ef5896219fe58db6cf4a2910769c81e7.ppt
- Количество слайдов: 30

RSA Solutions Overview Security Solutions for Business Accelleration Ivan Svoboda Key Account Manager RSA Security ivan. svoboda@rsa. com

RSA Protection in Action 134, 000+ Billion+ 200 Million+ 150, 000+ 25+ Applications shipped withprotected Encryption Year legacy in information security Phishing attacks shut down Organizations BSAFE® Identities protected 25+ 34, 000+ 150, 000+ 250 Million+ 1 Billion+ year legacy in information security and risk management organizations protected by RSA technology online phishing attacks shut down by the RSA Anti-Fraud Command Center online identities protected with RSA identification and protection technology applications shipped with RSA BSAFE® encryption most widely deployed software in the world* *Embedded in Microsoft, HP, Sun and IBM operating systems, Internet Explorer and Netscape browsers, Ericsson, Nokia, Motorola phones, major US government agencies and the list goes on

RSA: Award Winning Company

Frost and Sullivan – Competitive Landscape OTP Authentication(December 2008)

Leadership Beyond Authentication “RSA is vastly more than user authentication; it is a key portion of how companies, particularly in the financial industry, protect critical records and comply with critical regulations. ” -- “EMC Addresses the 2009 ‘OMG’ Budget”, ITBusiness Edge, Rob Enderle, Enderle Group, Dec. 9, 2008 Data Loss Prevention MQ June 2008 Web Fraud Detection MQ Dec. 2008 SIEM MQ May 2008

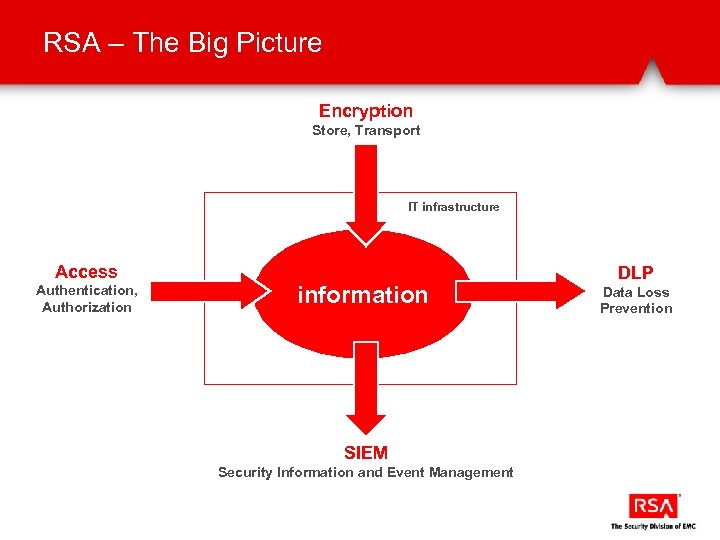
RSA – The Big Picture Encryption Store, Transport IT infrastructure Access Authentication, Authorization information SIEM Security Information and Event Management DLP Data Loss Prevention
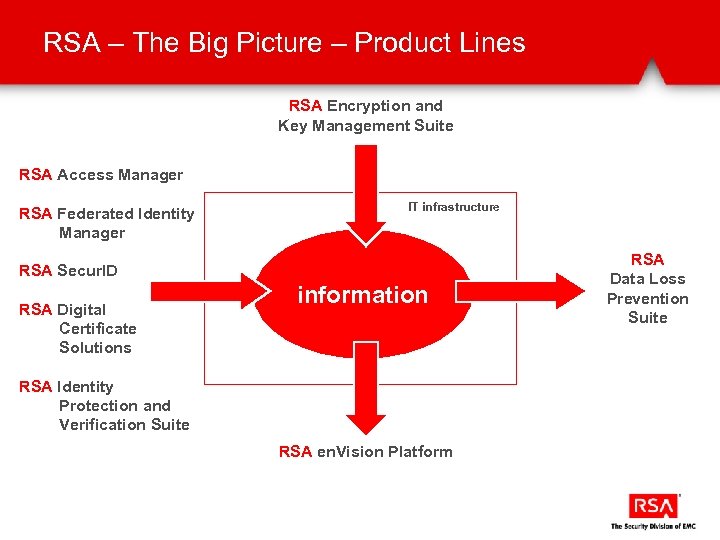
RSA – The Big Picture – Product Lines RSA Encryption and Key Management Suite RSA Access Manager RSA Federated Identity Manager IT infrastructure RSA Secur. ID RSA Digital Certificate Solutions information RSA Identity Protection and Verification Suite RSA en. Vision Platform RSA Data Loss Prevention Suite
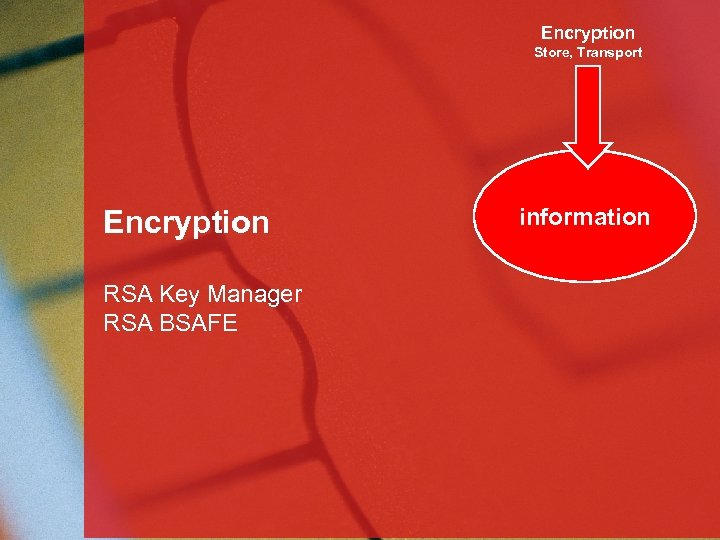
Encryption Store, Transport Encryption RSA Key Manager RSA BSAFE information

RSA Key Manager Enterprise-Wide Key Management Apps/DB FS/CMS RSA Key Manager (RKM) Policy-based Interface 1. Generate Keys 2. Securely Distribute Keys 3. Vault Keys 4. Expire / Turnover Keys 5. Monitor + Audit 13 Storage
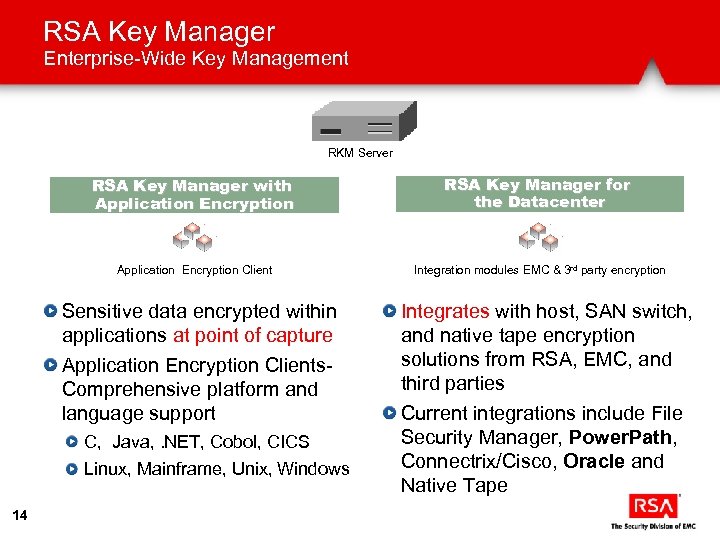
RSA Key Manager Enterprise-Wide Key Management RKM Server RSA Key Manager with Application Encryption RSA Key Manager for the Datacenter Application Encryption Client Integration modules EMC & 3 rd party encryption Sensitive data encrypted within applications at point of capture Application Encryption Clients. Comprehensive platform and language support C, Java, . NET, Cobol, CICS Linux, Mainframe, Unix, Windows 14 Integrates with host, SAN switch, and native tape encryption solutions from RSA, EMC, and third parties Current integrations include File Security Manager, Power. Path, Connectrix/Cisco, Oracle and Native Tape

Access Authentication, Authorization information Access RSA Access Manager RSA Federated Identity Manager RSA Secur. ID, RSA Authentication Manager RSA Digital Certificate Solutions RSA Identity Protection and Verification Suite
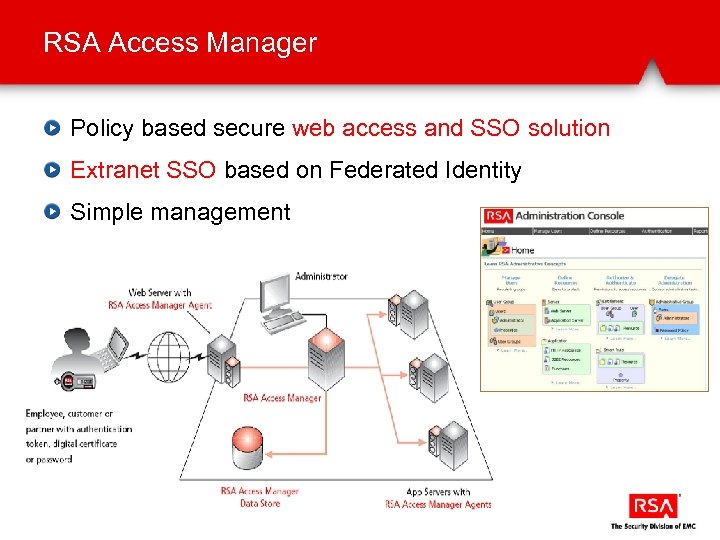
RSA Access Manager Policy based secure web access and SSO solution Extranet SSO based on Federated Identity Simple management

RSA Secur. ID – Two-Factor Authentication: “The act of identifying an individual by using any combination of something they know, something they have or something they are. ” “Something you know” = PIN, password, life question “Something you have” = Token, Smartcard, Trusted Device “Something you are” = Biometrics (fingerprint, retinal scan, etc)
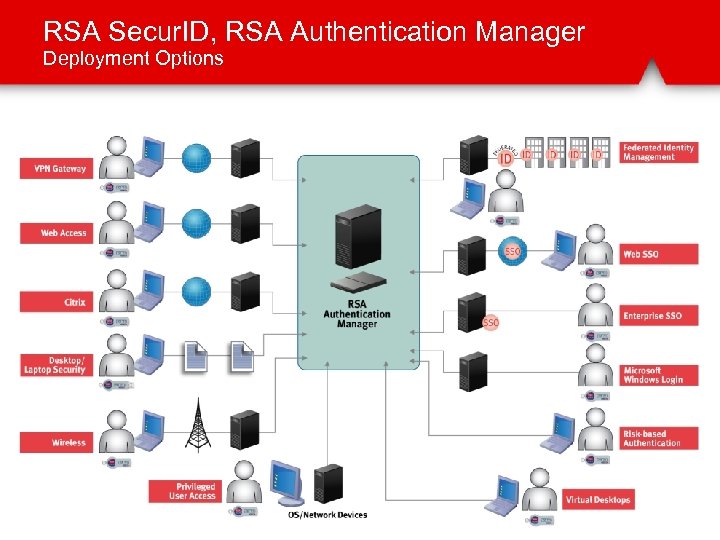
RSA Secur. ID, RSA Authentication Manager Deployment Options
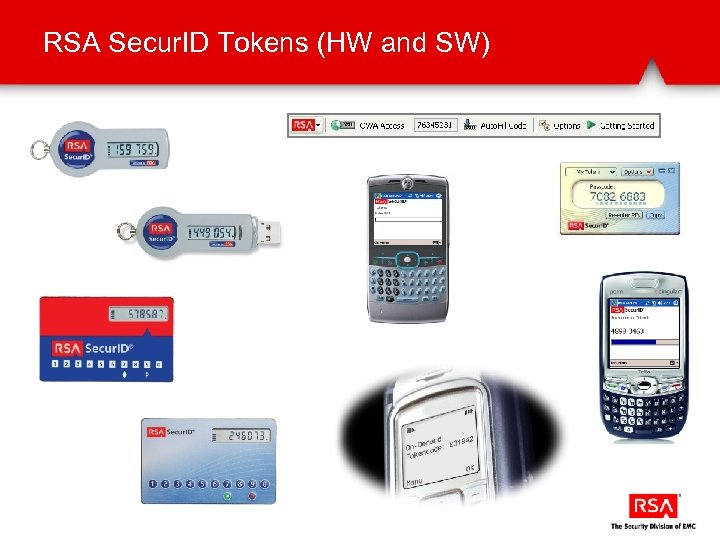
RSA Secur. ID Tokens (HW and SW)

RSA Identity Protection and Verification Suite RSA Adaptive Authentication and Transaction Monitoring (with Risk Engine) RSA e. Fraud. Network RSA Fraud. Action
information DLP RSA Data Loss Prevention Suite DLP Data Loss Prevention

RSA Data Loss Prevention Suite Your Sensitive Data are Everywhere Endpoint Network/E-mail Apps/DB FS/CMS Storage LAN Internal Employees WAN Enterprise Applications Production Database File Server Replica File Server Disk Arrays Backup Tape Disk Arrays Backup System VPN Business Analytics Remote Employees Disk Arrays Backup Disk Outsourced Dev. Partners Endpoint Network/E-mail Staging Apps/DB Collaboration & Content Mgmt Systems FS/CMS Storage
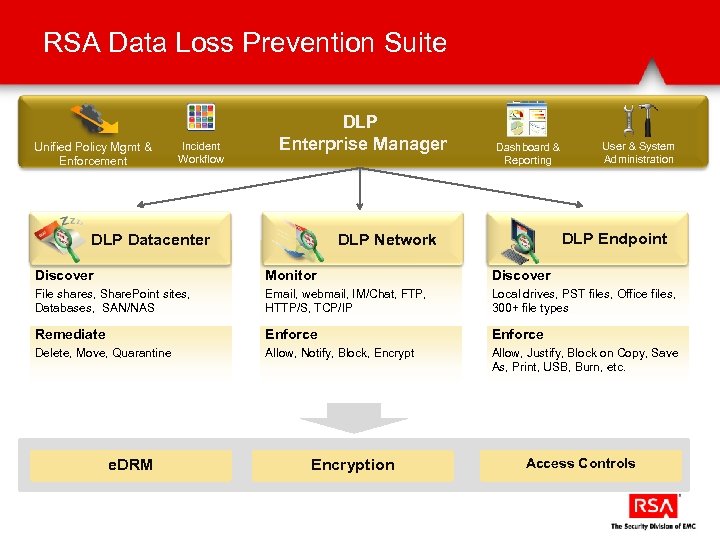
RSA Data Loss Prevention Suite Unified Policy Mgmt & Enforcement Incident Workflow DLP Enterprise Manager Dashboard & Reporting DLP Endpoint DLP Network DLP Datacenter User & System Administration Discover Monitor Discover File shares, Share. Point sites, Databases, SAN/NAS Email, webmail, IM/Chat, FTP, HTTP/S, TCP/IP Local drives, PST files, Office files, 300+ file types Remediate Enforce Delete, Move, Quarantine Allow, Notify, Block, Encrypt Allow, Justify, Block on Copy, Save As, Print, USB, Burn, etc. e. DRM Encryption Access Controls

RSA DLP with Microsoft AD RMS Current Status 1. RMS admin creates RMS templates for data protection 2. RSA DLP admin designs policies to find sensitive data and protect it using RMS Legal Department Outside law firm Others View, Edit, Print Microsoft AD RMS View No Access Find Legal Contracts Apply Legal Contracts RMS Contracts DLP Policy RSA DLP Legal department 3. RSA DLP discovers and classifies sensitive files 4. RSA DLP applies RMS controls based on policy Legal Contracts RMS Outside law firm Laptops/desktops File shares Share. Point Others 5. Users request files - RMS provides policy based access
information SIEM RSA en. Vision Platform SIEM Security Information and Event Management

RSA en. Vision 3 -in-1 SIEM Platform Simplifying Compliance Enhancing Security Optimizing IT & Network Operations Compliance reports for regulations and internal policy Real-time security alerting and analysis IT monitoring across the infrastructure Reporting Forensics Auditing Purpose-built database (IPDB) security devices Network baseline Alert / correlation Visibility RSA en. Vision Log Management platform network devices applications / databases servers storage

RSA Security Pozvánky na semináře

Další semináře, konference 14. 5. (čtvrtek): RSA Security Day • komplet přehled všech řešení 11. 6. : Soft-tronik Forum 2009: www. stforum 2009. cz • DLP and SIEM 24. 6. : RSA Security snídaně • Fraud Detection, Identity Protection (IPV)

Další semináře, konference Další plánovaná témata: • • • Šifrování dat Data Loss Prevention (DLP) Identita a zákony, tokeny a certifikáty Společné řešení RSA a Oracle Společné řešení RSA a Microsoft Stačí poslat email: ivan. svoboda@rsa. com

Conclusion
RSA – The Big Picture Encryption Store, Transport IT infrastructure Access Authentication, Authorization information SIEM Security Information and Event Management DLP Data Loss Prevention

RSA – The First Aid in Security : -) information

Otázka: Jaké jsou 3 oblasti, ve kterých je společnost RSA hodnocena jako LEADER v Gartner Magic Quadrantu? DLP SIEM Web Fraud Detection

ef5896219fe58db6cf4a2910769c81e7.ppt