220c5a9abf721a1797247cc3a5bf6c4b.ppt
- Количество слайдов: 17
 Quiz 1 Topics ECE 6612 - Computer Network Security Feb. 19, Spring 2016 These slides are in http: //www. csc. gatech. edu/copeland/jac/6612/slides/ Click on “ 05 Quiz-1 topics. ppt” Past Quizzes and Answers are in “Resources” on T-square/ You may bring one 8. 5” by 11” reference sheet to the quiz. It must be handwritten by you. Both sides are available. Otherwise, pencil or pen, and a simple calculator only (no stored text or wireless access).
Quiz 1 Topics ECE 6612 - Computer Network Security Feb. 19, Spring 2016 These slides are in http: //www. csc. gatech. edu/copeland/jac/6612/slides/ Click on “ 05 Quiz-1 topics. ppt” Past Quizzes and Answers are in “Resources” on T-square/ You may bring one 8. 5” by 11” reference sheet to the quiz. It must be handwritten by you. Both sides are available. Otherwise, pencil or pen, and a simple calculator only (no stored text or wireless access).
 Chapter 1 - Intro Definitions and examples: Security Attacks (Spoofing, Interception, Trojan Horse, Bot, Worm, IP & Port Scanning, Sniffing, Root Kit, Spam, Malware, . . . ) Services (below, P & 4 A’s) & Mechanisms (e. g. , Encryption) Privacy (Secrecy) Authentication (Identification & Nonrepudiation) Authorization (limit access based on Authentication) Alteration Protection - Integrity Availability (avoid Denial of Service Attacks) Combination of Authentication and Authorization: Access Control (good password, use of hashes) RFC's (IETF “Request for Comments”) IEEE (802. x LANs), ISO (X. 509 Cert), NIST (AES Encryption) Defenses (Firewalls, Virus Detection, Honey Pots or Honey Nets, …) 1 st of 3 Basic Rules: No Security without physical (access) security. 2
Chapter 1 - Intro Definitions and examples: Security Attacks (Spoofing, Interception, Trojan Horse, Bot, Worm, IP & Port Scanning, Sniffing, Root Kit, Spam, Malware, . . . ) Services (below, P & 4 A’s) & Mechanisms (e. g. , Encryption) Privacy (Secrecy) Authentication (Identification & Nonrepudiation) Authorization (limit access based on Authentication) Alteration Protection - Integrity Availability (avoid Denial of Service Attacks) Combination of Authentication and Authorization: Access Control (good password, use of hashes) RFC's (IETF “Request for Comments”) IEEE (802. x LANs), ISO (X. 509 Cert), NIST (AES Encryption) Defenses (Firewalls, Virus Detection, Honey Pots or Honey Nets, …) 1 st of 3 Basic Rules: No Security without physical (access) security. 2
 Chapter 2 - Cryptography Conventional (Secret-Key), cryptographer vs. cryptanalyst , plaintext, ciphertext, decrypt vs. decipher, number of possible keys (time for exhaustive search), characteristics of good encryption and random numbers. Feistel structure: DES, 3 -DES, Blowfish (but not AES) Crypto-feedback: CBC, CFB, Streaming-mode Key distribution, use of a session key (why). Concept of Information Entropy (encryption, compression) Use of redundancy to recognize plaintext and break codes (Caesar codes, substitution codes, block codes). Self-synchronizing codes (pros and cons), link versus end-to-end encryption. Prove quality of encryption technique (Fundamental Tenet)? Hash algorithms: output same size, one-way, weak or strong collision resistance. How are they used, which are safe today: Not Safe: MD 5, SHA(-1) Safe: SHA-2 (SHA-256 or SHA-512), SHA -3. 3
Chapter 2 - Cryptography Conventional (Secret-Key), cryptographer vs. cryptanalyst , plaintext, ciphertext, decrypt vs. decipher, number of possible keys (time for exhaustive search), characteristics of good encryption and random numbers. Feistel structure: DES, 3 -DES, Blowfish (but not AES) Crypto-feedback: CBC, CFB, Streaming-mode Key distribution, use of a session key (why). Concept of Information Entropy (encryption, compression) Use of redundancy to recognize plaintext and break codes (Caesar codes, substitution codes, block codes). Self-synchronizing codes (pros and cons), link versus end-to-end encryption. Prove quality of encryption technique (Fundamental Tenet)? Hash algorithms: output same size, one-way, weak or strong collision resistance. How are they used, which are safe today: Not Safe: MD 5, SHA(-1) Safe: SHA-2 (SHA-256 or SHA-512), SHA -3. 3
 Chapter 3 - Public-Key and Authentication Role of trusted authority (CA) - who (is/are) the top level CA(s). How does your browser use them. Man-in-the-middle attack (when is it effective, how do you defeat it). MAC and MIC, one-way hashes (desired characteristics) RSA and Diffie-Hellman (basic operation), uses. How does modulo arithmetic simplify calculations, add to security? RSA security depends on the difficulty of factoring large prime numbers. Digital Signatures, certificates, CA, Web transactions. PKI (Public Key Infrastructure): What is needed besides distribution of Public-Private Keys? (Revocation database). Email Encryption and Signing: Use of session key per message and it’s encryption with each recipient’s Public Key. 4
Chapter 3 - Public-Key and Authentication Role of trusted authority (CA) - who (is/are) the top level CA(s). How does your browser use them. Man-in-the-middle attack (when is it effective, how do you defeat it). MAC and MIC, one-way hashes (desired characteristics) RSA and Diffie-Hellman (basic operation), uses. How does modulo arithmetic simplify calculations, add to security? RSA security depends on the difficulty of factoring large prime numbers. Digital Signatures, certificates, CA, Web transactions. PKI (Public Key Infrastructure): What is needed besides distribution of Public-Private Keys? (Revocation database). Email Encryption and Signing: Use of session key per message and it’s encryption with each recipient’s Public Key. 4
 Chapter 4 - Authentication Applications Kerberos: How is user (person) authenticated, tickets, role of KDC, and Nonce (replay attack). How does it solve the key distribution problem for n*(n-1)/2 pairs of hosts. X. 509 Authentication (certificates, steps of a Web buy) Review slides from Feb. 4, 2013 lecture – “ 07 b-SSL_TLS 2013. pdf” Chain of authentication (CA hierarchy). Theory and Practice Certificate Authority (who, where found) Digital Signature - how is it done, what does it do? SSH (SCP and SFTP): How do they securely replace Telnet and FTP? What’s needed to allow secure login without a password? What is an “SSH Tunnel”? How are passwords safely stored, and compared to typed-in password? What is a Dictionary Attack, and how is it foiled? How are keys safely stored on a computer, and accessed? 5
Chapter 4 - Authentication Applications Kerberos: How is user (person) authenticated, tickets, role of KDC, and Nonce (replay attack). How does it solve the key distribution problem for n*(n-1)/2 pairs of hosts. X. 509 Authentication (certificates, steps of a Web buy) Review slides from Feb. 4, 2013 lecture – “ 07 b-SSL_TLS 2013. pdf” Chain of authentication (CA hierarchy). Theory and Practice Certificate Authority (who, where found) Digital Signature - how is it done, what does it do? SSH (SCP and SFTP): How do they securely replace Telnet and FTP? What’s needed to allow secure login without a password? What is an “SSH Tunnel”? How are passwords safely stored, and compared to typed-in password? What is a Dictionary Attack, and how is it foiled? How are keys safely stored on a computer, and accessed? 5
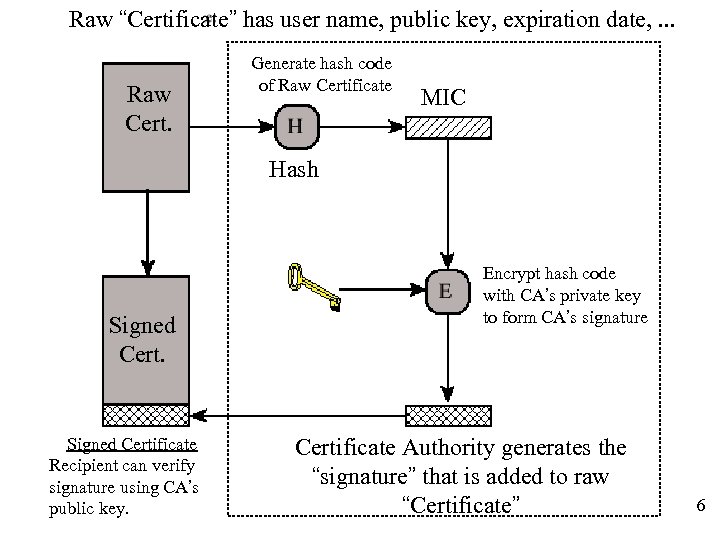 Raw “Certificate” has user name, public key, expiration date, . . . Raw Cert. Generate hash code of Raw Certificate MIC Hash Signed Certificate Recipient can verify signature using CA’s public key. Encrypt hash code with CA’s private key to form CA’s signature Certificate Authority generates the “signature” that is added to raw “Certificate” 6
Raw “Certificate” has user name, public key, expiration date, . . . Raw Cert. Generate hash code of Raw Certificate MIC Hash Signed Certificate Recipient can verify signature using CA’s public key. Encrypt hash code with CA’s private key to form CA’s signature Certificate Authority generates the “signature” that is added to raw “Certificate” 6
 Email Privacy Establishing Keys • Public Key Certification • Exchange Public Keys Multiple Recipients • Encrypt message m with session key, S • Encrypt S with each recipient's key • Send: {S; Kbob}, {S; Kann}, . . . , {m; S} Authentication of Source (digital signatures) • Hash (MD 5, SHA 2) of message, encrypted with signer's private key. Check by decrypting with signer's public key, and compare to new hash. 7
Email Privacy Establishing Keys • Public Key Certification • Exchange Public Keys Multiple Recipients • Encrypt message m with session key, S • Encrypt S with each recipient's key • Send: {S; Kbob}, {S; Kann}, . . . , {m; S} Authentication of Source (digital signatures) • Hash (MD 5, SHA 2) of message, encrypted with signer's private key. Check by decrypting with signer's public key, and compare to new hash. 7
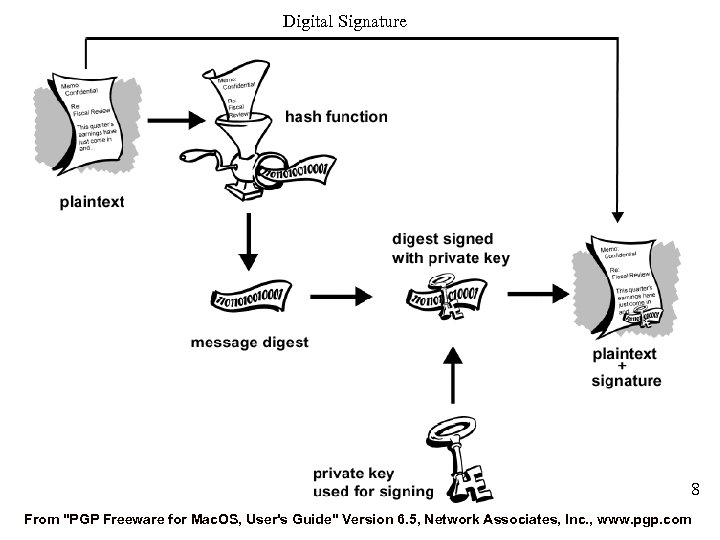 Digital Signature 8 From "PGP Freeware for Mac. OS, User's Guide" Version 6. 5, Network Associates, Inc. , www. pgp. com
Digital Signature 8 From "PGP Freeware for Mac. OS, User's Guide" Version 6. 5, Network Associates, Inc. , www. pgp. com
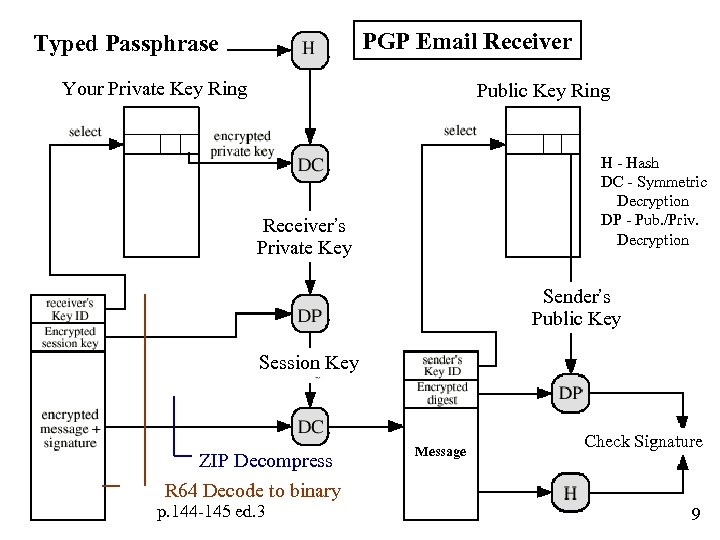 PGP Email Receiver Typed Passphrase Your Private Key Ring Public Key Ring H - Hash DC - Symmetric Decryption DP - Pub. /Priv. Decryption Receiver’s Private Key Sender’s Public Key Session Key ZIP Decompress R 64 Decode to binary p. 144 -145 ed. 3 Message Check Signature 9
PGP Email Receiver Typed Passphrase Your Private Key Ring Public Key Ring H - Hash DC - Symmetric Decryption DP - Pub. /Priv. Decryption Receiver’s Private Key Sender’s Public Key Session Key ZIP Decompress R 64 Decode to binary p. 144 -145 ed. 3 Message Check Signature 9
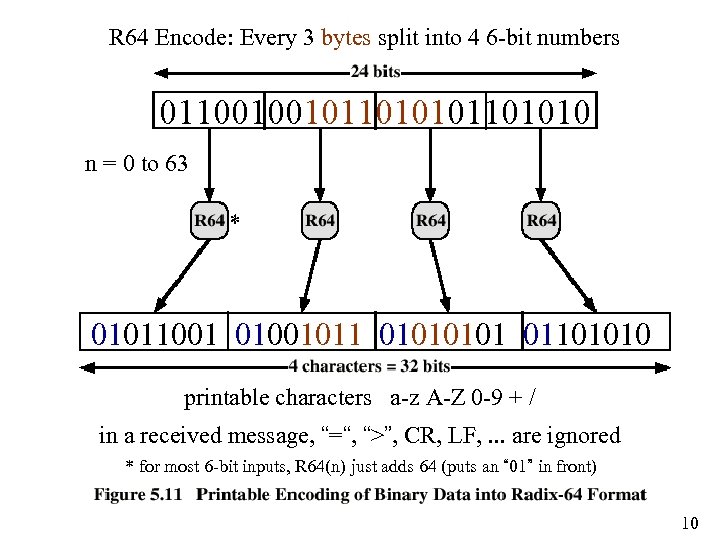 R 64 Encode: Every 3 bytes split into 4 6 -bit numbers 01100100101101010 n = 0 to 63 * 01011001 01001011 0101 01101010 printable characters a-z A-Z 0 -9 + / in a received message, “=“, “>”, CR, LF, . . . are ignored * for most 6 -bit inputs, R 64(n) just adds 64 (puts an “ 01” in front) 10
R 64 Encode: Every 3 bytes split into 4 6 -bit numbers 01100100101101010 n = 0 to 63 * 01011001 01001011 0101 01101010 printable characters a-z A-Z 0 -9 + / in a received message, “=“, “>”, CR, LF, . . . are ignored * for most 6 -bit inputs, R 64(n) just adds 64 (puts an “ 01” in front) 10
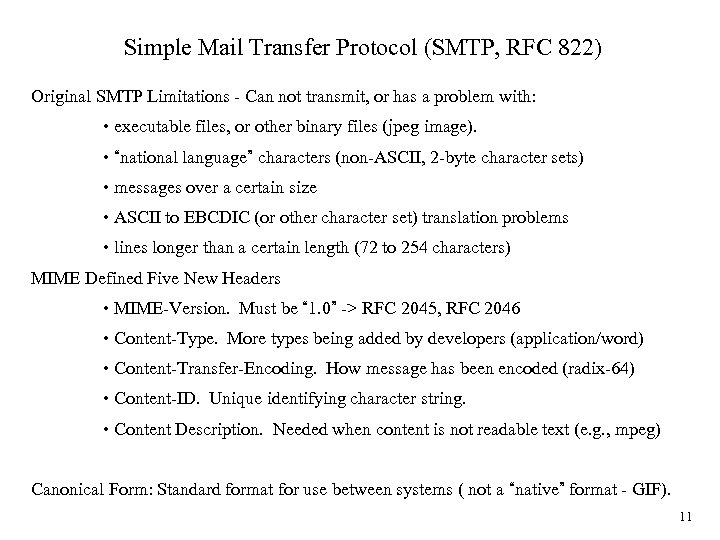 Simple Mail Transfer Protocol (SMTP, RFC 822) Original SMTP Limitations - Can not transmit, or has a problem with: • executable files, or other binary files (jpeg image). • “national language” characters (non-ASCII, 2 -byte character sets) • messages over a certain size • ASCII to EBCDIC (or other character set) translation problems • lines longer than a certain length (72 to 254 characters) MIME Defined Five New Headers • MIME-Version. Must be “ 1. 0” -> RFC 2045, RFC 2046 • Content-Type. More types being added by developers (application/word) • Content-Transfer-Encoding. How message has been encoded (radix-64) • Content-ID. Unique identifying character string. • Content Description. Needed when content is not readable text (e. g. , mpeg) Canonical Form: Standard format for use between systems ( not a “native” format - GIF). 11
Simple Mail Transfer Protocol (SMTP, RFC 822) Original SMTP Limitations - Can not transmit, or has a problem with: • executable files, or other binary files (jpeg image). • “national language” characters (non-ASCII, 2 -byte character sets) • messages over a certain size • ASCII to EBCDIC (or other character set) translation problems • lines longer than a certain length (72 to 254 characters) MIME Defined Five New Headers • MIME-Version. Must be “ 1. 0” -> RFC 2045, RFC 2046 • Content-Type. More types being added by developers (application/word) • Content-Transfer-Encoding. How message has been encoded (radix-64) • Content-ID. Unique identifying character string. • Content Description. Needed when content is not readable text (e. g. , mpeg) Canonical Form: Standard format for use between systems ( not a “native” format - GIF). 11
 Investigating Email You Receive Look at “Raw” or “Source” Message to see: Headers (from? -“Received: ” headers (IP, time zone) HTML Links (where they will take you) Investigate Source (who sent it) Lowest "Received: ” header Active Links in , {text} Images (can compromise, or “Web Bug”) in
Investigating Email You Receive Look at “Raw” or “Source” Message to see: Headers (from? -“Received: ” headers (IP, time zone) HTML Links (where they will take you) Investigate Source (who sent it) Lowest "Received: ” header Active Links in , {text} Images (can compromise, or “Web Bug”) in Programs to Use nslookup (dig, host) - IP from URL, or URL from IP whois - Register of domain (not URL) traceroute - path of packets through routers Configure email reader to not download links automatically 12
 Summary - Problems and Solutions 64 -bit Keys can be found by a Brute-Force Attack Use a 128 -bit or larger key. Code-book encrypting allows interchange and duplication of blocks Use Cipher-Block Chaining (Crypto-Feedback). The same Plaintext encrypted with the same key = same Ciphertext Use a random, non-repeating Initial Vector. How do you know the Ciphertext was not altered? Include a Message Digest (Hash of Plaintext ). How do you know the authenticity of the sender? Encrypt the Message Digest with the sender’s Private Key (3). How do you manage encryption keys securely and efficiently? Key Management System (Kerberos) (4 a) X. 509 Certificates (SSL) – high level covered, and in talk on Monday PGP Email (5 a) – only high level covered PKI (Public Key Infrastructure) (3) CA, Revocation Database. How do you authenticate passwords without storing them on the computer? Store crypto-hashes of the passwords (with “Salt”) 13
Summary - Problems and Solutions 64 -bit Keys can be found by a Brute-Force Attack Use a 128 -bit or larger key. Code-book encrypting allows interchange and duplication of blocks Use Cipher-Block Chaining (Crypto-Feedback). The same Plaintext encrypted with the same key = same Ciphertext Use a random, non-repeating Initial Vector. How do you know the Ciphertext was not altered? Include a Message Digest (Hash of Plaintext ). How do you know the authenticity of the sender? Encrypt the Message Digest with the sender’s Private Key (3). How do you manage encryption keys securely and efficiently? Key Management System (Kerberos) (4 a) X. 509 Certificates (SSL) – high level covered, and in talk on Monday PGP Email (5 a) – only high level covered PKI (Public Key Infrastructure) (3) CA, Revocation Database. How do you authenticate passwords without storing them on the computer? Store crypto-hashes of the passwords (with “Salt”) 13
 The test will also cover these slide sets: 05 a-PGP-Email. ppt (encrypt, sign, armor [base 64]) 05 c-Phishing Email. ppt (information in headers*) 05 e-Plain Text Email. ppt (how to view raw email) 06 -IP Networks. ppt (Through Slide 9) Ethernet Addresses (how far do they go? ), ARP (ARP spoofing – Man-in-the-Middle) AS (Autonomous System) Routing Protocols: OSPF within AS, BGP between AS) * Know uses of: nslookup, whois, traceroute, google. 14
The test will also cover these slide sets: 05 a-PGP-Email. ppt (encrypt, sign, armor [base 64]) 05 c-Phishing Email. ppt (information in headers*) 05 e-Plain Text Email. ppt (how to view raw email) 06 -IP Networks. ppt (Through Slide 9) Ethernet Addresses (how far do they go? ), ARP (ARP spoofing – Man-in-the-Middle) AS (Autonomous System) Routing Protocols: OSPF within AS, BGP between AS) * Know uses of: nslookup, whois, traceroute, google. 14
 Homework Problems Answers are posted in “Resources” on T-square HW_1 Five basic Security Services, Mechanisms to provide those services Safer use of the Internet with email configuration, and HTTPS use. HW-2 – Basic Principles, Brute Force Attack, Entropy All encrypted messages can be deciphered by a brute-force attack. The time it takes (1) depends of the state-of-the-art in computers and special integrated circuits, and (2) the number of possible keys (= 2^entropy). For a random binary number with N bits, the entropy = N. For a mixed password with different classes of symbols, the entropy is the sum of the entropy of the elements. 15
Homework Problems Answers are posted in “Resources” on T-square HW_1 Five basic Security Services, Mechanisms to provide those services Safer use of the Internet with email configuration, and HTTPS use. HW-2 – Basic Principles, Brute Force Attack, Entropy All encrypted messages can be deciphered by a brute-force attack. The time it takes (1) depends of the state-of-the-art in computers and special integrated circuits, and (2) the number of possible keys (= 2^entropy). For a random binary number with N bits, the entropy = N. For a mixed password with different classes of symbols, the entropy is the sum of the entropy of the elements. 15
 HW-2 (cont. ) If W is a word from a list of 40, 000, then the entropy of a single word is: entropy(W) = log 2( 40, 000) = log 10 (40, 000)/log 10(2) = 4. 6 / 0. 3 = 15. 3 If a password is Wp. W where p is one of 16 punctuation characters: entropy(Wp. W) = 15. 3 + 4 + 15. 3 = 34. 6 bits To convert entropy to the number of possibilities M in decimal: M = 2^entropy = 2^34. 6 = 2. 6 e 10 possibilities A brute force attack would take M / [number of tries per hour] hours. To be very safe today, a password should have about 120 bits of entropy. HW-3 – Use of Public/Private Keys, RSA, Diffie-Hellman, Kerberos, Secure Hashes. 16
HW-2 (cont. ) If W is a word from a list of 40, 000, then the entropy of a single word is: entropy(W) = log 2( 40, 000) = log 10 (40, 000)/log 10(2) = 4. 6 / 0. 3 = 15. 3 If a password is Wp. W where p is one of 16 punctuation characters: entropy(Wp. W) = 15. 3 + 4 + 15. 3 = 34. 6 bits To convert entropy to the number of possibilities M in decimal: M = 2^entropy = 2^34. 6 = 2. 6 e 10 possibilities A brute force attack would take M / [number of tries per hour] hours. To be very safe today, a password should have about 120 bits of entropy. HW-3 – Use of Public/Private Keys, RSA, Diffie-Hellman, Kerberos, Secure Hashes. 16
 Old quizzes are posted in “Resources” on T-square Rules: i This quiz is closed book. One sheet of notes (8. 5"x 11") may be used (both sides, your handwriting only). Pen or pencil, and a simple calculator are allowed. ii Answer all questions and show all work to receive full credit. iii Each regular sub-question counts 4 points (4 deducted from 100 for each missed question) unless otherwise noted. iv Please do not ask the proctors any questions during the exam about exam questions. Part of the test is understanding the question, as written, without supplemental information. If you feel additional data is needed to solve the problem, make (and state) an assumption and then work the problem. v. This is a time-limited test. All papers must be turned in 45 minutes after the start. If you find you are taking more than 10 minutes on a particular problem, move on and come back to that problem after finishing the others. The Georgia Honor Code applies (see last page). Answers should be 1 to 3 words, or a number (no essays, please). 17
Old quizzes are posted in “Resources” on T-square Rules: i This quiz is closed book. One sheet of notes (8. 5"x 11") may be used (both sides, your handwriting only). Pen or pencil, and a simple calculator are allowed. ii Answer all questions and show all work to receive full credit. iii Each regular sub-question counts 4 points (4 deducted from 100 for each missed question) unless otherwise noted. iv Please do not ask the proctors any questions during the exam about exam questions. Part of the test is understanding the question, as written, without supplemental information. If you feel additional data is needed to solve the problem, make (and state) an assumption and then work the problem. v. This is a time-limited test. All papers must be turned in 45 minutes after the start. If you find you are taking more than 10 minutes on a particular problem, move on and come back to that problem after finishing the others. The Georgia Honor Code applies (see last page). Answers should be 1 to 3 words, or a number (no essays, please). 17


