35377bcea1f80e9ac6146244c74d4c0c.ppt
- Количество слайдов: 20

Public Key Infrastructure Rocky K. C. Chang 6 March 2007 1

The problem Problem: How do principals learn each other’s public keys for a number of publickey based protocols, such as IPSec, IKE, PGP, S/MIME, or SSL? p Some naïve solutions: p n n Configure each principal with the public key of every other principal (scalability problem). Publish public keys in Web sites or newspapers (authentication and scalability problems). Rocky, K. C. Chang 2

The PKI solution One accepted solution is through trusted intermediaries known as certification authorities (CAs). p Alice generates her public/private key pair. p n n Keep the private key. Take the public key to the CA, say k. The CA has to verify that Alice is who she says she is. The CA then issues a digital statement stating that k belongs to Alice. Rocky, K. C. Chang 3
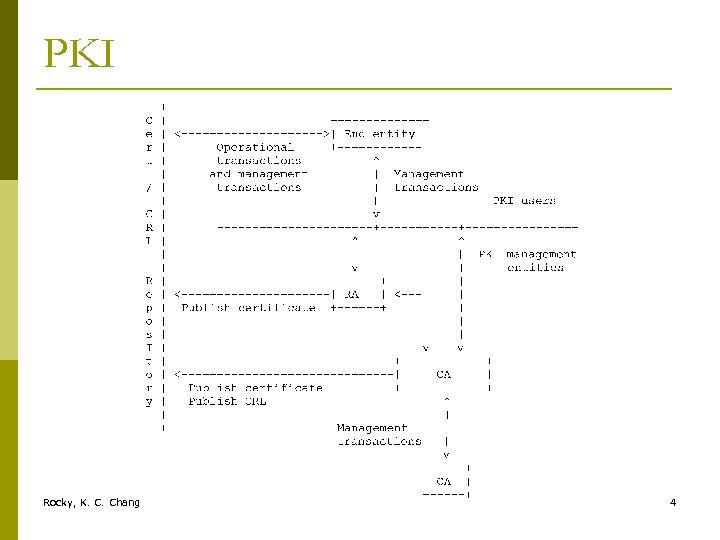
PKI Rocky, K. C. Chang 4
The digital certificate p p CAs digitally sign data structures known as certificates that state the mapping between names and public keys. A typical certificate contains n n n n a serial number (03) the name of the principal being certified (www. comp. polyu. edu. hk) the public key of the principal (PKCS#1 RSA encryption, 140 bytes) the name of the certification authority (HKPU) valid duration of the certificate (not before, not after) extensions a digital signature (PKCS#1 MD 5 with RSA encryption, 128 bytes) Rocky, K. C. Chang 5
X. 509 PKI (PKIX) p PKIX defines a profile to facilitate the use of X. 509 certificates within Internet application (RFC 2459). n n n It specifically profiles the X. 509 v 3 certificate and X. 509 v 2 CRL. This profile does not assume the deployment of an X. 500 directory system. The v 3 certificate format extends the v 2 format by adding provision for additional extension fields, e. g. , p The subject alternative names extension allows additional identities to be bound to the subject of the certificate, such as an Internet electronic mail address, a DNS name, an IP address, and a URI. Rocky, K. C. Chang 6
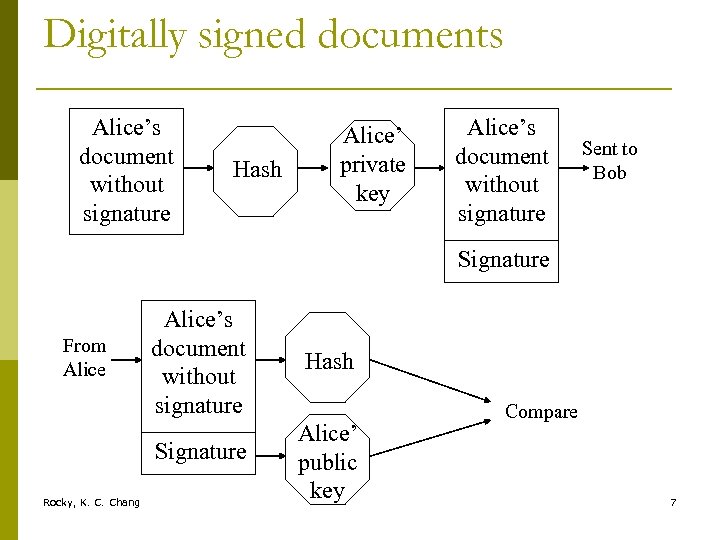
Digitally signed documents Alice’s document without signature Hash Alice’ private key Alice’s document without signature Sent to Bob Signature Rocky, K. C. Chang Hash Signature From Alice’s document without signature Alice’ public key Compare 7
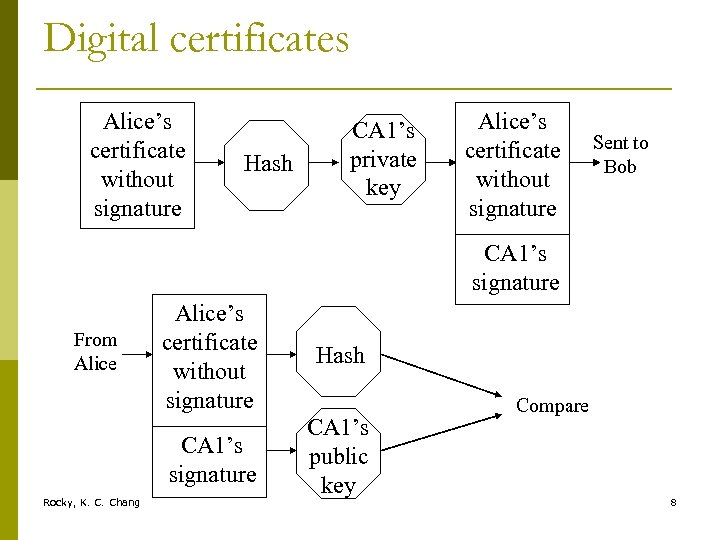
Digital certificates Alice’s certificate without signature Hash CA 1’s private key Alice’s certificate without signature Sent to Bob CA 1’s signature Rocky, K. C. Chang Hash CA 1’s signature From Alice’s certificate without signature CA 1’s public key Compare 8

Multilevel certificates p p If Alice’s certification is issued by CA 1 and Bob knows CA 1’s public key, he can securely obtain Alice’s public key from Alice’s certificate. In general, Bob may not know the public key of Alice’s CA (but he knows CA 3’s public key). Therefore, it is necessary for Bob to obtain a chain of certificates (also known as certification path), e. g. , n n n [CA 2’s public key is P 2] signed by CA 3 [CA 1’s public key is P 3] signed by CA 2 [Alice’s public key is P 4] signed by CA 1 Rocky, K. C. Chang 9

Expiration p No cryptographic key should be used indefinitely. n A certificate should not be valid forever either. Expiration is also important in keeping information up-to-date. p Not before and not after p n Participants in a PKI needs a clock. Rocky, K. C. Chang 10

Separate registration authority A HR department verifies the employees and the IT department runs as the CA. p Adding a third party RA complicates the protocol sigificantly. p The best model for this scenario: p n n IT acts as a CA and the HR as a sub-CA. Have IT and HR serve as separate entities and specify the HR-IT interaction. Rocky, K. C. Chang 11

Examples p Every HK resident can communicate with each other securely. n n p A company has a VPN to allow its employees to access to the corporate network from outside. n n p Have the post office serve as the CA for HK. Every resident is issued a certificate. The company acts as the CA. Each employee is issued a certificate. A bank allows its customers to perform financial transactions on the bank’s website. n n The bank is the CA. The customers are issued certificates. Rocky, K. C. Chang 12

Certificate revocation p p The hardest problem to solve in a PKI is revocation. For various reasons (e. g. , employment termination, key compromised), a certificate may no longer be valid before the expiration date. Requirements: speed and reliability of revocation. Two solutions n n Define a Certification Revocation List (CRL), which contains serial numbers that should not be honored. Fast expiration: each certificate is given a very short expiration time. Rocky, K. C. Chang 13

Certification Revocation List p A CA periodically issues a signed CRL available in a public repository. n p An advantage of this approach is that CRLs may be distributed by exactly the same means as certificates. Therefore, a certificate is valid if it has a valid CA signature and has not expired and is not listed in the CA’s most recent CRL. Rocky, K. C. Chang 14

Fast expiration Each time Alice wants to use her certificate, she gets a new one from the CA. p The major advantage is using the already available certificate issuing mechanism. p Whether this approach is possible depends on mostly whether the application demands instantaneous revocation. p Rocky, K. C. Chang 15

PKI in reality p The PKI ties Alice’s public key to her name. n n p What name should be used in a PKI? Identical names A person with multiple names Cannot use HKID, Authority of assigning keys to names n n What makes that CA authoritative with respect to these names? Who has the authority of assigning keys in a universal PKI? Rocky, K. C. Chang 16

PKI in reality (cont’d) p Trust of being the CA n n p What/who can be trusted as a CA in a universal PKI? The trust relationships that are used by the CA are ones that already exist and are based on contractual relationships. Authorization n n Who is authorized to do what? Keys (PKI) names (ACL) permissions Direct authorization: Keys permissions E. g. , a bank’s PKI ties Alice’s key to the credential that allow access to Alice’s account. E. g. , a door lock does not recognize who holds the key. Rocky, K. C. Chang 17

A more realistic PKI p Each application/organization has its own CA. n n n p The world consists of a large number of small PKIs. Each user is a member of many different PKIs at the same time. Cross certification The PKI’s main purpose is to tie a credential to the key. n Not to tie keys to names. Rocky, K. C. Chang 18

Summary p p There will never be a universal PKI is difficult to manage and use. n p The PKI’s main purpose is to tie a credential to the key. n p p The 5 th Annual PKI R&D Workshop: “Making PKI Easy to Use. ” It is not about the key management problem. Choose between a key server approach and a PKI approach. Nevertheless, a number of PKI initiatives is still going on, e. g. , Federal PKI (FPKI) in the US. Rocky, K. C. Chang 19

Acknowledgments p The notes are prepared mostly based on n n N. Ferguson and B. Schneier, Practical Cryptography, Wiley, 2003. R. Housley, W. Ford, W. Polk, D. Solo, “Internet X. 509 Public Key Infrastructure Certificate and CRL Profile, ” RFC 2459, January 1999. Rocky, K. C. Chang 20
35377bcea1f80e9ac6146244c74d4c0c.ppt