8b7040c34f175f2894d60c2079274667.ppt
- Количество слайдов: 40

 Raymond K. Ng Technical Lead - JAAS Platform Security Oracle Corporation
Raymond K. Ng Technical Lead - JAAS Platform Security Oracle Corporation
 Securing J 2 EE Applications with Oracle Identity Management
Securing J 2 EE Applications with Oracle Identity Management
 Agenda Ÿ Application Security Overview Ÿ Authentication Requirements Ÿ Authorization Requirements Ÿ J 2 EE Security Ÿ JAAS Ÿ Oracle Strategy
Agenda Ÿ Application Security Overview Ÿ Authentication Requirements Ÿ Authorization Requirements Ÿ J 2 EE Security Ÿ JAAS Ÿ Oracle Strategy
 Application Security Ÿ Security is a process, not a product or feature – No 100% security Ÿ Only as secure as weakest link – – Go beyond firewall security Implement multi-layer security Ÿ Considerations – – Authentication Authorization Accountability/Audit Secure Transport
Application Security Ÿ Security is a process, not a product or feature – No 100% security Ÿ Only as secure as weakest link – – Go beyond firewall security Implement multi-layer security Ÿ Considerations – – Authentication Authorization Accountability/Audit Secure Transport
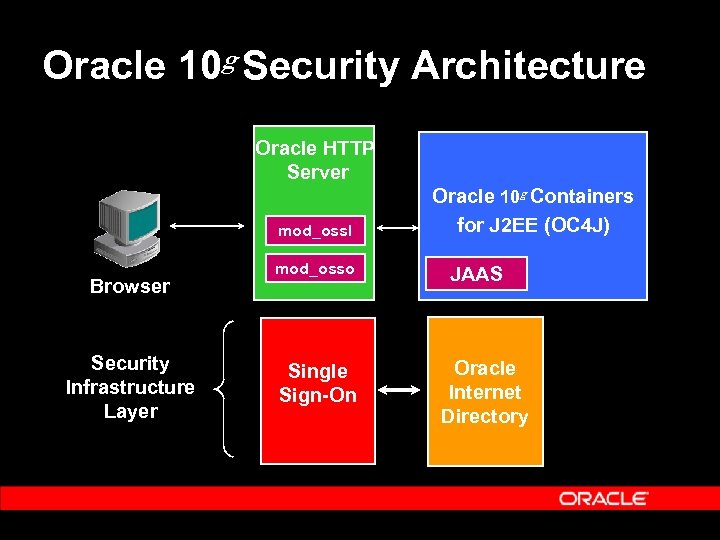 Oracle 10 g Security Architecture Oracle HTTP Server mod_ossl Browser Security Infrastructure Layer mod_osso Single Sign-On Oracle 10 g Containers for J 2 EE (OC 4 J) JAAS Oracle Internet Directory
Oracle 10 g Security Architecture Oracle HTTP Server mod_ossl Browser Security Infrastructure Layer mod_osso Single Sign-On Oracle 10 g Containers for J 2 EE (OC 4 J) JAAS Oracle Internet Directory
 Authentication Requirements
Authentication Requirements
 Use The Appropriate Mechanism Ÿ Username and password Ÿ Client certificate Ÿ Smart Card Ÿ Biometrics
Use The Appropriate Mechanism Ÿ Username and password Ÿ Client certificate Ÿ Smart Card Ÿ Biometrics
 Single Sign-On (SSO) Ÿ Why SSO-enable your application? – – – User Convenience Security Cost Reduction Ÿ Factors to consider – – Integration with infrastructure Extensible framework
Single Sign-On (SSO) Ÿ Why SSO-enable your application? – – – User Convenience Security Cost Reduction Ÿ Factors to consider – – Integration with infrastructure Extensible framework
 Oracle 10 g Single Sign-On Ÿ Centralized authentication for web applications Ÿ Multiple authentication options – – – Username/password Client certificates 3 rd party API (Biometrics, Smart Card, etc. ) Ÿ Single Sign-Off Ÿ Multiple application types Ÿ Integrated across Oracle 10 g – OID, OC 4 J/JAAS , Portal, OHS, Wireless, Workflow, UM, Ultrasearch, Personalization, Reports, Forms, Discoverer…
Oracle 10 g Single Sign-On Ÿ Centralized authentication for web applications Ÿ Multiple authentication options – – – Username/password Client certificates 3 rd party API (Biometrics, Smart Card, etc. ) Ÿ Single Sign-Off Ÿ Multiple application types Ÿ Integrated across Oracle 10 g – OID, OC 4 J/JAAS , Portal, OHS, Wireless, Workflow, UM, Ultrasearch, Personalization, Reports, Forms, Discoverer…
 Relevant Standards Ÿ HTTP Ÿ SSL/X. 509 Ÿ J 2 EE Ÿ JAAS Ÿ Java Authentication SPI Ÿ SAML Ÿ WS-Security Ÿ Plus emerging specifications
Relevant Standards Ÿ HTTP Ÿ SSL/X. 509 Ÿ J 2 EE Ÿ JAAS Ÿ Java Authentication SPI Ÿ SAML Ÿ WS-Security Ÿ Plus emerging specifications
 Authorization Requirements
Authorization Requirements
 Choose The Right Authorization Model Ÿ Roll Your Own (Application-specific) – – – Maintenance Administrative Cost Inconsistent Authorization Policy => Insecurity Ÿ Understand The Relevant Standards – – J 2 EE Security Java 2 Security JAAS JACC
Choose The Right Authorization Model Ÿ Roll Your Own (Application-specific) – – – Maintenance Administrative Cost Inconsistent Authorization Policy => Insecurity Ÿ Understand The Relevant Standards – – J 2 EE Security Java 2 Security JAAS JACC
 J 2 EE Security
J 2 EE Security
 J 2 EE Security Ÿ Design Principles – – Declarative security model ŸDecouple security logic from application logic ŸWrite once run anywhere (WORA) Leverage existing security infrastructure Ÿ J 2 EE Roles – – Application Provider Application Assembler Application Deployer System Administrator
J 2 EE Security Ÿ Design Principles – – Declarative security model ŸDecouple security logic from application logic ŸWrite once run anywhere (WORA) Leverage existing security infrastructure Ÿ J 2 EE Roles – – Application Provider Application Assembler Application Deployer System Administrator
 J 2 EE Security: Authentication Ÿ Multiple Authentication Methods - Basic, Form, SSL client certificate, etc. Ÿ Declarative Security – Deployment descriptors: web. xml, ejb-jar. xml Ÿ JSR 196: Java Authentication SPI – – J 2 EE 1. 5 JAAS Login. Module integration Ÿ Missing – Single Sign-On support
J 2 EE Security: Authentication Ÿ Multiple Authentication Methods - Basic, Form, SSL client certificate, etc. Ÿ Declarative Security – Deployment descriptors: web. xml, ejb-jar. xml Ÿ JSR 196: Java Authentication SPI – – J 2 EE 1. 5 JAAS Login. Module integration Ÿ Missing – Single Sign-On support
 J 2 EE Security: Authorization Ÿ Protected Resources – – Web Resources: URL-patterns Enterprise Beans: Method permissions Ÿ “Role”-based Authorization – – Not “Role Based Access Control (RBAC)” Portability Ÿ JSR 115: Integration with Java 2/JAAS – – Pluggable security (authorization) provider J 2 EE security constraints => Java 2 permissions
J 2 EE Security: Authorization Ÿ Protected Resources – – Web Resources: URL-patterns Enterprise Beans: Method permissions Ÿ “Role”-based Authorization – – Not “Role Based Access Control (RBAC)” Portability Ÿ JSR 115: Integration with Java 2/JAAS – – Pluggable security (authorization) provider J 2 EE security constraints => Java 2 permissions
 JAAS: Java Authentication and Authorization Service
JAAS: Java Authentication and Authorization Service
 Java 2 Security Ÿ Key Components – – Security Policy defines authorization policy Security. Manager/Access. Controller is security monitor Ÿ Necessary if running any untrusted code in your JVM Ÿ Limitations – – – Code-based security only No policy management API File-based implementation doesn’t scale
Java 2 Security Ÿ Key Components – – Security Policy defines authorization policy Security. Manager/Access. Controller is security monitor Ÿ Necessary if running any untrusted code in your JVM Ÿ Limitations – – – Code-based security only No policy management API File-based implementation doesn’t scale
 What is JAAS? Ÿ Principal-Based security Ÿ Authentication – Pluggable Authentication Module (PAM) framework Ÿ Authorization – Extension to Java 2 Security Model Ÿ Optional Package to JDK 1. 3 – JDK 1. 4 Core API Ÿ J 2 EE 1. 3 Requirement – – J 2 EE 1. 4: JACC (JSR 115) J 2 EE 1. 5: Java Authentication SPI (JSR 196)
What is JAAS? Ÿ Principal-Based security Ÿ Authentication – Pluggable Authentication Module (PAM) framework Ÿ Authorization – Extension to Java 2 Security Model Ÿ Optional Package to JDK 1. 3 – JDK 1. 4 Core API Ÿ J 2 EE 1. 3 Requirement – – J 2 EE 1. 4: JACC (JSR 115) J 2 EE 1. 5: Java Authentication SPI (JSR 196)
 Oracle 10 g JAAS Provider Ÿ Oracle’s JAAS (Java Authentication and Authorization Services) Implementation, plus Extensions Ÿ Integrated with Oracle 10 g SSO and OID Ÿ Default Security Provider for Oracle 10 g Containers for J 2 EE
Oracle 10 g JAAS Provider Ÿ Oracle’s JAAS (Java Authentication and Authorization Services) Implementation, plus Extensions Ÿ Integrated with Oracle 10 g SSO and OID Ÿ Default Security Provider for Oracle 10 g Containers for J 2 EE
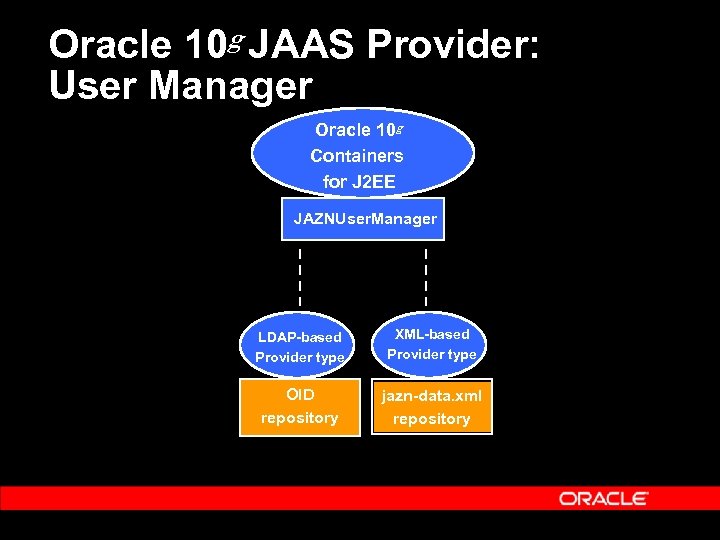 Oracle 10 g JAAS Provider: User Manager Oracle 10 g Containers for J 2 EE JAZNUser. Manager LDAP-based Provider type XML-based Provider type OID repository jazn-data. xml repository
Oracle 10 g JAAS Provider: User Manager Oracle 10 g Containers for J 2 EE JAZNUser. Manager LDAP-based Provider type XML-based Provider type OID repository jazn-data. xml repository
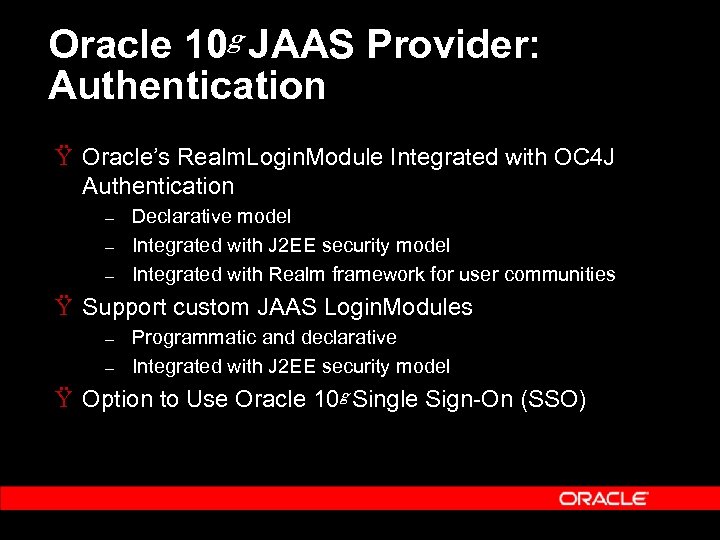 Oracle 10 g JAAS Provider: Authentication Ÿ Oracle’s Realm. Login. Module Integrated with OC 4 J Authentication – – – Declarative model Integrated with J 2 EE security model Integrated with Realm framework for user communities Ÿ Support custom JAAS Login. Modules – – Programmatic and declarative Integrated with J 2 EE security model Ÿ Option to Use Oracle 10 g Single Sign-On (SSO)
Oracle 10 g JAAS Provider: Authentication Ÿ Oracle’s Realm. Login. Module Integrated with OC 4 J Authentication – – – Declarative model Integrated with J 2 EE security model Integrated with Realm framework for user communities Ÿ Support custom JAAS Login. Modules – – Programmatic and declarative Integrated with J 2 EE security model Ÿ Option to Use Oracle 10 g Single Sign-On (SSO)
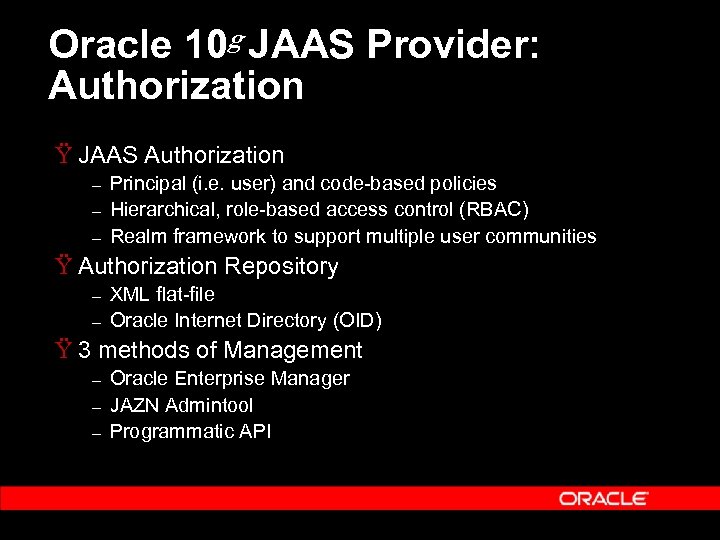 Oracle 10 g JAAS Provider: Authorization Ÿ JAAS Authorization – – – Principal (i. e. user) and code-based policies Hierarchical, role-based access control (RBAC) Realm framework to support multiple user communities Ÿ Authorization Repository – – XML flat-file Oracle Internet Directory (OID) Ÿ 3 methods of Management – – – Oracle Enterprise Manager JAZN Admintool Programmatic API
Oracle 10 g JAAS Provider: Authorization Ÿ JAAS Authorization – – – Principal (i. e. user) and code-based policies Hierarchical, role-based access control (RBAC) Realm framework to support multiple user communities Ÿ Authorization Repository – – XML flat-file Oracle Internet Directory (OID) Ÿ 3 methods of Management – – – Oracle Enterprise Manager JAZN Admintool Programmatic API
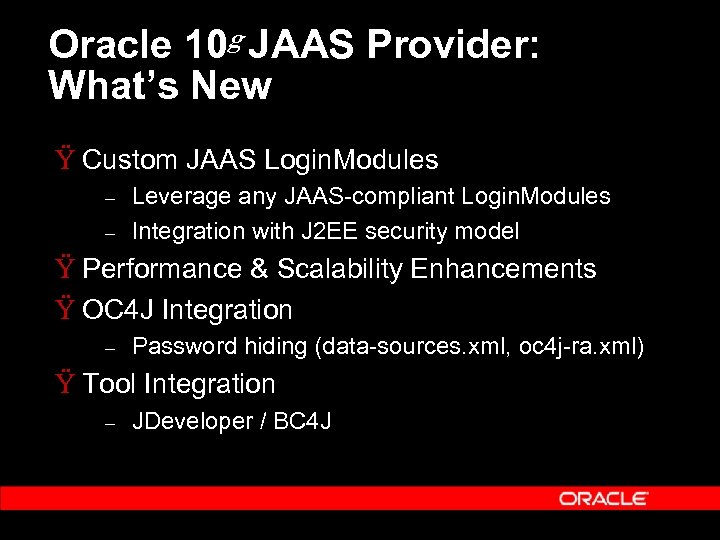 Oracle 10 g JAAS Provider: What’s New Ÿ Custom JAAS Login. Modules – – Leverage any JAAS-compliant Login. Modules Integration with J 2 EE security model Ÿ Performance & Scalability Enhancements Ÿ OC 4 J Integration – Password hiding (data-sources. xml, oc 4 j-ra. xml) Ÿ Tool Integration – JDeveloper / BC 4 J
Oracle 10 g JAAS Provider: What’s New Ÿ Custom JAAS Login. Modules – – Leverage any JAAS-compliant Login. Modules Integration with J 2 EE security model Ÿ Performance & Scalability Enhancements Ÿ OC 4 J Integration – Password hiding (data-sources. xml, oc 4 j-ra. xml) Ÿ Tool Integration – JDeveloper / BC 4 J
 Oracle 10 g JAAS Provider: Future Directions Ÿ Support for 3 rd party LDAP directories – Default Login. Module certified against AD and Sun. ONE Ÿ JACC Provider (JSR 115) – Unified authorization model for managed components Ÿ Java Authentication SPI (JSR 196) – Unified authentication model for managed components Ÿ Portlet Integration (JSR 168) – J 2 EE/JAAS authorization model for portlets Ÿ Management & Deployment Enhancements – JSR 77 & 88 Ÿ XML Services Security Ÿ Web Services Security
Oracle 10 g JAAS Provider: Future Directions Ÿ Support for 3 rd party LDAP directories – Default Login. Module certified against AD and Sun. ONE Ÿ JACC Provider (JSR 115) – Unified authorization model for managed components Ÿ Java Authentication SPI (JSR 196) – Unified authentication model for managed components Ÿ Portlet Integration (JSR 168) – J 2 EE/JAAS authorization model for portlets Ÿ Management & Deployment Enhancements – JSR 77 & 88 Ÿ XML Services Security Ÿ Web Services Security
 JAAS Up Your J 2 EE Apps
JAAS Up Your J 2 EE Apps
 JAAS Up your J 2 EE Apps: Putting the Pieces Together Ÿ Define your security policy – Enterprise policy: Ÿrole hierarchy Ÿuser->role assignment Ÿpermission->role assignment – Application-specific policy: Ÿauthentication method Ÿauthorization constraints (“security-roles”) Ÿ Deploy your J 2 EE Application – – – authentication method authorization constraints (“security-role-mappings”) Run. As identity
JAAS Up your J 2 EE Apps: Putting the Pieces Together Ÿ Define your security policy – Enterprise policy: Ÿrole hierarchy Ÿuser->role assignment Ÿpermission->role assignment – Application-specific policy: Ÿauthentication method Ÿauthorization constraints (“security-roles”) Ÿ Deploy your J 2 EE Application – – – authentication method authorization constraints (“security-role-mappings”) Run. As identity
 JAAS Up Your J 2 EE Apps: SSO-enabling your J 2 EE Apps Ÿ Specify static declarative constraints – in web. xml or ejb-jar. xml Ÿ Deploy your J 2 EE applications – – specify JAZN-LDAP User. Manager security-role mappings Ÿ OID realms, users and groups Ÿ Specify authentication method as SSO – in orion-web. xml: Ÿ
JAAS Up Your J 2 EE Apps: SSO-enabling your J 2 EE Apps Ÿ Specify static declarative constraints – in web. xml or ejb-jar. xml Ÿ Deploy your J 2 EE applications – – specify JAZN-LDAP User. Manager security-role mappings Ÿ OID realms, users and groups Ÿ Specify authentication method as SSO – in orion-web. xml: Ÿ
 JAAS Up Your J 2 EE Apps: Custom Login. Module Integration Ÿ Develop, package & deploy your application as usual Ÿ Package & deploy your custom Login. Module – As an independent JAR or as part of your application Ÿ Configure your application – – – Set JAZN property “role. mapping. dynamic” to “true” Set application classpath as appropriate Set security role mapping as appropriate Ÿ Register your custom Login. Module – – Associate your custom Login. Module with your application JAZN Admintool: “-addloginmodule” option
JAAS Up Your J 2 EE Apps: Custom Login. Module Integration Ÿ Develop, package & deploy your application as usual Ÿ Package & deploy your custom Login. Module – As an independent JAR or as part of your application Ÿ Configure your application – – – Set JAZN property “role. mapping. dynamic” to “true” Set application classpath as appropriate Set security role mapping as appropriate Ÿ Register your custom Login. Module – – Associate your custom Login. Module with your application JAZN Admintool: “-addloginmodule” option
 JAAS Up Your J 2 EE Apps: Tips & Tricks Ÿ JAZN-LDAP – – User/group management delegated to DAS grant RMIPermission to user accessing EJBs Ÿ JAZN-LDAP Cache – Tuning parameters: “ldap. cache. *” Ÿ Identity Management Realm – SSO integration Ÿ External Synchronization – Performance vs. Ease-of-development Ÿ Public Group – Authentication only
JAAS Up Your J 2 EE Apps: Tips & Tricks Ÿ JAZN-LDAP – – User/group management delegated to DAS grant RMIPermission to user accessing EJBs Ÿ JAZN-LDAP Cache – Tuning parameters: “ldap. cache. *” Ÿ Identity Management Realm – SSO integration Ÿ External Synchronization – Performance vs. Ease-of-development Ÿ Public Group – Authentication only
 Oracle Strategy
Oracle Strategy
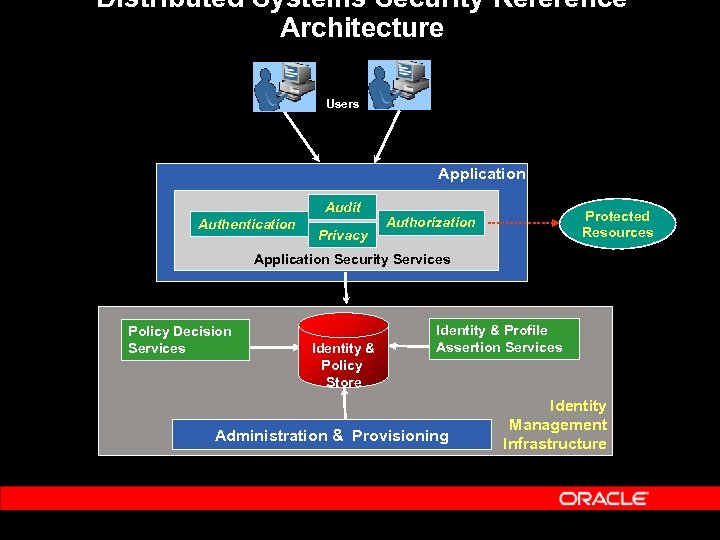 Distributed Systems Security Reference Architecture Users Application Audit Authentication Privacy Protected Resources Authorization Application Security Services Policy Decision Services Identity & Policy Store Identity & Profile Assertion Services Administration & Provisioning Identity Management Infrastructure
Distributed Systems Security Reference Architecture Users Application Audit Authentication Privacy Protected Resources Authorization Application Security Services Policy Decision Services Identity & Policy Store Identity & Profile Assertion Services Administration & Provisioning Identity Management Infrastructure
 Oracle 10 g Security Solution Ÿ Oracle Identity Management Infrastructure for the enterprise Ÿ Platform security enabled by Oracle Identity Management Ÿ Platform components with high security assurance
Oracle 10 g Security Solution Ÿ Oracle Identity Management Infrastructure for the enterprise Ÿ Platform security enabled by Oracle Identity Management Ÿ Platform components with high security assurance
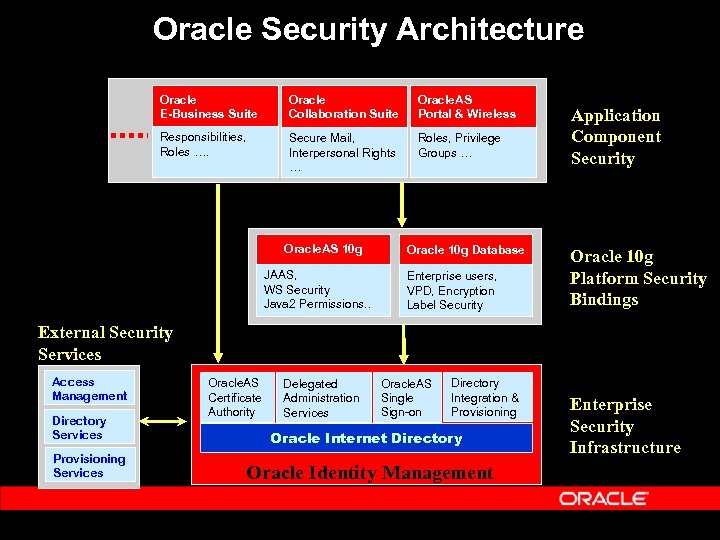 Oracle Security Architecture Oracle E-Business Suite Oracle Collaboration Suite Oracle. AS Portal & Wireless Responsibilities, Roles …. Secure Mail, Interpersonal Rights … Roles, Privilege Groups … Oracle. AS 10 g Oracle 10 g Database JAAS, WS Security Java 2 Permissions. . Enterprise users, VPD, Encryption Label Security Application Component Security Oracle 10 g Platform Security Bindings External Security Services Access Management Directory Services Provisioning Services Oracle. AS Certificate Authority Delegated Administration Services Oracle. AS Single Sign-on Directory Integration & Provisioning Oracle Internet Directory Oracle Identity Management Enterprise Security Infrastructure
Oracle Security Architecture Oracle E-Business Suite Oracle Collaboration Suite Oracle. AS Portal & Wireless Responsibilities, Roles …. Secure Mail, Interpersonal Rights … Roles, Privilege Groups … Oracle. AS 10 g Oracle 10 g Database JAAS, WS Security Java 2 Permissions. . Enterprise users, VPD, Encryption Label Security Application Component Security Oracle 10 g Platform Security Bindings External Security Services Access Management Directory Services Provisioning Services Oracle. AS Certificate Authority Delegated Administration Services Oracle. AS Single Sign-on Directory Integration & Provisioning Oracle Internet Directory Oracle Identity Management Enterprise Security Infrastructure
 Oracle Identity Management Benefits Ÿ Enables deployment of all Oracle products out of the box – AS, DB, OCS, e. Biz Ÿ An enterprise infrastructure that leverages Oracle’s “unbreakable” technology – Reliability, scalability, security, performance Ÿ A single point of integration for customer’s existing identity management solutions – Transparent 3 rd party integration for OIM enabled products Ÿ Accommodates wide variety of partner solutions and customer deployments – Open, standards-based infrastructure enables integration
Oracle Identity Management Benefits Ÿ Enables deployment of all Oracle products out of the box – AS, DB, OCS, e. Biz Ÿ An enterprise infrastructure that leverages Oracle’s “unbreakable” technology – Reliability, scalability, security, performance Ÿ A single point of integration for customer’s existing identity management solutions – Transparent 3 rd party integration for OIM enabled products Ÿ Accommodates wide variety of partner solutions and customer deployments – Open, standards-based infrastructure enables integration
 What’s Next Ÿ Implementing Identity Management at Lawrence Livermore National Labs – – – ID: 40287 Presentor: Tony Macedo, Computer Scientist, LLNL Date: Thursday, 9/11 Time: 3: 15 - 4: 15 Location: Moscone Center room 120
What’s Next Ÿ Implementing Identity Management at Lawrence Livermore National Labs – – – ID: 40287 Presentor: Tony Macedo, Computer Scientist, LLNL Date: Thursday, 9/11 Time: 3: 15 - 4: 15 Location: Moscone Center room 120
 Q & A QUESTIONS ANSWERS
Q & A QUESTIONS ANSWERS
 Raymond K. Ng Technical Lead - JAAS Platform Security Oracle Corporation
Raymond K. Ng Technical Lead - JAAS Platform Security Oracle Corporation



