17f3a9b821f05f59e5df6951c1bb59d0.ppt
- Количество слайдов: 37
 Risk Assessment - Where Security Meets Compliance Caroline R. Hamilton, CEO Risk. Watch, Inc.
Risk Assessment - Where Security Meets Compliance Caroline R. Hamilton, CEO Risk. Watch, Inc.
 3 New Watchwords 1. Governance 2. Risk 3. Compliance
3 New Watchwords 1. Governance 2. Risk 3. Compliance

 TJMAXX • TJX discovered the intrusion in December and reported it to authorities in the U. S. and Canada as well as the major credit card companies and its payment processors. At the request of law enforcement, the breach was kept quiet until Wednesday, TJX said. • The breach appears broad. In Massachusetts, 28 banks have been contacted by credit card companies indicating that some of their customers have had personal information that may have been exposed, the Massachusetts Bankers Association said in a statement Thursday. That number is likely to grow as more banks report into the association, it said.
TJMAXX • TJX discovered the intrusion in December and reported it to authorities in the U. S. and Canada as well as the major credit card companies and its payment processors. At the request of law enforcement, the breach was kept quiet until Wednesday, TJX said. • The breach appears broad. In Massachusetts, 28 banks have been contacted by credit card companies indicating that some of their customers have had personal information that may have been exposed, the Massachusetts Bankers Association said in a statement Thursday. That number is likely to grow as more banks report into the association, it said.
 Governance, Risk & Compliance Sarbanes Oxley has increased the accountability of management New regulations for financial institutions require every institution complete a risk analysis by December 2006 Risk - Physical Security Increase in terrorism around the world has hit multi-nationals Cargo security now requires risk analysis Workplace violence continues to affect U. S. companies Concept of Integrated, Holistic Security Governance - Information Technology IT has become the important part of most organizations New international standards require more IT risk analysis
Governance, Risk & Compliance Sarbanes Oxley has increased the accountability of management New regulations for financial institutions require every institution complete a risk analysis by December 2006 Risk - Physical Security Increase in terrorism around the world has hit multi-nationals Cargo security now requires risk analysis Workplace violence continues to affect U. S. companies Concept of Integrated, Holistic Security Governance - Information Technology IT has become the important part of most organizations New international standards require more IT risk analysis
 New Requirements for Security Risk Assessments Based on Published Standards Governments are instituting requirements or expecting that companies will perform security risk assessments. Assessments can include identification of threats, vulnerabilities, and — based on both — an analysis of security gaps and mitigation strategies. Some of the assessment requirements also require that companies identify the most critical assets and propose plans to protect core business functions and human assets.
New Requirements for Security Risk Assessments Based on Published Standards Governments are instituting requirements or expecting that companies will perform security risk assessments. Assessments can include identification of threats, vulnerabilities, and — based on both — an analysis of security gaps and mitigation strategies. Some of the assessment requirements also require that companies identify the most critical assets and propose plans to protect core business functions and human assets.
 Compliance Regulations, Standards and Guidelines Financial & Regulatory Compliance 4 GLBA (Gramm Leach Bliley Act) 4 FFIEC Audit Framework for Information Security and for Risk Analysis 4 California SB 1386 (Identity Theft) 4 Bank Secrecy Act (BSA) 4 PCI Data Security Standard 4 Sarbanes Oxley Act HIPAA 4 Health Insurance Portability and Accountability Act of 1996 Utilities 4 NERC – CIP 002 -009 (North American Electric Reliability Council) Critical Infrastructure Protection 4 Nuclear Power Generators NRC (Nuclear Regulatory Commission) & NEI (Nuclear Energy Institute) PHYSICAL SECURITY Ø Army Field Manual Best Practices Ø FEMA 426 – Protecting Buildings Against Terrorism ØC-TPAT (Customs Trade Partnership Again Terrorism) ØFEMA 426 – School Security Guidelines ØNFPA ØMaritime & Port Security – ISPS, MTSA Information Security/ISO 17799 4 NIST 800 -26, NIST 800 -53 4 ISO/IEC 1779: 2005 4 ISO/IEC 27001 4 Office of Management and Budget (OMB) A-123, A-124, A-127, and A 130 4 COBIT 4
Compliance Regulations, Standards and Guidelines Financial & Regulatory Compliance 4 GLBA (Gramm Leach Bliley Act) 4 FFIEC Audit Framework for Information Security and for Risk Analysis 4 California SB 1386 (Identity Theft) 4 Bank Secrecy Act (BSA) 4 PCI Data Security Standard 4 Sarbanes Oxley Act HIPAA 4 Health Insurance Portability and Accountability Act of 1996 Utilities 4 NERC – CIP 002 -009 (North American Electric Reliability Council) Critical Infrastructure Protection 4 Nuclear Power Generators NRC (Nuclear Regulatory Commission) & NEI (Nuclear Energy Institute) PHYSICAL SECURITY Ø Army Field Manual Best Practices Ø FEMA 426 – Protecting Buildings Against Terrorism ØC-TPAT (Customs Trade Partnership Again Terrorism) ØFEMA 426 – School Security Guidelines ØNFPA ØMaritime & Port Security – ISPS, MTSA Information Security/ISO 17799 4 NIST 800 -26, NIST 800 -53 4 ISO/IEC 1779: 2005 4 ISO/IEC 27001 4 Office of Management and Budget (OMB) A-123, A-124, A-127, and A 130 4 COBIT 4
 Mapping to Audit • Must map to audit Guidelines – ISACA (ASIS partner organization) • Every Vulnerability or Risk Assessment Ends Up with Corporate Management – CFO or IG • Executives are being held PERSONALLY ACCOUNTABLE and need the assessments to demonstrate Due Care
Mapping to Audit • Must map to audit Guidelines – ISACA (ASIS partner organization) • Every Vulnerability or Risk Assessment Ends Up with Corporate Management – CFO or IG • Executives are being held PERSONALLY ACCOUNTABLE and need the assessments to demonstrate Due Care
 APPROACH TO GOOD SECURITY “The approach to good security is fundamentally similar regardless of the assets being protected. As GAO has previously reported for homeland security and information systems security, applying risk management principles can provide a sound foundation for effective security whether the assets are information, operations, people, or facilities. These principles, which have been followed by members of the intelligence and defense community for many years, can be reduced to five basic steps: GAO-02 -687 T National Security
APPROACH TO GOOD SECURITY “The approach to good security is fundamentally similar regardless of the assets being protected. As GAO has previously reported for homeland security and information systems security, applying risk management principles can provide a sound foundation for effective security whether the assets are information, operations, people, or facilities. These principles, which have been followed by members of the intelligence and defense community for many years, can be reduced to five basic steps: GAO-02 -687 T National Security
 ELEMENTS OF RISK ASSESSMENT VS. COMPLIANCE ASSESSMENT ASSETS THREATS VULNERABILITIES LOSSES SAFEGUARDS
ELEMENTS OF RISK ASSESSMENT VS. COMPLIANCE ASSESSMENT ASSETS THREATS VULNERABILITIES LOSSES SAFEGUARDS
 What Is Risk Assessment compared to a Site Survey ? § A process used to determine what controls are needed to protect critical or sensitive assets adequately & costeffectively § The process examines five variable functions: 1. Specific Assets to be protected (value) 2. Potential Threats to the various assets 3. Vulnerabilities that would allow the threats to materialize 4. Kinds of Losses that the threats could cause 5. Safeguards that would reduce the loss or eliminate threats
What Is Risk Assessment compared to a Site Survey ? § A process used to determine what controls are needed to protect critical or sensitive assets adequately & costeffectively § The process examines five variable functions: 1. Specific Assets to be protected (value) 2. Potential Threats to the various assets 3. Vulnerabilities that would allow the threats to materialize 4. Kinds of Losses that the threats could cause 5. Safeguards that would reduce the loss or eliminate threats
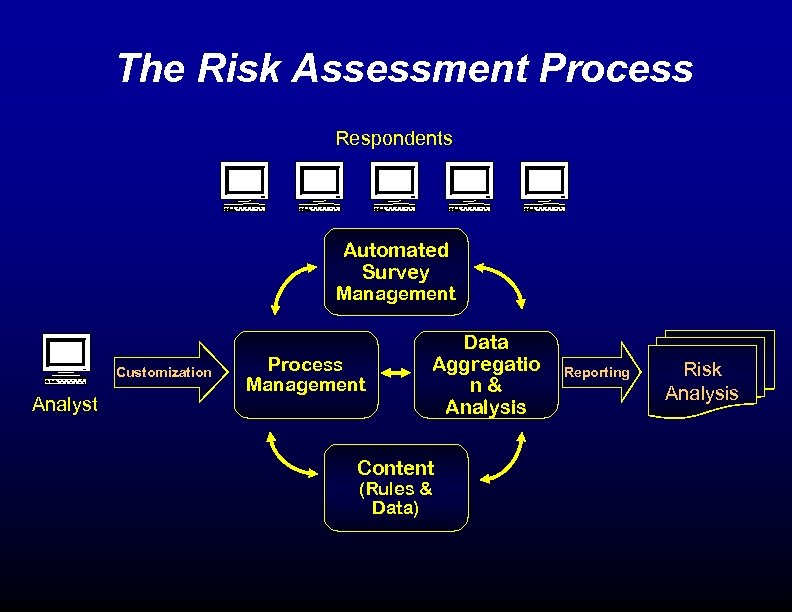 The Risk Assessment Process Respondents Automated Survey Management Customization Analyst Process Management Data Aggregatio n& Analysis Content (Rules & Data) Reporting Risk Analysis
The Risk Assessment Process Respondents Automated Survey Management Customization Analyst Process Management Data Aggregatio n& Analysis Content (Rules & Data) Reporting Risk Analysis
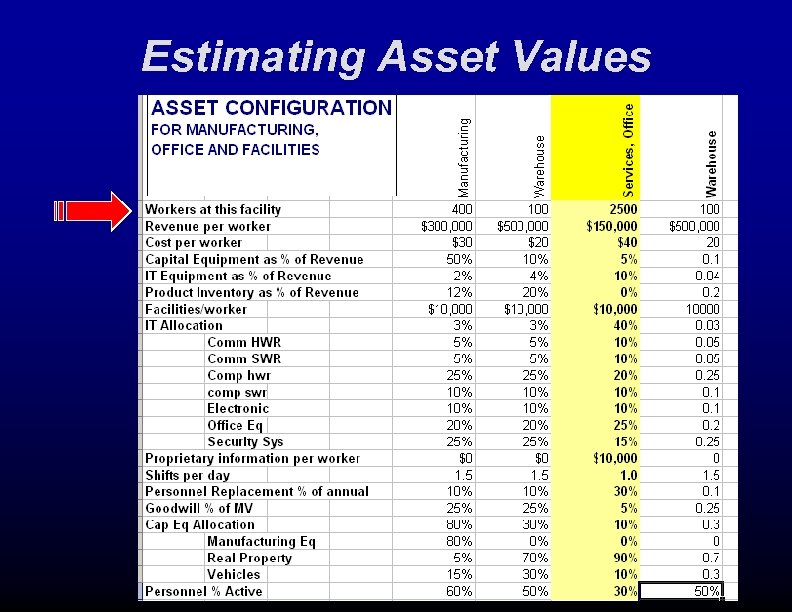 Estimating Asset Values
Estimating Asset Values
 FINDING THREAT DATA OR INPUT YOUR OWN ORGANIZATIONAL DATA SUCH AS INCIDENT REPORT DATA • Quantified threat data is hard to find. • Categories of Threats: Natural Disasters, Criminal Activity Terrorism, Theft, Systems Failures • Collect data from Web Sources, government data, weather data, crime casts, global info services, access control systems, incident logs. • Use data from internally collected sources
FINDING THREAT DATA OR INPUT YOUR OWN ORGANIZATIONAL DATA SUCH AS INCIDENT REPORT DATA • Quantified threat data is hard to find. • Categories of Threats: Natural Disasters, Criminal Activity Terrorism, Theft, Systems Failures • Collect data from Web Sources, government data, weather data, crime casts, global info services, access control systems, incident logs. • Use data from internally collected sources
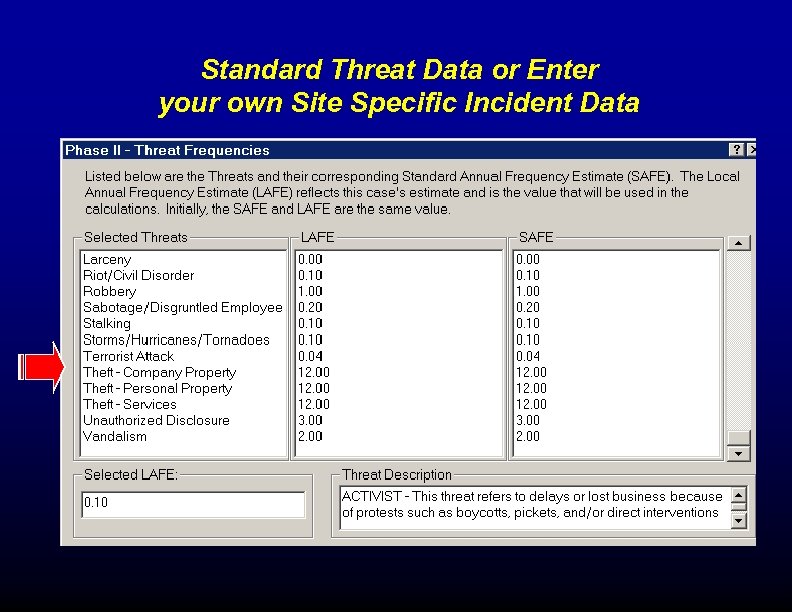 Standard Threat Data or Enter your own Site Specific Incident Data
Standard Threat Data or Enter your own Site Specific Incident Data
 Discovering Vulnerabilities • Vulnerabilities specific by organization • Can be completed only by the analyst • Or include key individuals • Web-Based surveys increase accuracy and speed of survey collection & aggregation
Discovering Vulnerabilities • Vulnerabilities specific by organization • Can be completed only by the analyst • Or include key individuals • Web-Based surveys increase accuracy and speed of survey collection & aggregation
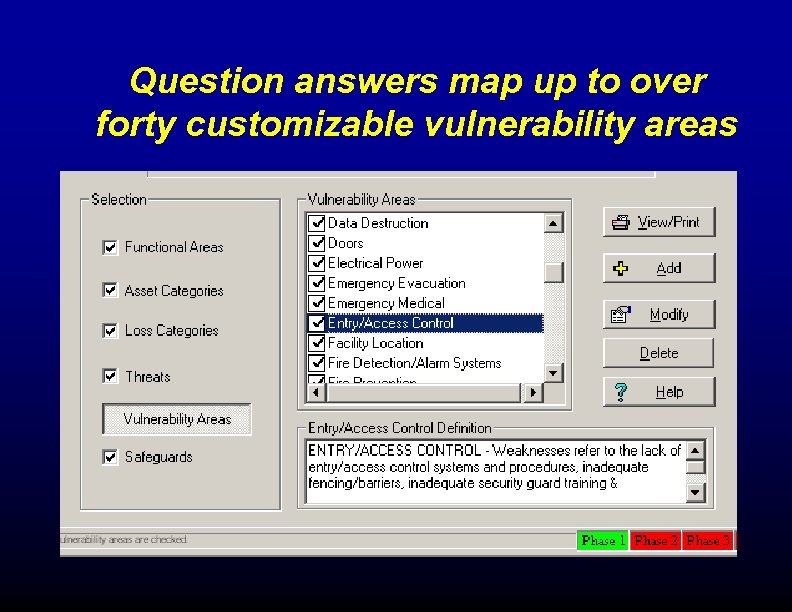 Question answers map up to over forty customizable vulnerability areas
Question answers map up to over forty customizable vulnerability areas
 Analysts Can Customize Questions or Add New Questions • Questions Follow Audit Format • Control Standard matches Question • Analyst Sets Threshold for Compliance • Questions Validate Compliance with Standards • Analyst can Add, Delete or Modify Questions
Analysts Can Customize Questions or Add New Questions • Questions Follow Audit Format • Control Standard matches Question • Analyst Sets Threshold for Compliance • Questions Validate Compliance with Standards • Analyst can Add, Delete or Modify Questions
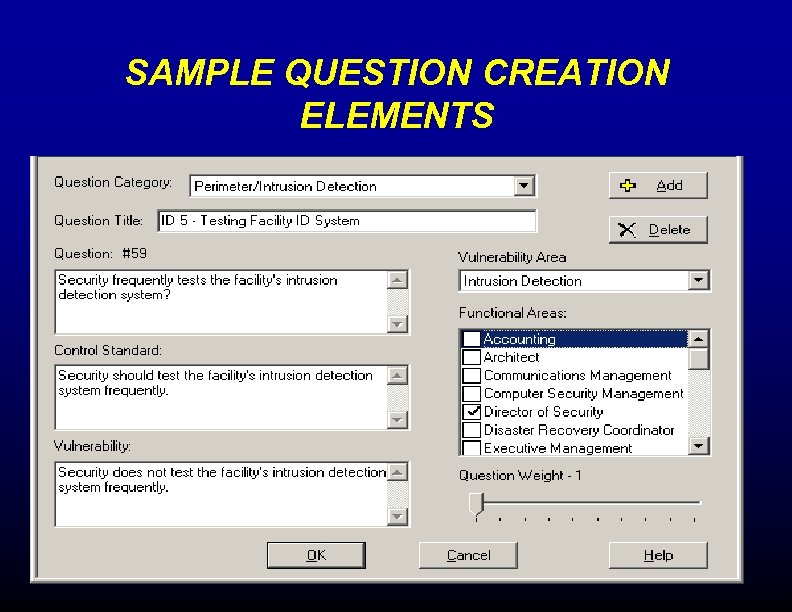 SAMPLE QUESTION CREATION ELEMENTS
SAMPLE QUESTION CREATION ELEMENTS
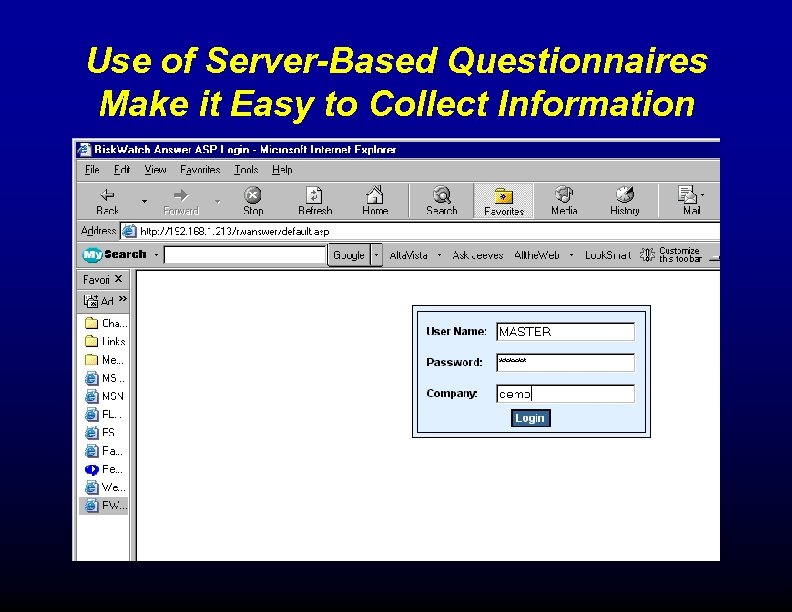 Use of Server-Based Questionnaires Make it Easy to Collect Information
Use of Server-Based Questionnaires Make it Easy to Collect Information
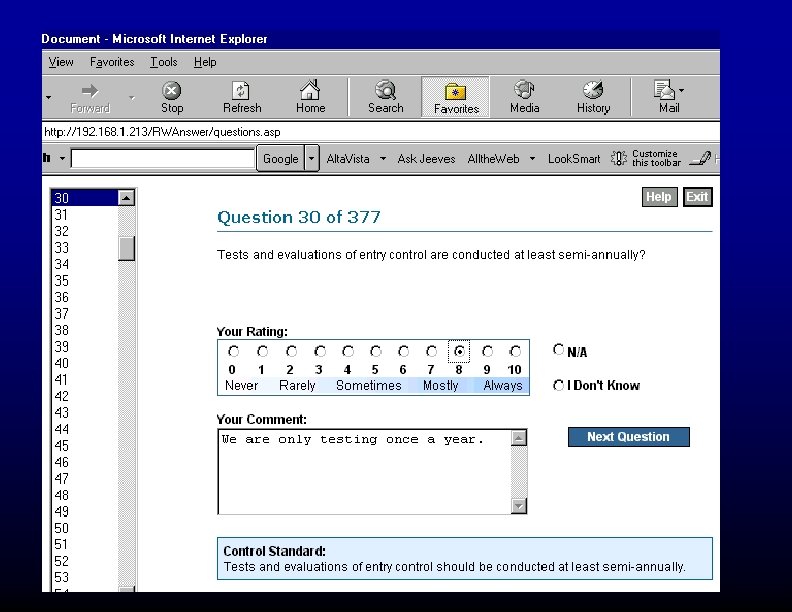
 Including all Relevant Safeguards and Controls • Alarm Systems • Background Checks • Barriers • Biometric Controls • Bomb Threat Procedures • Bomb Detection & Identification • CCTV Cameras • Disaster Recovery Planning • Emergency Response Planning • Entry Controls • Fire Controls • Guard Services • Incident Reporting • Incident Response • Intrusion Detection • Lock & Key Controls • Monitoring Systems • Risk Assessment • Security Planning • Security Policies • Security Staff • Technical Surveillance • Training Programs • Visitor Controls
Including all Relevant Safeguards and Controls • Alarm Systems • Background Checks • Barriers • Biometric Controls • Bomb Threat Procedures • Bomb Detection & Identification • CCTV Cameras • Disaster Recovery Planning • Emergency Response Planning • Entry Controls • Fire Controls • Guard Services • Incident Reporting • Incident Response • Intrusion Detection • Lock & Key Controls • Monitoring Systems • Risk Assessment • Security Planning • Security Policies • Security Staff • Technical Surveillance • Training Programs • Visitor Controls
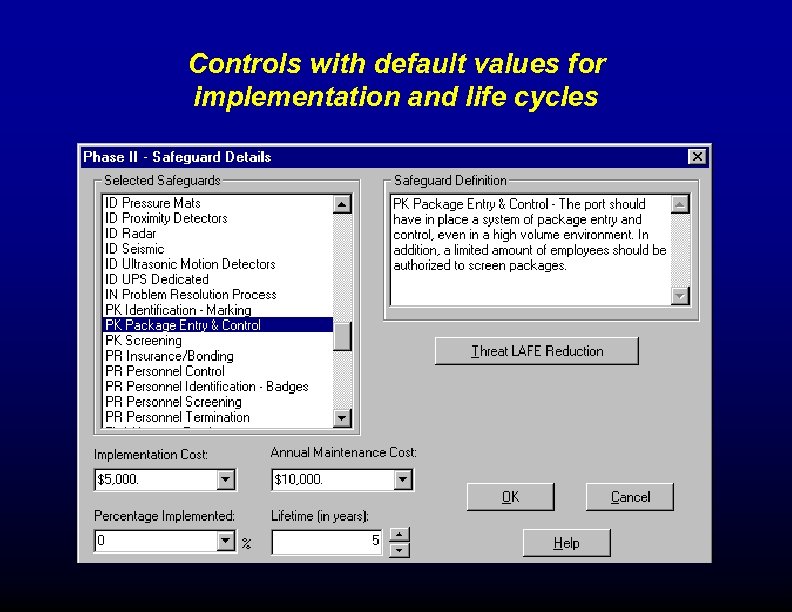 Controls with default values for implementation and life cycles
Controls with default values for implementation and life cycles
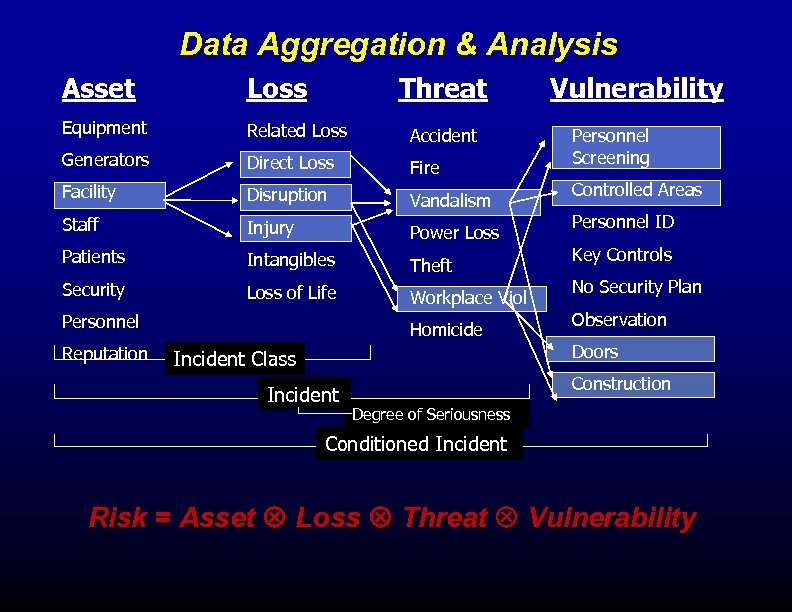 Data Aggregation & Analysis Asset Loss Threat Equipment Related Loss Accident Generators Direct Loss Fire Facility Disruption Vandalism Staff Injury Power Loss Patients Intangibles Theft Security Loss of Life Workplace Viol Personnel Reputation Homicide Incident Class Incident Vulnerability Personnel Screening Controlled Areas Personnel ID Key Controls No Security Plan Observation Doors Construction Degree of Seriousness Conditioned Incident Risk = Asset Loss Threat Vulnerability
Data Aggregation & Analysis Asset Loss Threat Equipment Related Loss Accident Generators Direct Loss Fire Facility Disruption Vandalism Staff Injury Power Loss Patients Intangibles Theft Security Loss of Life Workplace Viol Personnel Reputation Homicide Incident Class Incident Vulnerability Personnel Screening Controlled Areas Personnel ID Key Controls No Security Plan Observation Doors Construction Degree of Seriousness Conditioned Incident Risk = Asset Loss Threat Vulnerability
 WRITING REPORTS • Data which can be benchmarked • Making sure you include audit trails • Use of recognized statistical probability models • Includes both current and new directives • Creating management level reports
WRITING REPORTS • Data which can be benchmarked • Making sure you include audit trails • Use of recognized statistical probability models • Includes both current and new directives • Creating management level reports
 MITIGATION STRATEGIES 1. Accept Risk 2. Transfer Risk 2. Mitigate Risk 3. Better Risk Reactions 5. Dealing with Residual Risk
MITIGATION STRATEGIES 1. Accept Risk 2. Transfer Risk 2. Mitigate Risk 3. Better Risk Reactions 5. Dealing with Residual Risk
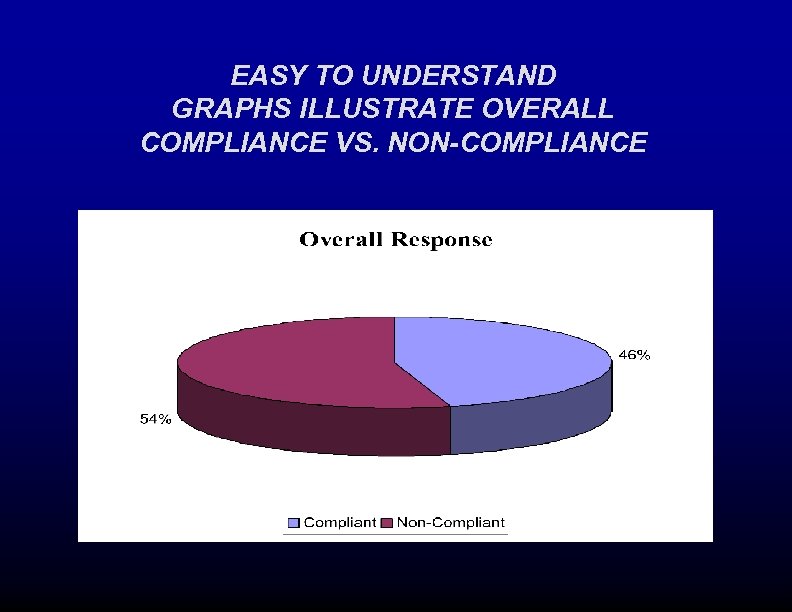 EASY TO UNDERSTAND GRAPHS ILLUSTRATE OVERALL COMPLIANCE VS. NON-COMPLIANCE
EASY TO UNDERSTAND GRAPHS ILLUSTRATE OVERALL COMPLIANCE VS. NON-COMPLIANCE
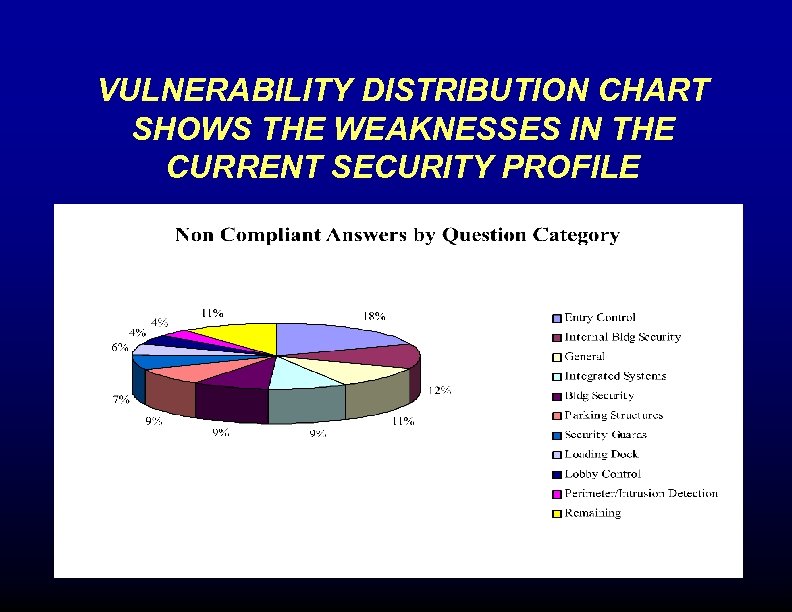 VULNERABILITY DISTRIBUTION CHART SHOWS THE WEAKNESSES IN THE CURRENT SECURITY PROFILE
VULNERABILITY DISTRIBUTION CHART SHOWS THE WEAKNESSES IN THE CURRENT SECURITY PROFILE
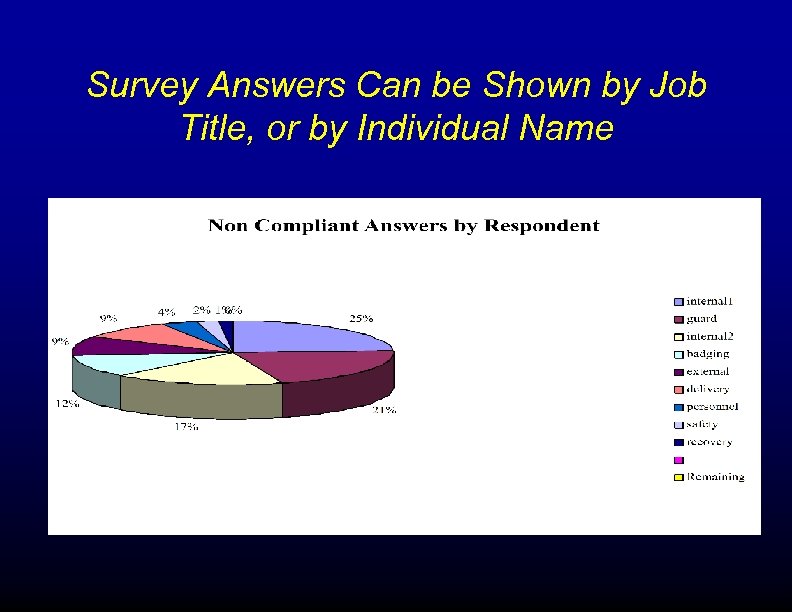 Survey Answers Can be Shown by Job Title, or by Individual Name
Survey Answers Can be Shown by Job Title, or by Individual Name
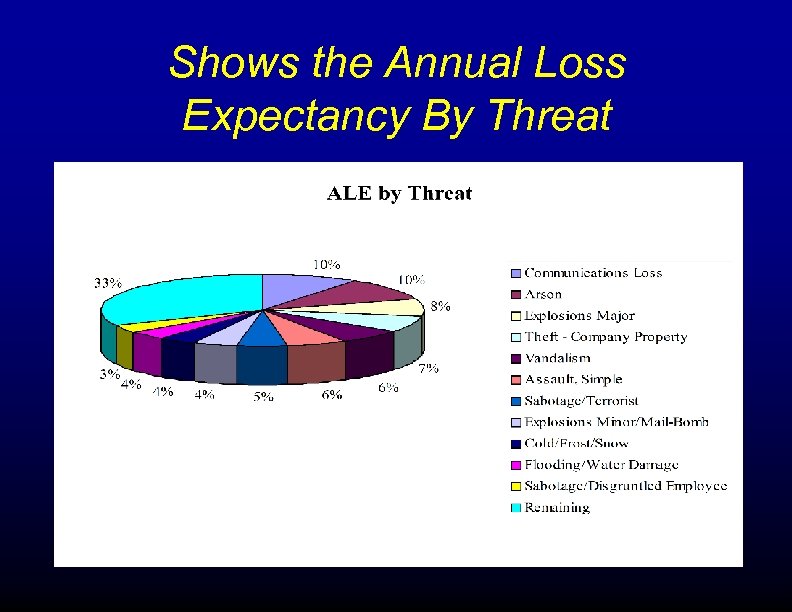 Shows the Annual Loss Expectancy By Threat
Shows the Annual Loss Expectancy By Threat
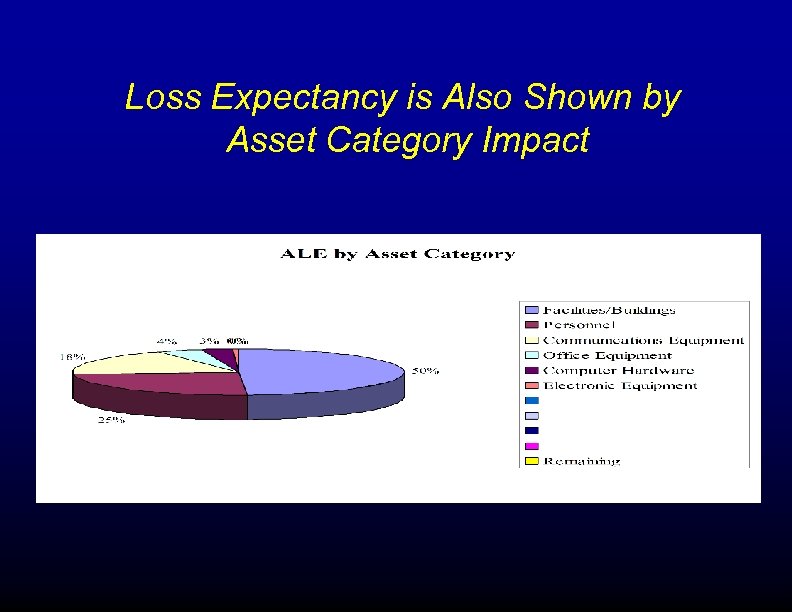 Loss Expectancy is Also Shown by Asset Category Impact
Loss Expectancy is Also Shown by Asset Category Impact
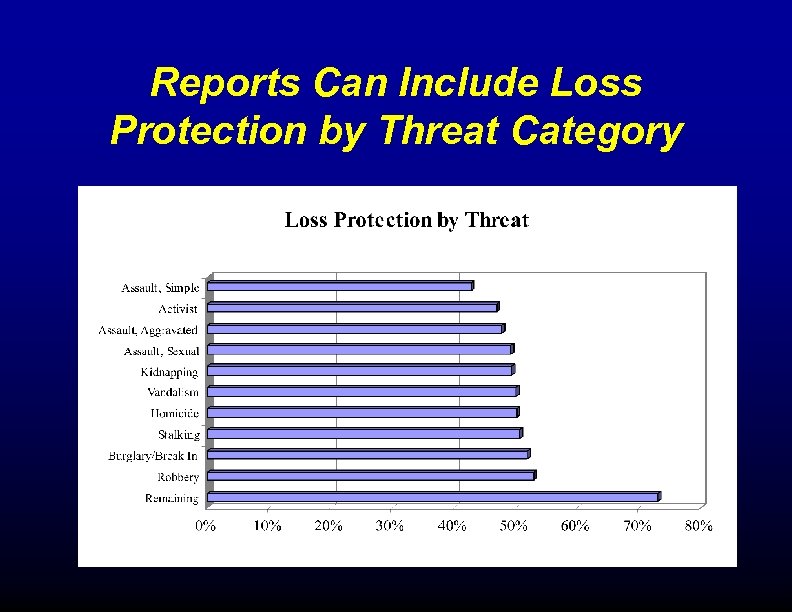 Reports Can Include Loss Protection by Threat Category
Reports Can Include Loss Protection by Threat Category
 How to Calculate Return on Investment to Support Proper Budgeting for Security. In this example, finishing and updating the Disaster Recovery Plan had a 2000 -1 ROI – that means for every dollar spent on updating the plan – the organization saves $2, 000 1. Finish Disaster Recovery Plan 2000: 1 2. Finish the Security Plan 1200: 1 3. Complete Security Training 943: 1
How to Calculate Return on Investment to Support Proper Budgeting for Security. In this example, finishing and updating the Disaster Recovery Plan had a 2000 -1 ROI – that means for every dollar spent on updating the plan – the organization saves $2, 000 1. Finish Disaster Recovery Plan 2000: 1 2. Finish the Security Plan 1200: 1 3. Complete Security Training 943: 1
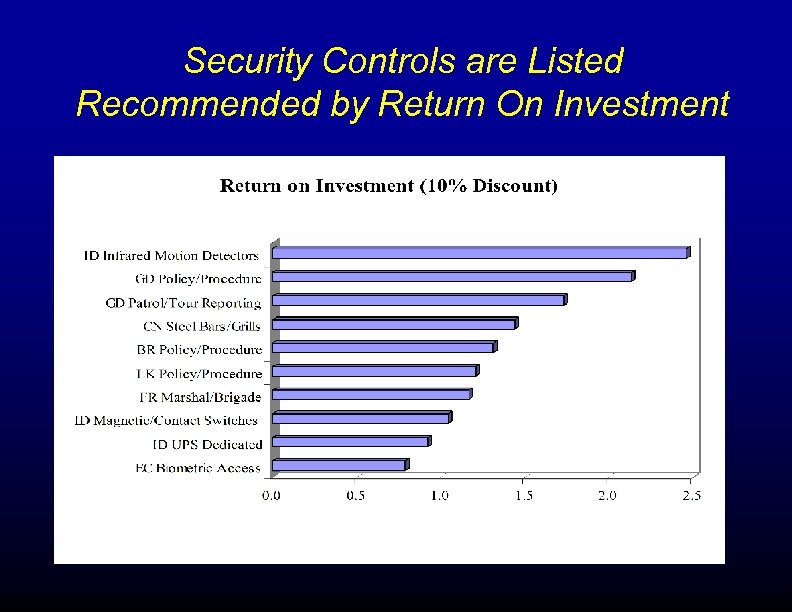 Security Controls are Listed Recommended by Return On Investment
Security Controls are Listed Recommended by Return On Investment
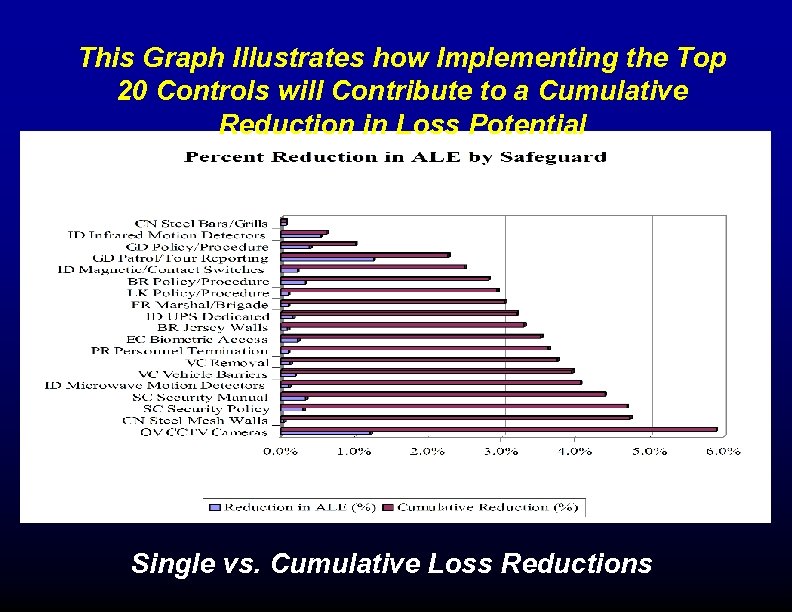 This Graph Illustrates how Implementing the Top 20 Controls will Contribute to a Cumulative Reduction in Loss Potential Single vs. Cumulative Loss Reductions
This Graph Illustrates how Implementing the Top 20 Controls will Contribute to a Cumulative Reduction in Loss Potential Single vs. Cumulative Loss Reductions
 The Bottom Line • Security Risk Management Requirements will Continue to Increase and need to be standardized. • Measuring and Managing Security by Return on Investment gives you the ‘best bang for the buck’ • Conducting Risk Assessments are the best way to meet security requirements, quantify areas of weakness, justify security controls, and manage and validate the security budget.
The Bottom Line • Security Risk Management Requirements will Continue to Increase and need to be standardized. • Measuring and Managing Security by Return on Investment gives you the ‘best bang for the buck’ • Conducting Risk Assessments are the best way to meet security requirements, quantify areas of weakness, justify security controls, and manage and validate the security budget.
 Caroline Hamilton 410 -224 -4773, x 105 chamilton@riskwatch. com
Caroline Hamilton 410 -224 -4773, x 105 chamilton@riskwatch. com


