eedbd9858273561c580e6bb0083e7a83.ppt
- Количество слайдов: 22

Relations between Security, Technologies and Citizens EUROCITIES FSF-Telecities Summer Event ICT FOR SAFE DIGITAL CITIES June 2007 Dr David Murakami Wood d. f. j. wood@ncl. ac. uk Global Urban Research Unit

Outline § Concepts: § Technology § Security § Citizenship § § 9 Steps Towards Ambient Surveillance? Examples 5 Models of Society Problems and Prospects § Technological Lock-in § Dehumanisation and Insecurity § Enabling Environments or Automated Societies? § Concluding Challenges

Concepts 1: Technology § Traditional view of technology: § Linear Cause-and-Effect ‘Impacts’ on Cities § Predictable e. g. : Cities will spread out or 'die‘ because of Internet § Utopian version = Technological determinism § If it can be done, it should be done § People should fit the system § ‘Silver bullet’ view: technology ‘x’ will solve problems e. g. : CCTV and crime § BUT: Technological relations are also social relations § § Produced for particular reasons, in particular contexts Support mobility and control for capital and social elites Uneven geographies reworked not eliminated Create new forms of social divisions § Technological capacity ahead of policy capacity

Concepts 2: Security § Predominance of risk and risk management § Militarisation: § Military concepts move to civil arena § Increasingly permanent State of Emergency / State of Exception § Security becomes ‘trump card’ over liberty, privacy, human rights etc. § Security = safety? § The Return of Mass Surveillance § Surveillance has always been part of government § Care and Control are not in opposition § Targeted v. mass surveillance

Concepts 3: Citizenship § Components of Trust: § § § Accountability Bias Predictability Affect Competence § Problems of Privacy § From individual to social / group privacy? § Problem of Data § Data still treated as simply ‘information about…’ § State sees right to acquire data as paramount? § But: ‘Data Doubles’ as important to life chances as physical bodies? § Data = valuable commodity, c. f. : image rights debate § Problem of Transparency § Surveillance and Freedom of Information = reciprocal
Towards Ambient Surveillance? 1 -3 1. Digitisation – information in searchable and remotely accessible databases § § § 2. Automation – algorithms analyse collected data § § § 3. Creation of Data Doubles - digital citizens composed of the information, stand for ‘real’ selves in transactions with the state. Profiling Social Sorting – based on risk / profit Simulation Pre-emption – anticipating and preventing Heuristics – learning systems, self-programming? Connection – telecommunication combination with computing § § § Connection between previously separate systems Information sharing – convenience but increased danger of unauthorized use Wireless – WPAN – WLAN – WWAN – WGAN?

Towards Ambient Surveillance? 4 -6 4. Increasing Power § § § 5. Miniturization § § § 6. Moore’s Law: processing power doubles approx. every 12 months Greater intensity of surveillance But also: speed – real time From room-sized machines to almost microscopic in 50 years Combination of greater power in smaller chips ‘Smart Dust’ sensors / ‘Motes’ c. 2 x 2 mm Nanotechnology – molecular machines Towards workable quantum computing? Distribution § § § Technologies no longer have to be single objects in boxes Dispersed networks of (invisibly) linked components At-a-distance surveillance and analysis

Towards Amient Surveillance? 7 -9 7. Infrastructurization § § 8. Technologies moved from being highly visible to being buried or moving within Components become assumed and taken for granted Mobility § § 9. Devices no longer have to be in one place Mobile with user Remote Controlled Independently mobile? Robots and ‘Swarms’ Addressability § § § Standard ‘address’ – URL, protocols and languages Location - where are you? Verification – are you entitled? Identification – who / what are you? Protocols are the key…

Example 1: Biometrics § Technologies that ‘recognise’ human bodily traits or movements, e. g. : § facial recognition § iris scanning § movement recognition etc. § Already widespread § Some more reliable than others § Problems with face recognition § Need to reorganise space to ‘make it work’? Privium System, Schiphol Airport,

Example 2: (Trans)National Databases § Growing numbers of national databases § § Police DNA Database (NDNAD) FIND Connecting for Health National Identity Register (NIR) etc. § Many questions, e. g. : NDNAD § Preponderance of black men’s DNA § DNA of innocent § Children’s DNA § New problem: cross-border sharing § With USA – e-borders projects § With EU – agreements on data-sharing (just signed) § Where are systems of accountability, consent etc. ?
Example 3: RFID § Radio Frequency Identification chips § Current ‘silver bullet’ (smart everything…) § Passive vs. Active § Tags and Implants § Used for: § § Cargo Retail products Animals People – from patients to nightclubbers to workers to…? Human RFID implant (Getty Images)

Example 4: Mobile Cameras § Increasing development of either temporary, remotecontrolled or independently mobile systems § e. g. : § § Helmet Cams – and not just for police Unmanned Aerial Vehicles (UAVs). Rolling Robots Swarms – robots working together From the skies over the Gulf to the streets of Liverpool and Milan: UAVs (top – military Predator drone aircraft (USAF); left – r/c helicopter camera (PA)

Example 5: Scanners § Only use a small part of the EM spectrum § Developers want to change this. e. g. : § Backscatter X-ray (Rapiscan) § Millimetre Wave (Qinetiq) § Increasingly portable and low-cost § From airports to train stations, shopping centres, schools… § Pinch-points § Brain scanning – moving Qinetiq’s next generation millimetre wave scanner (Qinetiq Press Release, 2004)
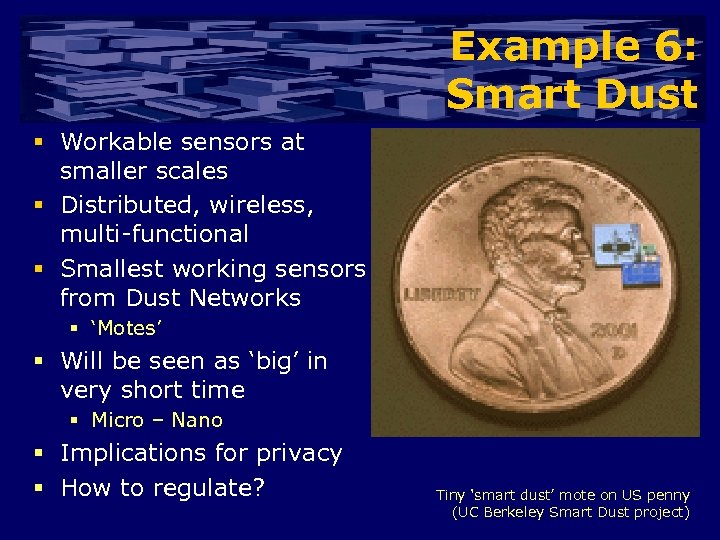
Example 6: Smart Dust § Workable sensors at smaller scales § Distributed, wireless, multi-functional § Smallest working sensors from Dust Networks § ‘Motes’ § Will be seen as ‘big’ in very short time § Micro – Nano § Implications for privacy § How to regulate? Tiny ‘smart dust’ mote on US penny (UC Berkeley Smart Dust project)

Five Models of the Ambient Intelligence Society 1. Volunteerism – the ‘British Way’ – muddlethrough, compromise etc… 2. Laissez-Faire – let the market decide 3. Security State – militaristic paternalism 4. Transparent Society – everything is known 5. Reciprocal Society – mutual accountability

Model 1: Volunteerism § Development of ambient intelligence and protocols ignored § Lack of fundamental rights § Codes of Practice and volunteerism predominate § Shackled regulators § State able to produced contingent arguments for exceptions and exemptions § Technological advances run ahead of policy § Trust problem not addressed § Costs out of control § Never certain where ‘lines crossed’ § Citizen participation = patchy

Model 2: Laissez-faire § All the privacy you can afford § Protocols developed by private sector: § Development of ‘Brandscapes’ § Encourage development of ‘Personal Information Economy’ § Personal data as commodity § State and private sector pays market value of data it wants § But in turn citizen has to pay for access to information § Embedded within existing unequal market relations § ‘Privacy’ set by market relations and technological capacity § Privacy-Enhancing Technologies (PETS) § Rich become ‘augmented’; poor left conventional
Model 3: Security State § Nothing to Hide, Nothing to Fear § Assume that State of Exception will become the norm § Security trumps all other considerations § Rights contingent on national security considerations § Citizen can obtain what information state feels is relevant and necessary § State can share data as it wishes and can change the purposes to which data is used as it wants. § Protocols developed by state: § Automated systems which cannot be questioned § Space altered to fit system requirements
Model 4: Transparent Society § Information Wants to Be Free § Proliferation of quasi-independent automated systems for multiple functions § Open-source protocols developing through interaction Assume all information will flow § Everything you do is public knowledge or liable to be known by the state, private companies, and other individuals § But everything the state or private companies do is equally available § No assumption of privacy, but build specific minimal protections based on contracts allowable in clearly-defined circumstances

Model 5: Reciprocal Society § Surveillance and accountability as reciprocal § Liberty and privacy integral part of national security, not opposed to it § Technologies fitted to policies not vice-versa § Mandatory Privacy / Surveillance Impact Assessment for new technologies and systems § Control exercised over developed of Ambient Intelligence protocols – for common good. § Create new legal bases for relationships between state and citizen § Strengthen independent oversight and audit capacity § States, companies are ‘custodians’ of data not owners

Problems and Prospects § Technological Lock-in § Choice and implementation of technologies in cities can cut down future choices for citizens § Can’t let ‘system requirements’ precede citizen choice § System failure § Dehumanisation and Insecurity § Does humanizing cities through ambient intelligence means relative dehumanisation of people? § Mass surveillance creates insecurity and division § Enabling Environments or Automated Societies? § Ambient Intelligence can enable the already disabled: sensory environments, interactive cities § Or it could industrialise and automate behaviour c. f. : Lianos’ Automated Socio-Technical Environments (ASTEs)

Concluding Challenges § Policy still a long way behind technological development § Need to move from ‘running to catch up’ to ‘getting ahead of the game’ § Need to understand challenges of ubiquity of surveillance § § § State – citizen Corporate – citizen Citizen – citizen Parastates, Criminals… Media Things… § Need to rethink conception of data § Need to rethink understanding of privacy § How to assess technologies? § Not just ‘education’ and ‘making people understand. ’ § Need to involve people § Open-source Protocols – interactive environments
eedbd9858273561c580e6bb0083e7a83.ppt