ae6d0cde4c9a2d2772d4b8ecc3142b20.ppt
- Количество слайдов: 28

Robust Defenses for Cross-Site Request Forgery Adam Barth, Collin Jackson, John C. Mitchell Stanford University, published on CCS Presented by: HAN Jin ’ 08

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 2

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 3

What is CSRF? • Cross-site request forgery (CSRF), also known as one-click attack or session riding • In a CSRF attack, a malicious site instructs a victim's browser to send a request to an honest site, as if the request were part of the victim's interaction with the honest site. • A typical example 4
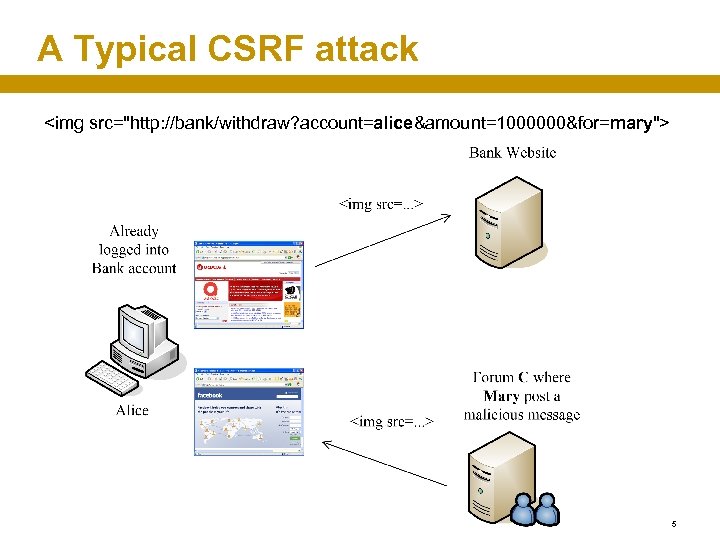
A Typical CSRF attack <img src="http: //bank/withdraw? account=alice&amount=1000000&for=mary"> 5

CSRF Harmfulness • Gmail CSRF vulnerability in 2007: – Forward all of David Airey’s email to the attacker, allowed attacker to control davidairey. com • 18 million users of e. Bay's Internet Auction Co. at Auction. co. kr in Korea lost personal information in February 2008 • An active exploit of CSRF against residential ADSL routers in Mexico in early 2008 – An e-mail with a malicious IMG tag was sent to victims. By accessing the image in the mail, the user initiated a router command to change the DNS entry of a leading Mexican bank, making any subsequent access by a user to the bank go through the attacker's server 6

CSRF Defined • In CSRF attack, the attacker disrupts the integrity of the session user a web site by injecting network requests via the user’s browser (the browser’s security policy allows web sites to send HTTP requests to any network address) This policy allows an attacker that controls content not otherwise under his or her control: – Network Connectivity – Read Browser State – Write Browser State (behind firewall) (cookie, certificate) (set cookie) 7
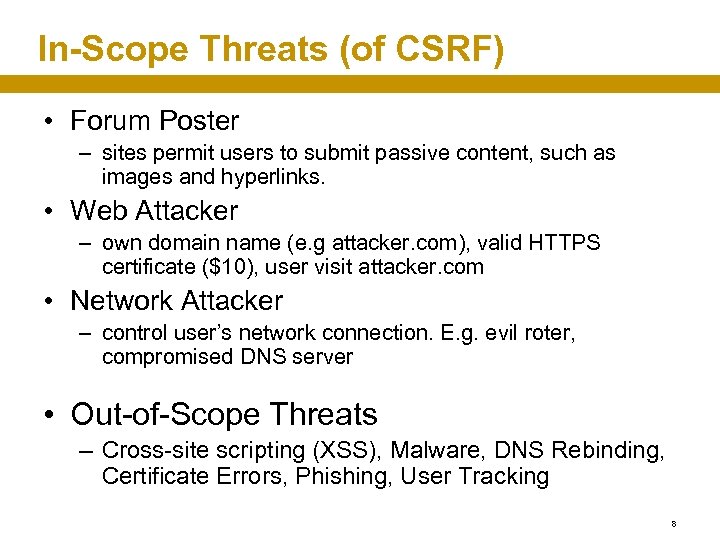
In-Scope Threats (of CSRF) • Forum Poster – sites permit users to submit passive content, such as images and hyperlinks. • Web Attacker – own domain name (e. g attacker. com), valid HTTPS certificate ($10), user visit attacker. com • Network Attacker – control user’s network connection. E. g. evil roter, compromised DNS server • Out-of-Scope Threats – Cross-site scripting (XSS), Malware, DNS Rebinding, Certificate Errors, Phishing, User Tracking 8

Outline • • • What is CSRF? What is Login CSRF? Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 9
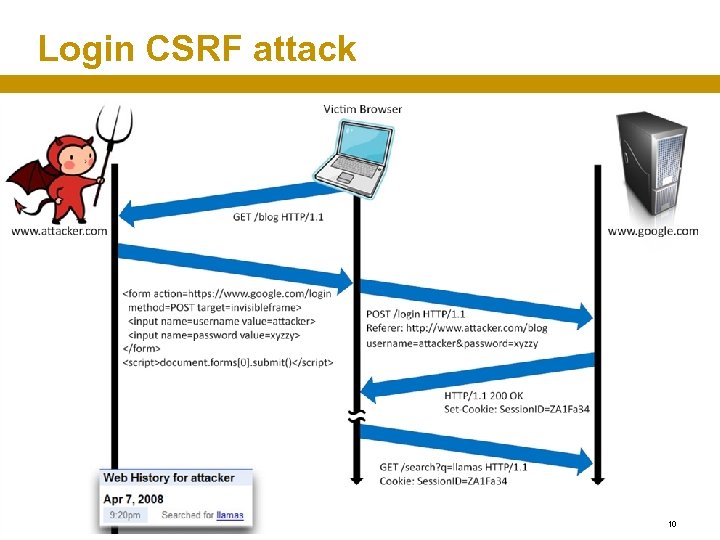
Login CSRF attack 10
Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 11

Secret Validation Token • Secret Validation Token: – send additional information in each HTTP request which can be used to determine whether the request came from an authorized source • can defend login CSRF • difficult to implement, forget to implement – before login, no session to bind the CSRF token – the site must: • first create a “pre-session” • implement token-based CSRF protection • and then transit to a real session after succesful authentication 12

Token Design • Session Identifier – user reveal the contents of web pages via email or uploading the web page token revealed • Session-Independent Nonce – fails to protect against Active Network Attackers, who can overwrite the Session-Independent Nonce • Session-dependent Nonce – site has to maintain large state table in order to validate the tokens • HMAC of Session Identifier • Case Study: No. Forge – difficulty & complexity to implement Secret Validation Token 13
Secret Validation Token • can defend login CSRF • difficult to implement 14

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 15
The Referer Header • The Referer (? ) header contains the URL of the site making the request – E. g. Referer: http: //en. wikipedia. org/query? =xxx – A site can defend itself against CSRF attacks by checking whether the request was issued by itself • Privacy – E. g. reveals contents of search queries – info about corporate intranets might leak • Strictness – Lenient Referer validation (wrong-reject, lack-accept) – Strict Refer validation (wrong-reject, lack-reject) 16

Interesting Story • Referer is a common misspelling of the word referrer. It is so common, in fact, that referrer it made it into the official specification of HTTP – the communication protocol of the World Wide Web – and has therefore become a widely used industry spelling when discussing HTTP referrers 17
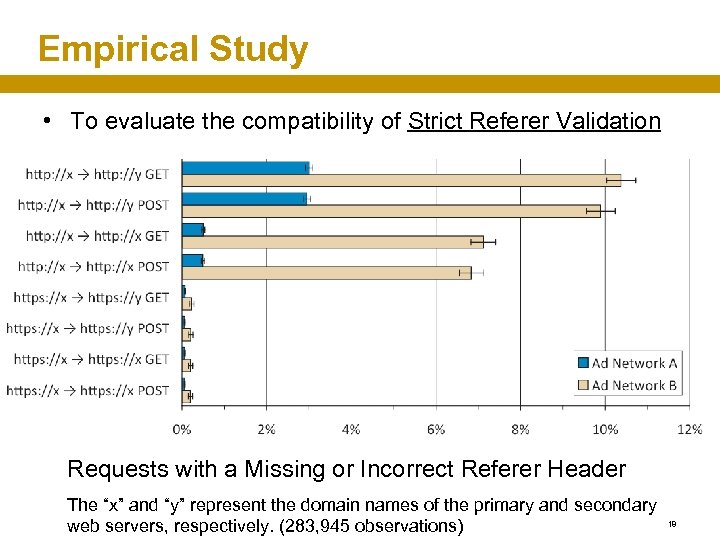
Empirical Study • To evaluate the compatibility of Strict Referer Validation Requests with a Missing or Incorrect Referer Header The “x” and “y” represent the domain names of the primary and secondary web servers, respectively. (283, 945 observations) 18
Discussion on results • Cross-domain > same-domain • HTTP > HTTPS • Referer header > document. referer Referer header is usually suppressed in the network and not in the browser (firewall, proxy, router…) 19

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 20
Custom HTTP Headers • Custom HTTP headers can prevent CSRF – because the browser prevents sites from sending custom HTTP headers to another site – but allows sites to send custom HTTP headers to themselves using XMLHttp. Request • The cookie value is not actually required, the presence of the header is sufficient • A site must – issue all state-modifying requests using XMLHttp. Request, – attach the custom header – reject all state-modifying requests without the header 21

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • • • Proposal: Origin Header Session Initialization Conclusion 22

Proposal: Origin Header • propose modifying browsers • to send a Origin header with POST requests that identifies • the origin that initiated the request • Privacy (Improves Referer header) – URL: only scheme, host, port – sent only for POST, prevent accidental leakage • Similar to four other proposals that identify the initiator of a request. Adopted by several working groups 23
Implementation Origin header Implementation: • Browser side: – 8 -line patch to Web. Kit, the open source component of Safari – 466 -line extension to Firefox • Server side: a web application firewall for CSRF in three lines of Mod. Security (a web application firewall language for Apache) 24

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 25

Session Initialization • Login CSRF is one example of a more general class of vulnerabilities in session initialization • Topics not covered in this presentation: – Two types of session initialization vul. : • Authenticated as User • Authenticated as Attacker – Two common approaches to mount attack • HTTP Request • Cookie Overwriting 26

Outline • What is CSRF? • What is Login CSRF? • Existing Defenses – Secret Validation Token – The Referer Header – Custom HTTP Headers • Proposal: Origin Header • Session Initialization • Conclusion 27
Conclusion Different defenses for different use cases: • Login CSRF strict Referer validation – login forms typically submit over HTTPS • HTTPS sites strict Referer validation – such as banking sites • Third-party Content secret token validation – spend the engineering effort to implement (HMAC token) • Long term Origin header – Privacy, both HTTP & HTTPS, no secret tokens leakage 28
ae6d0cde4c9a2d2772d4b8ecc3142b20.ppt