9e69e353e0631c9396ac1147631a7b1f.ppt
- Количество слайдов: 18
 RFID Devices and Cryptography Analysis of the DST 40 A review of the article: Bono, S. C. , et al, Security Analysis of a Cryptographically-Enabled RFID Device. In P. Mc. Daniel, ed. , USENIX Security '05, pp. 1 -16. 2005 Dennis Galvin Practical Aspects of Modern Cryptography 07 -Mar-2006
RFID Devices and Cryptography Analysis of the DST 40 A review of the article: Bono, S. C. , et al, Security Analysis of a Cryptographically-Enabled RFID Device. In P. Mc. Daniel, ed. , USENIX Security '05, pp. 1 -16. 2005 Dennis Galvin Practical Aspects of Modern Cryptography 07 -Mar-2006
 DST 40 TI spec sheet photo ● ● ● Texas Instruments Cryptographically Secured RFID system DST : : Digital Signature Transponder 40 -bit key Used in a number of applications – – Exxon Mobil Speed. Pass(TM) Automotive Immobilizers ● ● 2005 Ford Some European Mfgrs. 2000 – 2005
DST 40 TI spec sheet photo ● ● ● Texas Instruments Cryptographically Secured RFID system DST : : Digital Signature Transponder 40 -bit key Used in a number of applications – – Exxon Mobil Speed. Pass(TM) Automotive Immobilizers ● ● 2005 Ford Some European Mfgrs. 2000 – 2005
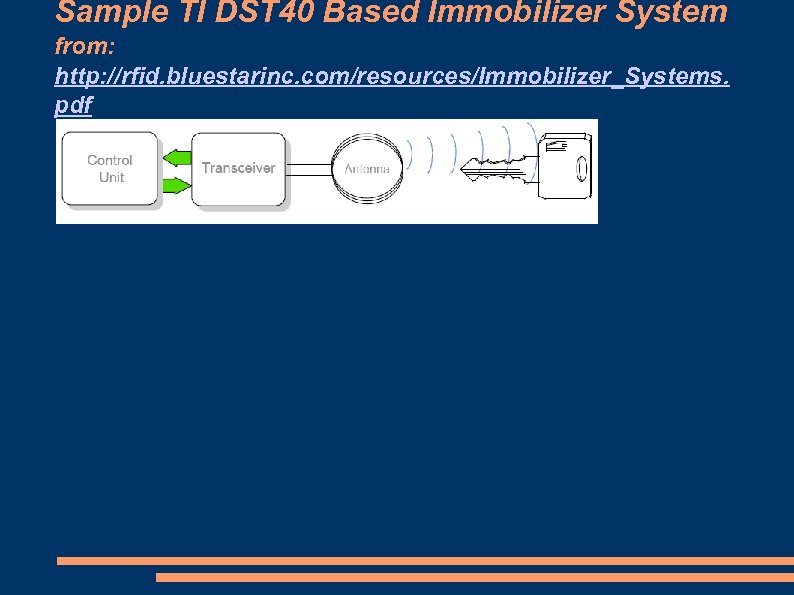 Sample TI DST 40 Based Immobilizer System from: http: //rfid. bluestarinc. com/resources/Immobilizer_Systems. pdf
Sample TI DST 40 Based Immobilizer System from: http: //rfid. bluestarinc. com/resources/Immobilizer_Systems. pdf
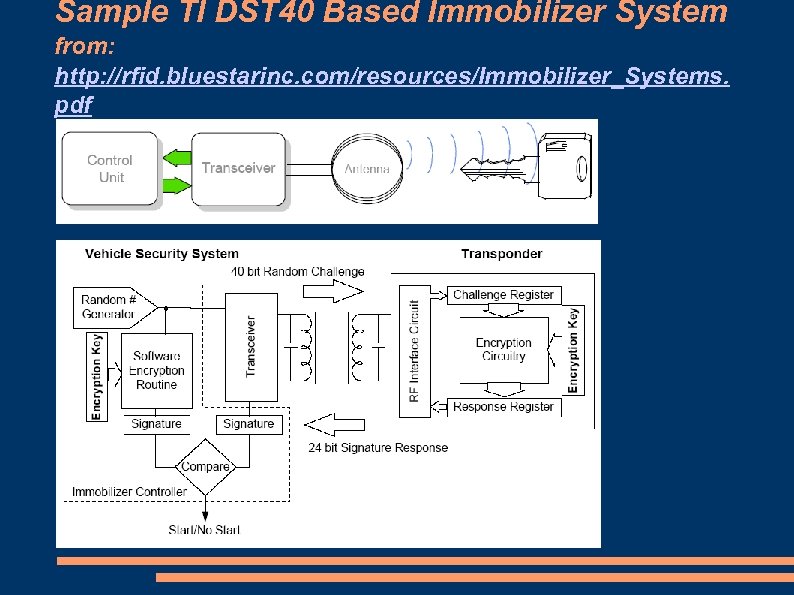 Sample TI DST 40 Based Immobilizer System from: http: //rfid. bluestarinc. com/resources/Immobilizer_Systems. pdf
Sample TI DST 40 Based Immobilizer System from: http: //rfid. bluestarinc. com/resources/Immobilizer_Systems. pdf
 Breaking the DST 40 ● Reverse engineer the cipher Build a key cracker Build the whole system – proof is in the pudding ● What's the big deal? ● ● – – Black box Use DST as oracle
Breaking the DST 40 ● Reverse engineer the cipher Build a key cracker Build the whole system – proof is in the pudding ● What's the big deal? ● ● – – Black box Use DST as oracle
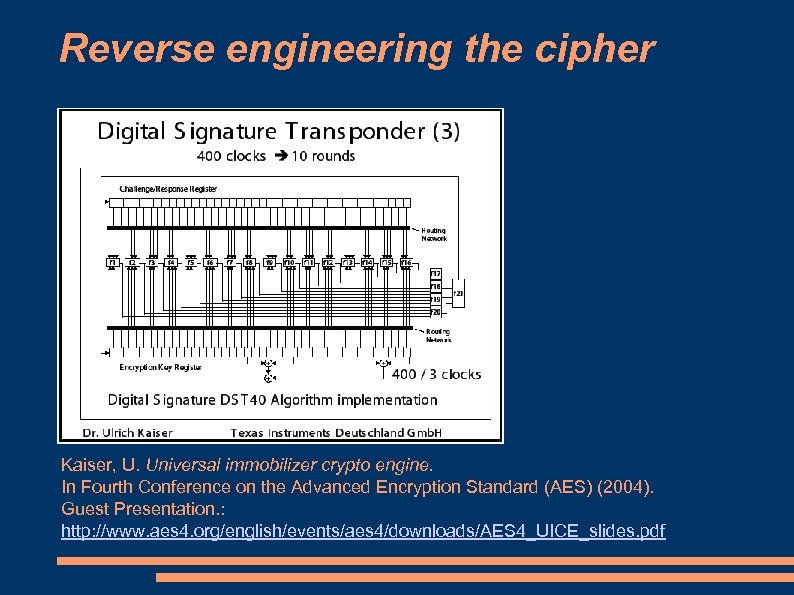 Reverse engineering the cipher Kaiser, U. Universal immobilizer crypto engine. In Fourth Conference on the Advanced Encryption Standard (AES) (2004). Guest Presentation. : http: //www. aes 4. org/english/events/aes 4/downloads/AES 4_UICE_slides. pdf
Reverse engineering the cipher Kaiser, U. Universal immobilizer crypto engine. In Fourth Conference on the Advanced Encryption Standard (AES) (2004). Guest Presentation. : http: //www. aes 4. org/english/events/aes 4/downloads/AES 4_UICE_slides. pdf
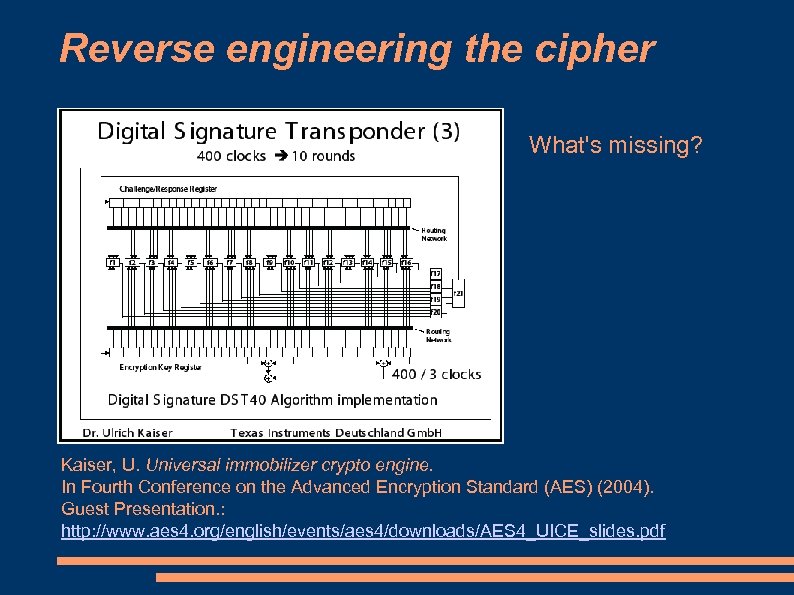 Reverse engineering the cipher What's missing? Kaiser, U. Universal immobilizer crypto engine. In Fourth Conference on the Advanced Encryption Standard (AES) (2004). Guest Presentation. : http: //www. aes 4. org/english/events/aes 4/downloads/AES 4_UICE_slides. pdf
Reverse engineering the cipher What's missing? Kaiser, U. Universal immobilizer crypto engine. In Fourth Conference on the Advanced Encryption Standard (AES) (2004). Guest Presentation. : http: //www. aes 4. org/english/events/aes 4/downloads/AES 4_UICE_slides. pdf
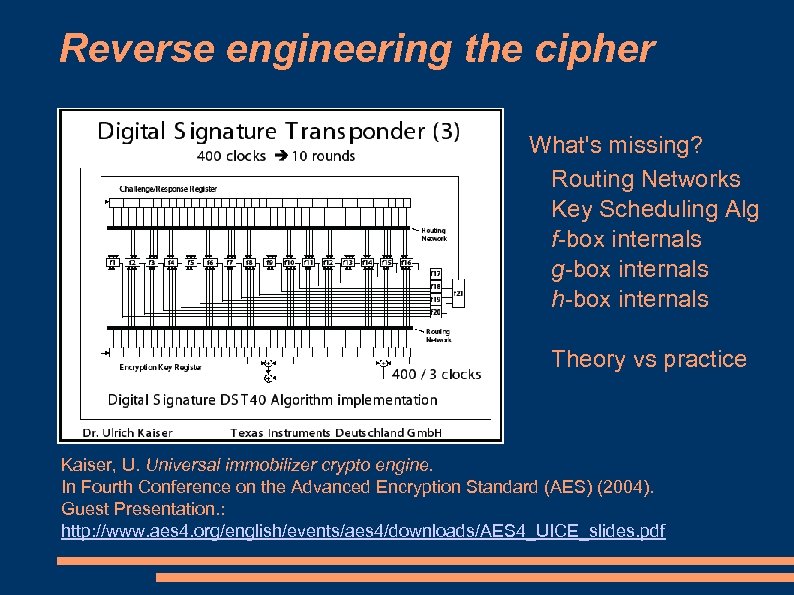 Reverse engineering the cipher What's missing? Routing Networks Key Scheduling Alg f-box internals g-box internals h-box internals Theory vs practice Kaiser, U. Universal immobilizer crypto engine. In Fourth Conference on the Advanced Encryption Standard (AES) (2004). Guest Presentation. : http: //www. aes 4. org/english/events/aes 4/downloads/AES 4_UICE_slides. pdf
Reverse engineering the cipher What's missing? Routing Networks Key Scheduling Alg f-box internals g-box internals h-box internals Theory vs practice Kaiser, U. Universal immobilizer crypto engine. In Fourth Conference on the Advanced Encryption Standard (AES) (2004). Guest Presentation. : http: //www. aes 4. org/english/events/aes 4/downloads/AES 4_UICE_slides. pdf
 Build the key cracker ● High end Intel based PC (3. 4 GHz)
Build the key cracker ● High end Intel based PC (3. 4 GHz)
 Build the key cracker ● ● High end Intel based PC (3. 4 GHz) Hardware based – – – Xilinx FPGA parallelize operations put 32 cores down on an FPGA ● ● – each core does full encryption in 200 clock cycles 100 Mhz clock now can search whole 40 -bit keyspace in 21 hrs ● on average only need to search half of the space
Build the key cracker ● ● High end Intel based PC (3. 4 GHz) Hardware based – – – Xilinx FPGA parallelize operations put 32 cores down on an FPGA ● ● – each core does full encryption in 200 clock cycles 100 Mhz clock now can search whole 40 -bit keyspace in 21 hrs ● on average only need to search half of the space
 Build the key cracker ● ● High end Intel based PC (3. 4 GHz) Hardware based – – – Xilinx FPGA parallelize operations put 32 cores down on an FPGA ● ● – now can search whole 40 -bit keyspace in 21 hrs ● ● each core does full encryption in 200 clock cycles 100 Mhz clock on average only need to search half of the space Parallelize again – – – put 16 FPGA's to the task 512 cores Cracked 5 DSTs from TI in less than 2 hrs.
Build the key cracker ● ● High end Intel based PC (3. 4 GHz) Hardware based – – – Xilinx FPGA parallelize operations put 32 cores down on an FPGA ● ● – now can search whole 40 -bit keyspace in 21 hrs ● ● each core does full encryption in 200 clock cycles 100 Mhz clock on average only need to search half of the space Parallelize again – – – put 16 FPGA's to the task 512 cores Cracked 5 DSTs from TI in less than 2 hrs.
 Build the key cracker ● ● High end Intel based PC (3. 4 GHz) Hardware based – – – Xilinx FPGA parallelize operations put 32 cores down on an FPGA ● ● – now can search whole 40 -bit keyspace in 21 hrs ● ● on average only need to search half of the space Parallelize again – – – ● each core does full encryption in 200 clock cycles 100 Mhz clock put 16 FPGA's to the task 512 cores Cracked 5 DSTs from TI in less than 2 hrs. Hellman Time-Memory Tradeoff (future work)
Build the key cracker ● ● High end Intel based PC (3. 4 GHz) Hardware based – – – Xilinx FPGA parallelize operations put 32 cores down on an FPGA ● ● – now can search whole 40 -bit keyspace in 21 hrs ● ● on average only need to search half of the space Parallelize again – – – ● each core does full encryption in 200 clock cycles 100 Mhz clock put 16 FPGA's to the task 512 cores Cracked 5 DSTs from TI in less than 2 hrs. Hellman Time-Memory Tradeoff (future work)
 Putting it all together: RF Protocol ● Easiest Piece of the puzzle – Build the device to actively interrogate DST ● ● ● Antenna from TI's development kit 12 -bit DAC/ADC board capable of 1 Mhz From this can actively interrogate responses to known challenges, feed back into the key cracker
Putting it all together: RF Protocol ● Easiest Piece of the puzzle – Build the device to actively interrogate DST ● ● ● Antenna from TI's development kit 12 -bit DAC/ADC board capable of 1 Mhz From this can actively interrogate responses to known challenges, feed back into the key cracker
 Putting it all together: RF Protocol ● Easiest Piece of the puzzle – Build the device to actively interrogate DST ● ● ● – Antenna from TI's development kit 12 -bit DAC/ADC board capable of 1 Mhz From this can actively interrogate responses to known challenges, feed back into the key cracker Build the device to simulate a DST ● ● Use the same physical setup as above Now can take information from the active attack plus the cracked keys and use it – – Start the car Buy gas
Putting it all together: RF Protocol ● Easiest Piece of the puzzle – Build the device to actively interrogate DST ● ● ● – Antenna from TI's development kit 12 -bit DAC/ADC board capable of 1 Mhz From this can actively interrogate responses to known challenges, feed back into the key cracker Build the device to simulate a DST ● ● Use the same physical setup as above Now can take information from the active attack plus the cracked keys and use it – – Start the car Buy gas
 What happenned ● What went wrong? – – – 40 bits too weak Security by Obscurity LFSR, only 80 -bits state
What happenned ● What went wrong? – – – 40 bits too weak Security by Obscurity LFSR, only 80 -bits state
 What happenned ● What went wrong? – – – ● 40 bits too weak Security by Obscurity LFSR, only 80 -bits state How to fix – – Use bigger key Don't use LFSR ● SHA 1, maybe even SHA 256
What happenned ● What went wrong? – – – ● 40 bits too weak Security by Obscurity LFSR, only 80 -bits state How to fix – – Use bigger key Don't use LFSR ● SHA 1, maybe even SHA 256
 Implications ● Other Crypto enabled applications of RFID – – RFID Scheduled for Passports Possible use in Identity cards Medical Insurance Cards Hospital Bracelets?
Implications ● Other Crypto enabled applications of RFID – – RFID Scheduled for Passports Possible use in Identity cards Medical Insurance Cards Hospital Bracelets?
 Web sites: ● ● http: //rfid-analysis. org/ (authors' web site) http: //www. ti. com/rfid/default. htm (Texas Instr. )
Web sites: ● ● http: //rfid-analysis. org/ (authors' web site) http: //www. ti. com/rfid/default. htm (Texas Instr. )


