e590b4c9bfed66bdf2317e98b69dd7d4.ppt
- Количество слайдов: 15
 Protecting Your Organization Against Ransomware (while ensuring no one sends you a Christmas card) Timothy J Gallo @timjgallo Allan Liska @uuallan
Protecting Your Organization Against Ransomware (while ensuring no one sends you a Christmas card) Timothy J Gallo @timjgallo Allan Liska @uuallan
 About Us § Tim § Allan - 15+ years in Networking and Security - 15+ Years Experience in security - Worked internationally on threat intelligence asset and product development - Written about: Intelligence, DNS, Ransomware and NTP. - Phishing lures: Micro-distilleries, Motorcycles, Boba Fett, Arduino - Phishing Lures: Bordeaux, Redheads, Steelers, DC vs Marvel - Converting his burning man art car to pirate con ship - Has the greatest fiancée ever.
About Us § Tim § Allan - 15+ years in Networking and Security - 15+ Years Experience in security - Worked internationally on threat intelligence asset and product development - Written about: Intelligence, DNS, Ransomware and NTP. - Phishing lures: Micro-distilleries, Motorcycles, Boba Fett, Arduino - Phishing Lures: Bordeaux, Redheads, Steelers, DC vs Marvel - Converting his burning man art car to pirate con ship - Has the greatest fiancée ever.
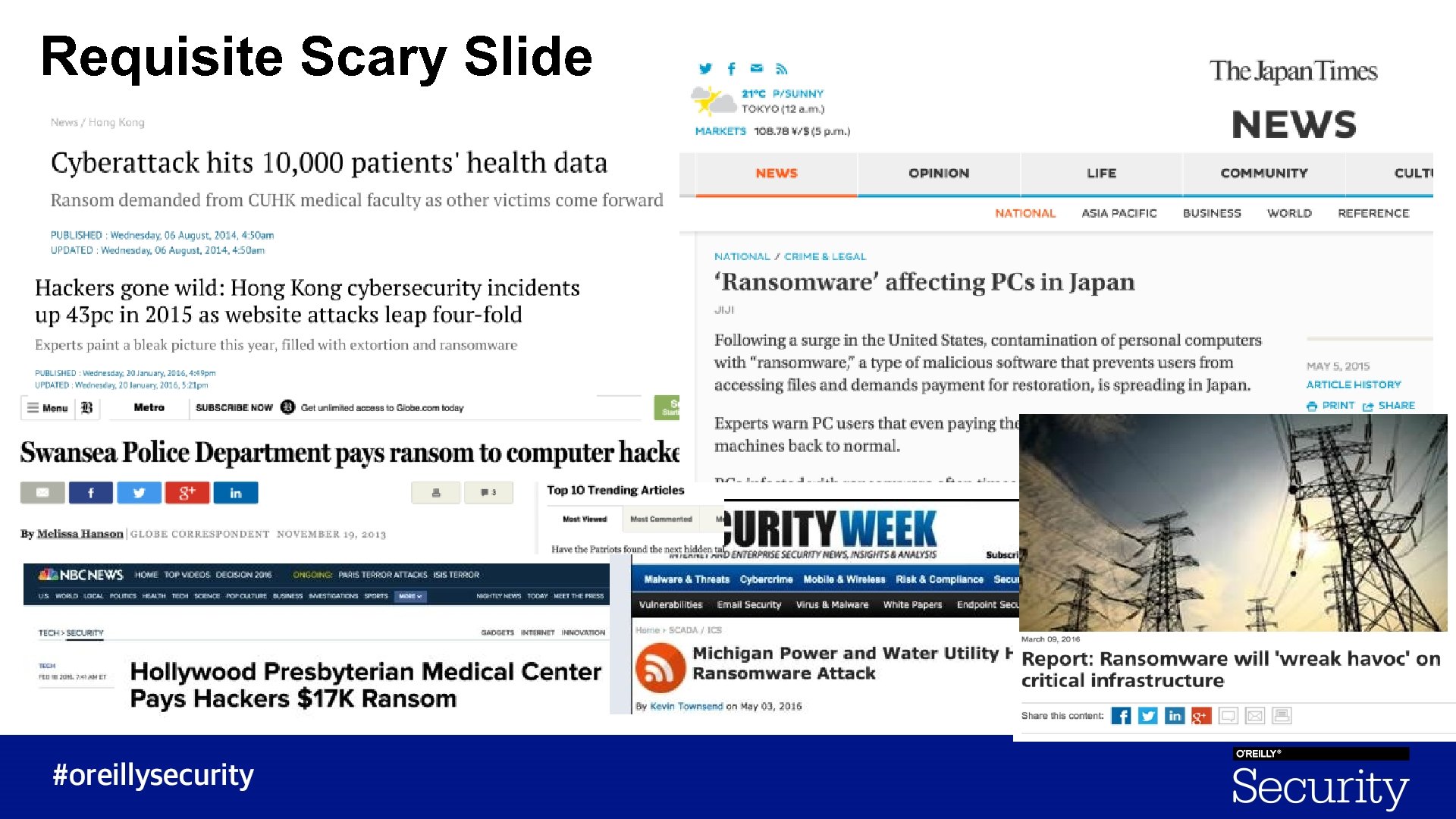 Requisite Scary Slide
Requisite Scary Slide
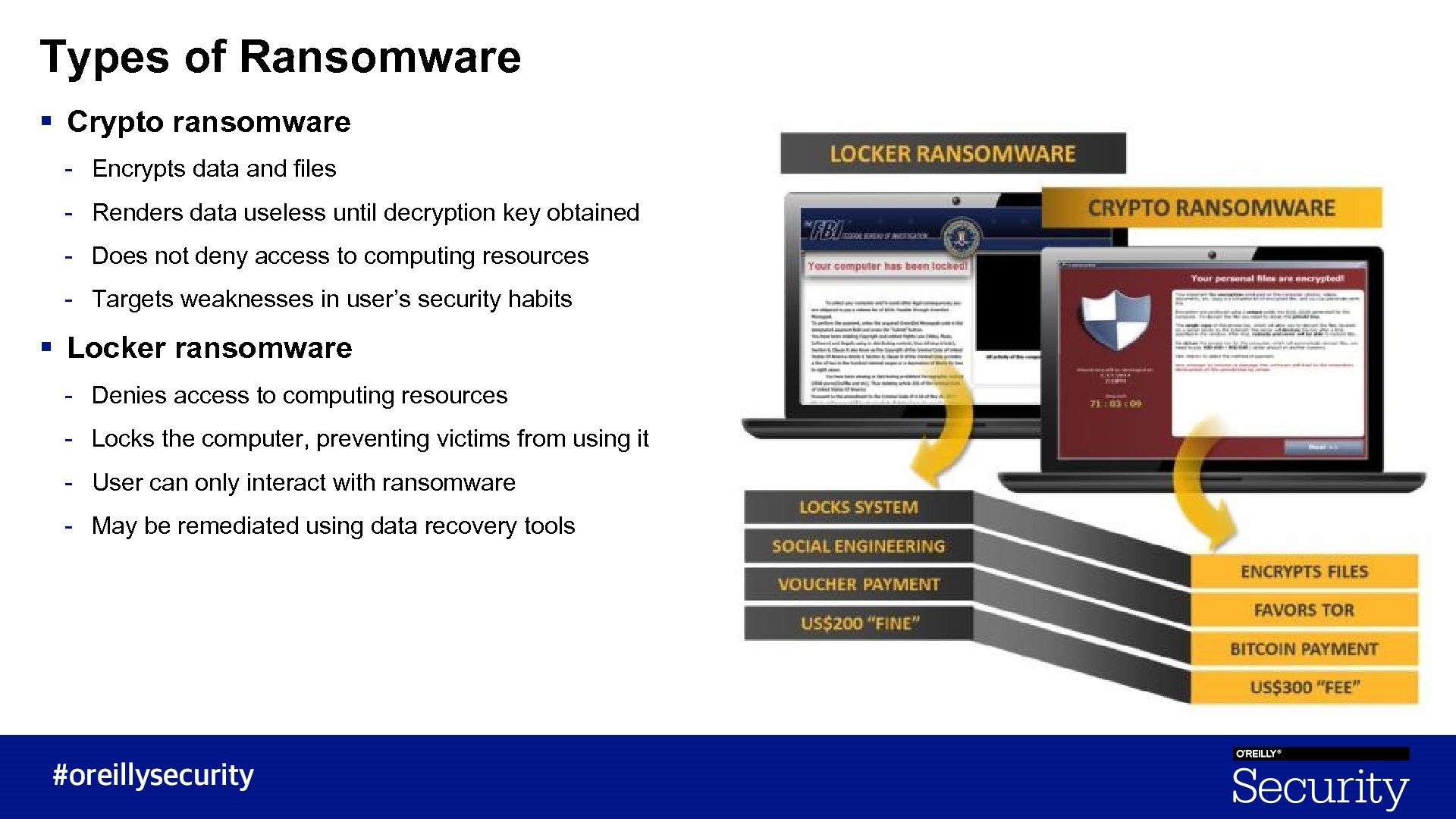 Types of Ransomware § Crypto ransomware - Encrypts data and files - Renders data useless until decryption key obtained - Does not deny access to computing resources - Targets weaknesses in user’s security habits § Locker ransomware - Denies access to computing resources - Locks the computer, preventing victims from using it - User can only interact with ransomware - May be remediated using data recovery tools
Types of Ransomware § Crypto ransomware - Encrypts data and files - Renders data useless until decryption key obtained - Does not deny access to computing resources - Targets weaknesses in user’s security habits § Locker ransomware - Denies access to computing resources - Locks the computer, preventing victims from using it - User can only interact with ransomware - May be remediated using data recovery tools
 Ransomware Attack Vectors § E-Mail - Locky is primarily delivered this way - Usually sent as a Microsoft Office Document with a macro - Alternatives are to send as a Java. Script (. js), Windows Scripting File (. wsf) or Power. Shell File. - Targets weaknesses in user’s security habits § Web - Cerber and Crypt. XXX are delivered this way. - Works in conjunction with popular exploit kits such as Ri. G, Sunset and Magnitude. - Relies on unpatched browser plug-ins
Ransomware Attack Vectors § E-Mail - Locky is primarily delivered this way - Usually sent as a Microsoft Office Document with a macro - Alternatives are to send as a Java. Script (. js), Windows Scripting File (. wsf) or Power. Shell File. - Targets weaknesses in user’s security habits § Web - Cerber and Crypt. XXX are delivered this way. - Works in conjunction with popular exploit kits such as Ri. G, Sunset and Magnitude. - Relies on unpatched browser plug-ins
 This is the part of the presentation where you lose friends. . . Quick and easy steps for protecting an organization from ransomware: 1. Administratively disable macros in Microsoft Office Documents across the organization. 2. Automatically delete any incoming email attachments that are. js or. wsf files and inspect any. zip, . rar, or. 7 z files. 3. Disable unnecessary browser plug-ins, especially Adobe Flash, Microsoft Silverlight, Java, and Adobe PDF. 4. Do not allow users to have local administrator privileges on their machines. These steps will stop a lot of ransomware from executing inside an organization, they won’t cost any money to implement and, for the most part, they will not impede productivity in an organization. These steps may result in push-back from users. The trick is to get user buy-in before implementing these steps, be willing to listen and compromise, and pick security battles.
This is the part of the presentation where you lose friends. . . Quick and easy steps for protecting an organization from ransomware: 1. Administratively disable macros in Microsoft Office Documents across the organization. 2. Automatically delete any incoming email attachments that are. js or. wsf files and inspect any. zip, . rar, or. 7 z files. 3. Disable unnecessary browser plug-ins, especially Adobe Flash, Microsoft Silverlight, Java, and Adobe PDF. 4. Do not allow users to have local administrator privileges on their machines. These steps will stop a lot of ransomware from executing inside an organization, they won’t cost any money to implement and, for the most part, they will not impede productivity in an organization. These steps may result in push-back from users. The trick is to get user buy-in before implementing these steps, be willing to listen and compromise, and pick security battles.
 But you don’t have…you do have to think differently Too often security is thought of as the department of NO.
But you don’t have…you do have to think differently Too often security is thought of as the department of NO.
 Security needs to be more collaborative The security team needs to work with other teams to not just keep the organization more secure, but to do so collaboratively 1. Rather than simply ”laying down the law” security has to do a better job of explaining the why. 2. Explaining the why helps to get user buy-in to security policies, making them easier to enforce. 3. Security communication needs to be ongoing, security teams need to send out regular updates explaining new threats and how the organization is addressing those threats. 4. Making exceptions to security policies need to be non-onerous, there needs to be clear and welldefined documentation for how to make an exception. In short, security teams need to pick their battles. Stand firm on important security issues, but those that can be dealt without having to put more burden on users should be addressed in other ways.
Security needs to be more collaborative The security team needs to work with other teams to not just keep the organization more secure, but to do so collaboratively 1. Rather than simply ”laying down the law” security has to do a better job of explaining the why. 2. Explaining the why helps to get user buy-in to security policies, making them easier to enforce. 3. Security communication needs to be ongoing, security teams need to send out regular updates explaining new threats and how the organization is addressing those threats. 4. Making exceptions to security policies need to be non-onerous, there needs to be clear and welldefined documentation for how to make an exception. In short, security teams need to pick their battles. Stand firm on important security issues, but those that can be dealt without having to put more burden on users should be addressed in other ways.
 Before we get to the rest…you have backups, right? § The easiest and most effective way to remediate a ransomware attack is to restore from backup. § Assuming backups are working. § Security teams aren’t responsible for backups, so they often don’t have any insight into how well the backup systems are working – and how often they are tested. § They might not even have insight into which systems are backed up. § This conversation should happen with the DR team, before ransomware hits the organization.
Before we get to the rest…you have backups, right? § The easiest and most effective way to remediate a ransomware attack is to restore from backup. § Assuming backups are working. § Security teams aren’t responsible for backups, so they often don’t have any insight into how well the backup systems are working – and how often they are tested. § They might not even have insight into which systems are backed up. § This conversation should happen with the DR team, before ransomware hits the organization.
 No One Likes People Who Use Macros § Locky ransomware is the most delivered ransomware in the world. § Locky Team regularly launches campaigns to spam 10 s of millions of users. § Relies primarily Microsoft Office documents with embedded macros. § These macros easily avoid detection by anti-virus vendors.
No One Likes People Who Use Macros § Locky ransomware is the most delivered ransomware in the world. § Locky Team regularly launches campaigns to spam 10 s of millions of users. § Relies primarily Microsoft Office documents with embedded macros. § These macros easily avoid detection by anti-virus vendors.
 No One Likes People Who Use Macros § Are macros really necessary? § For some users maybe, but for most users no. § Starting with Office 2013, administrators are able to globally ban macros. Do that. § Security teams can make exceptions for users who “need” macros. § Exceptions should include additional security awareness training and perhaps additional security monitoring.
No One Likes People Who Use Macros § Are macros really necessary? § For some users maybe, but for most users no. § Starting with Office 2013, administrators are able to globally ban macros. Do that. § Security teams can make exceptions for users who “need” macros. § Exceptions should include additional security awareness training and perhaps additional security monitoring.
 I am going to bash your Power. Shell § Just as users don’t all need macros enabled, scripting engines do not need to be enabled on all workstations. § Remove the cscript. exe and wscript. exe and disable Power. Shell administratively across all workstations. § Most users won’t notice this, but system admin teams might. § Work with the administrative team to re-write management scripts that use Power. Shell so they originate from the admin workstation, rather than use the local Power. Shell executable.
I am going to bash your Power. Shell § Just as users don’t all need macros enabled, scripting engines do not need to be enabled on all workstations. § Remove the cscript. exe and wscript. exe and disable Power. Shell administratively across all workstations. § Most users won’t notice this, but system admin teams might. § Work with the administrative team to re-write management scripts that use Power. Shell so they originate from the admin workstation, rather than use the local Power. Shell executable.
 Umm…I think we patched everyone § Ransomware that is delivered via the web relies on exploit kits. § This is not just a matter of users going to bad websites. § Even well-known websites, like uhh. . Yahoo? , can be infected with malvertising. § That is why it is important to keep Internetfacing applications up to date. § And, why it is important to have an accurate inventory of what is on each system.
Umm…I think we patched everyone § Ransomware that is delivered via the web relies on exploit kits. § This is not just a matter of users going to bad websites. § Even well-known websites, like uhh. . Yahoo? , can be infected with malvertising. § That is why it is important to keep Internetfacing applications up to date. § And, why it is important to have an accurate inventory of what is on each system.
 Flash is No Superhero § Is it time to ditch Adobe Flash? § Exploit kits scan incoming web traffic and look for certain versions of browsers or plugins, notably: - Adobe Flash - Microsoft Silverlight - Java and JRE § Exploit kits like, the Ri. G EK, have exploits against: CVE-2014 -0515, CVE-2014 -0569, CVE -2016 -4171, and CVE-2016 -4166 and many more. . § Start by explaining the problem with these plug-ins, and that there alternatives to use them. § Determine which teams need to use these plug-ins and which ones. Compromise with setting higher security settings.
Flash is No Superhero § Is it time to ditch Adobe Flash? § Exploit kits scan incoming web traffic and look for certain versions of browsers or plugins, notably: - Adobe Flash - Microsoft Silverlight - Java and JRE § Exploit kits like, the Ri. G EK, have exploits against: CVE-2014 -0515, CVE-2014 -0569, CVE -2016 -4171, and CVE-2016 -4166 and many more. . § Start by explaining the problem with these plug-ins, and that there alternatives to use them. § Determine which teams need to use these plug-ins and which ones. Compromise with setting higher security settings.
 And you get local admin, and… § Many organizations give all of their users local admin access to their machines. § Not having local admin makes it harder for ransomware to run on the local system. § Work with users and IT staff to set up a process for installing new software. § Create a list of approved applications, and a process for getting approval for other applications.
And you get local admin, and… § Many organizations give all of their users local admin access to their machines. § Not having local admin makes it harder for ransomware to run on the local system. § Work with users and IT staff to set up a process for installing new software. § Create a list of approved applications, and a process for getting approval for other applications.


