 Reading CSCE 522 - Farkas 2
Reading CSCE 522 - Farkas 2
 Program Flaws CSCE 522 - Farkas 3
Program Flaws CSCE 522 - Farkas 3
 Security Flaws by Genesis CSCE 522 - Farkas 4
Security Flaws by Genesis CSCE 522 - Farkas 4
 Secure Software CSCE 522 - Farkas 5
Secure Software CSCE 522 - Farkas 5
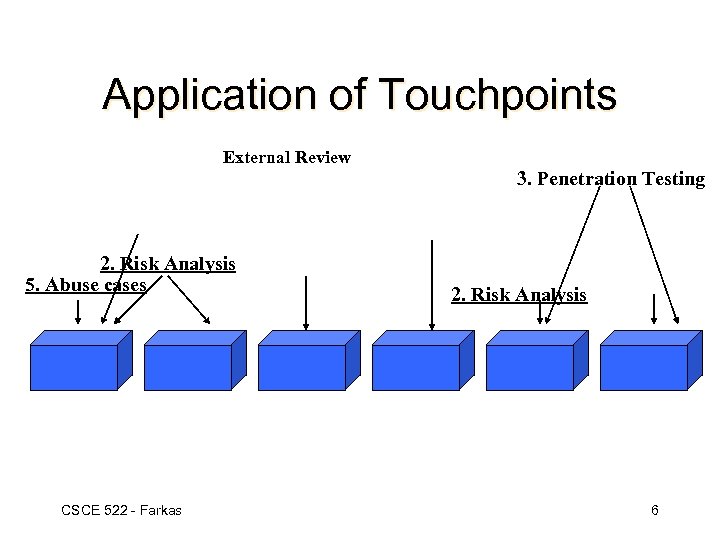 Application of Touchpoints External Review 3. Penetration Testing 2. Risk Analysis 5. Abuse cases CSCE 522 - Farkas 2. Risk Analysis 6
Application of Touchpoints External Review 3. Penetration Testing 2. Risk Analysis 5. Abuse cases CSCE 522 - Farkas 2. Risk Analysis 6
 Web Applications CSCE 522 - Farkas 7
Web Applications CSCE 522 - Farkas 7
 OWASP Top 10 2013 Vulnerabilities CSCE 522 - Farkas 8
OWASP Top 10 2013 Vulnerabilities CSCE 522 - Farkas 8
 Malware CSCE 522 - Farkas
Malware CSCE 522 - Farkas
 Kinds of Malicious Codes CSCE 522 - Farkas 10
Kinds of Malicious Codes CSCE 522 - Farkas 10
 Kinds of Malicious Code CSCE 522 - Farkas 11
Kinds of Malicious Code CSCE 522 - Farkas 11
 Kinds of Malicious Code CSCE 522 - Farkas 12
Kinds of Malicious Code CSCE 522 - Farkas 12
 Virus CSCE 522 - Farkas 13
Virus CSCE 522 - Farkas 13
 Virus Types CSCE 522 - Farkas 14
Virus Types CSCE 522 - Farkas 14
 Virus Types CSCE 522 - Farkas 15
Virus Types CSCE 522 - Farkas 15
 Virus Types CSCE 522 - Farkas 16
Virus Types CSCE 522 - Farkas 16
 How Viruses Append CSCE 522 - Farkas 17
How Viruses Append CSCE 522 - Farkas 17
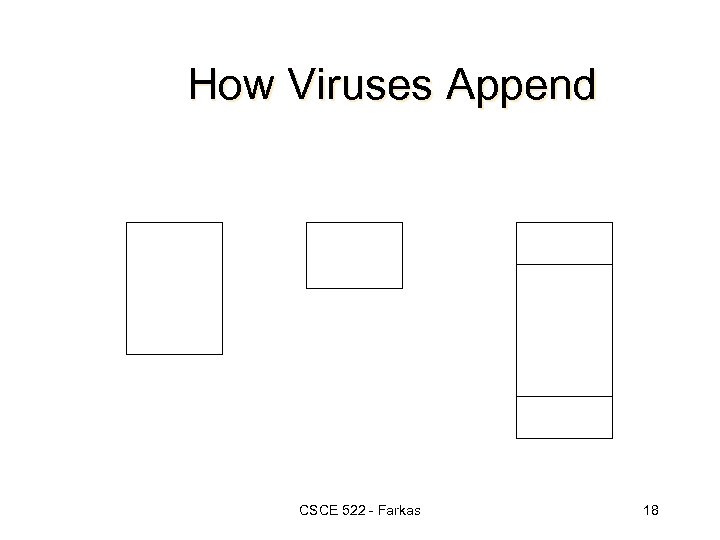 How Viruses Append CSCE 522 - Farkas 18
How Viruses Append CSCE 522 - Farkas 18
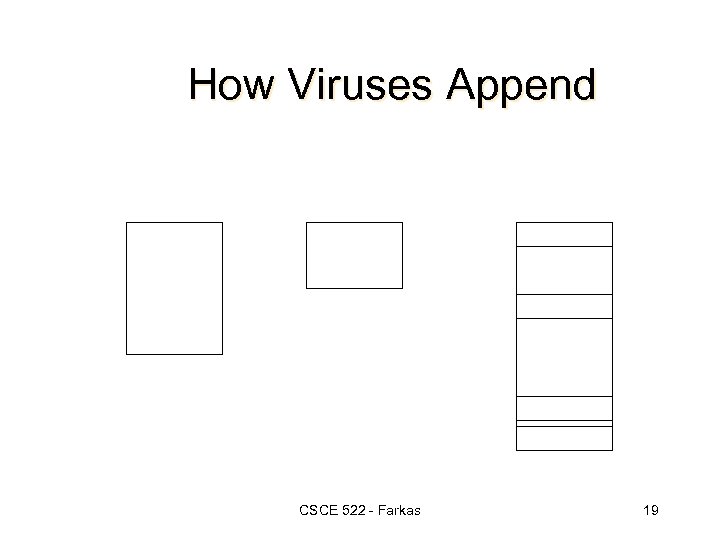 How Viruses Append CSCE 522 - Farkas 19
How Viruses Append CSCE 522 - Farkas 19
 How Viruses Gain Control CSCE 522 - Farkas 20
How Viruses Gain Control CSCE 522 - Farkas 20
 Antivirus Approaches CSCE 522 - Farkas 21
Antivirus Approaches CSCE 522 - Farkas 21
 Preventing Virus Infection CSCE 522 - Farkas 22
Preventing Virus Infection CSCE 522 - Farkas 22
 Virus Detection 1. CSCE 522 - Farkas 23
Virus Detection 1. CSCE 522 - Farkas 23
 Virus Detection 2. CSCE 522 - Farkas 24
Virus Detection 2. CSCE 522 - Farkas 24
 Worm CSCE 522 - Farkas 25
Worm CSCE 522 - Farkas 25
 Adware and Spyware CSCE 522 - Farkas 26
Adware and Spyware CSCE 522 - Farkas 26
 Scareware CSCE 522 - Farkas 27
Scareware CSCE 522 - Farkas 27
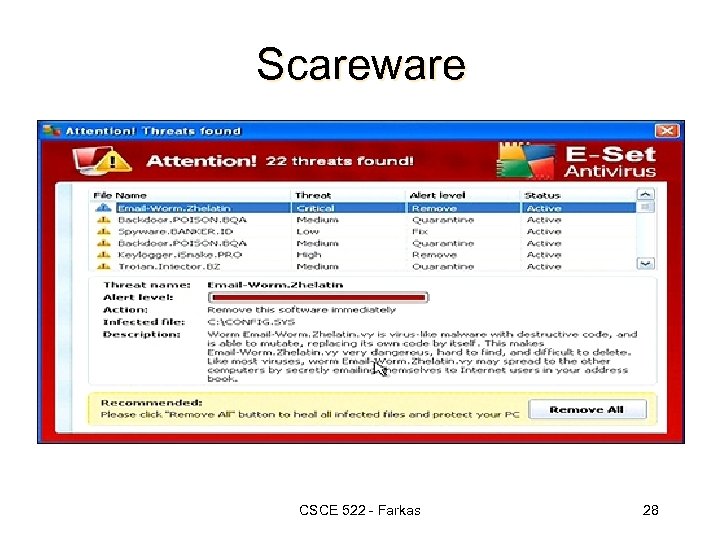 Scareware CSCE 522 - Farkas 28
Scareware CSCE 522 - Farkas 28
 Ransomware CSCE 522 - Farkas 29
Ransomware CSCE 522 - Farkas 29
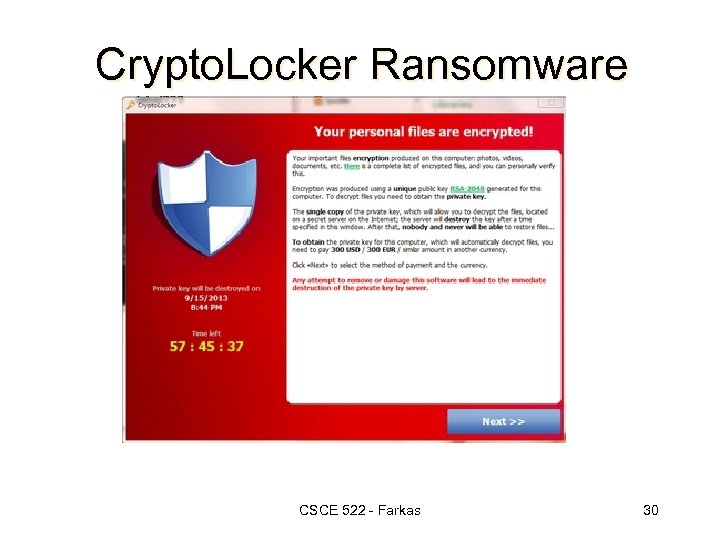 Crypto. Locker Ransomware CSCE 522 - Farkas 30
Crypto. Locker Ransomware CSCE 522 - Farkas 30
 Next Class CSCE 522 - Farkas 31
Next Class CSCE 522 - Farkas 31