723c7fd4fbd258eb09986ae4a57a1de6.ppt
- Количество слайдов: 47

RFID/USN Security Issues 2009/7/14 신승목 Cryptography & Information Security Lab

Contents 1 Ubiquitous world 2 RFID 개론 및 보안 이슈 3 USN 개론 및 보안 이슈 4 Quiz 2 / 48 KAIST-ICC
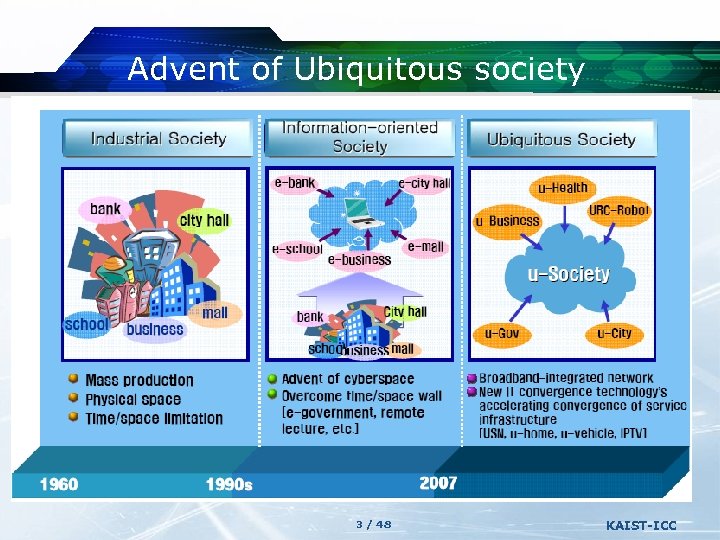
Advent of Ubiquitous society 3 / 48 KAIST-ICC
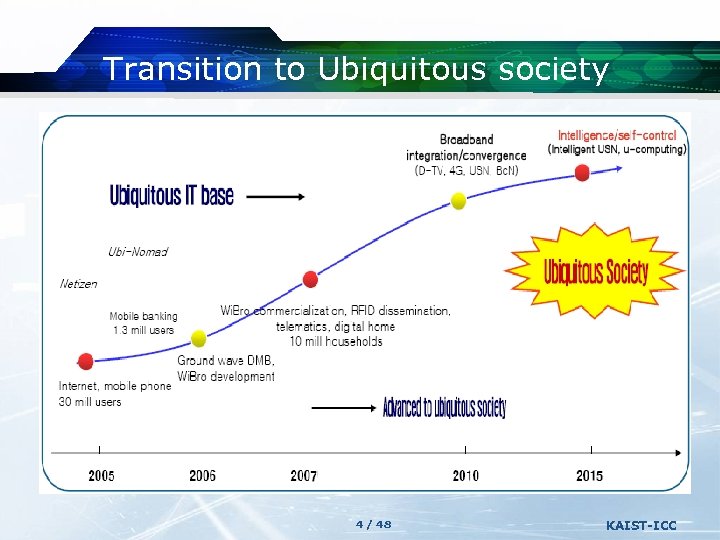
Transition to Ubiquitous society 4 / 48 KAIST-ICC
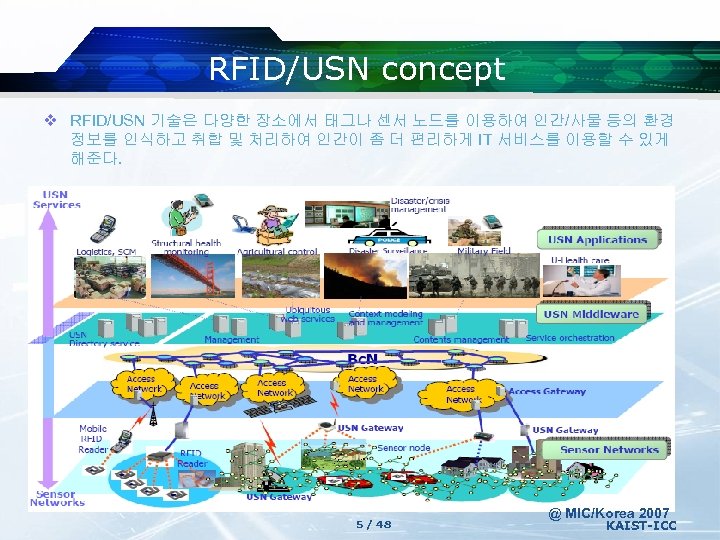
RFID/USN concept v RFID/USN 기술은 다양한 장소에서 태그나 센서 노드를 이용하여 인간/사물 등의 환경 정보를 인식하고 취합 및 처리하여 인간이 좀 더 편리하게 IT 서비스를 이용할 수 있게 해준다. 5 / 48 @ MIC/Korea 2007 KAIST-ICC

Introduction to RFID 6 KAIST-ICC
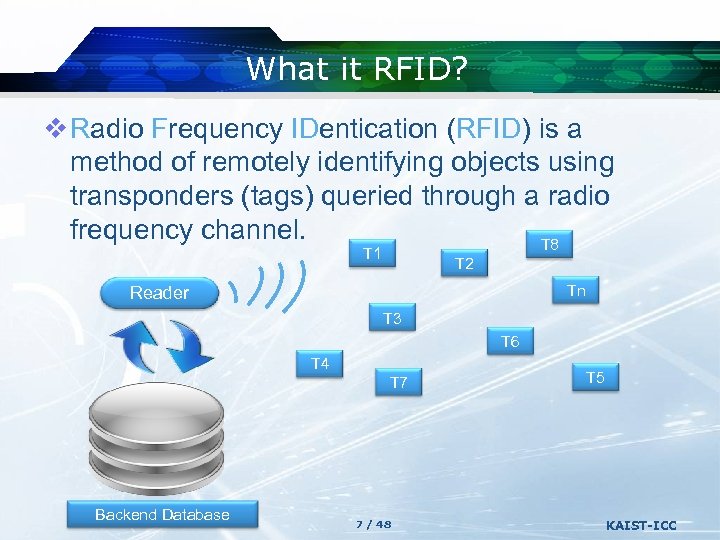
What it RFID? v Radio Frequency IDentication (RFID) is a method of remotely identifying objects using transponders (tags) queried through a radio frequency channel. T 8 T 1 T 2 Tn Reader T 3 T 6 T 4 T 7 Backend Database 7 / 48 T 5 KAIST-ICC
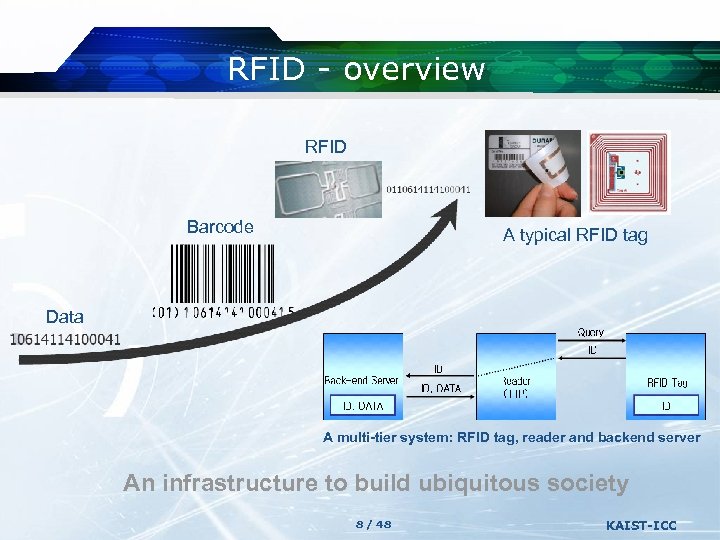
RFID - overview RFID Barcode A typical RFID tag Data A multi-tier system: RFID tag, reader and backend server An infrastructure to build ubiquitous society 8 / 48 KAIST-ICC

RFID readers (1/2) v Fixed-Type Readers v Mobile Readers 9 / 48 KAIST-ICC
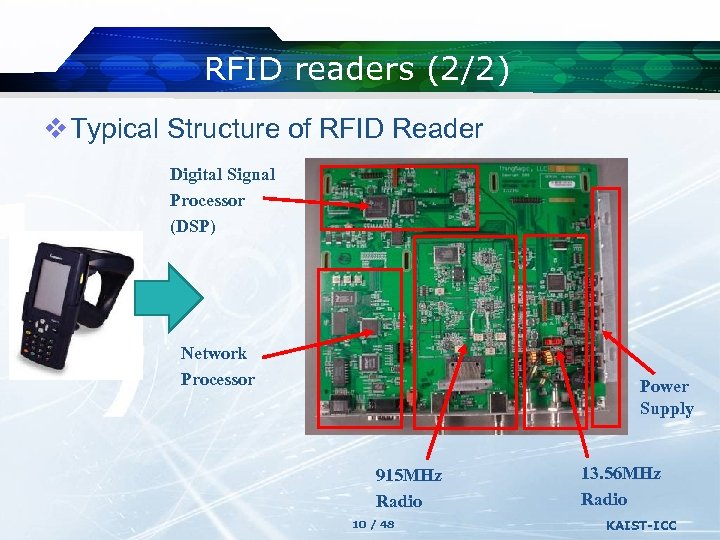
RFID readers (2/2) v Typical Structure of RFID Reader Digital Signal Processor (DSP) Network Processor Power Supply 915 MHz Radio 10 / 48 13. 56 MHz Radio KAIST-ICC
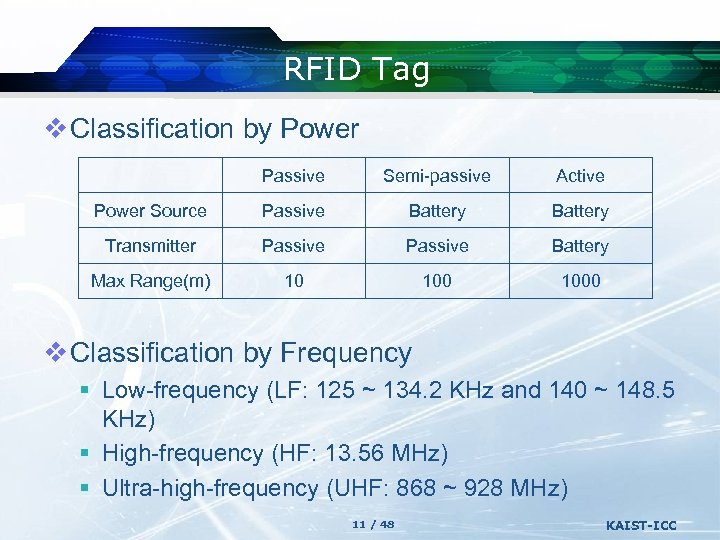
RFID Tag v Classification by Power Passive Semi-passive Active Power Source Passive Battery Transmitter Passive Battery Max Range(m) 10 1000 v Classification by Frequency § Low-frequency (LF: 125 ~ 134. 2 KHz and 140 ~ 148. 5 KHz) § High-frequency (HF: 13. 56 MHz) § Ultra-high-frequency (UHF: 868 ~ 928 MHz) 11 / 48 KAIST-ICC

Electronic Product Code (EPC) Version EPC Manager (Manufacturer) Object Class (Product) Serial Number 8 bits 24 bits 36 bits v 296 = 79, 228, 162, 514, 264, 337, 593, 543, 950, 336 v 96 bits can uniquely label all products for the next 1, 000 years. 12 / 48 KAIST-ICC
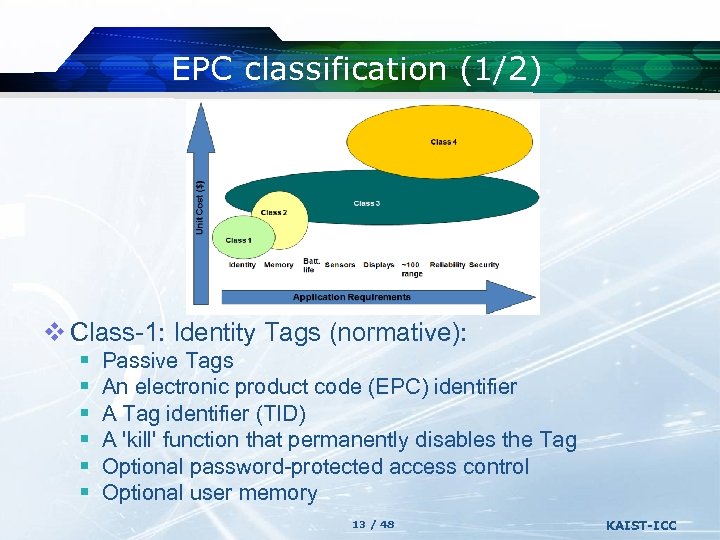
EPC classification (1/2) v Class-1: Identity Tags (normative): § § § Passive Tags An electronic product code (EPC) identifier A Tag identifier (TID) A 'kill' function that permanently disables the Tag Optional password-protected access control Optional user memory 13 / 48 KAIST-ICC

EPC classification (2/2) v Higher-class Tags (informative) § Class-2: Higher-Functionality Passive Tags • An extended TID (Tag ID) • Extended user memory • Authenticated access control § Class-3: Semi-Passive Tags • An integral power source • Integrated sensing circuitry § Class-4: Active Tags (i. e. , sensor node) • Tag-to-Tag communications • Active communications • ad-hoc networking capabilities 14 / 48 KAIST-ICC

RFID system applications (1/3) v Libraries v Supply chain management 15 / 48 KAIST-ICC

RFID system applications (2/3) v Airline Baggage @ JFK Airport 16 / 48 KAIST-ICC

RFID system applications (3/3) v Passports v Transport payments v Anti-counterfeiting § Whitepapers in 2006 (by Auto-ID Labs. ) v Access control v Animal tracking, etc. 17 / 48 KAIST-ICC

RFID security issues 18 / 48 KAIST-ICC
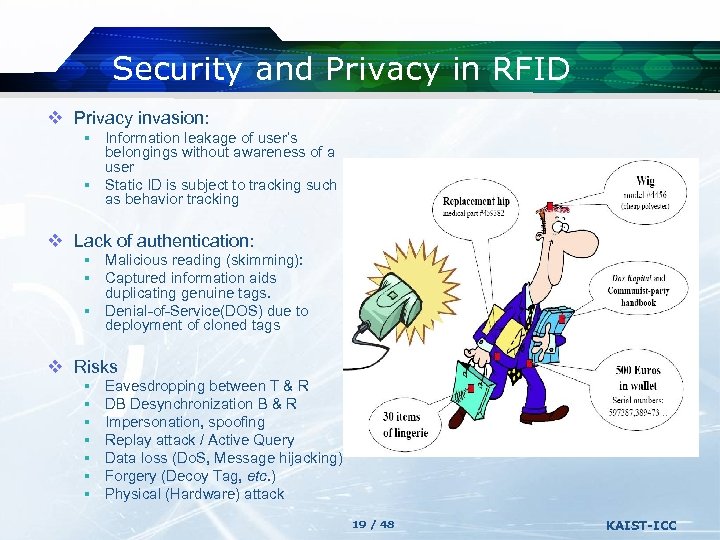
Security and Privacy in RFID v Privacy invasion: § Information leakage of user’s belongings without awareness of a user § Static ID is subject to tracking such as behavior tracking v Lack of authentication: § Malicious reading (skimming): § Captured information aids duplicating genuine tags. § Denial-of-Service(DOS) due to deployment of cloned tags v Risks § § § § Eavesdropping between T & R DB Desynchronization B & R Impersonation, spoofing Replay attack / Active Query Data loss (Do. S, Message hijacking) Forgery (Decoy Tag, etc. ) Physical (Hardware) attack 19 / 48 KAIST-ICC

Security Requirements in RFID Systems v. Confidentiality v. Indistinguishability v. Anti-cloning v. Availability v. Forward security 20 / 48 KAIST-ICC
Weak Implementations (1/2) v In January 2005, researchers at John Hopkins University and the RSA Lab announced a successful attack on the Texas Instruments DST RFID by guessing its 40 -bit key using bruteforce. v The DST RFID was used in Ford immobilizers and Exxon. Mobil Speed. Pass. 21 / 48 KAIST-ICC

Weak Implementations (2/2) - Video v. Cracking TI (Texas Instrument) DST (Digital Signature Transponder) chip TI DST Sniffing a DST tag in a victim's pocket Cracking the key in a DST tag Buying gas using the DST simulator 22 / 48 KAIST-ICC

Security Challenge v The narrow cost requirements of low-cost RFID systems make low-cost tags extremely resourcescarce environments, far below the requirements for any public-key and symmetric-key cryptographic systems. v EPC tags: $0. 05, 250 – 1000 gates v AES: 20, 000 – 30, 000 gates 23 / 48 KAIST-ICC

Introduction to USN 24 KAIST-ICC
Sensor & Sensor Network v What is a Sensor? § A device that produces a measurable response to a change in a physical or chemical condition, e. g. temperature, ground composition, etc. v Sensor Networks § A large number of low-cost, low-power, multifunctional, and small sensor nodes § They benefit from advances in 3 technologies • digital circuitry • wireless communication • silicon micro-machining 25 / 48 KAIST-ICC

Wireless Sensor Networks (WSN) v New technologies have reduced the cost, size, and power of micro-sensors and wireless interfaces. Sensing Networking Circulatory Net Computation Structural 26 / 48 Environmental Monitoring KAIST-ICC
WSN - Properties v Compose of a large number of sensor nodes v Densely deployed inside(near) the phenomenon v Low energy consumption § Relocation or recharge is impossible v Self-organizing network (infrastructureless) § Random deployment : manual configuration is unfeasible 27 / 48 KAIST-ICC
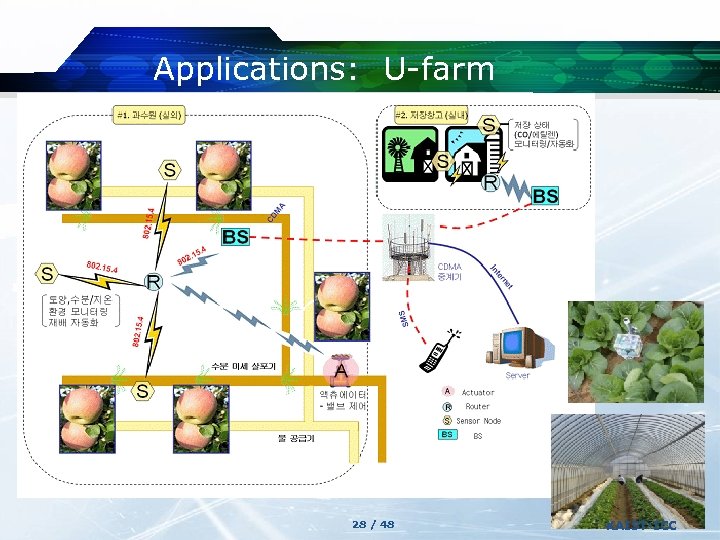
Applications: U-farm 28 / 48 KAIST-ICC
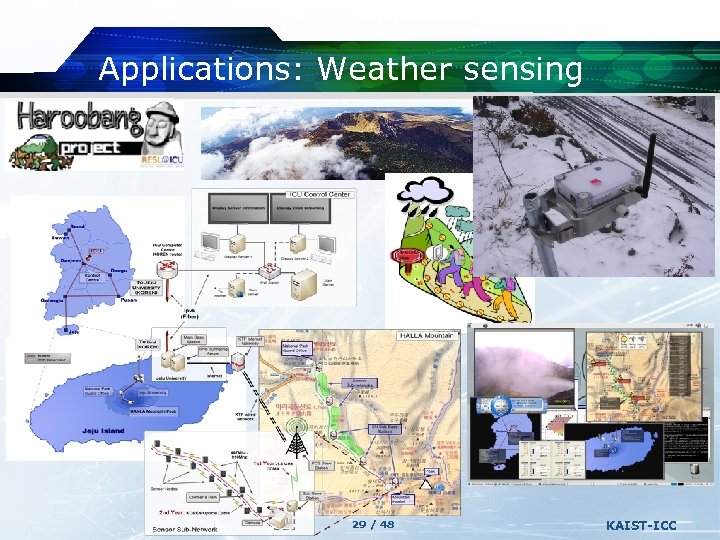
Applications: Weather sensing Fire Detection 29 / 48 KAIST-ICC

Applications: Fire Detection Cultural Property Asset Management using USN Bush Fire Detection 30 / 48 KAIST-ICC

Applications: Battle Field 31 / 48 KAIST-ICC
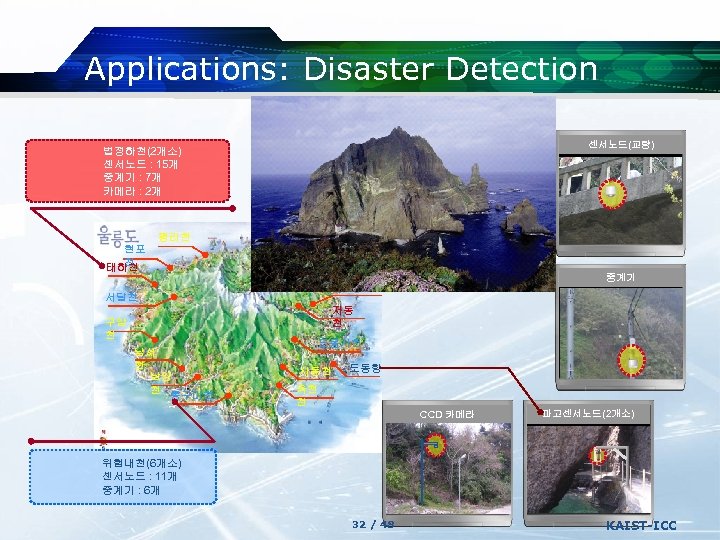
Applications: Disaster Detection 법정하천(2개소) 센서노드 : 15개 중계기 : 7개 카메라 : 2개 평리천 소하천(7개소) 센서노드 : 4 개 중계기 : 2개 카메라 : 2개 센서노드(교량) 죽암 천 현포 천 태하천 내수전천 중계기 저동 2리천 서달천 저동 천 구암 천 남서 천 남양 천 통구미천 도동사천 사동천 도동항 옥천 천 CCD 카메라 파고센서노드(2개소) 위험내천(6개소) 센서노드 : 11개 중계기 : 6개 32 / 48 KAIST-ICC
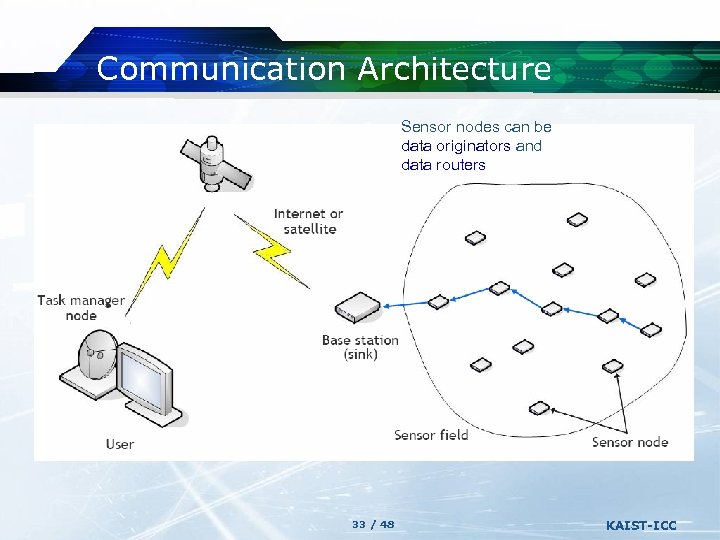
Communication Architecture Sensor nodes can be data originators and data routers 33 / 48 KAIST-ICC
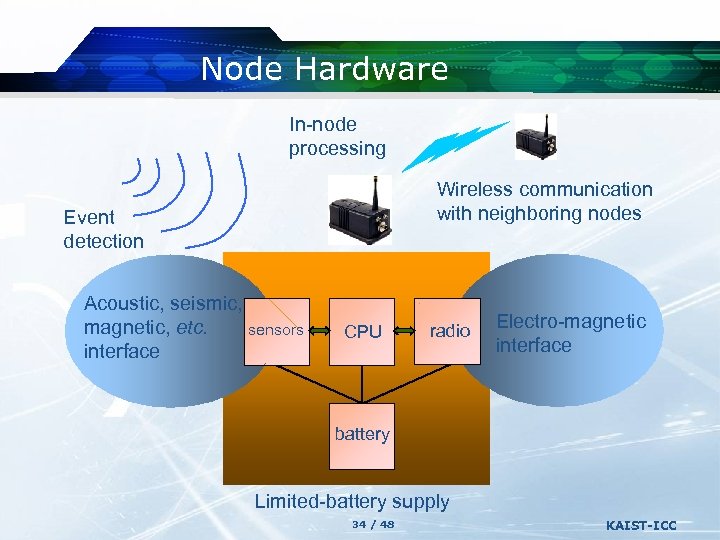
Node Hardware In-node processing Wireless communication with neighboring nodes Event detection Acoustic, seismic, magnetic, etc. sensors interface CPU radio Electro-magnetic interface battery Limited-battery supply 34 / 48 KAIST-ICC
Examples of Sensor Nodes 35 / 48 KAIST-ICC

USN security issues 36 / 48 KAIST-ICC
Why should we consider the Security? (1/2) v. Providing confidentiality, integrity, and availability of the communications and computations v. Sensor networks are vulnerable to security attacks due to the broadcast nature of transmission v. Sensor nodes can be physically captured or destroyed 37 / 48 KAIST-ICC

Why should we consider the Security? (2/2) v. Since the system is able control house infrastructure § e. g. , gas, water control etc § If the adversary attacks house infra system • House infrastructure can be a serious harm to human • e. g. , Open gas valve, overheat the micro-wave 38 / 48 KAIST-ICC
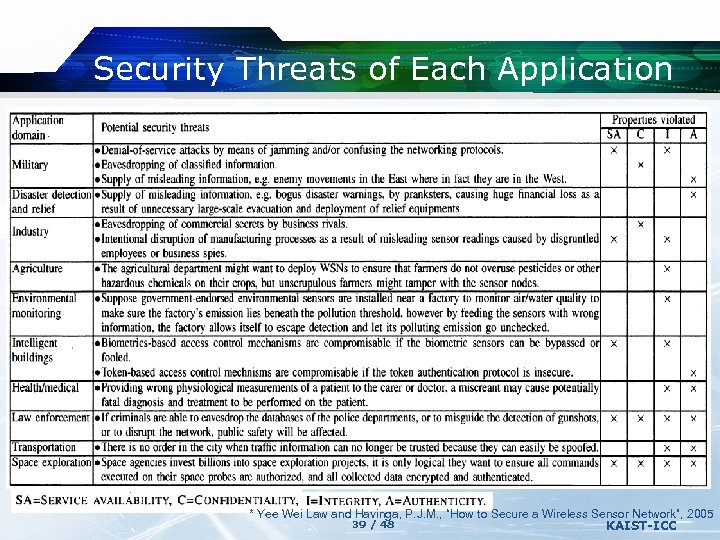
Security Threats of Each Application * Yee Wei Law and Havinga, P. J. M. , “How to Secure a Wireless Sensor Network”, 2005 39 / 48 KAIST-ICC
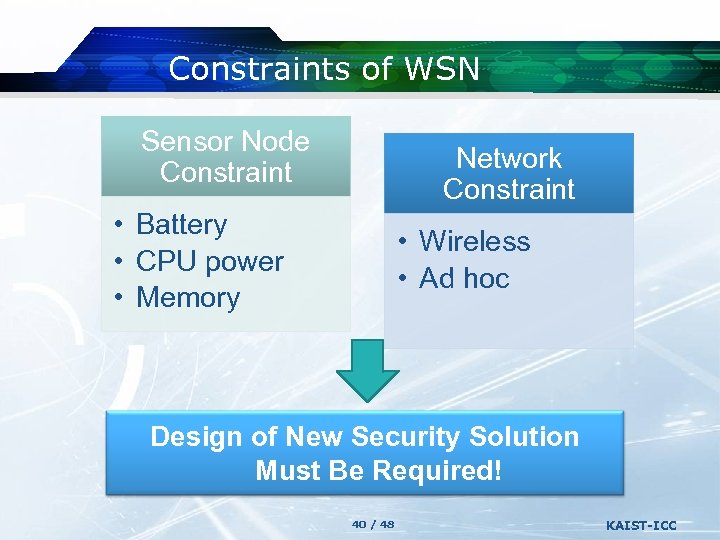
Constraints of WSN Sensor Node Constraint Network Constraint • Battery • CPU power • Memory • Wireless • Ad hoc Design of New Security Solution Must Be Required! 40 / 48 KAIST-ICC

Security Requirements for WSN v. Data Confidentiality (Eavesdropping) § Don’t leak sensor readings § Solution: Encryption v. Data Authentication (inject / alter Attack) § data was really from claimed sender § Solution: MAC v. Data Integrity (inject / alter Attack) § Received data is not altered in the mid-way § Solution: data authentication 41 / 48 KAIST-ICC

Attacks on WSN v Typical attacks on WSN are: § Sybil attack § Wormholes § HELLO flood attacks v Notations = adversary = base station = sensor node * D. Wagner, “Security for Sensor Networks: Cryptography and Beyond”, SASN 2003 42 / 48 KAIST-ICC

HELLO flood attack v Inferring a node is a neighbor (i. e. within radio range) after receiving a broadcast packet from them may be ill-conceived. An adversary with a powerful transmitter could easily reach every node in the network. * D. Wagner, “Security for Sensor Networks: Cryptography and Beyond”, SASN 2003 43 / 48 KAIST-ICC
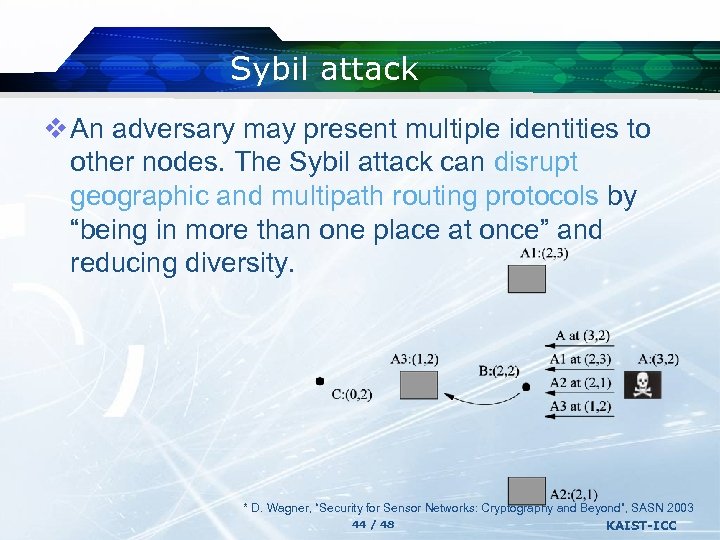
Sybil attack v An adversary may present multiple identities to other nodes. The Sybil attack can disrupt geographic and multipath routing protocols by “being in more than one place at once” and reducing diversity. * D. Wagner, “Security for Sensor Networks: Cryptography and Beyond”, SASN 2003 44 / 48 KAIST-ICC
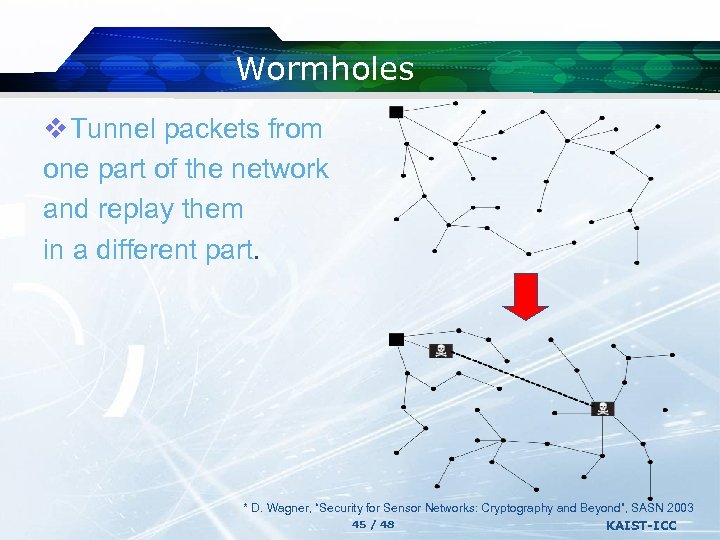
Wormholes v Tunnel packets from one part of the network and replay them in a different part. * D. Wagner, “Security for Sensor Networks: Cryptography and Beyond”, SASN 2003 45 / 48 KAIST-ICC

Conclusion v. RFID/USNs are essential technology for up-coming Ubiquitous world v. If the system is not designed with security in mind § This technology would harm human life v. Security should be considered from the design of entire Ubiquitous system 46 / 48 KAIST-ICC

723c7fd4fbd258eb09986ae4a57a1de6.ppt