b39a6e6305ece0d0b431a20741f8d551.ppt
- Количество слайдов: 52

Regents Education Program September 2006 Information Technology and Higher Education: Managing Achievements and Expectations Kurt A. Snodgrass Vice Chancellor, IT & Telecommunications

Perfect Storm or New Dawn? In today’s knowledge economy, the role of higher education is being redefined – not simply tweaked and fine-tuned but, rather, fundamentally redefined. James Hilton, Associate Provost for Academic, Information, and Instructional Technology Affairs and Interim University Librarian at the University of Michigan

A Balancing Act for Higher Ed Institutional Mission Student Needs & Expectations • Striking a fine balance is key for institutional CIOs
A Balancing Act for Higher Ed Instit utiona l Missio n Stude nt Ne eds & Expec tation s • Institutional mission can be jeopardized • Security, Data Integrity can be compromised • Bandwidth bottleneck can affect networking, communications and research
A Balancing Act for Higher Ed l tiona u nstit sion I Mis eeds N dent Stu & tions a pect Ex • Overly tight controls limit access to technologies and information • Curbs innovation in teaching and learning • Will likely result in student dissatisfaction

State System CIO Perspective • Council on Information Technology 2005 survey identified key issues facing system CIOs – Top 5 Issues • • • Funding Security threats Upgrading and maintaining infrastructure Simplification (Enterprise Contracts and Collaboration) Moving faculty toward better use of technology

Proliferation of New Technologies • Distance Learning – Synchronous (2 -way interactive) – Asynchronous (Web-based) • Wireless – Anytime, anywhere access – Mobile computing and communications • Bandwidth Management – Peer-to-Peer (P 2 P) • Music and movie downloads
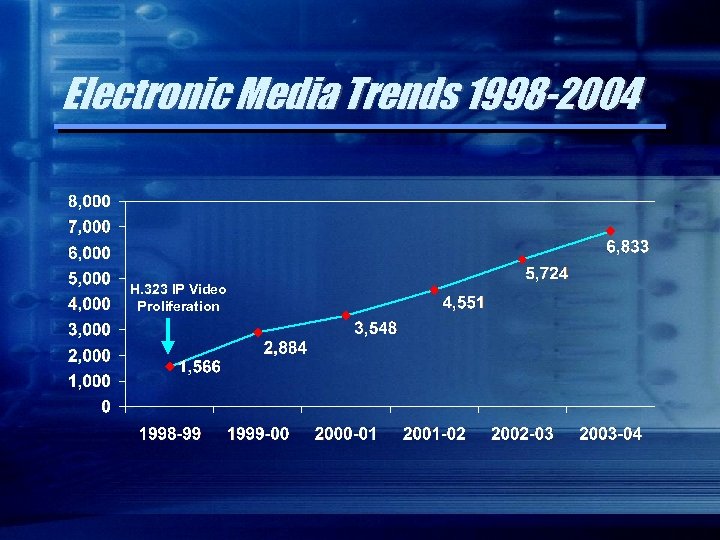
Electronic Media Trends 1998 -2004 H. 323 IP Video Proliferation
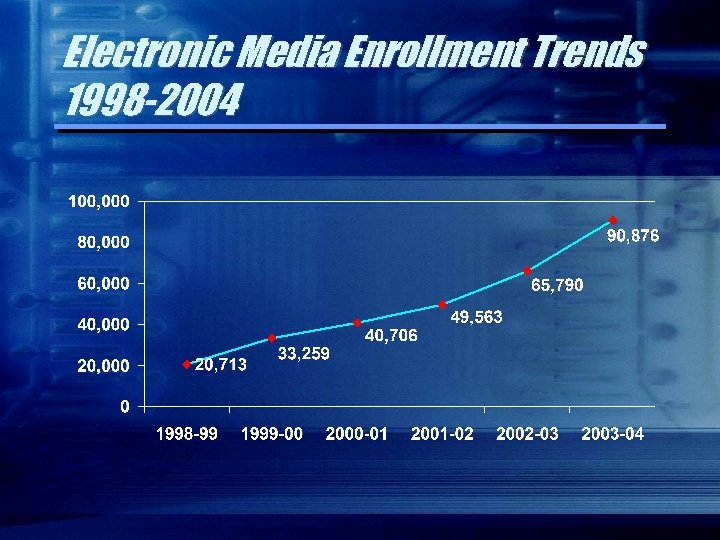
Electronic Media Enrollment Trends 1998 -2004
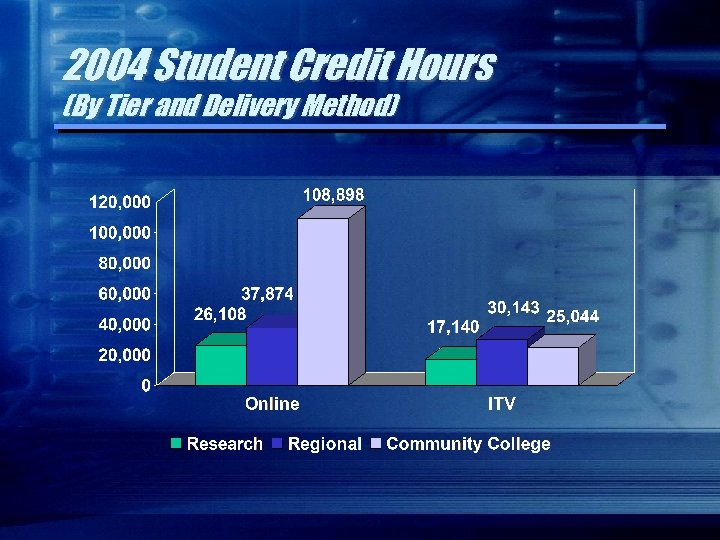
2004 Student Credit Hours (By Tier and Delivery Method)

In Higher Education Alone… Over 245 K Credit Hours Delivered Via Technology!

Rationale for Growth • Increased comfort and familiarity with technology by both faculty and students • Enhancements in Content Management Systems (CMS) – Quality – Ease of use • More schools developing hybrid classes • More emphasis on reaching nontraditional and/or adult students

Wireless Technologies • Sprint Higher Education Advisory Board Findings – Trends • Cellular dominates – students prefer it and use it almost exclusively – Decline of landline phones • Adoption of personal email (gmail, yahoo mail, hotmail, etc. ) – University emails go unread • 3 rd party portals (Face. Book, Daily. Jolt, My. Space) – University portal usage declining

Wireless Technologies • Sprint Higher Education Advisory Board Findings – Effects • • It’s hard to communicate with students! Emergency calls bypass campus safety Decrease in sense of community Decrease in long distance revenue

Wireless Technologies • Campus Local Area Networks (LANs) and Wide Area Networks (WANs) – 90 percent of campuses in the United States have some form of wireless networking, according to the Campus Computing Project – Relatively low cost with big impact • Significantly reduces cabling costs – Increases access and productivity – Provides for scalability and flexibility

Wireless Technologies • Can be isolated – Classroom or building-based • Can be campus-wide • Increases competitiveness of institution • Supports innovation – Provides enhanced collaboration and e-learning environments

Wireless Technologies • Security is a major concern – A multitude of operating systems, devices and platforms accessing the network creates specific challenges – Unmanaged devices can become infected off-site and introduce issues when connected to the campus network • Students, staff & faculty with laptops • Clean Access – Security and authentication are paramount

Wireless Technologies • Wardriving – Is searching for Wi-Fi wireless networks by moving vehicle. It involves using a car or truck and a Wi-Fi -equipped computer, such as a laptop or a PDA, to detect the networks – Normally engaged in to gain free internet access or illegal access to an organization’s data though some do it for sport – No longer have to have physical access to an institution’s facilities to gain access to private data
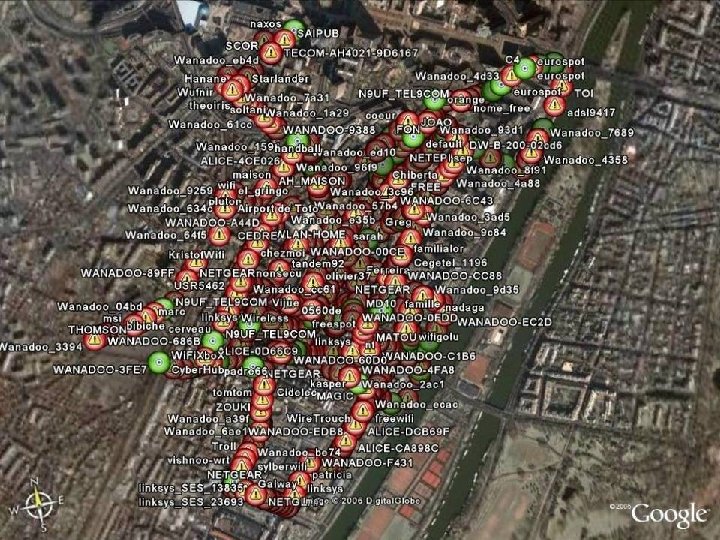

First Wardriver

Real Wardriving Gear
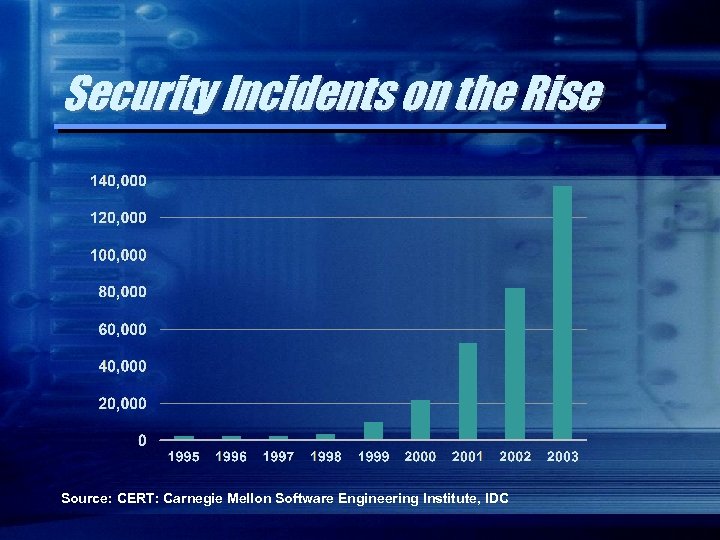
Security Incidents on the Rise Source: CERT: Carnegie Mellon Software Engineering Institute, IDC

Security Incidents on the Rise One virus/worm incident costs $100, 000 -Source: International Computer Security Association (ICSA) 2003 Annual Virus Survey

Network Security Threats • • • Worm Virus Spyware/Malware Denial of Service (DOS) Attack Trojan Horse

Security is no longer an option… It’s a necessity • Security as an Option • Security as INTEGRAL of a System • Security is an add-on • Security is built-in • Challenging integration • Intelligent collaboration • Not cost-effective • Appropriate security • Cannot focus on core priority • Direct focus on core priority Source: Cisco Systems

Recent State Security Mandates • HB 2935 – Requires risk assessments be completed for all agencies and institutions • Will remain confidential • Will classify each site as low to high in profile – Two vendors will be chosen to conduct full security assessments • Institutions can accomplish this independently – No funds were appropriated to assist in the thirdparty engagements – All security audits due by December 1 st, 2006

Bandwidth Management • Putting it in perspective – Kinda’ like not knowing if you have enough gas to get you to the next station • Leaves a sick feeling in your stomach until you get there… • IF you get there – Better yet, its like having a dinner party and not knowing if you have enough brisket – Then you realize…

Bandwidth Management

Bandwidth Management

Bandwidth Management

Bandwidth Management • Usual Bandwidth Hog Suspects – Limited few computer engineering geeks developing networkintensive computer models & algorithms – Normally maintain some level of anonymity – An “underground” group difficult to identify

Bandwidth Management • The reality is… – The general student population is the real culprit – Peer-to-Peer (P 2 P) file sharing is bringing many networks to their knees

Peer-to-Peer Defined • P 2 P is a type of network in which each workstation has equivalent capabilities and responsibilities. – Files are propagated on every machine accessing the service and then shared with others • Once considered as totally illegal and now has legitimate sites • Not all P 2 P is bad. – – – Grid computing Operating system distribution (Condor) Legitimate music and movie sites

Peer-to-Peer Applications • • Napster Kazaa Ares Bit. Torrent Direct Connect e. Donkey Fast. Track • • • Filetopia Gnutella IRC Manolito P 2 P Open. Nap Soul. Seek – Many applications are disguising their code as normal Web traffic (Bit. Torrent) – Costs are staggering in terms of operations

Peer-to-Peer Realities • Affects both institutional and statewide networks • Can impact distance learning missions if not kept in check – Clogs the network pipes • Continues to morph and become harder to identify and manage • Can compromise Disaster Recovery/Business Continuity efforts • Recording Industry Association of America – Those pirating music and movies are being sued and arrested
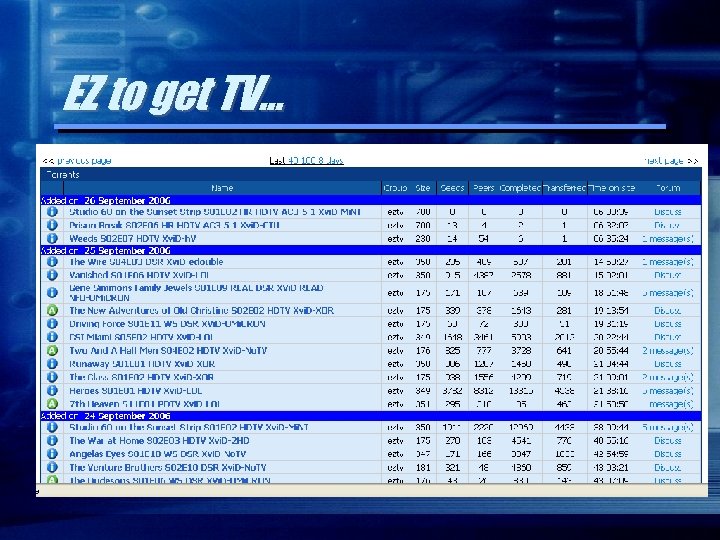
EZ to get TV…

One Solution to P 2 P Traffic • Ruckus – A digital entertainment service for universities – Ruckus offers: • • National, local, and campus based programming 1. 5 million licensed tracks of music from major labels Hollywood blockbusters, cult classics, and independent films Robust community features that allow students with similar music, video and programming interests to connect, share and explore on their campus – A few campuses already have agreements – One. Net is exploring an enterprise solution for the system • Will keep traffic within the state network and off commodity Internet
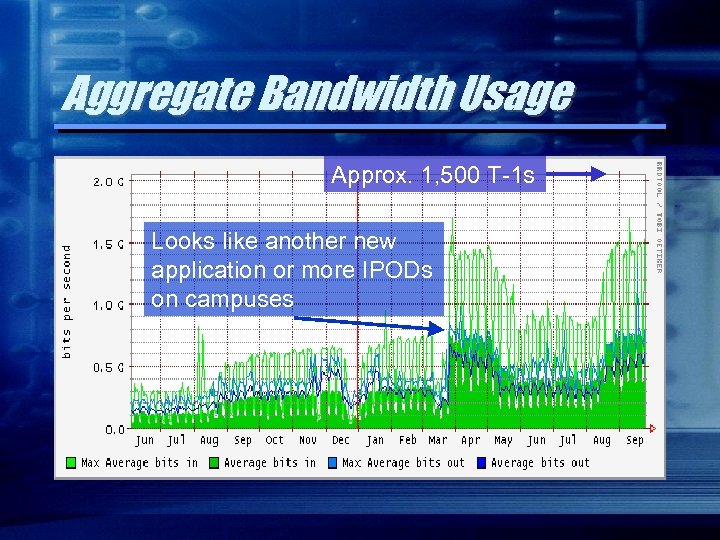
Aggregate Bandwidth Usage Approx. 1, 500 T-1 s Looks like another new application or more IPODs on campuses

Meeting Research Needs • Research needs cannot be compromised by limitations in bandwidth • National efforts in place to assure network resources are available • Network demands have grown from megabytes to gigabytes, to terabytes and now petabytes – States can’t afford this type of commodity Internet

Internet 2 • Goals – Enable a new generation of applications – Recreate a leading edge research and education network capability – Transfer new capabilities to the global production Internet
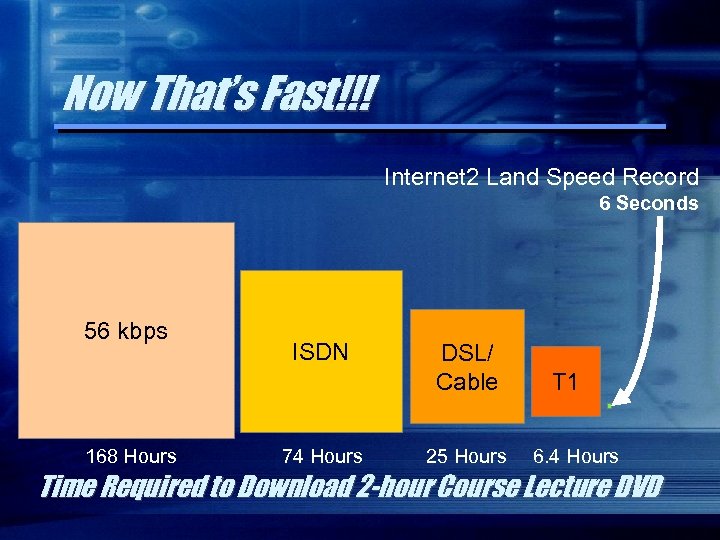
Now That’s Fast!!! Internet 2 Land Speed Record 6 Seconds 56 kbps 168 Hours ISDN 74 Hours DSL/ Cable 25 Hours T 1 6. 4 Hours Time Required to Download 2 -hour Course Lecture DVD

Sea Change in R&E Impacting Networking Needs • Growing urgency for new network technologies • Increased collaboration worldwide on "Big” Science projects • Exponential growth in size of data sets being accessed (High Energy Physics) • Need for multiple dedicated/private research networks

The National Lambda. Rail (NLR) • A major initiative of U. S. research universities and private sector technology companies to provide a national scale infrastructure for research and experimentation in networking technologies and applications. – Focus is on ownership and control of infrastructure

Participation in the NLR will: • Move Oklahoma to the forefront in advanced network initiatives • Position Oklahoma Universities on an equal footing • Facilitate creation of new technologies and markets • Provide robust technical support services

National Lambda. Rail Members and Associates • • • CENIC Pacific Northwest Gigapop Pittsburgh Supercomputing Center/University of Pittsburgh Duke University, representing a coalition of NC universities Mid-Atlantic Terascale Partnership Cisco Systems Internet 2 Florida Lambda. Rail Georgia Institute of Technology • • • Committee on Institutional Cooperation (CIC) Cornell University Louisiana Board of Regents Oklahoma State Regents Lonestar Education and Research Network (LEARN) University of New Mexico (on behalf of the State of New Mexico) UCAR/FRGP SURA Oak Ridge National Lab (ORNL) Case Western Reserve University

One. Net NLR Connection Complete • Infrastructure – Fault-tolerant DWDM connection live March, 2006 • Cisco 15454 Architecture • Same as One. Net’s Core

Differences of I 2 and the NLR • Internet 2 is a large, shared network resource – Difficult to dedicate large capacity to a single user • NLR is architected on a DWDM infrastructure – Capability to guarantee and dedicate specific bandwidth – Maximum of 32 10 Gig. E lambdas • Same architecture as Oklahoma Research Network – 50% of infrastructure is dedicated to network research
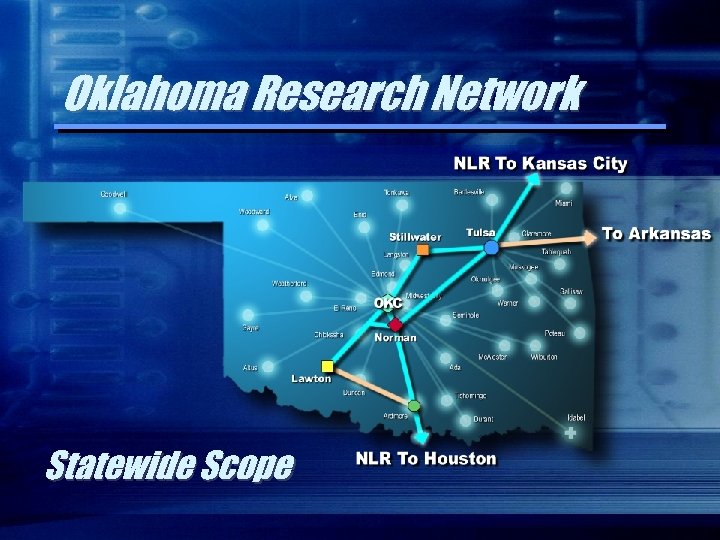
Oklahoma Research Network Statewide Scope

Regional Optical Networks (RONs) Regional Scope

National Lambda. Rail Architecture National Scope
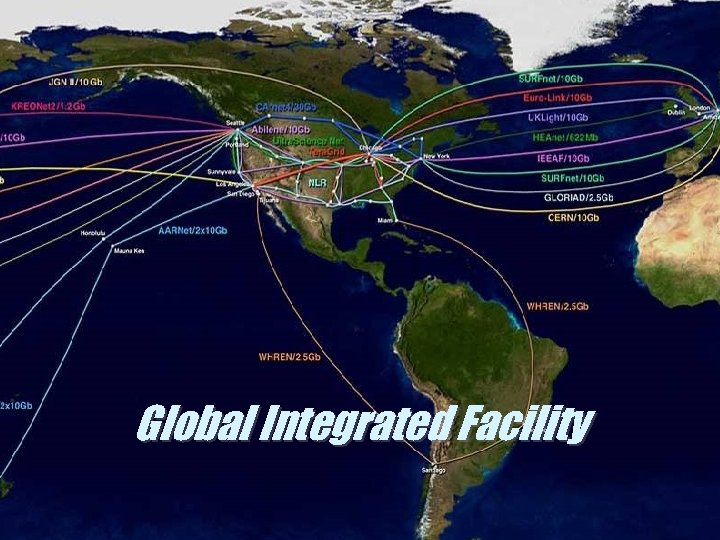
Global Integrated Facility

Other Areas of Interest • Communications Assistance Law Enforcement Act (CALEA) – Recent interpretations of FCC ruling by Educause provide that all institutional networks are exempt • Institutions will, however, cooperate fully on intercepts – No clarity on One. Net as of yet • Net Neutrality – May impact providers’ ability to deliver content • Identity Management – Single sign-on to multiple information resources
b39a6e6305ece0d0b431a20741f8d551.ppt