08808d988c9932a1930e005933bcc204.ppt
- Количество слайдов: 26
 Receipt-freedom in voting Pieter van Ede 1
Receipt-freedom in voting Pieter van Ede 1
 Important properties of voting Authority: only authorized persons can vote One vote Secrecy: nobody may know who voted for which candidate Correctness Verifiability Coercion-free: unable to bride or threaten people to vote for particular candidate Show up checks, useability 2
Important properties of voting Authority: only authorized persons can vote One vote Secrecy: nobody may know who voted for which candidate Correctness Verifiability Coercion-free: unable to bride or threaten people to vote for particular candidate Show up checks, useability 2
 Receipt-freedom Focus of this talk is coercion protection Imagine a threatened or bribed Alice We want to prevent Alice getting a proof of her vote. Called receipt-freedom 3
Receipt-freedom Focus of this talk is coercion protection Imagine a threatened or bribed Alice We want to prevent Alice getting a proof of her vote. Called receipt-freedom 3
 Rise of electronic voting Government wants cheaper voting Also less dependence on honesty of small number of election officials Electronic voting works efficient 4
Rise of electronic voting Government wants cheaper voting Also less dependence on honesty of small number of election officials Electronic voting works efficient 4
 Fall of electronic voting No paper trail, so no recounting (Verifiability) No public verifying of voting software If verified, is THIS machine correct? (Correctness) Is what is printed the same as recorded? In the Netherlands, electronic voting is discontinued 5
Fall of electronic voting No paper trail, so no recounting (Verifiability) No public verifying of voting software If verified, is THIS machine correct? (Correctness) Is what is printed the same as recorded? In the Netherlands, electronic voting is discontinued 5
 Change of mind Do not rely on correctness of machine Rely on cryptographic correctness 6
Change of mind Do not rely on correctness of machine Rely on cryptographic correctness 6
 First idea: paper ballots Idea: Choose candidate on machine Machine prints out ballot Voter verifies and puts in box Advantages: User can simply check for correctness No dependance on programmers or machineintegrity 7
First idea: paper ballots Idea: Choose candidate on machine Machine prints out ballot Voter verifies and puts in box Advantages: User can simply check for correctness No dependance on programmers or machineintegrity 7
 First idea: paper ballots (2) Drawbacks: Still counting of paper (could be done automatically) Transportation of paper ballots Not much use for cryptography No coercion freedom: villain demands photograph 8
First idea: paper ballots (2) Drawbacks: Still counting of paper (could be done automatically) Transportation of paper ballots Not much use for cryptography No coercion freedom: villain demands photograph 8
 Ongoing research Many cryptographic protocols proposed: Mixing: scrambles large batches of votes Blind signatures: require safe publishing channel Homomorphic: sum results and decrypt with secure computing Many not receipt-free 9
Ongoing research Many cryptographic protocols proposed: Mixing: scrambles large batches of votes Blind signatures: require safe publishing channel Homomorphic: sum results and decrypt with secure computing Many not receipt-free 9
 Second idea Give user receipt Use commitment protocol Commitment protocol: 1. User has secret A. 2. User commits to A by computing y=C(A). There is no A' so C(A)=C(A') and y does not reveil a. 3. User opens y to provide it was a commitment to A. 10
Second idea Give user receipt Use commitment protocol Commitment protocol: 1. User has secret A. 2. User commits to A by computing y=C(A). There is no A' so C(A)=C(A') and y does not reveil a. 3. User opens y to provide it was a commitment to A. 10
 Second idea (2) Receipt-free universally verifiable voting protocol with everlasting privacy. By Tal Moran and Moni Naor (Weizmann Institute of Science, Rehovot, Israel) Based on other protocols, in particular Neff's voting Scheme 11
Second idea (2) Receipt-free universally verifiable voting protocol with everlasting privacy. By Tal Moran and Moni Naor (Weizmann Institute of Science, Rehovot, Israel) Based on other protocols, in particular Neff's voting Scheme 11
 Properties of Moran-Naor Everlasting privacy, but not in efficient version (Secrecy) Universally verifiable: everybody interested can verify result (Verifiability) Safe on voting machine running malicious code. Receipt-freedom 12
Properties of Moran-Naor Everlasting privacy, but not in efficient version (Secrecy) Universally verifiable: everybody interested can verify result (Verifiability) Safe on voting machine running malicious code. Receipt-freedom 12
 Assumptions of Moran-Naor One-way untappable channel Achieved by requireing a booth Voter must easily verify machine 13
Assumptions of Moran-Naor One-way untappable channel Achieved by requireing a booth Voter must easily verify machine 13
 Voter perspective Dharma goes to vote Authorizes with election officials Enters the booth 14
Voter perspective Dharma goes to vote Authorizes with election officials Enters the booth 14
 Voter perspective Finds a screen, keyboard and ATMstyle printer Votes for Betty 15
Voter perspective Finds a screen, keyboard and ATMstyle printer Votes for Betty 15
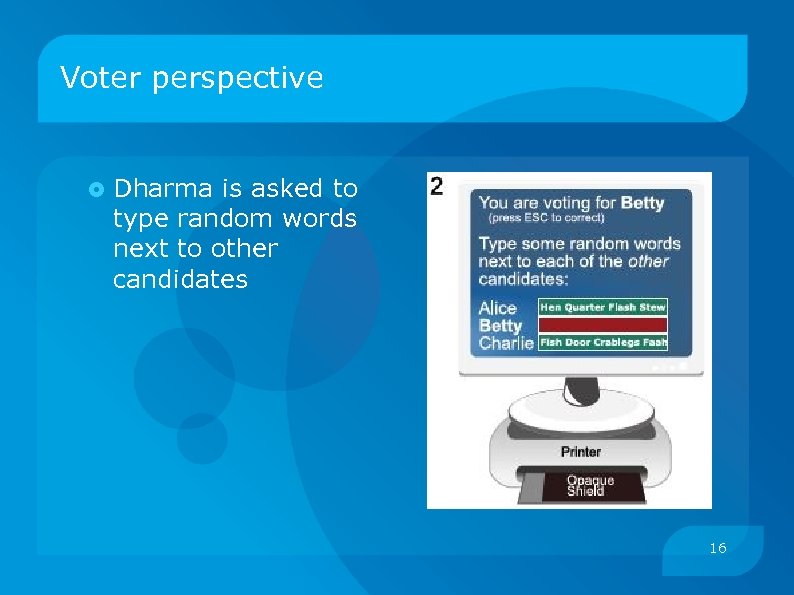 Voter perspective Dharma is asked to type random words next to other candidates 16
Voter perspective Dharma is asked to type random words next to other candidates 16
 Voter perspective Printer prints out 2 lines, the commitment to Betty. Dharma must verify that 2 lines were printed. She does not see what was printed, important for next phase. 17
Voter perspective Printer prints out 2 lines, the commitment to Betty. Dharma must verify that 2 lines were printed. She does not see what was printed, important for next phase. 17
 Voters perspective Dharma is asked to input random words next to Betty. This a challenge, later used in the verifiability, therefore she must not know the commitment statement. 18
Voters perspective Dharma is asked to input random words next to Betty. This a challenge, later used in the verifiability, therefore she must not know the commitment statement. 18
 Voters perspective If all good, press OK. Otherwise, cancel and printout is still worthless. Prints out voter and candidates with random words. 19
Voters perspective If all good, press OK. Otherwise, cancel and printout is still worthless. Prints out voter and candidates with random words. 19
 Voters perspective Dharma chooses OK, machine prints CERTIFIED RECEIPT. Now there is no way back. Receipt also posted on bulletin board. At home, check if receipt is correct on bulletin board. 20
Voters perspective Dharma chooses OK, machine prints CERTIFIED RECEIPT. Now there is no way back. Receipt also posted on bulletin board. At home, check if receipt is correct on bulletin board. 20
 Receipt-freedom of Moran-Naor Coercer Trudy cannot see in what orde the challenges where given. She might however reverse engineer the commitment. Impossible because of commitment scheme 21
Receipt-freedom of Moran-Naor Coercer Trudy cannot see in what orde the challenges where given. She might however reverse engineer the commitment. Impossible because of commitment scheme 21
 Pedersen commitment scheme Moran-Naor use Pedersen commitments in the efficient scheme Based on the hardness of discrete logarithm 22
Pedersen commitment scheme Moran-Naor use Pedersen commitments in the efficient scheme Based on the hardness of discrete logarithm 22
 Pedersen commitment scheme (2) Computations in Zq 1. Machine commits to secret A. 2. Computes y=P(A, r) (r is random) 3. P(A, r) = h. H(A)gr (h, g of order q; H collision free hash function) 4. Verifies that y is commitment of A, by sending (A, r). Only done in context of zero knowledge proof for verifiable counting, so this is safe. Due to random r, commitment never shows secret A to Trudy. 23
Pedersen commitment scheme (2) Computations in Zq 1. Machine commits to secret A. 2. Computes y=P(A, r) (r is random) 3. P(A, r) = h. H(A)gr (h, g of order q; H collision free hash function) 4. Verifies that y is commitment of A, by sending (A, r). Only done in context of zero knowledge proof for verifiable counting, so this is safe. Due to random r, commitment never shows secret A to Trudy. 23
 Pedersen commitment scheme (3) No A' and r' so P(A', r)=y, because that implies: HA'gr' = hagr h. A' – A = gr – r' r-r' / A'-A = Log h g But we assumed discrete logarithms were hard, so infeasible to do. 24
Pedersen commitment scheme (3) No A' and r' so P(A', r)=y, because that implies: HA'gr' = hagr h. A' – A = gr – r' r-r' / A'-A = Log h g But we assumed discrete logarithms were hard, so infeasible to do. 24
 One step further: Cybervote Project of European Commission Vote via mobile phone or internet All cryptography for nothing: • Pressure from father • Or friends at bar Could be fixed by allowing changing of votes, but does that work after a night at the bar? 25
One step further: Cybervote Project of European Commission Vote via mobile phone or internet All cryptography for nothing: • Pressure from father • Or friends at bar Could be fixed by allowing changing of votes, but does that work after a night at the bar? 25
 Conclusion Advantages: Receipt-freedom Many other nice properties of voting satisfied Feasible Disadvantages: Users must trust mathematicians Coercion by bluffing about commitment Still a lot more work then paper voting Difficult for visually disabled Difficult for older people to use bulletin 26
Conclusion Advantages: Receipt-freedom Many other nice properties of voting satisfied Feasible Disadvantages: Users must trust mathematicians Coercion by bluffing about commitment Still a lot more work then paper voting Difficult for visually disabled Difficult for older people to use bulletin 26


