696678cef3865f5db24c301dfff60b0b.ppt
- Количество слайдов: 43
 Radio Frequency Identification Foundations of Privacy 2010 Guy Katz
Radio Frequency Identification Foundations of Privacy 2010 Guy Katz
 Planned Topics Introduction to RFID How does it work Threats to user privacy Possible solutions
Planned Topics Introduction to RFID How does it work Threats to user privacy Possible solutions
 Introduction to RFID
Introduction to RFID
 Radio Frequency Identification “Wireless” Identification System Consists of ◦ Tag Small transponder Attached to a physical object ◦ Transceiver Reads (writes) data from tags Connected to some database
Radio Frequency Identification “Wireless” Identification System Consists of ◦ Tag Small transponder Attached to a physical object ◦ Transceiver Reads (writes) data from tags Connected to some database
 Origins RFID has been around for 60 years ◦ “Friend or Foe” systems in WW II: German pilots would roll their planes when coming back to base The British put basic transmitters on theirs Theft prevention (1970’s) ◦ Trucks in Los Alamos laboratory had transponders Toll payments Agriculture
Origins RFID has been around for 60 years ◦ “Friend or Foe” systems in WW II: German pilots would roll their planes when coming back to base The British put basic transmitters on theirs Theft prevention (1970’s) ◦ Trucks in Los Alamos laboratory had transponders Toll payments Agriculture
 Recent Developments A large increase in deployment since year 2000 Reasons: ◦ Tags and readers much smaller and cheaper ◦ World wide standardization (ISO)
Recent Developments A large increase in deployment since year 2000 Reasons: ◦ Tags and readers much smaller and cheaper ◦ World wide standardization (ISO)
 Current Uses Supply Chain Management ◦ From production to customer; replaces bar codes Payment systems ◦ Toll roads, cafeterias, Rav-Kav Access Control ◦ Weizmann Institute of Science Theft Prevention Anti-Counterfeiting ◦ Passports, Money Bills Implanted Tags
Current Uses Supply Chain Management ◦ From production to customer; replaces bar codes Payment systems ◦ Toll roads, cafeterias, Rav-Kav Access Control ◦ Weizmann Institute of Science Theft Prevention Anti-Counterfeiting ◦ Passports, Money Bills Implanted Tags
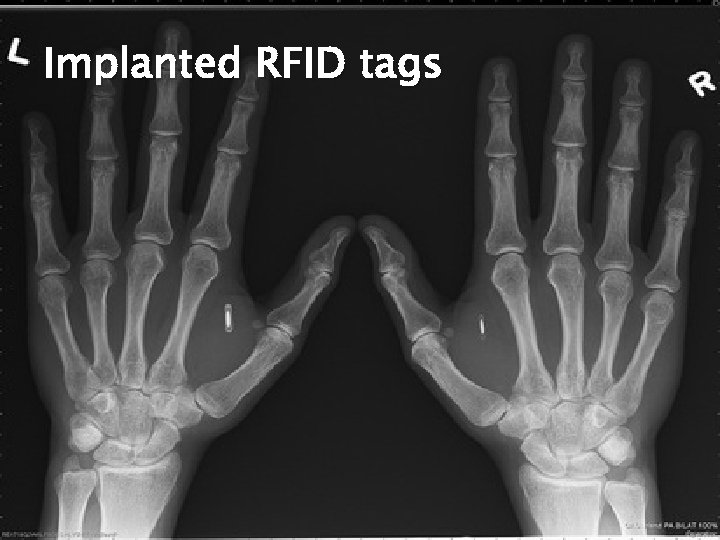 Implanted RFID tags
Implanted RFID tags
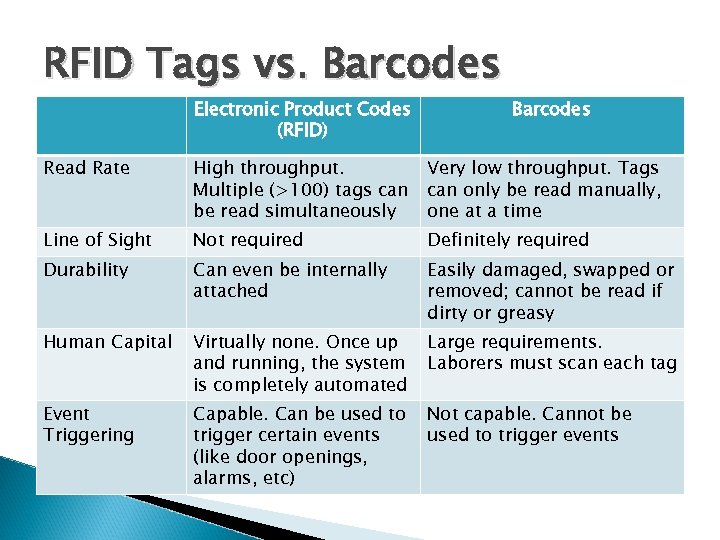 RFID Tags vs. Barcodes Electronic Product Codes (RFID) Barcodes Read Rate High throughput. Multiple (>100) tags can be read simultaneously Very low throughput. Tags can only be read manually, one at a time Line of Sight Not required Definitely required Durability Can even be internally attached Easily damaged, swapped or removed; cannot be read if dirty or greasy Human Capital Virtually none. Once up and running, the system is completely automated Large requirements. Laborers must scan each tag Event Triggering Capable. Can be used to trigger certain events (like door openings, alarms, etc) Not capable. Cannot be used to trigger events
RFID Tags vs. Barcodes Electronic Product Codes (RFID) Barcodes Read Rate High throughput. Multiple (>100) tags can be read simultaneously Very low throughput. Tags can only be read manually, one at a time Line of Sight Not required Definitely required Durability Can even be internally attached Easily damaged, swapped or removed; cannot be read if dirty or greasy Human Capital Virtually none. Once up and running, the system is completely automated Large requirements. Laborers must scan each tag Event Triggering Capable. Can be used to trigger certain events (like door openings, alarms, etc) Not capable. Cannot be used to trigger events
 How does it work?
How does it work?
 Tags Contain an antenna and a small circuit Purpose in life: broadcast an ID ◦ Usually 128 bits Very small - a few millimeters “Cost Barrier” – 5 cent per tag Two subgroups: ◦ Active Tags ◦ Passive Tags Integrated Circuit 4 x 4 mm
Tags Contain an antenna and a small circuit Purpose in life: broadcast an ID ◦ Usually 128 bits Very small - a few millimeters “Cost Barrier” – 5 cent per tag Two subgroups: ◦ Active Tags ◦ Passive Tags Integrated Circuit 4 x 4 mm
 Active Tags Can initiate communication on their own ◦ Transmit, looking for a reader Range can be over 100 meters Require a power source ◦ Consequently, expensive Active RFIF Tag Part of a monitoring system 6. 5 x 4 x 2 cm
Active Tags Can initiate communication on their own ◦ Transmit, looking for a reader Range can be over 100 meters Require a power source ◦ Consequently, expensive Active RFIF Tag Part of a monitoring system 6. 5 x 4 x 2 cm
 Passive Tags No power source ◦ Consequently, very cheap Energy extracted from RF signal Can’t initiate communication on their own ◦ Need to receive energy before they can answer Range up to 10 meters
Passive Tags No power source ◦ Consequently, very cheap Energy extracted from RF signal Can’t initiate communication on their own ◦ Need to receive energy before they can answer Range up to 10 meters
 Readers Power tags through RF signals Usually connected to some database Singulation (Anti-Collision) ◦ Communicate with many tags at once Still a bit expensive ◦ Cheapest ones around 500$
Readers Power tags through RF signals Usually connected to some database Singulation (Anti-Collision) ◦ Communicate with many tags at once Still a bit expensive ◦ Cheapest ones around 500$
 Singulation A method used by readers Goal: discover all present tags Difficulty: If many tags answer together, answers get mixed up The reader can’t separate their answers ◦ Does know that more than one tag responded Need a way to solve collisions…
Singulation A method used by readers Goal: discover all present tags Difficulty: If many tags answer together, answers get mixed up The reader can’t separate their answers ◦ Does know that more than one tag responded Need a way to solve collisions…
 Tree Walking The standard singulation protocol Each round, readers looks for a n-bit prefix ◦ Asks: “Who starts with 1010…? ” ◦ Tags answer with their next digit If multiple tags answer, recurse on both (n+1) bits prefixes For n tags and k identity bits, O(n*k) In practice, a few seconds for a shopping cart
Tree Walking The standard singulation protocol Each round, readers looks for a n-bit prefix ◦ Asks: “Who starts with 1010…? ” ◦ Tags answer with their next digit If multiple tags answer, recurse on both (n+1) bits prefixes For n tags and k identity bits, O(n*k) In practice, a few seconds for a shopping cart
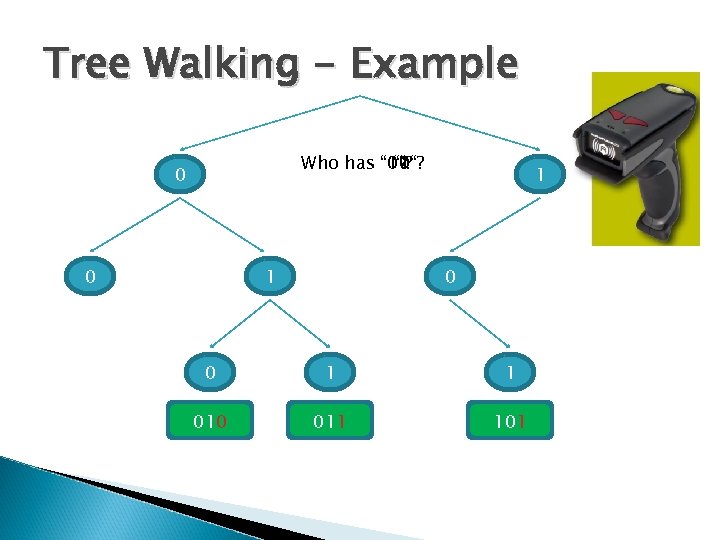 Tree Walking - Example Who has “ “? “ 01“? “ 00“? “ 10“? “ 1“? 0 0 1 1 010 011 101
Tree Walking - Example Who has “ “? “ 01“? “ 00“? “ 10“? “ 1“? 0 0 1 1 010 011 101
 Frequencies Various ranges ◦ From 120 KHz to 10. 6 GHz Dictate passive read range ◦ From 10 cm to 10 meters, accordingly. Can be used to ignore more distant tags
Frequencies Various ranges ◦ From 120 KHz to 10. 6 GHz Dictate passive read range ◦ From 10 cm to 10 meters, accordingly. Can be used to ignore more distant tags
 Threats to user privacy
Threats to user privacy
 Possible Attacks on RFID Sniffing/Eavesdropping Spoofing/Cloning Tracking Replay Denial Of Service Not all attacks related to privacy!
Possible Attacks on RFID Sniffing/Eavesdropping Spoofing/Cloning Tracking Replay Denial Of Service Not all attacks related to privacy!
 Privacy Concern – Unique Identification Tags contain an identification code EPC usually consists of 64 -128 bits ◦ Some bits indicate vendor and product ID ◦ Others form a unique product ID Tags becomes associated with a person! ◦ Don’t even need to know item type
Privacy Concern – Unique Identification Tags contain an identification code EPC usually consists of 64 -128 bits ◦ Some bits indicate vendor and product ID ◦ Others form a unique product ID Tags becomes associated with a person! ◦ Don’t even need to know item type
 Privacy Concern – Unique Identification (Continued) Reading is done silently and remotely Personal information can be gathered ◦ Information about individuals’ habits: where you go, what you buy… ◦ Physical tracking of people Military and Corporate Espionage ◦ Track down parts and components Implanted Tags ◦ Big Brother?
Privacy Concern – Unique Identification (Continued) Reading is done silently and remotely Personal information can be gathered ◦ Information about individuals’ habits: where you go, what you buy… ◦ Physical tracking of people Military and Corporate Espionage ◦ Track down parts and components Implanted Tags ◦ Big Brother?
 The Difficulty Need to keep the tags cheap A wide range of systems and uses ◦ No single solution suits everyone Need to only block malicious readings Defining the typical adversary ◦ What sort of equipment? Readers, tags, scanners, etc… ◦ What sort of abilities? Can impersonate a reader? Connect to the DB? ◦ Always present?
The Difficulty Need to keep the tags cheap A wide range of systems and uses ◦ No single solution suits everyone Need to only block malicious readings Defining the typical adversary ◦ What sort of equipment? Readers, tags, scanners, etc… ◦ What sort of abilities? Can impersonate a reader? Connect to the DB? ◦ Always present?
 Possible Solutions
Possible Solutions
 Our Scope We focus on EPC (Electronic Product Code) RFID tags Goal: prevent the adversary from associating a tag with a person
Our Scope We focus on EPC (Electronic Product Code) RFID tags Goal: prevent the adversary from associating a tag with a person
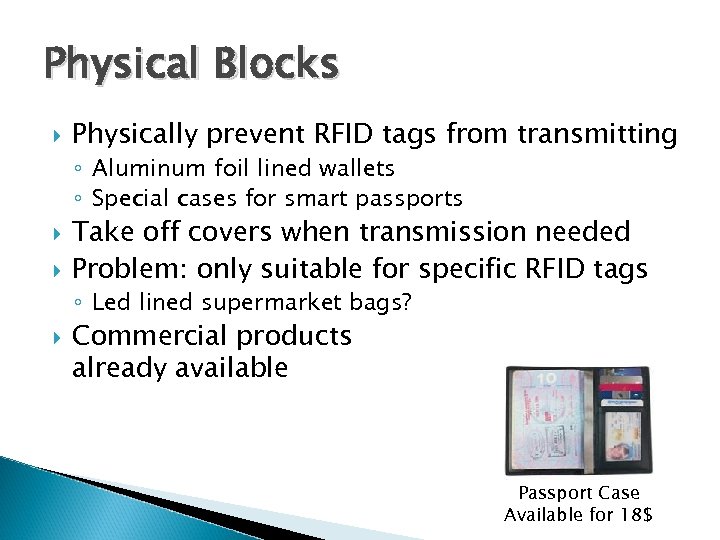 Physical Blocks Physically prevent RFID tags from transmitting ◦ Aluminum foil lined wallets ◦ Special cases for smart passports Take off covers when transmission needed Problem: only suitable for specific RFID tags ◦ Led lined supermarket bags? Commercial products already available Passport Case Available for 18$
Physical Blocks Physically prevent RFID tags from transmitting ◦ Aluminum foil lined wallets ◦ Special cases for smart passports Take off covers when transmission needed Problem: only suitable for specific RFID tags ◦ Led lined supermarket bags? Commercial products already available Passport Case Available for 18$
 Zombie Tags contain a “kill” command ◦ A supermarket might disable tags on checkout Zombie tags don’t answer readers Prevents association of people with their tags ◦ Covers most privacy concerns Problems: ◦ Some applications need the tag alive Alice’s milk carton Return products to stores Toll payment tags, implanted tags
Zombie Tags contain a “kill” command ◦ A supermarket might disable tags on checkout Zombie tags don’t answer readers Prevents association of people with their tags ◦ Covers most privacy concerns Problems: ◦ Some applications need the tag alive Alice’s milk carton Return products to stores Toll payment tags, implanted tags
 Privacy Bits An approach proposed by Juels and Brainard (2004) Tags broadcast a privacy bit – “its ok/not ok to read me” Problem: readers may choose to obey policy ◦ Corrupt readers risk being caught How does the owner configure the tags? Naïve solution…
Privacy Bits An approach proposed by Juels and Brainard (2004) Tags broadcast a privacy bit – “its ok/not ok to read me” Problem: readers may choose to obey policy ◦ Corrupt readers risk being caught How does the owner configure the tags? Naïve solution…
 The obvious answer… Crypto! Cryptographic solutions inherently expensive ◦ Require computational power ◦ Require more memory ◦ Sometimes require source of randomness Three approaches have been proposed: ◦ Hash-Lock ◦ Re-Encryption ◦ Silent Tree Walking So far, all too expensive to be practical ◦ But we’ll have a look anyway…
The obvious answer… Crypto! Cryptographic solutions inherently expensive ◦ Require computational power ◦ Require more memory ◦ Sometimes require source of randomness Three approaches have been proposed: ◦ Hash-Lock ◦ Re-Encryption ◦ Silent Tree Walking So far, all too expensive to be practical ◦ But we’ll have a look anyway…
 Hash-Lock (Weis et al, 2003) Similar to a password A tag can be locked by a reader ◦ Locked tags don’t transmit until unlocked ◦ Locked tags have an ID y ◦ Can only be unlocked by x s. t. h(x) = y h: standard one-way hash function The consumer knows x, can unlock at home When locked, cannot be associated with the owner
Hash-Lock (Weis et al, 2003) Similar to a password A tag can be locked by a reader ◦ Locked tags don’t transmit until unlocked ◦ Locked tags have an ID y ◦ Can only be unlocked by x s. t. h(x) = y h: standard one-way hash function The consumer knows x, can unlock at home When locked, cannot be associated with the owner
 Hash-Lock (Continuted) Problems: ◦ Tags still need to calculate h(x) Expensive… ◦ Many tags, hard to manage ◦ Consumer might not be aware of all the tags he’s carrying
Hash-Lock (Continuted) Problems: ◦ Tags still need to calculate h(x) Expensive… ◦ Many tags, hard to manage ◦ Consumer might not be aware of all the tags he’s carrying
 Re-Encryption (Juels & Pappu 2003) Mechanism to prevent counterfeiting of money bills The idea: ◦ ◦ Put an RFID tag inside the bill Every bill has a unique ID Encrypt the ID with a police public key Periodically re-encrypt it Can’t link different appearances of a given tag
Re-Encryption (Juels & Pappu 2003) Mechanism to prevent counterfeiting of money bills The idea: ◦ ◦ Put an RFID tag inside the bill Every bill has a unique ID Encrypt the ID with a police public key Periodically re-encrypt it Can’t link different appearances of a given tag
 Re-Encryption (Continued) Re-encryption done by external agents (in big stores, banks, etc) Problems: ◦ Costly infrastructure ◦ Burdensome process Often need to re-encrypt People naturally lazy ◦ Unclear just how effective the process is
Re-Encryption (Continued) Re-encryption done by external agents (in big stores, banks, etc) Problems: ◦ Costly infrastructure ◦ Burdensome process Often need to re-encrypt People naturally lazy ◦ Unclear just how effective the process is
 Silent Tree Walking (Weis et al, 2003) Readers use singulation protocols ◦ Most common: Tree Walking It is sufficient to eavesdrop the reader to identify the tag (up to last bit) A reader transmits much louder ◦ Can be “heard” from further away The idea: encrypt the reader’s requests ◦ Makes eavesdropping harder
Silent Tree Walking (Weis et al, 2003) Readers use singulation protocols ◦ Most common: Tree Walking It is sufficient to eavesdrop the reader to identify the tag (up to last bit) A reader transmits much louder ◦ Can be “heard” from further away The idea: encrypt the reader’s requests ◦ Makes eavesdropping harder
 Silent Tree Walking (Continued) Problem: How to encrypt? ◦ Tags have limited resources and no randomness ◦ Need a shared reader-tag key beforehand ◦ Makes the system impractical Still, might be useful combined with other solutions…
Silent Tree Walking (Continued) Problem: How to encrypt? ◦ Tags have limited resources and no randomness ◦ Need a shared reader-tag key beforehand ◦ Makes the system impractical Still, might be useful combined with other solutions…
 Blocker Tags (Juels, Rivest and Szydlo, 2003) Using an exterior device to block tag readers Enables a user to block the adversary ◦ One blocker suffices for all tags ◦ Cheap Same price as a tag Don’t have to change existing RFID tags Can turn off at home…
Blocker Tags (Juels, Rivest and Szydlo, 2003) Using an exterior device to block tag readers Enables a user to block the adversary ◦ One blocker suffices for all tags ◦ Cheap Same price as a tag Don’t have to change existing RFID tags Can turn off at home…
 How do blocker tags work? The idea: disrupt the singulation protocol ◦ Trick the reader - make it think all tags are present ◦ Makes reading useless For instance, a tag that disrupts the tree walking algorithm ◦ Always answers both 0 and 1 Might require two antennas ◦ The reader doesn’t know which tags exist
How do blocker tags work? The idea: disrupt the singulation protocol ◦ Trick the reader - make it think all tags are present ◦ Makes reading useless For instance, a tag that disrupts the tree walking algorithm ◦ Always answers both 0 and 1 Might require two antennas ◦ The reader doesn’t know which tags exist
 Partial Blocking – Private Branch The blocker will disrupt any reading around it Can be configured to only disrupt “private branches” ◦ Specific ID’s defined as private ◦ Readers have no right to read them… Can change the tree walking algorithm to avoid unneeded queries
Partial Blocking – Private Branch The blocker will disrupt any reading around it Can be configured to only disrupt “private branches” ◦ Specific ID’s defined as private ◦ Readers have no right to read them… Can change the tree walking algorithm to avoid unneeded queries
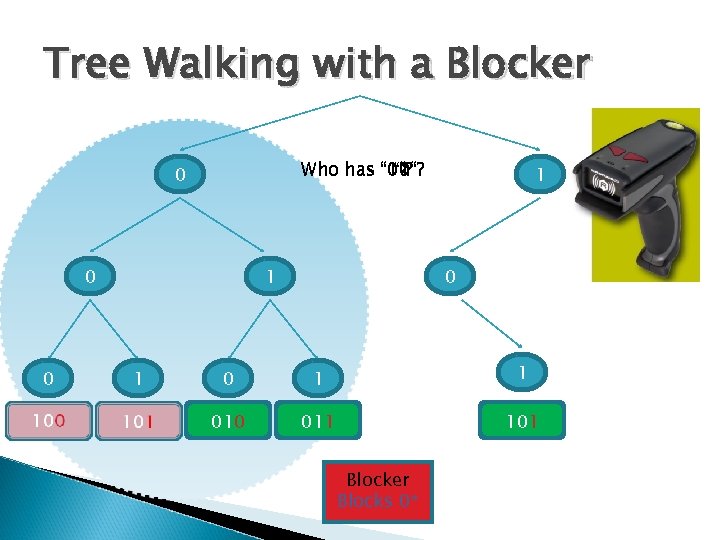 Tree Walking with a Blocker Who has “ “? “ 01“? “ 10“? “ 1“? “ 00“? “ 0“? 0 0 0 1 1 1 0 0 1 1 010 011 101 Blocker Blocks 0*
Tree Walking with a Blocker Who has “ “? “ 01“? “ 10“? “ 1“? “ 00“? “ 0“? 0 0 0 1 1 1 0 0 1 1 010 011 101 Blocker Blocks 0*
 Other Blocker Tag Issues Can the blocker itself pose a privacy breech? ◦ Can track a unique “private zone” ◦ Allow only a few privacy policies? Bob’s blocker may disrupt Alice’s readings ◦ Can use a random “private zone” to avoid conflicts ◦ Tradeoff with the previous bullet Tailored for the tree walking algorithm ◦ However, should be adjustable to any other algorithm as well Can be used in Denial of Service attacks
Other Blocker Tag Issues Can the blocker itself pose a privacy breech? ◦ Can track a unique “private zone” ◦ Allow only a few privacy policies? Bob’s blocker may disrupt Alice’s readings ◦ Can use a random “private zone” to avoid conflicts ◦ Tradeoff with the previous bullet Tailored for the tree walking algorithm ◦ However, should be adjustable to any other algorithm as well Can be used in Denial of Service attacks
 Conclusions RFID is becoming cheap and widespread It can easily disclose private information Partial solutions: ◦ Physical blocks ◦ Zombie tags ◦ Privacy Bits Encryption schemes are effective, but require expensive tags and infrastructure ◦ Only suitable for specific cases Blocker tags are a cheap, effective solution for EPC RFID tags
Conclusions RFID is becoming cheap and widespread It can easily disclose private information Partial solutions: ◦ Physical blocks ◦ Zombie tags ◦ Privacy Bits Encryption schemes are effective, but require expensive tags and infrastructure ◦ Only suitable for specific cases Blocker tags are a cheap, effective solution for EPC RFID tags
 Thank you!
Thank you!
 References “Squealing Euros: Privacy-Protection in RFIDEnabled Banknotes” by Juels and Pappu, 2003 “Security and Privacy Aspects of Low-Cost Radio Frequency Identification Systems” by Weis et al, 2003 “Selective Blocking of RFID Tags for Consumer Privacy” by Juels, Rivest & Szydlo, 2003 “RFID Privacy: An Overview of Problems and Proposed Solutions” by Garfinkel, Juels & Pappu, 2005 “RFID”, presentation by Alon Rosen
References “Squealing Euros: Privacy-Protection in RFIDEnabled Banknotes” by Juels and Pappu, 2003 “Security and Privacy Aspects of Low-Cost Radio Frequency Identification Systems” by Weis et al, 2003 “Selective Blocking of RFID Tags for Consumer Privacy” by Juels, Rivest & Szydlo, 2003 “RFID Privacy: An Overview of Problems and Proposed Solutions” by Garfinkel, Juels & Pappu, 2005 “RFID”, presentation by Alon Rosen


