213c201280490751951638869a984fe5.ppt
- Количество слайдов: 22

® Qualys. Guard Vulnerability Analysis – The new Frontier of Security by Tom Clare Director, Channel Marketing Dataway Seminar San Francisco, 26 June 2002 Securing Your Network

Agenda § Company Background/Team § Vulnerability Assessment § Qualys. Guard - Product Family Internet Scanner Live Demonstration Product Enhancements § Q&A Securing Your Network
Qualys Company Background § Single focus on Vulnerability Assessment Highly Scalable Web Service Platform Most Comprehensive Vulnerability Database – Daily Updates Live since May 2000, run rate of 32, 000+ scans per month § 525+ customers growing at 25+ per month, includes: § Adobe, Apple, HP, Siebel, Agilent, Cartier, L’Oreal, Bank of the West, First State Bank, Cincinnati Children’s Hospital, Veri. Sign, Web Power Associates, Tower Records, Broadwing, BASF, Generali… § Founded in March 1999 90 Employees, 45 in R&D Global offices in US, France, Germany and UK § $40 M in funding Trident Capital, Deutch Bank ABS Ventures, Mercury Interactive and Veri. Sign § Headquartered in Redwood Shores, CA Securing Your Network
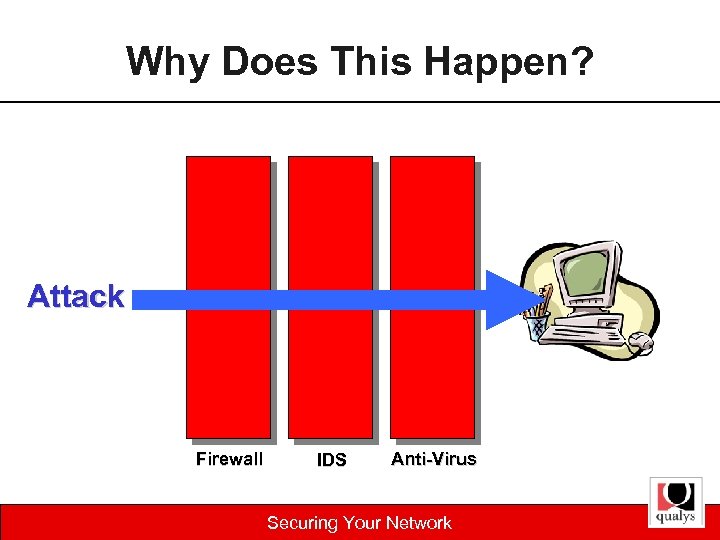
Why Does This Happen? Attack Firewall IDS Anti-Virus Securing Your Network

Why Vulnerability Assessment ? “ 99% of intrusions result from exploitation of known vulnerabilities or configuration errors where countermeasures were available” Source: 2001 CERT, Carnegie Mellon University “In 2001, more than 30 vulnerabilities were discovered each week” (compared to 5 vulnerabilities discovered per week in 1998) Source: 2001 Forrester Research Securing Your Network
The worm. sdsc. edu Project § Experiment: Attaching and monitoring a “default installed” system on the Internet § After 8 hours first probe for rpc vulnerabilities was detected § Within a few days over 20 exploit attempts § A few weeks later the system was completely compromised and a network sniffer was installed by an attacker Securing Your Network
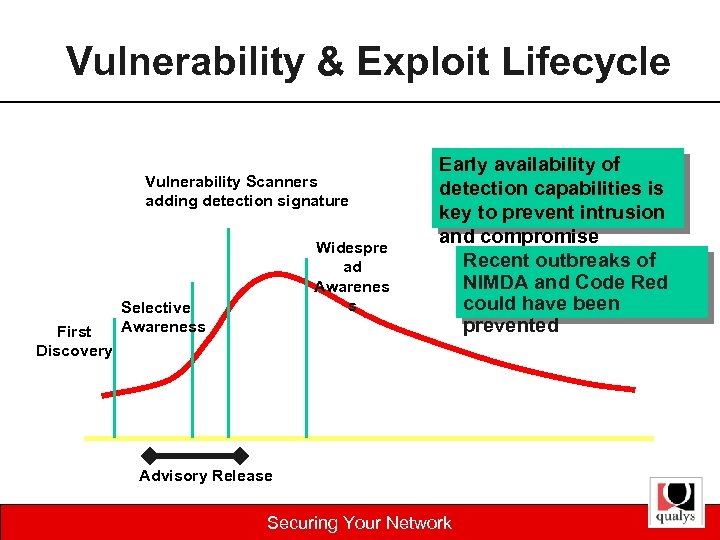
Vulnerability & Exploit Lifecycle Vulnerability Scanners adding detection signature First Discovery Widespre ad Awarenes s Selective Awareness Early availability of detection capabilities is key to prevent intrusion and compromise Recent outbreaks of NIMDA and Code Red could have been prevented Advisory Release Securing Your Network

Compromise is Costly § Compromised systems may not be immediately identified § To fully recover a compromised system, it must be taken offline § Downtime of critical servers § Time invested by administrators § To restore the integrity of the system it must be validated § Forensics may take days to complete § Reinstall operating system and applications & all security patches § Back-ups may contain altered data making it useless during recovery activities Securing Your Network
Frequency Shift § Automated worms, malicious code and multi-part viruses are making “security through obscurity” a bygone § Vulnerability Assessment offers the most value to customers for today’s security threats - Closes open doors that viruses frequently enter Verifies what firewall policy changes expose Provides an inventory of affected systems for IDS alerts Scans web site applications daily with latest VA tests Detects unknown rogue systems on networks § Tools are evolving into online service architectures, constantly updated and ready § Detection is shifting to prevention Securing Your Network
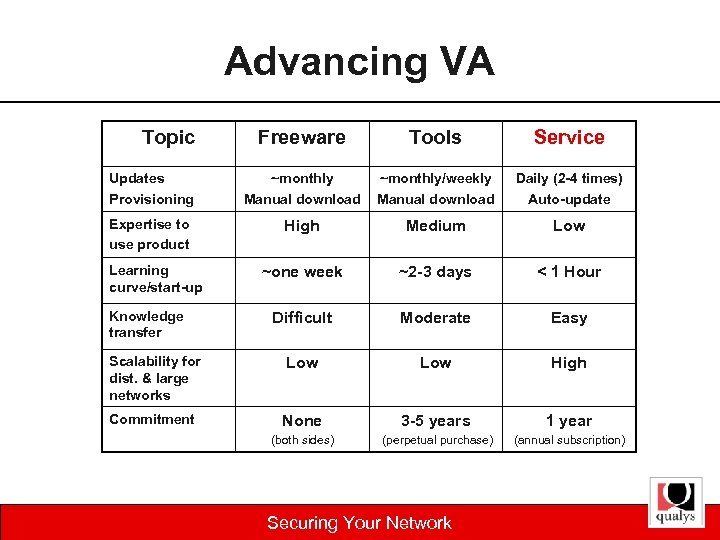
Advancing VA Topic Freeware Tools Service Updates Provisioning ~monthly Manual download ~monthly/weekly Manual download Daily (2 -4 times) Auto-update Expertise to use product High Medium Low ~one week ~2 -3 days < 1 Hour Difficult Moderate Easy Scalability for dist. & large networks Low High Commitment None 3 -5 years 1 year (both sides) (perpetual purchase) (annual subscription) Learning curve/start-up Knowledge transfer Securing Your Network
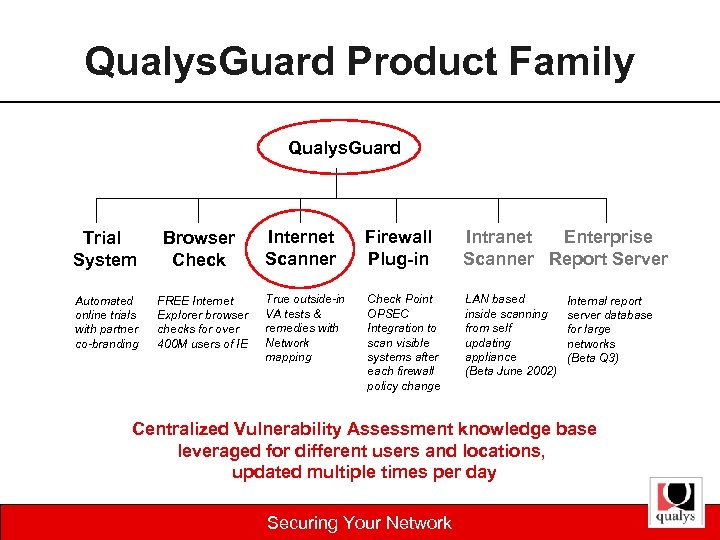
Qualys. Guard Product Family Qualys. Guard Trial System Browser Check Automated online trials with partner co-branding FREE Internet Explorer browser checks for over 400 M users of IE Internet Scanner Firewall Plug-in Intranet Enterprise Scanner Report Server True outside-in VA tests & remedies with Network mapping Check Point OPSEC Integration to scan visible systems after each firewall policy change LAN based inside scanning from self updating appliance (Beta June 2002) Internal report server database for large networks (Beta Q 3) Centralized Vulnerability Assessment knowledge base leveraged for different users and locations, updated multiple times per day Securing Your Network
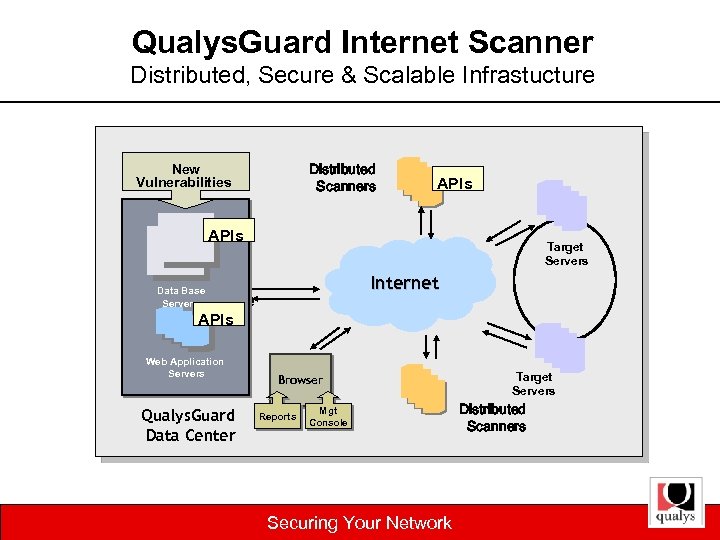
Qualys. Guard Internet Scanner Distributed, Secure & Scalable Infrastucture Distributed Scanners New Vulnerabilities APIs Target Servers Internet Data Base Servers Hacke r APIs Web Application Servers Qualys. Guard Data Center Browser Reports Mgt Console Securing Your Network Target Servers Distributed Scanners
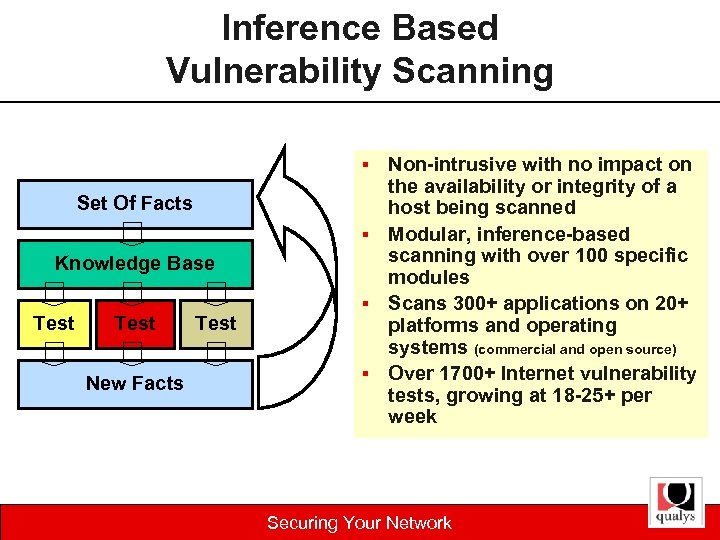
Inference Based Vulnerability Scanning Non-intrusive with no impact on the availability or integrity of a host being scanned § Modular, inference-based scanning with over 100 specific modules § Scans 300+ applications on 20+ platforms and operating systems (commercial and open source) § Over 1700+ Internet vulnerability tests, growing at 18 -25+ per week § Set Of Facts Knowledge Base Test New Facts Test Securing Your Network

Live Demonstration - Network Mapping - Vulnerability Scanning - Detail Reporting - Dynamic Reports - CVE Database - Configuration Options - Account Maintenance Securing Your Network
Qualys. Guard Features § Scalability, Reliability and Speed § Enterprise level scanning – Class C & B Networks § Comprehensive database of vulnerabilities with aggregated signatures and patches § Graphical and Actionable Reporting § Network Discovery for Large Networks § 90+% OS detection correctness § Minimizing false positives § Full set of extensible XML APIs to fully integrate into the security process Securing Your Network
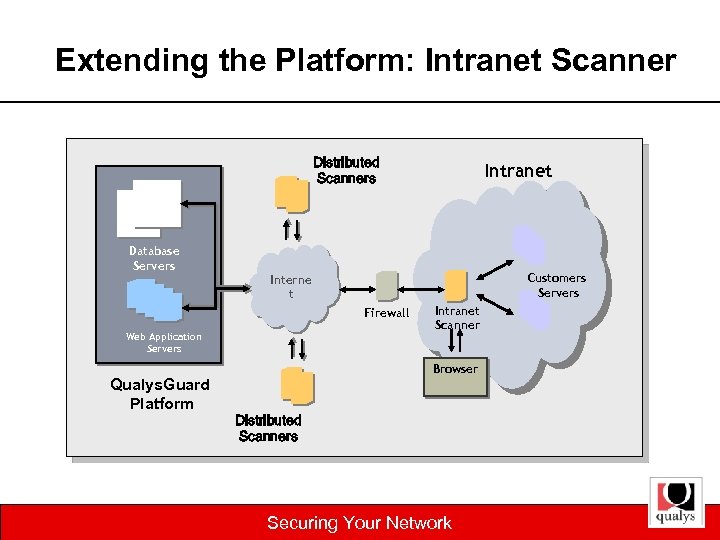
Extending the Platform: Intranet Scanner Distributed Scanners Intranet Database Servers Customers Servers Interne t Firewall Web Application Servers Qualys. Guard Platform Intranet Scanner Browser Distributed Scanners Securing Your Network
Qualys. Guard for Check Point § Monitors firewall policy changes § Automatically scans updated firewalls § Analyzes results with previous assessment § Produces trend analysis results (+/-) § Results/Reports Email with trend summary & URL report links Firewall log entries including trend summary Online Detail & Differential HTML reports Securing Your Network
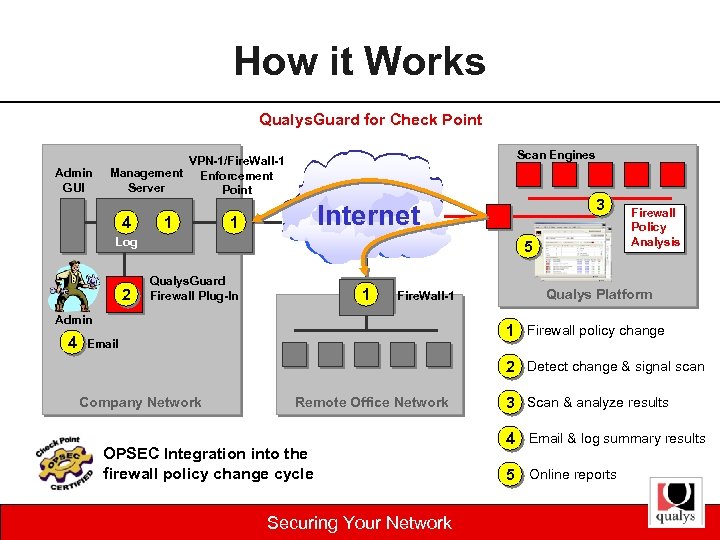
How it Works Qualys. Guard for Check Point Admin GUI Scan Engines VPN-1/Fire. Wall-1 Management Enforcement Server Point 4 1 Internet 1 Log 2 5 Qualys. Guard Firewall Plug-In 1 Fire. Wall-1 Admin 4 3 Firewall Policy Analysis Qualys Platform 1 Firewall policy change Email 2 Detect change & signal scan Company Network Remote Office Network OPSEC Integration into the firewall policy change cycle Securing Your Network 3 Scan & analyze results 4 Email & log summary results 5 Online reports
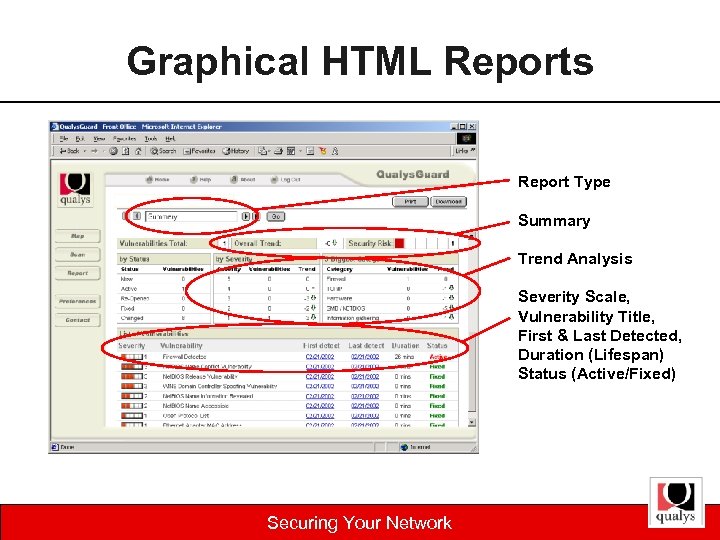
Graphical HTML Reports Report Type Summary Trend Analysis Severity Scale, Vulnerability Title, First & Last Detected, Duration (Lifespan) Status (Active/Fixed) Securing Your Network
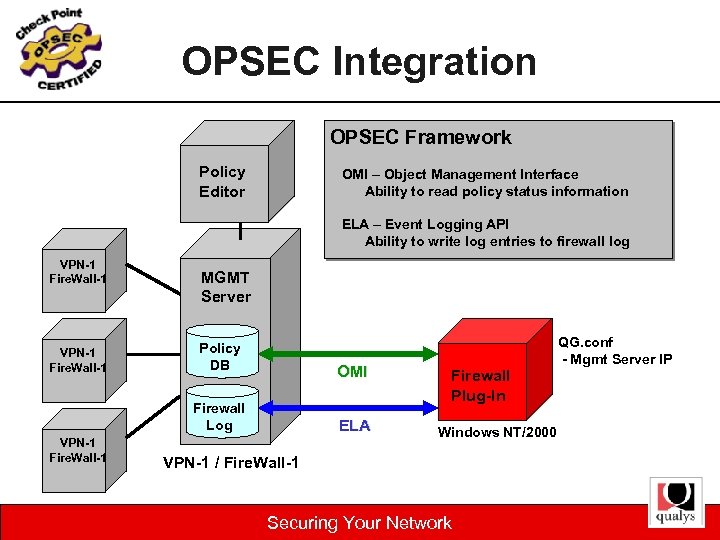
OPSEC Integration OPSEC Framework Policy Editor OMI – Object Management Interface Ability to read policy status information ELA – Event Logging API Ability to write log entries to firewall log VPN-1 Fire. Wall-1 MGMT Server Policy DB OMI Firewall Log VPN-1 Fire. Wall-1 ELA Firewall Plug-In Windows NT/2000 VPN-1 / Fire. Wall-1 Securing Your Network QG. conf - Mgmt Server IP

Summary § Vulnerability Assessment offers the most value to customers for today’s security threats - Closes open doors that viruses frequently enter Verifies what firewall policy changes expose Provides an inventory of affected systems for IDS alerts Scans web site applications daily with latest VA tests Detects rogue systems unknown to administrators § In 2001, 99% of incidents and exposures utilized a known vulnerability where a counter measure was available (CERT) § Tools are evolving into online service architectures, constantly updated and ready § Detection is shifting to prevention Securing Your Network

Q&A support@qualys. com www. qualys. com Securing Your Network
213c201280490751951638869a984fe5.ppt