967c0aff3b04b70650c866fbec2b8745.ppt
- Количество слайдов: 18

Protecting the Data that Drive Business Chris Gale Partner Director EMEA Chris. gale@imperva. com

Almost Twenty Years Ago Today. . . Fleischmann & Pons Tim Berners-Lee ‘Cold fusion’ ‘Distributed hypertext system’
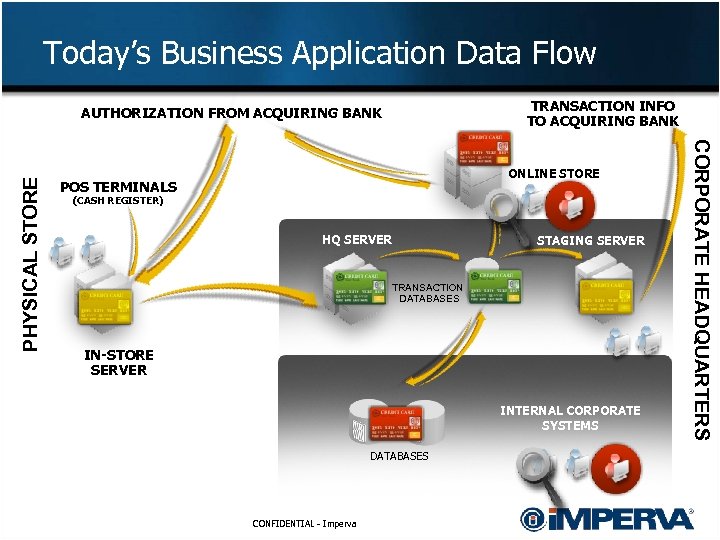
Today’s Business Application Data Flow TRANSACTION INFO TO ACQUIRING BANK ONLINE STORE POS TERMINALS (CASH REGISTER) HQ SERVER STAGING SERVER TRANSACTION DATABASES IN-STORE SERVER INTERNAL CORPORATE SYSTEMS DATABASES CONFIDENTIAL - Imperva CORPORATE HEADQUARTERS PHYSICAL STORE AUTHORIZATION FROM ACQUIRING BANK
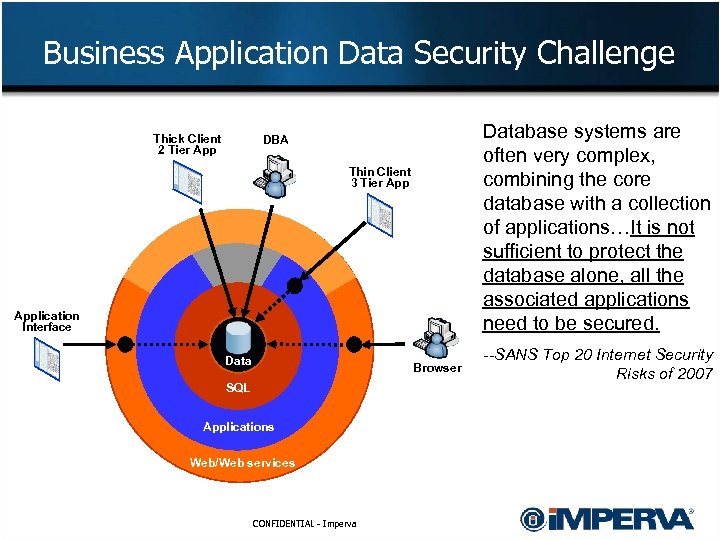
Business Application Data Security Challenge Thick Client 2 Tier App Database systems are often very complex, combining the core database with a collection of applications…It is not sufficient to protect the database alone, all the associated applications need to be secured. DBA Thin Client 3 Tier Application Interface Data Browser SQL Applications Web/Web services CONFIDENTIAL - Imperva --SANS Top 20 Internet Security Risks of 2007

Why Should You Care? 85% of organizations have experienced a data breach Theft, Abuse, Misuse & Leakage Happen Even in Leading Organizations Sources: Privacy Rights Clearinghouse & Ponemon Institute Survey, “The Business Impact of Data Breach” CONFIDENTIAL - Imperva
Why Should You Care? Data governance is not optional PCI – Required to process credit card transaction SOX – Required to report financial results EU DD Privacy – Required to process personal data What do regulations require of you? CONFIDENTIAL - Imperva

New Web 2. 0 – Old Threats & New § 92% of Web applications have vulnerabilities § 93% of vulnerable sites are still vulnerable after code fixes!! § SQL Injection – still majority cause of data leakage § Ponemon estimates breaches cost on average $202 per compromised record § April 08: automated SQL injection affects 500 k IIS webpages § July 08: Asprox ‘infects’ reputable sites including NHS § Exploiting server’s trust in the client (versus XSS) § Cross Site Request Forgery (CSRF) & JS-Hijacking (AJAX) § Growing cause of web fraud

Worrying Threat Trends in 2008 § Majority of malware now ‘cloaked’ in Web protocols § Both exploits and Command & Control § HTTP poorly monitored – traffic volume, SSL & difficult to block § Indirect attacks exploiting ‘trusted’ websites for malware distribution § Implicitly trusted by the user – ‘Drive-by’ downloads § Sophos reported 1 webpage ‘infected’ every 5 secs during 2008 § ‘Google Hacking’ & ‘Web worms’ – search-engine seeded attacks & data breach discovery § Concept first analyzed in March 2004 ADC paper: “Web Application Worms: Myth or Reality? ”
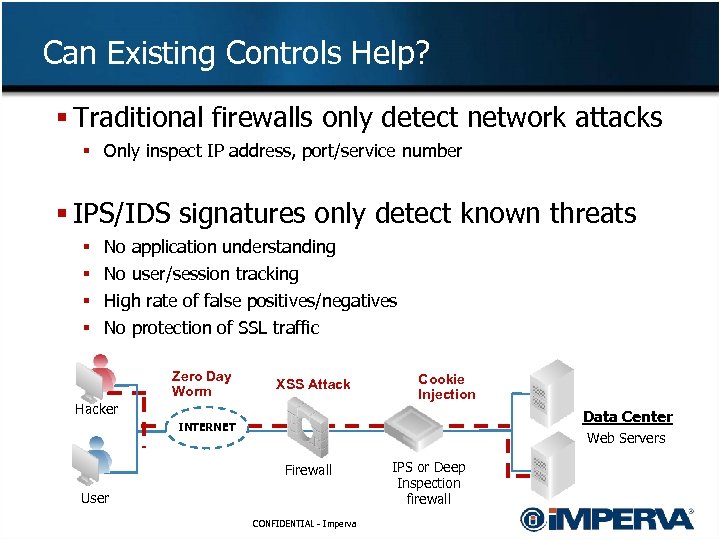
Can Existing Controls Help? § Traditional firewalls only detect network attacks § Only inspect IP address, port/service number § IPS/IDS signatures only detect known threats § § No application understanding No user/session tracking High rate of false positives/negatives No protection of SSL traffic Zero Day Worm XSS Attack Hacker Cookie Injection Data Center INTERNET Web Servers Firewall User CONFIDENTIAL - Imperva IPS or Deep Inspection firewall

§ Founded in 2002 § CEO Shlomo Kramer – CEO of the Year, co-founder of Check Point § The leader in Data Security § Global company with over 40% international revenue § North American HQ in California; International HQ in Israel § Local presence in all major markets (EMEA, APAC, Japan) § Customers in 35+ countries § Over 700 customers and 4500+ organizations protected CONFIDENTIAL - Imperva

Imperva Application Defence Centre § Business application Data Security experts § Research the latest threats and compliance best practices § Applications (SAP, Oracle EBS, People. Soft & others) § Databases (Oracle, DB 2, SQL-Server & others) § Compliance mandates (SOX, PCI, HIPAA & others) § Deliver actionable, up-to-date content to Imperva customers - CONFIDENTIAL -
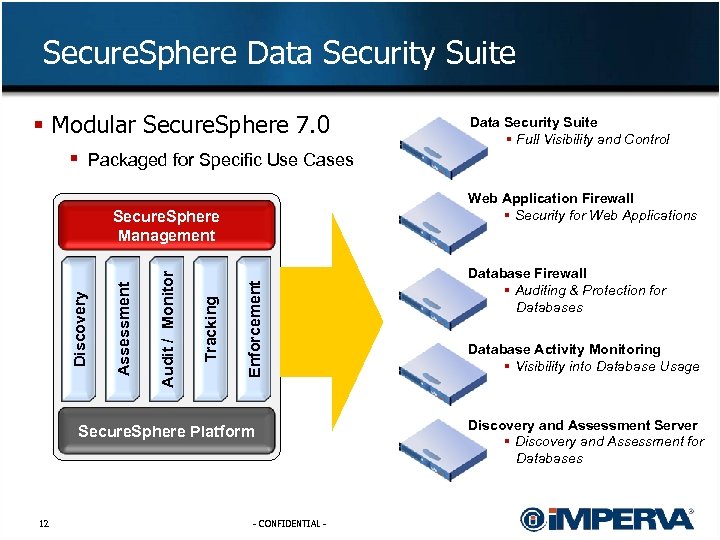
Secure. Sphere Data Security Suite § Modular Secure. Sphere 7. 0 § Packaged for Specific Use Cases Web Application Firewall § Security for Web Applications Enforcement Tracking Audit / Monitor Assessment Discovery Secure. Sphere Management Secure. Sphere Platform 12 Data Security Suite § Full Visibility and Control - CONFIDENTIAL - Database Firewall § Auditing & Protection for Databases Database Activity Monitoring § Visibility into Database Usage Discovery and Assessment Server § Discovery and Assessment for Databases
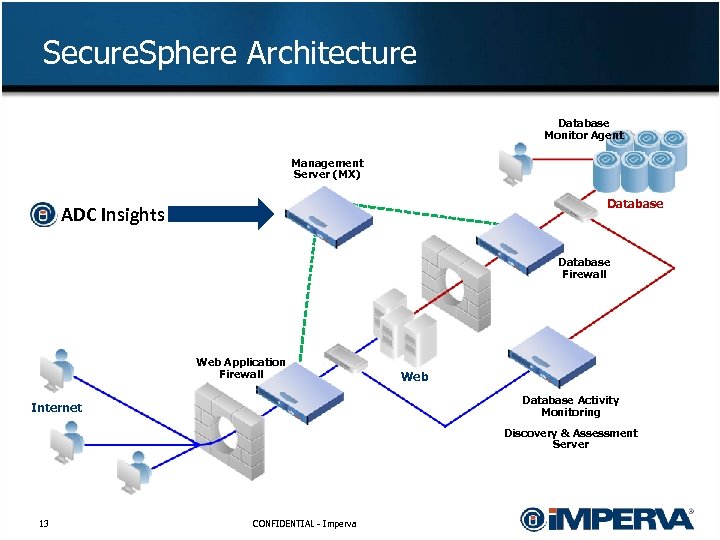
Secure. Sphere Architecture Database Monitor Agent Management Server (MX) Database ADC Insights Database Firewall Web Application Firewall Web Database Activity Monitoring Internet Discovery & Assessment Server 13 CONFIDENTIAL - Imperva
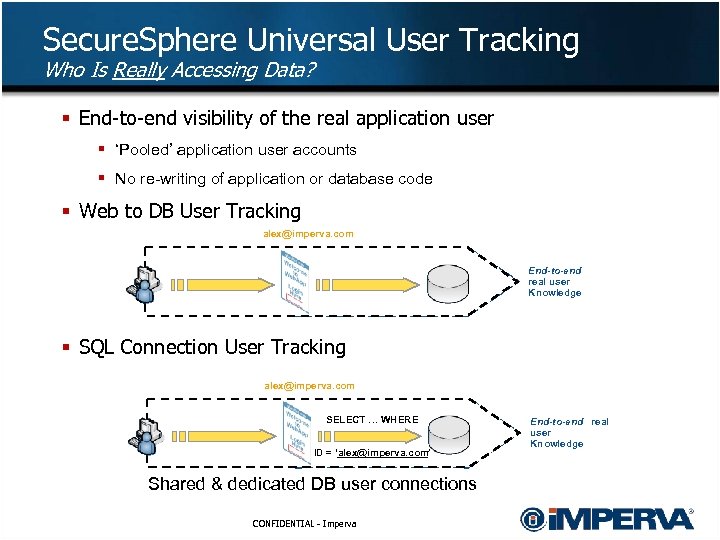
Secure. Sphere Universal User Tracking Who Is Really Accessing Data? § End-to-end visibility of the real application user § ‘Pooled’ application user accounts § No re-writing of application or database code § Web to DB User Tracking alex@imperva. com Webapp. company. com End-to-end No user real user Knowledge § SQL Connection User Tracking alex@imperva. com Webapp. company. com SELECT … WHERE ID = ‘alex@imperva. com’ Shared & dedicated DB user connections CONFIDENTIAL - Imperva End-to-end real Limited real user Knowledge
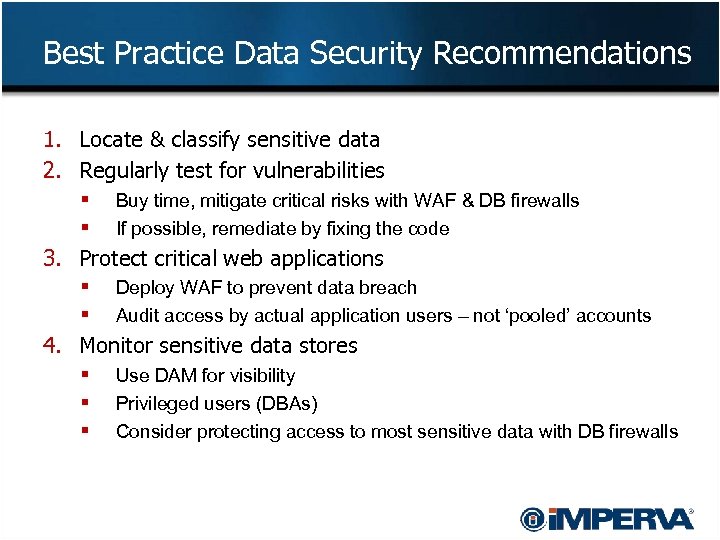
Best Practice Data Security Recommendations 1. Locate & classify sensitive data 2. Regularly test for vulnerabilities § Buy time, mitigate critical risks with WAF & DB firewalls § If possible, remediate by fixing the code 3. Protect critical web applications § Deploy WAF to prevent data breach § Audit access by actual application users – not ‘pooled’ accounts 4. Monitor sensitive data stores § Use DAM for visibility § Privileged users (DBAs) § Consider protecting access to most sensitive data with DB firewalls
PCI DSS Compliance & Secure. Sphere 6. 6 Application layer firewall or external code review § Secure. Sphere WAF: Cost-effective, non-intrusive threat mitigation 10 Track and monitor all access to cardholder data § Secure. Sphere DAM: SQL auditing, tamper-proof, separation of duty 3. 4 Compensating controls for protecting stored cardholder data § Secure. Sphere DB Firewall: Prevents unauthorised access to card holder data
Imperva The Leader in Data Security Only complete solution for visibility and control over business data Veteran leadership with deep industry expertise • Dynamic Profiling & Universal User Tracking • Industry veterans in security • ADC - only research team dedicated to business application data security • Consistent industry recognition of technical superiority More application data security deployments than any other vendor • Over 700 direct customers • 54 Fortune 1000 • 86 Global 2000 • Over 4500 protected organizations CONFIDENTIAL - Imperva Consistent growth fueled by • Surge in data breaches • Regulatory compliance requirements • Tightening Data Security legislation

Thank You www. imperva. com
967c0aff3b04b70650c866fbec2b8745.ppt