9e6f82eb9716533b819f454800dfd9ad.ppt
- Количество слайдов: 92

Role-Based Access Control Prof. Ravi Sandhu Laboratory for Information Security Technology George Mason University www. list. gmu. edu sandhu@gmu. edu © 2004 Ravi Sandhu www. list. gmu. edu

Access Control Models: A perspective © 2004 Ravi Sandhu www. list. gmu. edu
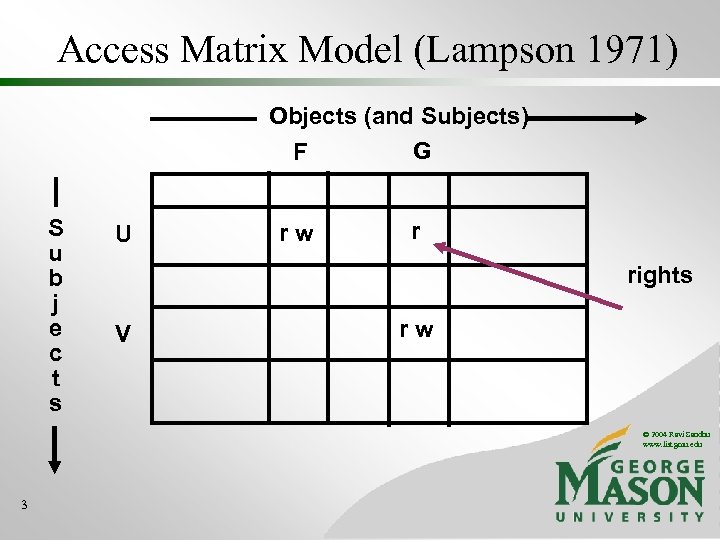
Access Matrix Model (Lampson 1971) Objects (and Subjects) G F S u b j e c t s U rw r rights V rw © 2004 Ravi Sandhu www. list. gmu. edu 3

Access Matrix Model • Separates authentication from authorization • Rights are persistent These items have come into question in recent times, but that is a topic for another talk. • Separates model from implementation • Policy versus mechanism This separation continues to be valuable and will be discussed and refined later in this talk. © 2004 Ravi Sandhu www. list. gmu. edu 4

MAC, DAC and RBAC • For 25 years (1971 -96) access control was divided into • Mandatory Access Control (MAC) • Discretionary Access Control (DAC) • Since the early-mid 1990’s Role-Based Access Control (RBAC) has become a dominant force • RBAC subsumes MAC and DAC • RBAC is not the “final” answer BUT is a critical piece of the “final” answer © 2004 Ravi Sandhu www. list. gmu. edu 5
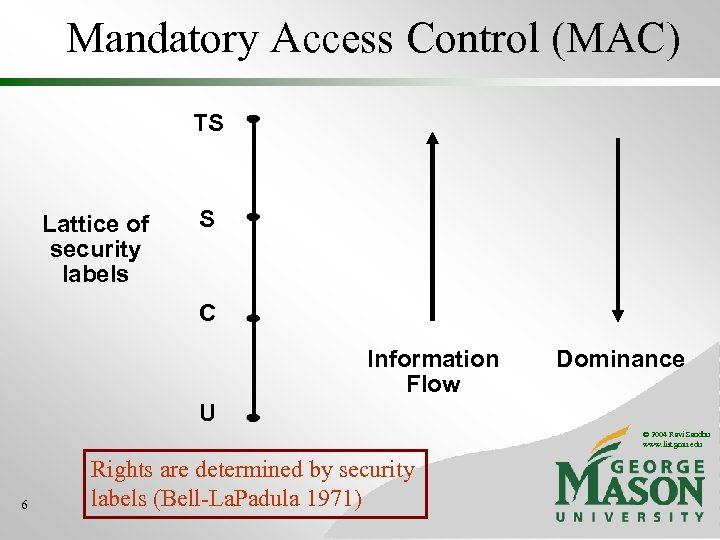
Mandatory Access Control (MAC) TS Lattice of security labels S C Information Flow Dominance U © 2004 Ravi Sandhu www. list. gmu. edu 6 Rights are determined by security labels (Bell-La. Padula 1971)
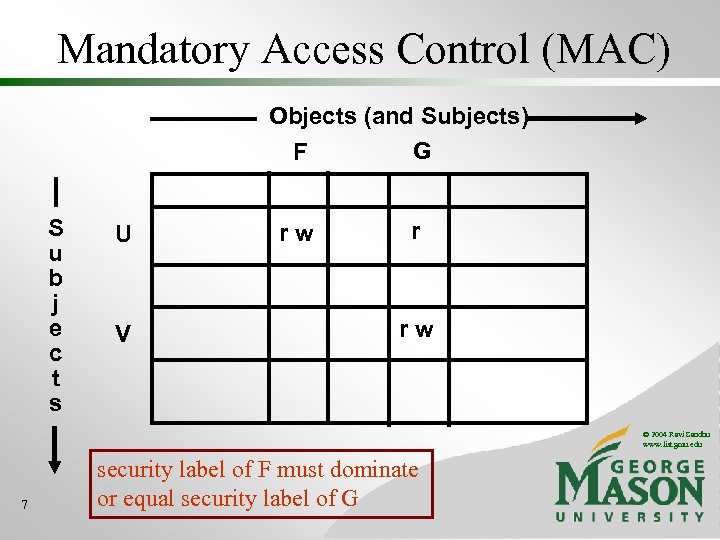
Mandatory Access Control (MAC) Objects (and Subjects) G F S u b j e c t s U V rw r rw © 2004 Ravi Sandhu www. list. gmu. edu 7 security label of F must dominate or equal security label of G

Discretionary Access Control (DAC) • The owner of a resource determines access to that resource • The owner is often the creator of the resource • Fails to distinguish read from copy • This distinction has re-emerged recently under the name Dissemination Control (DCON) © 2004 Ravi Sandhu www. list. gmu. edu 8
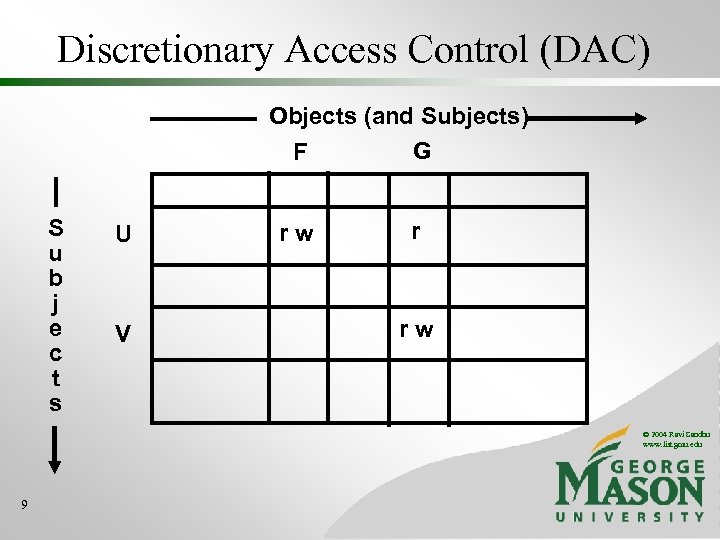
Discretionary Access Control (DAC) Objects (and Subjects) G F S u b j e c t s U V rw r rw © 2004 Ravi Sandhu www. list. gmu. edu 9
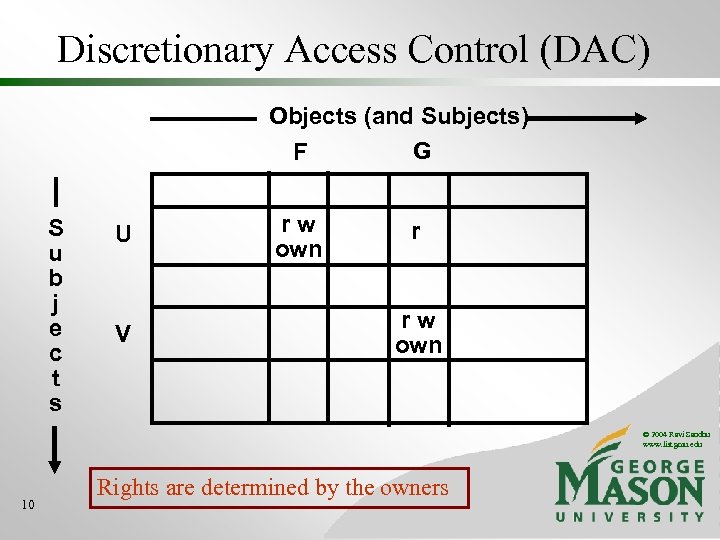
Discretionary Access Control (DAC) Objects (and Subjects) G F S u b j e c t s U V rw own r rw own © 2004 Ravi Sandhu www. list. gmu. edu 10 Rights are determined by the owners
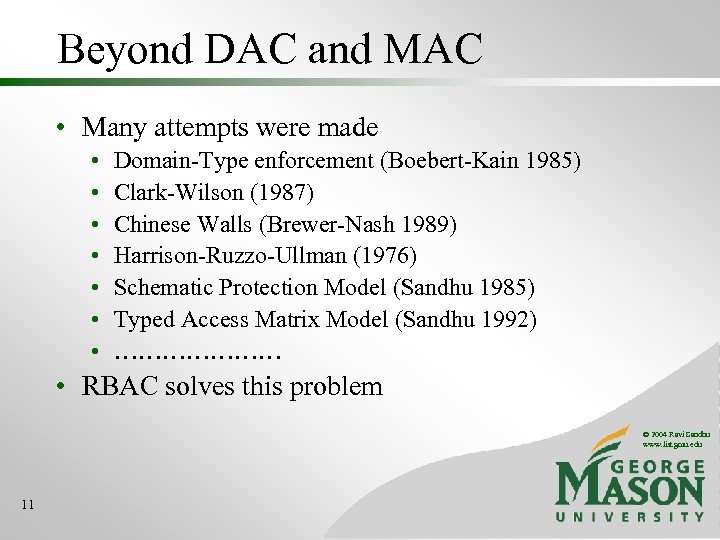
Beyond DAC and MAC • Many attempts were made • • Domain-Type enforcement (Boebert-Kain 1985) Clark-Wilson (1987) Chinese Walls (Brewer-Nash 1989) Harrison-Ruzzo-Ullman (1976) Schematic Protection Model (Sandhu 1985) Typed Access Matrix Model (Sandhu 1992) ………………… • RBAC solves this problem © 2004 Ravi Sandhu www. list. gmu. edu 11
Role-Based Access Control: The RBAC 96 Model • Ravi Sandhu, Edward Coyne, Hal Feinstein and Charles Youman, “Role-Based Access Control Models. ” IEEE Computer, Volume 29, Number 2, February 1996, pages 38 -47. © 2004 Ravi Sandhu www. list. gmu. edu
ROLE-BASED ACCESS CONTROL (RBAC) • A user’s permissions are determined by the user’s roles • rather than identity or clearance • roles can encode arbitrary attributes • multi-faceted • ranges from very simple to very sophisticated © 2004 Ravi Sandhu www. list. gmu. edu 13
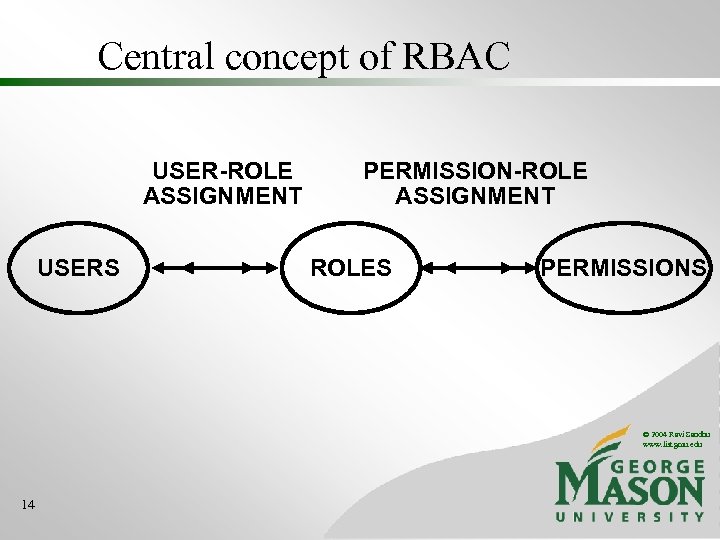
Central concept of RBAC USER-ROLE ASSIGNMENT USERS PERMISSION-ROLE ASSIGNMENT ROLES PERMISSIONS © 2004 Ravi Sandhu www. list. gmu. edu 14

WHAT IS THE POLICY IN RBAC? • RBAC is a framework to help in articulating policy • The main point of RBAC is to facilitate security management © 2004 Ravi Sandhu www. list. gmu. edu 15

RBAC SECURITY PRINCIPLES • • least privilege separation of duties separation of administration and access abstract operations © 2004 Ravi Sandhu www. list. gmu. edu 16
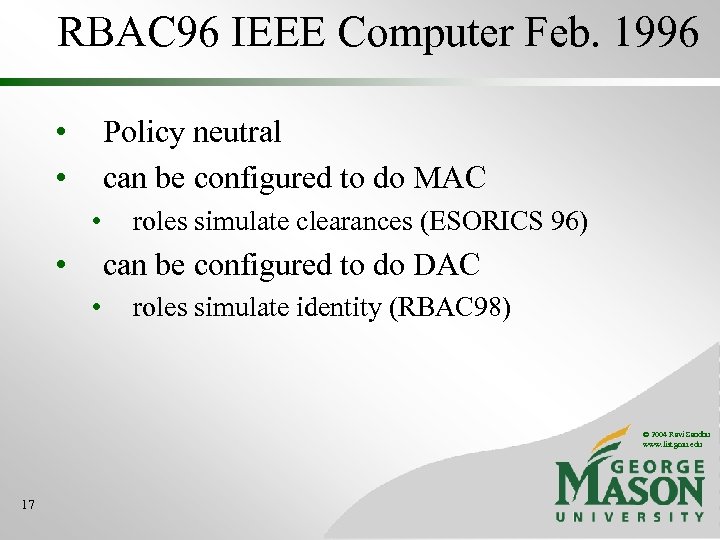
RBAC 96 IEEE Computer Feb. 1996 • • Policy neutral can be configured to do MAC • • roles simulate clearances (ESORICS 96) can be configured to do DAC • roles simulate identity (RBAC 98) © 2004 Ravi Sandhu www. list. gmu. edu 17
WHAT IS RBAC? • multidimensional • open ended • ranges from simple to sophisticated © 2004 Ravi Sandhu www. list. gmu. edu 18
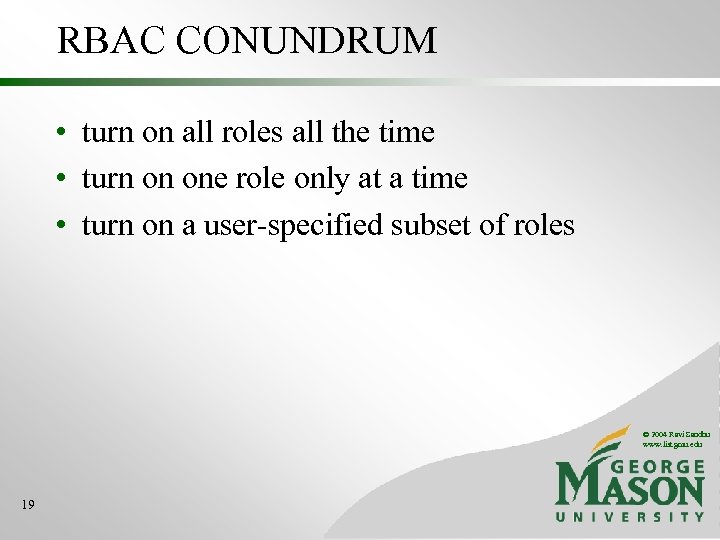
RBAC CONUNDRUM • turn on all roles all the time • turn on one role only at a time • turn on a user-specified subset of roles © 2004 Ravi Sandhu www. list. gmu. edu 19
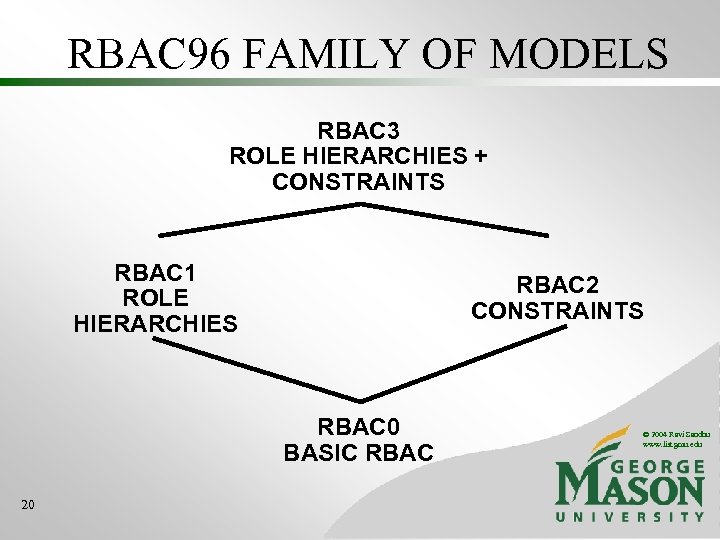
RBAC 96 FAMILY OF MODELS RBAC 3 ROLE HIERARCHIES + CONSTRAINTS RBAC 1 ROLE HIERARCHIES RBAC 2 CONSTRAINTS RBAC 0 BASIC RBAC 20 © 2004 Ravi Sandhu www. list. gmu. edu
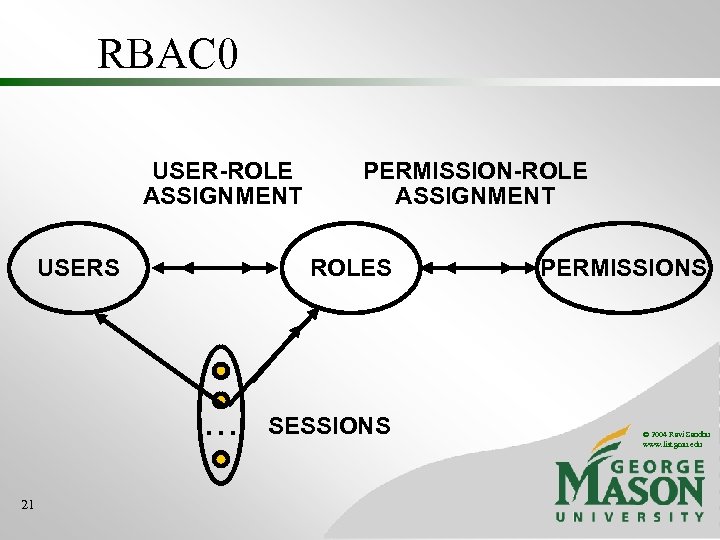
RBAC 0 USER-ROLE ASSIGNMENT USERS ROLES . . . 21 PERMISSION-ROLE ASSIGNMENT SESSIONS PERMISSIONS © 2004 Ravi Sandhu www. list. gmu. edu

PERMISSIONS • Primitive permissions • read, write, append, execute • Abstract permissions • credit, debit, inquiry © 2004 Ravi Sandhu www. list. gmu. edu 22

PERMISSIONS • System permissions • Auditor • Object permissions • read, write, append, execute, credit, debit, inquiry © 2004 Ravi Sandhu www. list. gmu. edu 23

PERMISSIONS • Permissions are positive • No negative permissions or denials • negative permissions and denials can be handled by constraints • No duties or obligations • outside scope of access control © 2004 Ravi Sandhu www. list. gmu. edu 24

ROLES AS POLICY • A role brings together • a collection of users and • a collection of permissions • These collections will vary over time • A role has significance and meaning beyond the particular users and permissions brought together at any moment © 2004 Ravi Sandhu www. list. gmu. edu 25

ROLES VERSUS GROUPS • Groups are often defined as • a collection of users • A role is • a collection of users and • a collection of permissions • Some authors define role as • a collection of permissions © 2004 Ravi Sandhu www. list. gmu. edu 26

USERS • Users are • human beings or • other active agents • Each individual should be known as exactly one user © 2004 Ravi Sandhu www. list. gmu. edu 27

USER-ROLE ASSIGNMENT • A user can be a member of many roles • Each role can have many users as members © 2004 Ravi Sandhu www. list. gmu. edu 28

SESSIONS • A user can invoke multiple sessions • In each session a user can invoke any subset of roles that the user is a member of © 2004 Ravi Sandhu www. list. gmu. edu 29

PERMISSION-ROLE ASSIGNMENT • A permission can be assigned to many roles • Each role can have many permissions © 2004 Ravi Sandhu www. list. gmu. edu 30
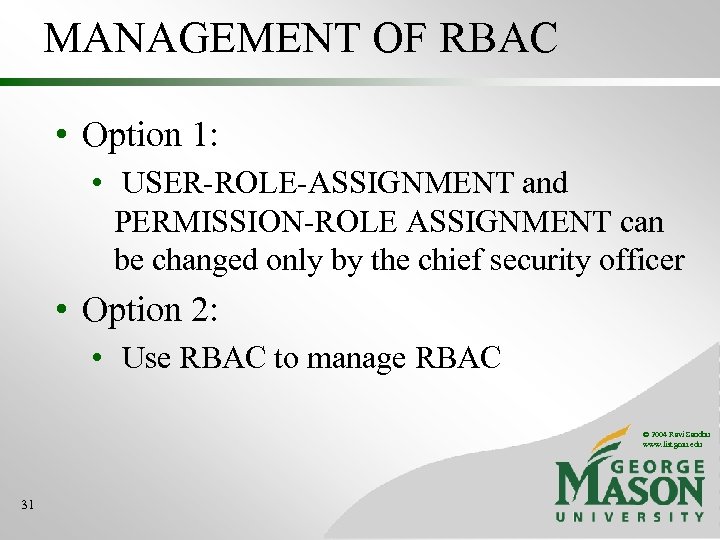
MANAGEMENT OF RBAC • Option 1: • USER-ROLE-ASSIGNMENT and PERMISSION-ROLE ASSIGNMENT can be changed only by the chief security officer • Option 2: • Use RBAC to manage RBAC © 2004 Ravi Sandhu www. list. gmu. edu 31
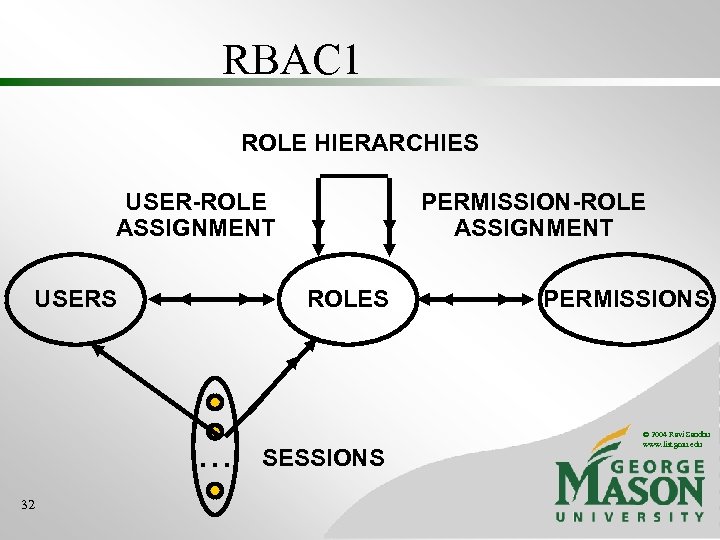
RBAC 1 ROLE HIERARCHIES USER-ROLE ASSIGNMENT USERS ROLES . . . 32 PERMISSION-ROLE ASSIGNMENT SESSIONS PERMISSIONS © 2004 Ravi Sandhu www. list. gmu. edu
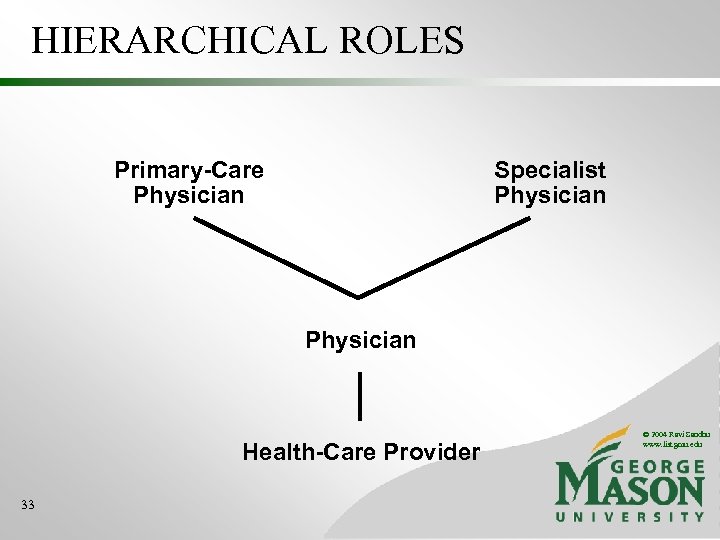
HIERARCHICAL ROLES Primary-Care Physician Specialist Physician Health-Care Provider 33 © 2004 Ravi Sandhu www. list. gmu. edu
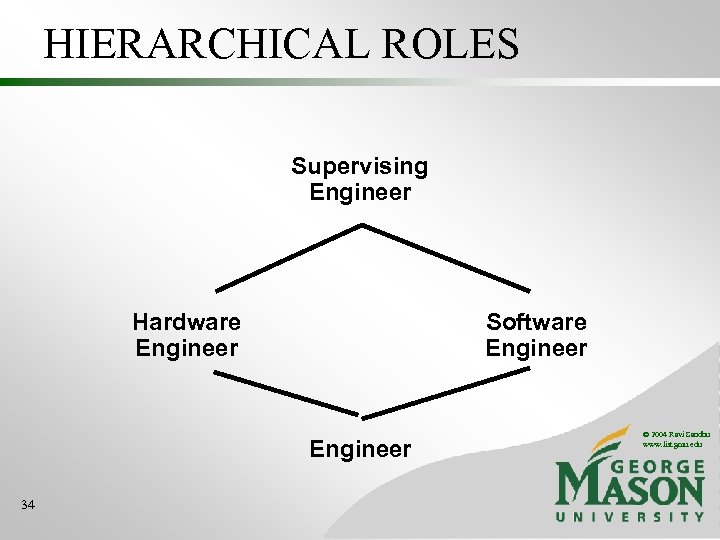
HIERARCHICAL ROLES Supervising Engineer Hardware Engineer Software Engineer 34 © 2004 Ravi Sandhu www. list. gmu. edu
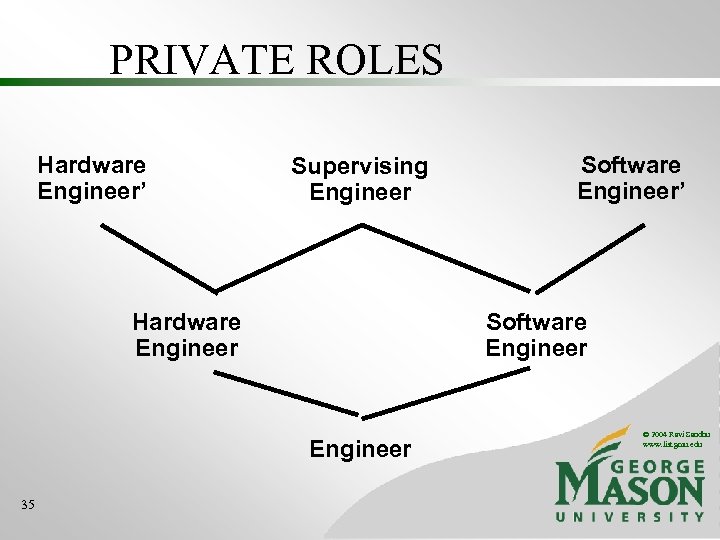
PRIVATE ROLES Hardware Engineer’ Supervising Engineer Hardware Engineer Software Engineer 35 Software Engineer’ © 2004 Ravi Sandhu www. list. gmu. edu
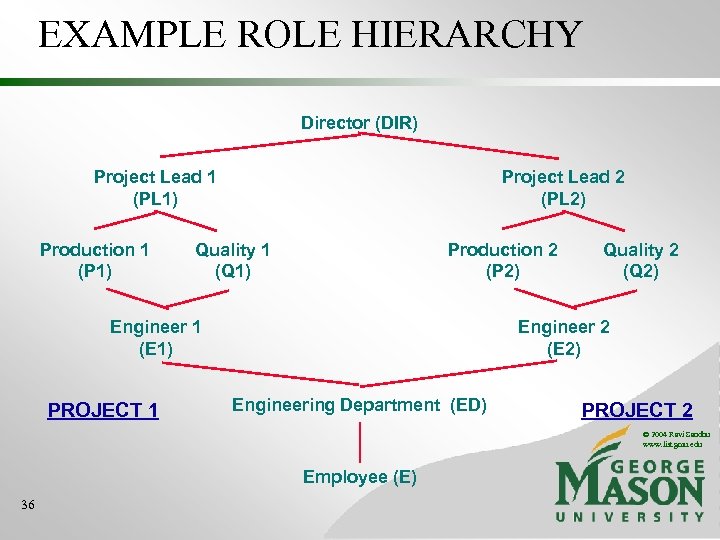
EXAMPLE ROLE HIERARCHY Director (DIR) Project Lead 1 (PL 1) Production 1 (P 1) Project Lead 2 (PL 2) Quality 1 (Q 1) Production 2 (P 2) Engineer 1 (E 1) PROJECT 1 Quality 2 (Q 2) Engineer 2 (E 2) Engineering Department (ED) PROJECT 2 © 2004 Ravi Sandhu www. list. gmu. edu Employee (E) 36
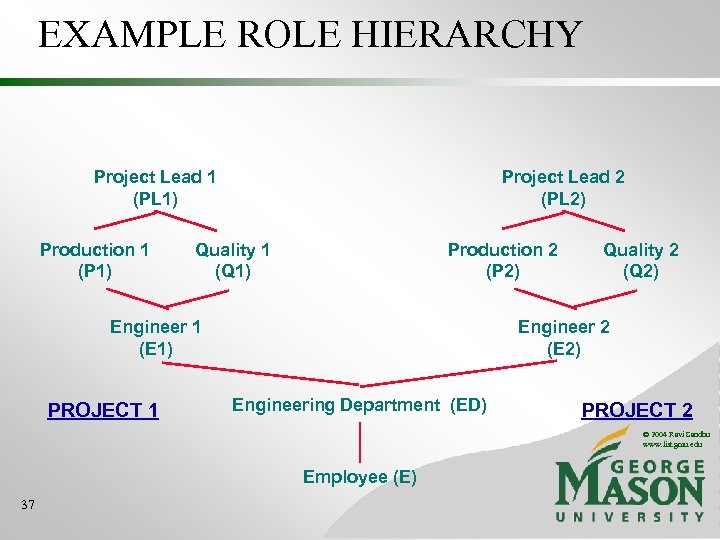
EXAMPLE ROLE HIERARCHY Project Lead 1 (PL 1) Production 1 (P 1) Project Lead 2 (PL 2) Quality 1 (Q 1) Production 2 (P 2) Engineer 1 (E 1) PROJECT 1 Quality 2 (Q 2) Engineer 2 (E 2) Engineering Department (ED) PROJECT 2 © 2004 Ravi Sandhu www. list. gmu. edu Employee (E) 37
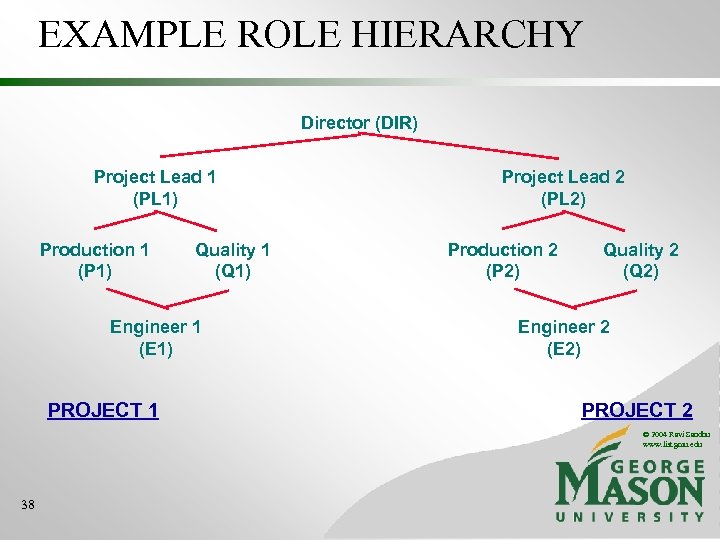
EXAMPLE ROLE HIERARCHY Director (DIR) Project Lead 1 (PL 1) Production 1 (P 1) Quality 1 (Q 1) Engineer 1 (E 1) PROJECT 1 Project Lead 2 (PL 2) Production 2 (P 2) Quality 2 (Q 2) Engineer 2 (E 2) PROJECT 2 © 2004 Ravi Sandhu www. list. gmu. edu 38
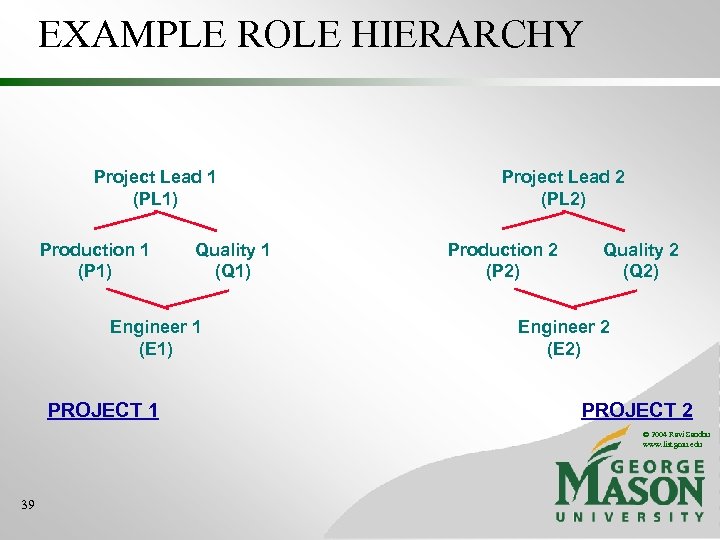
EXAMPLE ROLE HIERARCHY Project Lead 1 (PL 1) Production 1 (P 1) Quality 1 (Q 1) Engineer 1 (E 1) PROJECT 1 Project Lead 2 (PL 2) Production 2 (P 2) Quality 2 (Q 2) Engineer 2 (E 2) PROJECT 2 © 2004 Ravi Sandhu www. list. gmu. edu 39
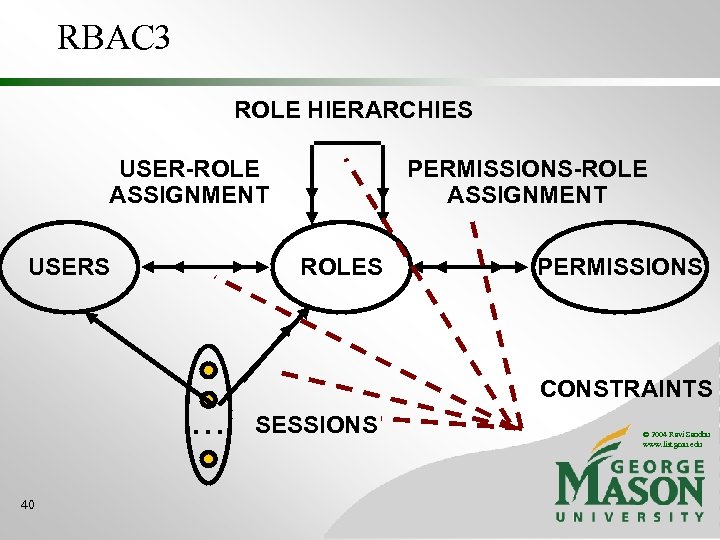
RBAC 3 ROLE HIERARCHIES USER-ROLE ASSIGNMENT USERS ROLES . . . 40 PERMISSIONS-ROLE ASSIGNMENT PERMISSIONS CONSTRAINTS SESSIONS © 2004 Ravi Sandhu www. list. gmu. edu

CONSTRAINTS Mutually Exclusive Roles • Static Exclusion: The same individual can never hold both roles • Dynamic Exclusion: The same individual can never hold both roles in the same context © 2004 Ravi Sandhu www. list. gmu. edu 41

CONSTRAINTS • Mutually Exclusive Permissions • Static Exclusion: The same role should never be assigned both permissions • Dynamic Exclusion: The same role can never hold both permissions in the same context © 2004 Ravi Sandhu www. list. gmu. edu 42

CONSTRAINTS • Cardinality Constraints on User-Role Assignment • At most k users can belong to the role • At least k users must belong to the role • Exactly k users must belong to the role © 2004 Ravi Sandhu www. list. gmu. edu 43

CONSTRAINTS • Cardinality Constraints on Permissions-Role Assignment • At most k roles can get the permission • At least k roles must get the permission • Exactly k roles must get the permission © 2004 Ravi Sandhu www. list. gmu. edu 44

The NIST-ANSI and (hopefully) soon-to -be ISO RBAC Standard Model • David F. Ferraiolo, Ravi Sandhu, Serban Gavrila, D. Richard Kuhn and Ramaswamy Chandramouli. “Proposed NIST Standard for Role-Based Access Control. ” ACM Transactions on Information and System Security, Volume 4, Number 3, August 2001, pages 224 -274. © 2004 Ravi Sandhu www. list. gmu. edu

The NIST-ANSI-ISO RBAC Model • Adds much needed detail and consensus agreement to the RBAC 96 model and other contemporary models • Focuses on areas where consensus agreement exists and commercial implementations have been demonstrated • Leaves many important areas for future work • Eventual goal is much more ambitious • Test suite for conformance testing © 2004 Ravi Sandhu www. list. gmu. edu 46
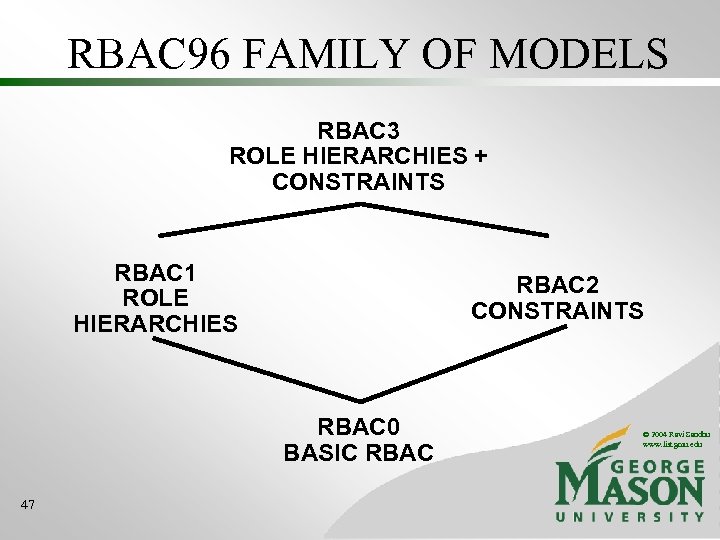
RBAC 96 FAMILY OF MODELS RBAC 3 ROLE HIERARCHIES + CONSTRAINTS RBAC 1 ROLE HIERARCHIES RBAC 2 CONSTRAINTS RBAC 0 BASIC RBAC 47 © 2004 Ravi Sandhu www. list. gmu. edu
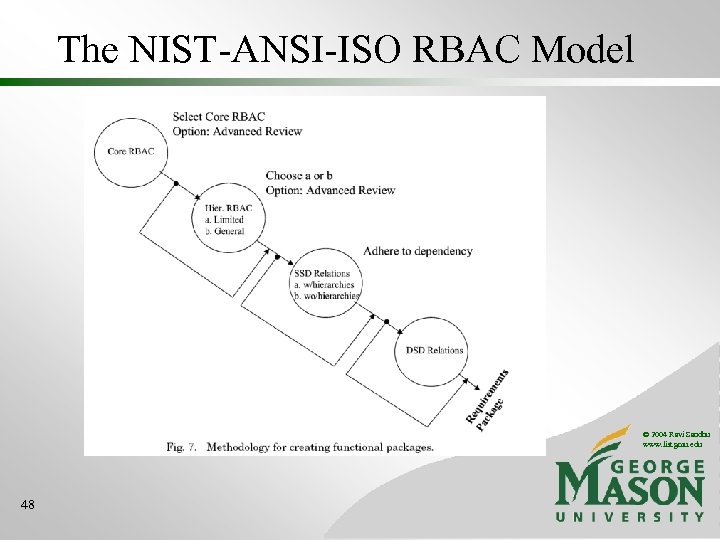
The NIST-ANSI-ISO RBAC Model © 2004 Ravi Sandhu www. list. gmu. edu 48

The NIST-ANSI-ISO RBAC Model • Additional details • Administrative Functions • Supporting System Functions • Review Functions © 2004 Ravi Sandhu www. list. gmu. edu 49
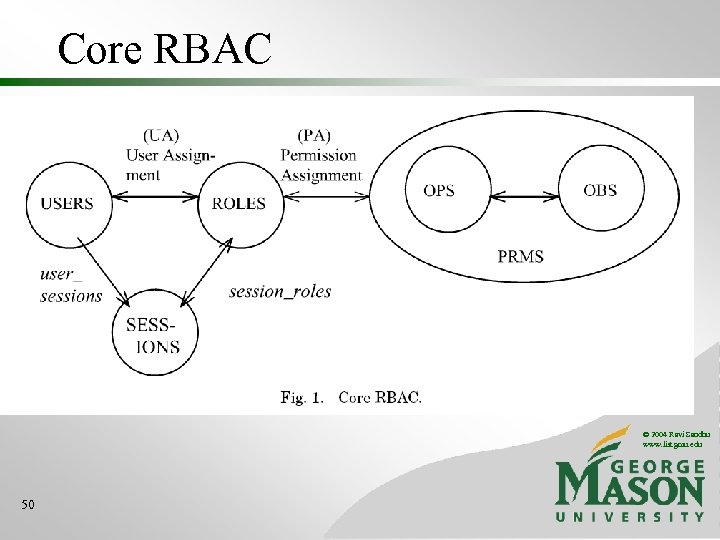
Core RBAC © 2004 Ravi Sandhu www. list. gmu. edu 50

Core RBAC: Administrative Functions • • Add. User Delete. User Add. Role Delete. Role Assign. User Deassign. User Grant-Permission Revoke-Permission © 2004 Ravi Sandhu www. list. gmu. edu 51

Core RBAC: Supporting System Functions • • Create. Session Add. Active. Role Drop. Active. Role Check. Access © 2004 Ravi Sandhu www. list. gmu. edu 52

Core RBAC: Review Functions • Required • Assigned. Users • Assigned. Roles • Optional • • • Role. Permissions User. Permissions Session. Roles Session. Permissions Role. Operations. On. Object Session. Operations. On. Object Role-user review is required Role-permission review is optional © 2004 Ravi Sandhu www. list. gmu. edu 53
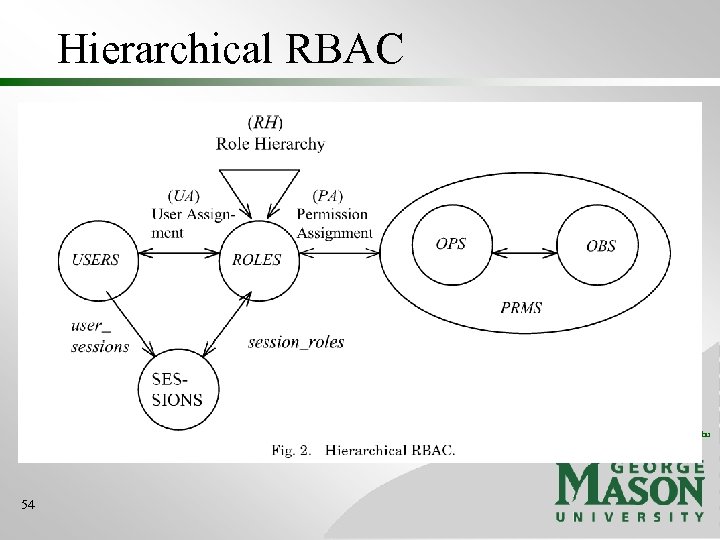
Hierarchical RBAC © 2004 Ravi Sandhu www. list. gmu. edu 54
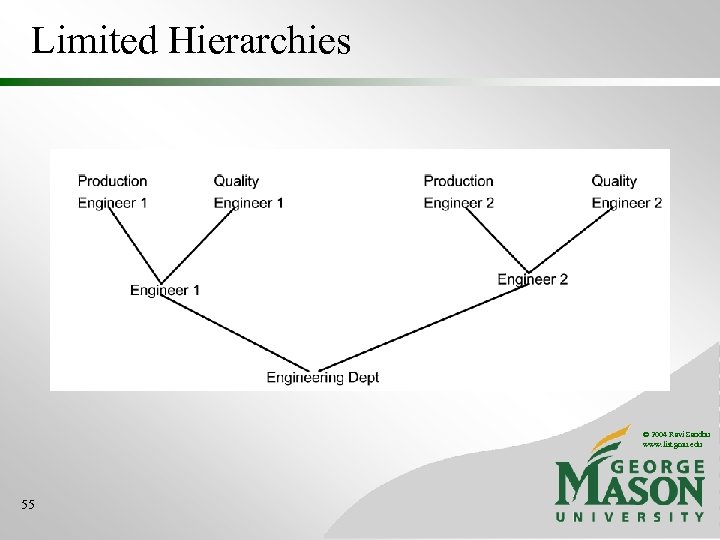
Limited Hierarchies © 2004 Ravi Sandhu www. list. gmu. edu 55
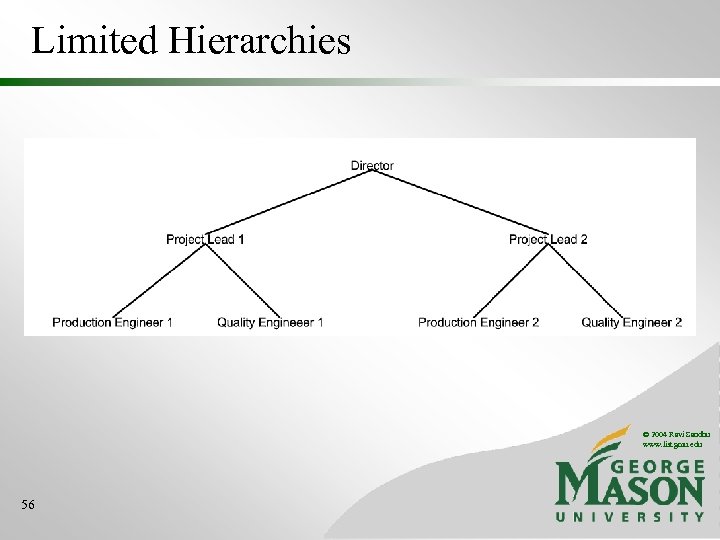
Limited Hierarchies © 2004 Ravi Sandhu www. list. gmu. edu 56
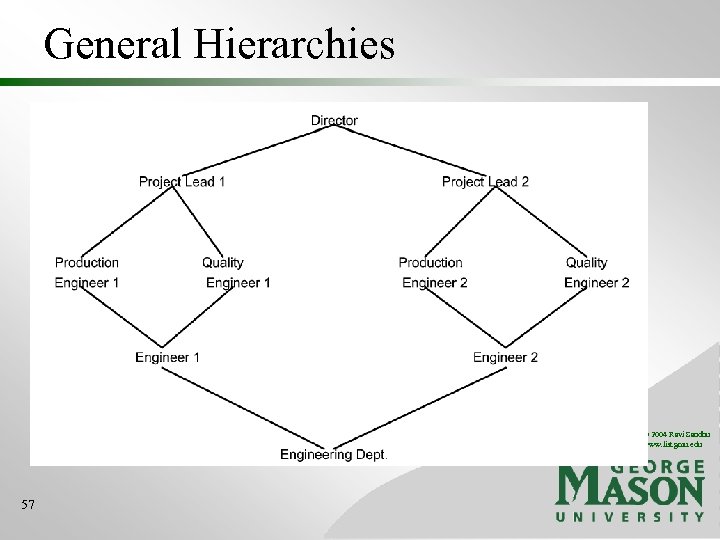
General Hierarchies © 2004 Ravi Sandhu www. list. gmu. edu 57
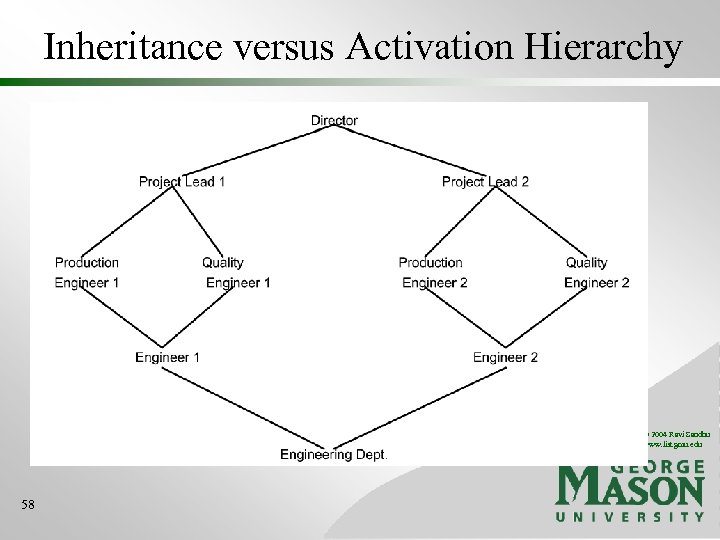
Inheritance versus Activation Hierarchy © 2004 Ravi Sandhu www. list. gmu. edu 58
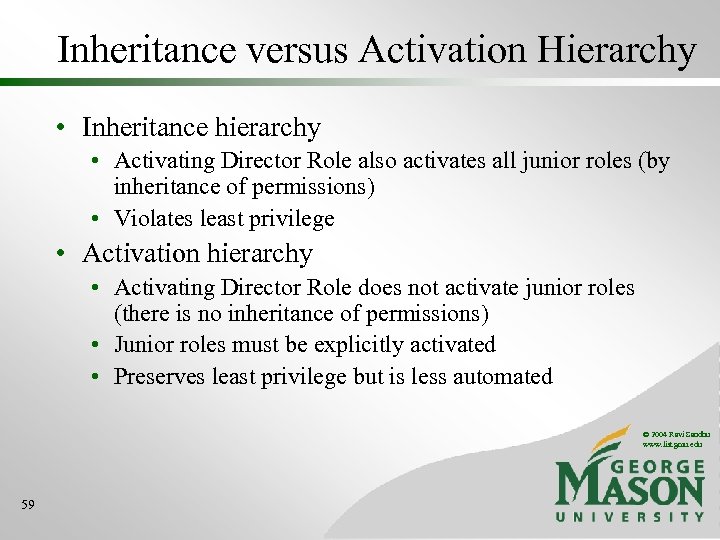
Inheritance versus Activation Hierarchy • Inheritance hierarchy • Activating Director Role also activates all junior roles (by inheritance of permissions) • Violates least privilege • Activation hierarchy • Activating Director Role does not activate junior roles (there is no inheritance of permissions) • Junior roles must be explicitly activated • Preserves least privilege but is less automated © 2004 Ravi Sandhu www. list. gmu. edu 59
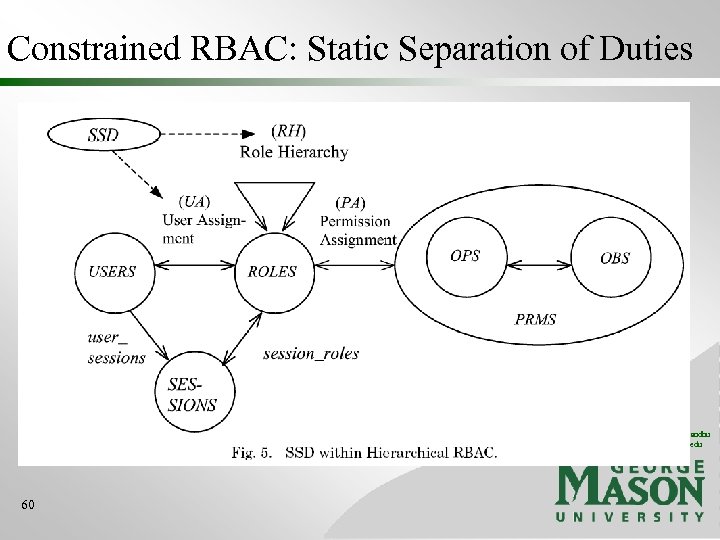
Constrained RBAC: Static Separation of Duties © 2004 Ravi Sandhu www. list. gmu. edu 60
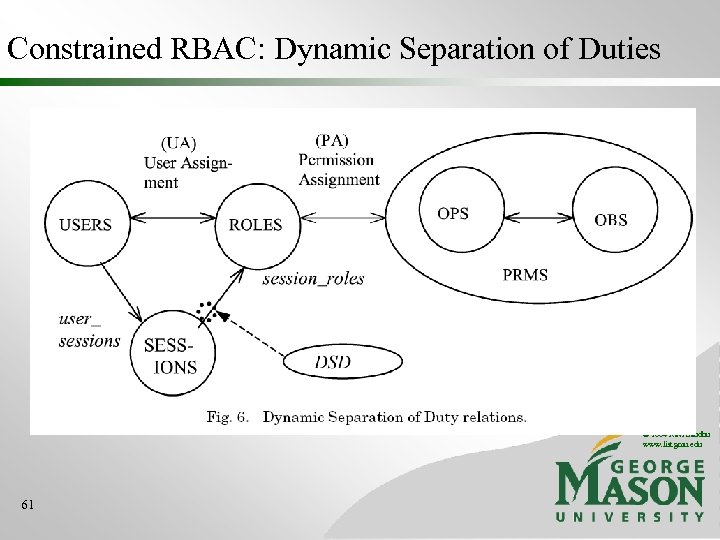
Constrained RBAC: Dynamic Separation of Duties © 2004 Ravi Sandhu www. list. gmu. edu 61

MAC and DAC in RBAC • Sylvia Osborn, Ravi Sandhu and Qamar Munawer. “Configuring Role-Based Access Control to Enforce Mandatory and Discretionary Access Control Policies. ” ACM Transactions on Information and System Security, Volume 3, Number 2, May 2000, pages 85 -106. © 2004 Ravi Sandhu www. list. gmu. edu
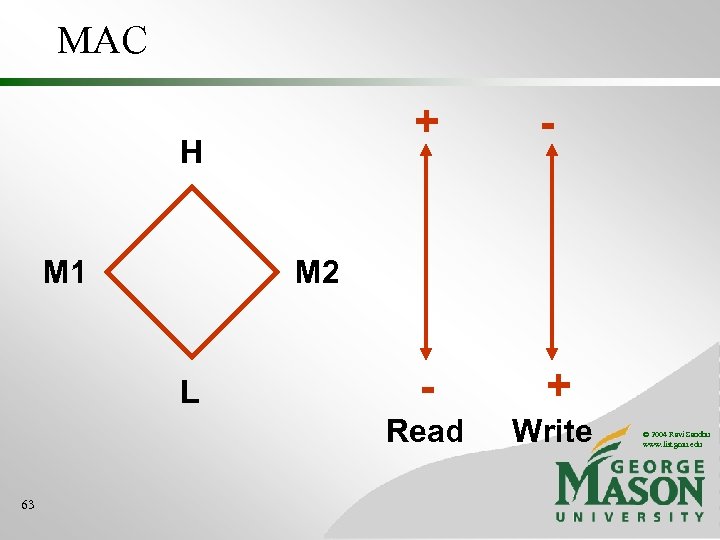
MAC + M 1 + Write M 2 L 63 Read H - © 2004 Ravi Sandhu www. list. gmu. edu
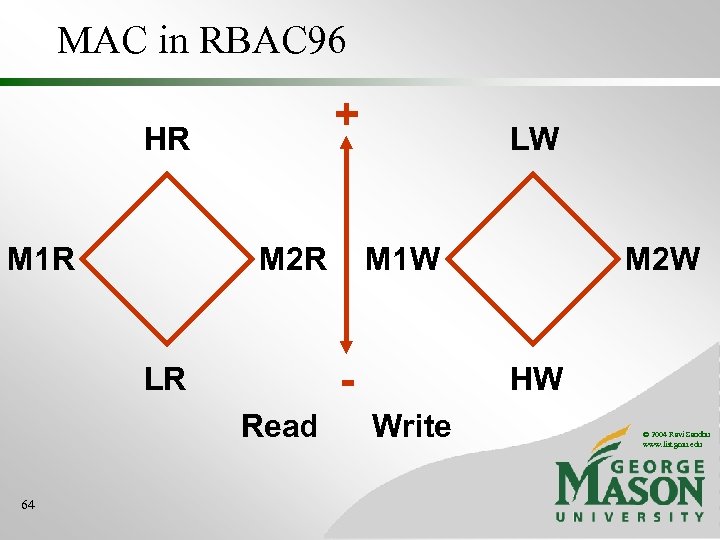
MAC in RBAC 96 + HR M 1 W M 2 R - LR Read 64 LW M 2 W HW Write © 2004 Ravi Sandhu www. list. gmu. edu
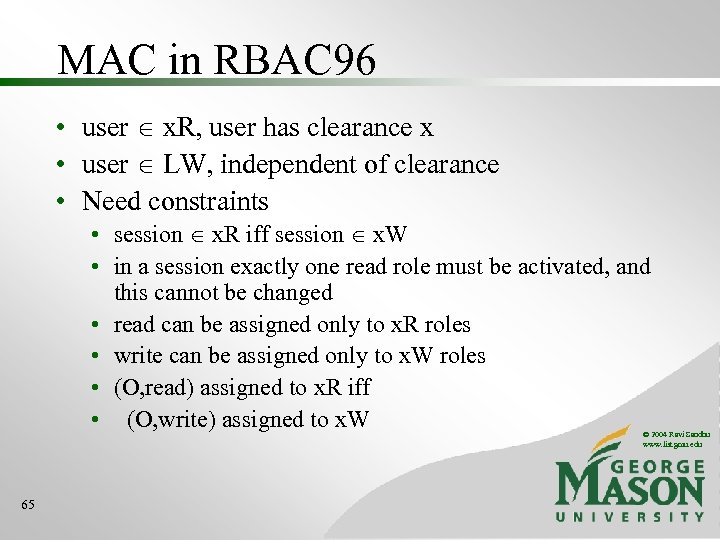
MAC in RBAC 96 • user x. R, user has clearance x • user LW, independent of clearance • Need constraints • session x. R iff session x. W • in a session exactly one read role must be activated, and this cannot be changed • read can be assigned only to x. R roles • write can be assigned only to x. W roles • (O, read) assigned to x. R iff • (O, write) assigned to x. W © 2004 Ravi Sandhu www. list. gmu. edu 65

DAC in RBAC 96 • Construction is more complex • Requires multiple roles for every object • Revocation • Grant-dependent revocation is harder to handle • Grant-independent revocation is easier to handle © 2004 Ravi Sandhu www. list. gmu. edu 66
MAC and DAC in the NIST-ANSI-ISO Model • RBAC 96 constructions use cardinality constraints in addition to Static and Dynamic separation of duties • These constructions are not applicable to NIST-ANSI -ISO RBAC model • Can NIST-ANSI-ISO RBAC model do MAC and DAC? • With extensions: yes • Without extensions: probably not © 2004 Ravi Sandhu www. list. gmu. edu 67

Administrative RBAC: ARBAC 97 • Ravi Sandhu, Venkata Bhamidipati and Qamar Munawer. “The ARBAC 97 Model for Role-Based Administration of Roles. ” ACM Transactions on Information and System Security, Volume 2, Number 1, February 1999, pages 105 -135. © 2004 Ravi Sandhu www. list. gmu. edu
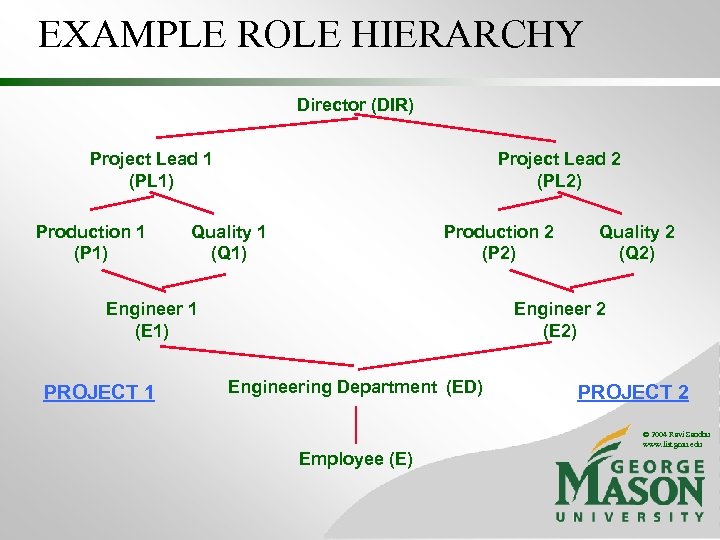
EXAMPLE ROLE HIERARCHY Director (DIR) Project Lead 1 (PL 1) Production 1 (P 1) Project Lead 2 (PL 2) Quality 1 (Q 1) Production 2 (P 2) Engineer 1 (E 1) PROJECT 1 Quality 2 (Q 2) Engineer 2 (E 2) Engineering Department (ED) PROJECT 2 © 2004 Ravi Sandhu www. list. gmu. edu Employee (E)
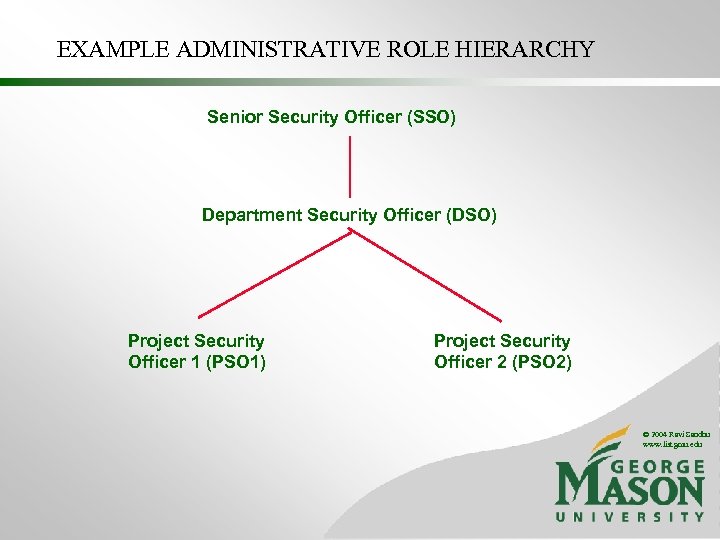
EXAMPLE ADMINISTRATIVE ROLE HIERARCHY Senior Security Officer (SSO) Department Security Officer (DSO) Project Security Officer 1 (PSO 1) Project Security Officer 2 (PSO 2) © 2004 Ravi Sandhu www. list. gmu. edu
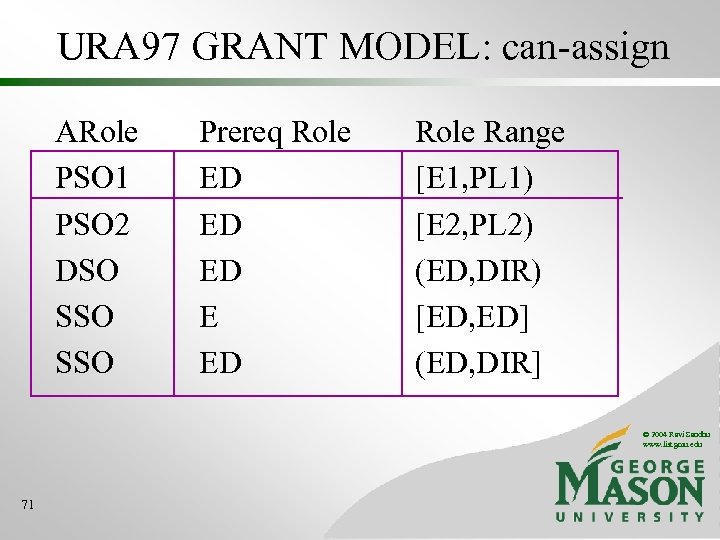
URA 97 GRANT MODEL: can-assign ARole PSO 1 PSO 2 DSO SSO Prereq Role ED ED ED E ED Role Range [E 1, PL 1) [E 2, PL 2) (ED, DIR) [ED, ED] (ED, DIR] © 2004 Ravi Sandhu www. list. gmu. edu 71
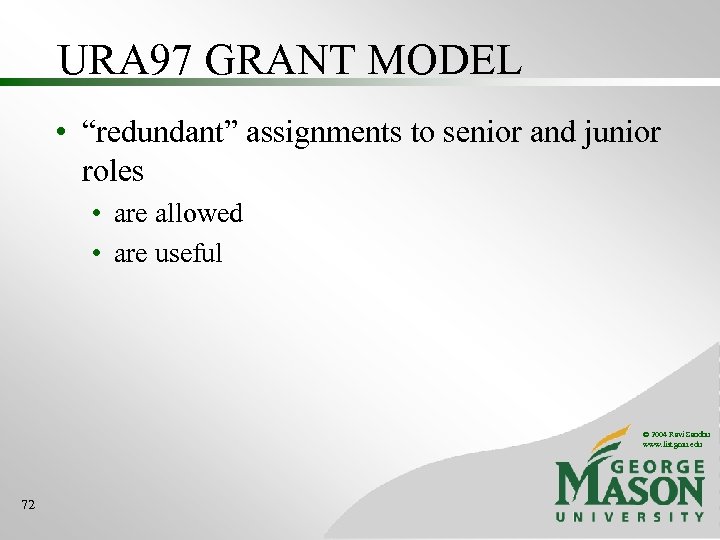
URA 97 GRANT MODEL • “redundant” assignments to senior and junior roles • are allowed • are useful © 2004 Ravi Sandhu www. list. gmu. edu 72

URA 97 REVOKE MODEL WEAK REVOCATION • revokes explicit membership in a role • independent of who did the assignment © 2004 Ravi Sandhu www. list. gmu. edu 73

URA 97 REVOKE MODEL STRONG REVOCATION • revokes explicit membership in a role and its seniors • authorized only if corresponding weak revokes are authorized • alternatives – all-or-nothing – revoke within range © 2004 Ravi Sandhu www. list. gmu. edu 74
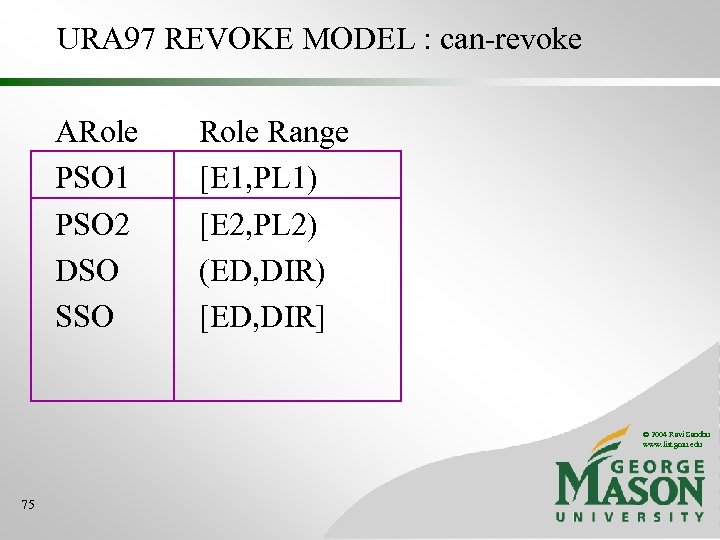
URA 97 REVOKE MODEL : can-revoke ARole PSO 1 PSO 2 DSO SSO Role Range [E 1, PL 1) [E 2, PL 2) (ED, DIR) [ED, DIR] © 2004 Ravi Sandhu www. list. gmu. edu 75

PERMISSION-ROLE ASSIGNMENT • dual of user-role assignment • • can-assign-permission can-revoke-permission weak revoke strong revoke (propagates down) © 2004 Ravi Sandhu www. list. gmu. edu 76
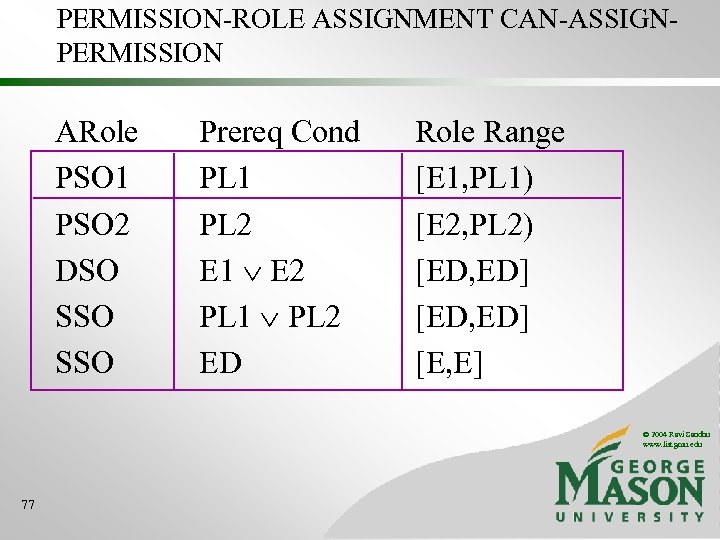
PERMISSION-ROLE ASSIGNMENT CAN-ASSIGNPERMISSION ARole PSO 1 PSO 2 DSO SSO Prereq Cond PL 1 PL 2 E 1 E 2 PL 1 PL 2 ED Role Range [E 1, PL 1) [E 2, PL 2) [ED, ED] [E, E] © 2004 Ravi Sandhu www. list. gmu. edu 77
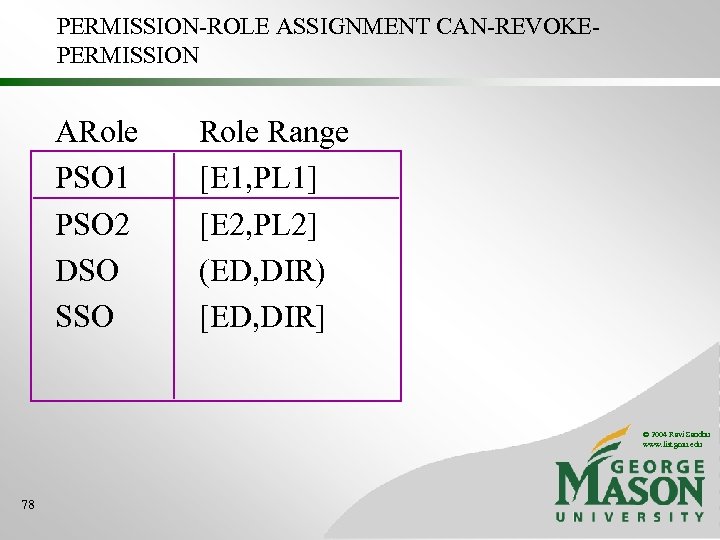
PERMISSION-ROLE ASSIGNMENT CAN-REVOKEPERMISSION ARole PSO 1 PSO 2 DSO SSO Role Range [E 1, PL 1] [E 2, PL 2] (ED, DIR) [ED, DIR] © 2004 Ravi Sandhu www. list. gmu. edu 78

OM-AM and RBAC © 2004 Ravi Sandhu www. list. gmu. edu
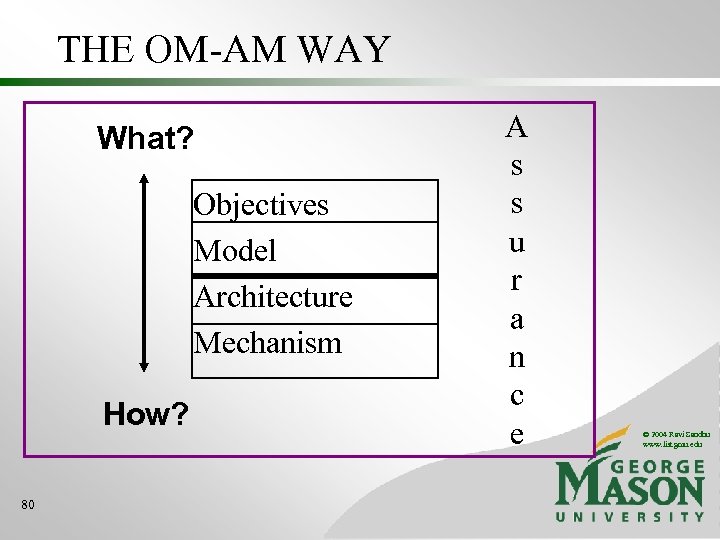
THE OM-AM WAY What? Objectives Model Architecture Mechanism How? 80 A s s u r a n c e © 2004 Ravi Sandhu www. list. gmu. edu
LAYERS AND LAYERS • • Multics rings Layered abstractions Waterfall model Network protocol stacks Napolean layers Ro. Fi layers OM-AM etcetera © 2004 Ravi Sandhu www. list. gmu. edu 81
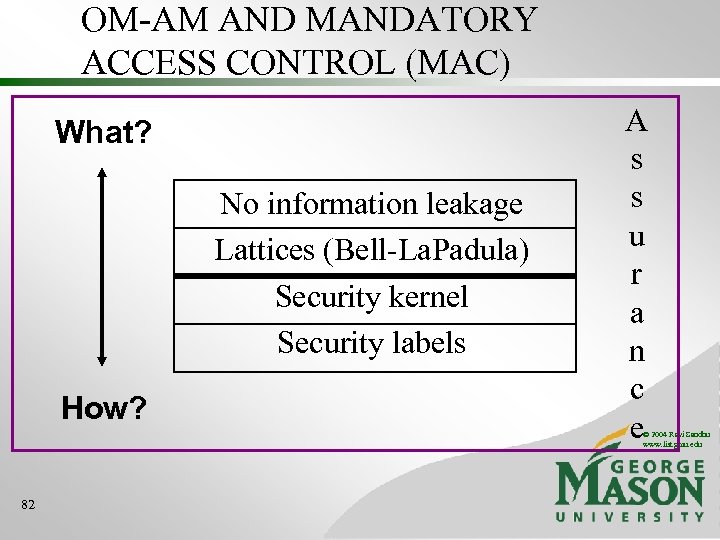
OM-AM AND MANDATORY ACCESS CONTROL (MAC) What? No information leakage Lattices (Bell-La. Padula) Security kernel Security labels How? A s s u r a n c e © 2004 Ravi Sandhu www. list. gmu. edu 82
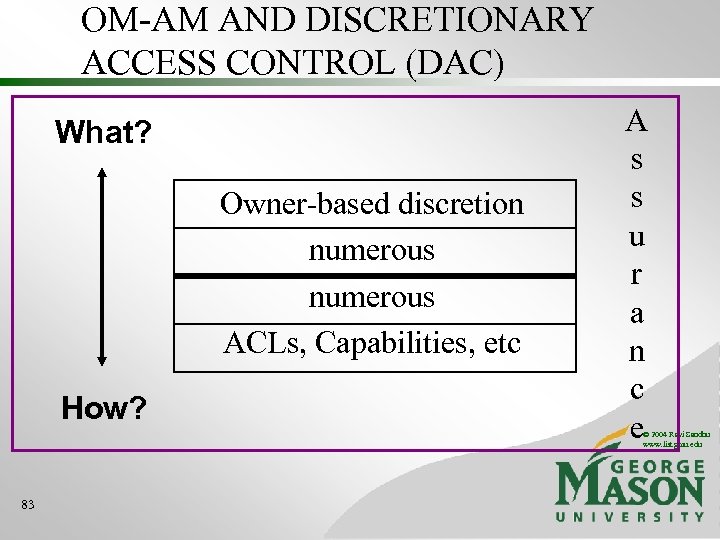
OM-AM AND DISCRETIONARY ACCESS CONTROL (DAC) What? Owner-based discretion numerous ACLs, Capabilities, etc How? A s s u r a n c e © 2004 Ravi Sandhu www. list. gmu. edu 83
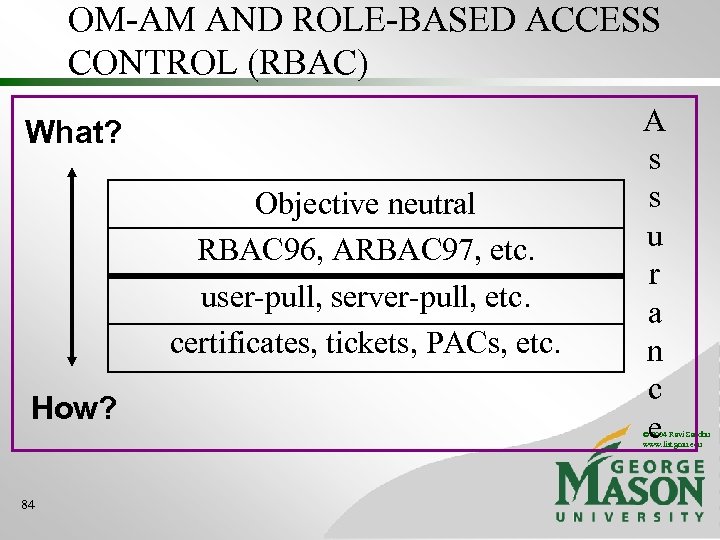
OM-AM AND ROLE-BASED ACCESS CONTROL (RBAC) What? Objective neutral RBAC 96, ARBAC 97, etc. user-pull, server-pull, etc. certificates, tickets, PACs, etc. How? A s s u r a n c e © 2004 Ravi Sandhu www. list. gmu. edu 84
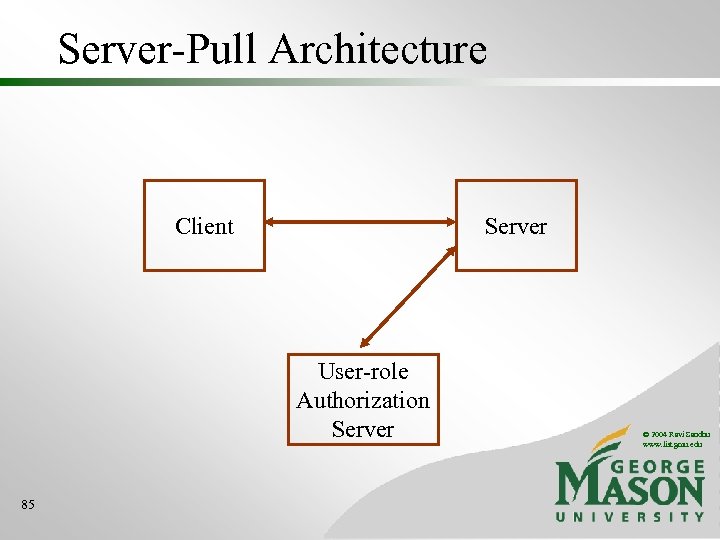
Server-Pull Architecture Client Server User-role Authorization Server 85 © 2004 Ravi Sandhu www. list. gmu. edu
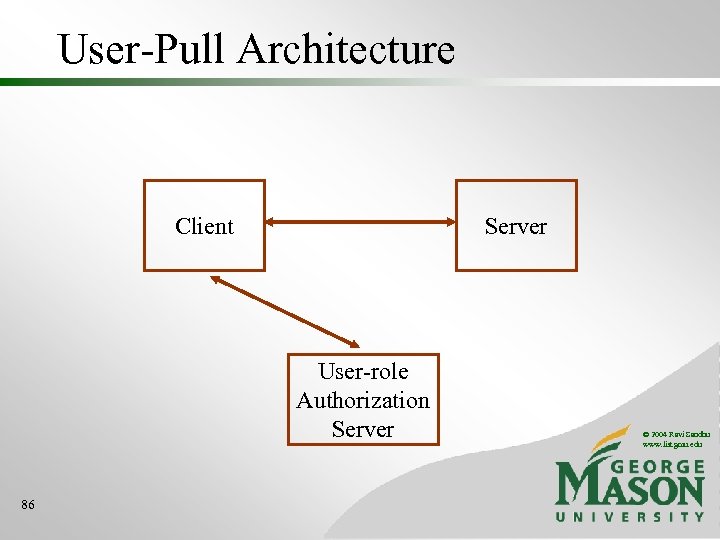
User-Pull Architecture Client Server User-role Authorization Server 86 © 2004 Ravi Sandhu www. list. gmu. edu
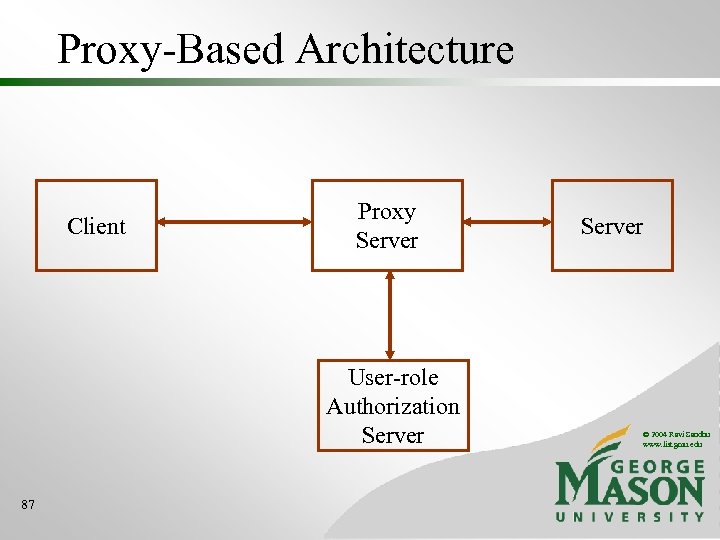
Proxy-Based Architecture Client Proxy Server User-role Authorization Server 87 Server © 2004 Ravi Sandhu www. list. gmu. edu
RBAC Mechanisms • RBAC can be implemented using • Secure cookies: user-pull architecture • X. 509 certificates: user-pull or server-pull architectures © 2004 Ravi Sandhu www. list. gmu. edu 88
Other RBAC Research and Results © 2004 Ravi Sandhu www. list. gmu. edu

RBAC Research (dates are approximate) • • • • The early NIST model: Ferraiolo et al 1992 onwards Role-Graph Model: Osborn et al 1994 onwards OASIS model and architecture: Moody et al 1994 onwards Trust Management: Herzberg, Li, Winsborough, et al 1996 onwards Temporal RBAC: Bertino et al 1998 onwards Constraint languages: Ahn and Sandhu, 2000 Delegation in RBAC: Barka, Sandhu, Ahn et al 2000 onwards RBAC and workflow systems: Atluri, Sandhu, Ahn, Park et al 1998 onwards RBAC administration: Kern, Sandhu, Oh, Moffett et al 1998 onwards RBAC engineering: Thomsen, Kern, Epstein, Sandhu et al 2000 onwards Context-aware RBAC: Covington et al, 2000 onwards Rule-based RBAC: Al-Khatani and Sandhu, 2002 onwards …………………. © 2004 Ravi Sandhu www. list. gmu. edu 90

Ongoing and Future Work in RBAC © 2004 Ravi Sandhu www. list. gmu. edu

Research Challenges • • Automated RBAC engineering Formal models for RBAC Analysis of RBAC policies Integration with attribute-based access control RBAC in pervasive and ad hoc environments Cross-domain RBAC …………. © 2004 Ravi Sandhu www. list. gmu. edu 92
9e6f82eb9716533b819f454800dfd9ad.ppt