134769fa3af32a191b7e70bd0f01a5d9.ppt
- Количество слайдов: 35

PUBLIC KEY CRYPTOGRAPHY IN THE BOUNDED RETRIEVAL MODEL Based on joint works with Joël Alwen, Moni Naor, Gil Segev, Shabsi Walfish and Daniel Wichs Speaker: Yevgeniy Dodis (NYU)

Leakage Attacks
Modeling Incomplete Leakage
Modeling Incomplete Leakage
Only Computation Leaks Information

Crypto Primitives with Leakage
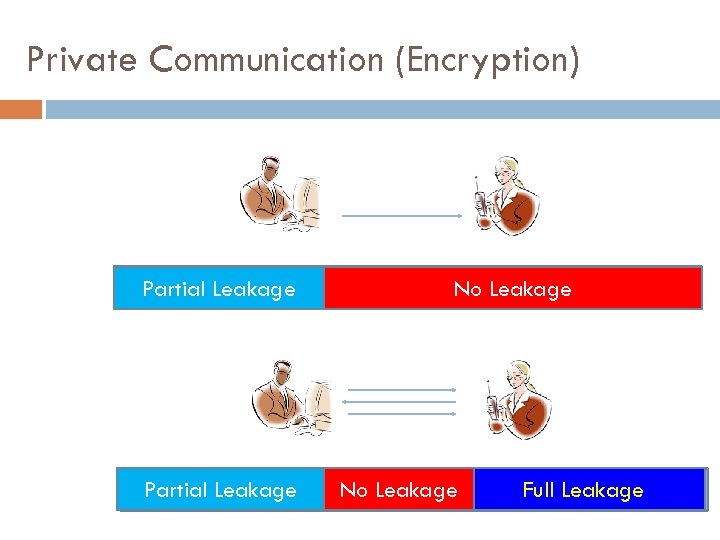
Private Communication (Encryption) Partial Leakage No Leakage Full Leakage

Recent History

Our Results
Efficiency of Our Results
Roadmap
Identification Schemes Learning Stage Impersonation Stage
Leakage-Resilient Identification Learning Stage Impersonation Stage
Roadmap
Okamoto’s ID Scheme

Relative Leakage-Resilience

Relative Leakage-Resilience
Roadmap

Direct Products: Naive Attempt

Direct Products: Problem 1 • Invisible Key Updates! • store Sig. Key “offline” • periodically refresh SK = (sk 1, …, sk. N) • public key Ver. Key does not change ! • secure as long as < L leakage between refreshes • approaches “continuous leakage”, but without assuming “only computation leaks information”

Direct Products: Problem 2

Direct Products: Problem 3

Direct Products: Our Solution

Direct Products: Our Solution
Roadmap
Compressing Communication
Parameters of BRM ID Schemes
Roadmap

Leakage-Resilient Signatures
From ID to Signatures
Roadmap
Message has entropy! Forward secrecy!

What does it mean? For example…
Roadmap

Conclusions + Open Problems
134769fa3af32a191b7e70bd0f01a5d9.ppt