bccaf9475d4e257de3b559a23c66e8d5.ppt
- Количество слайдов: 23
 RAPIDware: Adaptive Software for Critical Infrastructure Protection Philip K. Mc. Kinley Software Engineering and Network Systems Laboratory Department of Computer Science and Engineering Michigan State University
RAPIDware: Adaptive Software for Critical Infrastructure Protection Philip K. Mc. Kinley Software Engineering and Network Systems Laboratory Department of Computer Science and Engineering Michigan State University
 Critical Infrastructures l Examples: Ø Electric power grids Ø Telecommunication networks Ø Water systems Ø Nuclear facilities, hydroelectric dams Ø Command control networks Ø Financial networks, and so on… l Managed by distributed computing facilities, connected to the Internet l Hence, they are at risk of cyber attack. l The consequences could be catastrophic.
Critical Infrastructures l Examples: Ø Electric power grids Ø Telecommunication networks Ø Water systems Ø Nuclear facilities, hydroelectric dams Ø Command control networks Ø Financial networks, and so on… l Managed by distributed computing facilities, connected to the Internet l Hence, they are at risk of cyber attack. l The consequences could be catastrophic.
 RAPIDware Project l Five-year, $3. 1 M project in CSE SENS Laboratory l Funded by U. S Office of Naval Research ØAdaptable Software / Critical Infrastructure Protection Program ØOutgrowth of Presidential Decision Directive 63 (May ’ 98) l Goal: Software (middleware) that can protect itself from: ØCyber attack ØHardware and software component failures ØChanging environmental conditions ØDynamic application/user requirements (e. g. security policies) l RAPIDware supports: Ø 5 CSE faculty members Ø 10 graduate research assistants
RAPIDware Project l Five-year, $3. 1 M project in CSE SENS Laboratory l Funded by U. S Office of Naval Research ØAdaptable Software / Critical Infrastructure Protection Program ØOutgrowth of Presidential Decision Directive 63 (May ’ 98) l Goal: Software (middleware) that can protect itself from: ØCyber attack ØHardware and software component failures ØChanging environmental conditions ØDynamic application/user requirements (e. g. security policies) l RAPIDware supports: Ø 5 CSE faculty members Ø 10 graduate research assistants
 RAPIDware Investigators l Phil Mc. Kinley - distributed computing, network protocols, adaptive middleware, anomaly detection l Kurt Stirewalt - software analysis, interactive systems, model checking l Laura Dillon - formal methods for concurrent systems, realtime systems l Betty Cheng - software engineering, formal methods, object -oriented development l Sandeep Kulkarni - fault tolerance, security
RAPIDware Investigators l Phil Mc. Kinley - distributed computing, network protocols, adaptive middleware, anomaly detection l Kurt Stirewalt - software analysis, interactive systems, model checking l Laura Dillon - formal methods for concurrent systems, realtime systems l Betty Cheng - software engineering, formal methods, object -oriented development l Sandeep Kulkarni - fault tolerance, security
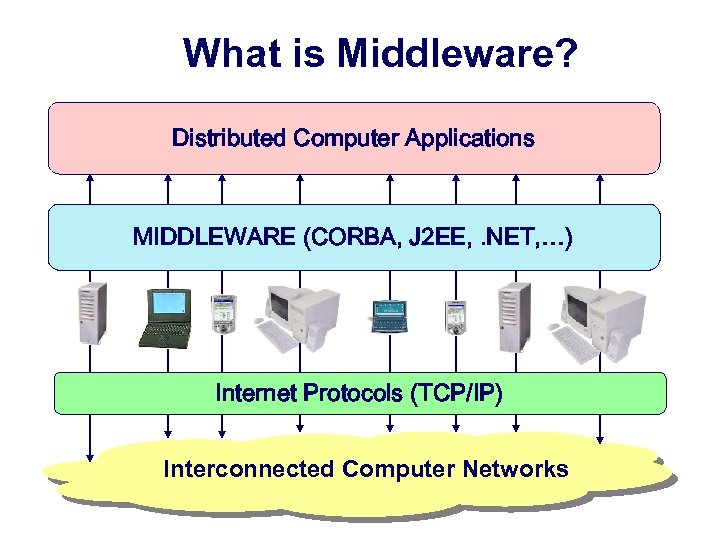 What is Middleware? Distributed Computer Applications MIDDLEWARE (CORBA, J 2 EE, . NET, …) Internet Protocols (TCP/IP) Interconnected Computer Networks
What is Middleware? Distributed Computer Applications MIDDLEWARE (CORBA, J 2 EE, . NET, …) Internet Protocols (TCP/IP) Interconnected Computer Networks
 Adaptive Middleware l Adaptive middleware can manage nonfunctional aspects of the system in coordinated fashion: Ø actively monitor the system, execute security policies Ø provide fault tolerance for specified components Ø adapt to changing environmental conditions Ø manage energy consumption in battery-powered devices Ø insulate the application from device/network differences l “Always On” systems Ø E. g. , command control, many critical infrastructure systems Ø require dynamic adaptation in ways not envisioned during development. l Enables systems to Operate Through Attacks
Adaptive Middleware l Adaptive middleware can manage nonfunctional aspects of the system in coordinated fashion: Ø actively monitor the system, execute security policies Ø provide fault tolerance for specified components Ø adapt to changing environmental conditions Ø manage energy consumption in battery-powered devices Ø insulate the application from device/network differences l “Always On” systems Ø E. g. , command control, many critical infrastructure systems Ø require dynamic adaptation in ways not envisioned during development. l Enables systems to Operate Through Attacks
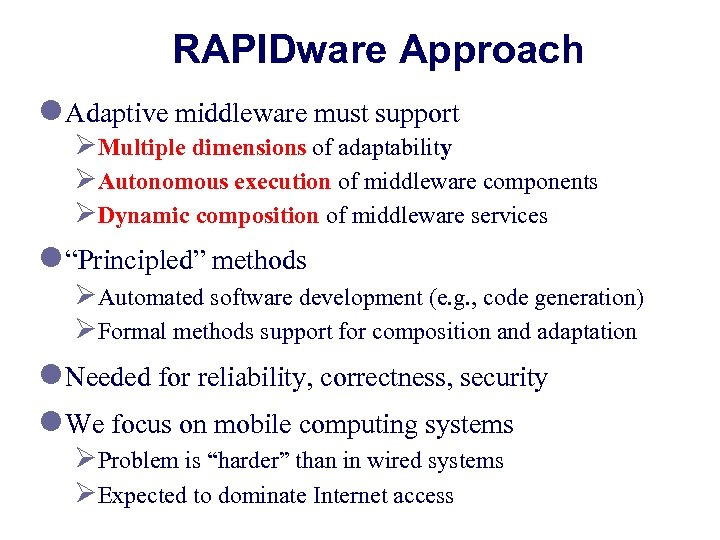 RAPIDware Approach l Adaptive middleware must support ØMultiple dimensions of adaptability ØAutonomous execution of middleware components ØDynamic composition of middleware services l “Principled” methods ØAutomated software development (e. g. , code generation) ØFormal methods support for composition and adaptation l Needed for reliability, correctness, security l We focus on mobile computing systems ØProblem is “harder” than in wired systems ØExpected to dominate Internet access
RAPIDware Approach l Adaptive middleware must support ØMultiple dimensions of adaptability ØAutonomous execution of middleware components ØDynamic composition of middleware services l “Principled” methods ØAutomated software development (e. g. , code generation) ØFormal methods support for composition and adaptation l Needed for reliability, correctness, security l We focus on mobile computing systems ØProblem is “harder” than in wired systems ØExpected to dominate Internet access
 Mobile Computing Testbed l Multiple-cell wireless LAN l Various laptop, handheld, and wearable computers
Mobile Computing Testbed l Multiple-cell wireless LAN l Various laptop, handheld, and wearable computers
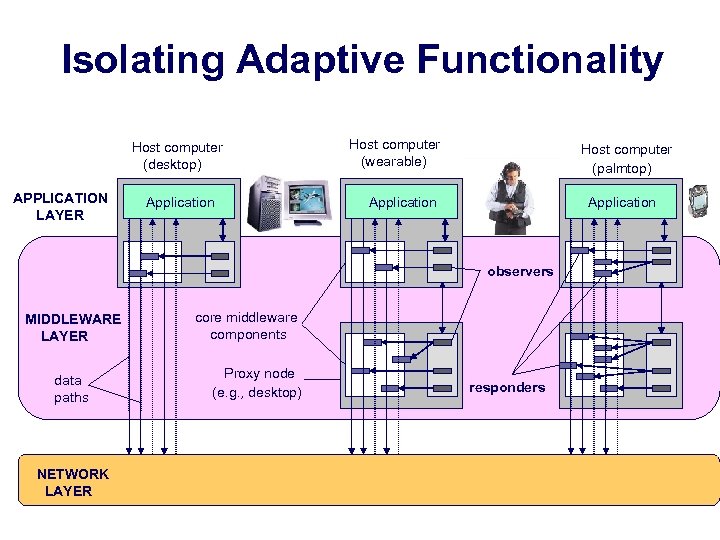 Isolating Adaptive Functionality Host computer (desktop) APPLICATION LAYER Application Host computer (wearable) Host computer (palmtop) Application observers MIDDLEWARE LAYER data paths NETWORK LAYER core middleware components Proxy node (e. g. , desktop) responders
Isolating Adaptive Functionality Host computer (desktop) APPLICATION LAYER Application Host computer (wearable) Host computer (palmtop) Application observers MIDDLEWARE LAYER data paths NETWORK LAYER core middleware components Proxy node (e. g. , desktop) responders
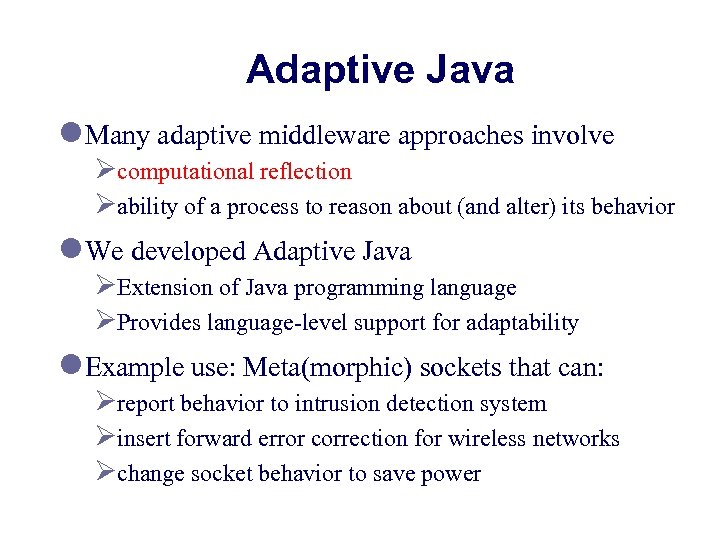 Adaptive Java l Many adaptive middleware approaches involve Øcomputational reflection Øability of a process to reason about (and alter) its behavior l We developed Adaptive Java ØExtension of Java programming language ØProvides language-level support for adaptability l Example use: Meta(morphic) sockets that can: Øreport behavior to intrusion detection system Øinsert forward error correction for wireless networks Øchange socket behavior to save power
Adaptive Java l Many adaptive middleware approaches involve Øcomputational reflection Øability of a process to reason about (and alter) its behavior l We developed Adaptive Java ØExtension of Java programming language ØProvides language-level support for adaptability l Example use: Meta(morphic) sockets that can: Øreport behavior to intrusion detection system Øinsert forward error correction for wireless networks Øchange socket behavior to save power
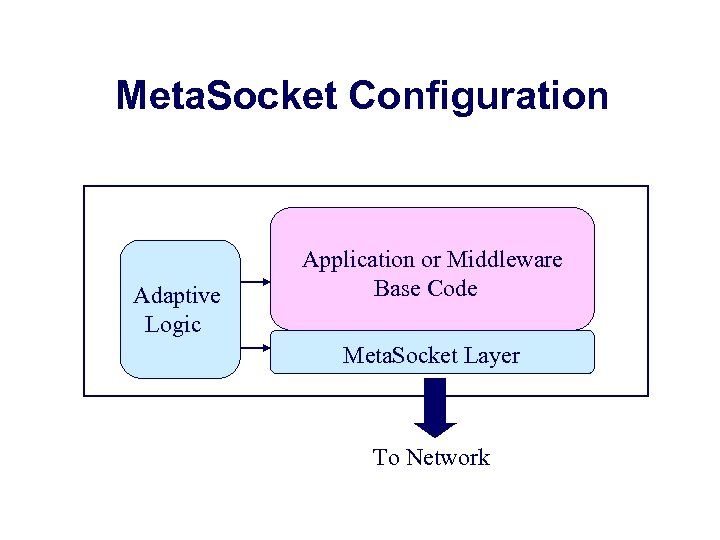 Meta. Socket Configuration Adaptive Logic Application or Middleware Base Code Meta. Socket Layer To Network
Meta. Socket Configuration Adaptive Logic Application or Middleware Base Code Meta. Socket Layer To Network
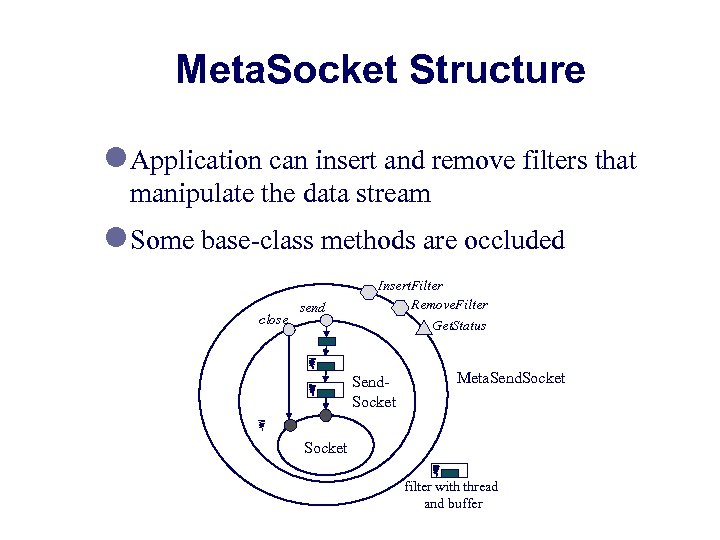 Meta. Socket Structure l Application can insert and remove filters that manipulate the data stream l Some base-class methods are occluded close send Insert. Filter Remove. Filter Get. Status Send. Socket Meta. Send. Socket filter with thread and buffer
Meta. Socket Structure l Application can insert and remove filters that manipulate the data stream l Some base-class methods are occluded close send Insert. Filter Remove. Filter Get. Status Send. Socket Meta. Send. Socket filter with thread and buffer
 Examples: Error Control and Component Auditing l Adaptive Java makes it possible to change components dynamically. l Effectively, any component can be made more robust, or more secure at run time. l Nature of auditing can be determined after development. l On-demand auditing may be especially useful to mobile systems.
Examples: Error Control and Component Auditing l Adaptive Java makes it possible to change components dynamically. l Effectively, any component can be made more robust, or more secure at run time. l Nature of auditing can be determined after development. l On-demand auditing may be especially useful to mobile systems.
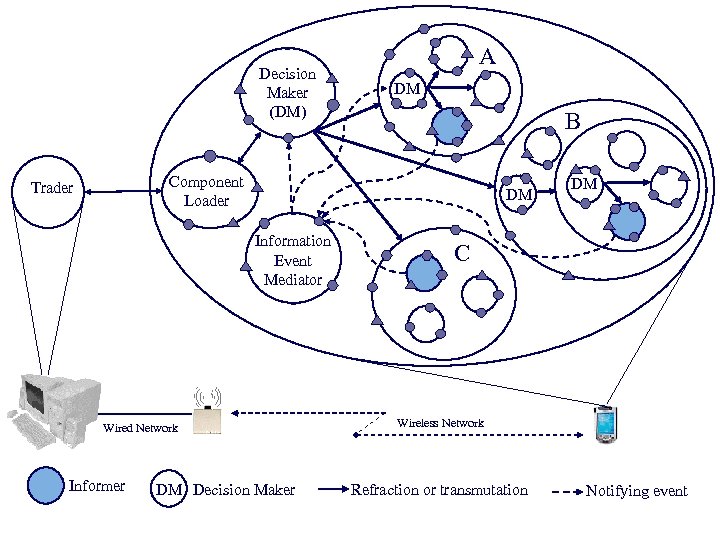 Decision Maker (DM) A DM B Component Loader Trader DM Information Event Mediator Wired Network Informer DM Decision Maker DM C Wireless Network Refraction or transmutation Notifying event
Decision Maker (DM) A DM B Component Loader Trader DM Information Event Mediator Wired Network Informer DM Decision Maker DM C Wireless Network Refraction or transmutation Notifying event
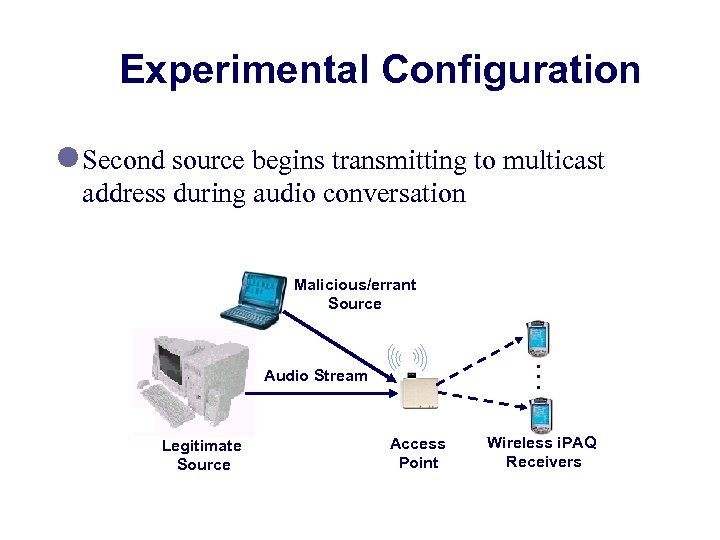 Experimental Configuration l Second source begins transmitting to multicast address during audio conversation Malicious/errant Source . . . Audio Stream Legitimate Source Access Point Wireless i. PAQ Receivers
Experimental Configuration l Second source begins transmitting to multicast address during audio conversation Malicious/errant Source . . . Audio Stream Legitimate Source Access Point Wireless i. PAQ Receivers
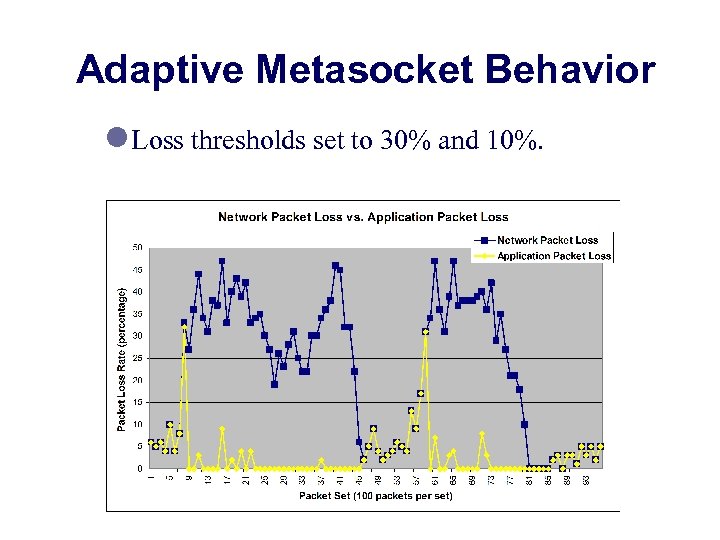 Adaptive Metasocket Behavior l Loss thresholds set to 30% and 10%.
Adaptive Metasocket Behavior l Loss thresholds set to 30% and 10%.
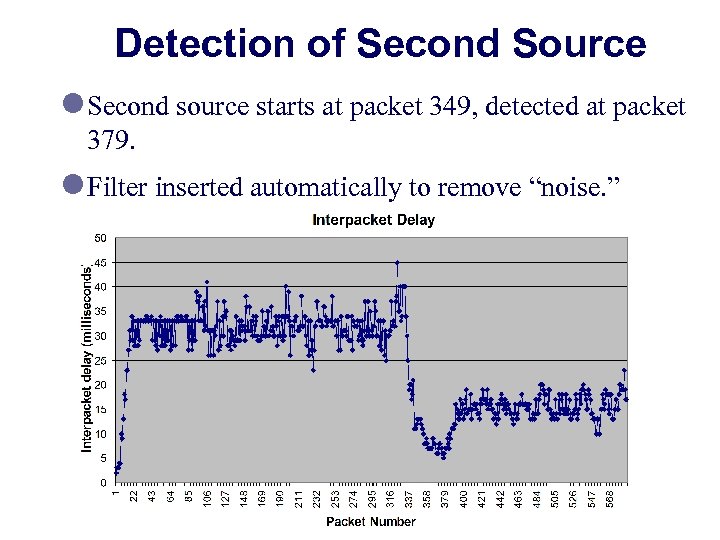 Detection of Second Source l Second source starts at packet 349, detected at packet 379. l Filter inserted automatically to remove “noise. ”
Detection of Second Source l Second source starts at packet 349, detected at packet 379. l Filter inserted automatically to remove “noise. ”
 Summary l RAPIDware is an ONR-funded project in the CSE Dept. l Addresses adaptive middleware to protect critical infrastructures from: Ø Cyber attacks Ø Component failures Ø Dynamic external conditions l Particular focus on wireless, collaborative computing systems l Adaptive Java Ø Programming language support for adaptability Ø Enables dynamic reconfiguration and auditing of components in deployed systems
Summary l RAPIDware is an ONR-funded project in the CSE Dept. l Addresses adaptive middleware to protect critical infrastructures from: Ø Cyber attacks Ø Component failures Ø Dynamic external conditions l Particular focus on wireless, collaborative computing systems l Adaptive Java Ø Programming language support for adaptability Ø Enables dynamic reconfiguration and auditing of components in deployed systems
 Ongoing Work l Adaptive Java and Meta. Sockets: Ø Dynamic auditing of components Ø Dynamic energy consumption management Ø Quality of service for wireless networks l Higher-level languages for adaptability l Middleware/Operating System cooperation for Ø Security Ø Energy management l Anomaly detection using statistical methods l Wireless network protocols (video, audio, data) l Security and robustness of peer-to-peer networks
Ongoing Work l Adaptive Java and Meta. Sockets: Ø Dynamic auditing of components Ø Dynamic energy consumption management Ø Quality of service for wireless networks l Higher-level languages for adaptability l Middleware/Operating System cooperation for Ø Security Ø Energy management l Anomaly detection using statistical methods l Wireless network protocols (video, audio, data) l Security and robustness of peer-to-peer networks
 Potential Collaboration l We are always looking for new research collaborators l Security/robustness of mobile computing systems Ø Emergency services Ø Command control Ø Medical applications l Intrusion/anomaly detection and monitoring l Control of: Ø Telecommunication networks Ø Water distribution systems Ø Power grids Ø Business/financial systems l “Smart” physical infrastructures: buildings, bridges, dams, etc. l Traceability of software development and usage for Ø Computer forensics? Ø Tracking intruders l Cognitive/Decision-making processes
Potential Collaboration l We are always looking for new research collaborators l Security/robustness of mobile computing systems Ø Emergency services Ø Command control Ø Medical applications l Intrusion/anomaly detection and monitoring l Control of: Ø Telecommunication networks Ø Water distribution systems Ø Power grids Ø Business/financial systems l “Smart” physical infrastructures: buildings, bridges, dams, etc. l Traceability of software development and usage for Ø Computer forensics? Ø Tracking intruders l Cognitive/Decision-making processes
 Related Papers l P. Mc. Kinley, U. Padmanabhan, N. Ancha, “Experiments in composing l l proxy audio services for mobile users, ” Proc. ACM/IFIP International Conference on Distributed Systems Platforms (Middleware’ 01), Heidelberg, Germany, Nov. 2001. P. K. Mc. Kinley, et al. , Realizing multi-dimensional software adaptation, '' in Proceedings of the ACM Workshop on Self-Healing, Adaptive and self. MANaged Systems (SHAMAN), (New York), June 2002. E. Kasten, et al. , “Separating introspection and intercession to support metamorphic distributed systems, ” Proc. IEEE Workshop on Aspect. Oriented Programming for Distributed Computing Systems (AOPDCS’ 02), Vienna, Austria, July 2002. P. K. Mc. Kinley, S. Sadjadi, E. P. Kasten, and R. Kalaskar, “Programming language support for adaptable wearable computing, ‘” in Proceedings of the Sixth International Symposium on Wearable Computers, Seattle, Washington, October 2002. Z. Yang, et al. , “An aspect-oriented approach to dynamic adaptation, ” in Proceedings of the ACM SIGSOFT Workshop on Self-Healing Systems (WOSS 02) (Charleston, South Carolina), November 2002.
Related Papers l P. Mc. Kinley, U. Padmanabhan, N. Ancha, “Experiments in composing l l proxy audio services for mobile users, ” Proc. ACM/IFIP International Conference on Distributed Systems Platforms (Middleware’ 01), Heidelberg, Germany, Nov. 2001. P. K. Mc. Kinley, et al. , Realizing multi-dimensional software adaptation, '' in Proceedings of the ACM Workshop on Self-Healing, Adaptive and self. MANaged Systems (SHAMAN), (New York), June 2002. E. Kasten, et al. , “Separating introspection and intercession to support metamorphic distributed systems, ” Proc. IEEE Workshop on Aspect. Oriented Programming for Distributed Computing Systems (AOPDCS’ 02), Vienna, Austria, July 2002. P. K. Mc. Kinley, S. Sadjadi, E. P. Kasten, and R. Kalaskar, “Programming language support for adaptable wearable computing, ‘” in Proceedings of the Sixth International Symposium on Wearable Computers, Seattle, Washington, October 2002. Z. Yang, et al. , “An aspect-oriented approach to dynamic adaptation, ” in Proceedings of the ACM SIGSOFT Workshop on Self-Healing Systems (WOSS 02) (Charleston, South Carolina), November 2002.
 Acknowledgements This work was supported in part by: l U. S. Department of the Navy, Office of Naval Research, Grant No. N 00014 -01 -1 -0744. l U. S. National Science Foundation grants: CDA 9617310, NCR-9706285, CCR-9912407, EIA 0000433, and EIA-0130724
Acknowledgements This work was supported in part by: l U. S. Department of the Navy, Office of Naval Research, Grant No. N 00014 -01 -1 -0744. l U. S. National Science Foundation grants: CDA 9617310, NCR-9706285, CCR-9912407, EIA 0000433, and EIA-0130724
 Further Information l Software Engineering and Network Systems Lab: www. cse. msu. edu/sens l RAPIDware Project: www. cse. msu. edu/rapidware l Email contact: mckinley@cse. msu. edu
Further Information l Software Engineering and Network Systems Lab: www. cse. msu. edu/sens l RAPIDware Project: www. cse. msu. edu/rapidware l Email contact: mckinley@cse. msu. edu


