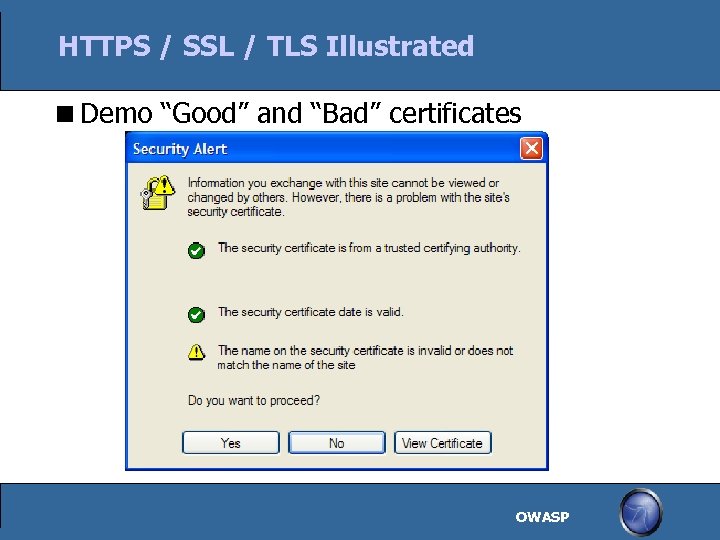
HTTPS / SSL / TLS Illustrated Demo “Good” and “Bad” certificates OWASP
The Internet is a pretty rough place at times. . . As web browsing has increased in popularity and other security weakness have been addressed, browsers are now a very likely target Making browsers behave badly Phishing - an attempt to criminally and fraudulently acquire sensitive information, such as usernames, passwords and credit card details, by masquerading as a trustworthy entity online Browser Hijacking - the modification of a web browser's settings by malware. The term "hijacking" is used as the changes are performed without the user's permission. Can be difficult to reverse. Drive by Installs – When web site uses a browser flaw to install software of their choice when a user views a specially crafted web page. OWASP
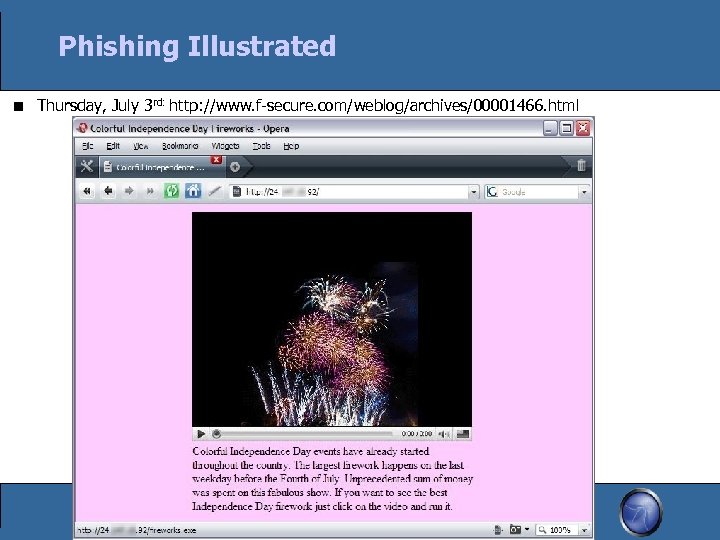
Phishing Illustrated Thursday, July 3 rd: http: //www. f-secure. com/weblog/archives/00001466. html OWASP
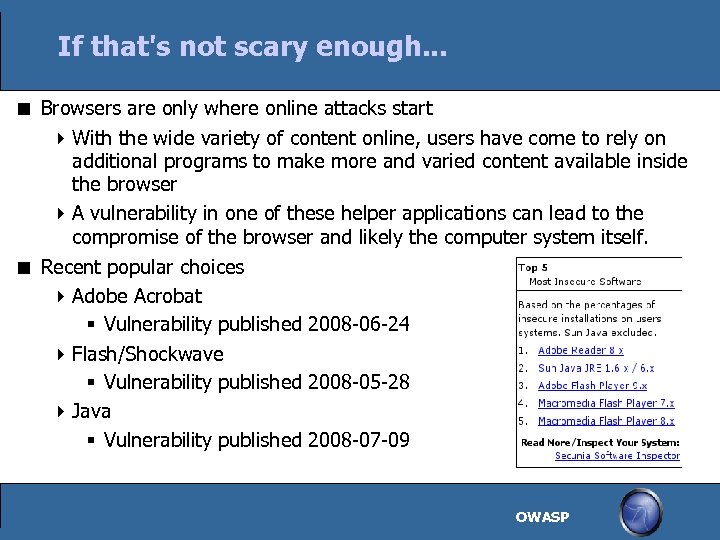
If that's not scary enough. . . Browsers are only where online attacks start With the wide variety of content online, users have come to rely on additional programs to make more and varied content available inside the browser A vulnerability in one of these helper applications can lead to the compromise of the browser and likely the computer system itself. Recent popular choices Adobe Acrobat Vulnerability published 2008 -06 -24 Flash/Shockwave Vulnerability published 2008 -05 -28 Java Vulnerability published 2008 -07 -09 OWASP

Helper Applications aren't the only ones HTML is a static language – originally meant to display text and some simple images People wanted web pages which did more At the time, Netscape was the dominant browser and they came up with something called Live. Script allowed a programming language to be included with HTML so that computer processing could happen within the browser Live. Script was renamed Java. Script after Sun launched the Java language. Sadly, Java. Script has no real connection to Java except the name. XSS, XSRF, Phishing sites and many other attack vectors rely on using/breaking Javascript to the advantage of the attacker OWASP

Hacking: Now commercially supported with updates Browser hacking has reached new levels of sophistication with the introd MPack is a web application designed to exploit known web browser vulnerabilities Primarily focuses on IE but FF & Opera are also targets An automated system to try exploit after exploit in an attempt to find a vulnerable browser Commercial software costing from $500 to $1000 Estimated to have infected ~160, 000 computers Includes a management console which enumerates the browsers which have been compromised New versions are released each month and additional modules can be installed to increase its functionality OWASP

OK, I'm scared. Can you stop talking? Luckily there are things you can do to not be a victim The general IT security stuff Keep your computer OS patched Keep your other software updated to the most recent version (Java, Acrobat, Flash. . . ) Install and keep updated Anti-Virus software Anti-Spyware software Keep out of the bad 'neighborhoods' on the Internet Be careful about downloading programs you're not 100% familiar with or that are email'ed to you. Consider attending the other security classes OWASP
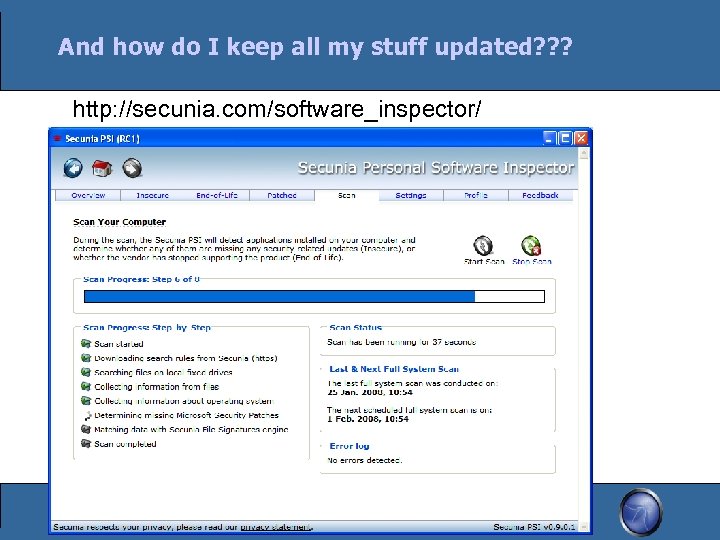
And how do I keep all my stuff updated? ? ? http: //secunia. com/software_inspector/ OWASP

Browser Specific Recommendations Firefox is the smart choice for your web browser Has had a better track record of addressing security issues Has a built in update mechanism so keeping the browser updated is rather painless Tons of add-ons which can greatly increase security Watch out for “Toolbars” - particularly for IE Many of the tool bars will add many handy functions to your browsing experience However, many of them will “phone home” and report on your browser habits – a definite privacy concern You can bury your browser under multiple toolbars Some web sites won't work with FF, so keep another browser around for those (Windows Update) OWASP
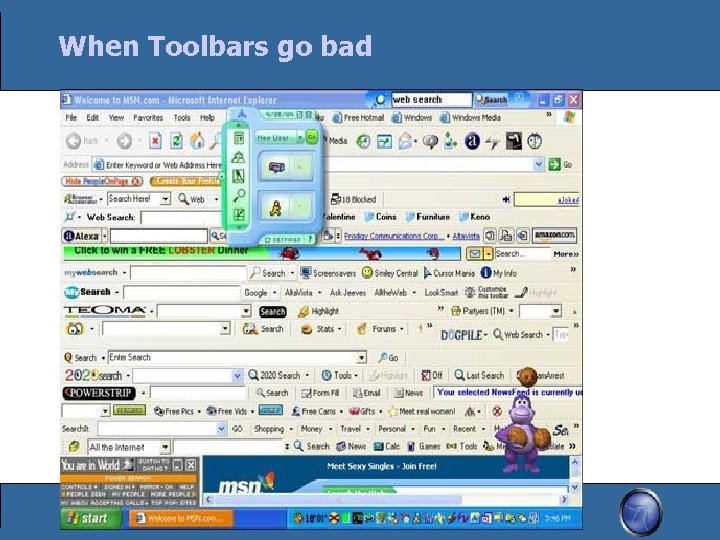
When Toolbars go bad OWASP

Still scared? Have a cookie! Brief overview of cookies and their reason for being (at least web browser cookies) Cookies can make your browsing experience much richer but can also be used to track your as you travel from site to site In and of themselves, they are just some text stored on your computer, you just have to decide how much privacy you want Can also have security ramifications Recent Gmail cookie hack OWA and its cookie OWASP

Making Firefox even better No-Script Gives you the option to decide who you trust (and don't) while browsing online Defaults to dis-allowing scripts and other programs from running unless you says its OK. You will find pages which this breaks (until you allow them to run scripts) https: //addons. mozilla. org/en-US/firefox/addon/722 User-Agent : For sites which check what browser you are using Many of these will work fine with FF but you've got to trick the web site first https: //addons. mozilla. org/en-US/firefox/addon/59 This barely scratches the surface. Poke around Mozilla's add-on site for many, many more OWASP
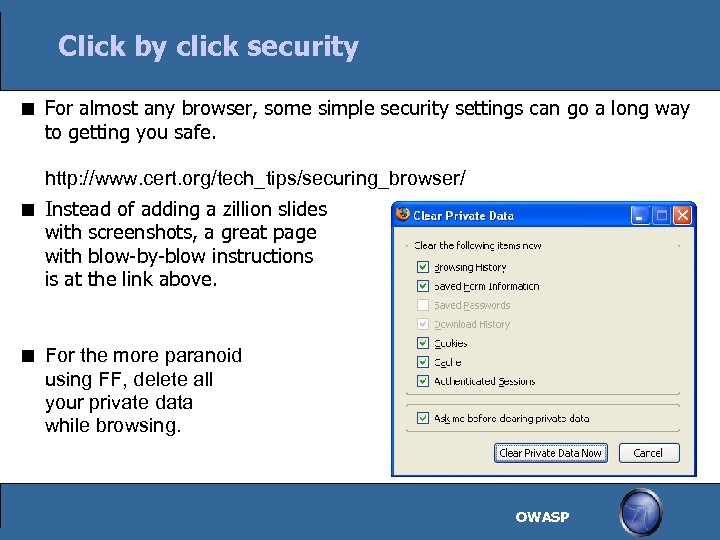
Click by click security For almost any browser, some simple security settings can go a long way to getting you safe. http: //www. cert. org/tech_tips/securing_browser/ Instead of adding a zillion slides with screenshots, a great page with blow-by-blow instructions is at the link above. For the more paranoid using FF, delete all your private data while browsing. OWASP

Why stop at just one Another trick is to use one browser for your “important” surfing and another for “casual” browsing. That way data from one can't leak to the other (generally speaking) Tor – Geeky stuff to keep your surfing anonymous Tor stands for The Onion Router Using Tor, your traffic enters the Tor network and is encrypted The Tor network bounces your traffic inside it self enough that determining where you originated from is very difficult. You exit the Tor network at an 'Exit Node' and are decrypted and flow over the Internet as normal FF users can easily combine Tor with Foxy. Proxy add-on OWASP
Links, Links and more Links Web browser defined http: //en. wikipedia. org/wiki/Web_browser Site dedicated to helping the average PC user safe on the Internet http: //surfthenetsafely. com/ Great site for explicit instructions on how to secure the browser of your choice. http: //www. cert. org/tech_tips/securing_browser/ Microsoft article on how to secure web browsing (IE only) http: //www. microsoft. com/protect/computer/advanced/browsing. mspx Article on browser security in general http: //www. networkcomputing. com/channels/security/show. Article. jhtml? article. ID=197700134 Article comparing IE to FF http: //itmanagement. earthweb. com/secu/article. php/3698606 More browser vs. browser comparison http: //www. pcworld. com/article/id, 118959 -page, 1/article. html Article on how IE in particular is becoming a popular target of attacks http: //www. pcworld. com/article/id, 134949 -page, 1 -c, browsersecurity/article. html OWASP
Links, Links and more Links Article on the MPack Attack Kit http: //www. pcworld. com/article/id, 136286 -page, 1 -c, browsersecurity/article. html Article on the rise of the malicious web server http: //www. darkreading. com/document. asp? doc_id=131584 Blog post about the Phishing example used in this class http: //www. f-secure. com/weblog/archives/00001288. html Article on hacking 2. 0 – (Ab)using interactivity http: //isc. sans. org/diary. html? storyid=3106 Web page which discusses alternative browsers (where a lot of the icons I used came from) http: //www. alternativebrowseralliance. com/browsers. html No-Script Firefox add-on https: //addons. mozilla. org/en-US/firefox/addon/722 User-Agent Switcher Firefox add-on https: //addons. mozilla. org/en-US/firefox/addon/59 OWASP
Links, Links and more Links Password Maker Firefox add-on (I've not tried this one, yet) https: //addons. mozilla. org/en-US/firefox/addon/469 Tor Network for anonymous browsing http: //tor. eff. org/ Browser Statistics http: //www. w 3 schools. com/browsers_stats. asp http: //marketshare. hitslink. com/report. aspx? qprid=0 http: //en. wikipedia. org/wiki/Usage_share_of_web_browsers Blog with Phishing Example: http: //www. f-secure. com/weblog/archives/00001466. html Secunia Software Inspector Online Scanner: http: //secunia. com/software_inspector/ Firefox 3: http: //www. mozilla. com/en-US/firefox/ OWASP

Questions? OWASP
54e881d1c3734fd8d406dfc4e35628f2.ppt