dd301aaeeeef7dbc772474f6b915df25.ppt
- Количество слайдов: 56
 PSIRP Architectural Components Part 2 Walter Wong Nomadic. Lab & HIIT 10. 02. 2010
PSIRP Architectural Components Part 2 Walter Wong Nomadic. Lab & HIIT 10. 02. 2010
 Outline Forwarding Mechanism ◦ Bloom-filters ◦ z. Filters ◦ Link Identity Tables (LITs) Topology Management & Formation Network Attachment
Outline Forwarding Mechanism ◦ Bloom-filters ◦ z. Filters ◦ Link Identity Tables (LITs) Topology Management & Formation Network Attachment
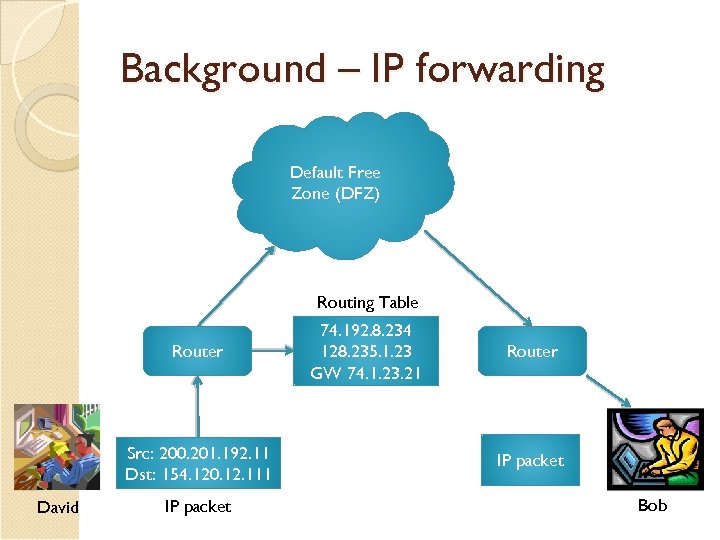 Background – IP forwarding Default Free Zone (DFZ) Routing Table Router Src: 200. 201. 192. 11 Dst: 154. 120. 12. 111 David IP packet 74. 192. 8. 234 128. 235. 1. 23 GW 74. 1. 23. 21 Router IP packet Bob
Background – IP forwarding Default Free Zone (DFZ) Routing Table Router Src: 200. 201. 192. 11 Dst: 154. 120. 12. 111 David IP packet 74. 192. 8. 234 128. 235. 1. 23 GW 74. 1. 23. 21 Router IP packet Bob
 IP forwarding IP address ◦ Hierarchical topologic semantic (reflects some location in the network) Forwarding ◦ ◦ Longest prefix matching Route aggregation Default route towards the Internet Core Bidirectional (reverse path is easily computed) Drawback ◦ Identification and location entangled
IP forwarding IP address ◦ Hierarchical topologic semantic (reflects some location in the network) Forwarding ◦ ◦ Longest prefix matching Route aggregation Default route towards the Internet Core Bidirectional (reverse path is easily computed) Drawback ◦ Identification and location entangled
 Forwarding in PSIRP Major challenges ◦ there is no IP end-point in PSIRP ◦ Fid has no topological information, but cryptographic semantics ◦ No default forwarding layer for packets ◦ Unidirectional ◦ No route aggregation Benefit ◦ Forwarding based on content identifiers instead of location ◦ Data is identified in the network level
Forwarding in PSIRP Major challenges ◦ there is no IP end-point in PSIRP ◦ Fid has no topological information, but cryptographic semantics ◦ No default forwarding layer for packets ◦ Unidirectional ◦ No route aggregation Benefit ◦ Forwarding based on content identifiers instead of location ◦ Data is identified in the network level
 Forwarding – Design Goals Efficient ◦ Low latency and high bandwidth Line speed Secure: protection against DDo. S capabilities Multicast support Content-centric naming Path splitting ◦ Slow path (routing, policies, security, topology management) ◦ Fast path (forwarding path)
Forwarding – Design Goals Efficient ◦ Low latency and high bandwidth Line speed Secure: protection against DDo. S capabilities Multicast support Content-centric naming Path splitting ◦ Slow path (routing, policies, security, topology management) ◦ Fast path (forwarding path)
 Intra-domain Forwarding Characteristics ◦ Links have identifiers (Link IDs) ◦ Source routing mechanism ◦ Install forwarding state on demand (traffic aggregation) Topology Manager ◦ Constructs Bloom filter-based forwarding identifiers
Intra-domain Forwarding Characteristics ◦ Links have identifiers (Link IDs) ◦ Source routing mechanism ◦ Install forwarding state on demand (traffic aggregation) Topology Manager ◦ Constructs Bloom filter-based forwarding identifiers
 Bloom Filters – Theory Probabilistic data structure Aggregates a set of information Allows for membership tests ◦ Given one key, is it in the bloom filter? Drawback ◦ False positives
Bloom Filters – Theory Probabilistic data structure Aggregates a set of information Allows for membership tests ◦ Given one key, is it in the bloom filter? Drawback ◦ False positives
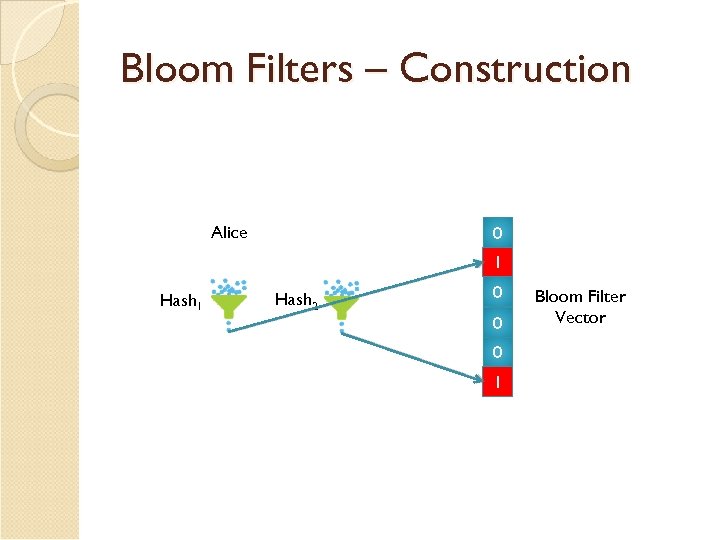 Bloom Filters – Construction Alice 0 1 0 Hash 1 Hash 2 0 0 1 Bloom Filter Vector
Bloom Filters – Construction Alice 0 1 0 Hash 1 Hash 2 0 0 1 Bloom Filter Vector
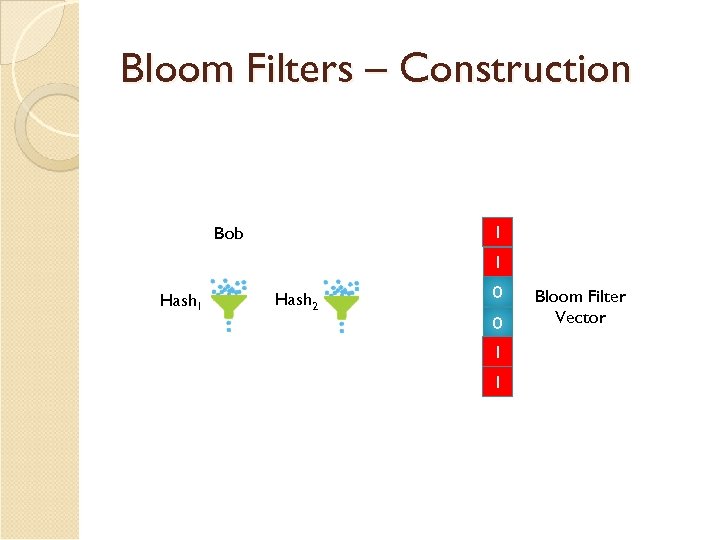 Bloom Filters – Construction 1 0 Bob 1 0 Hash 1 Hash 2 0 0 1 Bloom Filter Vector
Bloom Filters – Construction 1 0 Bob 1 0 Hash 1 Hash 2 0 0 1 Bloom Filter Vector
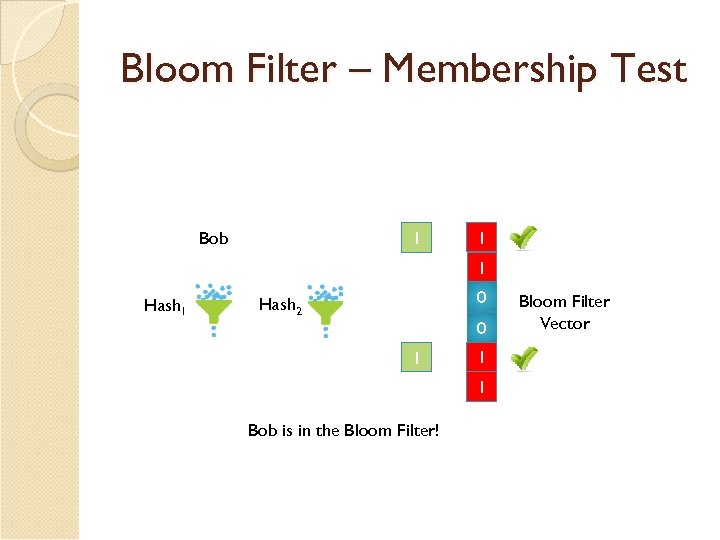 Bloom Filter – Membership Test Bob 1 1 0 0 1 Hash 1 0 Hash 2 0 1 1 0 Bob is in the Bloom Filter! Bloom Filter Vector
Bloom Filter – Membership Test Bob 1 1 0 0 1 Hash 1 0 Hash 2 0 1 1 0 Bob is in the Bloom Filter! Bloom Filter Vector
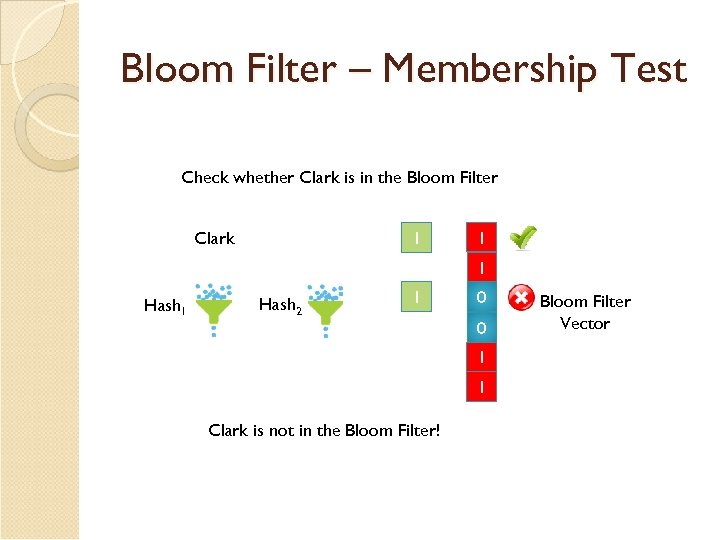 Bloom Filter – Membership Test Check whether Clark is in the Bloom Filter Clark 1 1 0 Hash 1 Hash 2 1 0 0 1 0 Clark is not in the Bloom Filter! Bloom Filter Vector
Bloom Filter – Membership Test Check whether Clark is in the Bloom Filter Clark 1 1 0 Hash 1 Hash 2 1 0 0 1 0 Clark is not in the Bloom Filter! Bloom Filter Vector
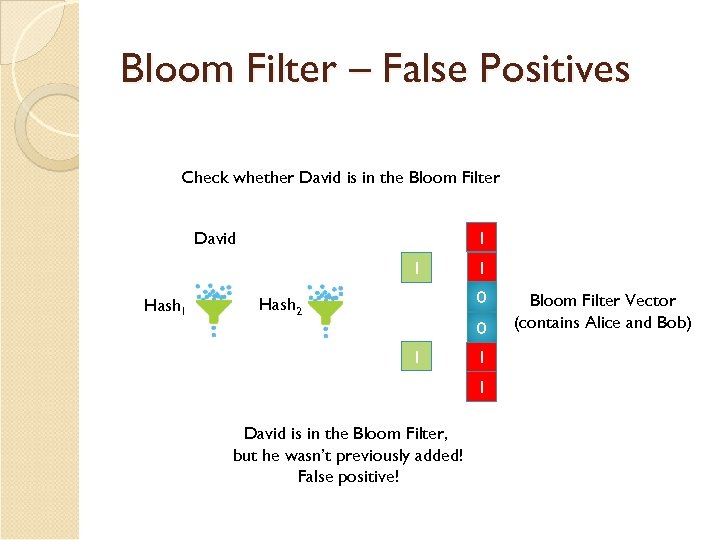 Bloom Filter – False Positives Check whether David is in the Bloom Filter 1 0 David 1 Hash 1 1 0 0 Hash 2 0 1 1 0 David is in the Bloom Filter, but he wasn’t previously added! False positive! Bloom Filter Vector (contains Alice and Bob)
Bloom Filter – False Positives Check whether David is in the Bloom Filter 1 0 David 1 Hash 1 1 0 0 Hash 2 0 1 1 0 David is in the Bloom Filter, but he wasn’t previously added! False positive! Bloom Filter Vector (contains Alice and Bob)
 False Positives – Math False positive rate: ◦ Fp = (0, 6185)^m/n ◦ k = (m/n)ln 2 m = bits in the data structure n = number of keys in the data structure k = number of different hash functions
False Positives – Math False positive rate: ◦ Fp = (0, 6185)^m/n ◦ k = (m/n)ln 2 m = bits in the data structure n = number of keys in the data structure k = number of different hash functions
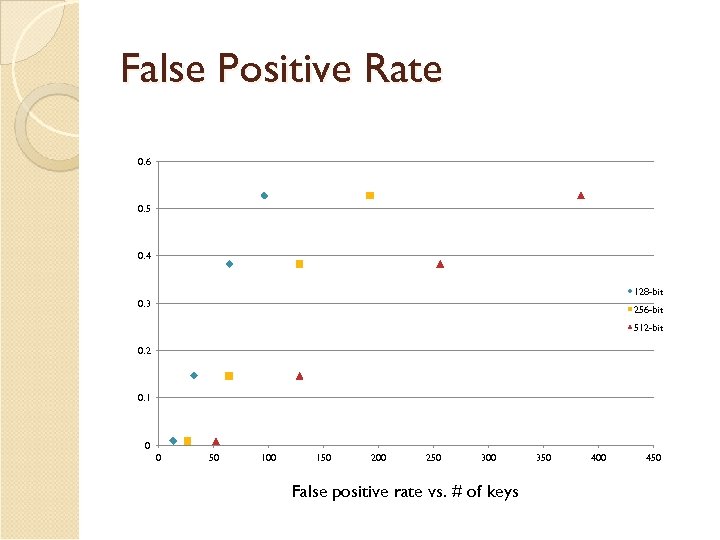 False Positive Rate 0. 6 0. 5 0. 4 128 -bit 0. 3 256 -bit 512 -bit 0. 2 0. 1 0 0 50 100 150 200 250 300 False positive rate vs. # of keys 350 400 450
False Positive Rate 0. 6 0. 5 0. 4 128 -bit 0. 3 256 -bit 512 -bit 0. 2 0. 1 0 0 50 100 150 200 250 300 False positive rate vs. # of keys 350 400 450
 Bloom Filter – Summary Probabilistic data structure ◦ False positives ◦ Never false negatives ◦ Trade-off between storage and false positives Efficient membership queries ◦ Hash functions ◦ Line speed
Bloom Filter – Summary Probabilistic data structure ◦ False positives ◦ Never false negatives ◦ Trade-off between storage and false positives Efficient membership queries ◦ Hash functions ◦ Line speed
 Flat Identifiers Routing How to route flat identifiers in the network? ◦ Bloom filters? General idea ◦ Add the network interfaces where packets must pass through in the Bloom filter ◦ Forwarding nodes check which network interfaces are included in the Bloom filter
Flat Identifiers Routing How to route flat identifiers in the network? ◦ Bloom filters? General idea ◦ Add the network interfaces where packets must pass through in the Bloom filter ◦ Forwarding nodes check which network interfaces are included in the Bloom filter
 Forwarding Header Construction Each link in PSIRP has an identifier ◦ Link identifier (LID) ◦ Unidirectional Topology system ◦ Conceptual delivery tree ◦ Retrieve all links where the data must pass through ◦ Forwarding tree
Forwarding Header Construction Each link in PSIRP has an identifier ◦ Link identifier (LID) ◦ Unidirectional Topology system ◦ Conceptual delivery tree ◦ Retrieve all links where the data must pass through ◦ Forwarding tree
 Data Forwarding Default case ◦ Source-routing based approach ◦ Encode all link Ids into a Bloom filter in the packet header ◦ Check which output interface has LIds included in the Bloom filter z. Filter ◦ In-packet Bloom-filter ◦ Used to take the forwarding decision
Data Forwarding Default case ◦ Source-routing based approach ◦ Encode all link Ids into a Bloom filter in the packet header ◦ Check which output interface has LIds included in the Bloom filter z. Filter ◦ In-packet Bloom-filter ◦ Used to take the forwarding decision
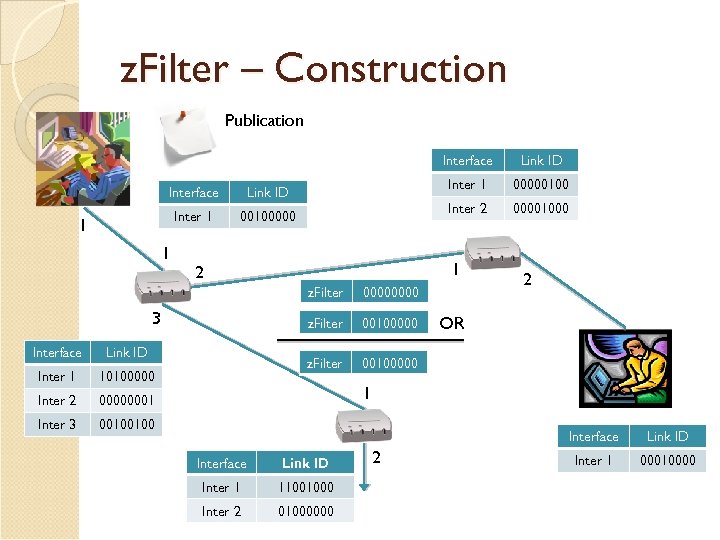 z. Filter – Construction Publication Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 2 00100000001 Inter 3 00100000 z. Filter 10100000 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 OR 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Construction Publication Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 2 00100000001 Inter 3 00100000 z. Filter 10100000 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 OR 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
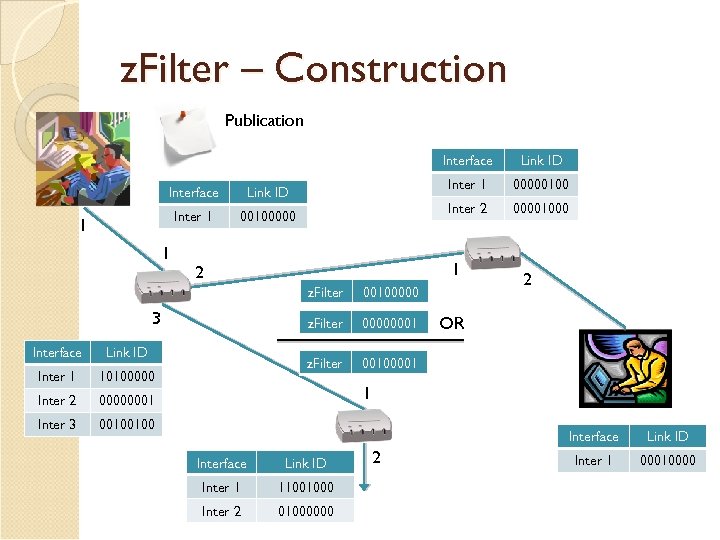 z. Filter – Construction Publication Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 2 00100001 00000001 Inter 3 00000001 z. Filter 10100000 00100000 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 OR 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Construction Publication Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 2 00100001 00000001 Inter 3 00000001 z. Filter 10100000 00100000 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 OR 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
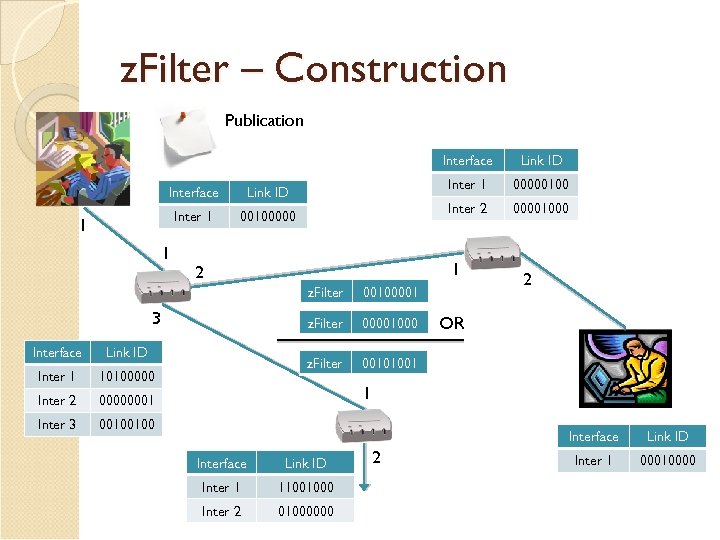 z. Filter – Construction Publication Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 2 00101001 00000001 Inter 3 00001000 z. Filter 10100000 00100001 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 OR 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Construction Publication Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 2 00101001 00000001 Inter 3 00001000 z. Filter 10100000 00100001 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 OR 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
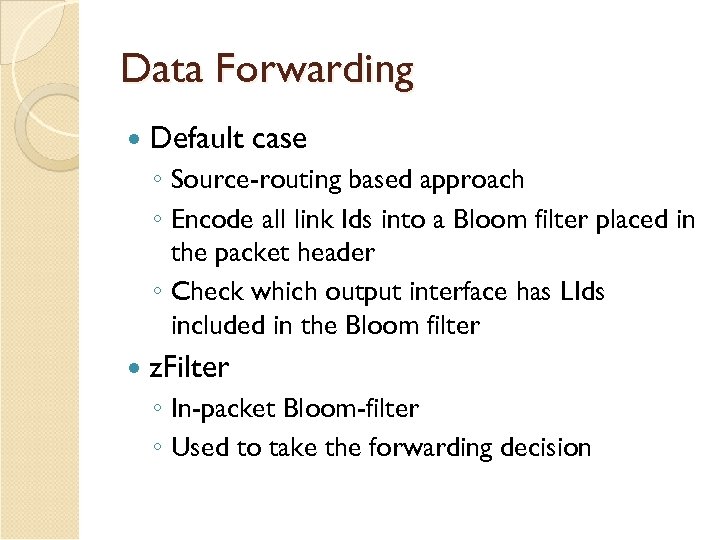 Data Forwarding Default case ◦ Source-routing based approach ◦ Encode all link Ids into a Bloom filter placed in the packet header ◦ Check which output interface has LIds included in the Bloom filter z. Filter ◦ In-packet Bloom-filter ◦ Used to take the forwarding decision
Data Forwarding Default case ◦ Source-routing based approach ◦ Encode all link Ids into a Bloom filter placed in the packet header ◦ Check which output interface has LIds included in the Bloom filter z. Filter ◦ In-packet Bloom-filter ◦ Used to take the forwarding decision
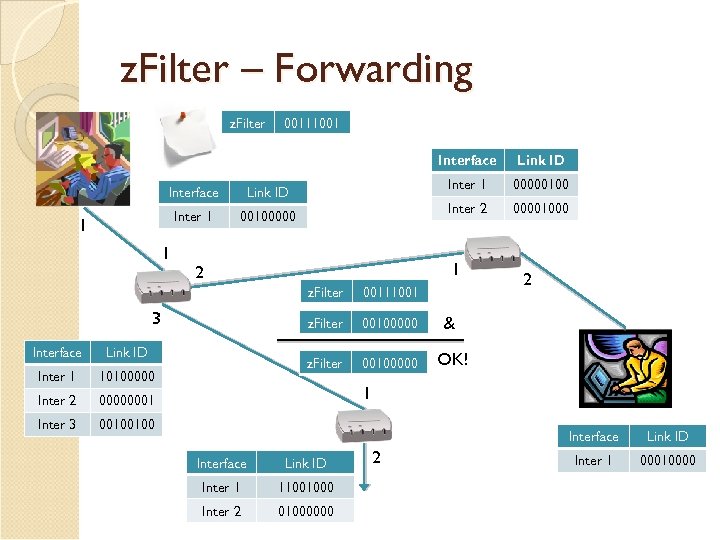 z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00100000 2 & OK! 00000001 Inter 3 00100000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00100000 2 & OK! 00000001 Inter 3 00100000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
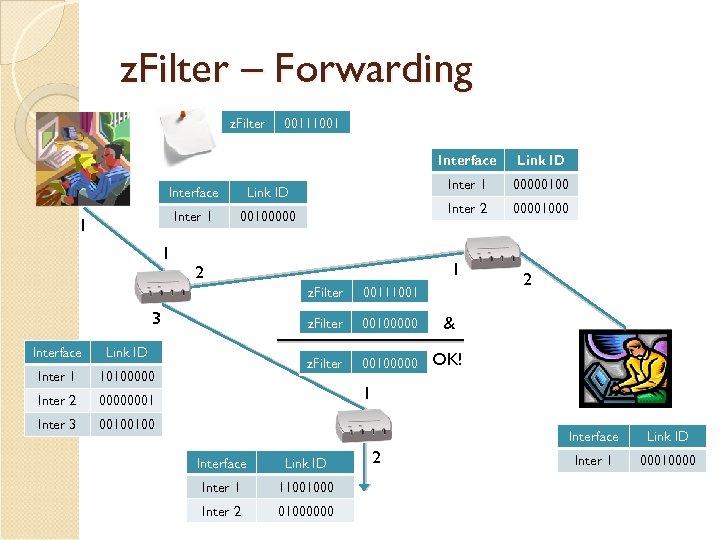 z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00100000 2 & OK! 00000001 Inter 3 00100000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00100000 2 & OK! 00000001 Inter 3 00100000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
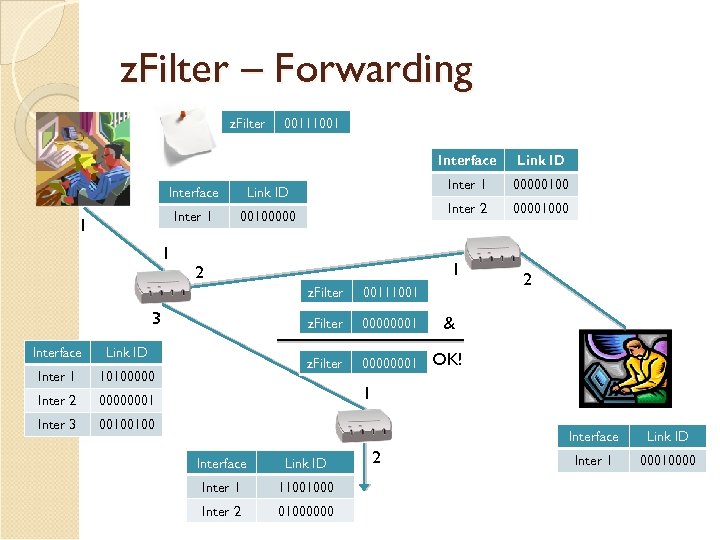 z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00000001 2 & OK! 00000001 Inter 3 00000001 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00000001 2 & OK! 00000001 Inter 3 00000001 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
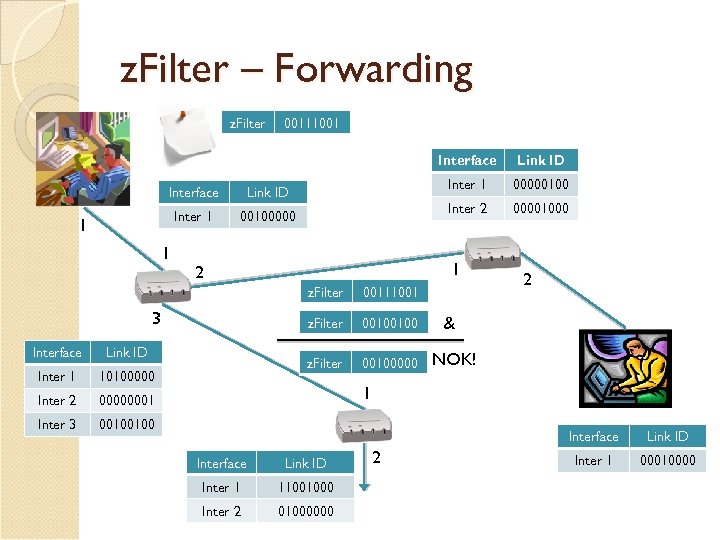 z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 00100000001 Inter 3 00100100 z. Filter 10100000 00111001 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 2 & NOK! 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 z. Filter Interface Inter 1 Inter 2 00100000001 Inter 3 00100100 z. Filter 10100000 00111001 z. Filter Link ID 00001000 1 2 3 00000100 Inter 2 Link ID 00100100 2 & NOK! 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
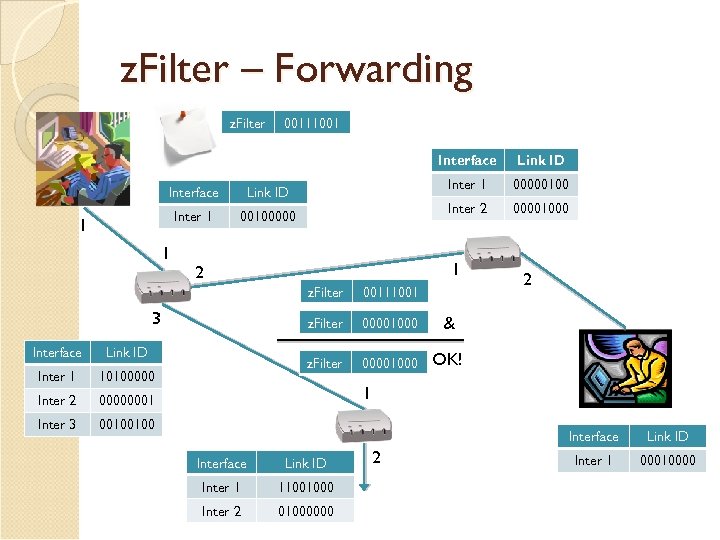 z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00001000 2 & OK! 00000001 Inter 3 00001000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00001000 2 & OK! 00000001 Inter 3 00001000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
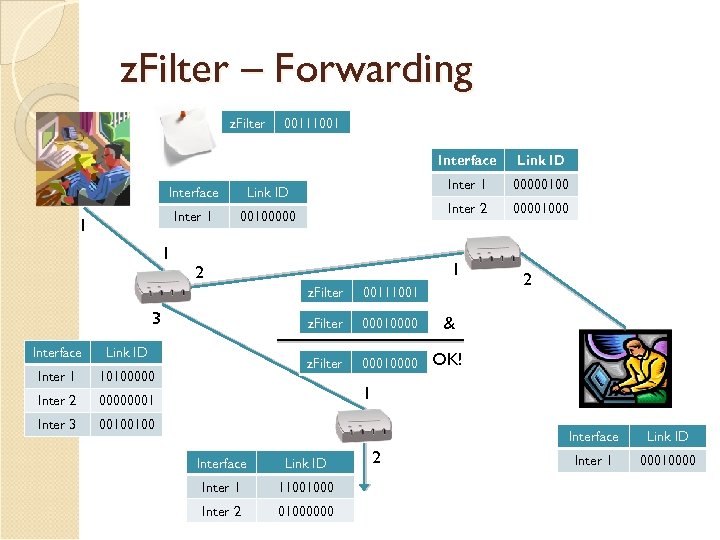 z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00010000 2 & OK! 00000001 Inter 3 00010000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
z. Filter – Forwarding z. Filter 00111001 Interface Inter 1 00100000 1 1 00000100 Inter 2 Link ID 00001000 1 2 z. Filter Interface Link ID Inter 1 10100000 Inter 2 00010000 2 & OK! 00000001 Inter 3 00010000 z. Filter 3 00111001 00100100 1 Interface Link ID Inter 1 11001000 Inter 2 01000000 2 Link ID Inter 1 00010000
 z. Filter – Summary Efficient flat identifier routing ◦ Currrent z. Filter = 256 bits ◦ Link IDs are added in the z. Filter (OR operation) ◦ Verification requires one comparison (AND operation) Drawback ◦ Possible false positive ◦ Wrong forwarding path
z. Filter – Summary Efficient flat identifier routing ◦ Currrent z. Filter = 256 bits ◦ Link IDs are added in the z. Filter (OR operation) ◦ Verification requires one comparison (AND operation) Drawback ◦ Possible false positive ◦ Wrong forwarding path
 Link Identity Tags (LITs) Solution to reduce false positives Each link has d distinct LITs Allows for constructing z. Filters with higher number of zeros Topology Manager has more options to construct the z. Filter for the same path
Link Identity Tags (LITs) Solution to reduce false positives Each link has d distinct LITs Allows for constructing z. Filters with higher number of zeros Topology Manager has more options to construct the z. Filter for the same path
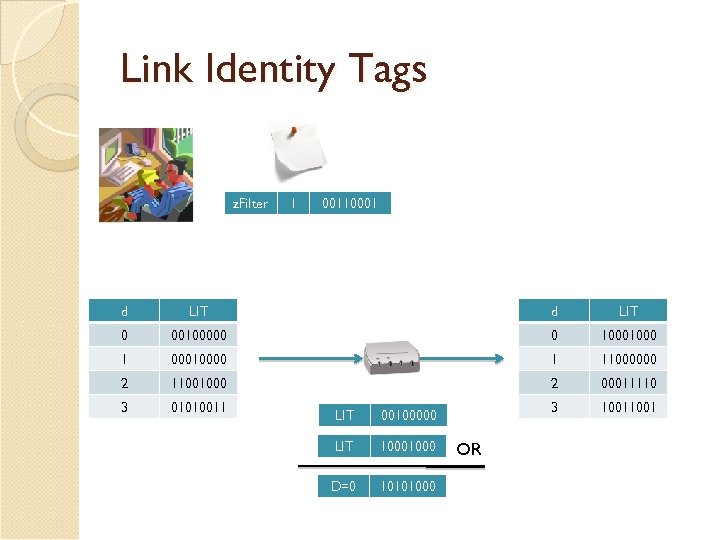 Link Identity Tags z. Filter 1 00110001 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 00100000 LIT 1000 D=0 10101000 OR
Link Identity Tags z. Filter 1 00110001 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 00100000 LIT 1000 D=0 10101000 OR
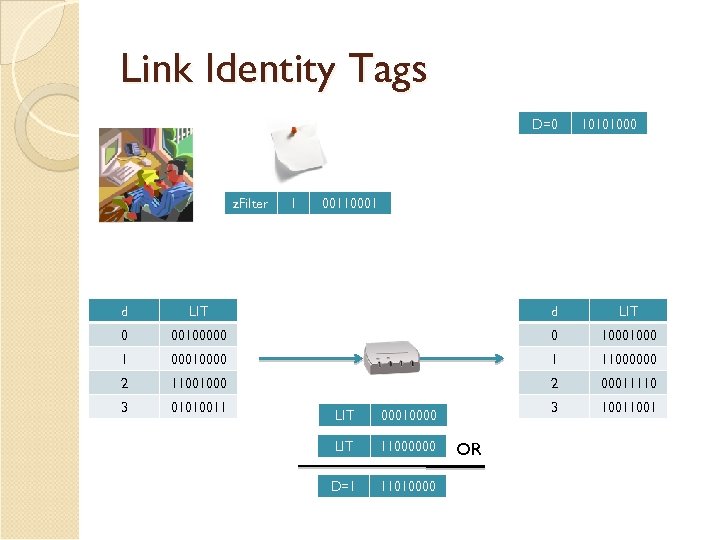 Link Identity Tags D=0 z. Filter 1 10101000 00110001 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 00010000 LIT 11000000 D=1 11010000 OR
Link Identity Tags D=0 z. Filter 1 10101000 00110001 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 00010000 LIT 11000000 D=1 11010000 OR
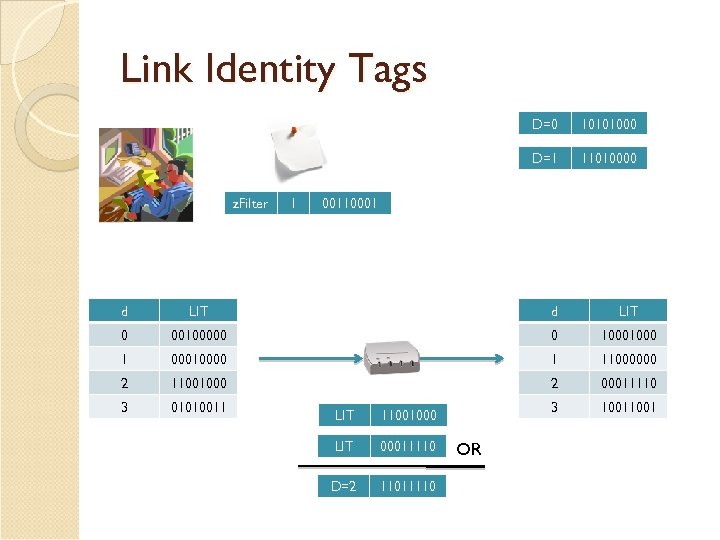 Link Identity Tags D=0 D=1 z. Filter 1 10101000 11010000 00110001 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 11001000 LIT 00011110 D=2 11011110 OR
Link Identity Tags D=0 D=1 z. Filter 1 10101000 11010000 00110001 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 11001000 LIT 00011110 D=2 11011110 OR
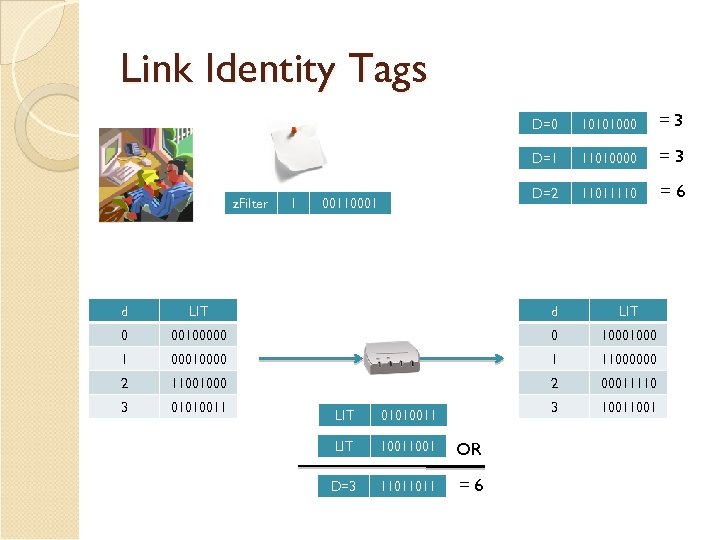 Link Identity Tags D=0 1 11010000 =3 D=2 00110001 =3 D=1 z. Filter 10101000 11011110 =6 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 01010011 LIT 1001 OR D=3 11011011 =6
Link Identity Tags D=0 1 11010000 =3 D=2 00110001 =3 D=1 z. Filter 10101000 11011110 =6 d LIT 0 00100000 0 1000 1 00010000 1 11000000 2 11001000 2 00011110 3 01010011 3 1001 LIT 01010011 LIT 1001 OR D=3 11011011 =6
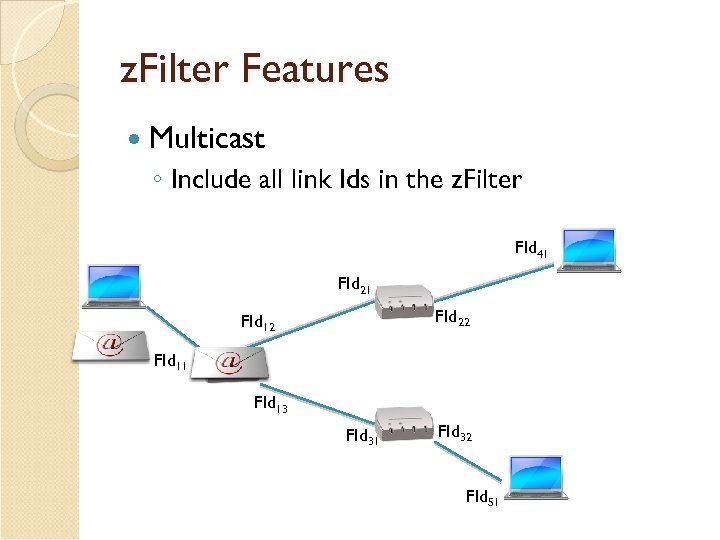 z. Filter Features Multicast ◦ Include all link Ids in the z. Filter FId 41 FId 22 FId 11 FId 13 FId 31 FId 32 FId 51
z. Filter Features Multicast ◦ Include all link Ids in the z. Filter FId 41 FId 22 FId 11 FId 13 FId 31 FId 32 FId 51
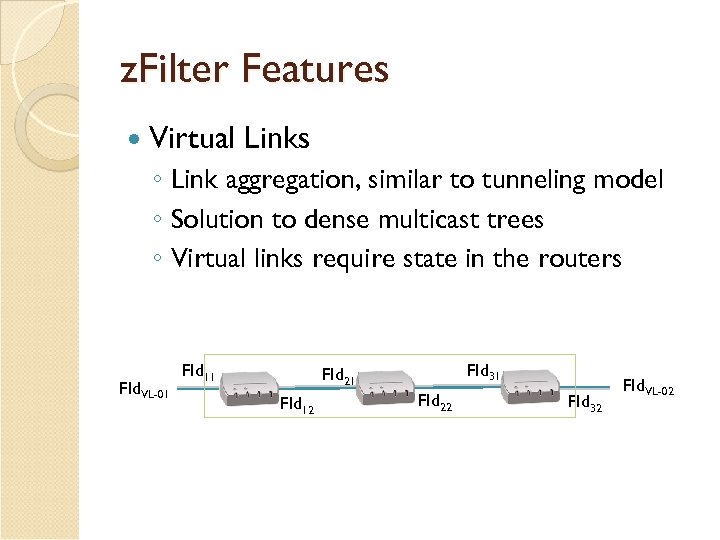 z. Filter Features Virtual Links ◦ Link aggregation, similar to tunneling model ◦ Solution to dense multicast trees ◦ Virtual links require state in the routers FId. VL-01 FId 11 FId 31 FId 21 FId 12 FId 22 FId 32 FId. VL-02
z. Filter Features Virtual Links ◦ Link aggregation, similar to tunneling model ◦ Solution to dense multicast trees ◦ Virtual links require state in the routers FId. VL-01 FId 11 FId 31 FId 21 FId 12 FId 22 FId 32 FId. VL-02
 Fast Recovery Backup virtual link ◦ Separate virtual backup path pre-configured for each physical link ID ◦ No need to change the packets ◦ Use activation message, informing the backup route to activate the path Second approach ◦ Pre-computed z. Filter, add the d value to represent the new path
Fast Recovery Backup virtual link ◦ Separate virtual backup path pre-configured for each physical link ID ◦ No need to change the packets ◦ Use activation message, informing the backup route to activate the path Second approach ◦ Pre-computed z. Filter, add the d value to represent the new path
 Loop Prevention First approach ◦ Select BF with lowest false-positive percentage ◦ LIT approach Second approach ◦ Cache packets for small period to detect loops Third ◦ TTL approach
Loop Prevention First approach ◦ Select BF with lowest false-positive percentage ◦ LIT approach Second approach ◦ Cache packets for small period to detect loops Third ◦ TTL approach
 Topology Management/Formation Goal: path creation/computation/management between data sources and sinks Assumptions ◦ Publishers & subscribers don’t know each other’s location Topology Manager (TM) ◦ Node interested in receiving physical information about the network ◦ Creates/Manages forwarding paths ◦ Computes the path from the publishers to the subscribers ◦ Returns the z. Filter
Topology Management/Formation Goal: path creation/computation/management between data sources and sinks Assumptions ◦ Publishers & subscribers don’t know each other’s location Topology Manager (TM) ◦ Node interested in receiving physical information about the network ◦ Creates/Manages forwarding paths ◦ Computes the path from the publishers to the subscribers ◦ Returns the z. Filter
 Topology Manager (TM) One or more TM per domain Work simultaneously or in anycast way Nodes ◦ Local bootstrapping with HELLO messages ◦ Collect local connectivity with link quality and forwarding capabilities ◦ Publish local connectivity information to the TM ◦ Reconstructs the overall forwarding level topology in the network
Topology Manager (TM) One or more TM per domain Work simultaneously or in anycast way Nodes ◦ Local bootstrapping with HELLO messages ◦ Collect local connectivity with link quality and forwarding capabilities ◦ Publish local connectivity information to the TM ◦ Reconstructs the overall forwarding level topology in the network
 Topology Management Intra-domain Topology Management ◦ ◦ Local network topology generation Intra-domain forwarding structures management Computes network states Updates forwarding information Inter-domain Topology Management ◦ Topology formation in the domain level ◦ Between administrative domains ◦ Configuring and maintaining inter-domain topology based on policies
Topology Management Intra-domain Topology Management ◦ ◦ Local network topology generation Intra-domain forwarding structures management Computes network states Updates forwarding information Inter-domain Topology Management ◦ Topology formation in the domain level ◦ Between administrative domains ◦ Configuring and maintaining inter-domain topology based on policies
 Intra-domain Forwarding & z. Filters z. Filter requirement LIDs list generated based on the Sid and Rid Intra-domain TM ◦ Knowledge of the individual links composing the forwarding path ◦ Domain-specific end-points for data delivery ◦ Builds a forwarding graph between end-points ◦ Identifying possible virtual trees (constantly used paths) ◦ Traffic pattern evaluation for virtual tree creation ◦ Lifetime and tree management (state in the router)
Intra-domain Forwarding & z. Filters z. Filter requirement LIDs list generated based on the Sid and Rid Intra-domain TM ◦ Knowledge of the individual links composing the forwarding path ◦ Domain-specific end-points for data delivery ◦ Builds a forwarding graph between end-points ◦ Identifying possible virtual trees (constantly used paths) ◦ Traffic pattern evaluation for virtual tree creation ◦ Lifetime and tree management (state in the router)
 Inter-domain Topology Formation (ITF) Helps building the forwarding information ◦ Based on policies set by operators and users Manages edge routers between domains ◦ Protection against policy violations ◦ Protect domain internals
Inter-domain Topology Formation (ITF) Helps building the forwarding information ◦ Based on policies set by operators and users Manages edge routers between domains ◦ Protection against policy violations ◦ Protect domain internals
 Motivation – ITF PSIRP network vision ◦ Divided in autonomous systems or domains ◦ Controlled by different and competing organizations ◦ Similar to the current Internet Domain level connectivity ◦ Defined by the relationships between organizations ◦ Customers needs ◦ Similar to BGP policies
Motivation – ITF PSIRP network vision ◦ Divided in autonomous systems or domains ◦ Controlled by different and competing organizations ◦ Similar to the current Internet Domain level connectivity ◦ Defined by the relationships between organizations ◦ Customers needs ◦ Similar to BGP policies
 Motivation – Inter-domain Routing Approximately ~10 tier-1 operators Relationships ◦ Customer-provider ◦ Peer-peer ◦ Sibling-sibling Tier-1 operators ◦ Peer with each other and don’t buy traffic from other operators ◦ Monopoly
Motivation – Inter-domain Routing Approximately ~10 tier-1 operators Relationships ◦ Customer-provider ◦ Peer-peer ◦ Sibling-sibling Tier-1 operators ◦ Peer with each other and don’t buy traffic from other operators ◦ Monopoly
 Inter-domain Topology Formation Goals ◦ Stores forwarding information among domains ◦ Builds forwarding paths based on operator’s policies ◦ Glue together Internet domains
Inter-domain Topology Formation Goals ◦ Stores forwarding information among domains ◦ Builds forwarding paths based on operator’s policies ◦ Glue together Internet domains
 Inter-domain Topology Formation Connect multiple intra-domain Topology Managers Communication between local topology formation and inter-domain topology formation Offline route computation ◦ Faster approach Path construction between publishers and subscribers through different domains
Inter-domain Topology Formation Connect multiple intra-domain Topology Managers Communication between local topology formation and inter-domain topology formation Offline route computation ◦ Faster approach Path construction between publishers and subscribers through different domains
 ITF – Design Requirements Flexible control of the routing policies ◦ Packets with different Rids should have different routing policies High granularity ◦ Customers should be able to define per-Rid policies Multi-homing and partial data transit support Operators are able to hide their internal topology
ITF – Design Requirements Flexible control of the routing policies ◦ Packets with different Rids should have different routing policies High granularity ◦ Customers should be able to define per-Rid policies Multi-homing and partial data transit support Operators are able to hide their internal topology
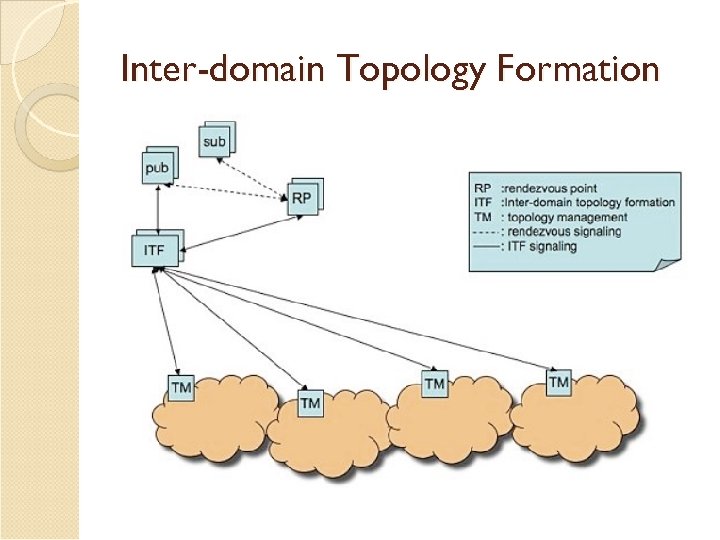 Inter-domain Topology Formation
Inter-domain Topology Formation
 ITF – Information Gathering Prior to publications ◦ RVS inform status of subscribers regarding Sid/Rids Depends on granularity of information in the RVS ◦ Forward network identifier ITF has to know a list of network identifiers to connect publishers to subscribers ◦ Landmark identifier Some landmark close to the subscriber knows how to deliver publications ◦ Forwarding tree identifier Construct partial distribution trees in anticipation of publications
ITF – Information Gathering Prior to publications ◦ RVS inform status of subscribers regarding Sid/Rids Depends on granularity of information in the RVS ◦ Forward network identifier ITF has to know a list of network identifiers to connect publishers to subscribers ◦ Landmark identifier Some landmark close to the subscriber knows how to deliver publications ◦ Forwarding tree identifier Construct partial distribution trees in anticipation of publications
 ITF – Pub/sub approach benefits ITF components can subscribe to route changes ◦ There is no need to sequentially notify each domain ◦ Multicast support in pub/sub Simultaneous delivery to all ITF through common scope ◦ Avoids route flapping (convergence problem) ◦ Avoids propagation problems (when to stop)
ITF – Pub/sub approach benefits ITF components can subscribe to route changes ◦ There is no need to sequentially notify each domain ◦ Multicast support in pub/sub Simultaneous delivery to all ITF through common scope ◦ Avoids route flapping (convergence problem) ◦ Avoids propagation problems (when to stop)
 Fault tolerance & Multipath routing Benefits ◦ Spread network load Can switch between paths and establish new ones ◦ Fault tolerance ◦ Security against eavesdropping Some problems ◦ TCP ordering Solution ◦ Single path for delay sensitive applications No guarantee that there will be path separation if they share the same forwarding domains
Fault tolerance & Multipath routing Benefits ◦ Spread network load Can switch between paths and establish new ones ◦ Fault tolerance ◦ Security against eavesdropping Some problems ◦ TCP ordering Solution ◦ Single path for delay sensitive applications No guarantee that there will be path separation if they share the same forwarding domains
 Network Attachment Discovery of attachment points Node authentication Configuration information retrieval ◦ Information on compatibility, identity, services, policies, etc ◦ Initial attachment parameters ◦ Bootstrapping procedure ◦ Identity verification ◦ Access rights ◦ Setting up identifiers (Fid, Sid, Rid) for communication ◦ Security parameters negotiation
Network Attachment Discovery of attachment points Node authentication Configuration information retrieval ◦ Information on compatibility, identity, services, policies, etc ◦ Initial attachment parameters ◦ Bootstrapping procedure ◦ Identity verification ◦ Access rights ◦ Setting up identifiers (Fid, Sid, Rid) for communication ◦ Security parameters negotiation
 Network Attachment Communication approaches ◦ Information advertisement in the link layer ◦ Publish solicitations Nodes can answer with parameters Requirement ◦ Default identifiers for initial communication ◦ Common scope Scope where advertisements are published
Network Attachment Communication approaches ◦ Information advertisement in the link layer ◦ Publish solicitations Nodes can answer with parameters Requirement ◦ Default identifiers for initial communication ◦ Common scope Scope where advertisements are published
 Questions? Comments? Thanks!
Questions? Comments? Thanks!


