8b887cc62715f40de99ba3c773fafb85.ppt
- Количество слайдов: 60
 RANDOM TOPICS IN INFOSEC AND FORENSICS Michigan HTCIA 3/19/2018 Mark Lachniet mark. lachniet@cdw. com (517 -242 -4874)
RANDOM TOPICS IN INFOSEC AND FORENSICS Michigan HTCIA 3/19/2018 Mark Lachniet mark. lachniet@cdw. com (517 -242 -4874)
 DISCLAIMER • I will be discussing techniques that could be misused • Make sure you know the law • Consult a lawyer • Opinions expressed are my own not that of my employer • Be particularly aware of wiretap and intrusion laws 2 | Security solutions
DISCLAIMER • I will be discussing techniques that could be misused • Make sure you know the law • Consult a lawyer • Opinions expressed are my own not that of my employer • Be particularly aware of wiretap and intrusion laws 2 | Security solutions
 ABOUT THE SPEAKER • Several terms on the board of the Michigan chapter of the High Technology Crime Investigation Association (MIHTCIA) • Member of the Michigan Council of Private Investigators (MCPI) • Licensed Private Investigator in the State of Michigan #3701 -205679 • Currently: Information Security Solutions Manager at CDW • Previous jobs: • Holt Public Schools (IT Director) • Sequoia / Analysts Intl. (Consultant) • Walsh College (instructor) • CDW (Security engineer that did actual work) • 15+ years in security consulting • Many tech certifications – CISA, CISSP, blah 3 | Security solutions
ABOUT THE SPEAKER • Several terms on the board of the Michigan chapter of the High Technology Crime Investigation Association (MIHTCIA) • Member of the Michigan Council of Private Investigators (MCPI) • Licensed Private Investigator in the State of Michigan #3701 -205679 • Currently: Information Security Solutions Manager at CDW • Previous jobs: • Holt Public Schools (IT Director) • Sequoia / Analysts Intl. (Consultant) • Walsh College (instructor) • CDW (Security engineer that did actual work) • 15+ years in security consulting • Many tech certifications – CISA, CISSP, blah 3 | Security solutions
 ABOUT THE SPEAKER • M. S. U. English Major™ 4 | Security solutions
ABOUT THE SPEAKER • M. S. U. English Major™ 4 | Security solutions
 AGENDA • Lock picking • Phone shenanigans • Mark Lachniet's experience getting his saving account looted through a clever online financial scam and how they did it • Voice over IP and falsifying phone information • Internet of Things • Government: Fear, loathing, tracking and the OPM breach • A review of some interesting leaked NSA documents • A New and easy way to bypass Bitlocker on some workstations 5 | Security solutions
AGENDA • Lock picking • Phone shenanigans • Mark Lachniet's experience getting his saving account looted through a clever online financial scam and how they did it • Voice over IP and falsifying phone information • Internet of Things • Government: Fear, loathing, tracking and the OPM breach • A review of some interesting leaked NSA documents • A New and easy way to bypass Bitlocker on some workstations 5 | Security solutions
 AGENDA • Review of some new original research on password complexity/security from hundreds of audits that can help practitioners get access to protected systems • A non-salesy review of current security software tool capabilities that can help the security practitioner by Jeff Falcon 6 | Security solutions
AGENDA • Review of some new original research on password complexity/security from hundreds of audits that can help practitioners get access to protected systems • A non-salesy review of current security software tool capabilities that can help the security practitioner by Jeff Falcon 6 | Security solutions
 HACKERS, PHONES AND SOCIAL ENGINEERING • “Hackers” have always been interested in ways to manipulate people and systems in order to achieve their ends • This has historically included telephones, harkening back to the “phone phreaking” days of free long distance phone calls, conference bridges and phone system hacking • A few interesting examples: • • 7 War Dialing – repeated phone calls with a computer and a modem to find other modems, fax machines and valid calling card codes Blue Boxing / Red Boxing – using specific sounds to take control of a phone switch as an operator or make free long distance calls from a pay phone | Security solutions
HACKERS, PHONES AND SOCIAL ENGINEERING • “Hackers” have always been interested in ways to manipulate people and systems in order to achieve their ends • This has historically included telephones, harkening back to the “phone phreaking” days of free long distance phone calls, conference bridges and phone system hacking • A few interesting examples: • • 7 War Dialing – repeated phone calls with a computer and a modem to find other modems, fax machines and valid calling card codes Blue Boxing / Red Boxing – using specific sounds to take control of a phone switch as an operator or make free long distance calls from a pay phone | Security solutions
 HACKERS, PHONES AND SOCIAL ENGINEERING • A diverse kind of online culture • Black Hats, Grey Hats, White Hats, Toques • There are special events at infosec conferences like Def. Con (https: //www. defcon. org/) and Black Hat (https: //www. blackhat. com/) • Includes social engineering competitions (being given a target such as a specific company and having to extract sensitive information over the phone – pretexting) • Another popular conference feature is the “lockpick village” where you can practice your lock picking skills with increasingly difficult locks • I went to a lockpick village this year…. 8 | Security solutions
HACKERS, PHONES AND SOCIAL ENGINEERING • A diverse kind of online culture • Black Hats, Grey Hats, White Hats, Toques • There are special events at infosec conferences like Def. Con (https: //www. defcon. org/) and Black Hat (https: //www. blackhat. com/) • Includes social engineering competitions (being given a target such as a specific company and having to extract sensitive information over the phone – pretexting) • Another popular conference feature is the “lockpick village” where you can practice your lock picking skills with increasingly difficult locks • I went to a lockpick village this year…. 8 | Security solutions
 LOCK PICKING DIAGRAMS… • From: http: //www. blackscoutsurvival. com/p/lockpicking 101. html • The long and short of it – keep a small but constant pressure on the tension wrench to rotate the cylinder so that when a pin goes into place it stays there, and poke with the picks to get the pins in place. Jiggle occasionally. • I have brought a lock and picks for you to play with when you get bored of my presentation 9 | Security solutions
LOCK PICKING DIAGRAMS… • From: http: //www. blackscoutsurvival. com/p/lockpicking 101. html • The long and short of it – keep a small but constant pressure on the tension wrench to rotate the cylinder so that when a pin goes into place it stays there, and poke with the picks to get the pins in place. Jiggle occasionally. • I have brought a lock and picks for you to play with when you get bored of my presentation 9 | Security solutions
 LOCKS I PICKED WHEN I GOT HOME… • So it turns out that many locks are easy to pick (if I can do it… anyone can) • This is what I was able to pick with 2 minutes of training and a cumulative hour or so of dinking around The fire “safe” I keep my important documents 10 | Security solutions The “Master” lock I previously used to lock my pelican case for transporting forensic equipment & firearms
LOCKS I PICKED WHEN I GOT HOME… • So it turns out that many locks are easy to pick (if I can do it… anyone can) • This is what I was able to pick with 2 minutes of training and a cumulative hour or so of dinking around The fire “safe” I keep my important documents 10 | Security solutions The “Master” lock I previously used to lock my pelican case for transporting forensic equipment & firearms
 TELEPHONE SOCIAL ENGINEERING SCAMS • Some are fairly obvious… •
TELEPHONE SOCIAL ENGINEERING SCAMS • Some are fairly obvious… •
 MY OWN EXPERIENCE • First indication of something odd was that for about the span of a day our telephones didn’t work • After they started working again we got some kind of automated AT&T message, didn’t think much of it • A few days later, I am asked by wife “did you just transfer all the money out of our savings account? ” • Contacted credit union to inquire and was asked by a young clerk if I hadn’t recently authorized it, to which I said no, and was put on hold, came back saying they would look into it • Obtained a copy of the wire transfer, it is for an amount just below the account balance, wiring the money to what looks like a construction company in Illinois • The wire transfer had a copy of my signature from some source, but it was an old signature that I no longer use, at least 10 years old 12 | Security solutions
MY OWN EXPERIENCE • First indication of something odd was that for about the span of a day our telephones didn’t work • After they started working again we got some kind of automated AT&T message, didn’t think much of it • A few days later, I am asked by wife “did you just transfer all the money out of our savings account? ” • Contacted credit union to inquire and was asked by a young clerk if I hadn’t recently authorized it, to which I said no, and was put on hold, came back saying they would look into it • Obtained a copy of the wire transfer, it is for an amount just below the account balance, wiring the money to what looks like a construction company in Illinois • The wire transfer had a copy of my signature from some source, but it was an old signature that I no longer use, at least 10 years old 12 | Security solutions
 MY OWN EXPERIENCE • It turns out that the scammers had gotten AT&T to disconnect my phone line and connect it to them somehow • They then used a fax machine from my stolen “home phone” line to fax in the wire transfer (this number is what showed up on the fax machine’s caller ID) • The CU, as per procedure, called to verify the large amount • Unfortunately they verified it with the criminal that answered on my behalf on my phone number • Entered my info at http: //www. ic 3. gov/default. aspx (it didn’t help me but maybe it will help make a case some day) • My losses were too small for federal investigators, the MSP refused to take a report, so I ended up working with my township (a nice guy but very pessimistic about even getting results from telcos, and too late by that point) 13 | Security solutions
MY OWN EXPERIENCE • It turns out that the scammers had gotten AT&T to disconnect my phone line and connect it to them somehow • They then used a fax machine from my stolen “home phone” line to fax in the wire transfer (this number is what showed up on the fax machine’s caller ID) • The CU, as per procedure, called to verify the large amount • Unfortunately they verified it with the criminal that answered on my behalf on my phone number • Entered my info at http: //www. ic 3. gov/default. aspx (it didn’t help me but maybe it will help make a case some day) • My losses were too small for federal investigators, the MSP refused to take a report, so I ended up working with my township (a nice guy but very pessimistic about even getting results from telcos, and too late by that point) 13 | Security solutions
 MY OWN EXPERIENCE • Put extra security and passwords on CU systems • Changed all my important passwords • Ended up being reimbursed through the CU’s insurance, but did not vigorously pursue law enforcement help due to the trail going cold and no firepower • Consider the amount of funding, planning and research that had to go into that attack, not to mention the amount of employee time • The attack wouldn’t have been possible without telephone tomfoolery! • Quite likely the scammers were from another country entirely and just using the Chicago company as a shell • All made possible with the Power Of Telco! 14 | Security solutions
MY OWN EXPERIENCE • Put extra security and passwords on CU systems • Changed all my important passwords • Ended up being reimbursed through the CU’s insurance, but did not vigorously pursue law enforcement help due to the trail going cold and no firepower • Consider the amount of funding, planning and research that had to go into that attack, not to mention the amount of employee time • The attack wouldn’t have been possible without telephone tomfoolery! • Quite likely the scammers were from another country entirely and just using the Chicago company as a shell • All made possible with the Power Of Telco! 14 | Security solutions
 PLAIN OLD TELEPHONE SERVICE (POTS) • More or less like two tin cans with a string between them, only with a lot more strings and parts 15 | Security solutions
PLAIN OLD TELEPHONE SERVICE (POTS) • More or less like two tin cans with a string between them, only with a lot more strings and parts 15 | Security solutions
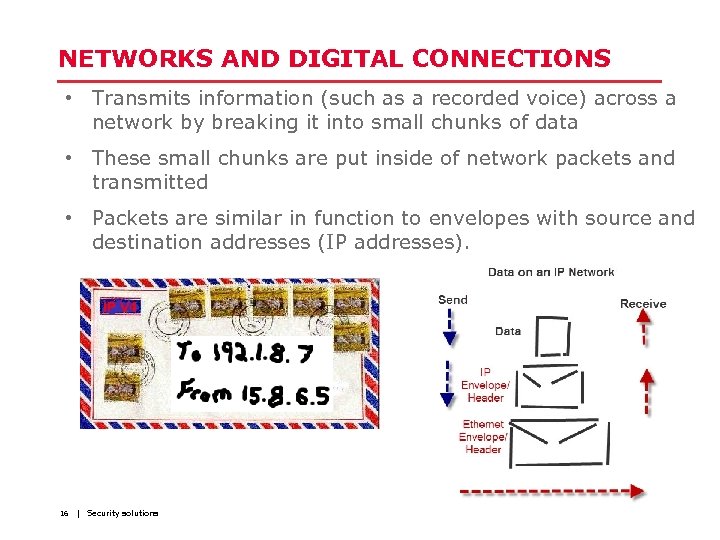 NETWORKS AND DIGITAL CONNECTIONS • Transmits information (such as a recorded voice) across a network by breaking it into small chunks of data • These small chunks are put inside of network packets and transmitted • Packets are similar in function to envelopes with source and destination addresses (IP addresses). 16 | Security solutions
NETWORKS AND DIGITAL CONNECTIONS • Transmits information (such as a recorded voice) across a network by breaking it into small chunks of data • These small chunks are put inside of network packets and transmitted • Packets are similar in function to envelopes with source and destination addresses (IP addresses). 16 | Security solutions
 NETWORKS AND DIGITAL CONNECTIONS • Many of you have simple home networks with a number of devices and an Internet router • Just as you can go to a website like Amazon. com, you can make telephone calls over the Internet 17 | Security solutions
NETWORKS AND DIGITAL CONNECTIONS • Many of you have simple home networks with a number of devices and an Internet router • Just as you can go to a website like Amazon. com, you can make telephone calls over the Internet 17 | Security solutions
 VOICE OVER IP • Wikipedia: “Voice over IP (Vo. IP) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. Other terms commonly associated with Vo. IP are IP telephony, Internet telephony, broadband telephony, and broadband phone service” • Commercial examples: • Skype • Google Voice / Google Hangouts • (Every modern and expensive phone system) • Can work on a client-server basis, as well as tying together phone systems from different physical locations 18 | Security solutions
VOICE OVER IP • Wikipedia: “Voice over IP (Vo. IP) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. Other terms commonly associated with Vo. IP are IP telephony, Internet telephony, broadband telephony, and broadband phone service” • Commercial examples: • Skype • Google Voice / Google Hangouts • (Every modern and expensive phone system) • Can work on a client-server basis, as well as tying together phone systems from different physical locations 18 | Security solutions
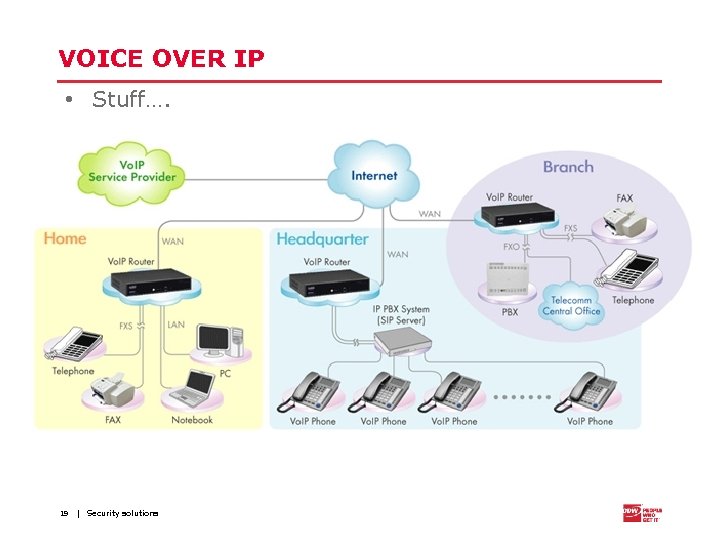 VOICE OVER IP • Stuff…. 19 | Security solutions
VOICE OVER IP • Stuff…. 19 | Security solutions
 CISCO IP PHONE • Issued to me by work for home office use in undies • Makes an encrypted VPN connection to CDW’s corporate office and connects to a voice gateway • Works more or less as if I were in an office – rings when called, voicemail, etc. • Gives me a (847) number 20 | Security solutions
CISCO IP PHONE • Issued to me by work for home office use in undies • Makes an encrypted VPN connection to CDW’s corporate office and connects to a voice gateway • Works more or less as if I were in an office – rings when called, voicemail, etc. • Gives me a (847) number 20 | Security solutions
 THE OBIHAI • A gateway that allows you to plug in a regular land-line phone for Vo. IP – price hovers around $50 • Supports different services – I use Google Voice / Google Hangouts to get a number with a 248 area code • Pretty much a free landline, thanks to Google! • With my two cell phones, I now have phone numbers in (847), (616), (248), and (517) – take your pick! 21 | Security solutions
THE OBIHAI • A gateway that allows you to plug in a regular land-line phone for Vo. IP – price hovers around $50 • Supports different services – I use Google Voice / Google Hangouts to get a number with a 248 area code • Pretty much a free landline, thanks to Google! • With my two cell phones, I now have phone numbers in (847), (616), (248), and (517) – take your pick! 21 | Security solutions
 CALLER ID SPOOFING • Caller ID can be controlled by the IPTel system making the outgoing phone call, thus can be faked • This is a problem for 911 services if they can’t find a valid number corresponding to a physical location for • Services also exist to allow you to spoof a caller ID, record the call, change your voice, etc. • Under the Truth in Caller ID Act, FCC rules: • • Subject violators to a penalty of up to $10, 000 for each violation of the rules. • 22 Prohibit any person or entity from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm, or wrongfully obtain anything of value. Exempt authorized activities by law enforcement agencies and situations where courts have authorized caller ID manipulation to occur. | Security solutions
CALLER ID SPOOFING • Caller ID can be controlled by the IPTel system making the outgoing phone call, thus can be faked • This is a problem for 911 services if they can’t find a valid number corresponding to a physical location for • Services also exist to allow you to spoof a caller ID, record the call, change your voice, etc. • Under the Truth in Caller ID Act, FCC rules: • • Subject violators to a penalty of up to $10, 000 for each violation of the rules. • 22 Prohibit any person or entity from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm, or wrongfully obtain anything of value. Exempt authorized activities by law enforcement agencies and situations where courts have authorized caller ID manipulation to occur. | Security solutions
 CALLER ID SPOOFING EXPLOITS • Call the IT helpdesk for a password reset, impersonating an employee’s short extension number or other pretexting • “Swatting” • Accessing a cell phone voice mail system by changing your number to that of the victim’s number • Text (SMS) message can also be spoofed • All of this traffic can be routed through virtual private networks and proxy servers to appear to originate from anywhere (both in terms of IP addresses and in terms of phone numbers) • In other words – never trust what your phone tells you! (or what it is telling others) 23 | Security solutions
CALLER ID SPOOFING EXPLOITS • Call the IT helpdesk for a password reset, impersonating an employee’s short extension number or other pretexting • “Swatting” • Accessing a cell phone voice mail system by changing your number to that of the victim’s number • Text (SMS) message can also be spoofed • All of this traffic can be routed through virtual private networks and proxy servers to appear to originate from anywhere (both in terms of IP addresses and in terms of phone numbers) • In other words – never trust what your phone tells you! (or what it is telling others) 23 | Security solutions
 VERIZON WIRELESS PLUS BUGGING • A feature from Verizon that lets you get your text messages on a different device such as a tablet or PC • To configure it, you download the Message Plus software and tell it what your cell phone number is • Verizon sends the cell phone a text message containing an authorization code • Once connected, all future text messages will be downloaded on this new tablet or PC as well • This includes pictures and multimedia files • Will likely also grab historical SMS data such as old text messages within N number of days • Configure it… delete the text message… text message bug win! 24 | Security solutions
VERIZON WIRELESS PLUS BUGGING • A feature from Verizon that lets you get your text messages on a different device such as a tablet or PC • To configure it, you download the Message Plus software and tell it what your cell phone number is • Verizon sends the cell phone a text message containing an authorization code • Once connected, all future text messages will be downloaded on this new tablet or PC as well • This includes pictures and multimedia files • Will likely also grab historical SMS data such as old text messages within N number of days • Configure it… delete the text message… text message bug win! 24 | Security solutions
 THE INTERNET OF THINGS FAIL • So how about we connect everything in our lives to the Internet like refrigerators, ovens, thermostats, door locks, pet doors and surveillance cameras? • What could go wrong? HUMANS! • Enter the search engine Shodan. io! • http: //search. slashdot. org/story/16/01/24/0256224/iotsecurity-is-so-bad-theres-a-search-engine-for-sleeping-kids • My Shodan Search: port: 554 has_screenshot: true country: "US" org: "Comcast Cable“ • i. e. show me all the systems running a system on port 554 for which a screen shot is available, for US systems originating on Comcast Cable • The following data was pulled from a fresh search 1/26/16 25 | Security solutions
THE INTERNET OF THINGS FAIL • So how about we connect everything in our lives to the Internet like refrigerators, ovens, thermostats, door locks, pet doors and surveillance cameras? • What could go wrong? HUMANS! • Enter the search engine Shodan. io! • http: //search. slashdot. org/story/16/01/24/0256224/iotsecurity-is-so-bad-theres-a-search-engine-for-sleeping-kids • My Shodan Search: port: 554 has_screenshot: true country: "US" org: "Comcast Cable“ • i. e. show me all the systems running a system on port 554 for which a screen shot is available, for US systems originating on Comcast Cable • The following data was pulled from a fresh search 1/26/16 25 | Security solutions
 THE INTERNET OF FAIL • So how about we connect everything in our lives to the Internet, like this office in Tracy California, and not require a password? 26 | Security solutions
THE INTERNET OF FAIL • So how about we connect everything in our lives to the Internet, like this office in Tracy California, and not require a password? 26 | Security solutions
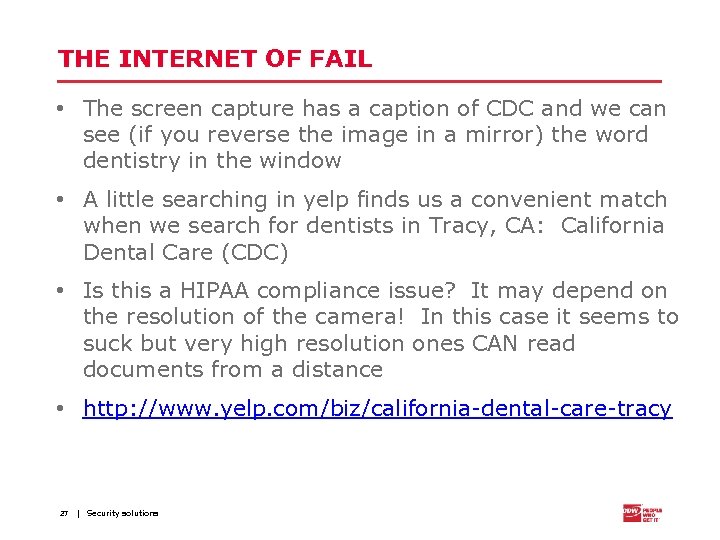 THE INTERNET OF FAIL • The screen capture has a caption of CDC and we can see (if you reverse the image in a mirror) the word dentistry in the window • A little searching in yelp finds us a convenient match when we search for dentists in Tracy, CA: California Dental Care (CDC) • Is this a HIPAA compliance issue? It may depend on the resolution of the camera! In this case it seems to suck but very high resolution ones CAN read documents from a distance • http: //www. yelp. com/biz/california-dental-care-tracy 27 | Security solutions
THE INTERNET OF FAIL • The screen capture has a caption of CDC and we can see (if you reverse the image in a mirror) the word dentistry in the window • A little searching in yelp finds us a convenient match when we search for dentists in Tracy, CA: California Dental Care (CDC) • Is this a HIPAA compliance issue? It may depend on the resolution of the camera! In this case it seems to suck but very high resolution ones CAN read documents from a distance • http: //www. yelp. com/biz/california-dental-care-tracy 27 | Security solutions
 THE INTERNET OF FAIL • Yelp gives some nice pictures of the inside… sure looks like the same desk! Note the Dell monitor and paper thingy 28 | Security solutions
THE INTERNET OF FAIL • Yelp gives some nice pictures of the inside… sure looks like the same desk! Note the Dell monitor and paper thingy 28 | Security solutions
 THE INTERNET OF FAIL • Pull up the web site and get location information including “Next to Mi Pueblo Market” • Its Google Street View time… put in the address, find the market, find the dentist office • If this was a pen-test we’d have an engineer go goof under the camera and take a screen cap 29 | Security solutions Nice and Stalky!
THE INTERNET OF FAIL • Pull up the web site and get location information including “Next to Mi Pueblo Market” • Its Google Street View time… put in the address, find the market, find the dentist office • If this was a pen-test we’d have an engineer go goof under the camera and take a screen cap 29 | Security solutions Nice and Stalky!
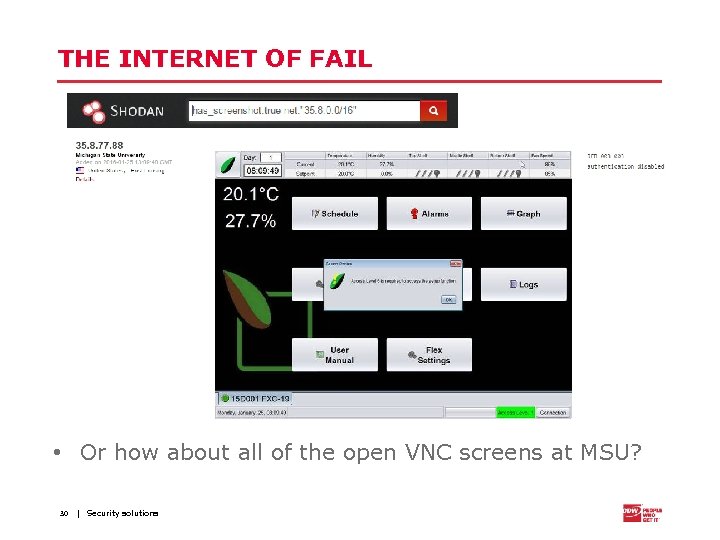 THE INTERNET OF FAIL • Or how about all of the open VNC screens at MSU? 30 | Security solutions
THE INTERNET OF FAIL • Or how about all of the open VNC screens at MSU? 30 | Security solutions
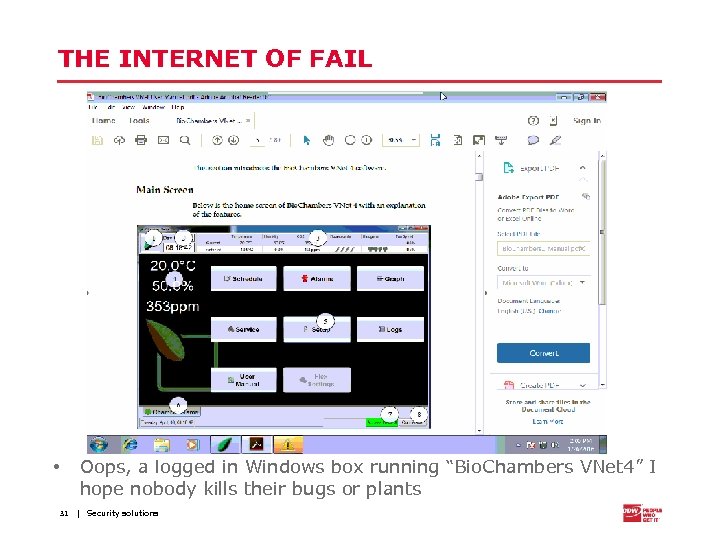 THE INTERNET OF FAIL Oops, a logged in Windows box running “Bio. Chambers VNet 4” I hope nobody kills their bugs or plants • 31 | Security solutions
THE INTERNET OF FAIL Oops, a logged in Windows box running “Bio. Chambers VNet 4” I hope nobody kills their bugs or plants • 31 | Security solutions
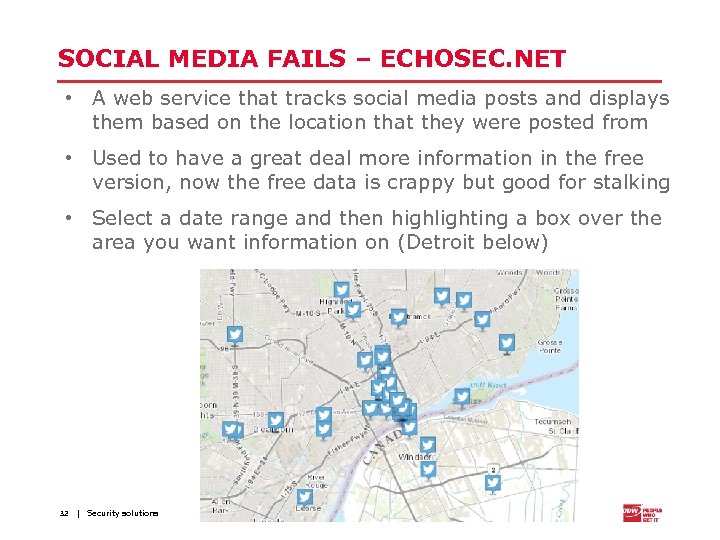 SOCIAL MEDIA FAILS – ECHOSEC. NET • A web service that tracks social media posts and displays them based on the location that they were posted from • Used to have a great deal more information in the free version, now the free data is crappy but good for stalking • Select a date range and then highlighting a box over the area you want information on (Detroit below) 32 | Security solutions
SOCIAL MEDIA FAILS – ECHOSEC. NET • A web service that tracks social media posts and displays them based on the location that they were posted from • Used to have a great deal more information in the free version, now the free data is crappy but good for stalking • Select a date range and then highlighting a box over the area you want information on (Detroit below) 32 | Security solutions
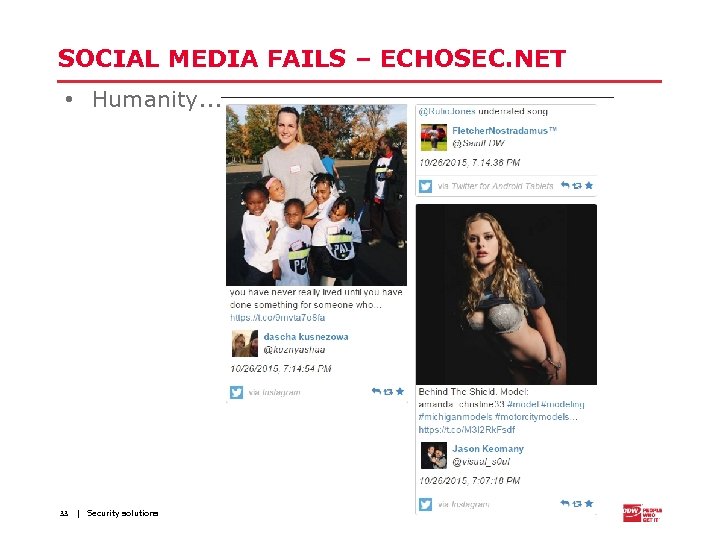 SOCIAL MEDIA FAILS – ECHOSEC. NET • Humanity. . . 33 | Security solutions
SOCIAL MEDIA FAILS – ECHOSEC. NET • Humanity. . . 33 | Security solutions
 GOVERNMENT ISSUES – FEAR AND LOATHING • We are all being tracked… TRUE! But it is as much the marketers as the government. • Even if you use the Ghostery plugin to stop advertising scripts, you are probably uniquely identifiable by just what your browser presents to web servers • Test how unique you are using https: //panopticlick. eff. org/ • My work laptop blocked advertising trackers, but my “browser fingerprint appears to be unique among the 6, 392, 013 tested so far. ” • Even if you use a VPN and other services, your computer is still uniquely identifiable • This has implications for law enforcement – this could be used to identify bad actors through proper technical techniques • Path of least resistance for would-be big brothers? Buy marketing services? 34 | Security solutions
GOVERNMENT ISSUES – FEAR AND LOATHING • We are all being tracked… TRUE! But it is as much the marketers as the government. • Even if you use the Ghostery plugin to stop advertising scripts, you are probably uniquely identifiable by just what your browser presents to web servers • Test how unique you are using https: //panopticlick. eff. org/ • My work laptop blocked advertising trackers, but my “browser fingerprint appears to be unique among the 6, 392, 013 tested so far. ” • Even if you use a VPN and other services, your computer is still uniquely identifiable • This has implications for law enforcement – this could be used to identify bad actors through proper technical techniques • Path of least resistance for would-be big brothers? Buy marketing services? 34 | Security solutions
 GOVERNMENT ISSUES – OPM • The Office of Personnel Management – The system that maintains all of the data for citizens that have government clearances • Survey: How many people have gotten the OPM oops letter? • Facts: • Contains an estimated 21. 5 M records, 5. 6 M fingerprints • Contains detailed background checks covering criminal history and drug use • Contains practically all information about a person’s education, work, place of residences, as well as SSN, Drivers License Numbers, etc. • Includes similar information for spouses • The Electronic Freedom Frontier (EFF) had previously sued them for poor data security and over-collection of data but lost • https: //www. eff. org/deeplinks/2015/07/we-told-you-so-opm-data -breach-reveals-not-only-lame-data-security-weak-legal 35 | Security solutions
GOVERNMENT ISSUES – OPM • The Office of Personnel Management – The system that maintains all of the data for citizens that have government clearances • Survey: How many people have gotten the OPM oops letter? • Facts: • Contains an estimated 21. 5 M records, 5. 6 M fingerprints • Contains detailed background checks covering criminal history and drug use • Contains practically all information about a person’s education, work, place of residences, as well as SSN, Drivers License Numbers, etc. • Includes similar information for spouses • The Electronic Freedom Frontier (EFF) had previously sued them for poor data security and over-collection of data but lost • https: //www. eff. org/deeplinks/2015/07/we-told-you-so-opm-data -breach-reveals-not-only-lame-data-security-weak-legal 35 | Security solutions
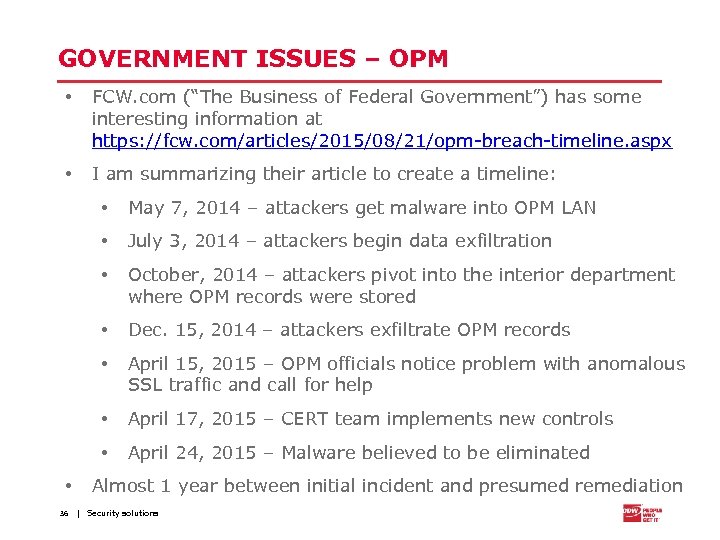 GOVERNMENT ISSUES – OPM • FCW. com (“The Business of Federal Government”) has some interesting information at https: //fcw. com/articles/2015/08/21/opm-breach-timeline. aspx • I am summarizing their article to create a timeline: • • October, 2014 – attackers pivot into the interior department where OPM records were stored • Dec. 15, 2014 – attackers exfiltrate OPM records • April 15, 2015 – OPM officials notice problem with anomalous SSL traffic and call for help • April 17, 2015 – CERT team implements new controls • 36 July 3, 2014 – attackers begin data exfiltration • • May 7, 2014 – attackers get malware into OPM LAN April 24, 2015 – Malware believed to be eliminated Almost 1 year between initial incident and presumed remediation | Security solutions
GOVERNMENT ISSUES – OPM • FCW. com (“The Business of Federal Government”) has some interesting information at https: //fcw. com/articles/2015/08/21/opm-breach-timeline. aspx • I am summarizing their article to create a timeline: • • October, 2014 – attackers pivot into the interior department where OPM records were stored • Dec. 15, 2014 – attackers exfiltrate OPM records • April 15, 2015 – OPM officials notice problem with anomalous SSL traffic and call for help • April 17, 2015 – CERT team implements new controls • 36 July 3, 2014 – attackers begin data exfiltration • • May 7, 2014 – attackers get malware into OPM LAN April 24, 2015 – Malware believed to be eliminated Almost 1 year between initial incident and presumed remediation | Security solutions
 GOVERNMENT ISSUES – OPM • Vendors are blamed… • The Chinese are blamed… • Security in government is simply bad, with a few exceptions • The “guvment work” attitude • Minimal funding and leadership support • Many large applications are developed using contract programmers rather than internal staff, often foreigners • Security is rarely a functional requirement, and when it is a requirement it is not properly tested and retested • My opinion: we have hundreds more important applications that are also insecure that nobody has gotten around to hacking, and the government needs a lot of help with application security. But what do I know…. 37 | Security solutions
GOVERNMENT ISSUES – OPM • Vendors are blamed… • The Chinese are blamed… • Security in government is simply bad, with a few exceptions • The “guvment work” attitude • Minimal funding and leadership support • Many large applications are developed using contract programmers rather than internal staff, often foreigners • Security is rarely a functional requirement, and when it is a requirement it is not properly tested and retested • My opinion: we have hundreds more important applications that are also insecure that nobody has gotten around to hacking, and the government needs a lot of help with application security. But what do I know…. 37 | Security solutions
 GOVERNMENT ISSUES – OPM “What you saw at OPM, you’re going to see a whole lot more of” (National Security Agency Director Adm. Mike Rogers, 1/21/16) 38 | Security solutions
GOVERNMENT ISSUES – OPM “What you saw at OPM, you’re going to see a whole lot more of” (National Security Agency Director Adm. Mike Rogers, 1/21/16) 38 | Security solutions
 GOVERNMENT ISSUES – OPM Thanks Obama Chinese Apathy, Obfuscation and Incompetence!! 39 | Security solutions
GOVERNMENT ISSUES – OPM Thanks Obama Chinese Apathy, Obfuscation and Incompetence!! 39 | Security solutions
 SOME INTERESTING “CAPABILITIES” INFORMATION • I have been keeping an eye on some of the data that is being leaked about US Government tools and techniques • I have no direct information about any of this other than what I read in news articles • Much of what I say is also speculation…. . • But here a few interesting things! 40 | Security solutions
SOME INTERESTING “CAPABILITIES” INFORMATION • I have been keeping an eye on some of the data that is being leaked about US Government tools and techniques • I have no direct information about any of this other than what I read in news articles • Much of what I say is also speculation…. . • But here a few interesting things! 40 | Security solutions
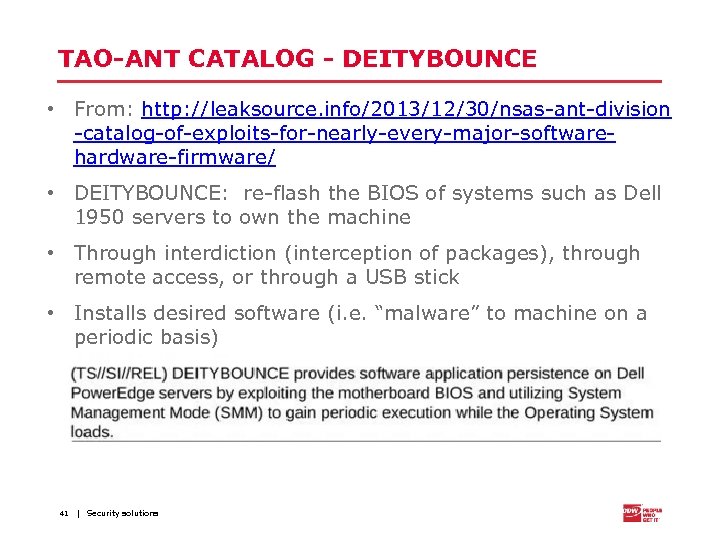 TAO-ANT CATALOG - DEITYBOUNCE • From: http: //leaksource. info/2013/12/30/nsas-ant-division -catalog-of-exploits-for-nearly-every-major-softwarehardware-firmware/ • DEITYBOUNCE: re-flash the BIOS of systems such as Dell 1950 servers to own the machine • Through interdiction (interception of packages), through remote access, or through a USB stick • Installs desired software (i. e. “malware” to machine on a periodic basis) 41 | Security solutions
TAO-ANT CATALOG - DEITYBOUNCE • From: http: //leaksource. info/2013/12/30/nsas-ant-division -catalog-of-exploits-for-nearly-every-major-softwarehardware-firmware/ • DEITYBOUNCE: re-flash the BIOS of systems such as Dell 1950 servers to own the machine • Through interdiction (interception of packages), through remote access, or through a USB stick • Installs desired software (i. e. “malware” to machine on a periodic basis) 41 | Security solutions
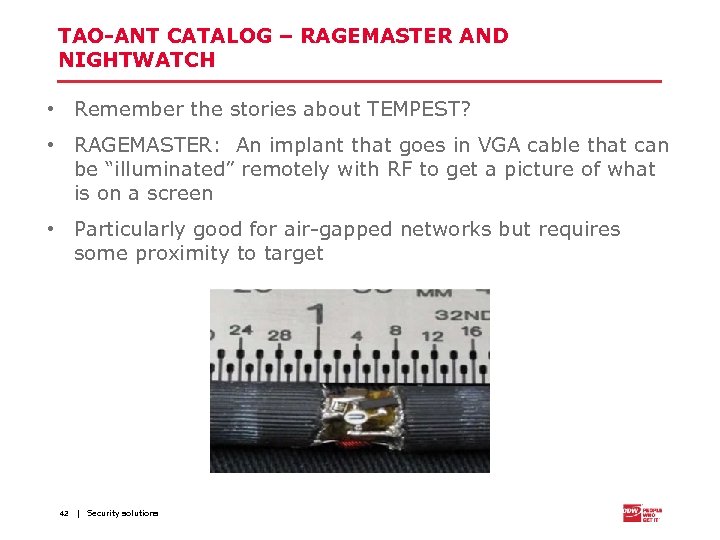 TAO-ANT CATALOG – RAGEMASTER AND NIGHTWATCH • Remember the stories about TEMPEST? • RAGEMASTER: An implant that goes in VGA cable that can be “illuminated” remotely with RF to get a picture of what is on a screen • Particularly good for air-gapped networks but requires some proximity to target 42 | Security solutions
TAO-ANT CATALOG – RAGEMASTER AND NIGHTWATCH • Remember the stories about TEMPEST? • RAGEMASTER: An implant that goes in VGA cable that can be “illuminated” remotely with RF to get a picture of what is on a screen • Particularly good for air-gapped networks but requires some proximity to target 42 | Security solutions
 TAO-ANT CATALOG – RAGEMASTER AND NIGHTWATCH • NIGHTWATCH: A device that can process the reflected data from RAGEMASTER and render it as a viewable screen 43 | Security solutions
TAO-ANT CATALOG – RAGEMASTER AND NIGHTWATCH • NIGHTWATCH: A device that can process the reflected data from RAGEMASTER and render it as a viewable screen 43 | Security solutions
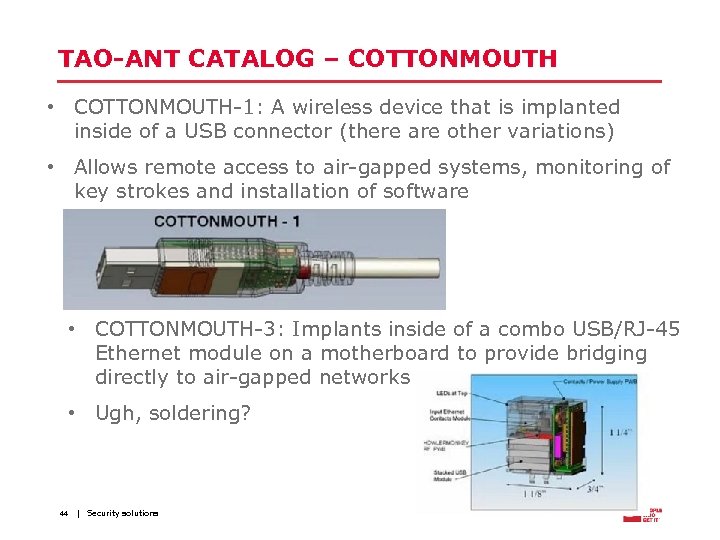 TAO-ANT CATALOG – COTTONMOUTH • COTTONMOUTH-1: A wireless device that is implanted inside of a USB connector (there are other variations) • Allows remote access to air-gapped systems, monitoring of key strokes and installation of software • COTTONMOUTH-3: Implants inside of a combo USB/RJ-45 Ethernet module on a motherboard to provide bridging directly to air-gapped networks • Ugh, soldering? 44 | Security solutions
TAO-ANT CATALOG – COTTONMOUTH • COTTONMOUTH-1: A wireless device that is implanted inside of a USB connector (there are other variations) • Allows remote access to air-gapped systems, monitoring of key strokes and installation of software • COTTONMOUTH-3: Implants inside of a combo USB/RJ-45 Ethernet module on a motherboard to provide bridging directly to air-gapped networks • Ugh, soldering? 44 | Security solutions
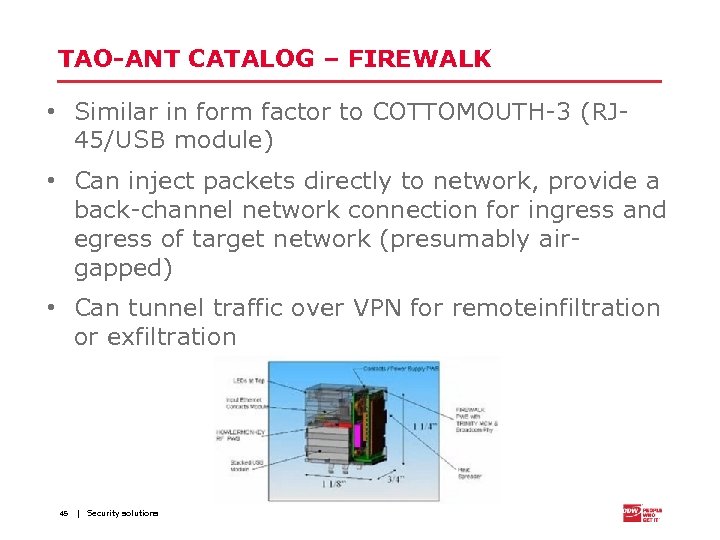 TAO-ANT CATALOG – FIREWALK • Similar in form factor to COTTOMOUTH-3 (RJ 45/USB module) • Can inject packets directly to network, provide a back-channel network connection for ingress and egress of target network (presumably airgapped) • Can tunnel traffic over VPN for remoteinfiltration or exfiltration 45 | Security solutions
TAO-ANT CATALOG – FIREWALK • Similar in form factor to COTTOMOUTH-3 (RJ 45/USB module) • Can inject packets directly to network, provide a back-channel network connection for ingress and egress of target network (presumably airgapped) • Can tunnel traffic over VPN for remoteinfiltration or exfiltration 45 | Security solutions
 TAO-ANT CATALOG – WISTFULTOLL • Wait a minute, obtaining forensic data through malware implants and hacking? That sounds hostile! 46 | Security solutions
TAO-ANT CATALOG – WISTFULTOLL • Wait a minute, obtaining forensic data through malware implants and hacking? That sounds hostile! 46 | Security solutions
 HOSTILE FORENSICS • Who would have thunk? http: //lachniet. com/forensics/2011 -0805_Hostile_Forensics_v 1. 0. pdf 47 | Security solutions
HOSTILE FORENSICS • Who would have thunk? http: //lachniet. com/forensics/2011 -0805_Hostile_Forensics_v 1. 0. pdf 47 | Security solutions
 JTAG HACKING • In layman’s terms, JTAG is a serial interface that is built into many hardware devices that is provided for debugging purposes • It exists on phones, servers and many other things • It can connect directly into the hardware level of the device • Some NSA implants are believed to be JTAG based • See the video from Defcon 2015 at https: //www. youtube. com/watch? v=o. Gu. ZNm. BZbjk • Want to make your own? http: //www. nsaplayset. org/ • JTAG hacking will be a massive area of development for hackers • Fortunately, it requires physical access, but unfortunately it can be used to find universally applicable attacks 48 | Security solutions
JTAG HACKING • In layman’s terms, JTAG is a serial interface that is built into many hardware devices that is provided for debugging purposes • It exists on phones, servers and many other things • It can connect directly into the hardware level of the device • Some NSA implants are believed to be JTAG based • See the video from Defcon 2015 at https: //www. youtube. com/watch? v=o. Gu. ZNm. BZbjk • Want to make your own? http: //www. nsaplayset. org/ • JTAG hacking will be a massive area of development for hackers • Fortunately, it requires physical access, but unfortunately it can be used to find universally applicable attacks 48 | Security solutions
 DNS RACE CONDITIONS AND MAN-IN-THEMIDDLE • A lot of the high end attacks seem to be based on one of these two attacks • In a DNS race condition, the spooks are able to get a DNS response back to a workstation faster than the actual Internet can • This may be due to a local compromised device or network • This may also be because of implants at telecommunication companies (QUANTUM) • Similarly the telecom may redirect a user to a malicious site that appears to be legitimate but is actually under the control of an attacker (like a fake Facebook, or a real Facebook page that is passing through a proxy) • With their devices in the path, they can inject data into the connection, install malware, etc. 49 | Security solutions
DNS RACE CONDITIONS AND MAN-IN-THEMIDDLE • A lot of the high end attacks seem to be based on one of these two attacks • In a DNS race condition, the spooks are able to get a DNS response back to a workstation faster than the actual Internet can • This may be due to a local compromised device or network • This may also be because of implants at telecommunication companies (QUANTUM) • Similarly the telecom may redirect a user to a malicious site that appears to be legitimate but is actually under the control of an attacker (like a fake Facebook, or a real Facebook page that is passing through a proxy) • With their devices in the path, they can inject data into the connection, install malware, etc. 49 | Security solutions
 CELL PHONE TECHNOLOGY • I was going to talk about the technology available for cell phone monitoring but there isn’t really that much interesting there to talk about • Most of it is based on cell tower emulation (a cell phone Man in the Middle attack) in many varieties to find physical phones • Refer to: https: //theintercept. com/2015/12/17/a-secretcatalogue-of-government-gear-for-spying-on-your-cellphone/ • One trend to watch – Software Defined Radio • $30 RTL SDR USB devices and a lot of mojo • Several videos of people capturing packets with them and decrypting voice traffic on Youtube • See: https: //www. youtube. com/watch? v=Bf. Coi. ZRHTbk (example decryption walkthrough) • See: https: //www. youtube. com/watch? v=Zu. NOD 3 XWp 4 A (Def. Con 2013 on how RTL SDR works in general) 50 | Security solutions
CELL PHONE TECHNOLOGY • I was going to talk about the technology available for cell phone monitoring but there isn’t really that much interesting there to talk about • Most of it is based on cell tower emulation (a cell phone Man in the Middle attack) in many varieties to find physical phones • Refer to: https: //theintercept. com/2015/12/17/a-secretcatalogue-of-government-gear-for-spying-on-your-cellphone/ • One trend to watch – Software Defined Radio • $30 RTL SDR USB devices and a lot of mojo • Several videos of people capturing packets with them and decrypting voice traffic on Youtube • See: https: //www. youtube. com/watch? v=Bf. Coi. ZRHTbk (example decryption walkthrough) • See: https: //www. youtube. com/watch? v=Zu. NOD 3 XWp 4 A (Def. Con 2013 on how RTL SDR works in general) 50 | Security solutions
 A FUN ATTACK ON BITLOCKER • On November 17, 2015 it was reported that a way was discovered to bypass bitlocker encryption on systems that were joined to a domain (https: //www. blackhat. com/docs/eu-15/materials/eu-15 Haken-Bypassing-Local-Windows-Authentication-To-Defeat -Full-Disk-Encryption-wp. pdf) • On November 10 th, or possibly December 9 th Microsoft had issued a patch (MS 15 -122) that fixes this vulnerability • However, this attack can still be used on machines that have been seized and disconnected before 11/10/15 with the following caveats: 1. It must be domain joined 2. It must not use a PIN (pre-boot) authentication 3. It must not have been able to update 51 | Security solutions
A FUN ATTACK ON BITLOCKER • On November 17, 2015 it was reported that a way was discovered to bypass bitlocker encryption on systems that were joined to a domain (https: //www. blackhat. com/docs/eu-15/materials/eu-15 Haken-Bypassing-Local-Windows-Authentication-To-Defeat -Full-Disk-Encryption-wp. pdf) • On November 10 th, or possibly December 9 th Microsoft had issued a patch (MS 15 -122) that fixes this vulnerability • However, this attack can still be used on machines that have been seized and disconnected before 11/10/15 with the following caveats: 1. It must be domain joined 2. It must not use a PIN (pre-boot) authentication 3. It must not have been able to update 51 | Security solutions
 A FUN ATTACK ON BITLOCKER – HOW IT WORKS 1. Using the original hardware (the key is stored in the BIOS TPM module) connect the device to a standalone test network 2. Watch network traffic from the workstation to see it look for servers so that it can “check in” to its domain controllers and note the name of this device 3. Stand up a Windows domain controller with the exact same name. 4. Create an account with the account used on the laptop on this domain controller and set an arbitrary password on it 5. The workstation will connect to the domain controller and see that it has a new password for it and use this password 6. Use the password you set to log into the bitlockered system 52 | Security solutions
A FUN ATTACK ON BITLOCKER – HOW IT WORKS 1. Using the original hardware (the key is stored in the BIOS TPM module) connect the device to a standalone test network 2. Watch network traffic from the workstation to see it look for servers so that it can “check in” to its domain controllers and note the name of this device 3. Stand up a Windows domain controller with the exact same name. 4. Create an account with the account used on the laptop on this domain controller and set an arbitrary password on it 5. The workstation will connect to the domain controller and see that it has a new password for it and use this password 6. Use the password you set to log into the bitlockered system 52 | Security solutions
 A FUN ATTACK ON BITLOCKER – WHY IT WORKS • The issue is that the workstation is not checking to see that the domain controller is legitimate • You would think that it would be checking for more than just the server name before trusting it, but no • Some type of certificate trust must have been created when the workstation was domain joined, but it just wasn’t used • So, bust out all those old cases you could never get in to and you might have some luck! 53 | Security solutions
A FUN ATTACK ON BITLOCKER – WHY IT WORKS • The issue is that the workstation is not checking to see that the domain controller is legitimate • You would think that it would be checking for more than just the server name before trusting it, but no • Some type of certificate trust must have been created when the workstation was domain joined, but it just wasn’t used • So, bust out all those old cases you could never get in to and you might have some luck! 53 | Security solutions
 RESULTS FROM A CDW PASSWORD STUDY • Dave Reflexia from CDW’s Security Assessment Team (the hackers) has been compiling a list of passwords from both our customer engagements and from data dumps from hacks • He has performed analysis on this to identify the characteristics of passwords “in the wild” • Contains 933, 979, 289 password records • This is very helpful for efficiently cracking the passwords using tools such as ocl. Hash. Cat • https: //blog. cdw. com/security/password-security-report • Here are some interesting findings from the top 100 most common passwords: 54 | Security solutions
RESULTS FROM A CDW PASSWORD STUDY • Dave Reflexia from CDW’s Security Assessment Team (the hackers) has been compiling a list of passwords from both our customer engagements and from data dumps from hacks • He has performed analysis on this to identify the characteristics of passwords “in the wild” • Contains 933, 979, 289 password records • This is very helpful for efficiently cracking the passwords using tools such as ocl. Hash. Cat • https: //blog. cdw. com/security/password-security-report • Here are some interesting findings from the top 100 most common passwords: 54 | Security solutions
 RESULTS FROM A CDW PASSWORD STUDY • Passwords based on the season are popular: • Given any especially large user population, it is very likely to find someone who takes this approach • This often allows us to get in over the Internet if we can find enough valid usernames through search tools • Among the most popular are those formatted with the season, capitalized, followed by the full year, such as Summer 2014 (3930 occurrences) • Also popular was the same with a two-digit year such as Summer 14 (6126 occurrences) • You will note that only one of these variations, such as fall 15, is short of the default Windows password length of seven characters 55 | Security solutions
RESULTS FROM A CDW PASSWORD STUDY • Passwords based on the season are popular: • Given any especially large user population, it is very likely to find someone who takes this approach • This often allows us to get in over the Internet if we can find enough valid usernames through search tools • Among the most popular are those formatted with the season, capitalized, followed by the full year, such as Summer 2014 (3930 occurrences) • Also popular was the same with a two-digit year such as Summer 14 (6126 occurrences) • You will note that only one of these variations, such as fall 15, is short of the default Windows password length of seven characters 55 | Security solutions
 RESULTS FROM A CDW PASSWORD STUDY • Also popular are variations on the word password: • 21, 328 instances of the password “password” • Also popular was a capitalized version, with a one to three digit number at the end, such as Password 123 (19, 472 instances) • We see the perpetual trick of “leet speak” vowel substitution, which hasn’t been a fresh idea for at least fifteen years (12, 134) • Rounding out the top 100, were initial user passwords and help desk passwords. 34, 147 passwords containing a variation on the world welcome, with Welcome 1 topping out the list at 22, 538 instances • 4, 105 of passwords based on the word helpdesk, with good old “helpdesk” pulling in 1, 629 occurrences. 56 | Security solutions
RESULTS FROM A CDW PASSWORD STUDY • Also popular are variations on the word password: • 21, 328 instances of the password “password” • Also popular was a capitalized version, with a one to three digit number at the end, such as Password 123 (19, 472 instances) • We see the perpetual trick of “leet speak” vowel substitution, which hasn’t been a fresh idea for at least fifteen years (12, 134) • Rounding out the top 100, were initial user passwords and help desk passwords. 34, 147 passwords containing a variation on the world welcome, with Welcome 1 topping out the list at 22, 538 instances • 4, 105 of passwords based on the word helpdesk, with good old “helpdesk” pulling in 1, 629 occurrences. 56 | Security solutions
 RESULTS FROM A CDW PASSWORD STUDY • Some results on password size: Password Size Uniq # Found Most common password at this size 6 135, 819 123456 (2, 033) 7 273, 978 Sales 01 (3, 546) 8 534, 187 Welcome 1 (22, 538) 9 378, 426 Password 1 10 266, 857 [REDACTED] 11 132, 960 Change. Pass (1, 984) 12 79, 215 600000 500000 400000 Password Size 300000 Uniq # Found 200000 100000 0 1 2 3 4 5 6 7 • Having an 8 -character password is not surprising as it is the recommended default by Microsoft • If you know what your opponents minimum password size and complexity is you can greatly decrease the amount of time it will take to crack it 57 | Security solutions
RESULTS FROM A CDW PASSWORD STUDY • Some results on password size: Password Size Uniq # Found Most common password at this size 6 135, 819 123456 (2, 033) 7 273, 978 Sales 01 (3, 546) 8 534, 187 Welcome 1 (22, 538) 9 378, 426 Password 1 10 266, 857 [REDACTED] 11 132, 960 Change. Pass (1, 984) 12 79, 215 600000 500000 400000 Password Size 300000 Uniq # Found 200000 100000 0 1 2 3 4 5 6 7 • Having an 8 -character password is not surprising as it is the recommended default by Microsoft • If you know what your opponents minimum password size and complexity is you can greatly decrease the amount of time it will take to crack it 57 | Security solutions
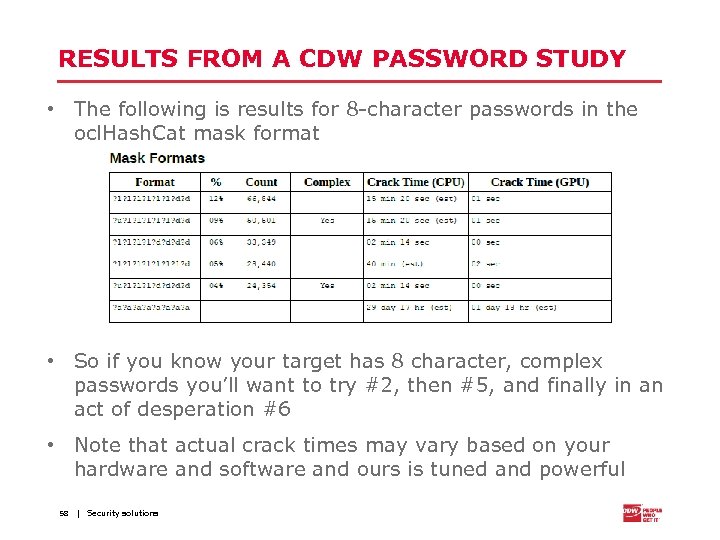 RESULTS FROM A CDW PASSWORD STUDY • The following is results for 8 -character passwords in the ocl. Hash. Cat mask format • So if you know your target has 8 character, complex passwords you’ll want to try #2, then #5, and finally in an act of desperation #6 • Note that actual crack times may vary based on your hardware and software and ours is tuned and powerful 58 | Security solutions
RESULTS FROM A CDW PASSWORD STUDY • The following is results for 8 -character passwords in the ocl. Hash. Cat mask format • So if you know your target has 8 character, complex passwords you’ll want to try #2, then #5, and finally in an act of desperation #6 • Note that actual crack times may vary based on your hardware and software and ours is tuned and powerful 58 | Security solutions
 RESULTS FROM A CDW PASSWORD STUDY • So how is this useful in a forensic investigation? • You may be able to get a password hash from their corporate environment, or figure out what the password requirement was at the time • It isn’t just Windows passwords, it could be anything – True. Crypt, 7 zip, PDF encryption, wireless pre-shared keys • Knowing that most the most common passwords are 8 characters and that the most likely mask is a word, capitalized, followed by 1 -3 numbers at the end, you can perform your “best chance” crack sometime this month • People also tend to reuse passwords – find other passwords they had through legal channels, crack them, and then try them on your target (such as whole disk encryption) 59 | Security solutions
RESULTS FROM A CDW PASSWORD STUDY • So how is this useful in a forensic investigation? • You may be able to get a password hash from their corporate environment, or figure out what the password requirement was at the time • It isn’t just Windows passwords, it could be anything – True. Crypt, 7 zip, PDF encryption, wireless pre-shared keys • Knowing that most the most common passwords are 8 characters and that the most likely mask is a word, capitalized, followed by 1 -3 numbers at the end, you can perform your “best chance” crack sometime this month • People also tend to reuse passwords – find other passwords they had through legal channels, crack them, and then try them on your target (such as whole disk encryption) 59 | Security solutions
 Q&A / ADDITIONAL DEMO • While Jeff Falcon gets set up…. • This preso: http: //lachniet. com/powerpoint/2016 -0127_MIHTCIA_Presentation-1. ppt • What I’m playing with: 1. The new secure HP printer line (giving it a test run) 2. My FLIR thermal imager 60 | Security solutions
Q&A / ADDITIONAL DEMO • While Jeff Falcon gets set up…. • This preso: http: //lachniet. com/powerpoint/2016 -0127_MIHTCIA_Presentation-1. ppt • What I’m playing with: 1. The new secure HP printer line (giving it a test run) 2. My FLIR thermal imager 60 | Security solutions


