f9d9c604f5cbe711a6da7fafa548dfb5.ppt
- Количество слайдов: 29
Real Life Information Security Bringing cost-benefit analysis into risk management OWASP Copyright © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http: //www. owasp. org

Hewitt Associates 4 Human Resources Outsourcing 4~25’ 000 employees worldwide 4 Highly sensitive clients’ data OWASP 2

HRO Market 4 Not purely financial 4 Mostly B 2 B 4 Highly competitive § Stay flexible OWASP 3

Shepherds or policemen? 4 Very high pressure from business 4 No „one size fits all” approach 4 Lessons learnt § Talk to business § Have real arguments § Talk business 4 Where do all these numbers come from? OWASP 4
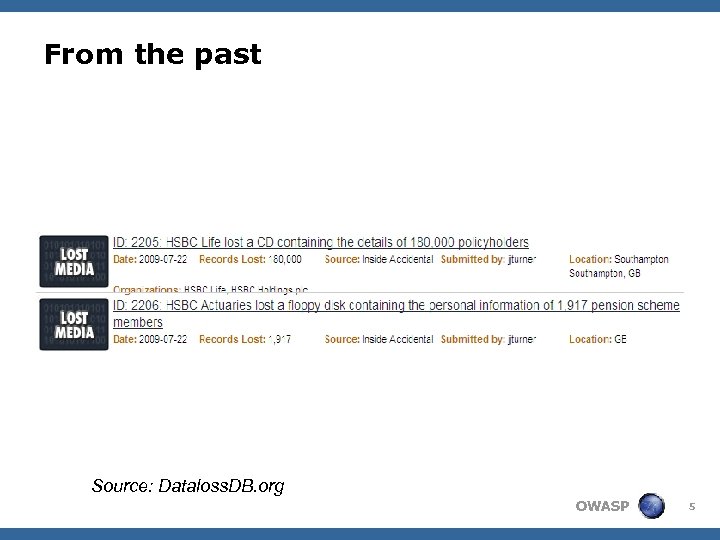
From the past Source: Dataloss. DB. org OWASP 5

From market analytics 4~$100 USD per record 4 No actual abuse required 4„Losing control” is the bad word 4 How much to spend and where to stop? Source: Ponemon Institute, „ 2008 Annual Study: Cost of Data Breach” OWASP 6
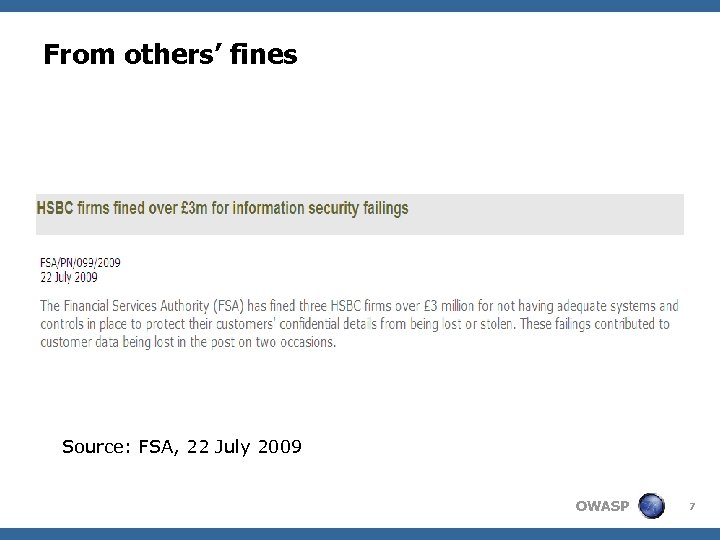
From others’ fines Source: FSA, 22 July 2009 OWASP 7

From Risk Analysis <Risk = Potential Loss * Threat Probability <Potential Loss ~ Asset Cost, Brand Value. . . OWASP 8

When Risk Analysis makes sense? Control Cost << Asset Cost Source: Flickr (edouаrd) OWASP 9

What makes Control cost? 4 Roll-out cost § Obvious 4 Change cost § Not so obvious 4 Management cost § Not so obvious 4 End-user usage cost § Largely ignored § Especially if outside Source: Flickr (dаveme) OWASP 10
Potential loss → Control → Real loss OWASP 11

Case studies OWASP 12
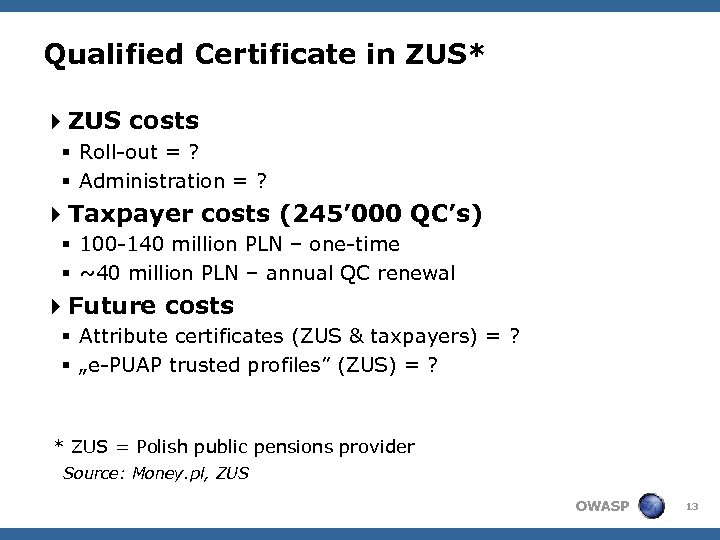
Qualified Certificate in ZUS* 4 ZUS costs § Roll-out = ? § Administration = ? 4 Taxpayer costs (245’ 000 QC’s) § 100 -140 million PLN – one-time § ~40 million PLN – annual QC renewal 4 Future costs § Attribute certificates (ZUS & taxpayers) = ? § „e-PUAP trusted profiles” (ZUS) = ? * ZUS = Polish public pensions provider Source: Money. pl, ZUS OWASP 13
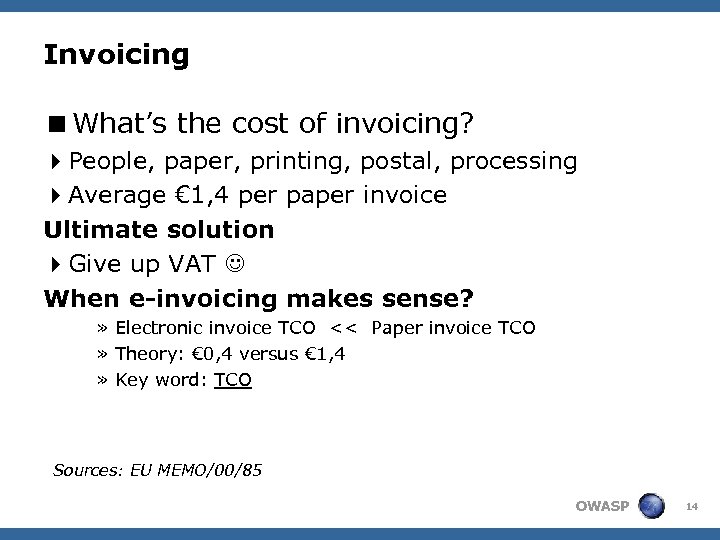
Invoicing <What’s the cost of invoicing? 4 People, paper, printing, postal, processing 4 Average € 1, 4 per paper invoice Ultimate solution 4 Give up VAT When e-invoicing makes sense? » Electronic invoice TCO << Paper invoice TCO » Theory: € 0, 4 versus € 1, 4 » Key word: TCO Sources: EU MEMO/00/85 OWASP 14
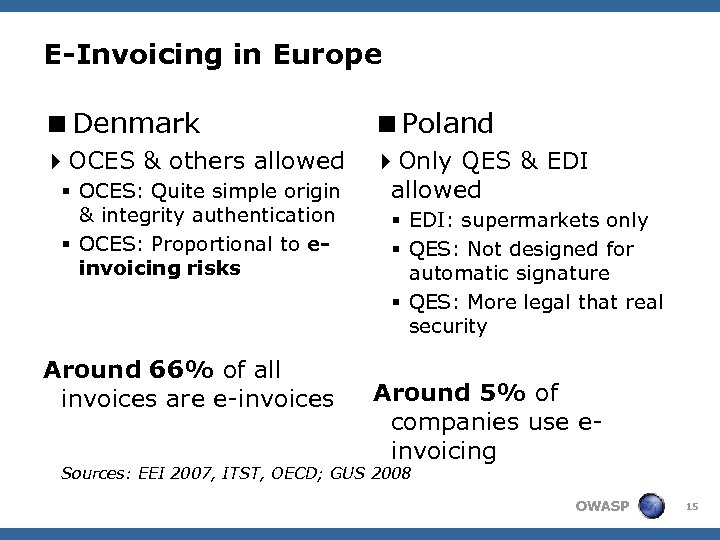
E-Invoicing in Europe <Denmark <Poland 4 OCES & others allowed 4 Only QES & EDI allowed § OCES: Quite simple origin & integrity authentication § OCES: Proportional to einvoicing risks Around 66% of all invoices are e-invoices § EDI: supermarkets only § QES: Not designed for automatic signature § QES: More legal that real security Around 5% of companies use einvoicing Sources: EEI 2007, ITST, OECD; GUS 2008 OWASP 15
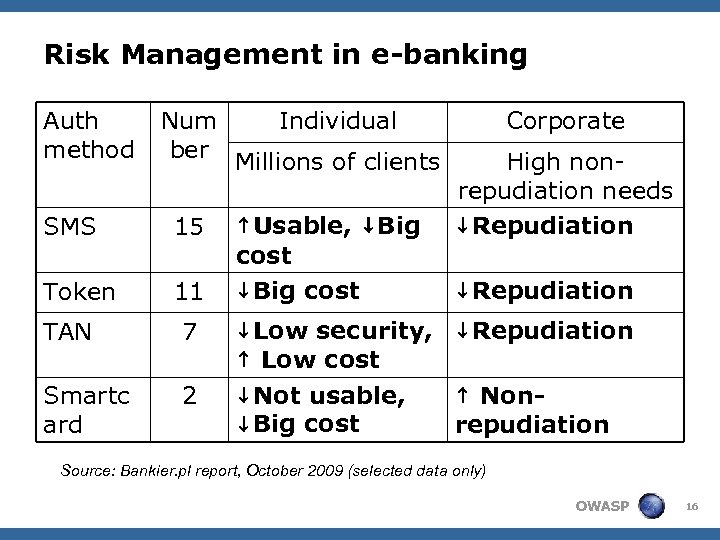
Risk Management in e-banking Auth method Num Individual ber Millions of clients SMS 15 Token 11 ↑Usable, ↓Big cost Corporate High nonrepudiation needs ↓Repudiation TAN 7 ↓Low security, ↓Repudiation ↑ Low cost Smartc ard 2 ↓Not usable, ↓Big cost ↑ Nonrepudiation Source: Bankier. pl report, October 2009 (selected data only) OWASP 16
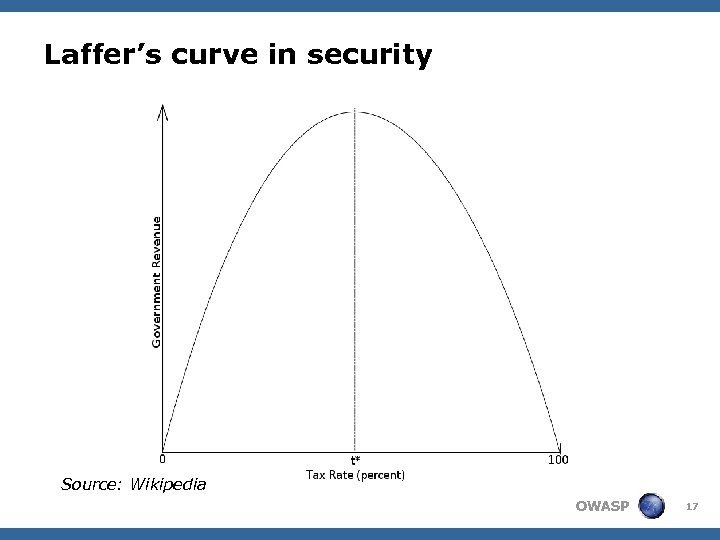
Laffer’s curve in security Source: Wikipedia OWASP 17
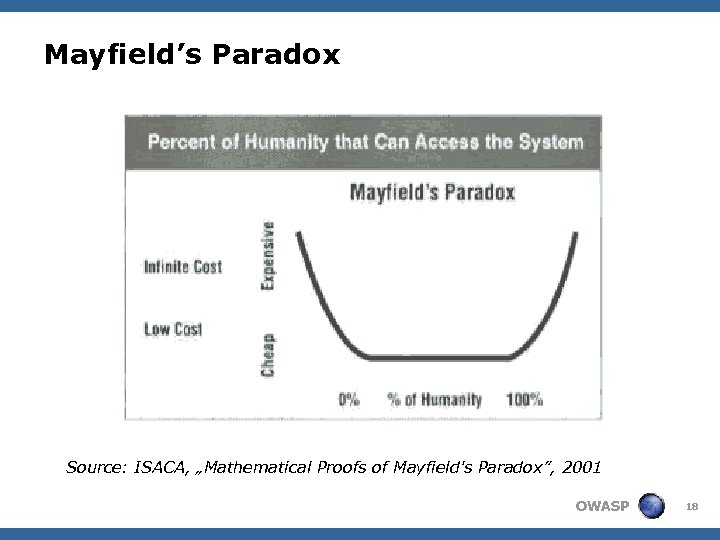
Mayfield’s Paradox Source: ISACA, „Mathematical Proofs of Mayfield's Paradox”, 2001 OWASP 18
How to? OWASP 19
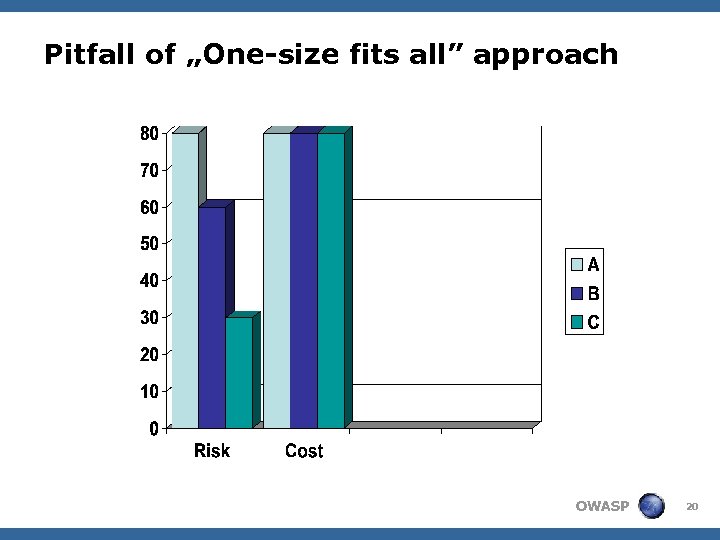
Pitfall of „One-size fits all” approach OWASP 20
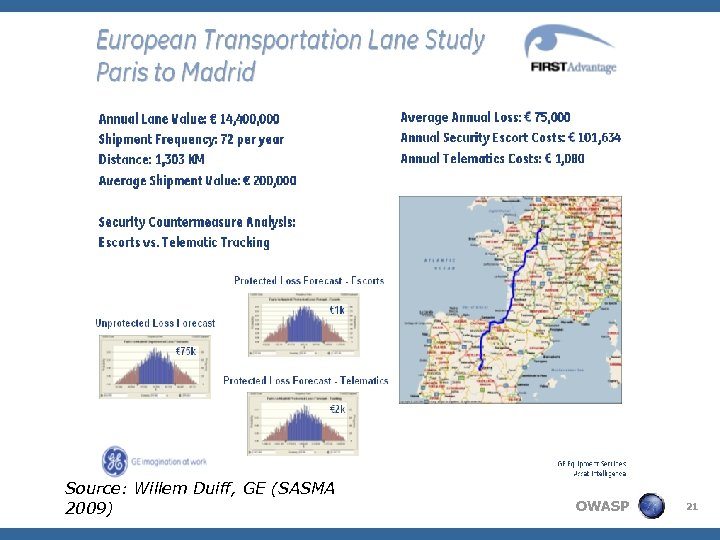
Source: Willem Duiff, GE (SASMA 2009) OWASP 21

Control questions Before deploying a new solution 4 Do my controls help, instead of breaking process? 4 How do my controls help business do its work? Before asking for new funding 4 What we earned on last project? OWASP 22

Is security a cost? Security is an investment to prevent losses 4 Spend $100 k to prevent losing $1 m = 10 x benefit 4 NOT: „Security again spent $100 k” 4 YES: „Security helped save $1 M for just $100 k” OWASP 23
How FDE saves money 4 Office break-in 4 Four laptops stolen 4 All with full-disk encryption 4 Cost of incident – zero § Hardware – insurance § Data confidentality – able to prove to client § Data availability – backups & network drives 4 Where’s ROI of FDE? § No $$$ in fines § No $$ in breach notification § No $? in brand damage OWASP 24

Building a consistent security policy #1 4 Should people should take their laptops home? § Isn’t that increasing risk of theft? 4 Laptop theft § Lose laptop ($) § Lose data ($$$) Source: Flickr (аresnick) OWASP 25

Building a consistent security policy #2 4 Laptop at home 4 Work from home § Disaster recovery, business continuity § Examples: UK snow (2009), London flood (2009), Hemel Hempstead explosion (2005) 4 Need to prevent the other risks Source: Wikipedia OWASP 26

Building a consistent security policy #3 4 End-user message § „Always take your laptop home” 4 FDE is standard, non-optional proces OWASP 27
Things we learned when talking to bussiness <Avoid „weasel talk” and buzzwords 4„Some attacks exist that might pose a significant risk. . . ” Use as much facts and numbers as possible 4 Do use industry reports 4 Be careful with vendor reports § „How spam filtering helps preventing global warming” 4 Filter them through your company’s reality check 4 Learn from historic incidents in your organisation Perform periodic review of your controls 4 Make sure at the old threat is still there 4 Make sure no new threats appeared OWASP 28
Questions? <Questions, comments <PAWEL. KRAWCZYK@HEWITT. COM <http: //www. linkedin. com/in/pawelkrawczyk OWASP 29
f9d9c604f5cbe711a6da7fafa548dfb5.ppt