d05551e36ca777c580cc1bf37da290f8.ppt
- Количество слайдов: 64
 Pulling a John Connor: Defeating Android Charlie Miller Independent Security Evaluators cmiller@securityevaluators. com
Pulling a John Connor: Defeating Android Charlie Miller Independent Security Evaluators cmiller@securityevaluators. com
 About me Former National Security Agency First to hack the i. Phone and Android G 1 phone Won Mac. Book Air at Pwn 2 Own competition with Safari 0 day Author of “Fuzzing for Software Security Testing and Quality Assurance” Author of “The Mac Hackers Handbook” Due out in a few weeks
About me Former National Security Agency First to hack the i. Phone and Android G 1 phone Won Mac. Book Air at Pwn 2 Own competition with Safari 0 day Author of “Fuzzing for Software Security Testing and Quality Assurance” Author of “The Mac Hackers Handbook” Due out in a few weeks
 Outline Phone hacking Android security model Attack surface Bug hunting Exploit dev After access is achieved
Outline Phone hacking Android security model Attack surface Bug hunting Exploit dev After access is achieved
 Smart phone hacking is fun! Small but capable computers Always on Always connected to the Internet (Wi-Fi, EDGE, 3 G) Cellular capabilities
Smart phone hacking is fun! Small but capable computers Always on Always connected to the Internet (Wi-Fi, EDGE, 3 G) Cellular capabilities
 Personal information Contacts Voicemail Pictures and movies Web credentials and cookies Email and text messages Calendar and events GPS information
Personal information Contacts Voicemail Pictures and movies Web credentials and cookies Email and text messages Calendar and events GPS information
 Good hacker asset “Smart phone DOS” Instant financial gain 1 -900 numbers, text messages, etc GPS (contrast with random compromised box on Internet) Listening device Circumvent network security protections
Good hacker asset “Smart phone DOS” Instant financial gain 1 -900 numbers, text messages, etc GPS (contrast with random compromised box on Internet) Listening device Circumvent network security protections
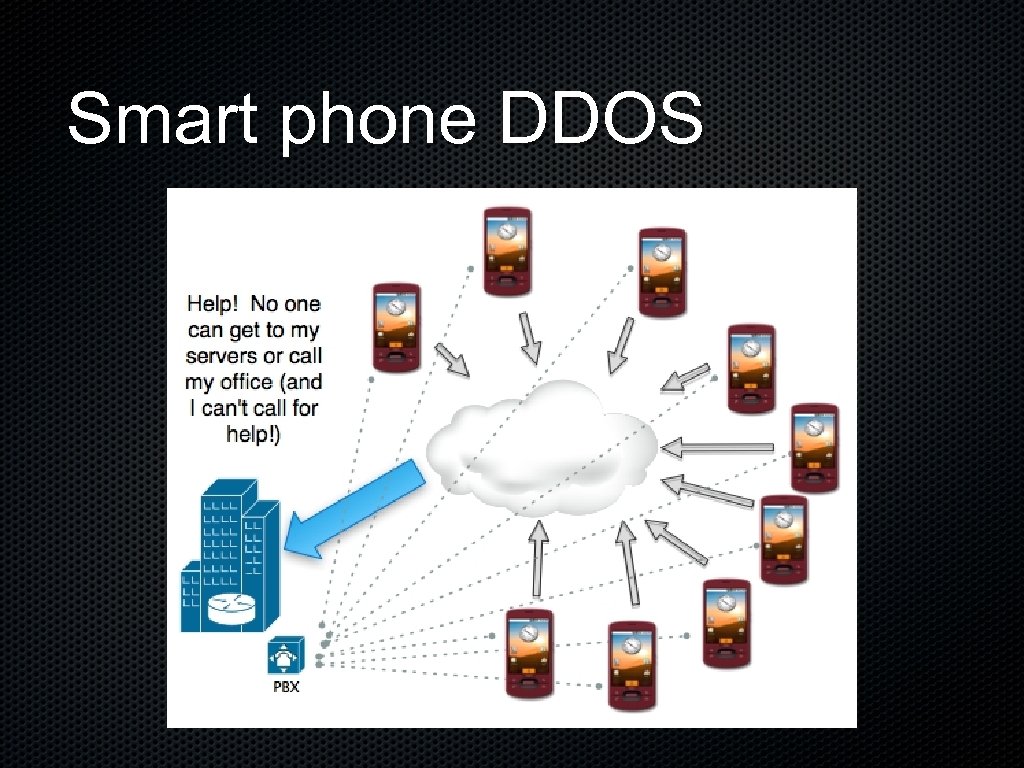 Smart phone DDOS
Smart phone DDOS
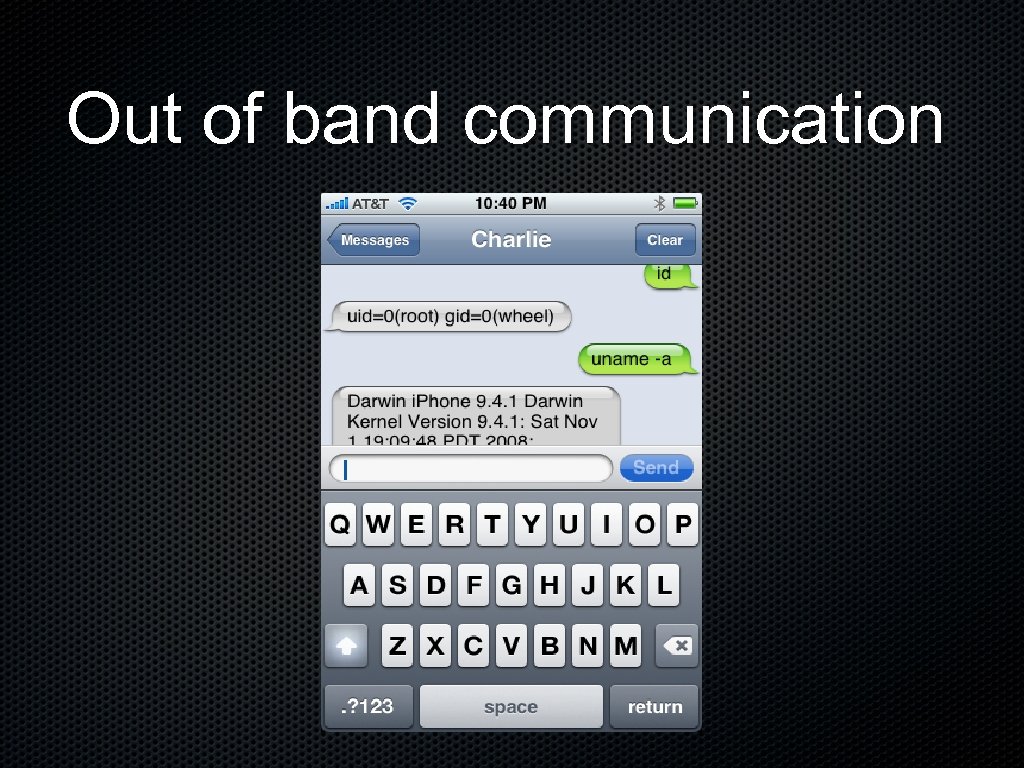 Out of band communication
Out of band communication
 Issues for defense Typically no AV on phones NIDS can be avoided with SMS Hard to determine phone has been compromised Tricky forensics Phones go to Starbucks for a break
Issues for defense Typically no AV on phones NIDS can be avoided with SMS Hard to determine phone has been compromised Tricky forensics Phones go to Starbucks for a break
 Android basics Open source, free, mobile platform One production phone runs it, T-Mobile G 1 Consists of OS, middleware, some applications Linux kernel Webkit based browser
Android basics Open source, free, mobile platform One production phone runs it, T-Mobile G 1 Consists of OS, middleware, some applications Linux kernel Webkit based browser
 Smart phone 3 G / Wi. Fi / Bluetooth Web browser SMS/MMS messaging Audio/video player AOL IM client GPS, integration with google maps. . . etc
Smart phone 3 G / Wi. Fi / Bluetooth Web browser SMS/MMS messaging Audio/video player AOL IM client GPS, integration with google maps. . . etc
 Security Architecture Linux - traditional user id Fine grained access controls
Security Architecture Linux - traditional user id Fine grained access controls
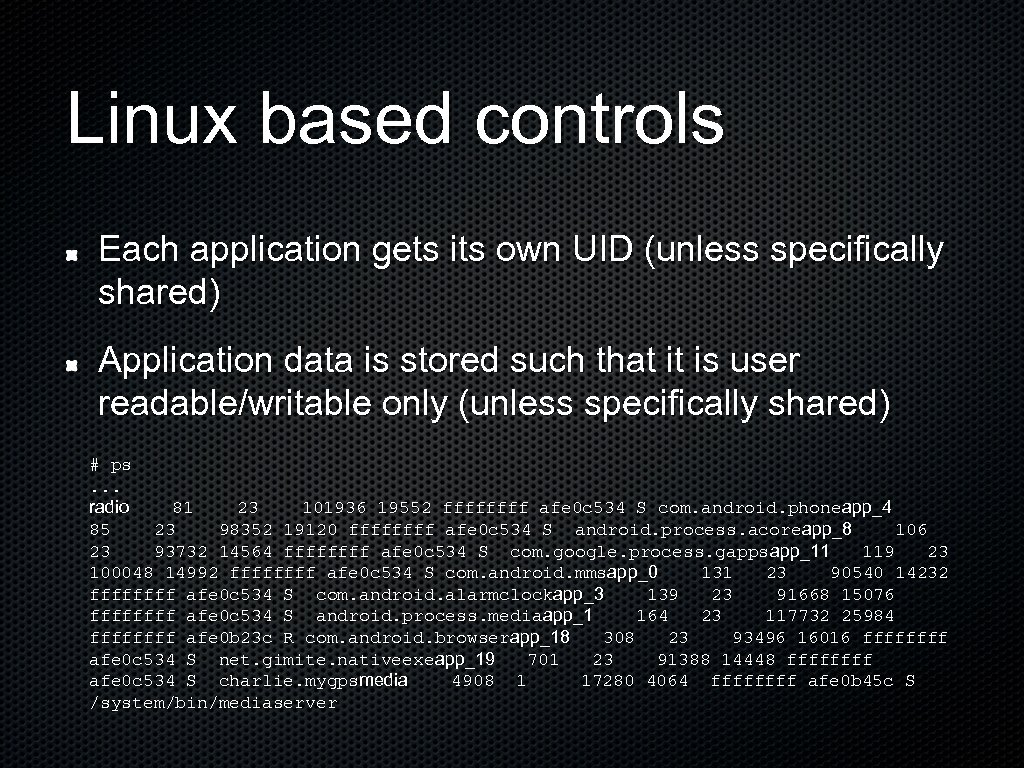 Linux based controls Each application gets its own UID (unless specifically shared) Application data is stored such that it is user readable/writable only (unless specifically shared) # ps. . . radio 81 23 101936 19552 ffff afe 0 c 534 S com. android. phoneapp_4 85 23 98352 19120 ffff afe 0 c 534 S android. process. acoreapp_8 106 23 93732 14564 ffff afe 0 c 534 S com. google. process. gappsapp_11 119 23 100048 14992 ffff afe 0 c 534 S com. android. mmsapp_0 131 23 90540 14232 ffff afe 0 c 534 S com. android. alarmclockapp_3 139 23 91668 15076 ffff afe 0 c 534 S android. process. mediaapp_1 164 23 117732 25984 ffff afe 0 b 23 c R com. android. browserapp_18 308 23 93496 16016 ffff afe 0 c 534 S net. gimite. nativeexeapp_19 701 23 91388 14448 ffff afe 0 c 534 S charlie. mygpsmedia 4908 1 17280 4064 ffff afe 0 b 45 c S /system/bin/mediaserver
Linux based controls Each application gets its own UID (unless specifically shared) Application data is stored such that it is user readable/writable only (unless specifically shared) # ps. . . radio 81 23 101936 19552 ffff afe 0 c 534 S com. android. phoneapp_4 85 23 98352 19120 ffff afe 0 c 534 S android. process. acoreapp_8 106 23 93732 14564 ffff afe 0 c 534 S com. google. process. gappsapp_11 119 23 100048 14992 ffff afe 0 c 534 S com. android. mmsapp_0 131 23 90540 14232 ffff afe 0 c 534 S com. android. alarmclockapp_3 139 23 91668 15076 ffff afe 0 c 534 S android. process. mediaapp_1 164 23 117732 25984 ffff afe 0 b 23 c R com. android. browserapp_18 308 23 93496 16016 ffff afe 0 c 534 S net. gimite. nativeexeapp_19 701 23 91388 14448 ffff afe 0 c 534 S charlie. mygpsmedia 4908 1 17280 4064 ffff afe 0 b 45 c S /system/bin/mediaserver
 Access controls Applications have install-time permissions associated with them User is informed what permissions it will require and may accept or reject “pm list permissions” Otherwise Security. Exception is (typically) thrown
Access controls Applications have install-time permissions associated with them User is informed what permissions it will require and may accept or reject “pm list permissions” Otherwise Security. Exception is (typically) thrown
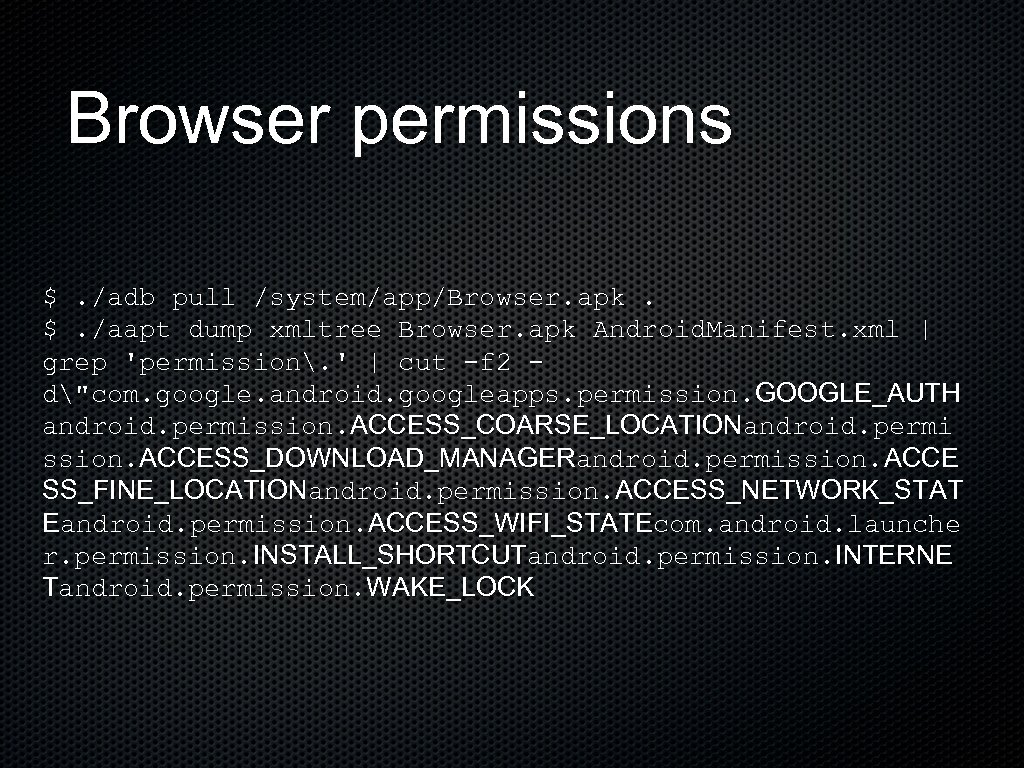 Browser permissions $. /adb pull /system/app/Browser. apk. $. /aapt dump xmltree Browser. apk Android. Manifest. xml | grep 'permission. ' | cut -f 2 d"com. google. android. googleapps. permission. GOOGLE_AUTH android. permission. ACCESS_COARSE_LOCATIONandroid. permi ssion. ACCESS_DOWNLOAD_MANAGERandroid. permission. ACCE SS_FINE_LOCATIONandroid. permission. ACCESS_NETWORK_STAT Eandroid. permission. ACCESS_WIFI_STATEcom. android. launche r. permission. INSTALL_SHORTCUTandroid. permission. INTERNE Tandroid. permission. WAKE_LOCK
Browser permissions $. /adb pull /system/app/Browser. apk. $. /aapt dump xmltree Browser. apk Android. Manifest. xml | grep 'permission. ' | cut -f 2 d"com. google. android. googleapps. permission. GOOGLE_AUTH android. permission. ACCESS_COARSE_LOCATIONandroid. permi ssion. ACCESS_DOWNLOAD_MANAGERandroid. permission. ACCE SS_FINE_LOCATIONandroid. permission. ACCESS_NETWORK_STAT Eandroid. permission. ACCESS_WIFI_STATEcom. android. launche r. permission. INSTALL_SHORTCUTandroid. permission. INTERNE Tandroid. permission. WAKE_LOCK
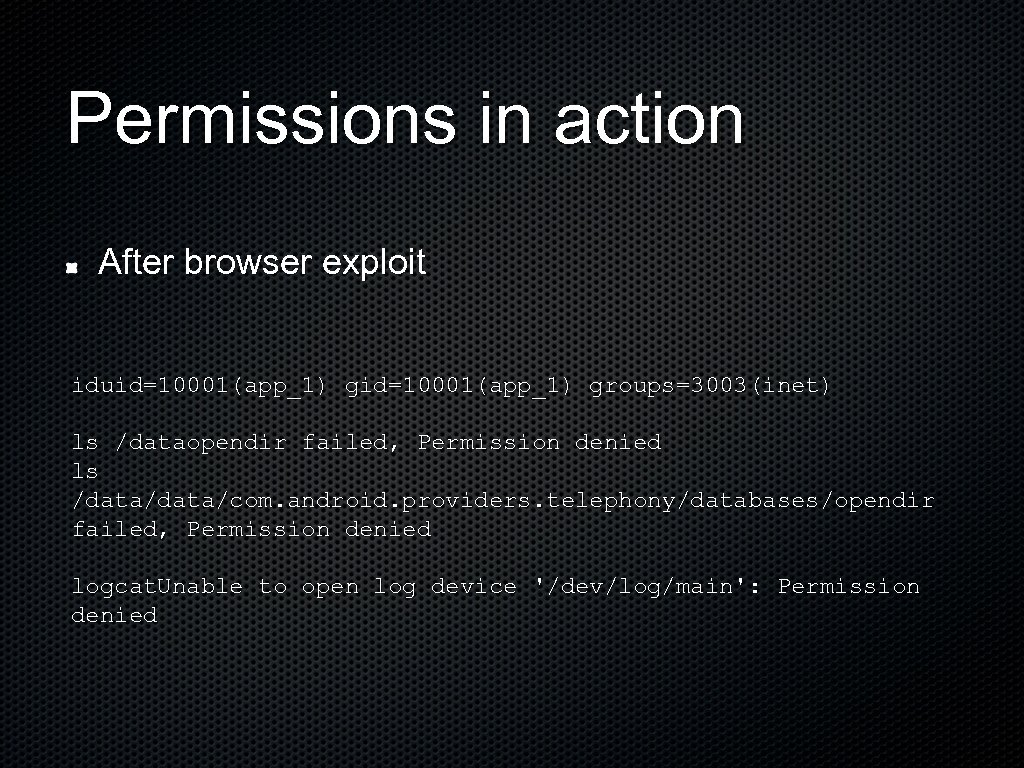 Permissions in action After browser exploit iduid=10001(app_1) groups=3003(inet) ls /dataopendir failed, Permission denied ls /data/com. android. providers. telephony/databases/opendir failed, Permission denied logcat. Unable to open log device '/dev/log/main': Permission denied
Permissions in action After browser exploit iduid=10001(app_1) groups=3003(inet) ls /dataopendir failed, Permission denied ls /data/com. android. providers. telephony/databases/opendir failed, Permission denied logcat. Unable to open log device '/dev/log/main': Permission denied
 Application Development SDK with emulator freely available All development done in Java Only signed. apk (Java apps) may be run May use self-signed certificate Apps may run in the background
Application Development SDK with emulator freely available All development done in Java Only signed. apk (Java apps) may be run May use self-signed certificate Apps may run in the background
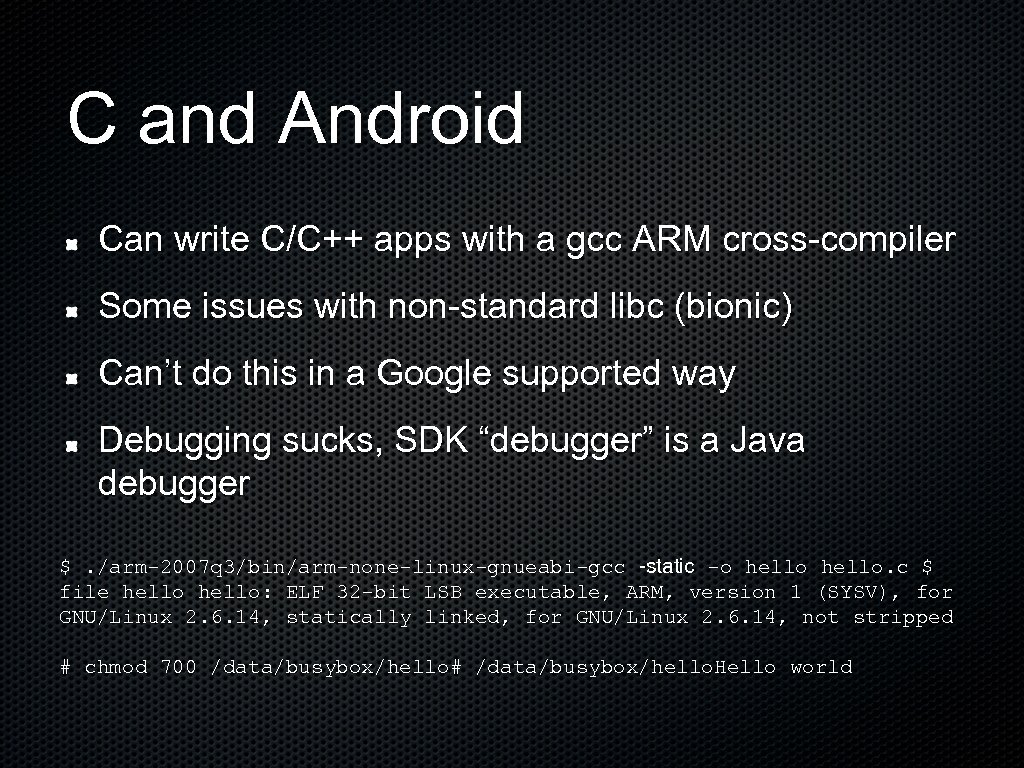 C and Android Can write C/C++ apps with a gcc ARM cross-compiler Some issues with non-standard libc (bionic) Can’t do this in a Google supported way Debugging sucks, SDK “debugger” is a Java debugger $. /arm-2007 q 3/bin/arm-none-linux-gnueabi-gcc -static -o hello. c $ file hello: ELF 32 -bit LSB executable, ARM, version 1 (SYSV), for GNU/Linux 2. 6. 14, statically linked, for GNU/Linux 2. 6. 14, not stripped # chmod 700 /data/busybox/hello# /data/busybox/hello. Hello world
C and Android Can write C/C++ apps with a gcc ARM cross-compiler Some issues with non-standard libc (bionic) Can’t do this in a Google supported way Debugging sucks, SDK “debugger” is a Java debugger $. /arm-2007 q 3/bin/arm-none-linux-gnueabi-gcc -static -o hello. c $ file hello: ELF 32 -bit LSB executable, ARM, version 1 (SYSV), for GNU/Linux 2. 6. 14, statically linked, for GNU/Linux 2. 6. 14, not stripped # chmod 700 /data/busybox/hello# /data/busybox/hello. Hello world
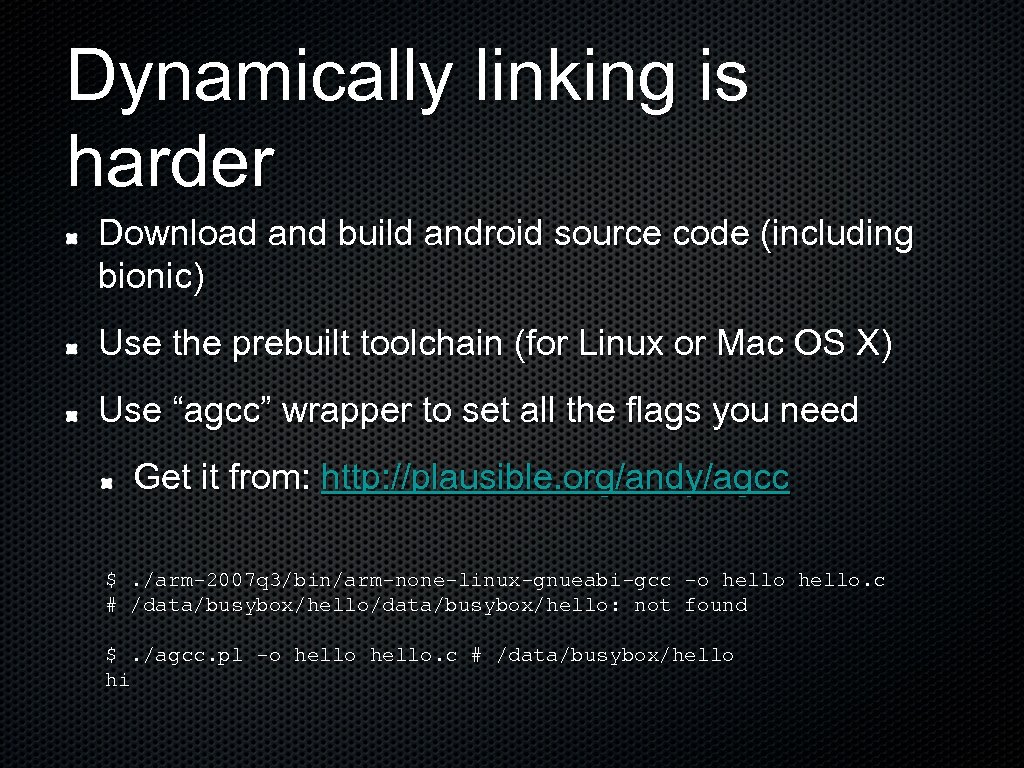 Dynamically linking is harder Download and build android source code (including bionic) Use the prebuilt toolchain (for Linux or Mac OS X) Use “agcc” wrapper to set all the flags you need Get it from: http: //plausible. org/andy/agcc $. /arm-2007 q 3/bin/arm-none-linux-gnueabi-gcc -o hello. c # /data/busybox/hello: not found $. /agcc. pl -o hello. c # /data/busybox/hello hi
Dynamically linking is harder Download and build android source code (including bionic) Use the prebuilt toolchain (for Linux or Mac OS X) Use “agcc” wrapper to set all the flags you need Get it from: http: //plausible. org/andy/agcc $. /arm-2007 q 3/bin/arm-none-linux-gnueabi-gcc -o hello. c # /data/busybox/hello: not found $. /agcc. pl -o hello. c # /data/busybox/hello hi
 Tale of firmwares RC 19 - Original factory install (old Webkit bug) RC 28 - a few people got this before RC 29 rolled out RC 29 - Fixed Webkit bug, had local root bug RC 30 - No more root 1. 1/RC 33 - Feature upgrade, all bugs fixed ; ) RC 7 - UK version of RC 29 RC 8 - UK version of RC 30 ADP 1 - Android Dev Phone 1. 0 ~ RC 28?
Tale of firmwares RC 19 - Original factory install (old Webkit bug) RC 28 - a few people got this before RC 29 rolled out RC 29 - Fixed Webkit bug, had local root bug RC 30 - No more root 1. 1/RC 33 - Feature upgrade, all bugs fixed ; ) RC 7 - UK version of RC 29 RC 8 - UK version of RC 30 ADP 1 - Android Dev Phone 1. 0 ~ RC 28?
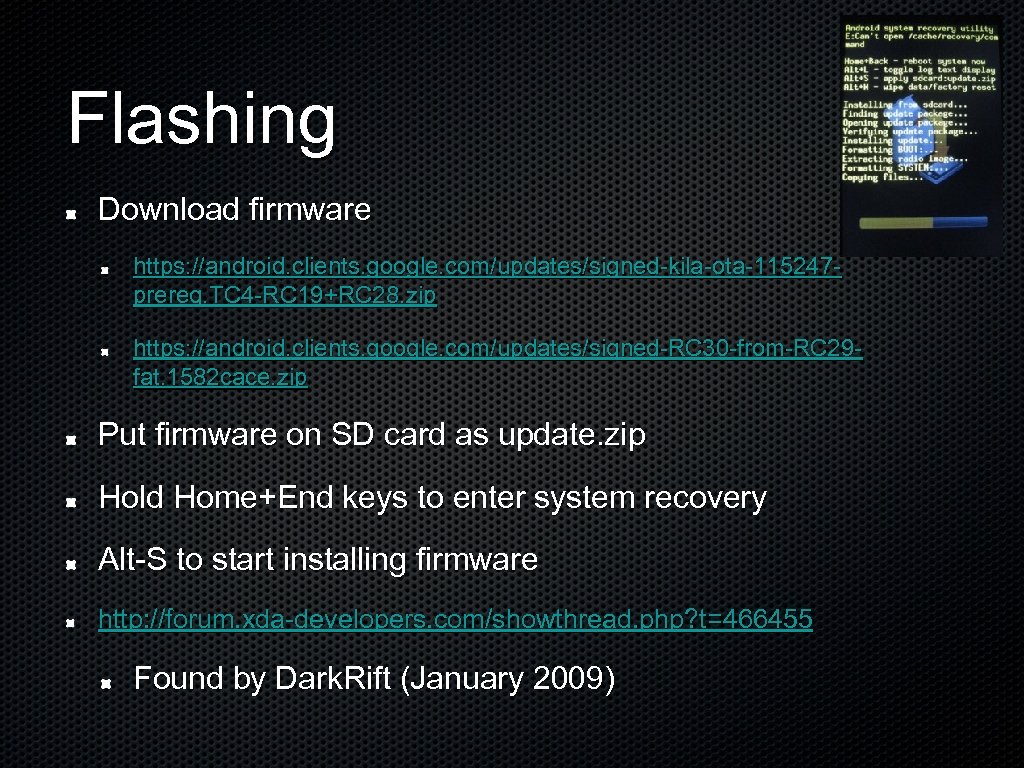 Flashing Download firmware https: //android. clients. google. com/updates/signed-kila-ota-115247 prereq. TC 4 -RC 19+RC 28. zip https: //android. clients. google. com/updates/signed-RC 30 -from-RC 29 fat. 1582 cace. zip Put firmware on SD card as update. zip Hold Home+End keys to enter system recovery Alt-S to start installing firmware http: //forum. xda-developers. com/showthread. php? t=466455 Found by Dark. Rift (January 2009)
Flashing Download firmware https: //android. clients. google. com/updates/signed-kila-ota-115247 prereq. TC 4 -RC 19+RC 28. zip https: //android. clients. google. com/updates/signed-RC 30 -from-RC 29 fat. 1582 cace. zip Put firmware on SD card as update. zip Hold Home+End keys to enter system recovery Alt-S to start installing firmware http: //forum. xda-developers. com/showthread. php? t=466455 Found by Dark. Rift (January 2009)
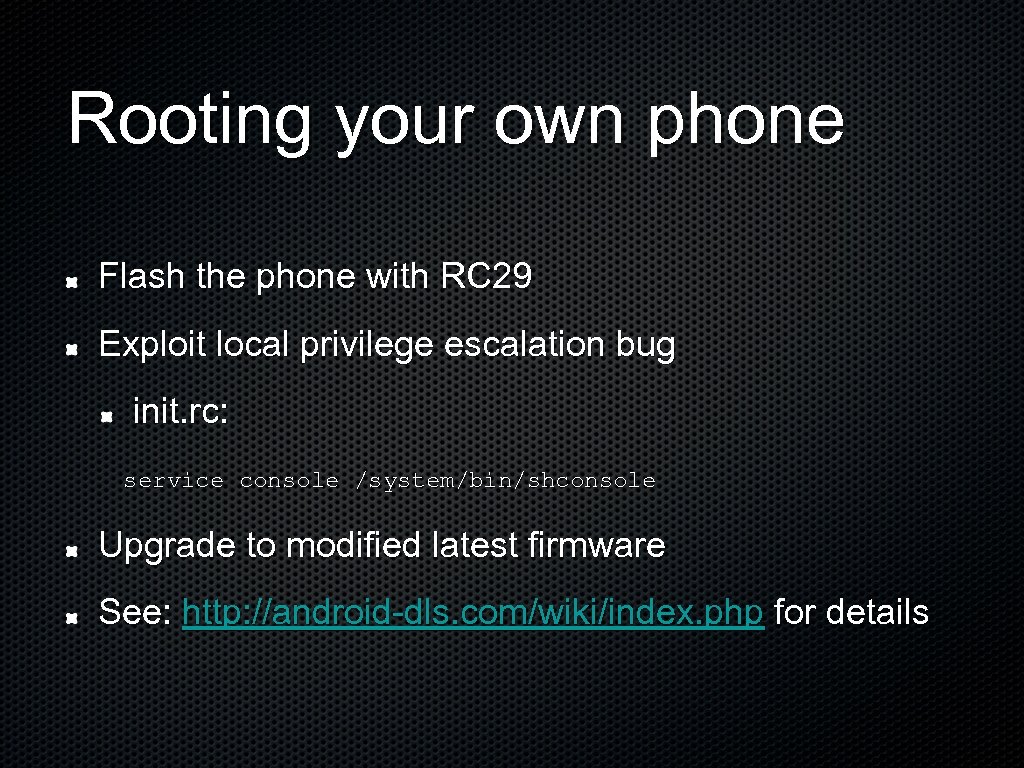 Rooting your own phone Flash the phone with RC 29 Exploit local privilege escalation bug init. rc: service console /system/bin/shconsole Upgrade to modified latest firmware See: http: //android-dls. com/wiki/index. php for details
Rooting your own phone Flash the phone with RC 29 Exploit local privilege escalation bug init. rc: service console /system/bin/shconsole Upgrade to modified latest firmware See: http: //android-dls. com/wiki/index. php for details
 Attack surface Server side Client side
Attack surface Server side Client side
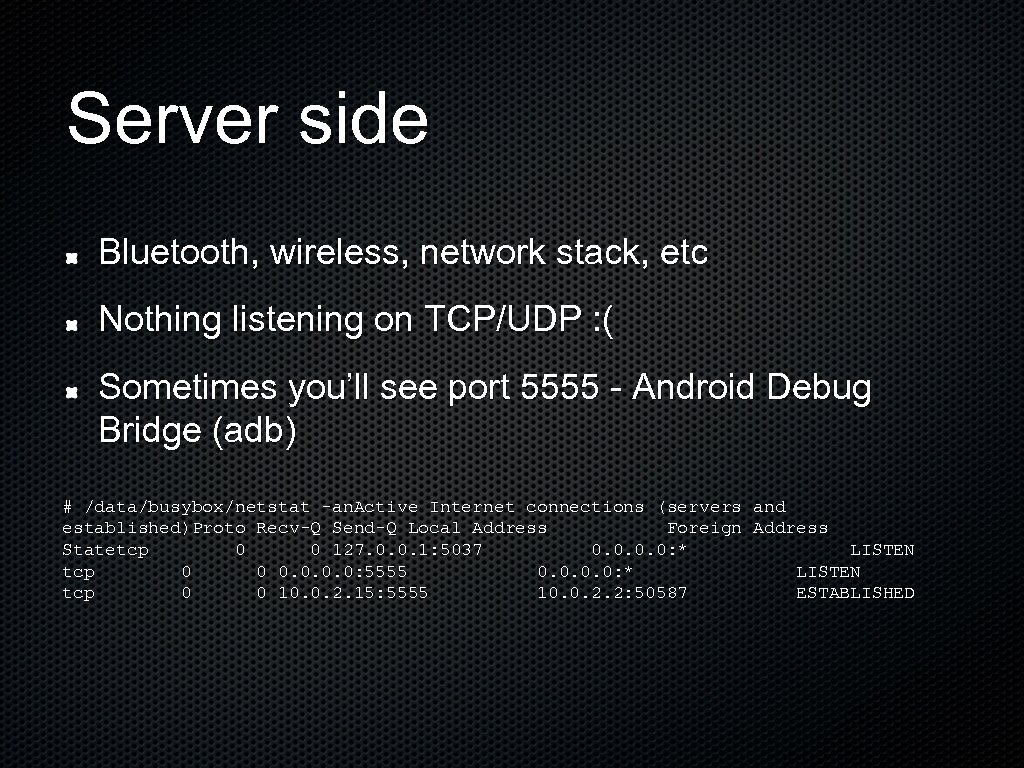 Server side Bluetooth, wireless, network stack, etc Nothing listening on TCP/UDP : ( Sometimes you’ll see port 5555 - Android Debug Bridge (adb) # /data/busybox/netstat -an. Active Internet connections (servers and established)Proto Recv-Q Send-Q Local Address Foreign Address Statetcp 0 0 127. 0. 0. 1: 5037 0. 0: * LISTEN tcp 0 0 0. 0: 5555 0. 0: * LISTEN tcp 0 0 10. 0. 2. 15: 5555 10. 0. 2. 2: 50587 ESTABLISHED
Server side Bluetooth, wireless, network stack, etc Nothing listening on TCP/UDP : ( Sometimes you’ll see port 5555 - Android Debug Bridge (adb) # /data/busybox/netstat -an. Active Internet connections (servers and established)Proto Recv-Q Send-Q Local Address Foreign Address Statetcp 0 0 127. 0. 0. 1: 5037 0. 0: * LISTEN tcp 0 0 0. 0: 5555 0. 0: * LISTEN tcp 0 0 10. 0. 2. 15: 5555 10. 0. 2. 2: 50587 ESTABLISHED
 Client side - much nicer Web browser Email client IM client SMS/MMS Multimedia player Android Market apps etc
Client side - much nicer Web browser Email client IM client SMS/MMS Multimedia player Android Market apps etc
 Java - safety? In theory these are all Java applications - and thus should be immune to memory corruption However the JVM is built on top of many C/C++ libraries Some API functions pass data to C/C++ daemons for processing
Java - safety? In theory these are all Java applications - and thus should be immune to memory corruption However the JVM is built on top of many C/C++ libraries Some API functions pass data to C/C++ daemons for processing
 Android libraries Bionic - custom libc implementation open. Core - multimedia functionality SGL - image rendering Web. Kit - HTML, JS rendering All this is open source and C/C++
Android libraries Bionic - custom libc implementation open. Core - multimedia functionality SGL - image rendering Web. Kit - HTML, JS rendering All this is open source and C/C++
 Bug hunting Static analysis Dynamic analysis
Bug hunting Static analysis Dynamic analysis
 Static Analysis Source code freely available http: //source. android. com/download Can build, read, run through tools, etc
Static Analysis Source code freely available http: //source. android. com/download Can build, read, run through tools, etc
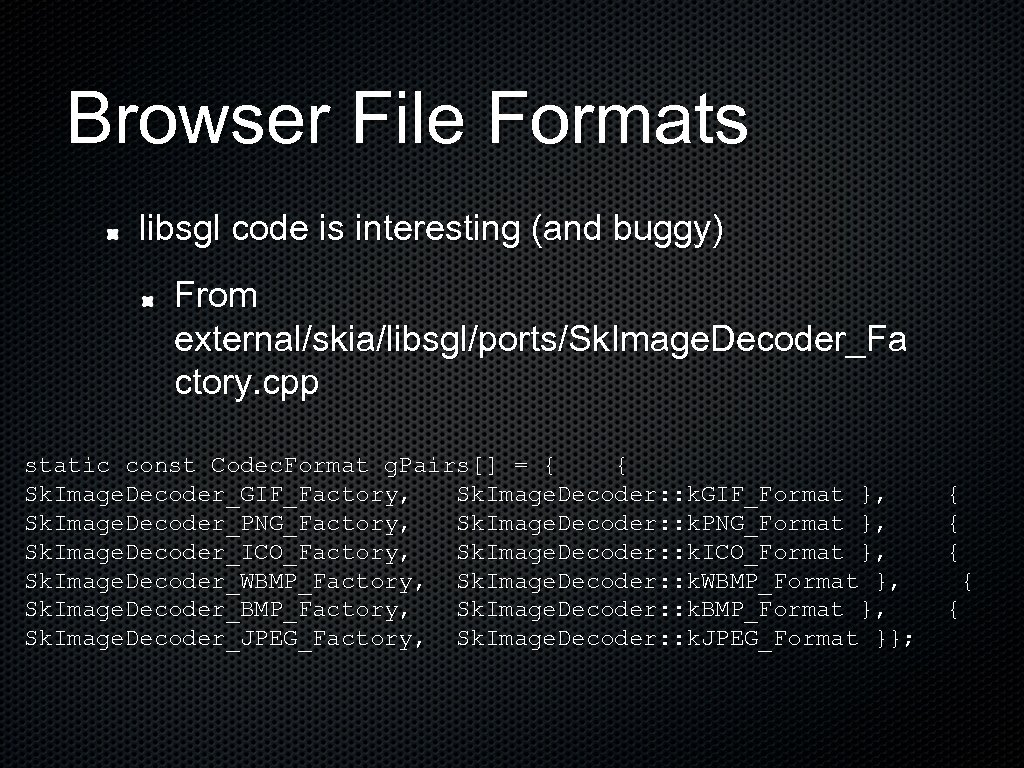 Browser File Formats libsgl code is interesting (and buggy) From external/skia/libsgl/ports/Sk. Image. Decoder_Fa ctory. cpp static const Codec. Format g. Pairs[] = { { Sk. Image. Decoder_GIF_Factory, Sk. Image. Decoder: : k. GIF_Format }, { Sk. Image. Decoder_PNG_Factory, Sk. Image. Decoder: : k. PNG_Format }, { Sk. Image. Decoder_ICO_Factory, Sk. Image. Decoder: : k. ICO_Format }, { Sk. Image. Decoder_WBMP_Factory, Sk. Image. Decoder: : k. WBMP_Format }, { Sk. Image. Decoder_BMP_Factory, Sk. Image. Decoder: : k. BMP_Format }, { Sk. Image. Decoder_JPEG_Factory, Sk. Image. Decoder: : k. JPEG_Format }};
Browser File Formats libsgl code is interesting (and buggy) From external/skia/libsgl/ports/Sk. Image. Decoder_Fa ctory. cpp static const Codec. Format g. Pairs[] = { { Sk. Image. Decoder_GIF_Factory, Sk. Image. Decoder: : k. GIF_Format }, { Sk. Image. Decoder_PNG_Factory, Sk. Image. Decoder: : k. PNG_Format }, { Sk. Image. Decoder_ICO_Factory, Sk. Image. Decoder: : k. ICO_Format }, { Sk. Image. Decoder_WBMP_Factory, Sk. Image. Decoder: : k. WBMP_Format }, { Sk. Image. Decoder_BMP_Factory, Sk. Image. Decoder: : k. BMP_Format }, { Sk. Image. Decoder_JPEG_Factory, Sk. Image. Decoder: : k. JPEG_Format }};
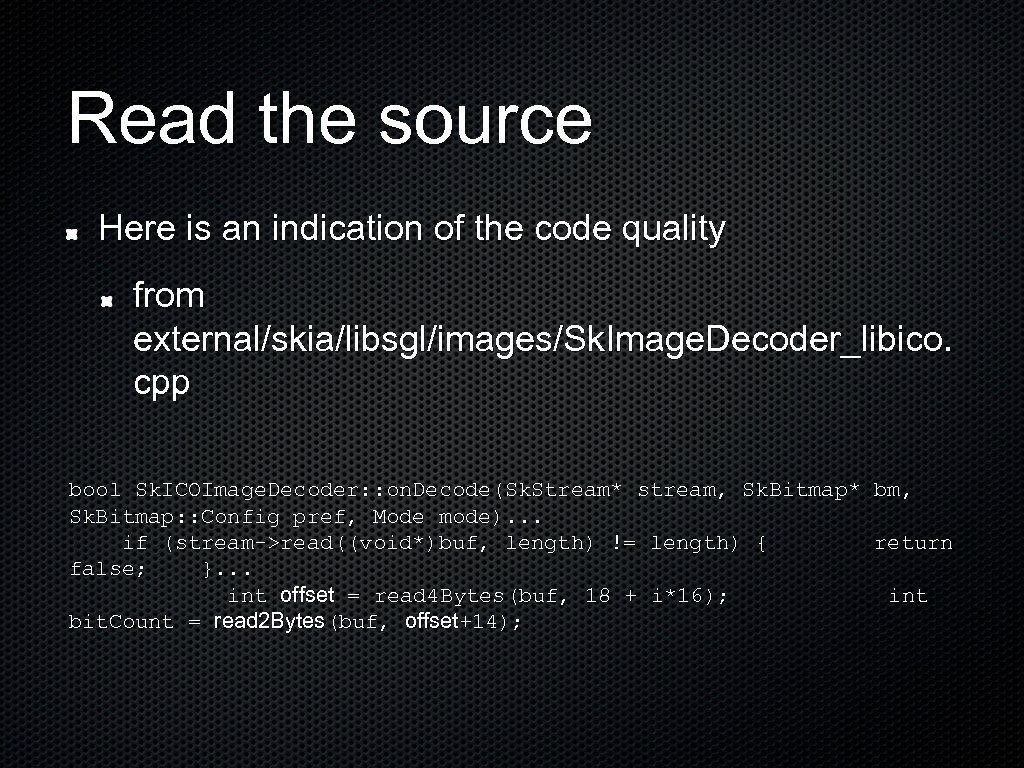 Read the source Here is an indication of the code quality from external/skia/libsgl/images/Sk. Image. Decoder_libico. cpp bool Sk. ICOImage. Decoder: : on. Decode(Sk. Stream* stream, Sk. Bitmap* bm, Sk. Bitmap: : Config pref, Mode mode). . . if (stream->read((void*)buf, length) != length) { return false; }. . . int offset = read 4 Bytes(buf, 18 + i*16); int bit. Count = read 2 Bytes(buf, offset+14);
Read the source Here is an indication of the code quality from external/skia/libsgl/images/Sk. Image. Decoder_libico. cpp bool Sk. ICOImage. Decoder: : on. Decode(Sk. Stream* stream, Sk. Bitmap* bm, Sk. Bitmap: : Config pref, Mode mode). . . if (stream->read((void*)buf, length) != length) { return false; }. . . int offset = read 4 Bytes(buf, 18 + i*16); int bit. Count = read 2 Bytes(buf, offset+14);
 Fuzzing The Android comes with an Emulator QEMU-based, ARM processor emulated Full Android stack Not updated as frequently as devices The Web. Kit bug still crashes the emulator Can fuzz emulator or device
Fuzzing The Android comes with an Emulator QEMU-based, ARM processor emulated Full Android stack Not updated as frequently as devices The Web. Kit bug still crashes the emulator Can fuzz emulator or device
 Emulator Fuzzing the emulator is convenient Don’t need device Can stick it in VMware and snapshot it Can even do exploit dev on it - to a point If things get hosed do: . /emulator -wipe-data
Emulator Fuzzing the emulator is convenient Don’t need device Can stick it in VMware and snapshot it Can even do exploit dev on it - to a point If things get hosed do: . /emulator -wipe-data
 ADB Android debugging bridge Allows to push files on off emulator/device Gives shell on emulator/device Gives root on emulator, “shell” on device Can watch system logs
ADB Android debugging bridge Allows to push files on off emulator/device Gives shell on emulator/device Gives root on emulator, “shell” on device Can watch system logs
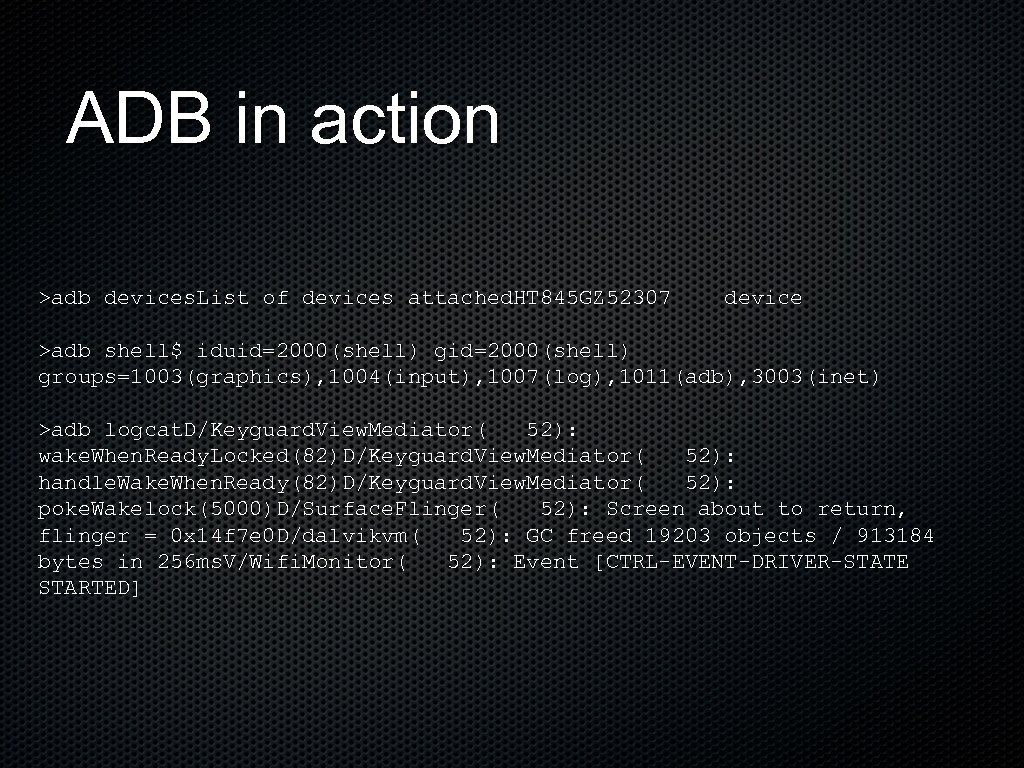 ADB in action >adb devices. List of devices attached. HT 845 GZ 52307 device >adb shell$ iduid=2000(shell) groups=1003(graphics), 1004(input), 1007(log), 1011(adb), 3003(inet) >adb logcat. D/Keyguard. View. Mediator( 52): wake. When. Ready. Locked(82)D/Keyguard. View. Mediator( 52): handle. Wake. When. Ready(82)D/Keyguard. View. Mediator( 52): poke. Wakelock(5000)D/Surface. Flinger( 52): Screen about to return, flinger = 0 x 14 f 7 e 0 D/dalvikvm( 52): GC freed 19203 objects / 913184 bytes in 256 ms. V/Wifi. Monitor( 52): Event [CTRL-EVENT-DRIVER-STATE STARTED]
ADB in action >adb devices. List of devices attached. HT 845 GZ 52307 device >adb shell$ iduid=2000(shell) groups=1003(graphics), 1004(input), 1007(log), 1011(adb), 3003(inet) >adb logcat. D/Keyguard. View. Mediator( 52): wake. When. Ready. Locked(82)D/Keyguard. View. Mediator( 52): handle. Wake. When. Ready(82)D/Keyguard. View. Mediator( 52): poke. Wakelock(5000)D/Surface. Flinger( 52): Screen about to return, flinger = 0 x 14 f 7 e 0 D/dalvikvm( 52): GC freed 19203 objects / 913184 bytes in 256 ms. V/Wifi. Monitor( 52): Event [CTRL-EVENT-DRIVER-STATE STARTED]
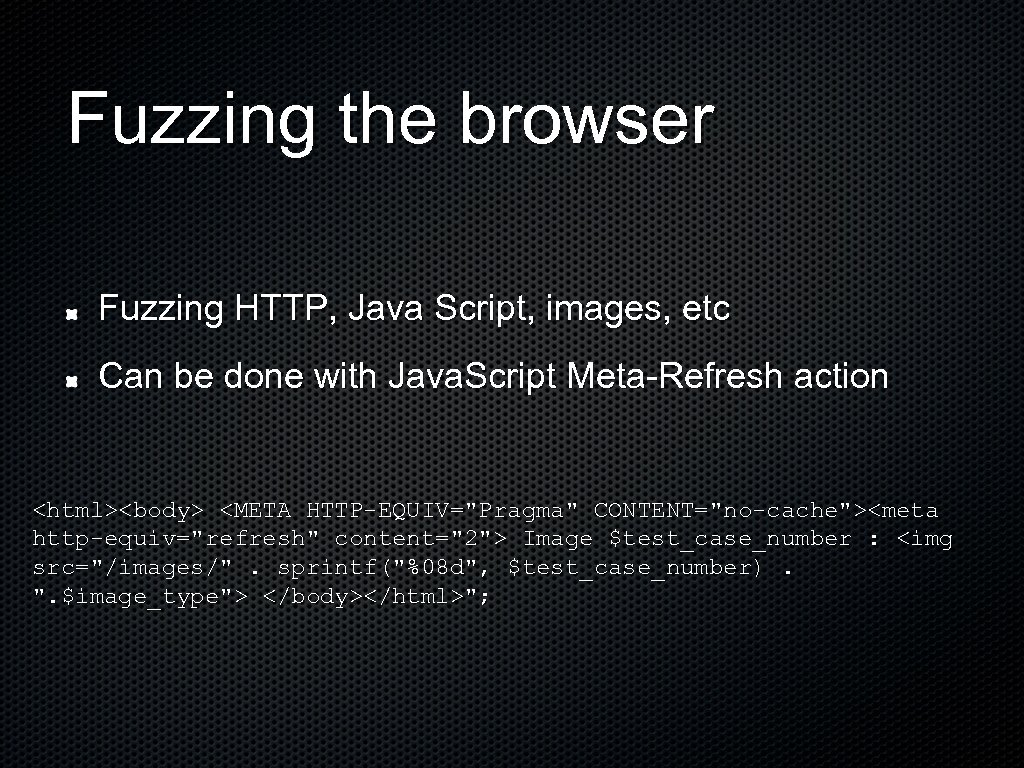 Fuzzing the browser Fuzzing HTTP, Java Script, images, etc Can be done with Java. Script Meta-Refresh action
Fuzzing the browser Fuzzing HTTP, Java Script, images, etc Can be done with Java. Script Meta-Refresh action
 ";
";
 Watching for crashes Use logcat to watch for crashes Examples coming
Watching for crashes Use logcat to watch for crashes Examples coming
 Demo: Fuzzing. ico
Demo: Fuzzing. ico
 Fuzzing Music Player Fuzzing other apps requires actually launching them from the command line and directing them to the fuzzed test cases Remember the apps are Java bytecode Need to launch inside the virtual machine
Fuzzing Music Player Fuzzing other apps requires actually launching them from the command line and directing them to the fuzzed test cases Remember the apps are Java bytecode Need to launch inside the virtual machine
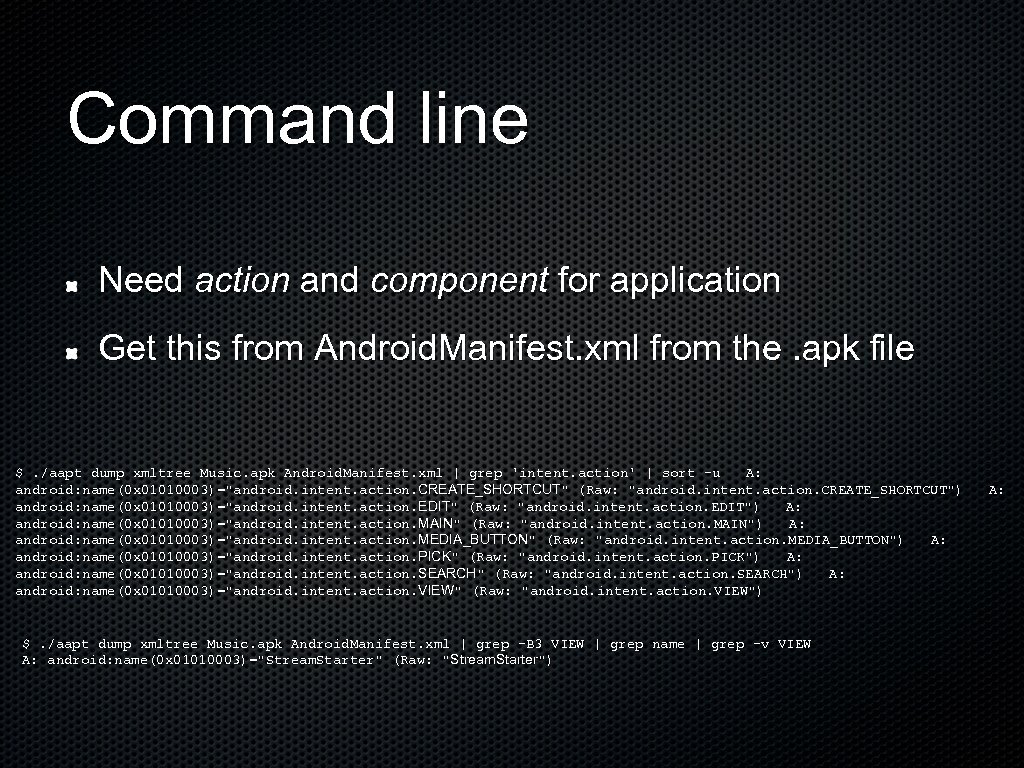 Command line Need action and component for application Get this from Android. Manifest. xml from the. apk file $. /aapt dump xmltree Music. apk Android. Manifest. xml | grep 'intent. action' | sort -u A: android: name(0 x 01010003)="android. intent. action. CREATE_SHORTCUT" (Raw: "android. intent. action. CREATE_SHORTCUT") A: android: name(0 x 01010003)="android. intent. action. EDIT" (Raw: "android. intent. action. EDIT") A: android: name(0 x 01010003)="android. intent. action. MAIN" (Raw: "android. intent. action. MAIN") A: android: name(0 x 01010003)="android. intent. action. MEDIA_BUTTON" (Raw: "android. intent. action. MEDIA_BUTTON") A: android: name(0 x 01010003)="android. intent. action. PICK" (Raw: "android. intent. action. PICK") A: android: name(0 x 01010003)="android. intent. action. SEARCH" (Raw: "android. intent. action. SEARCH") A: android: name(0 x 01010003)="android. intent. action. VIEW" (Raw: "android. intent. action. VIEW") $. /aapt dump xmltree Music. apk Android. Manifest. xml | grep -B 3 VIEW | grep name | grep -v VIEW A: android: name(0 x 01010003)="Stream. Starter" (Raw: "Stream. Starter")
Command line Need action and component for application Get this from Android. Manifest. xml from the. apk file $. /aapt dump xmltree Music. apk Android. Manifest. xml | grep 'intent. action' | sort -u A: android: name(0 x 01010003)="android. intent. action. CREATE_SHORTCUT" (Raw: "android. intent. action. CREATE_SHORTCUT") A: android: name(0 x 01010003)="android. intent. action. EDIT" (Raw: "android. intent. action. EDIT") A: android: name(0 x 01010003)="android. intent. action. MAIN" (Raw: "android. intent. action. MAIN") A: android: name(0 x 01010003)="android. intent. action. MEDIA_BUTTON" (Raw: "android. intent. action. MEDIA_BUTTON") A: android: name(0 x 01010003)="android. intent. action. PICK" (Raw: "android. intent. action. PICK") A: android: name(0 x 01010003)="android. intent. action. SEARCH" (Raw: "android. intent. action. SEARCH") A: android: name(0 x 01010003)="android. intent. action. VIEW" (Raw: "android. intent. action. VIEW") $. /aapt dump xmltree Music. apk Android. Manifest. xml | grep -B 3 VIEW | grep name | grep -v VIEW A: android: name(0 x 01010003)="Stream. Starter" (Raw: "Stream. Starter")
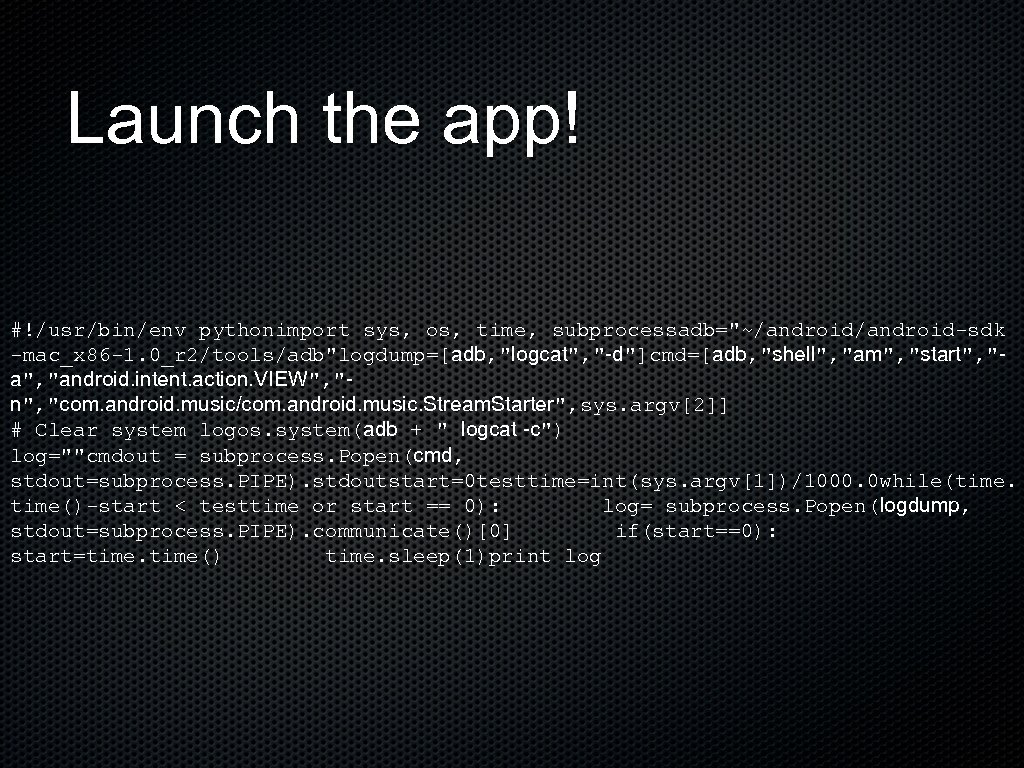 Launch the app! #!/usr/bin/env pythonimport sys, os, time, subprocessadb="~/android-sdk -mac_x 86 -1. 0_r 2/tools/adb"logdump=[adb, "logcat", "-d"]cmd=[adb, "shell", "am", "start", "android. intent. action. VIEW", "n", "com. android. music/com. android. music. Stream. Starter", sys. argv[2]] # Clear system logos. system(adb + " logcat -c") log=""cmdout = subprocess. Popen(cmd, stdout=subprocess. PIPE). stdoutstart=0 testtime=int(sys. argv[1])/1000. 0 while(time()-start < testtime or start == 0): log= subprocess. Popen(logdump, stdout=subprocess. PIPE). communicate()[0] if(start==0): start=time() time. sleep(1)print log
Launch the app! #!/usr/bin/env pythonimport sys, os, time, subprocessadb="~/android-sdk -mac_x 86 -1. 0_r 2/tools/adb"logdump=[adb, "logcat", "-d"]cmd=[adb, "shell", "am", "start", "android. intent. action. VIEW", "n", "com. android. music/com. android. music. Stream. Starter", sys. argv[2]] # Clear system logos. system(adb + " logcat -c") log=""cmdout = subprocess. Popen(cmd, stdout=subprocess. PIPE). stdoutstart=0 testtime=int(sys. argv[1])/1000. 0 while(time()-start < testtime or start == 0): log= subprocess. Popen(logdump, stdout=subprocess. PIPE). communicate()[0] if(start==0): start=time() time. sleep(1)print log
 Demo: Fuzzing Music
Demo: Fuzzing Music
 An exploitable bug in RC 33 Notified Google on Jan 21, 2009 17 days ago Still a 0 -day in G 1 phones In libpvplayer. so (open. Core) In pvmp 3_huffman_parsing() from pvmp 3_huffman_parsing. cpp
An exploitable bug in RC 33 Notified Google on Jan 21, 2009 17 days ago Still a 0 -day in G 1 phones In libpvplayer. so (open. Core) In pvmp 3_huffman_parsing() from pvmp 3_huffman_parsing. cpp
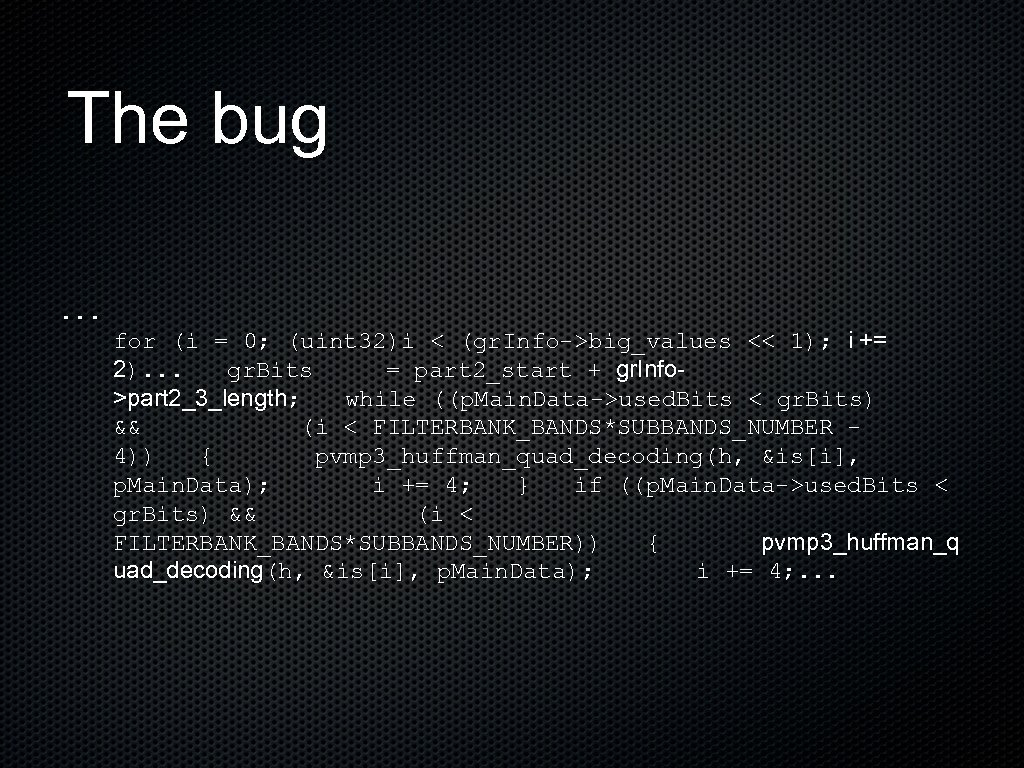 The bug. . . for (i = 0; (uint 32)i < (gr. Info->big_values << 1); i += 2). . . gr. Bits = part 2_start + gr. Info>part 2_3_length; while ((p. Main. Data->used. Bits < gr. Bits) && (i < FILTERBANK_BANDS*SUBBANDS_NUMBER - 4)) { pvmp 3_huffman_quad_decoding(h, &is[i], p. Main. Data); i += 4; } if ((p. Main. Data->used. Bits < gr. Bits) && (i < FILTERBANK_BANDS*SUBBANDS_NUMBER)) { pvmp 3_huffman_q uad_decoding(h, &is[i], p. Main. Data); i += 4; . . .
The bug. . . for (i = 0; (uint 32)i < (gr. Info->big_values << 1); i += 2). . . gr. Bits = part 2_start + gr. Info>part 2_3_length; while ((p. Main. Data->used. Bits < gr. Bits) && (i < FILTERBANK_BANDS*SUBBANDS_NUMBER - 4)) { pvmp 3_huffman_quad_decoding(h, &is[i], p. Main. Data); i += 4; } if ((p. Main. Data->used. Bits < gr. Bits) && (i < FILTERBANK_BANDS*SUBBANDS_NUMBER)) { pvmp 3_huffman_q uad_decoding(h, &is[i], p. Main. Data); i += 4; . . .
 The bug (cont) is is a uint array of size FILTERBANK_BANDS*SUBBANDS_NUMBER pvmp 3_huffman_quad_decoding writes dwords to is[i], is[i+1], is[i+2], is[i+3] grinfo->part 2_3_length is controllable Get 2 dword overflow
The bug (cont) is is a uint array of size FILTERBANK_BANDS*SUBBANDS_NUMBER pvmp 3_huffman_quad_decoding writes dwords to is[i], is[i+1], is[i+2], is[i+3] grinfo->part 2_3_length is controllable Get 2 dword overflow
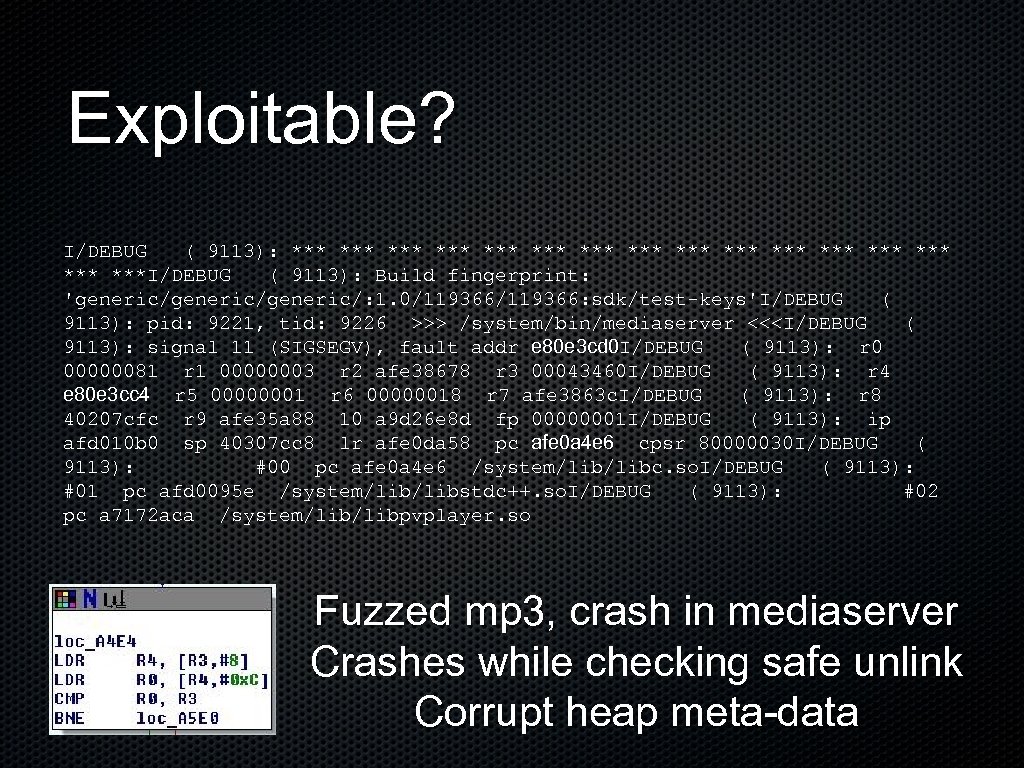 Exploitable? I/DEBUG ( 9113): *** *** *** ***I/DEBUG ( 9113): Build fingerprint: 'generic/generic/: 1. 0/119366: sdk/test-keys'I/DEBUG ( 9113): pid: 9221, tid: 9226 >>> /system/bin/mediaserver <<
Exploitable? I/DEBUG ( 9113): *** *** *** ***I/DEBUG ( 9113): Build fingerprint: 'generic/generic/: 1. 0/119366: sdk/test-keys'I/DEBUG ( 9113): pid: 9221, tid: 9226 >>> /system/bin/mediaserver <<
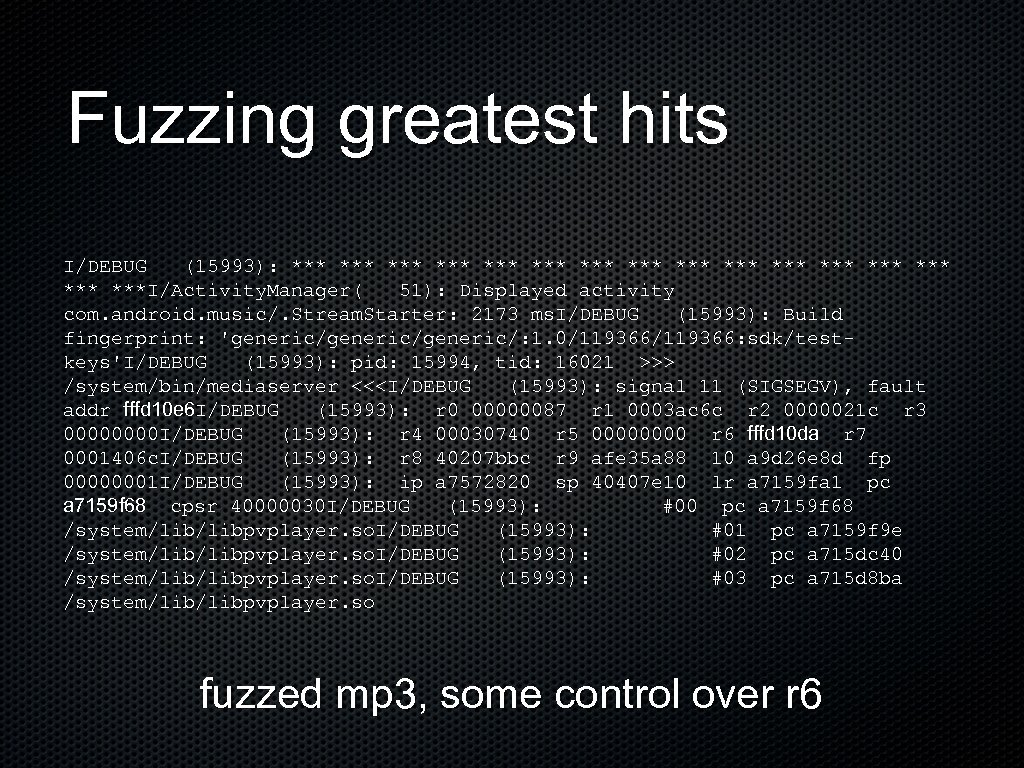 Fuzzing greatest hits I/DEBUG (15993): *** *** *** ***I/Activity. Manager( 51): Displayed activity com. android. music/. Stream. Starter: 2173 ms. I/DEBUG (15993): Build fingerprint: 'generic/generic/: 1. 0/119366: sdk/testkeys'I/DEBUG (15993): pid: 15994, tid: 16021 >>> /system/bin/mediaserver <<
Fuzzing greatest hits I/DEBUG (15993): *** *** *** ***I/Activity. Manager( 51): Displayed activity com. android. music/. Stream. Starter: 2173 ms. I/DEBUG (15993): Build fingerprint: 'generic/generic/: 1. 0/119366: sdk/testkeys'I/DEBUG (15993): pid: 15994, tid: 16021 >>> /system/bin/mediaserver <<
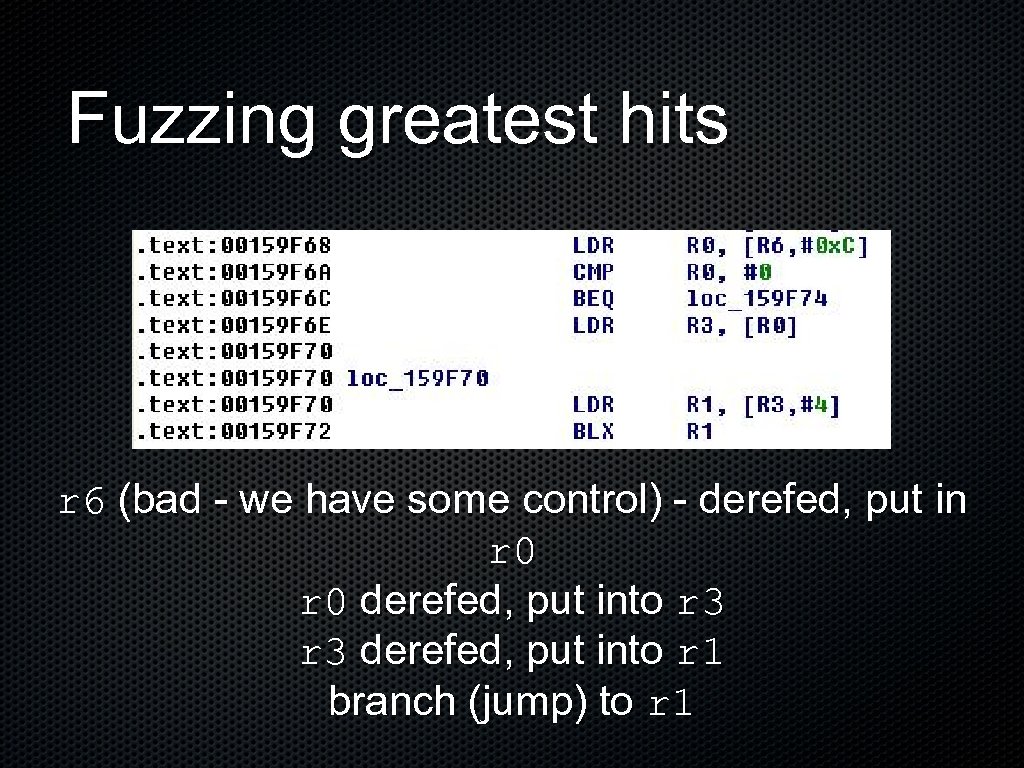 Fuzzing greatest hits r 6 (bad - we have some control) - derefed, put in r 0 derefed, put into r 3 derefed, put into r 1 branch (jump) to r 1
Fuzzing greatest hits r 6 (bad - we have some control) - derefed, put in r 0 derefed, put into r 3 derefed, put into r 1 branch (jump) to r 1
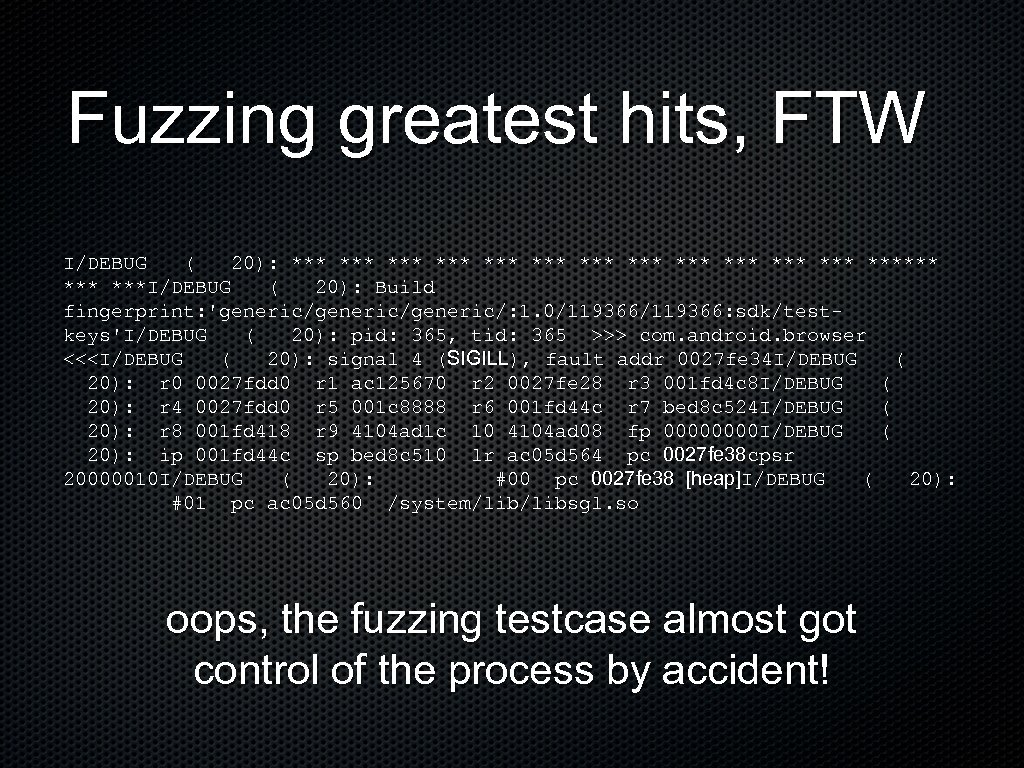 Fuzzing greatest hits, FTW I/DEBUG ( 20): *** *** *** ****** ***I/DEBUG ( 20): Build fingerprint: 'generic/generic/: 1. 0/119366: sdk/testkeys'I/DEBUG ( 20): pid: 365, tid: 365 >>> com. android. browser <<
Fuzzing greatest hits, FTW I/DEBUG ( 20): *** *** *** ****** ***I/DEBUG ( 20): Build fingerprint: 'generic/generic/: 1. 0/119366: sdk/testkeys'I/DEBUG ( 20): pid: 365, tid: 365 >>> com. android. browser <<
 Exploit Dev From an exploit perspective, the phone runs Linux on ARM Bionic library uses Doug Lea malloc Can use standard shellcode (almost) Limited by application sandbox
Exploit Dev From an exploit perspective, the phone runs Linux on ARM Bionic library uses Doug Lea malloc Can use standard shellcode (almost) Limited by application sandbox
 My 1 st exploit timeline Early SDK’s were full of bugs Pwn 2 Own Webkit bug was in the SDK leading to launch October 20 th - saw it was on phone too, reported to Google October 22 nd launch October 25 th - reported in media (no details) November 1 st, OTA update fixes
My 1 st exploit timeline Early SDK’s were full of bugs Pwn 2 Own Webkit bug was in the SDK leading to launch October 20 th - saw it was on phone too, reported to Google October 22 nd launch October 25 th - reported in media (no details) November 1 st, OTA update fixes
 OTA update
OTA update
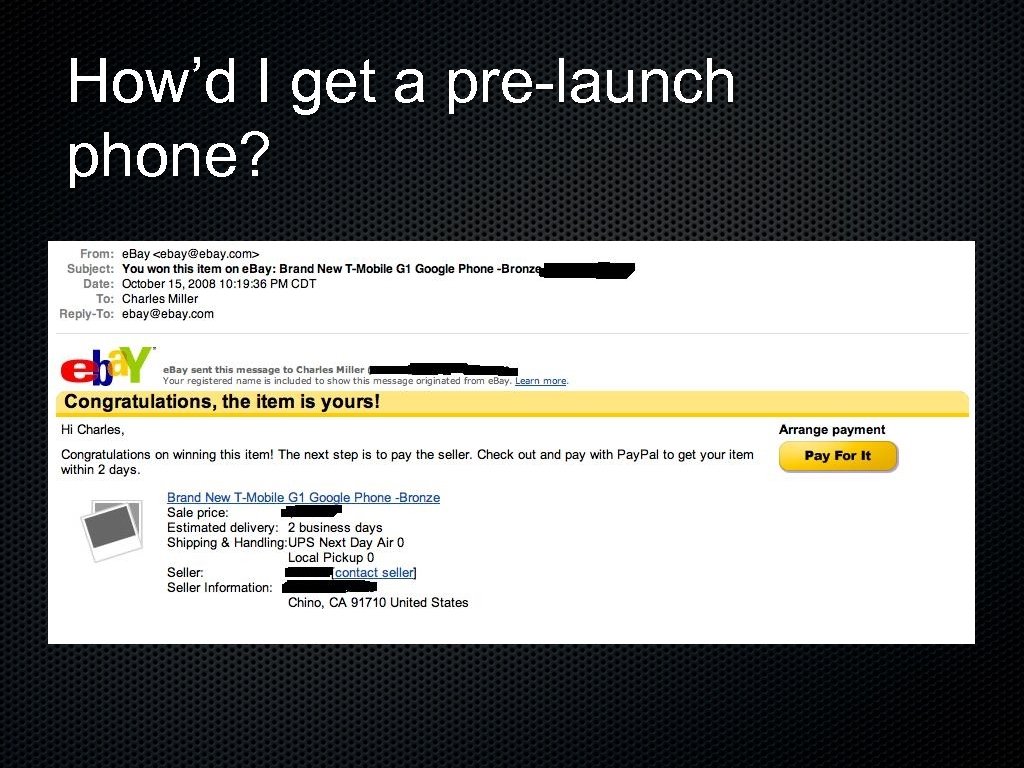 How’d I get a pre-launch phone?
How’d I get a pre-launch phone?
 Android exploits = Linux exploits A diff between the i. Phone and Android versions of the exploit consists of exactly Shellcode - duh data which writes over heap metadata (see below) Address of sled (in sled and in overflow) THAT’S IT! The heap metadata that was crushed was different libc Just had to see what we needed to survive for a bit
Android exploits = Linux exploits A diff between the i. Phone and Android versions of the exploit consists of exactly Shellcode - duh data which writes over heap metadata (see below) Address of sled (in sled and in overflow) THAT’S IT! The heap metadata that was crushed was different libc Just had to see what we needed to survive for a bit
 Exploit dev and emulator My original exploit developed for the emulator worked out of the box on the real device Some addresses may be different Very robust exploits will work on both, but may have to debug on phone, yuck
Exploit dev and emulator My original exploit developed for the emulator worked out of the box on the real device Some addresses may be different Very robust exploits will work on both, but may have to debug on phone, yuck
 ARM basics RISC 2 or 4 byte instructions 16 registers First arguments go in r 0 -r 4 Then stack Syscall number goes in r 7
ARM basics RISC 2 or 4 byte instructions 16 registers First arguments go in r 0 -r 4 Then stack Syscall number goes in r 7
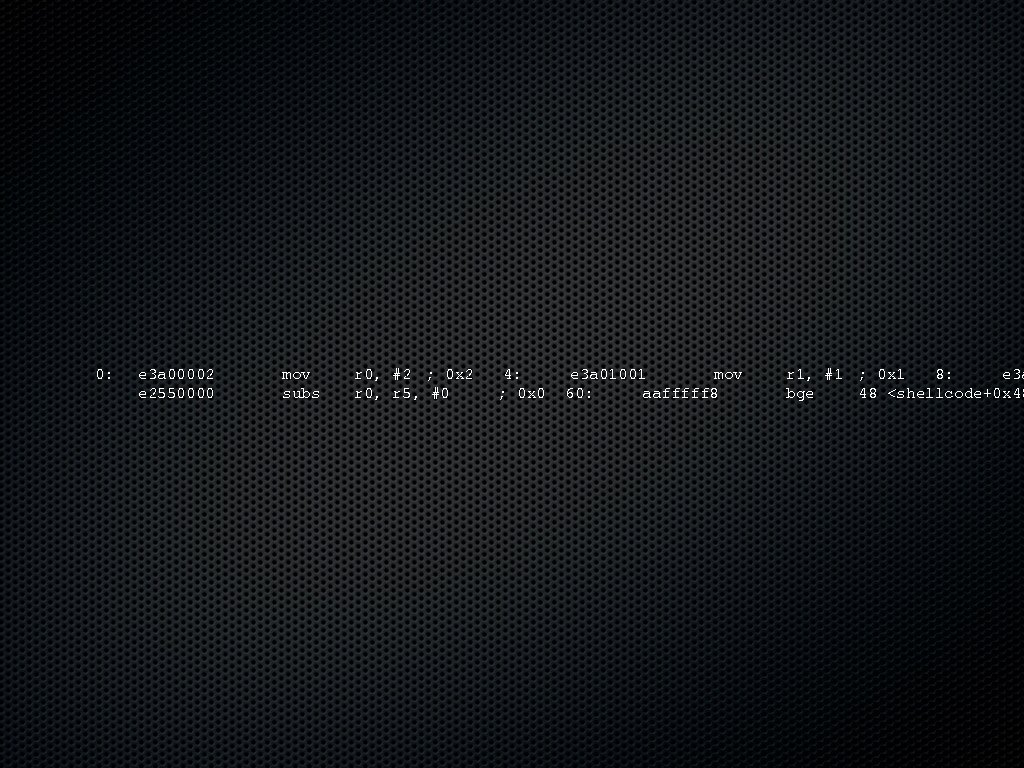 0: e 3 a 00002 e 2550000 mov subs r 0, #2 ; 0 x 2 4: e 3 a 01001 mov r 0, r 5, #0 ; 0 x 0 60: aafffff 8 r 1, #1 ; 0 x 1 8: e 3 a bge 48
0: e 3 a 00002 e 2550000 mov subs r 0, #2 ; 0 x 2 4: e 3 a 01001 mov r 0, r 5, #0 ; 0 x 0 60: aafffff 8 r 1, #1 ; 0 x 1 8: e 3 a bge 48
 Exploit demo
Exploit demo
 After access Straying from the sandbox Payloads
After access Straying from the sandbox Payloads
 Sandbox You can do anything the browser can do ls -l /data/com. android. browser/databases-rw-r--r-- app_1 3608 2009 -01 -20 01: 52 webview. Cache. db-journal-rw-rw---- app_1 17408 2009 -01 -16 05: 04 webview. db-rw-rw---- app_1 12288 2009 -01 -20 01: 52 browser. db-rw-rw---- app_1 6144 2009 -01 -20 01: 51 webview. Cache. db Persist across reboots ls -l /data/com. android. browser/app_plugins/gears. so-rw------- app_1 1 Get SMS messages dumpsys gives alerts, which include SMS info
Sandbox You can do anything the browser can do ls -l /data/com. android. browser/databases-rw-r--r-- app_1 3608 2009 -01 -20 01: 52 webview. Cache. db-journal-rw-rw---- app_1 17408 2009 -01 -16 05: 04 webview. db-rw-rw---- app_1 12288 2009 -01 -20 01: 52 browser. db-rw-rw---- app_1 6144 2009 -01 -20 01: 51 webview. Cache. db Persist across reboots ls -l /data/com. android. browser/app_plugins/gears. so-rw------- app_1 1 Get SMS messages dumpsys gives alerts, which include SMS info
 Payloads Can write standard shellcode Can write shellcode that uses android API Can write C/C++ programs Probably can’t use your own Java apps. . .
Payloads Can write standard shellcode Can write shellcode that uses android API Can write C/C++ programs Probably can’t use your own Java apps. . .
 Example C++ payload Modified gpstest from the android source code Change it not to use libhardware. so Have it call gps_get_hardware_interface from libgps. so Place libgps. so, librpc. so (from phone) in out/target/product/generic/obj/lib/. /agcc. pl -fno-short-enums -o gpstest. cpp -lgps. /gpsteststatus: GPS_STATUS_SESSION_BEGINstatus: GPS_STATUS_ENGINE_ONSV: 15 SNR: 23. 7 Elev: 53. 0 Azim: 146. 0 E AGot Fix: latitude: XX. 577622 longitude: -XX. 604768 altitude: 190. 0. . .
Example C++ payload Modified gpstest from the android source code Change it not to use libhardware. so Have it call gps_get_hardware_interface from libgps. so Place libgps. so, librpc. so (from phone) in out/target/product/generic/obj/lib/. /agcc. pl -fno-short-enums -o gpstest. cpp -lgps. /gpsteststatus: GPS_STATUS_SESSION_BEGINstatus: GPS_STATUS_ENGINE_ONSV: 15 SNR: 23. 7 Elev: 53. 0 Azim: 146. 0 E AGot Fix: latitude: XX. 577622 longitude: -XX. 604768 altitude: 190. 0. . .
 Thanks Mark Daniel - debugging guru Owen Arden - king of fuzz
Thanks Mark Daniel - debugging guru Owen Arden - king of fuzz
 Questions? Contact me at cmiller@securityevaluators. com
Questions? Contact me at cmiller@securityevaluators. com


