Review_on_Certification_Exam.pptx
- Количество слайдов: 45
 Review on Certification Exam alikhamt@umail. iu. edu
Review on Certification Exam alikhamt@umail. iu. edu
 1. Which of the following statements is (are) true? I. A computer stores data so that it will be available for processing. II. Most computers only have one location for storing data. (a) I only (b) II only (c) I and II (d) None
1. Which of the following statements is (are) true? I. A computer stores data so that it will be available for processing. II. Most computers only have one location for storing data. (a) I only (b) II only (c) I and II (d) None
 • Super computers • Four basic operations of computers • Input ( person or environment ? ? ? )
• Super computers • Four basic operations of computers • Input ( person or environment ? ? ? )
 2) Applications that manage and track raw components, their usage in the manufacturing process, and delivery of finished products are known as _____ software. (a) supply chain management (b) project management (c) virtual reality (d) customer relations
2) Applications that manage and track raw components, their usage in the manufacturing process, and delivery of finished products are known as _____ software. (a) supply chain management (b) project management (c) virtual reality (d) customer relations
 History • • 1200 s—Manual Calculating Devices 1600 s—Mechanical Calculators (Pascaline) 1800 s—Punched Cards (Tabul. Machine) 1940 s—Vacuum Tubes 1950 s—Transistors 1960 s—Integrated Circuits (IC) 1970 s to Present—Microprocessor
History • • 1200 s—Manual Calculating Devices 1600 s—Mechanical Calculators (Pascaline) 1800 s—Punched Cards (Tabul. Machine) 1940 s—Vacuum Tubes 1950 s—Transistors 1960 s—Integrated Circuits (IC) 1970 s to Present—Microprocessor
 3) Which of the following is (are) true of vacuum tubes? • They typically respond faster than mechanical components. • They burn out more quickly than transistors. • They were replaced by transistors. (a) I and III only (b) II and III only (c) II only (d) I, II, and III
3) Which of the following is (are) true of vacuum tubes? • They typically respond faster than mechanical components. • They burn out more quickly than transistors. • They were replaced by transistors. (a) I and III only (b) II and III only (c) II only (d) I, II, and III
 4) Thin slices of silicon packed with thousands of microscopic circuit elements are known as (a) vacuum tubes (b) transistors (c) microchips (d) punched cards
4) Thin slices of silicon packed with thousands of microscopic circuit elements are known as (a) vacuum tubes (b) transistors (c) microchips (d) punched cards
 Applications of Computer Systems • In Education – Multimedia-Facilitated Learning (Power. Point) – Simulation-Based Education – Intelligent Machine-Based Training – Interactive Learning • In Business – Supply Chain Management – Project Management – Customer Relationship Management – Sales and Marketing Using Electronic Commerce – Manufacturing Research • In Entertainment
Applications of Computer Systems • In Education – Multimedia-Facilitated Learning (Power. Point) – Simulation-Based Education – Intelligent Machine-Based Training – Interactive Learning • In Business – Supply Chain Management – Project Management – Customer Relationship Management – Sales and Marketing Using Electronic Commerce – Manufacturing Research • In Entertainment
 5) Applications that handle product requirements, work schedules, milestones, and budgets are known as ____ software. (a) project management (b) virtual reality (c) business (d) supply chain management
5) Applications that handle product requirements, work schedules, milestones, and budgets are known as ____ software. (a) project management (b) virtual reality (c) business (d) supply chain management
 • Digital/analog signals • Binary digits
• Digital/analog signals • Binary digits
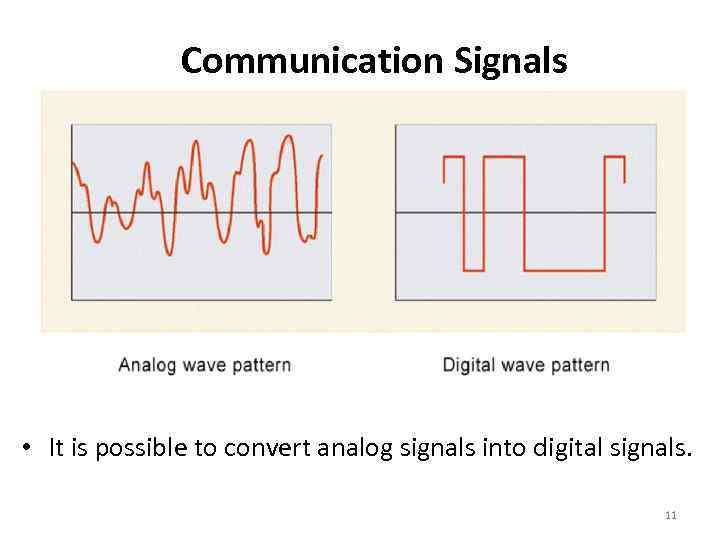 Communication Signals • It is possible to convert analog signals into digital signals. 11
Communication Signals • It is possible to convert analog signals into digital signals. 11
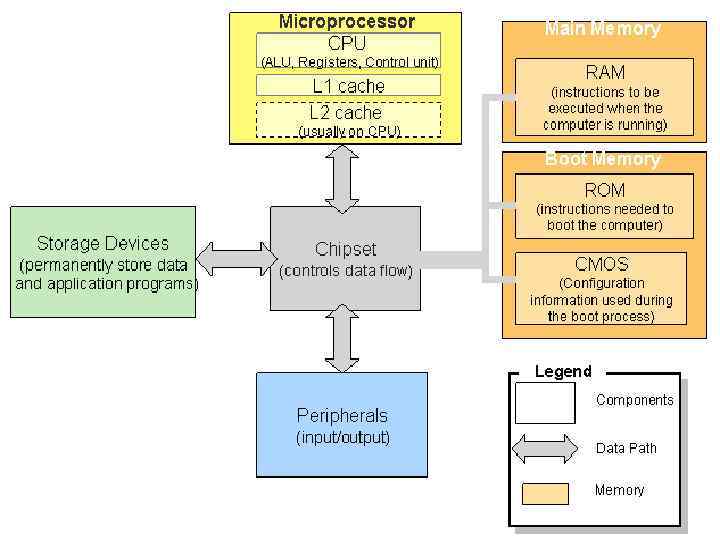
 Hardware 6) The _____ speed specifications in computer ads indicate the speed of the microprocessor. (a) clock (b) control unit (c) cache (d) register
Hardware 6) The _____ speed specifications in computer ads indicate the speed of the microprocessor. (a) clock (b) control unit (c) cache (d) register
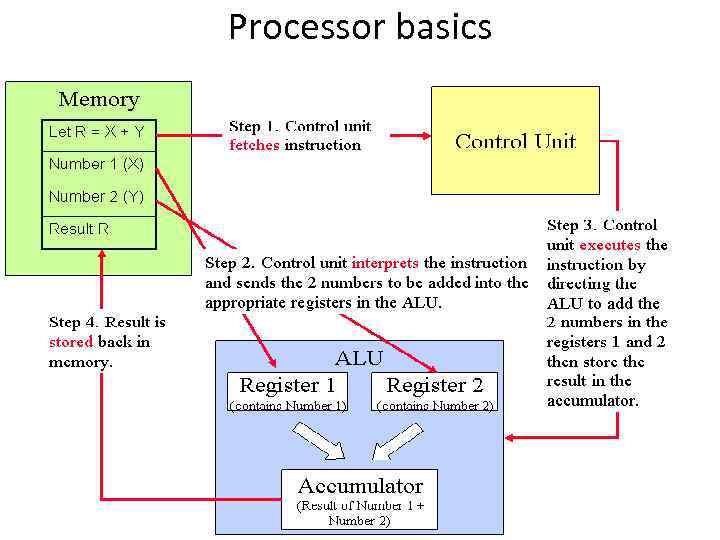 Processor basics
Processor basics
 7) The ALU uses _____ to hold data that is being processed. (a) cache (b) words (c) registers (d) control units
7) The ALU uses _____ to hold data that is being processed. (a) cache (b) words (c) registers (d) control units
 RAM • • • DRAM SDRAM DDR SDRAM RDRAM SRAM
RAM • • • DRAM SDRAM DDR SDRAM RDRAM SRAM
 Monitors 8) Cathode-ray-tube computer monitors use _____ color mixing, whereas color printers typically use _____ color mixing. (a) BIV, ROY (b) RGB, CMYK (c) CMYK, RGB (d) ROY, BIV
Monitors 8) Cathode-ray-tube computer monitors use _____ color mixing, whereas color printers typically use _____ color mixing. (a) BIV, ROY (b) RGB, CMYK (c) CMYK, RGB (d) ROY, BIV
 Monitors • Color depth • Resolution
Monitors • Color depth • Resolution
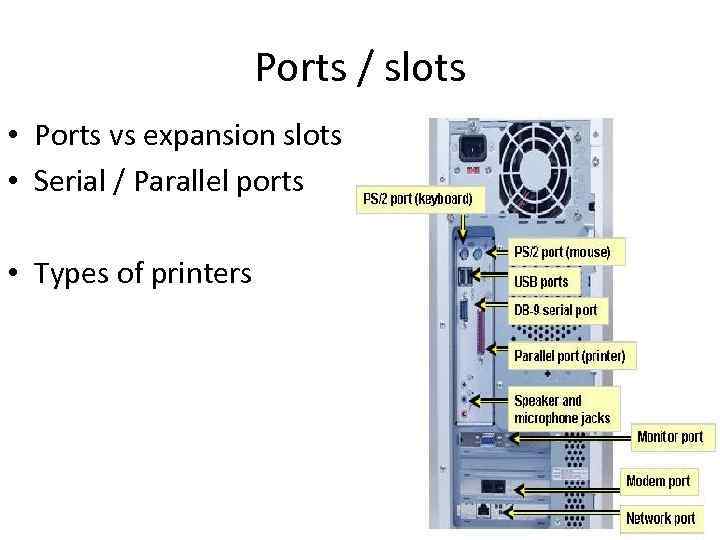 Ports / slots • Ports vs expansion slots • Serial / Parallel ports • Types of printers
Ports / slots • Ports vs expansion slots • Serial / Parallel ports • Types of printers
 Storage devices 9) Which of the following is (are) true regarding DVDs? I. They can have tracks on both sides of the disk. II. They can have two layers of tracks on one side of the disk. (a) I and II (b) II only (c) None (d) I only
Storage devices 9) Which of the following is (are) true regarding DVDs? I. They can have tracks on both sides of the disk. II. They can have two layers of tracks on one side of the disk. (a) I and II (b) II only (c) None (d) I only
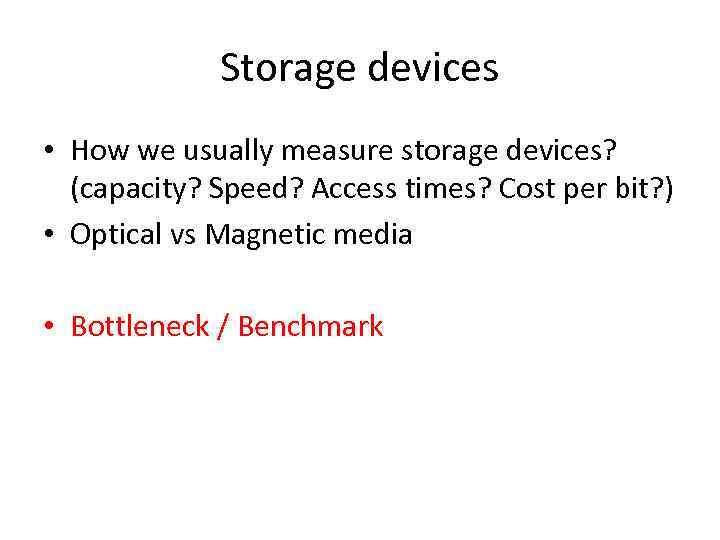 Storage devices • How we usually measure storage devices? (capacity? Speed? Access times? Cost per bit? ) • Optical vs Magnetic media • Bottleneck / Benchmark
Storage devices • How we usually measure storage devices? (capacity? Speed? Access times? Cost per bit? ) • Optical vs Magnetic media • Bottleneck / Benchmark
 Software • Polymorphism(один интерфейс, множество методов) • Encapsulation • Abstraction
Software • Polymorphism(один интерфейс, множество методов) • Encapsulation • Abstraction
 Layers of software User-Written Scripts or Macros User Interface Application Run-time Library Application Program Interface Operating System Kernel Device Drivers BIOS (Hardware)
Layers of software User-Written Scripts or Macros User Interface Application Run-time Library Application Program Interface Operating System Kernel Device Drivers BIOS (Hardware)
 10) Which of the following is an event similar to an interrupt, except that instead of being triggered by an external signal, it is generated by the execution of processor instructions? (a) A trap (b) An IRQ (c) A fault (d) A nested interrupt
10) Which of the following is an event similar to an interrupt, except that instead of being triggered by an external signal, it is generated by the execution of processor instructions? (a) A trap (b) An IRQ (c) A fault (d) A nested interrupt
 Software • • Interrupt priority Faults (page faults) IRQ ACL (access control list) Spooling System software / application software Bootstrap program
Software • • Interrupt priority Faults (page faults) IRQ ACL (access control list) Spooling System software / application software Bootstrap program
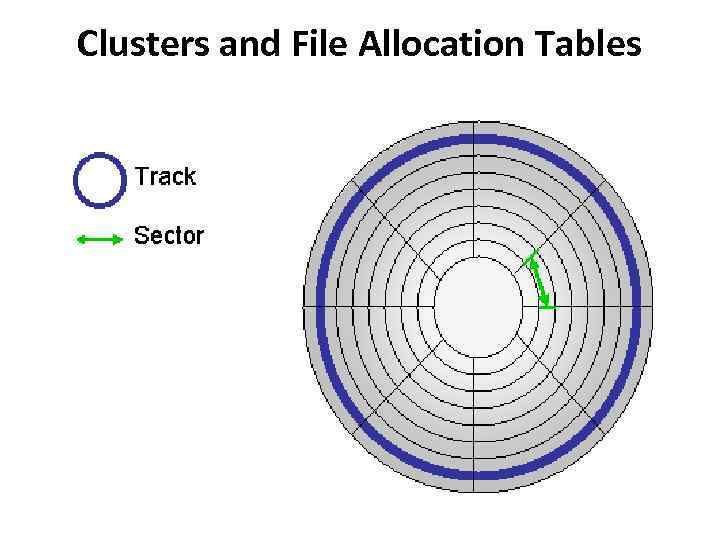 Clusters and File Allocation Tables
Clusters and File Allocation Tables
 11) The mechanism used by a computer to ensure that all keyboard strokes are properly recorded, regardless of how fast a user may type, is a keyboard (a) GUI (b) index (c) interpreter (d) buffer
11) The mechanism used by a computer to ensure that all keyboard strokes are properly recorded, regardless of how fast a user may type, is a keyboard (a) GUI (b) index (c) interpreter (d) buffer
 DOS commands • Where is the switch? Argument? Parameter? dir /w c: dir /o: s dir c: *. doc • Piping / Redirection • Pipe: dir c: windows | gzip > test. gz
DOS commands • Where is the switch? Argument? Parameter? dir /w c: dir /o: s dir c: *. doc • Piping / Redirection • Pipe: dir c: windows | gzip > test. gz
 12) Database models that have been used successfully include which of the following? I. Hierarchical II. Network III. Relational (a) I and III only (b) II and III only (c) I and II only (d) I, II, and III Which one is simplest?
12) Database models that have been used successfully include which of the following? I. Hierarchical II. Network III. Relational (a) I and III only (b) II and III only (c) I and II only (d) I, II, and III Which one is simplest?
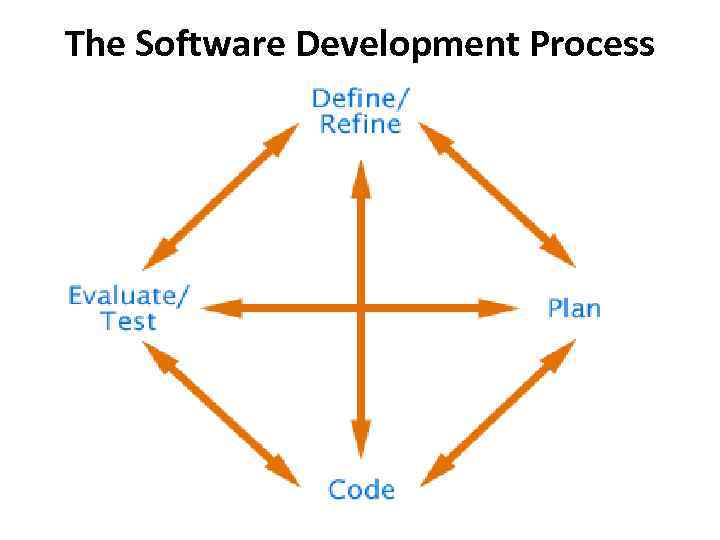 The Software Development Process
The Software Development Process
 The Software Development Process • Software Engineering - a systematic approach to the development, operation, maintenance, and retirement of a software system
The Software Development Process • Software Engineering - a systematic approach to the development, operation, maintenance, and retirement of a software system
 URL • http: //www. carnegietech. org
URL • http: //www. carnegietech. org
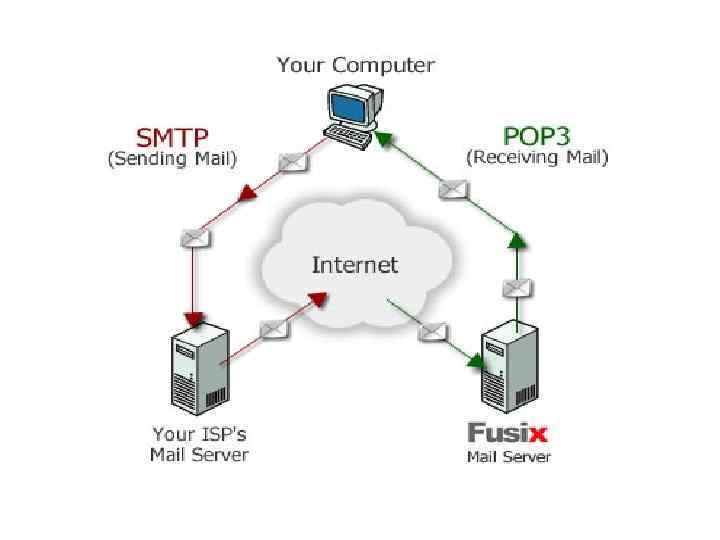
 13) A conversion system called _____ enables digital photos, sounds, and other media to be represented as ASCII text that can travel over the Internet as email attachments. (a) POP (b) IMAP (c) MIME (d) SMTP
13) A conversion system called _____ enables digital photos, sounds, and other media to be represented as ASCII text that can travel over the Internet as email attachments. (a) POP (b) IMAP (c) MIME (d) SMTP
 Architectures • Thick client / thin client • Web browser? ? ? • P 2 P / Client-Server (Apache) • Dial-up vs DSL (ADSL)
Architectures • Thick client / thin client • Web browser? ? ? • P 2 P / Client-Server (Apache) • Dial-up vs DSL (ADSL)
 Network devices • Hub • Router • Repeater • TCP/IP
Network devices • Hub • Router • Repeater • TCP/IP
 Security • Viruses 14) An intruder sending email messages that appear to be coming from a system administrator is an example of a _____ attack. (a) spoofing (b) cracking (c) packet sniffing (d) brute force
Security • Viruses 14) An intruder sending email messages that appear to be coming from a system administrator is an example of a _____ attack. (a) spoofing (b) cracking (c) packet sniffing (d) brute force
 Security • Cryptography • Biometrics • Smart cards • Backups • Passwords
Security • Cryptography • Biometrics • Smart cards • Backups • Passwords
 Smart Cards • Credit card-sized plastic card with an embedded integrated circuit chip that can serve as a secure medium for storing personal identification information such as - picture identifications - fingerprints, - account information. - voiceprints - signatures • Chip consists of a microprocessor, ROM, RAM, and electrically erasable programmable read only memory (EEPROM). • EEPROM enables the chip to retain its state even when power is removed.
Smart Cards • Credit card-sized plastic card with an embedded integrated circuit chip that can serve as a secure medium for storing personal identification information such as - picture identifications - fingerprints, - account information. - voiceprints - signatures • Chip consists of a microprocessor, ROM, RAM, and electrically erasable programmable read only memory (EEPROM). • EEPROM enables the chip to retain its state even when power is removed.
 Smart Cards • Information on card can be read by a customprogrammed reader for authentication • Can be used as an access key to a computer system • Can be embedded on phone cards, banking cards or health cards • Contain security features such as data encryption • Self-containment of a smart card allows it to be resistant to network or Internet attacks.
Smart Cards • Information on card can be read by a customprogrammed reader for authentication • Can be used as an access key to a computer system • Can be embedded on phone cards, banking cards or health cards • Contain security features such as data encryption • Self-containment of a smart card allows it to be resistant to network or Internet attacks.
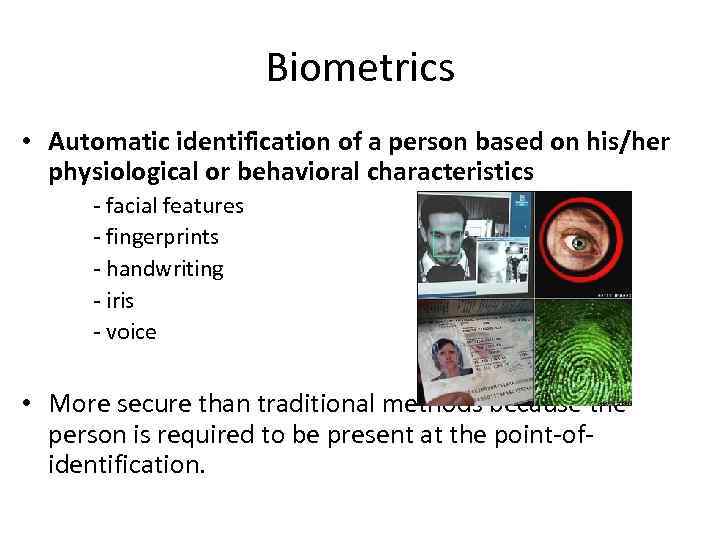 Biometrics • Automatic identification of a person based on his/her physiological or behavioral characteristics - facial features - fingerprints - handwriting - iris - voice • More secure than traditional methods because the person is required to be present at the point-ofidentification.
Biometrics • Automatic identification of a person based on his/her physiological or behavioral characteristics - facial features - fingerprints - handwriting - iris - voice • More secure than traditional methods because the person is required to be present at the point-ofidentification.
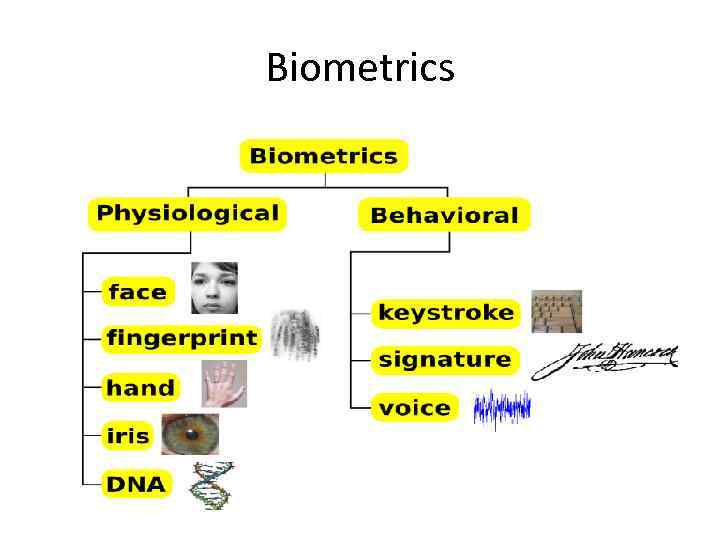 Biometrics
Biometrics
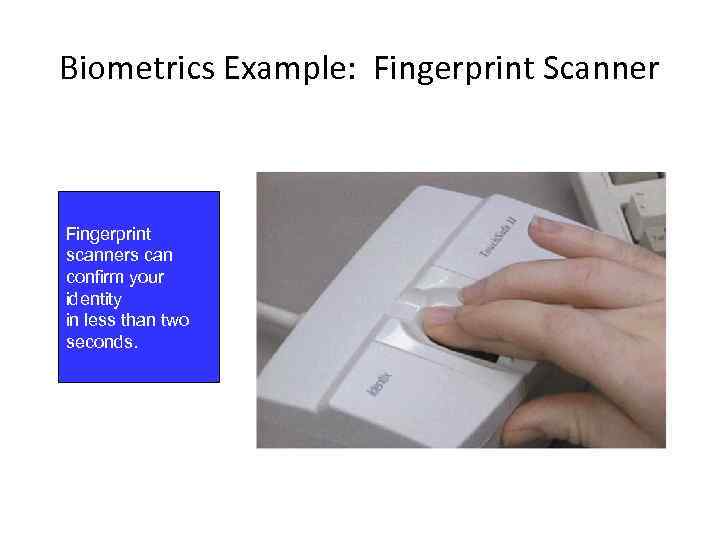 Biometrics Example: Fingerprint Scanner Fingerprint scanners can confirm your identity in less than two seconds.
Biometrics Example: Fingerprint Scanner Fingerprint scanners can confirm your identity in less than two seconds.
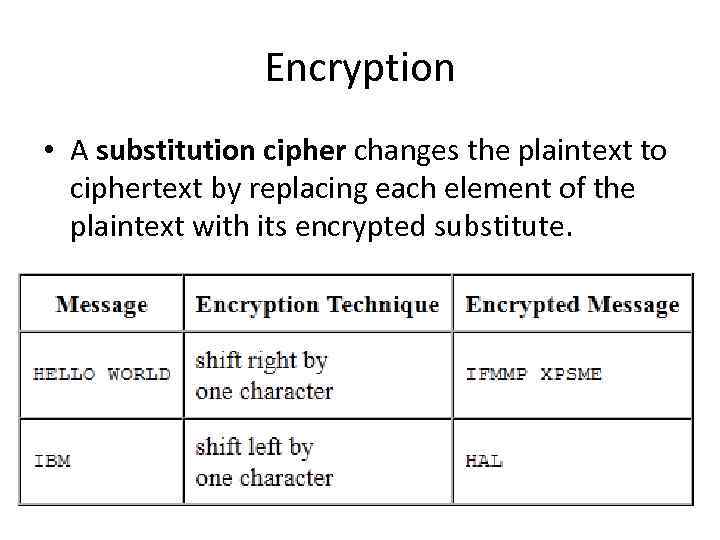 Encryption • A substitution cipher changes the plaintext to ciphertext by replacing each element of the plaintext with its encrypted substitute.
Encryption • A substitution cipher changes the plaintext to ciphertext by replacing each element of the plaintext with its encrypted substitute.
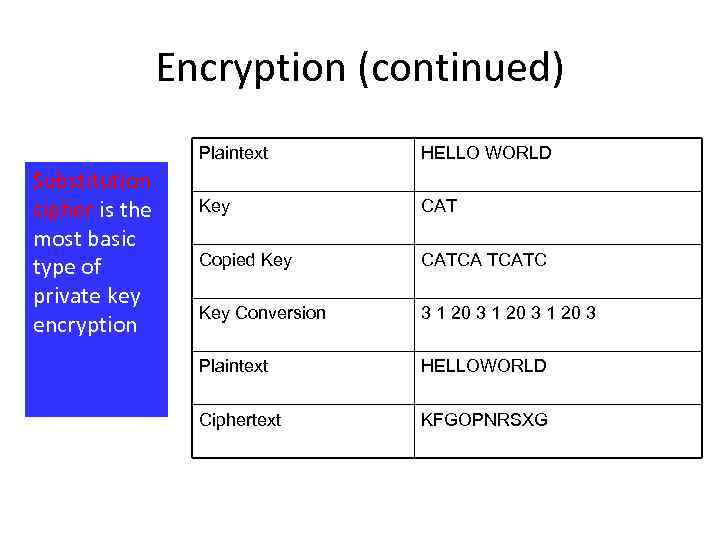 Encryption (continued) Plaintext Substitution cipher is the most basic type of private key encryption HELLO WORLD Key CAT Copied Key CATCA TCATC Key Conversion 3 1 20 3 Plaintext HELLOWORLD Ciphertext KFGOPNRSXG
Encryption (continued) Plaintext Substitution cipher is the most basic type of private key encryption HELLO WORLD Key CAT Copied Key CATCA TCATC Key Conversion 3 1 20 3 Plaintext HELLOWORLD Ciphertext KFGOPNRSXG


