9e045ced01bf9df2c482174f2c54e880.ppt
- Количество слайдов: 98
 Routing Protocols for Sensor Networks
Routing Protocols for Sensor Networks
 Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
 Acknowledgements n. E. Magistretti (U. Bologna n. J. Kulik (MIT; BBN Co. ) n. R. Italy) R. Choudhury, P. Kyasanur & N. Vaidya (UIUC) n. P. Desai (UFL) n. D. Braginsky and D. Estrin (UCLA) n. S. Hazarika, W. Chen, Y. Gong & X. Liu (UMASS) n. T. Kwon & Mjnam (SNU Korea) n. R. Peterson & D. Rus (Dartmouth C. ) n. H. C. Chung, K. Ghoshal & J. Krishna (TAMU) n. C. Tavoularis (Cornell ) n. G. Dong (Virginia U. )
Acknowledgements n. E. Magistretti (U. Bologna n. J. Kulik (MIT; BBN Co. ) n. R. Italy) R. Choudhury, P. Kyasanur & N. Vaidya (UIUC) n. P. Desai (UFL) n. D. Braginsky and D. Estrin (UCLA) n. S. Hazarika, W. Chen, Y. Gong & X. Liu (UMASS) n. T. Kwon & Mjnam (SNU Korea) n. R. Peterson & D. Rus (Dartmouth C. ) n. H. C. Chung, K. Ghoshal & J. Krishna (TAMU) n. C. Tavoularis (Cornell ) n. G. Dong (Virginia U. )
 WSN Dartmouth College
WSN Dartmouth College
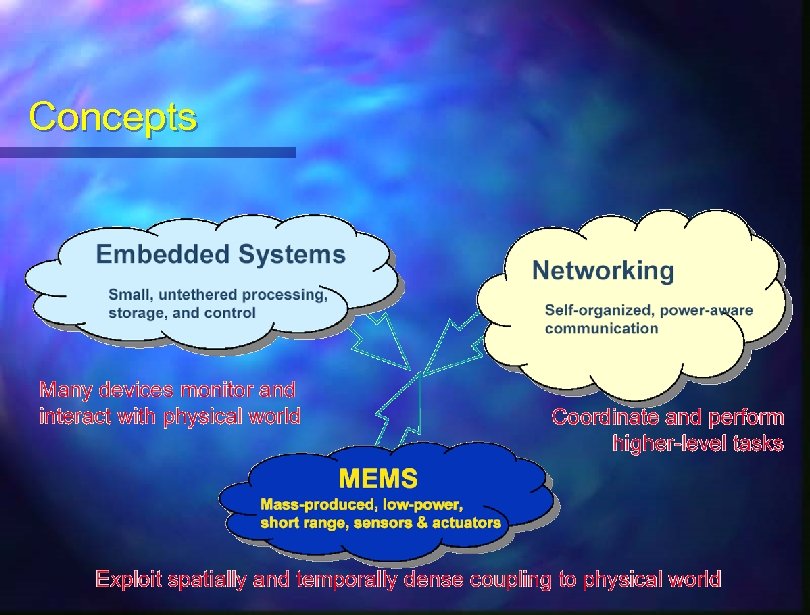 Concepts
Concepts
 Application: From UMASS Military
Application: From UMASS Military
 Environmental From UMASS
Environmental From UMASS
 Future Health Circulatory Net
Future Health Circulatory Net
 Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
 General Properties (1) n Mainly for Information Collection n Single Owner n Up to Hundreds of Thousands of Nodes n Disposable Nodes n Cheap Nodes n Security Concerns
General Properties (1) n Mainly for Information Collection n Single Owner n Up to Hundreds of Thousands of Nodes n Disposable Nodes n Cheap Nodes n Security Concerns
 General Properties (2) n Bounded Directed Stream (from/to Sink) n Somewhat Limited Computation Capability n Limited Communication Capability n Limited Power Resources n Node may not have Unique ID n Common case - Stationary Nodes
General Properties (2) n Bounded Directed Stream (from/to Sink) n Somewhat Limited Computation Capability n Limited Communication Capability n Limited Power Resources n Node may not have Unique ID n Common case - Stationary Nodes
 Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
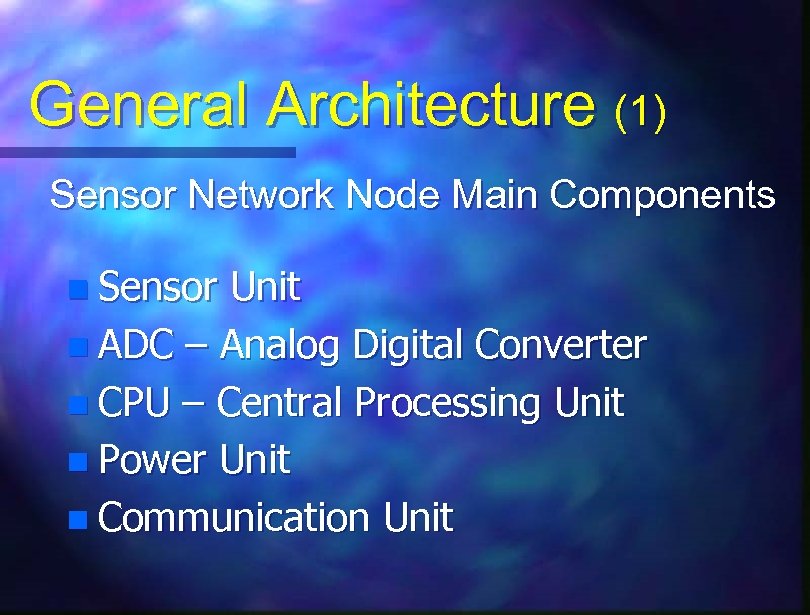 General Architecture (1) Sensor Network Node Main Components n Sensor Unit n ADC – Analog Digital Converter n CPU – Central Processing Unit n Power Unit n Communication Unit
General Architecture (1) Sensor Network Node Main Components n Sensor Unit n ADC – Analog Digital Converter n CPU – Central Processing Unit n Power Unit n Communication Unit
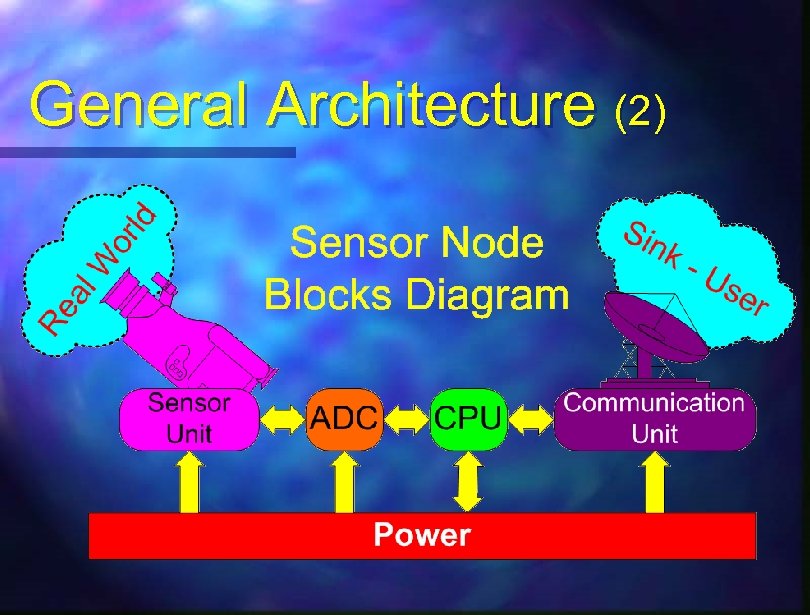 General Architecture (2)
General Architecture (2)
 General Requirements (1) n Varying Network Size n Inexpensive Nodes Equipment n Long Lifetime (Power) Þ Load-Balancing n Self-Organization n Re-tasking and Querying Capability
General Requirements (1) n Varying Network Size n Inexpensive Nodes Equipment n Long Lifetime (Power) Þ Load-Balancing n Self-Organization n Re-tasking and Querying Capability
 General Requirements (2) n Sensible Data Aggregation n Consolidation of Redundant Data n Application Awareness Þ Tradeoff Communication for Computation n Possible Mobility
General Requirements (2) n Sensible Data Aggregation n Consolidation of Redundant Data n Application Awareness Þ Tradeoff Communication for Computation n Possible Mobility
 Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
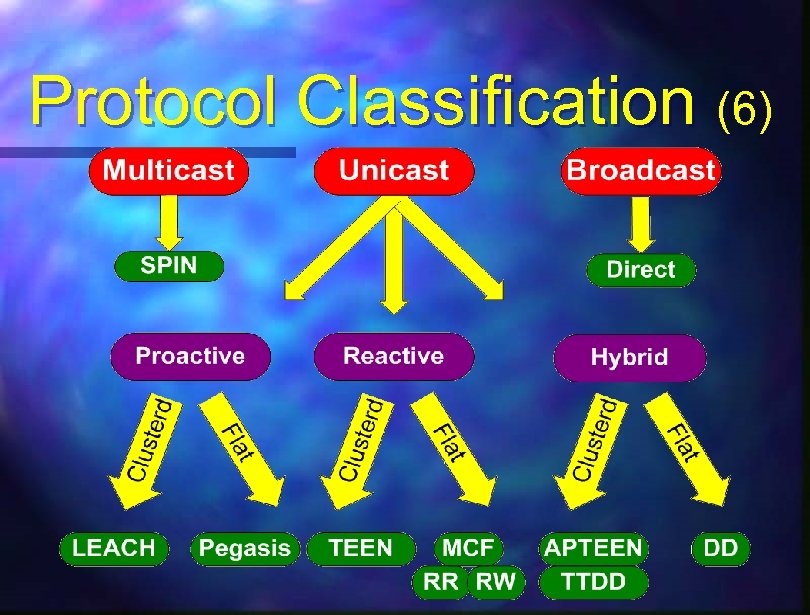
 Protocol Classification (1) n Proactive – First Compute all Routes; Then Route n Reactive – Compute Routes On-Demand n Hybrid – First Compute all Routes; Then Improve While Routing
Protocol Classification (1) n Proactive – First Compute all Routes; Then Route n Reactive – Compute Routes On-Demand n Hybrid – First Compute all Routes; Then Improve While Routing
 Protocol Classification (2) n Direct – Node and Sink Communicate Directly (Fast Drainage; Small Scale) n Flat (Equal) – Random Indirect Route (Fast Drainage Around Sink; Medium Scale) n Clustering (Hierarchical) – Route Thru Distinguished Nodes
Protocol Classification (2) n Direct – Node and Sink Communicate Directly (Fast Drainage; Small Scale) n Flat (Equal) – Random Indirect Route (Fast Drainage Around Sink; Medium Scale) n Clustering (Hierarchical) – Route Thru Distinguished Nodes
 Protocol Classification (3) n Location Aware – Nodes knows where they are n Location-Less – Nodes location is unimportant n Mobility Aware – Nodes may move – Sources; Sinks; All
Protocol Classification (3) n Location Aware – Nodes knows where they are n Location-Less – Nodes location is unimportant n Mobility Aware – Nodes may move – Sources; Sinks; All
 Protocol Classification (4) n Unicast – One-to-One Message Passing n Multicast (actually Local Broadcast) – Node-to-Neighbors Message Passing n Broadcast – Full-Mesh – Source to Everyone
Protocol Classification (4) n Unicast – One-to-One Message Passing n Multicast (actually Local Broadcast) – Node-to-Neighbors Message Passing n Broadcast – Full-Mesh – Source to Everyone
 Protocol Classification (5) Query Models: n Historical Queries: Analysis of historical data “What was the watermark 2 h ago in the southeast? ” n One-time Queries: Snapshot view “What is the watermark in the southeast? ” n Persistent Queries: Monitoring over time “Report the watermark in the southeast for the next 4 h”
Protocol Classification (5) Query Models: n Historical Queries: Analysis of historical data “What was the watermark 2 h ago in the southeast? ” n One-time Queries: Snapshot view “What is the watermark in the southeast? ” n Persistent Queries: Monitoring over time “Report the watermark in the southeast for the next 4 h”
 Protocol Classification (6)
Protocol Classification (6)
 Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
Agenda n. General Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
 Low Energy Adaptive Clustering Hierarchy Protocol Highlights 1 - LEACH – Discussed … n Self-Organizing – Adaptive Clustering n Cluster-Heads elect themselves – Now – “Random Round-Robin” Future – Power-Based Probability n Nodes die in random n Stationary Sink n Localized Coordination n Data Fusion
Low Energy Adaptive Clustering Hierarchy Protocol Highlights 1 - LEACH – Discussed … n Self-Organizing – Adaptive Clustering n Cluster-Heads elect themselves – Now – “Random Round-Robin” Future – Power-Based Probability n Nodes die in random n Stationary Sink n Localized Coordination n Data Fusion
 Low Energy Adaptive Clustering Hierarchy Main Drawbacks 1 - LEACH (2) n “Hot Spot” Problem (Nodes on a path from an event-congested area to the sink may drain) n Inadequate for Time-Critical Applications n Stationary Sink – Maybe Unpractical n Basic Algorithm assumes any node can communicate with sink – limited scale
Low Energy Adaptive Clustering Hierarchy Main Drawbacks 1 - LEACH (2) n “Hot Spot” Problem (Nodes on a path from an event-congested area to the sink may drain) n Inadequate for Time-Critical Applications n Stationary Sink – Maybe Unpractical n Basic Algorithm assumes any node can communicate with sink – limited scale
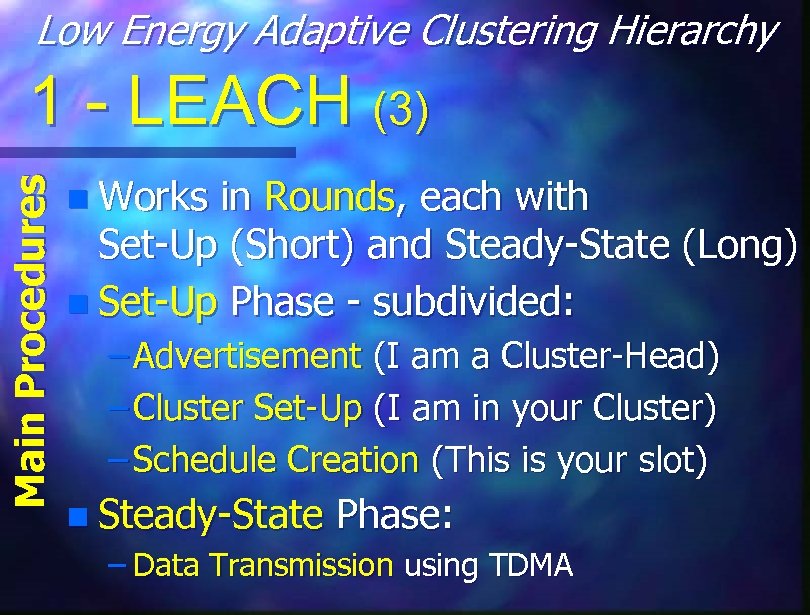 Low Energy Adaptive Clustering Hierarchy Main Procedures 1 - LEACH (3) n Works in Rounds, each with Set-Up (Short) and Steady-State (Long) n Set-Up Phase - subdivided: – Advertisement (I am a Cluster-Head) – Cluster Set-Up (I am in your Cluster) – Schedule Creation (This is your slot) n Steady-State Phase: – Data Transmission using TDMA
Low Energy Adaptive Clustering Hierarchy Main Procedures 1 - LEACH (3) n Works in Rounds, each with Set-Up (Short) and Steady-State (Long) n Set-Up Phase - subdivided: – Advertisement (I am a Cluster-Head) – Cluster Set-Up (I am in your Cluster) – Schedule Creation (This is your slot) n Steady-State Phase: – Data Transmission using TDMA
 Low Energy Adaptive Clustering Hierarchy Main Procedures 1 - LEACH (4) Everyone uses the same channel n Different clusters use different CDMA codes n Code chosen in random n Cluster-Head communicate with Sink n Can be extended to Hierarchical Clustering n
Low Energy Adaptive Clustering Hierarchy Main Procedures 1 - LEACH (4) Everyone uses the same channel n Different clusters use different CDMA codes n Code chosen in random n Cluster-Head communicate with Sink n Can be extended to Hierarchical Clustering n
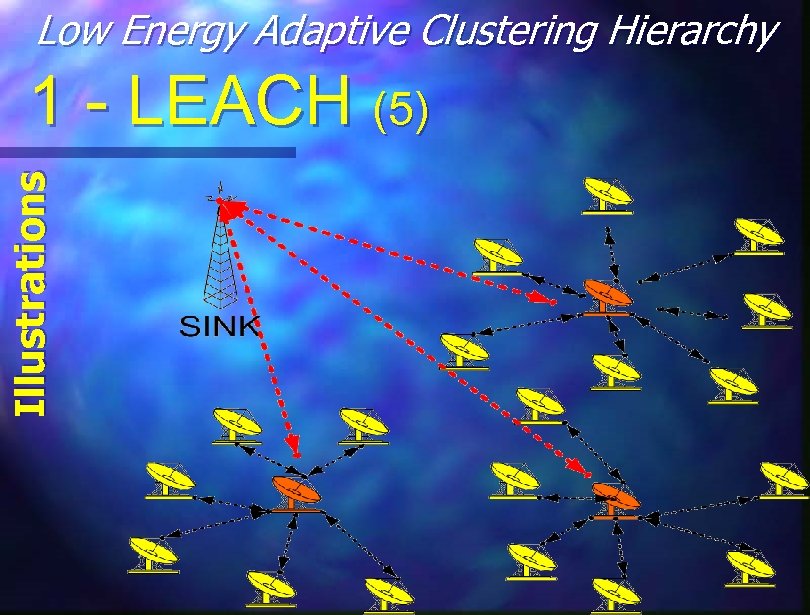 Low Energy Adaptive Clustering Hierarchy Illustrations 1 - LEACH (5)
Low Energy Adaptive Clustering Hierarchy Illustrations 1 - LEACH (5)
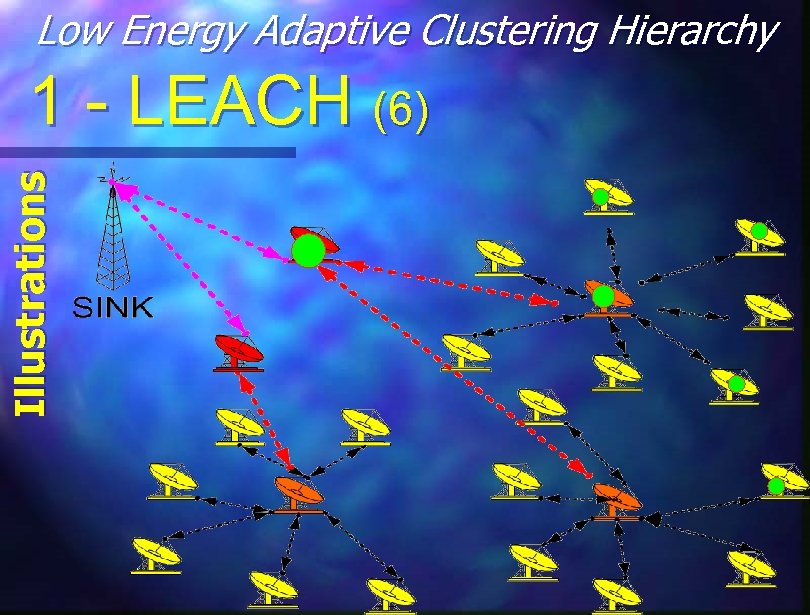 Low Energy Adaptive Clustering Hierarchy Illustrations 1 - LEACH (6)
Low Energy Adaptive Clustering Hierarchy Illustrations 1 - LEACH (6)
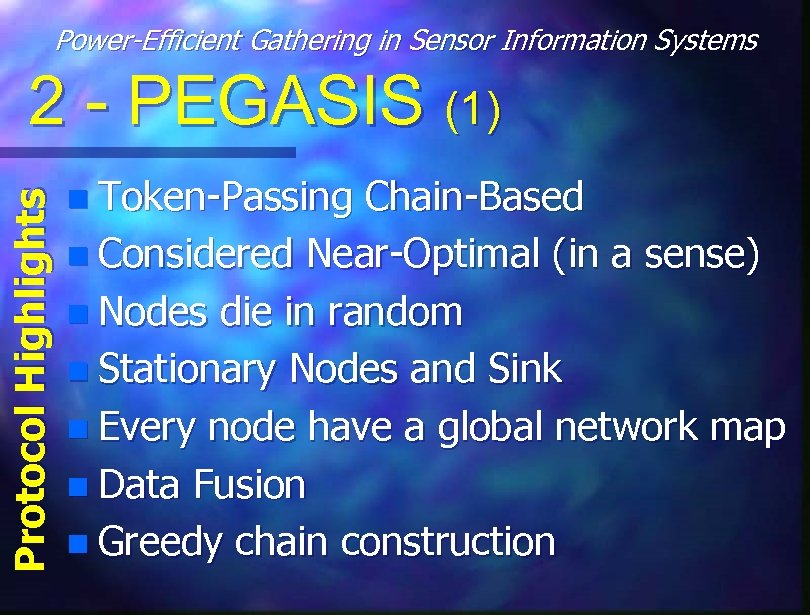 Power-Efficient Gathering in Sensor Information Systems Protocol Highlights 2 - PEGASIS (1) n Token-Passing Chain-Based n Considered Near-Optimal (in a sense) n Nodes die in random n Stationary Nodes and Sink n Every node have a global network map n Data Fusion n Greedy chain construction
Power-Efficient Gathering in Sensor Information Systems Protocol Highlights 2 - PEGASIS (1) n Token-Passing Chain-Based n Considered Near-Optimal (in a sense) n Nodes die in random n Stationary Nodes and Sink n Every node have a global network map n Data Fusion n Greedy chain construction
 Power-Efficient Gathering in Sensor Information Systems Main Drawbacks 2 - PEGASIS (2) n Stationary Nodes n Global Information Limited Scale: n Information travels many nodes n Assumes any node can communicate with sink
Power-Efficient Gathering in Sensor Information Systems Main Drawbacks 2 - PEGASIS (2) n Stationary Nodes n Global Information Limited Scale: n Information travels many nodes n Assumes any node can communicate with sink
 Power-Efficient Gathering in Sensor Information Systems Main Procedures 2 - PEGASIS (3) n Greedy Algorithm Construct Chain – Start at a node far from sink and gather everyone neighbor by neighbor n Node i (mod N) is the leader in round i Nodes passes token thru the chain to leader from both sides n Each node fuse its data with the rest n Leader transmit to sink n
Power-Efficient Gathering in Sensor Information Systems Main Procedures 2 - PEGASIS (3) n Greedy Algorithm Construct Chain – Start at a node far from sink and gather everyone neighbor by neighbor n Node i (mod N) is the leader in round i Nodes passes token thru the chain to leader from both sides n Each node fuse its data with the rest n Leader transmit to sink n
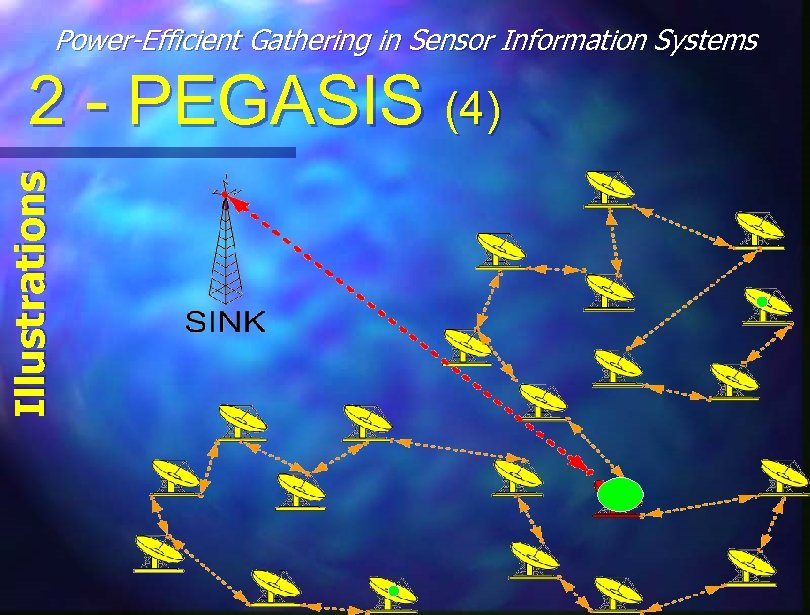 Power-Efficient Gathering in Sensor Information Systems Illustrations 2 - PEGASIS (4)
Power-Efficient Gathering in Sensor Information Systems Illustrations 2 - PEGASIS (4)
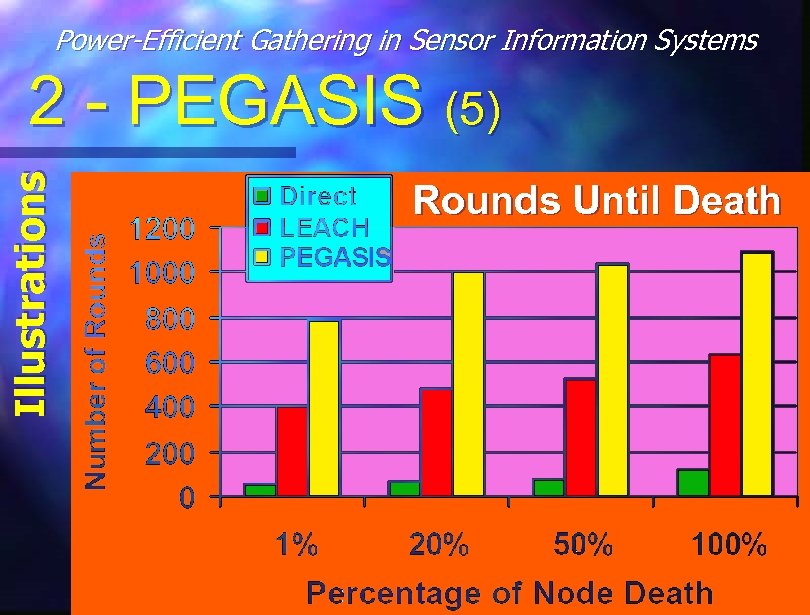 Power-Efficient Gathering in Sensor Information Systems Illustrations 2 - PEGASIS (5) Rounds Until Death
Power-Efficient Gathering in Sensor Information Systems Illustrations 2 - PEGASIS (5) Rounds Until Death
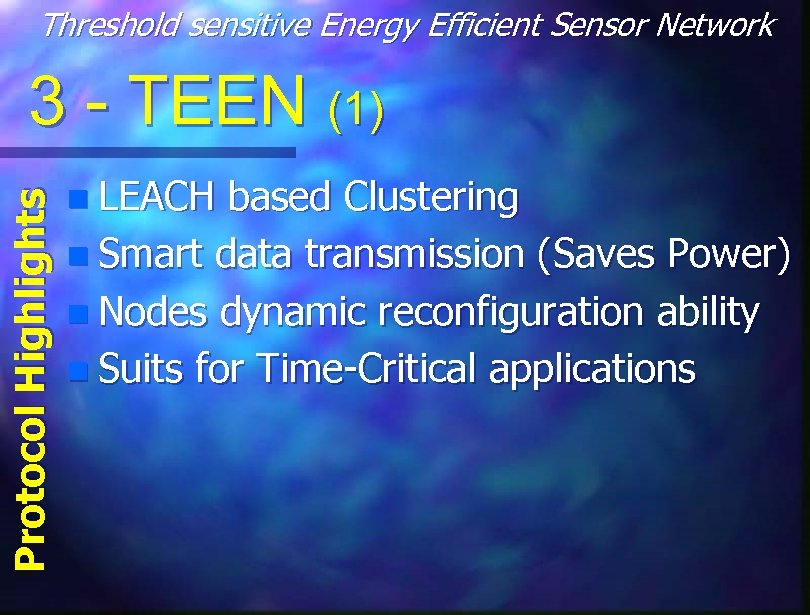 Threshold sensitive Energy Efficient Sensor Network Protocol Highlights 3 - TEEN (1) n LEACH based Clustering n Smart data transmission (Saves Power) n Nodes dynamic reconfiguration ability n Suits for Time-Critical applications
Threshold sensitive Energy Efficient Sensor Network Protocol Highlights 3 - TEEN (1) n LEACH based Clustering n Smart data transmission (Saves Power) n Nodes dynamic reconfiguration ability n Suits for Time-Critical applications
 Threshold sensitive Energy Efficient Sensor Network Main Drawbacks 3 - TEEN (2) n “Hot Spot” Problem n Cluster-Heads need to listen constantly n Wasted time-slots n Can’t distinguish dead nodes n Other LEACH problems…
Threshold sensitive Energy Efficient Sensor Network Main Drawbacks 3 - TEEN (2) n “Hot Spot” Problem n Cluster-Heads need to listen constantly n Wasted time-slots n Can’t distinguish dead nodes n Other LEACH problems…
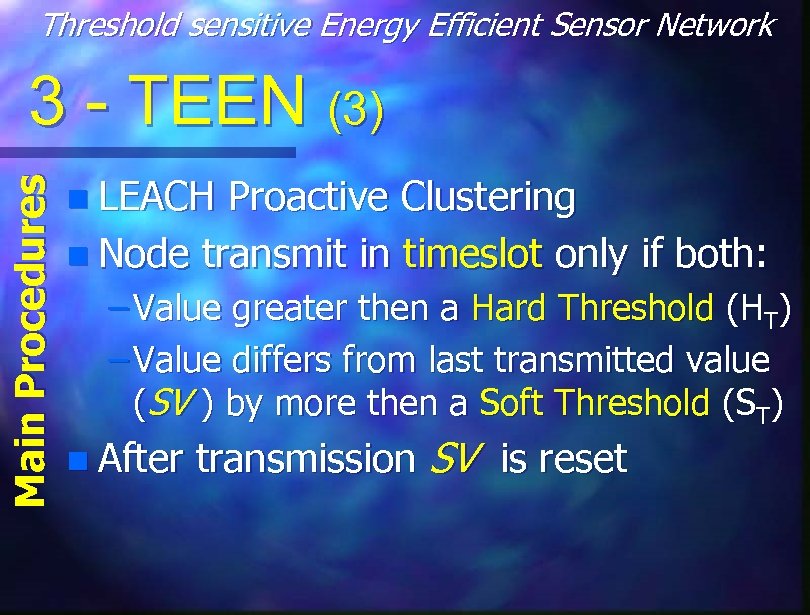 Threshold sensitive Energy Efficient Sensor Network Main Procedures 3 - TEEN (3) n LEACH Proactive Clustering n Node transmit in timeslot only if both: – Value greater then a Hard Threshold (HT) – Value differs from last transmitted value (SV ) by more then a Soft Threshold (ST) n After transmission SV is reset
Threshold sensitive Energy Efficient Sensor Network Main Procedures 3 - TEEN (3) n LEACH Proactive Clustering n Node transmit in timeslot only if both: – Value greater then a Hard Threshold (HT) – Value differs from last transmitted value (SV ) by more then a Soft Threshold (ST) n After transmission SV is reset
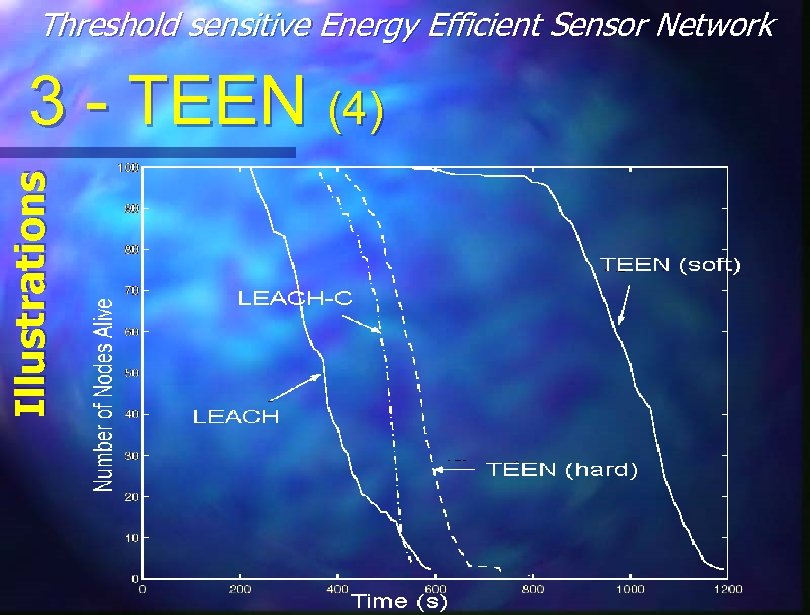 Threshold sensitive Energy Efficient Sensor Network Illustrations 3 - TEEN (4)
Threshold sensitive Energy Efficient Sensor Network Illustrations 3 - TEEN (4)
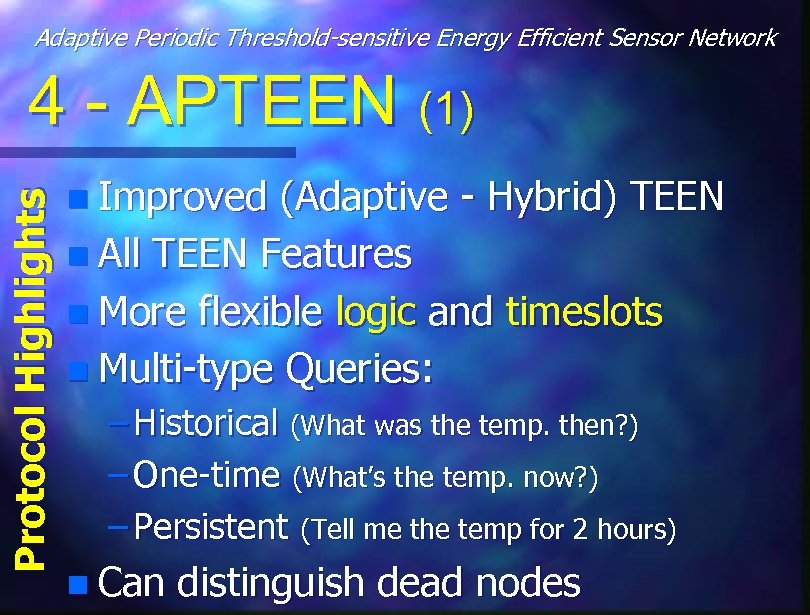 Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Protocol Highlights 4 - APTEEN (1) n Improved (Adaptive - Hybrid) TEEN n All TEEN Features n More flexible logic and timeslots n Multi-type Queries: – Historical (What was the temp. then? ) – One-time (What’s the temp. now? ) – Persistent (Tell me the temp for 2 hours) n Can distinguish dead nodes
Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Protocol Highlights 4 - APTEEN (1) n Improved (Adaptive - Hybrid) TEEN n All TEEN Features n More flexible logic and timeslots n Multi-type Queries: – Historical (What was the temp. then? ) – One-time (What’s the temp. now? ) – Persistent (Tell me the temp for 2 hours) n Can distinguish dead nodes
 Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Main Drawbacks 4 - APTEEN (2) n LEACH problems… n Complex logic
Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Main Drawbacks 4 - APTEEN (2) n LEACH problems… n Complex logic
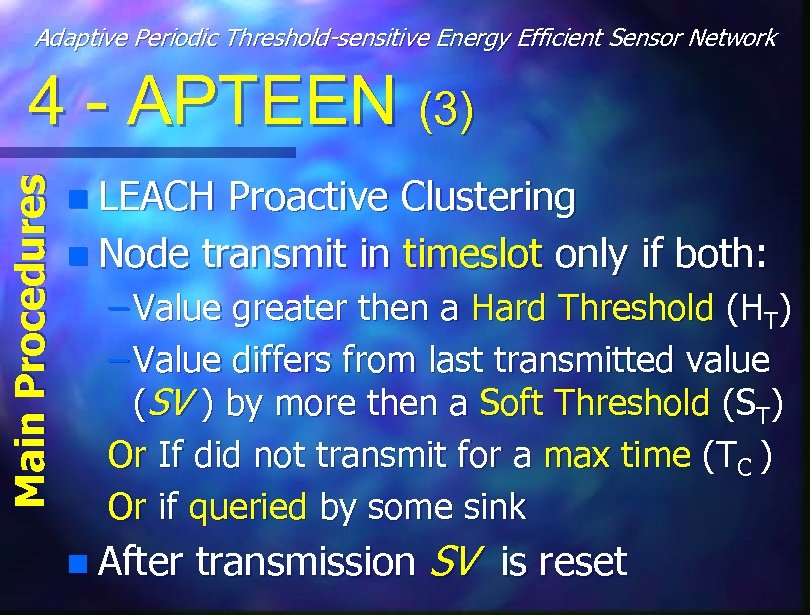 Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Main Procedures 4 - APTEEN (3) n LEACH Proactive Clustering n Node transmit in timeslot only if both: – Value greater then a Hard Threshold (HT) – Value differs from last transmitted value (SV ) by more then a Soft Threshold (ST) Or If did not transmit for a max time (TC ) Or if queried by some sink n After transmission SV is reset
Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Main Procedures 4 - APTEEN (3) n LEACH Proactive Clustering n Node transmit in timeslot only if both: – Value greater then a Hard Threshold (HT) – Value differs from last transmitted value (SV ) by more then a Soft Threshold (ST) Or If did not transmit for a max time (TC ) Or if queried by some sink n After transmission SV is reset
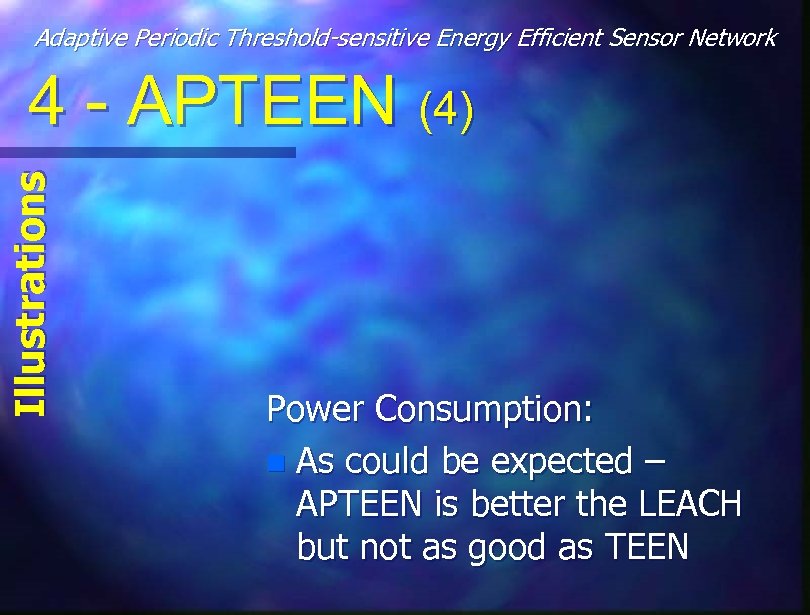 Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Illustrations 4 - APTEEN (4) Power Consumption: n As could be expected – APTEEN is better the LEACH but not as good as TEEN
Adaptive Periodic Threshold-sensitive Energy Efficient Sensor Network Illustrations 4 - APTEEN (4) Power Consumption: n As could be expected – APTEEN is better the LEACH but not as good as TEEN
 Sensor Protocol for Information via Negotiation Protocol Highlights 5 - SPIN (1) Network-wide Broadcast Limited by Negotiation and using Local Communication n Flooding problems solved: n n Implosion – same data from many neighbors n Detection of overlapping regions n Excessive resources consumption (Blindness) n Needs only Localized Information n Data Fusion n Two main protocols SPIN-PP & SPIN-BC
Sensor Protocol for Information via Negotiation Protocol Highlights 5 - SPIN (1) Network-wide Broadcast Limited by Negotiation and using Local Communication n Flooding problems solved: n n Implosion – same data from many neighbors n Detection of overlapping regions n Excessive resources consumption (Blindness) n Needs only Localized Information n Data Fusion n Two main protocols SPIN-PP & SPIN-BC
 Sensor Protocol for Information via Negotiation Main Drawbacks 5 - SPIN (2) n Broadcast - Limited Scale – every node handles O(n) messages n Data is updated throughout network – unnecessary in many cases n Network lifetime - not clear n High degree nodes = High power needs
Sensor Protocol for Information via Negotiation Main Drawbacks 5 - SPIN (2) n Broadcast - Limited Scale – every node handles O(n) messages n Data is updated throughout network – unnecessary in many cases n Network lifetime - not clear n High degree nodes = High power needs
 Sensor Protocol for Information via Negotiation Main Procedures 5 - SPIN (3) SPIN-PP (Point-to-Point Communication) n Data is described by meta-data ADV msg. n Node has data Þ sends ADV to neighbors n If neighbor do not have data Þ sends REQ n Node responds by sending the DATA n This process continues around the network n Nodes may aggregate their data to ADV n In a Lossy Network ADV may be repeated periodically and REQ if not answered
Sensor Protocol for Information via Negotiation Main Procedures 5 - SPIN (3) SPIN-PP (Point-to-Point Communication) n Data is described by meta-data ADV msg. n Node has data Þ sends ADV to neighbors n If neighbor do not have data Þ sends REQ n Node responds by sending the DATA n This process continues around the network n Nodes may aggregate their data to ADV n In a Lossy Network ADV may be repeated periodically and REQ if not answered
 Sensor Protocol for Information via Negotiation Main Procedures 5 - SPIN (4) SPIN-BC (Local Broadcast Communication) n ADV and DATA sending like PP (but in B. C. ) n Since only one REQ answer is needed, any node waits a random interval and B. C. REQ only if none was received yet. n The rest – like SPIN-PP
Sensor Protocol for Information via Negotiation Main Procedures 5 - SPIN (4) SPIN-BC (Local Broadcast Communication) n ADV and DATA sending like PP (but in B. C. ) n Since only one REQ answer is needed, any node waits a random interval and B. C. REQ only if none was received yet. n The rest – like SPIN-PP
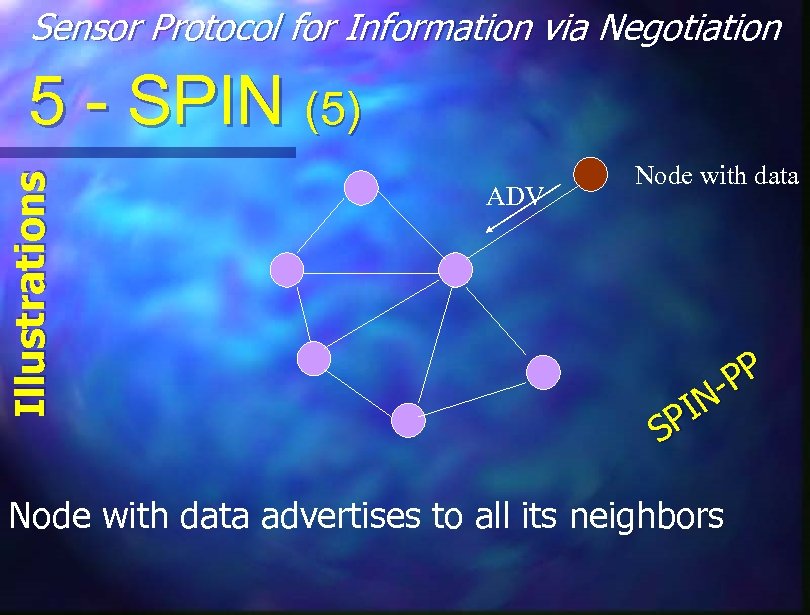 Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) ADV Node with data PP IN SP Node with data advertises to all its neighbors
Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) ADV Node with data PP IN SP Node with data advertises to all its neighbors
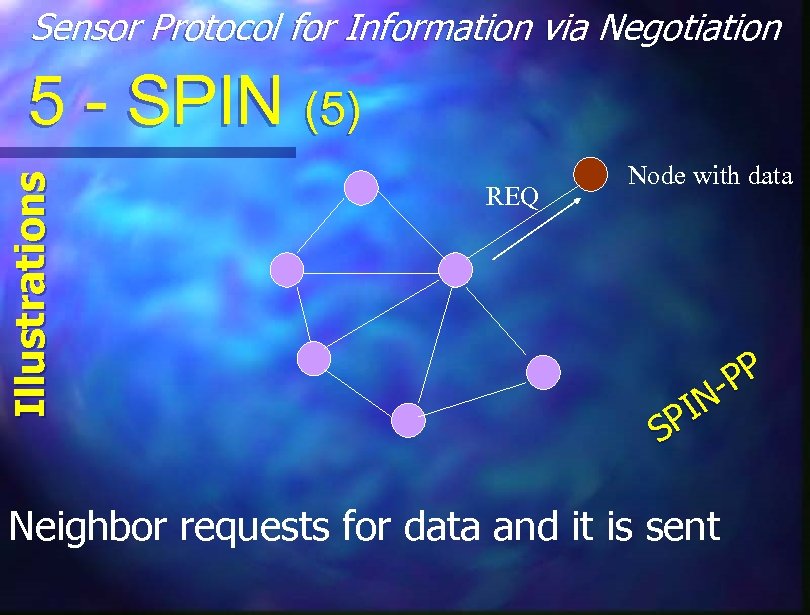 Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) REQ Node with data PP IN SP Neighbor requests for data and it is sent
Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) REQ Node with data PP IN SP Neighbor requests for data and it is sent
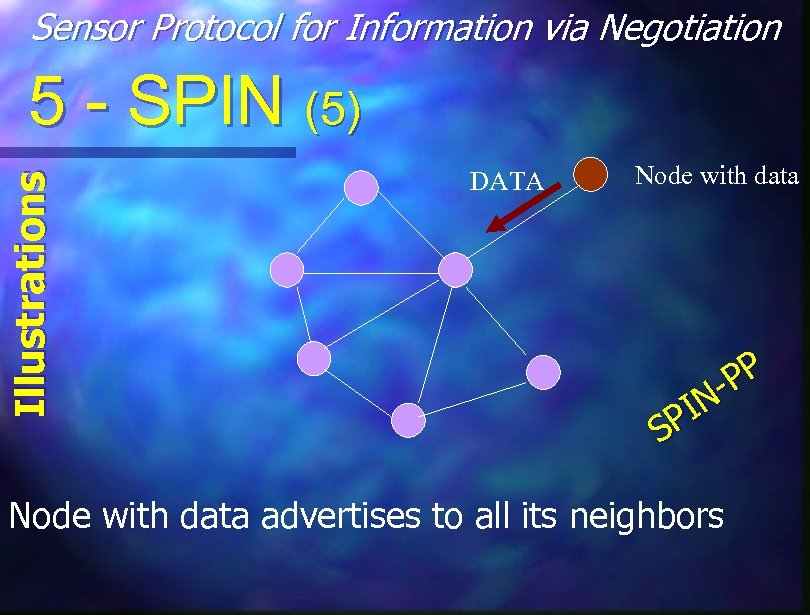 Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) DATA Node with data PP IN SP Node with data advertises to all its neighbors
Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) DATA Node with data PP IN SP Node with data advertises to all its neighbors
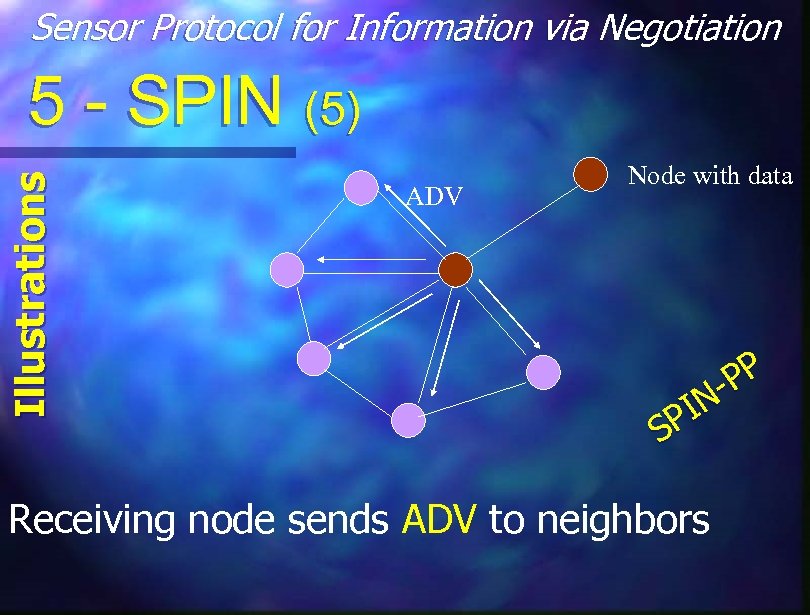 Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) ADV Node with data PP IN SP Receiving node sends ADV to neighbors
Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) ADV Node with data PP IN SP Receiving node sends ADV to neighbors
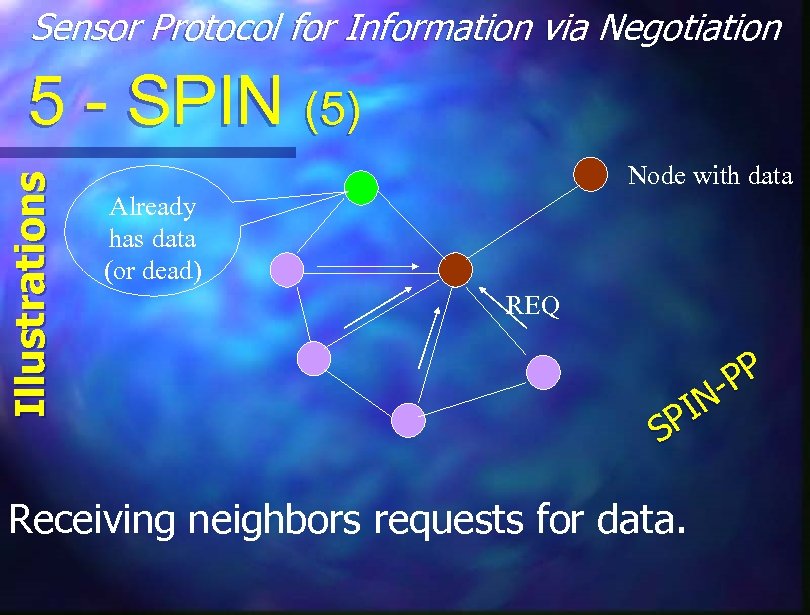 Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) Node with data Already has data (or dead) REQ PP IN SP Receiving neighbors requests for data.
Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) Node with data Already has data (or dead) REQ PP IN SP Receiving neighbors requests for data.
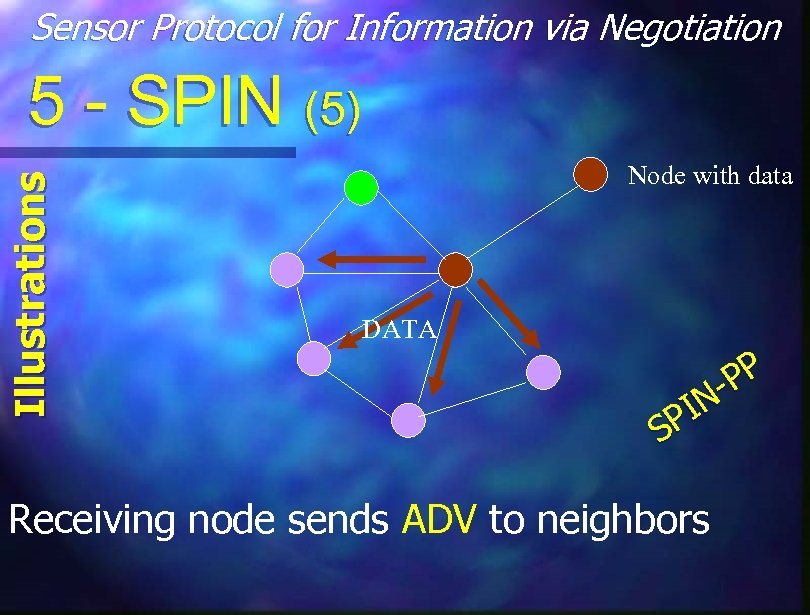 Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) Node with data DATA PP IN SP Receiving node sends ADV to neighbors
Sensor Protocol for Information via Negotiation Illustrations 5 - SPIN (5) Node with data DATA PP IN SP Receiving node sends ADV to neighbors
 Directed Diffusion Protocol Highlights 6 - DD (1) n Hybrid Data Centric Routing – Looking for Named Data Query–Response Model n Performs Better than Flooding n n Robust and Fault Tolerant (bypass faults) n Localized Interactions n Data Fusion - Application Specific Filters
Directed Diffusion Protocol Highlights 6 - DD (1) n Hybrid Data Centric Routing – Looking for Named Data Query–Response Model n Performs Better than Flooding n n Robust and Fault Tolerant (bypass faults) n Localized Interactions n Data Fusion - Application Specific Filters
 Directed Diffusion Main Drawbacks 6 - DD (2) n “Hot Spot” Problem near sink n Periodic Broadcasts of “Interest” Reduces Network Lifetime n Trade-off: Energy Efficiency vs. Robustness and Scalability n Complex Data Aggregation may Lead to Expensive Node
Directed Diffusion Main Drawbacks 6 - DD (2) n “Hot Spot” Problem near sink n Periodic Broadcasts of “Interest” Reduces Network Lifetime n Trade-off: Energy Efficiency vs. Robustness and Scalability n Complex Data Aggregation may Lead to Expensive Node
 Directed Diffusion Main Procedures 6 - DD (3) A Query (Interest) is Broadcasted by a node (sink) n Query Reaches Relevant Sensor Sources n This Sets-Up Exploratory Gradients n Once Data is Available in a Source it is Sent Back via Reinforced Path n Failing Links / Nodes are being Gradually Bypassed n
Directed Diffusion Main Procedures 6 - DD (3) A Query (Interest) is Broadcasted by a node (sink) n Query Reaches Relevant Sensor Sources n This Sets-Up Exploratory Gradients n Once Data is Available in a Source it is Sent Back via Reinforced Path n Failing Links / Nodes are being Gradually Bypassed n
 Directed Diffusion Illustrations 6 - DD (4) Source CLASS_KEY IS INTEREST_CLASS LONGITUDE_KEY GE 10 LONGITUDE_KEY LE 50 LATITUDE_KEY GE 100 LATITUDE_KEY LE 120 SENSOR EQ MOVEMENT INTENSITY GE 0. 6 CONFIDENCE GE 0. 7 INTERVAL IS 10 EXPIRE_TIME IS 100 Sink Interest = Interrogation Gradient = Who is interested
Directed Diffusion Illustrations 6 - DD (4) Source CLASS_KEY IS INTEREST_CLASS LONGITUDE_KEY GE 10 LONGITUDE_KEY LE 50 LATITUDE_KEY GE 100 LATITUDE_KEY LE 120 SENSOR EQ MOVEMENT INTENSITY GE 0. 6 CONFIDENCE GE 0. 7 INTERVAL IS 10 EXPIRE_TIME IS 100 Sink Interest = Interrogation Gradient = Who is interested
 Directed Diffusion Illustrations 6 - DD (4) Filter. Attr. Vec CLASS_KEY EQ DATA_CLASS SENSOR EQ MOVEMENT INTENSITY GE 0. 7 Source 3. add. Filter (Fil. Attr. Vec, Filter. Callback) 1. subscribe (Interest. Attr. Vec, Callback) 2. subscribe (Attr. Vec, Appl. Callback) Interest. Attr. Vec CLASS_KEY EQ INTEREST_CLASS LONGITUDE_KEY IS 35 LATITUDE_KEY IS 110 SENSOR IS MOVEMENT Sink Interest = Interrogation Gradient = Who is interested
Directed Diffusion Illustrations 6 - DD (4) Filter. Attr. Vec CLASS_KEY EQ DATA_CLASS SENSOR EQ MOVEMENT INTENSITY GE 0. 7 Source 3. add. Filter (Fil. Attr. Vec, Filter. Callback) 1. subscribe (Interest. Attr. Vec, Callback) 2. subscribe (Attr. Vec, Appl. Callback) Interest. Attr. Vec CLASS_KEY EQ INTEREST_CLASS LONGITUDE_KEY IS 35 LATITUDE_KEY IS 110 SENSOR IS MOVEMENT Sink Interest = Interrogation Gradient = Who is interested
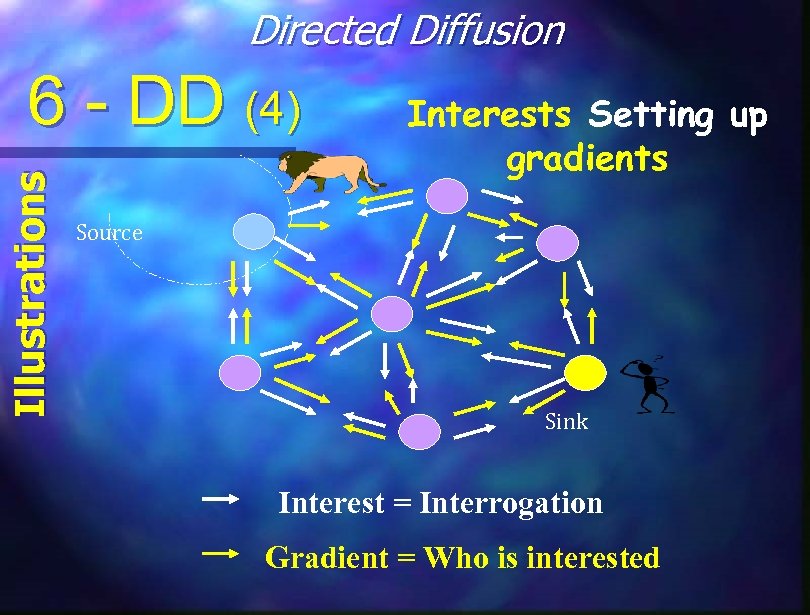 Directed Diffusion Illustrations 6 - DD (4) Interests Setting up gradients Source Sink Interest = Interrogation Gradient = Who is interested
Directed Diffusion Illustrations 6 - DD (4) Interests Setting up gradients Source Sink Interest = Interrogation Gradient = Who is interested
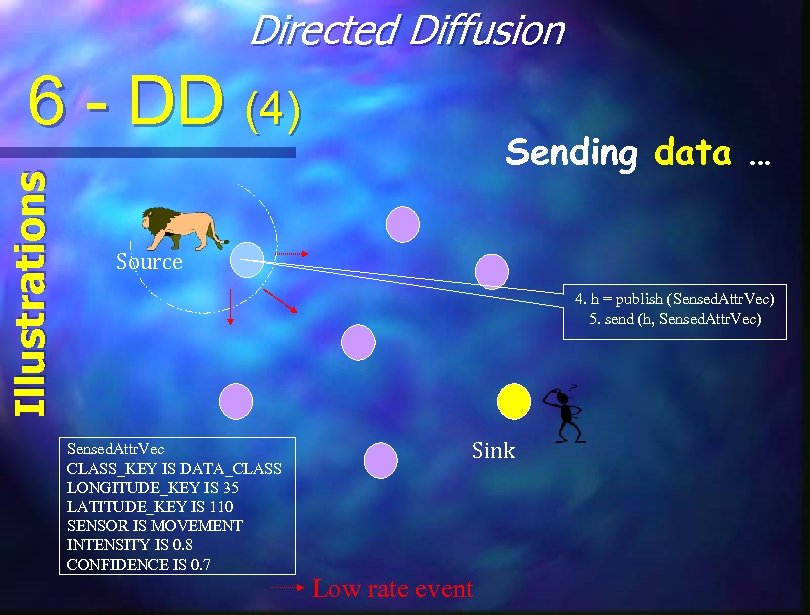 Directed Diffusion Illustrations 6 - DD (4) Sending data … Source 4. h = publish (Sensed. Attr. Vec) 5. send (h, Sensed. Attr. Vec) Sensed. Attr. Vec CLASS_KEY IS DATA_CLASS LONGITUDE_KEY IS 35 LATITUDE_KEY IS 110 SENSOR IS MOVEMENT INTENSITY IS 0. 8 CONFIDENCE IS 0. 7 Sink Low rate event
Directed Diffusion Illustrations 6 - DD (4) Sending data … Source 4. h = publish (Sensed. Attr. Vec) 5. send (h, Sensed. Attr. Vec) Sensed. Attr. Vec CLASS_KEY IS DATA_CLASS LONGITUDE_KEY IS 35 LATITUDE_KEY IS 110 SENSOR IS MOVEMENT INTENSITY IS 0. 8 CONFIDENCE IS 0. 7 Sink Low rate event
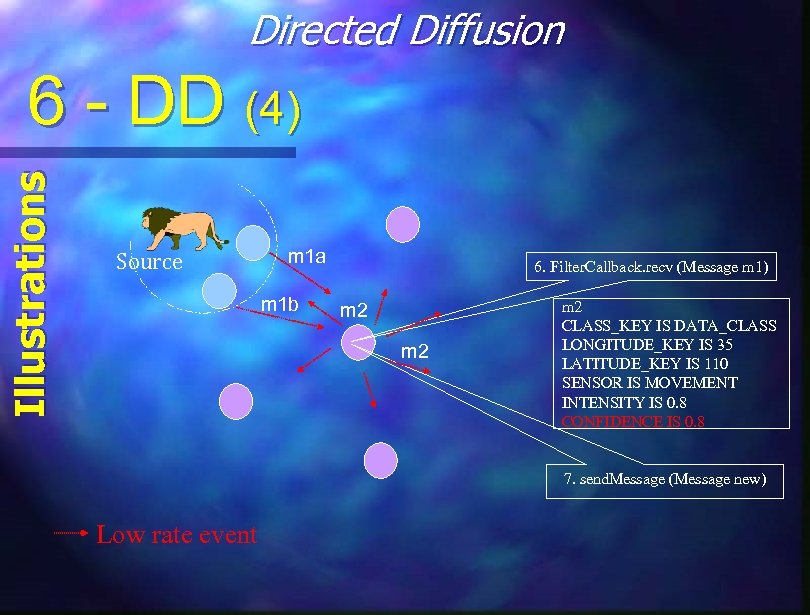 Directed Diffusion Illustrations 6 - DD (4) Source m 1 a m 1 b 6. Filter. Callback. recv (Message m 1) m 2 m 2 CLASS_KEY IS DATA_CLASS LONGITUDE_KEY IS 35 LATITUDE_KEY IS 110 SENSOR IS MOVEMENT INTENSITY IS 0. 8 CONFIDENCE IS 0. 8 7. send. Message (Message new) Low rate event
Directed Diffusion Illustrations 6 - DD (4) Source m 1 a m 1 b 6. Filter. Callback. recv (Message m 1) m 2 m 2 CLASS_KEY IS DATA_CLASS LONGITUDE_KEY IS 35 LATITUDE_KEY IS 110 SENSOR IS MOVEMENT INTENSITY IS 0. 8 CONFIDENCE IS 0. 8 7. send. Message (Message new) Low rate event
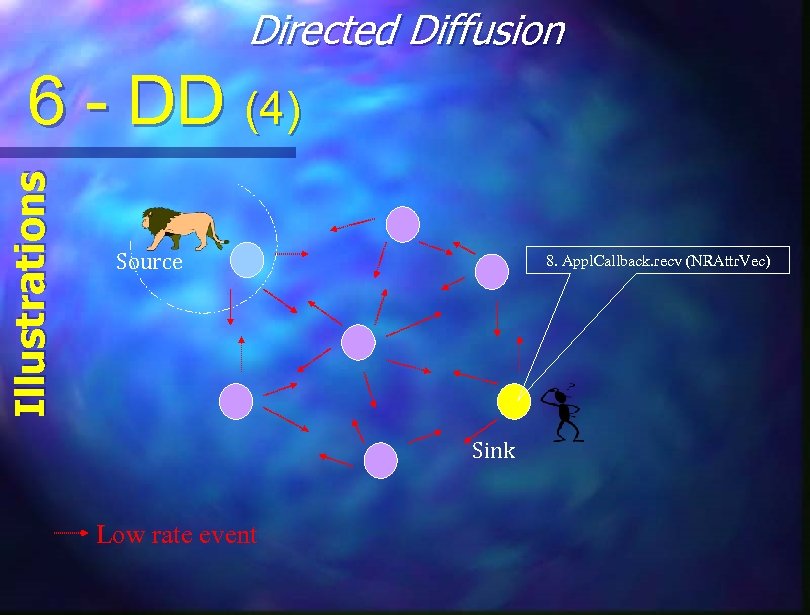 Directed Diffusion Illustrations 6 - DD (4) Source 8. Appl. Callback. recv (NRAttr. Vec) Sink Low rate event
Directed Diffusion Illustrations 6 - DD (4) Source 8. Appl. Callback. recv (NRAttr. Vec) Sink Low rate event
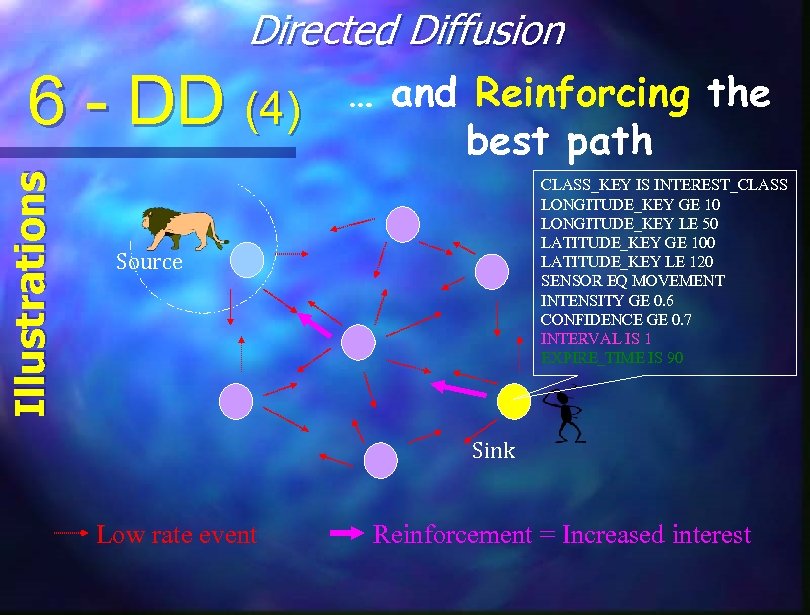 Directed Diffusion Illustrations 6 - DD (4) … and Reinforcing the best path CLASS_KEY IS INTEREST_CLASS LONGITUDE_KEY GE 10 LONGITUDE_KEY LE 50 LATITUDE_KEY GE 100 LATITUDE_KEY LE 120 SENSOR EQ MOVEMENT INTENSITY GE 0. 6 CONFIDENCE GE 0. 7 INTERVAL IS 1 EXPIRE_TIME IS 90 Source Sink Low rate event Reinforcement = Increased interest
Directed Diffusion Illustrations 6 - DD (4) … and Reinforcing the best path CLASS_KEY IS INTEREST_CLASS LONGITUDE_KEY GE 10 LONGITUDE_KEY LE 50 LATITUDE_KEY GE 100 LATITUDE_KEY LE 120 SENSOR EQ MOVEMENT INTENSITY GE 0. 6 CONFIDENCE GE 0. 7 INTERVAL IS 1 EXPIRE_TIME IS 90 Source Sink Low rate event Reinforcement = Increased interest
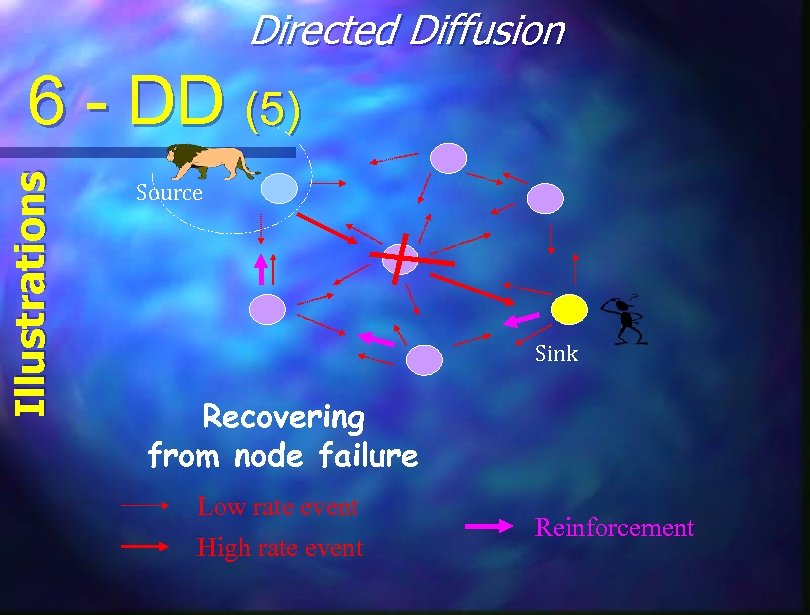 Directed Diffusion Illustrations 6 - DD (5) Source Sink Recovering from node failure Low rate event High rate event Reinforcement
Directed Diffusion Illustrations 6 - DD (5) Source Sink Recovering from node failure Low rate event High rate event Reinforcement
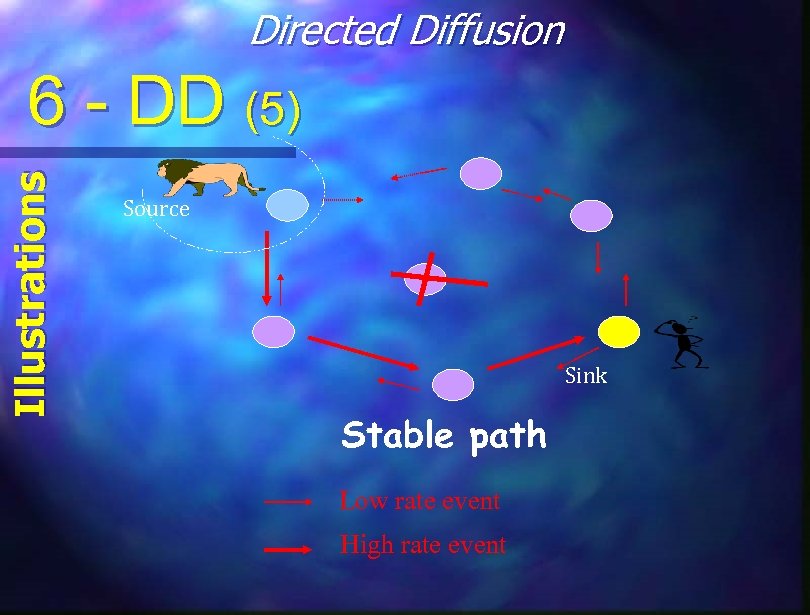 Directed Diffusion Illustrations 6 - DD (5) Source Sink Stable path Low rate event High rate event
Directed Diffusion Illustrations 6 - DD (5) Source Sink Stable path Low rate event High rate event
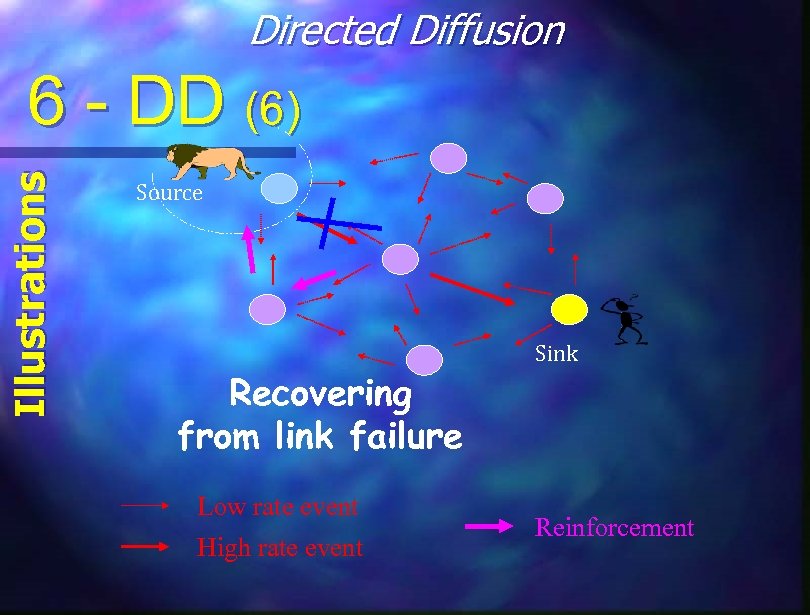 Directed Diffusion Illustrations 6 - DD (6) Source Recovering from link failure Low rate event High rate event Sink Reinforcement
Directed Diffusion Illustrations 6 - DD (6) Source Recovering from link failure Low rate event High rate event Sink Reinforcement
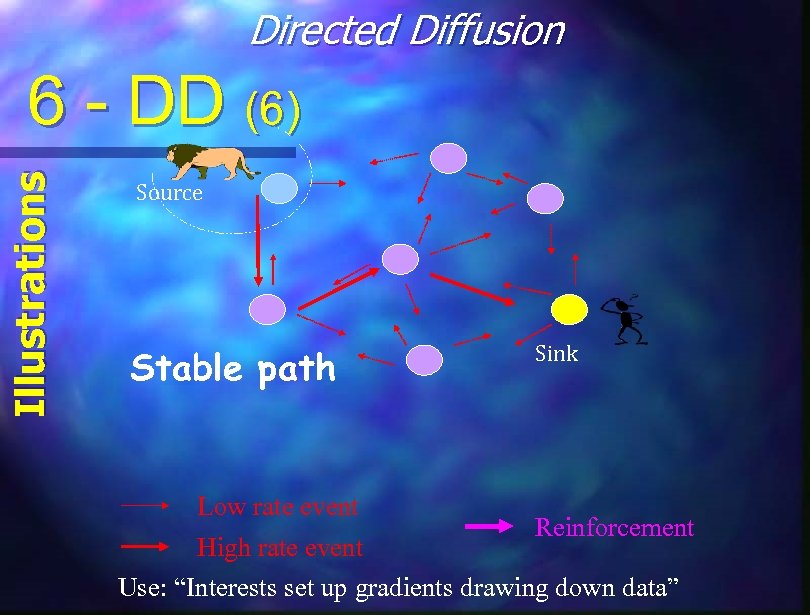 Directed Diffusion Illustrations 6 - DD (6) Source Stable path Low rate event Sink Reinforcement High rate event Use: “Interests set up gradients drawing down data”
Directed Diffusion Illustrations 6 - DD (6) Source Stable path Low rate event Sink Reinforcement High rate event Use: “Interests set up gradients drawing down data”
 Minimum Cost Forwarding Protocol Highlights 7 - MCF (1) Cost-Field min Cost from Node to Sink on Optimal Path n Slop-Down the Cost-Fields to Get to Sink n Minimize Multiple Transmissions using Back-Off Algorithm Based on Node Cost n Localized Communication n
Minimum Cost Forwarding Protocol Highlights 7 - MCF (1) Cost-Field min Cost from Node to Sink on Optimal Path n Slop-Down the Cost-Fields to Get to Sink n Minimize Multiple Transmissions using Back-Off Algorithm Based on Node Cost n Localized Communication n
 Minimum Cost Forwarding Main Drawbacks 7 - MCF (2) n High Time Complexity (due to back-off) n Many Sinks – Large Cost Tables n Cost Field Set-Up Time O(N) n No Load-Balancing
Minimum Cost Forwarding Main Drawbacks 7 - MCF (2) n High Time Complexity (due to back-off) n Many Sinks – Large Cost Tables n Cost Field Set-Up Time O(N) n No Load-Balancing
 Minimum Cost Forwarding Main Procedures 7 - MCF (3) Broadcast ADV msg. and get Answers from all Sinks Þ Create Cost-Fields n Calculate Back-Off Timer Proportional to Cost per each Sink n Needed Information Sent thru Slop n If no ACK until Timer Expires – Resend ADV n
Minimum Cost Forwarding Main Procedures 7 - MCF (3) Broadcast ADV msg. and get Answers from all Sinks Þ Create Cost-Fields n Calculate Back-Off Timer Proportional to Cost per each Sink n Needed Information Sent thru Slop n If no ACK until Timer Expires – Resend ADV n
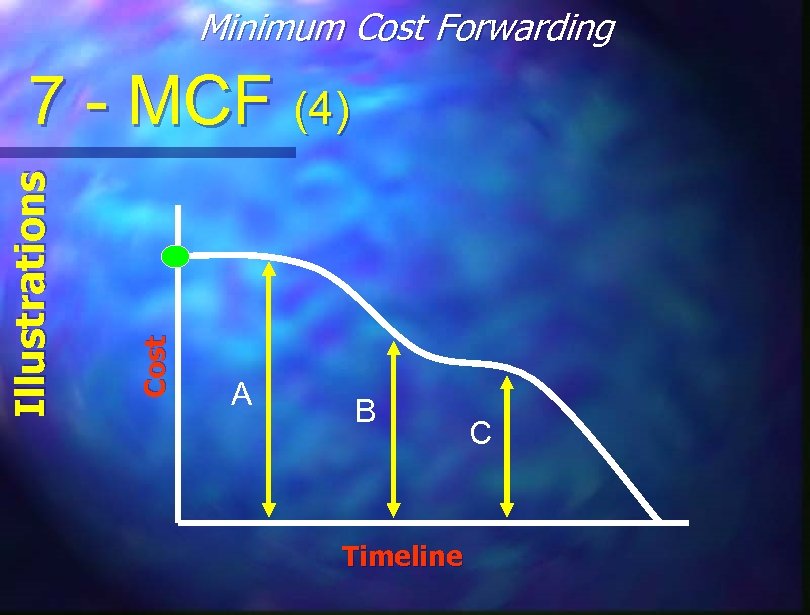 Minimum Cost Forwarding Cost Illustrations 7 - MCF (4) A B Timeline C
Minimum Cost Forwarding Cost Illustrations 7 - MCF (4) A B Timeline C
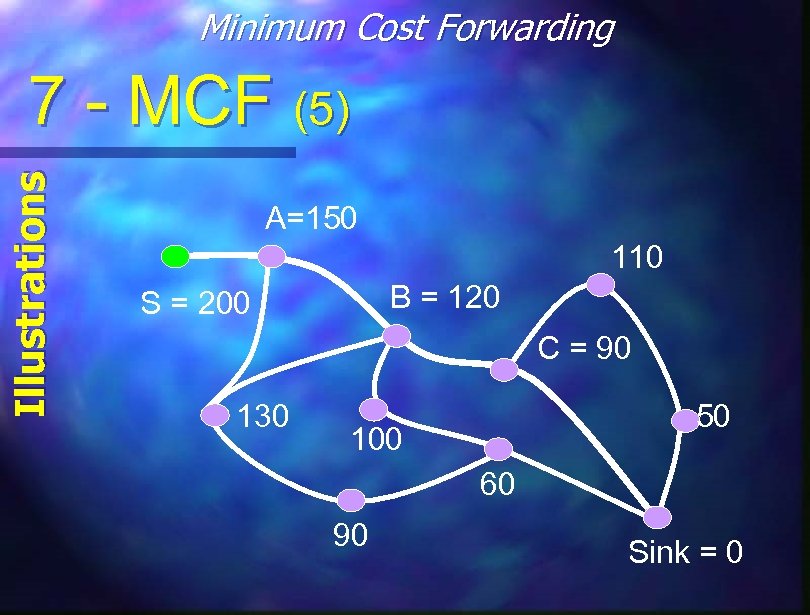 Minimum Cost Forwarding Illustrations 7 - MCF (5) A=150 110 B = 120 S = 200 C = 90 130 50 100 60 90 Sink = 0
Minimum Cost Forwarding Illustrations 7 - MCF (5) A=150 110 B = 120 S = 200 C = 90 130 50 100 60 90 Sink = 0
 Two-Tier Data Dissemination Protocol Highlights 8 - TTDD (1) n Grid Structure Clustering n Stationary n Location-Aware Nodes Mission Aware – Infrequent Changes n Greedy Geographical Forwarding – Building Grid n Localized Communication
Two-Tier Data Dissemination Protocol Highlights 8 - TTDD (1) n Grid Structure Clustering n Stationary n Location-Aware Nodes Mission Aware – Infrequent Changes n Greedy Geographical Forwarding – Building Grid n Localized Communication
 Two-Tier Data Dissemination Main Drawbacks 8 - TTDD (2) n No Mobile Sensors n Requires Location Information n Grid Nodes may Drain
Two-Tier Data Dissemination Main Drawbacks 8 - TTDD (2) n No Mobile Sensors n Requires Location Information n Grid Nodes may Drain
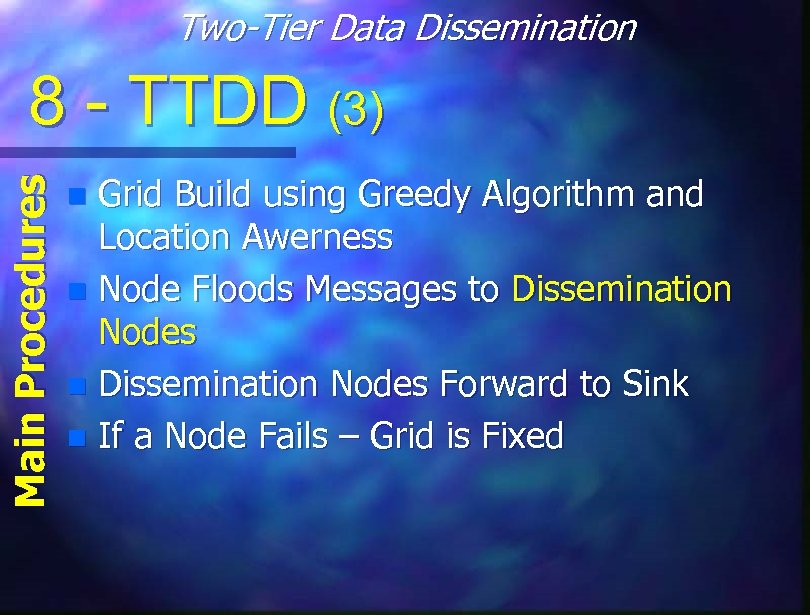 Two-Tier Data Dissemination Main Procedures 8 - TTDD (3) Grid Build using Greedy Algorithm and Location Awerness n Node Floods Messages to Dissemination Nodes n Dissemination Nodes Forward to Sink n If a Node Fails – Grid is Fixed n
Two-Tier Data Dissemination Main Procedures 8 - TTDD (3) Grid Build using Greedy Algorithm and Location Awerness n Node Floods Messages to Dissemination Nodes n Dissemination Nodes Forward to Sink n If a Node Fails – Grid is Fixed n
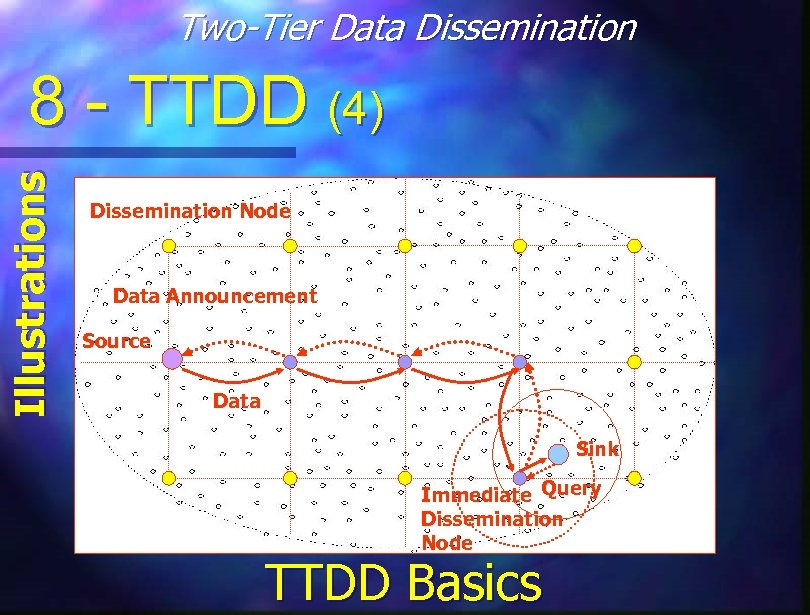 Two-Tier Data Dissemination Illustrations 8 - TTDD (4) Dissemination Node Data Announcement Source Data Sink Immediate Query Dissemination Node TTDD Basics
Two-Tier Data Dissemination Illustrations 8 - TTDD (4) Dissemination Node Data Announcement Source Data Sink Immediate Query Dissemination Node TTDD Basics
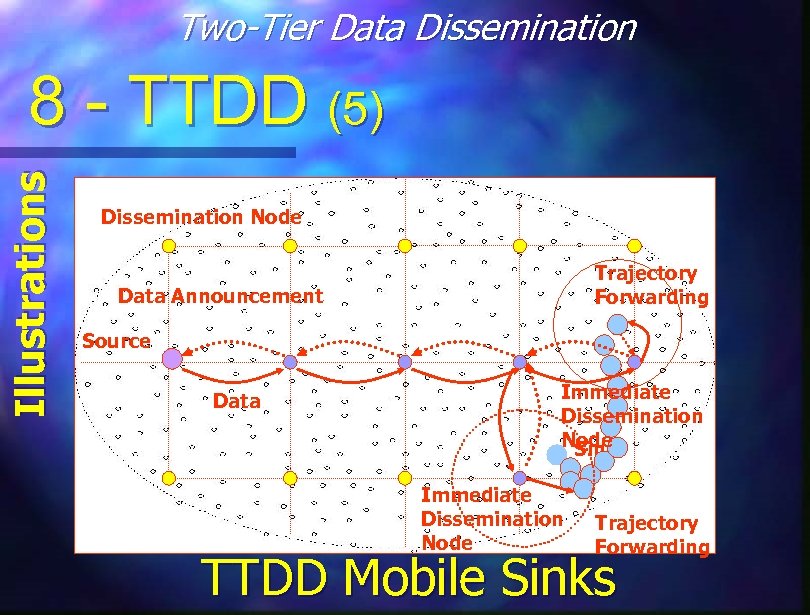 Two-Tier Data Dissemination Illustrations 8 - TTDD (5) Dissemination Node Trajectory Forwarding Data Announcement Source Data Immediate Dissemination Node Sink Immediate Dissemination Node Trajectory Forwarding TTDD Mobile Sinks
Two-Tier Data Dissemination Illustrations 8 - TTDD (5) Dissemination Node Trajectory Forwarding Data Announcement Source Data Immediate Dissemination Node Sink Immediate Dissemination Node Trajectory Forwarding TTDD Mobile Sinks
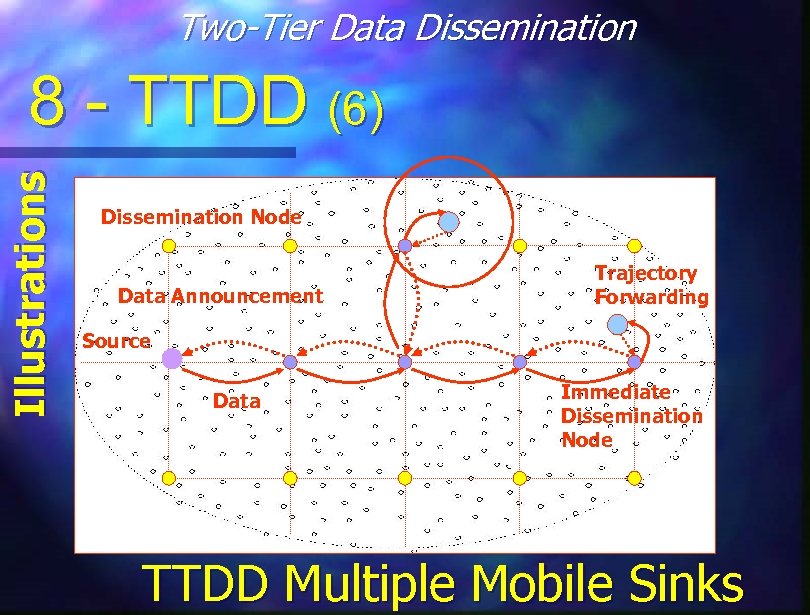 Two-Tier Data Dissemination Illustrations 8 - TTDD (6) Dissemination Node Data Announcement Trajectory Forwarding Source Data Immediate Dissemination Node TTDD Multiple Mobile Sinks
Two-Tier Data Dissemination Illustrations 8 - TTDD (6) Dissemination Node Data Announcement Trajectory Forwarding Source Data Immediate Dissemination Node TTDD Multiple Mobile Sinks
 Random Walks Protocol Highlights 9 - RW (1) Finding a Random Walk over a Grid n Multi-path Routing Different Routes n Load Balancing at Different Times n Large Scale Networks n Nodes Assumed to be Mostly Stationary n No Location Information Needed n Little State Information n Localized Communication n
Random Walks Protocol Highlights 9 - RW (1) Finding a Random Walk over a Grid n Multi-path Routing Different Routes n Load Balancing at Different Times n Large Scale Networks n Nodes Assumed to be Mostly Stationary n No Location Information Needed n Little State Information n Localized Communication n
 Random Walks Main Drawbacks 9 - RW (2) n Topology may not be Practical (Nodes are Assumed to be Located at Cubic Grid Junctions)
Random Walks Main Drawbacks 9 - RW (2) n Topology may not be Practical (Nodes are Assumed to be Located at Cubic Grid Junctions)
 Random Walks Main Procedures 9 - RW (3) - RSG Regular Static Graphs n Find coordinates differences (Dx, Dy) using Distributed Bellman Ford (local comm. ) n For every node compute probability of moving on X and Y (By the diagonal to the destination) n On each node move to a adjacent one on X or Y using that probability. Adjust near end. All Paths together draws a straight “Banana”
Random Walks Main Procedures 9 - RW (3) - RSG Regular Static Graphs n Find coordinates differences (Dx, Dy) using Distributed Bellman Ford (local comm. ) n For every node compute probability of moving on X and Y (By the diagonal to the destination) n On each node move to a adjacent one on X or Y using that probability. Adjust near end. All Paths together draws a straight “Banana”
 Random Walks Main Procedures 9 - RW (4) - ISG Irregular Static Graphs (Some dead nodes) n Same as RSG but… n If one adjacent node is missing – go to the other (with p=1). n If both are missing – go to a neighbor whose B-F distance to the destination is strictly smaller than the current node (This will create a detour). n (Could optimize by not getting to that node…).
Random Walks Main Procedures 9 - RW (4) - ISG Irregular Static Graphs (Some dead nodes) n Same as RSG but… n If one adjacent node is missing – go to the other (with p=1). n If both are missing – go to a neighbor whose B-F distance to the destination is strictly smaller than the current node (This will create a detour). n (Could optimize by not getting to that node…).
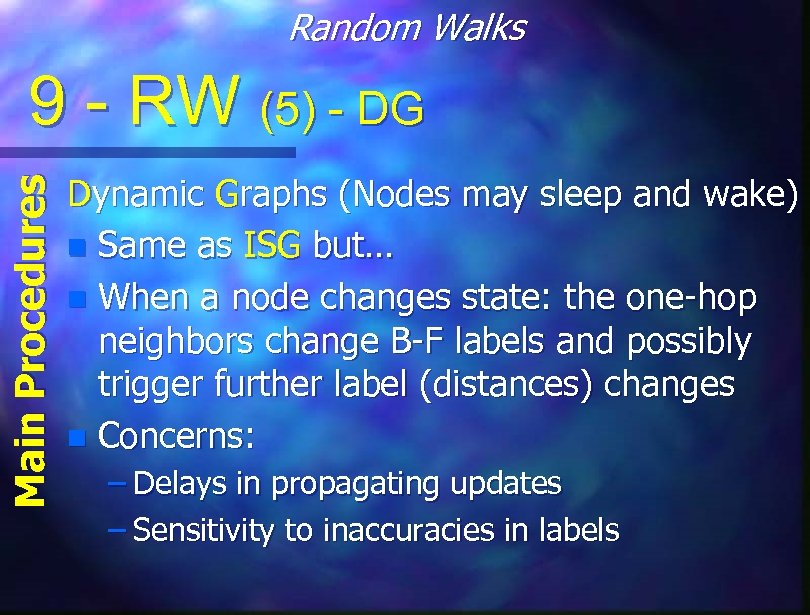 Random Walks Main Procedures 9 - RW (5) - DG Dynamic Graphs (Nodes may sleep and wake) n Same as ISG but… n When a node changes state: the one-hop neighbors change B-F labels and possibly trigger further label (distances) changes n Concerns: – Delays in propagating updates – Sensitivity to inaccuracies in labels
Random Walks Main Procedures 9 - RW (5) - DG Dynamic Graphs (Nodes may sleep and wake) n Same as ISG but… n When a node changes state: the one-hop neighbors change B-F labels and possibly trigger further label (distances) changes n Concerns: – Delays in propagating updates – Sensitivity to inaccuracies in labels
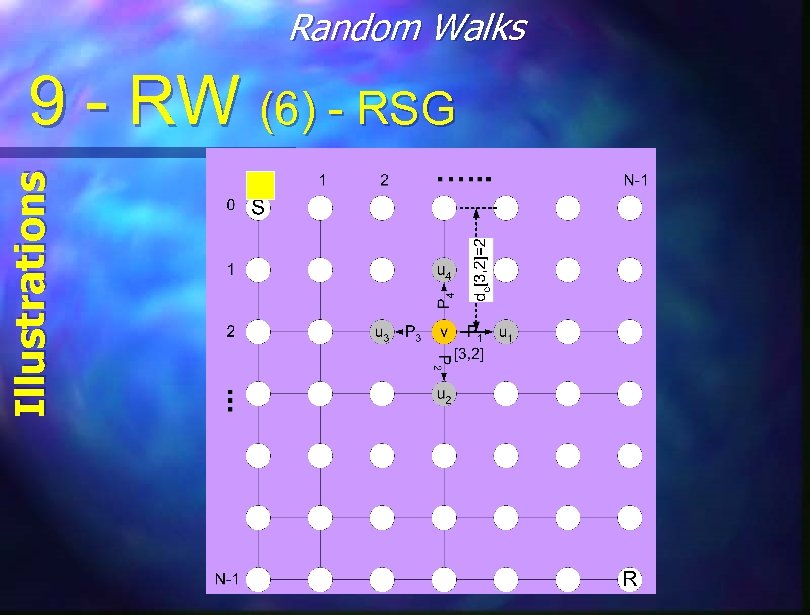 Random Walks Illustrations 9 - RW (6) - RSG
Random Walks Illustrations 9 - RW (6) - RSG
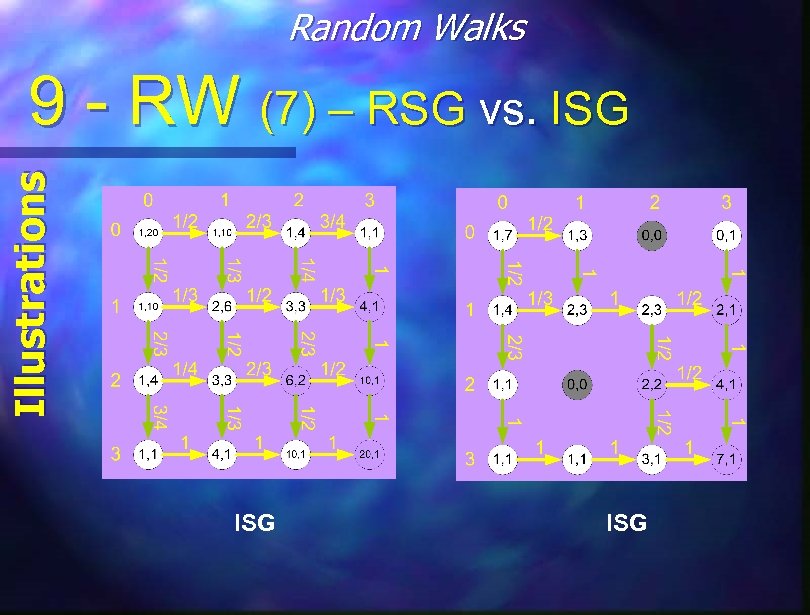 Random Walks Illustrations 9 - RW (7) – RSG vs. ISG ISG
Random Walks Illustrations 9 - RW (7) – RSG vs. ISG ISG
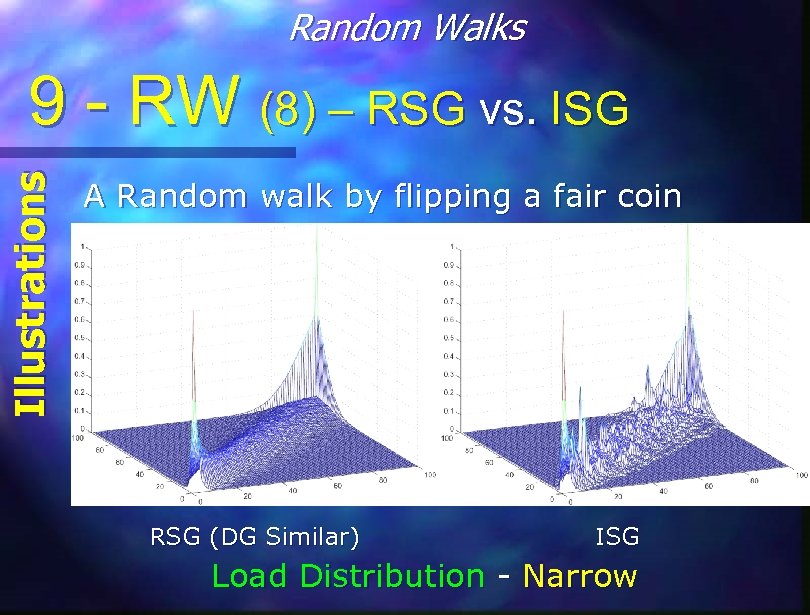 Random Walks Illustrations 9 - RW (8) – RSG vs. ISG A Random walk by flipping a fair coin RSG (DG Similar) ISG Load Distribution - Narrow
Random Walks Illustrations 9 - RW (8) – RSG vs. ISG A Random walk by flipping a fair coin RSG (DG Similar) ISG Load Distribution - Narrow
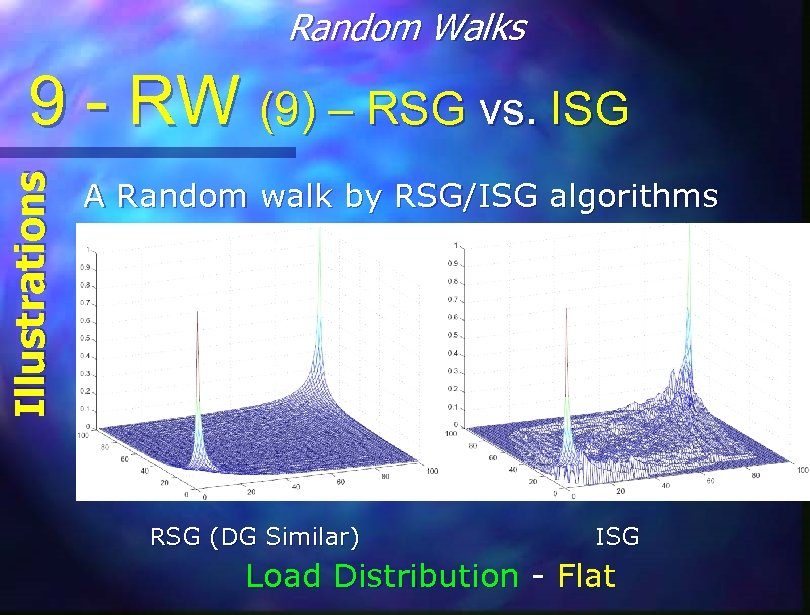 Random Walks Illustrations 9 - RW (9) – RSG vs. ISG A Random walk by RSG/ISG algorithms RSG (DG Similar) ISG Load Distribution - Flat
Random Walks Illustrations 9 - RW (9) – RSG vs. ISG A Random walk by RSG/ISG algorithms RSG (DG Similar) ISG Load Distribution - Flat
 Rumor Routing Protocol Highlights 10 - RR (1) n Observation: for many application any arbitrary path will do – No Need for a Shortest Path n Nodes are Densely Distributed n Bidirectional Links n Localized Communication n Stationary Nodes n Meet Trails of Queries and Events
Rumor Routing Protocol Highlights 10 - RR (1) n Observation: for many application any arbitrary path will do – No Need for a Shortest Path n Nodes are Densely Distributed n Bidirectional Links n Localized Communication n Stationary Nodes n Meet Trails of Queries and Events
 Rumor Routing Main Drawbacks 10 - RR (2) n Attractive only when the ratio between events and queries is inside a threshold where it is not attractive to flood neither. n Optimal parameters depend heavily on topology (but can be adaptively tuned) n Does not guarantee delivery
Rumor Routing Main Drawbacks 10 - RR (2) n Attractive only when the ratio between events and queries is inside a threshold where it is not attractive to flood neither. n Optimal parameters depend heavily on topology (but can be adaptively tuned) n Does not guarantee delivery
 Rumor Routing Main Procedures 10 - RR (3) Movement on the net is done by several agents, trying (randomly) to walk straight. n Every node maintains lists of neighbors and events (how to get to the reporting node). n An agent coming from and event is updating nodes it visits. n An agent coming from a query is searching for ways to the reporting nodes. n High probability the lines will intersect. n
Rumor Routing Main Procedures 10 - RR (3) Movement on the net is done by several agents, trying (randomly) to walk straight. n Every node maintains lists of neighbors and events (how to get to the reporting node). n An agent coming from and event is updating nodes it visits. n An agent coming from a query is searching for ways to the reporting nodes. n High probability the lines will intersect. n
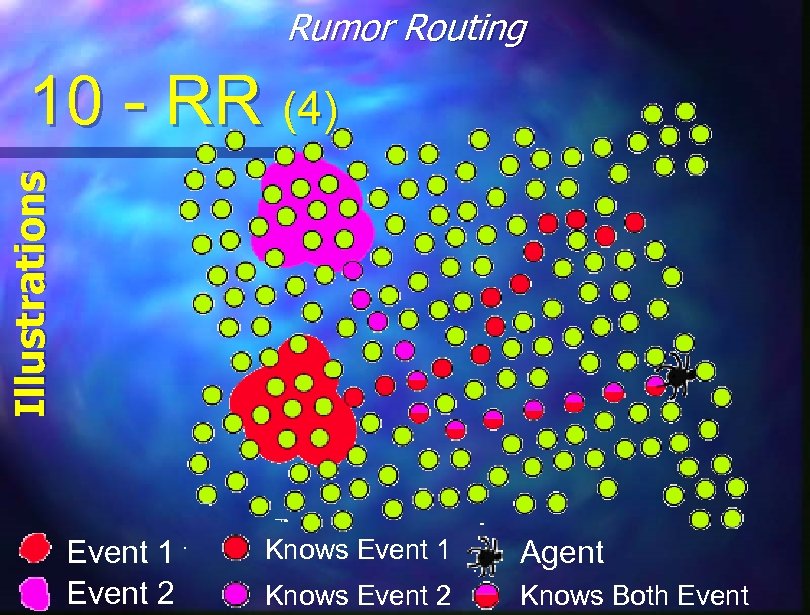 Rumor Routing Illustrations 10 - RR (4) Event 1 Event 2 Knows Event 1 Agent Knows Event 2 Knows Both Event
Rumor Routing Illustrations 10 - RR (4) Event 1 Event 2 Knows Event 1 Agent Knows Event 2 Knows Both Event
 Rumor Routing Illustrations 10 - RR (5) Event Source Ve Th eo ry re Ex ec tica ut l ion Query Source
Rumor Routing Illustrations 10 - RR (5) Event Source Ve Th eo ry re Ex ec tica ut l ion Query Source
 Agenda n. General ! ! ! e n o D Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
Agenda n. General ! ! ! e n o D Properties n. Architectures and Requirements n. Routing Protocols Classification n 10 Suggested Routing Protocols: n. LEACH n. DD n. PEGASIS n. MCF n. TEEN n. TTDD n. APTEEN n. RW n. SPIN n. RR
 Conclusions n. WSN will spread to many applications n. Properties and Requirements are both Unique and Diversified n. Routing Protocol choice is and probably will continue to be Application Driven n. More Analysis, Simulations and new Ideas are needed for every category
Conclusions n. WSN will spread to many applications n. Properties and Requirements are both Unique and Diversified n. Routing Protocol choice is and probably will continue to be Application Driven n. More Analysis, Simulations and new Ideas are needed for every category
 References (1) n n Q. Jiang, D. Manivannan, Routing Protocols for Sensor Networks, IEEE Consumer Communications and Networking Conference (CCNC'04), 2004. R. Jurdak, C. V. Lopes, P. Baldiy, A Framework for Modeling Sensor Networks, 19 th Annual ACM Conference on Object-Oriented Programming, Systems, Languages, and Applications (OOPSLA'04), 2004. W. Heinzelman, A. Chandrakasan, and H. Balakrishnan, Energy. Efficient Communication Protocol for Wireless Microsensor Networks, IEEE Proceedings of the IEEE International Conference on System Sciences, 2000. S. Lindsey, C. S. Raghavendra, PEGASIS: Power Efficient GAthering in Sensor Information Systems, IEEE Aerospace Conference, 2002.
References (1) n n Q. Jiang, D. Manivannan, Routing Protocols for Sensor Networks, IEEE Consumer Communications and Networking Conference (CCNC'04), 2004. R. Jurdak, C. V. Lopes, P. Baldiy, A Framework for Modeling Sensor Networks, 19 th Annual ACM Conference on Object-Oriented Programming, Systems, Languages, and Applications (OOPSLA'04), 2004. W. Heinzelman, A. Chandrakasan, and H. Balakrishnan, Energy. Efficient Communication Protocol for Wireless Microsensor Networks, IEEE Proceedings of the IEEE International Conference on System Sciences, 2000. S. Lindsey, C. S. Raghavendra, PEGASIS: Power Efficient GAthering in Sensor Information Systems, IEEE Aerospace Conference, 2002.
 References (2) n n A. Manjeshwar and D. P. Agrawal, TEEN: A Protocol for Enhanced Efficiency in Wireless Sensor Networks, Proceedings of the 1 st International Workshop on Parallel and Distributed Computing Issues in Wireless Networks and Mobile Computing (with IPDPS'01), 2001. A. Manjeshwar and D. P. Agrawal, APTEEN: a hybrid protocol for efficient routing and comprehensive information retrieval in wireless sensor networks, Proceedings of the International Parallel and Distributed Processing Symposium (IPDPS'02), 2002. J. Kulik, W. Heinzelman, and H. Balakrishnan, Negotiation-Based Protocols for Disseminating Information in Wireless Sensor Networks, Wireless Networks, Vol. 8, pp. 169 -185, 2002. C. Intanagonwiwat, R. Govindan, D. Estrin, J. S. Heidemann, and F. Silva, Directed Diffusion for Wireless Sensor Networking, IEEE/ACM Transactions on Networking, vol. 11, no. 1, pp. 2 -16, 2003.
References (2) n n A. Manjeshwar and D. P. Agrawal, TEEN: A Protocol for Enhanced Efficiency in Wireless Sensor Networks, Proceedings of the 1 st International Workshop on Parallel and Distributed Computing Issues in Wireless Networks and Mobile Computing (with IPDPS'01), 2001. A. Manjeshwar and D. P. Agrawal, APTEEN: a hybrid protocol for efficient routing and comprehensive information retrieval in wireless sensor networks, Proceedings of the International Parallel and Distributed Processing Symposium (IPDPS'02), 2002. J. Kulik, W. Heinzelman, and H. Balakrishnan, Negotiation-Based Protocols for Disseminating Information in Wireless Sensor Networks, Wireless Networks, Vol. 8, pp. 169 -185, 2002. C. Intanagonwiwat, R. Govindan, D. Estrin, J. S. Heidemann, and F. Silva, Directed Diffusion for Wireless Sensor Networking, IEEE/ACM Transactions on Networking, vol. 11, no. 1, pp. 2 -16, 2003.
 References (3) n n F. Ye, A. Chen, S. Lu, L. Zhang, A Scalable Solution to Minimum Cost Forwarding in Large Sensor Networks, Proceedings of the 10 th IEEE International Conference on Computer Communications and Networks (ICCCN'01), 2001. F. Ye, H. Luo, J. Cheng, S. Lu, and L. Zhang, A Two-Tier Data Dissemination Model for Large-scale Wireless Sensor Networks , ACM International Conference on Mobile Computing and Networking (MOBICOM'02), 2002. S. D. Servetto, G. Barrenechea, Constrained Random Walks on Random Graphs: Routing Algorithms for Large Scale Wireless Sensor Networks, In the Proceedings of the 1 st ACM International Workshop on Wireless Sensor Networks and Applications (WSNA'02), 2002. D. Braginsky, D. Estrin, Rumor Routing Algorithm For Sensor Networks, In the Proceedings of the 1 st ACM International Workshop on Wireless Sensor Networks and Applications (WSNA'02), 2002.
References (3) n n F. Ye, A. Chen, S. Lu, L. Zhang, A Scalable Solution to Minimum Cost Forwarding in Large Sensor Networks, Proceedings of the 10 th IEEE International Conference on Computer Communications and Networks (ICCCN'01), 2001. F. Ye, H. Luo, J. Cheng, S. Lu, and L. Zhang, A Two-Tier Data Dissemination Model for Large-scale Wireless Sensor Networks , ACM International Conference on Mobile Computing and Networking (MOBICOM'02), 2002. S. D. Servetto, G. Barrenechea, Constrained Random Walks on Random Graphs: Routing Algorithms for Large Scale Wireless Sensor Networks, In the Proceedings of the 1 st ACM International Workshop on Wireless Sensor Networks and Applications (WSNA'02), 2002. D. Braginsky, D. Estrin, Rumor Routing Algorithm For Sensor Networks, In the Proceedings of the 1 st ACM International Workshop on Wireless Sensor Networks and Applications (WSNA'02), 2002.
 Sense. Your Network Dude Karl Friedrich Hieronymus Baron of Munchausen (1720 -1797)
Sense. Your Network Dude Karl Friedrich Hieronymus Baron of Munchausen (1720 -1797)


