79bfe7ecfe24d6c290d855099a6c8d3c.ppt
- Количество слайдов: 101

Routing and Broadcast in a Mobile Ad Hoc Network Professor Yu-Chee Tseng Dept. of Computer Science and information Engineering National Central University (曾煜棋 中央大學 資訊 程系)

Outline q Introduction to Wireless Networks q Mobile Ad Hoc Network (MANET) q Routing in a Mobile Ad Hoc Network l Review l Fully Location-Aware Routing q Broadcast Storm Problem in MANET q MAC Introduction (IEEE 802. 11 Background) 2

Introduction to Wireless Networks

When You Are Mobile Today q Desperately looking for a computer to check your e-mails q Need to access Internet, WWW Info, etc. q Need cellular phone, airphone, pager, FAX, etc. q Using a laptop to do work while traveling q People of the late 20 th century: Keeping “connected” any time, any where!! 4

Applications of Wireless Communications q Mobile Office/Meeting Room: l with multitude of notebooks, palmtop, PDA, etc. q One who needs to work with customers face-to-face l doctor/nurse l clerk/salespersons l adv. : paperless, less error-prone q q Hospitality: 服務業, 餐廳入座, 代客泊車 Utility: 水公司, 電力公司 l Kansas City: wireless metering system. q q Field work, Field services: always on the road Warehousing/Supermarket: l pricing, order, bar-code input, etc. 5
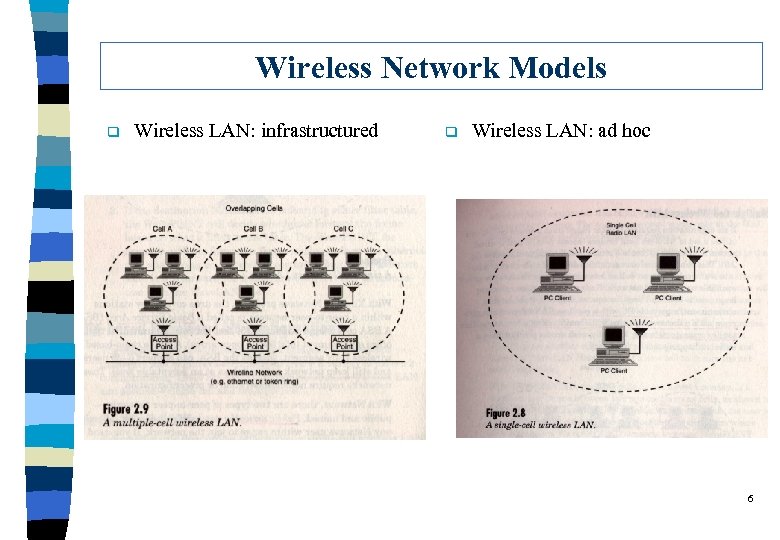
Wireless Network Models q Wireless LAN: infrastructured q Wireless LAN: ad hoc 6
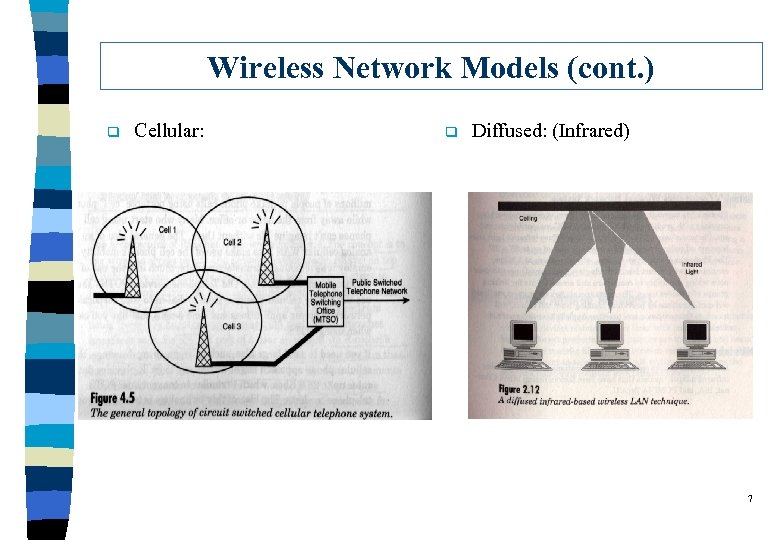
Wireless Network Models (cont. ) q Cellular: q Diffused: (Infrared) 7

Wireless Network Models (cont. ) q Wireless MAN: q Wireless WAN: 8

MANET: Mobile Ad Hoc Network

MANET q MANET = Mobile Ad Hoc Networks l a set of mobile hosts, each with a transceiver l no base stations; no fixed network infrastructure l multi-hop communication l needs a routing protocol which can handle changing topology 10

Applications of MANET q battlefields (戰場) q nature disaster areas (緊急救難) q fleet in oceans q historical cites (古蹟) q festival ground (集會) 11
Related Information q IEEE 802. 11 for Wireless LANs l MAC l PHY q IETF manet group l to stimulate research in this area l RFC 2503 q Routing Protocols: l unicast – AODV, DSR, ZRP, TORA, CBRP, CEDAR l multicast – AMRoute, ODMRP, AMRIS 12
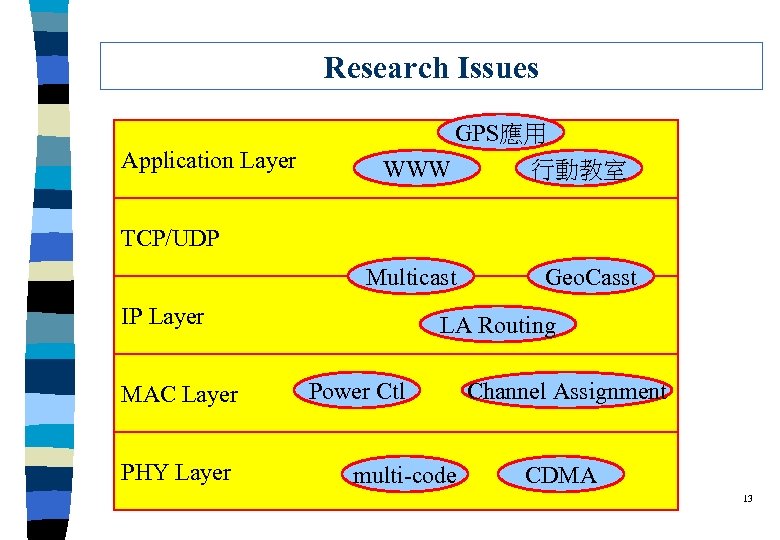
Research Issues GPS應用 Application Layer WWW 行動教室 TCP/UDP Multicast IP Layer MAC Layer PHY Layer Geo. Casst LA Routing Power Ctl multi-code Channel Assignment CDMA 13

Routing in a Mobile Ad Hoc Network (Part I: Review) q q Ant’s Food Search Reviews (DSR, ABR, SSR, LAR, TORA)

Ants Searching for Food ? ? ? ? ? ? ? ? ? ? ? 15
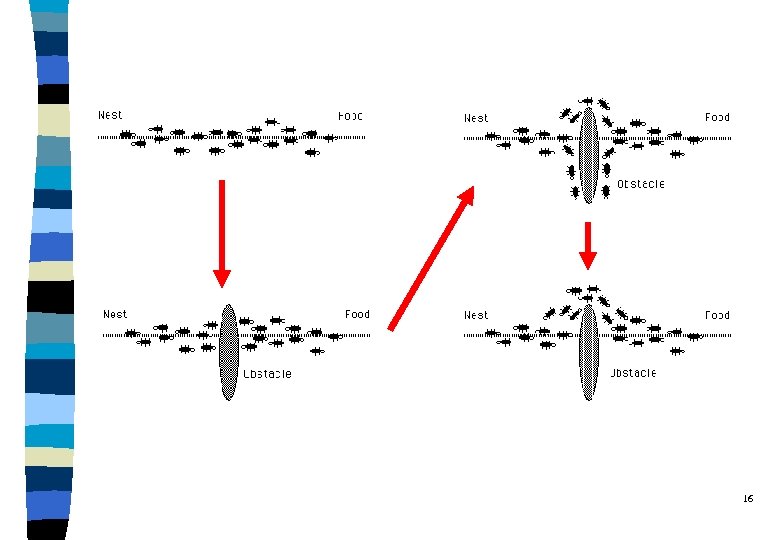
16
Three Main Issues in Ants’ Search q Route Discovery: l searching for the places with food q Packet Forwarding: l delivering foods back home q Route Maintenance: l when foods move to new place 17

Protocol 1: DRS (Dynamic Source Routing) q on-demand q Source Routing: l routes are denoted with complete information (each hop is registered) q Two major parts: l route discovery l route maintenance 18

Route Discovery of DSR q When a host has a packet to send, it first consults its route cache. l If there is an unexpired route, then it will use it. l Otherwise, a route discovery will be performed. q Route Discovery: l A ROUTE_REQUEST packet is sent by flooding. l There is a “route record” field in the packet. Ø Each node will append its address to the record. 19
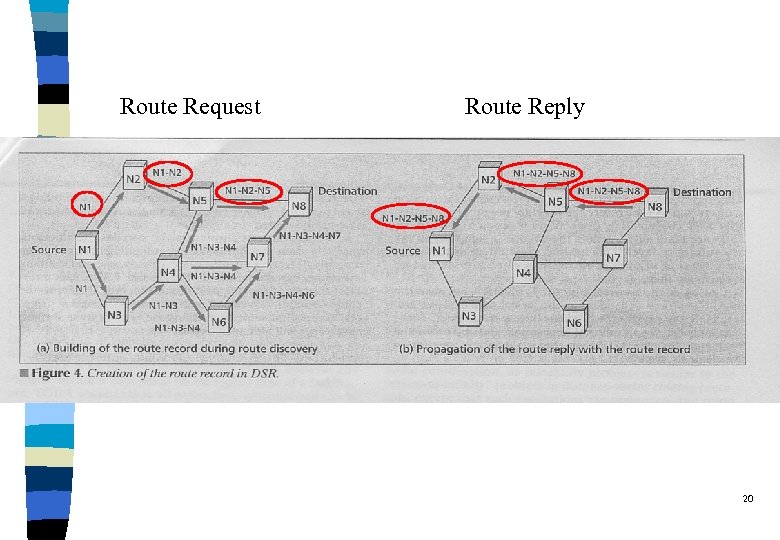
Route Request Route Reply 20

Route Reply of DSR q A ROUTE_REPLY packet is generated when l the route request packet reaches the destination l an intermediate host has an “unexpired” route to the destination q A route is then generated in two manner: l from destination: Ø the route traversed by the ROUTE_REQUEST packet l from intermediate host: Ø the route traversed by the ROUTE_REQUEST packet concatenated with the route in the intermediate host’s route cache 21

Path of ROUTE_REPLY q Which way should be taken by the ROUTE_REPLY? q Two possibilities: l symmetric path: Ø follow the same route in the reverse order to reach the source l asymmetric path: Ø need to discover a new route to the source by initiating a ROUTE_REQUEST to the source Ø piggyback the discovered route to the ROUTE_REQUEST packet S D 22
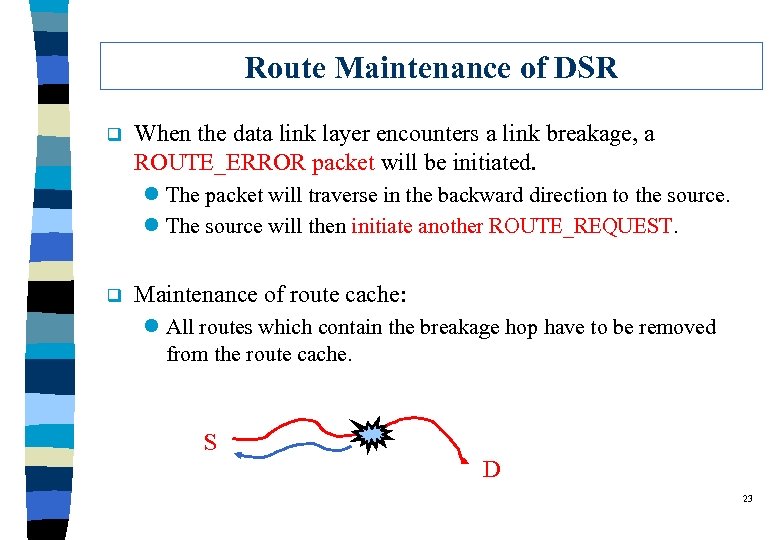
Route Maintenance of DSR q When the data link layer encounters a link breakage, a ROUTE_ERROR packet will be initiated. l The packet will traverse in the backward direction to the source. l The source will then initiate another ROUTE_REQUEST. q Maintenance of route cache: l All routes which contain the breakage hop have to be removed from the route cache. S D 23

How to Detect a Link Breakage q Active Acknowledge: l The receiver of a packet actively sends an ACK to the sender. q Passive Acknowledge: l The sender passively listen to the receiver’s sending. S R data packets active/passive ACK S R V 24

Protocol 2: ZRP q q ZRP = Zone Routing Protocol A hierarchical approach: l zone = the area that a node knows the complete routing information l so routing goes in a zone-to-zone basis 25
Protocol 3: ABR (Associativity-Based Routing) q ABR considers the stability of a link. q Basic Idea: l Each node periodically generates a beacon to signify its existence. l On receipt of the beacon, a node increases the “tick” of the sender by 1. Ø A higher degree means more stability. Ø A lower degree means less reliable. l When a link becomes broken, the node will set the tick of the other node to 0. 26

ABR Outline q Route Discovery: l (similar to DSR) Ø On needing a route, a host will broadcast a ROUTE_REQUEST packet. Ø Each receiving host will append its address to the packet. l The “ticks” will be appended in the ROUTE_REQUEST packet. l The destination node will select the route with the highest tick. 7 5 source 8 10 4 destination 27
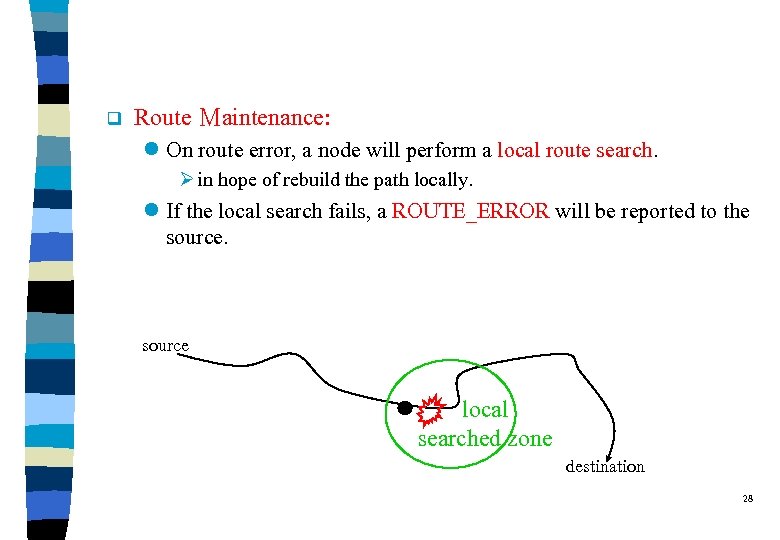
q Route Maintenance: l On route error, a node will perform a local route search. Ø in hope of rebuild the path locally. l If the local search fails, a ROUTE_ERROR will be reported to the source local searched zone destination 28
Protocol 4: SSR (Signal Stability Routing) q Observation: l The ABR only considers the stability to nodes. q Two more metrics: l signal strength: Ø the strength of a signal Ø provided by link layer l location stability Ø how fast a host moves Ø could be measure by: ü the change of signal strength over a period of time ü location devices (such as GPS) 29

Protocol 5: Location-Aided Routing (LAR) q to limit the area to search for the route l I will forward the ROUTE_REQ; l J will not forward the ROUTE_REQ. A B D J I Expected zone of D S C Route search zone 30
Assumption of LAR q Location Device is available. l outdoor positioning device: Ø GPS: global positioning system Ø accuracy: in about 20 to 50 meters l indoor positioning device: Ø Infrared Ø short-distance radio, bluetooth, etc. 31
Protocol 6: TORA (Temporally Ordered Routing Algorithm) q q source-initiated protocol provide multiple paths for any source-destination pair l Like water flowing, it goes from upstream to downstream. q for highly dynamic mobile networks 32
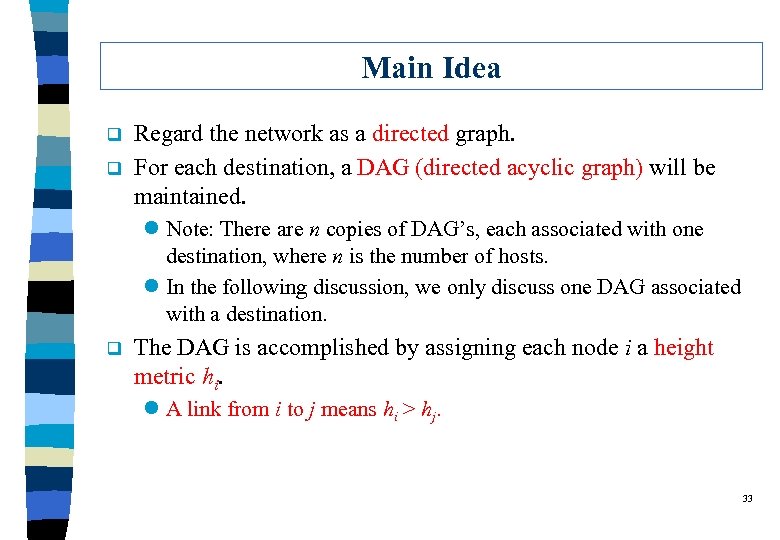
Main Idea q q Regard the network as a directed graph. For each destination, a DAG (directed acyclic graph) will be maintained. l Note: There are n copies of DAG’s, each associated with one destination, where n is the number of hosts. l In the following discussion, we only discuss one DAG associated with a destination. q The DAG is accomplished by assigning each node i a height metric hi. l A link from i to j means hi > hj. 33
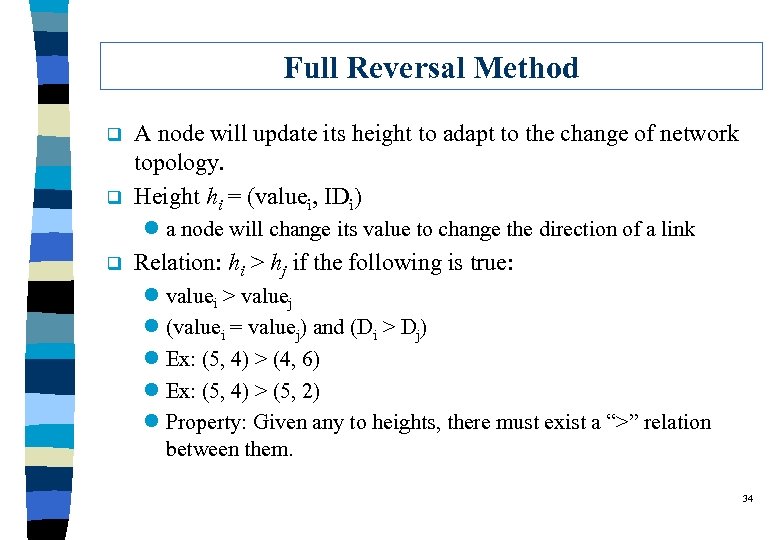
Full Reversal Method q q A node will update its height to adapt to the change of network topology. Height hi = (valuei, IDi) l a node will change its value to change the direction of a link q Relation: hi > hj if the following is true: l valuei > valuej l (valuei = valuej) and (Di > Dj) l Ex: (5, 4) > (4, 6) l Ex: (5, 4) > (5, 2) l Property: Given any to heights, there must exist a “>” relation between them. 34

q Rule: l Each node other than the destination that has no outgoing links reverses the direction of all its incoming links. l This means that the node’s height is a local minimum. q This is done by getting a larger height such that the node becomes a local maximum. l MAX{all neighbors’ heights} + 1 a, 5 b, 6 e, 3 d, 4 c, 3 dest, 8 f, 1 g, 2 35
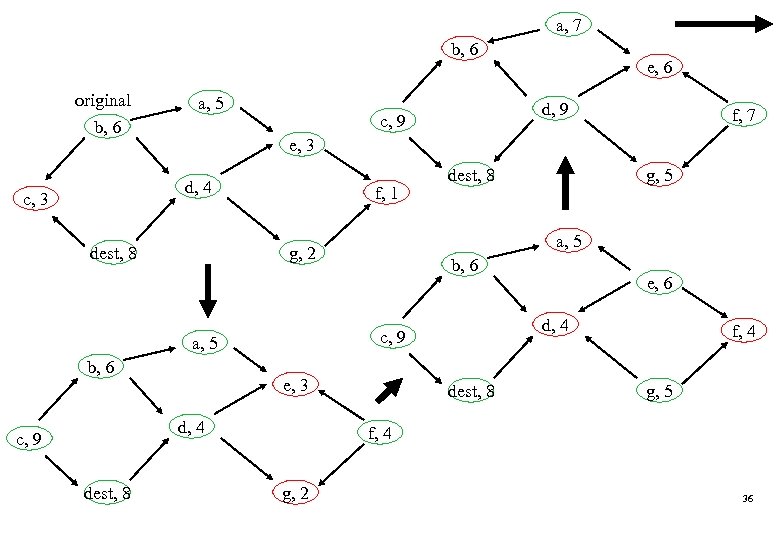
a, 7 b, 6 original b, 6 a, 5 f, 1 b, 6 dest, 8 b, 6 e, 3 e, 6 d, 4 c, 9 d, 4 g, 5 a, 5 g, 2 a, 5 dest, 8 f, 7 e, 3 dest, 8 c, 9 d, 9 c, 9 d, 4 c, 3 e, 6 dest, 8 f, 4 g, 5 f, 4 g, 2 36
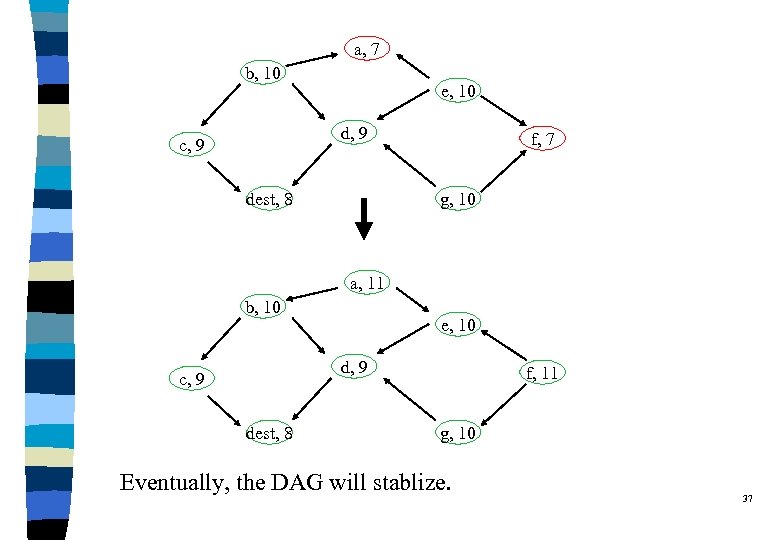
a, 7 b, 10 e, 10 d, 9 c, 9 dest, 8 f, 7 g, 10 a, 11 b, 10 e, 10 d, 9 c, 9 dest, 8 f, 11 g, 10 Eventually, the DAG will stablize. 37
TORA Summary q q There will exist multiple paths leading to a destination. Note: l The above DAG is associated with node dest. l Associated with each node, there is a DAG. q The above scheme is called Full Reversal. l In TORA, more complicated rules are used. Ø Partial reversal Ø Temporally-ordered routing l Height metric 38

Routing in a Mobile Ad Hoc Network (Part II: Fully Location-Aware Routing) “GRID: A Fully Location-Aware Routing Protocol for Mobile Ad Hoc Networks”, Telecommunication Systems (to appear)

Basic Idea q Adopt Positioning Systems l such as GPS receivers l President Clinton ordered to discontinue SA (selective availability) in May 2000 Ø will increase the accuracy by an order q Fully utilize location information: l route discovery l data forwarding l route maintenance q We propose a new protocol called GRID. 40
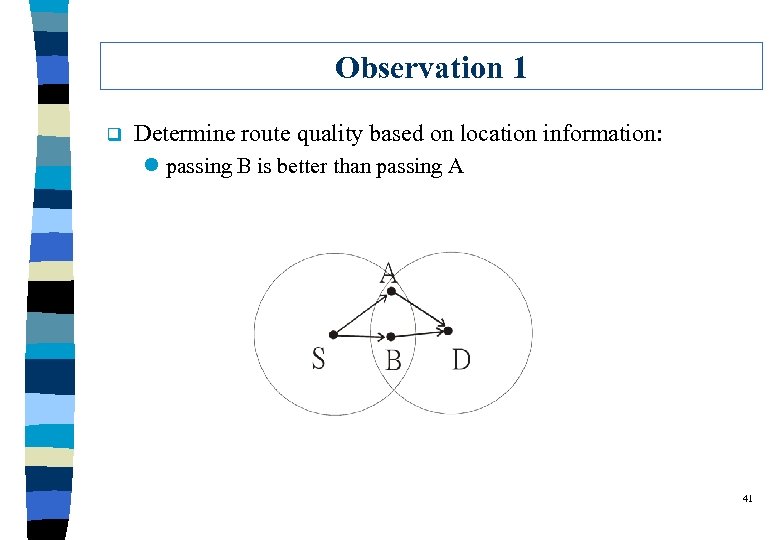
Observation 1 q Determine route quality based on location information: l passing B is better than passing A 41
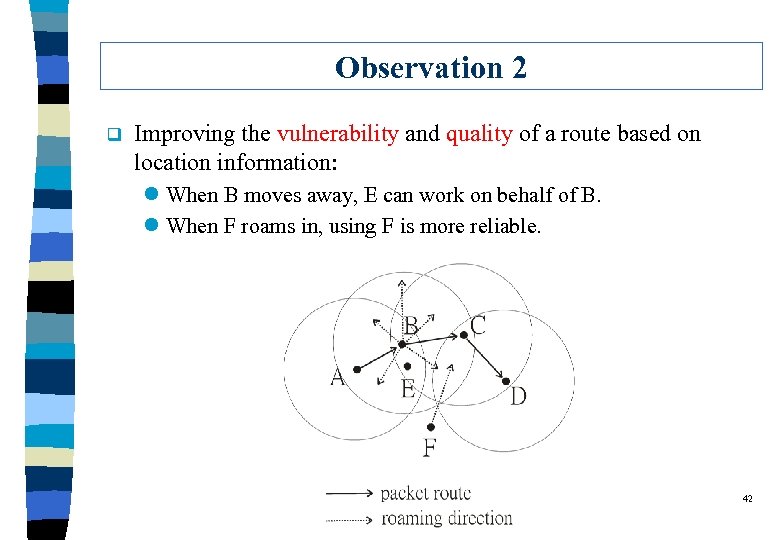
Observation 2 q Improving the vulnerability and quality of a route based on location information: l When B moves away, E can work on behalf of B. l When F roams in, using F is more reliable. 42
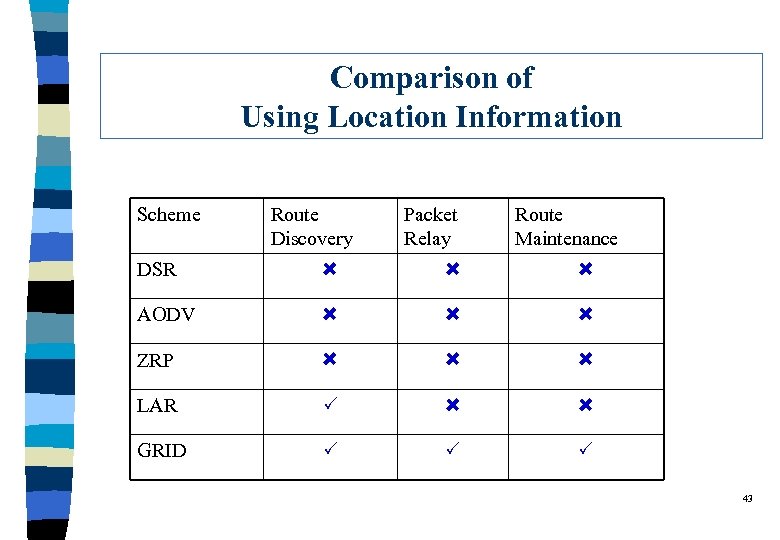
Comparison of Using Location Information Scheme Route Discovery Packet Relay Route Maintenance DSR AODV ZRP LAR GRID 43
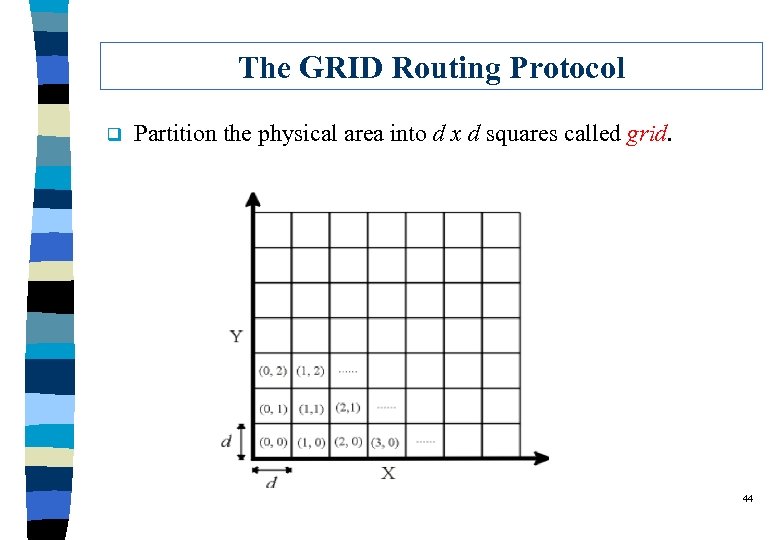
The GRID Routing Protocol q Partition the physical area into d x d squares called grid. 44

Protocol Overview q In each grid, a leader will be elected, called gateway. q Routing is performed in a grid-by-grid manner. q Responsibility of gateway: l forward route discovery packets l propagate data packets to neighbor grids l maintain routes which passes the grid 45

Route Search q We can adopt any existing route discovery protocol. q Major features/differences: l limit the search range by the locations of source and destination l only gateway will help with the discovery process Ø The more crowded the area is, the more saving. l routing table is indicated by grid ID (instead of host address) 46

Route Search Example route search route reply 47
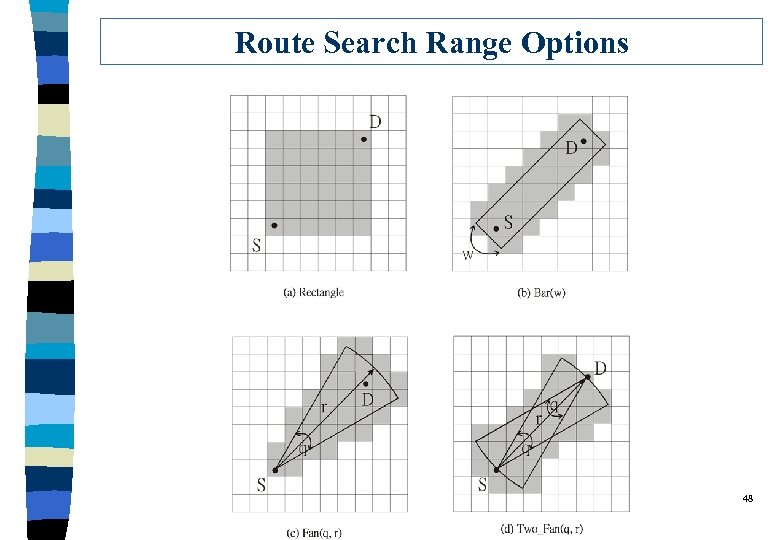
Route Search Range Options 48
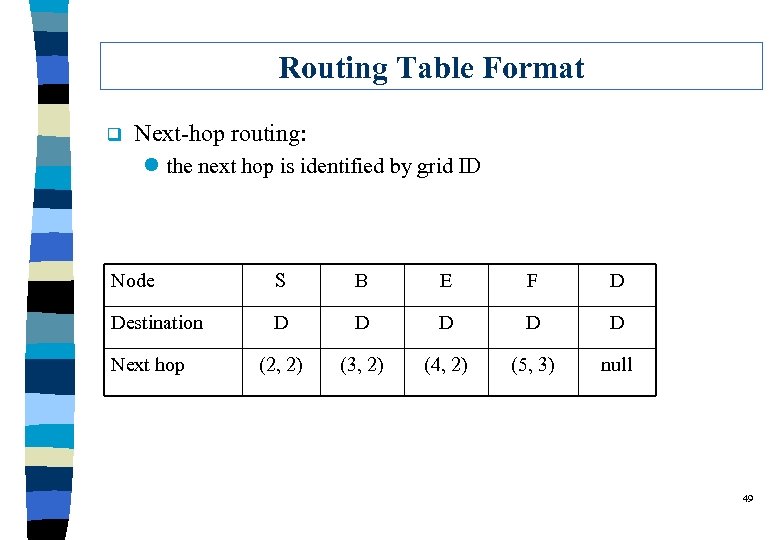
Routing Table Format q Next-hop routing: l the next hop is identified by grid ID Node S B E F D Destination D D D (2, 2) (3, 2) (4, 2) (5, 3) null Next hop 49
Route Maintenance q Two issues: l how to maintain a gateway in each grid l how to maintain a grid-by-grid route q Special Feature: l longer route lifetime: Ø as long as there is a host in each gateway, a route will be alive Ø more robust l In existing protocols, once a node in the route roams away, the route will be broken. 50
Gateway Election in a Grid q Any “leader election” protocol in distributed computing can be used. q Weaker than leader election: l It is acceptable that there are multiple leaders in a grid. Ø less acceptable without leader q Preference in electing a gateway: X l near the physical center of the grid Ø likely to remain in the grid for longer time l once elected, a gateway will remain as so until leaving the grid Ø to avoid ping-pong effect 51

Gateway Election Details BID(g, loc) GATE(g, loc) RETIRE(g, T) 52
How to Maintain a Grid-by-Grid Route q Strength: more robust route l mobility-resistant q Problems: l Gateway moves away: Ø The gateway election will find the new gateway. Ø So the route will remain alive. l Source moves away: (see next page) Ø getting closer Ø getting farther away l Destination move away: (similar) 53

54
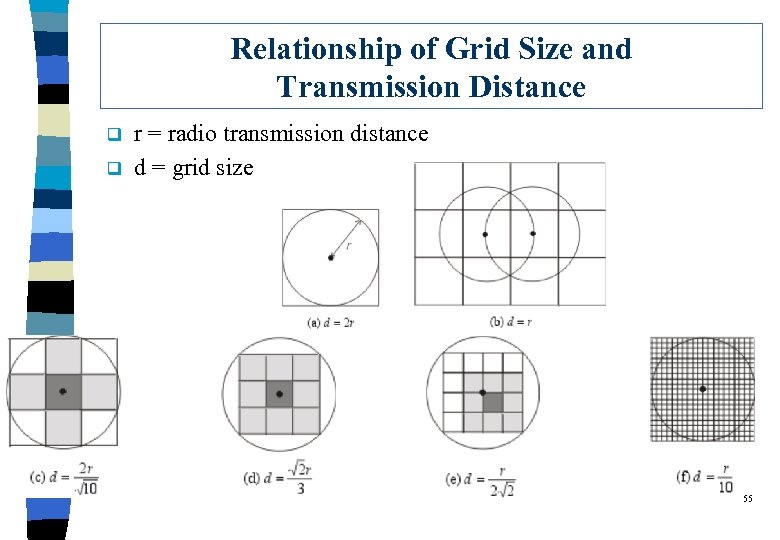
Relationship of Grid Size and Transmission Distance q q r = radio transmission distance d = grid size 55

Simulation Model q q Physical area of size 1000 m n = number of hosts: 100~300 r=300 m d = grid size l GRID-1: l GRID-2: l GRID-3: q Roaming speed: 30 km/hr, 60 km/hr 56
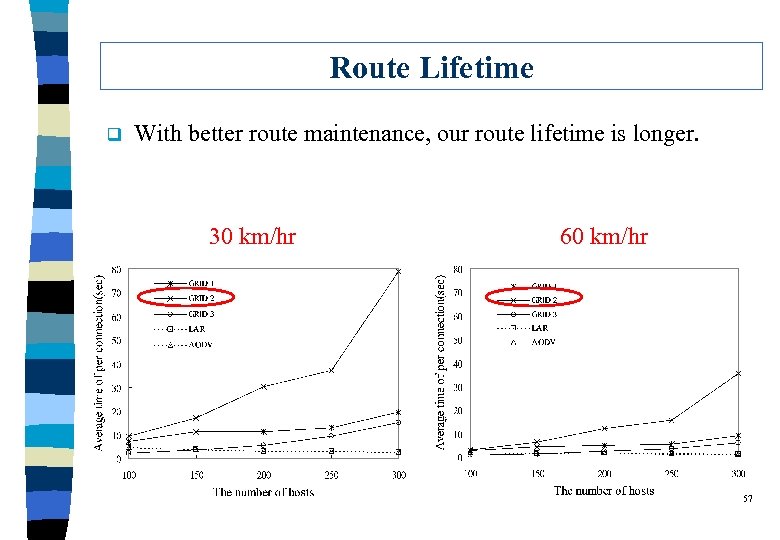
Route Lifetime q With better route maintenance, our route lifetime is longer. 30 km/hr 60 km/hr 57
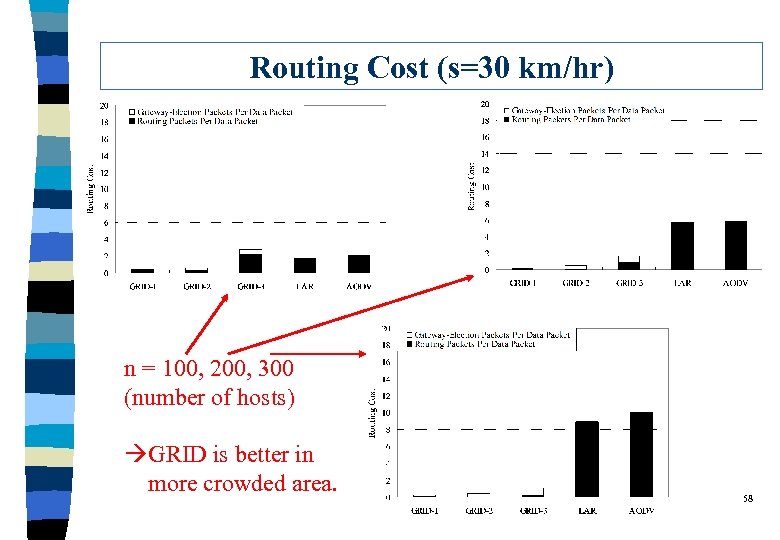
Routing Cost (s=30 km/hr) n = 100, 200, 300 (number of hosts) àGRID is better in more crowded area. 58
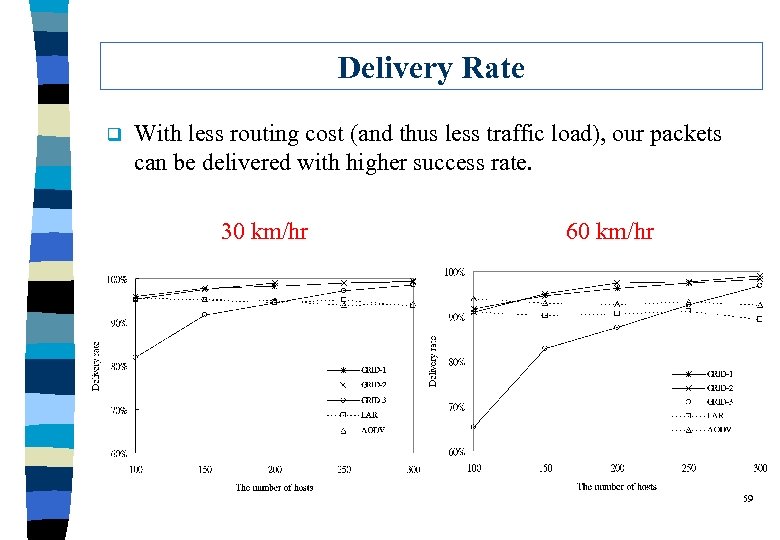
Delivery Rate q With less routing cost (and thus less traffic load), our packets can be delivered with higher success rate. 30 km/hr 60 km/hr 59
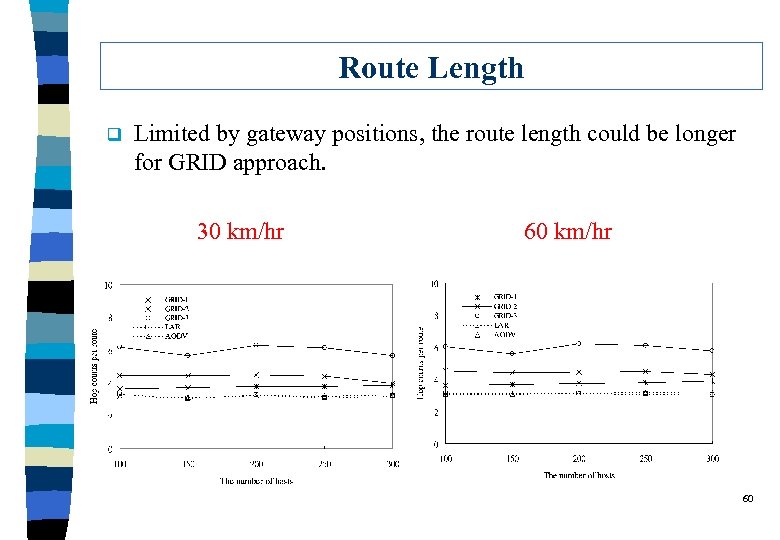
Route Length q Limited by gateway positions, the route length could be longer for GRID approach. 30 km/hr 60
Conclusions q A FULLY location-aware routing protocol: l route discovery: by gateways only l data forwarding: by gateway ID, instead of host ID l route maintenance: like handoff in GSM systems q Taking advantage of geometric property of network. l instead of graph property in other approaches q Less routing cost l longer route lifetime, more resilient route l less traffic load 61

The Broadcast Storm Problem in MANETs

Storms of Nature 63

T-Storm in St. Louis 64

“Touchdown” of a Tornado 65

Can Human Create Storms? 66

The Storms in the Internet Subject: 我有六千一百萬筆最新Email名單,我只賣 NT$3000元! Date: Sun, 11 Jul 1999 18: 47: 21 +0800 (CST) From: ****@***. university. edu To: <yctseng@csie. ncu. edu. tw> 你想要賺錢嗎? 你可以在花費極少的情形下,接觸到全世界六千萬一百萬人! 是的!沒錯! 我有六千一百萬筆最新Email名單,我只賣 NT$3000元!!! 這些都是最新的地址,基本上可說包含了網際網路上所有的人, 而且這些地址沒有一個是重複的!!! 並且都已經過排序整理過了,可以立即上手使用!!! 這可能是當今市場上所能找到最物超所值的交易了!!! 想想看,賣一個五十塊錢的商品,如果回收率只有千分之一, 就有三百零五萬元進到你的口袋了!!! (a 3 -page long email. . . ) 67

Call for Papers Dear Friends, Sorry if you receive the duplicate messages. But please distribute the following message to your friends. Prof. ***, University of %%% *********************************** Call for Papers International Conference on ? ? IC? ? ? '99 to be held in ? ? ? , September ? ? ? , 1999 http: //www. ? ? ? /conf/ic? ? ? 99 THEME: Research on mobile computing is gaining more and more attention. . . 68

The Storms in the Internet 69
Broadcast Problem q Broadcast: the sending of a message to other hosts l Ex: Route search in a MANET l Ex: DSR, AODV, ZRP protocols. q Assumptions: l The broadcast is spontaneous. Ø no synchronization Ø no prior global topology knowledge l The broadcast is unreliable. Ø no acknowledgement of any kind ü not to cause more contention ü 100% reliability is unnecessary for some application l No RTS/CTS dialogue. 70
Broadcast by Flooding q A straight-forward approach l A host rebroadcasts the message on receiving a broadcast message for the first time. q Broadcast storm problem: l redundant rebroadcasts l contention problem l collision problem 71

Serious Redundancy q Optimal broadcasting vs. Flooding (a) optimal = 2 steps (b) optimal = 2 steps q Severity of Redundant Coverage. 72

Analysis on Redundancy q Additional Coverage provided by a rebroadcast. l The max. additional coverage is 61%. l The coverage is 41% in average. q The expected additional coverage EAC(k)/ r 2 after a host heard a broadcast message k times. 73
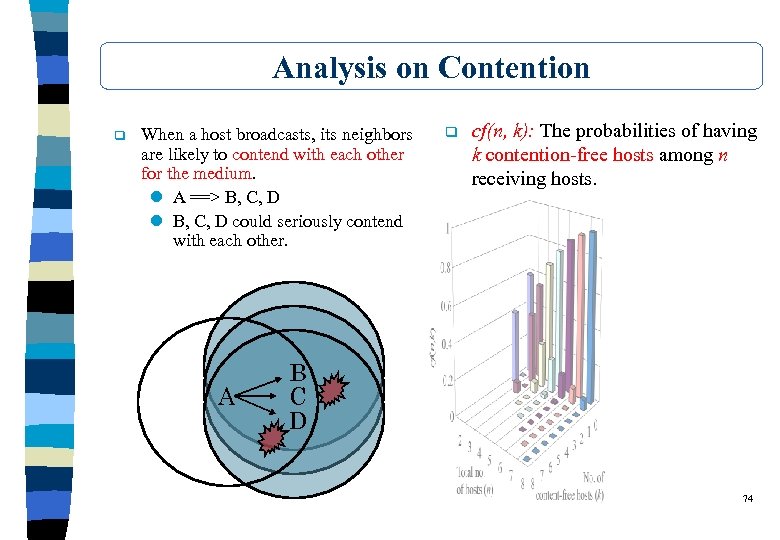
Analysis on Contention q When a host broadcasts, its neighbors are likely to contend with each other for the medium. l A ==> B, C, D l B, C, D could seriously contend with each other. A q cf(n, k): The probabilities of having k contention-free hosts among n receiving hosts. B C D 74

Analysis on Collision q Higher Possibility of Collision: l Rebroadcasts are likely to start at the same time. Ø Backoff window runs out if medium is quiet for a while. l lack of RTS/CTS dialogues l lack of collision detection (CD) if collision occurs l hidden terminal problem 75

Broadcast Storm Problem Summary q Redundancy q Contention q Collision q How to derive an efficient scheme for broadcasting in a MANET? 76

Possible Broadcast Solutions q Probabilistic Scheme q Counter-Based Scheme q Distance-Based Scheme q Location-Based Scheme q Cluster-Based Scheme 77
Probabilistic Scheme q Rebroadcast by “Tossing a Die” q A host always rebroadcasts with a certain probability P. l When P = 1, this is flooding. l A smaller P will reduce the storm effect. 78
Simulation Parameters q q q no of hosts = 100 transmission radius = 500 meters packet size = 280 bytes transmission rate = 1 M bits/sec broadcast arrival rate: 1 per sec. to the whole map: (1 unit = 500 meters) l 1 x 1, 3 x 3, 5 x 5, 7 x 7, 10 x 10 q roaming pattern: random walk l speed: 0~10 km/hr in a 1 x 1 map, 0~30 km/hr in a 3 x 3 map, etc. q IEEE 802. 11 without PCF (point coordination function) 79

Performance of Probabilistic Scheme RE = REachability (in lines) SRB = Saved Re. Broadcast (in bars) Latency 80

Observation q Reachability: l In smaller maps, a low P is sufficient to achieve high reachability. l A larger P is needed in a larger map. q Saved Rebroadcast: l linear with respect to P q Latency: l Interestingly, in smaller areas, broadcast tends to complete in a slower speed. 81

Counter-Based Scheme q If a host has received a broadcast packet > C times, l then do not rebroadcast. q Examples: Addition Coverage l 1 time => 41% l 2 times => 19% l 3 times => 9% l 4 times => 5% l > 4 times, very little extra area 82
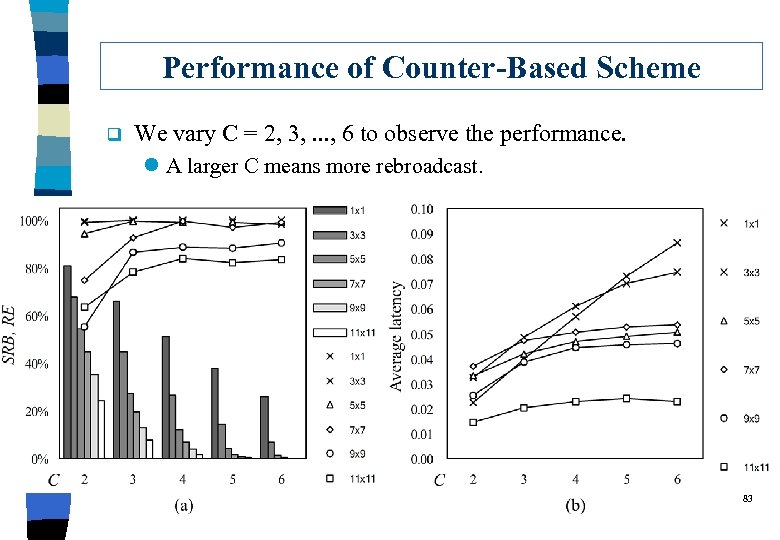
Performance of Counter-Based Scheme q We vary C = 2, 3, . . . , 6 to observe the performance. l A larger C means more rebroadcast. 83

Observation q Reachability: l C >= 3 can offer a reachability close to flooding. q Saved Rebroadcast: l In denser area, there is more saving. In sparser area, there is less saving. q Latency: l Higher latency is smaller area. 84
Distance-Based Scheme q Calculate the distance to the sending host. q dmin = Min{the distance to each sending host} q If dmin < D (a threshold), then do not rebroadcast. q How to find distance: l signal strength l GPS devices 85
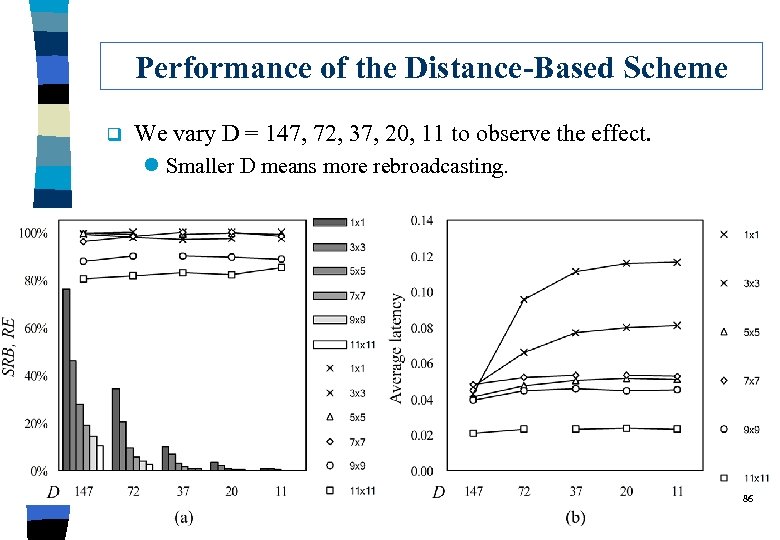
Performance of the Distance-Based Scheme q We vary D = 147, 72, 37, 20, 11 to observe the effect. l Smaller D means more rebroadcasting. 86

Observation q Why choosing D=147? l addition coverage = 0. 187, equal to that of C=2 q Reachability: l All look good, close to flooding. q Saved Rebradcast: l not much q Latency: l smaller area has higher latency 87

Location-Based Scheme q q From GPS to obtain the sender’s location. Let (x 1, y 1), (x 2, y 2), (x 3, y 3), . . . , (xk, yk) be locations of senders. l We can accurately calculate the additional coverage of this rebroadcast. No Extra Coverage Some Coverage S 2 S 1 A S 1 S 3 A S 2 88

Difficulty q Involve complicated math to calculate the extra coverage. l A lot of calculus! q Approximation: l grid simulation S 1 A S 3 S 2 89
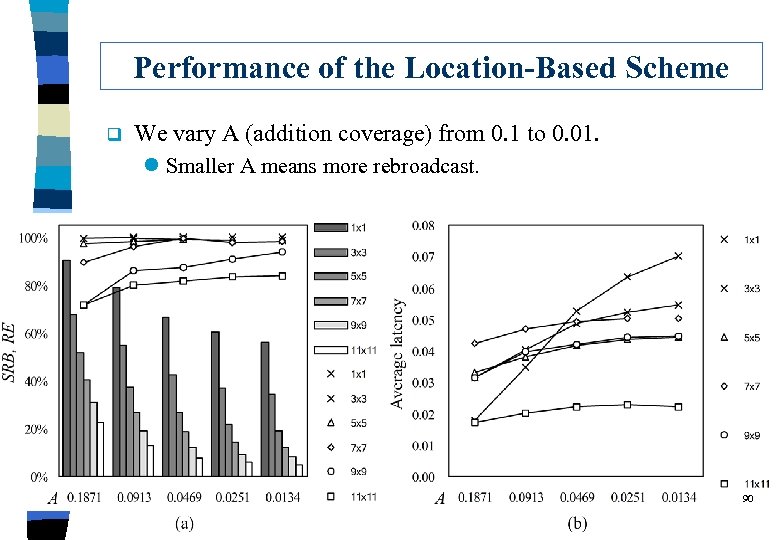
Performance of the Location-Based Scheme q We vary A (addition coverage) from 0. 1 to 0. 01. l Smaller A means more rebroadcast. 90

Observation q Why choosing A=0. 187? l This is additional coverage offered by C=2. q Best performance over all the above schemes! 91
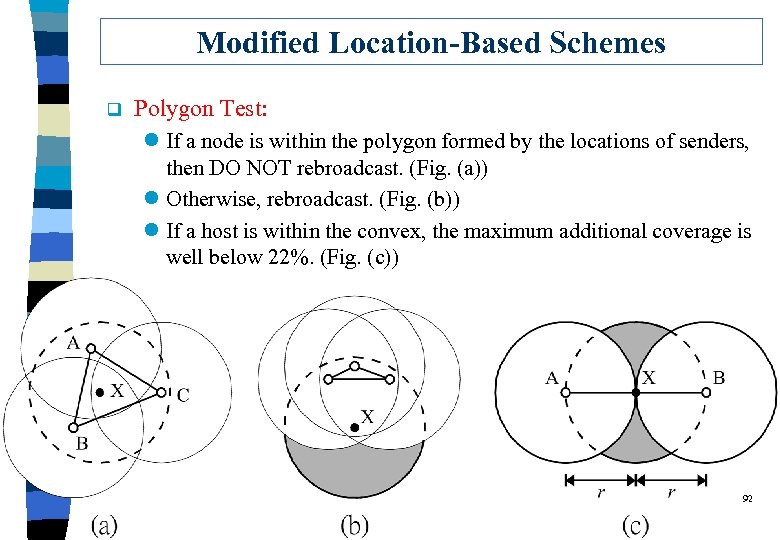
Modified Location-Based Schemes q Polygon Test: l If a node is within the polygon formed by the locations of senders, then DO NOT rebroadcast. (Fig. (a)) l Otherwise, rebroadcast. (Fig. (b)) l If a host is within the convex, the maximum additional coverage is well below 22%. (Fig. (c)) 92
A Short Summary q Main Concern: l Extra coverage of a rebroadcast q Different levels of accuracy: l probabilistic, counter, distance, location, polygon q Performance: l Flooding < Probabilistic Scheme < Counter-Based Scheme < Distance-Based Scheme < Location-Based 93

Relationship between Reachability and Saving q Points closer to the upper-right corner are better. 94
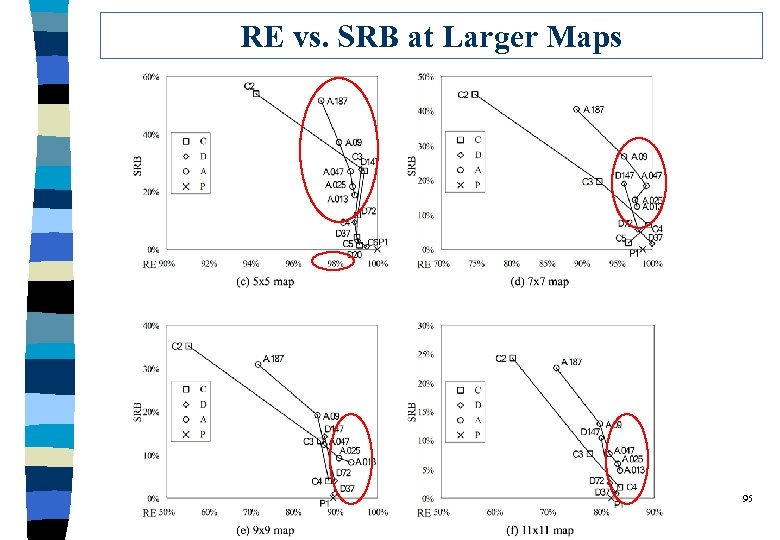
RE vs. SRB at Larger Maps 95
Conclusions q Broadcast Storm: l a newly identified problem that could affect the performance of MANET l deserve more debate in the future l high severity: Ø redundancy, contention, collision q Solutions: l based on the expected additional coverage of a rebroadcast l probabilistic ==> counter ==> distance ==> location 96

Medium Access Control (MAC) Introduction (IEEE 802. 11 Background)
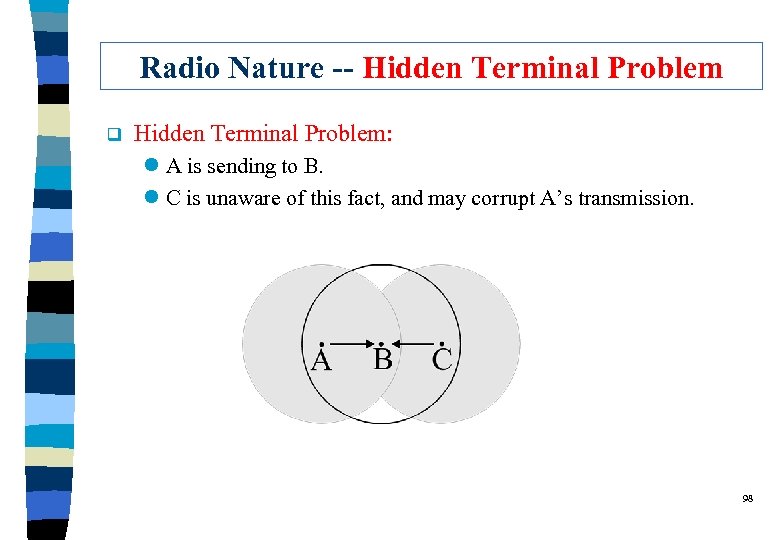
Radio Nature -- Hidden Terminal Problem q Hidden Terminal Problem: l A is sending to B. l C is unaware of this fact, and may corrupt A’s transmission. 98
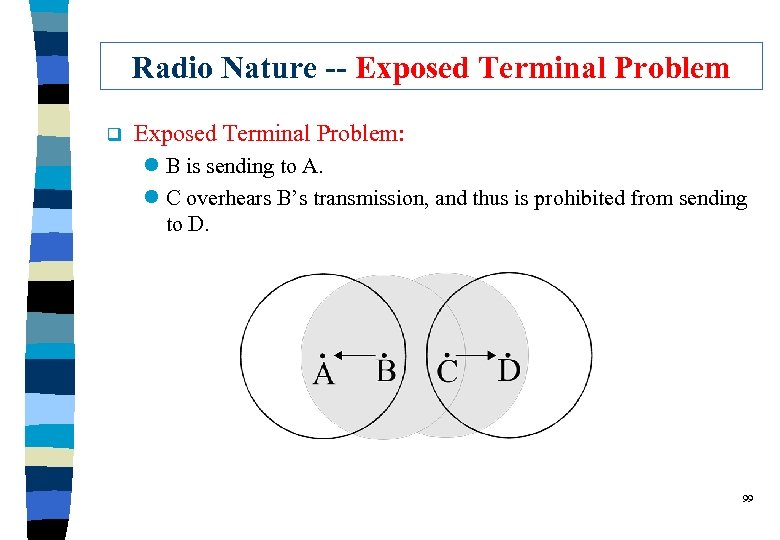
Radio Nature -- Exposed Terminal Problem q Exposed Terminal Problem: l B is sending to A. l C overhears B’s transmission, and thus is prohibited from sending to D. 99
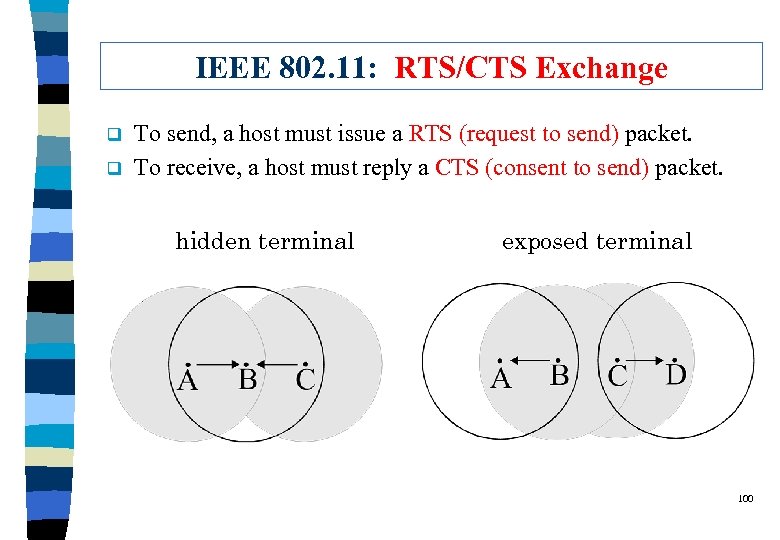
IEEE 802. 11: RTS/CTS Exchange q q To send, a host must issue a RTS (request to send) packet. To receive, a host must reply a CTS (consent to send) packet. hidden terminal exposed terminal 100

IEEE 802. 11: CSMA/CA q CSMA (Carrier Sense Multiple Access): l sense the channel before attempting to transmit l several packets may collide at the end of previous transmission q CD (collision detection): l abort current transmission once collision is detected l in Ethernet, collision can be sensed at transmitter side l IEEE 802. 3 for Ethernet q CA (collision avoidance): l hard to sense collision while transmission is going on l exponential-backoff + acknowledge + RTS-CTS l IEEE 802. 11 for wireless LAN 101
79bfe7ecfe24d6c290d855099a6c8d3c.ppt