f76f948f2130d9b5ad28350f26e2ee02.ppt
- Количество слайдов: 11

Protecting Software Code By Guards Hoi Chang and Mikhail J. Atallah CERIAS, Purdue University and Arxan Technologies, Inc. {changh, mja}@cerias. purdue. edu

Contents v v v Introduction Related work The guarding framework Description of system Experimental result Conclusion 2

Introduction v Existing TRS Single point of failure or high cost v Protection mechanisms should have … Resilience: no single point of failure, hard to disable v Self-defense: detect tampering v Configurability: customizable v White-box security: security based on secret key v v Network of Guards Security is shared among all guard v Many ways to form a network v More guard greater level of security v 3
Related work v Hardware based protection Coprocessor v Smart card v Dongles v v Software based protection Code obfuscation v Self-modifying code v Code encryption/decryption v 4

The guarding framework (1/2) v Guards Checksum code: 1 -way property v Repair code v v Strengthening individual guards v Stealthiness v v Guard templates: polymorphic instance Delayed alarm upon detection of an attack Blurred boundaries between the runtime code and data Tamper-resistance v v Guard protect itself (not by other guards) Code obfuscation 5
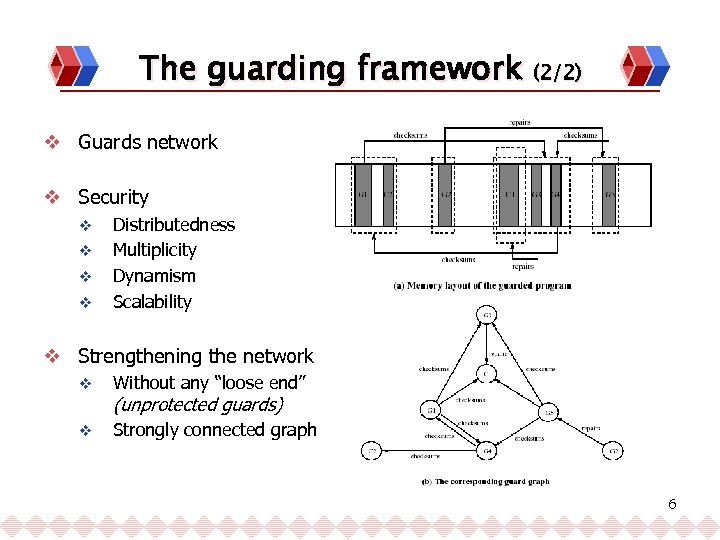
The guarding framework (2/2) v Guards network v Security v v Distributedness Multiplicity Dynamism Scalability v Strengthening the network v Without any “loose end” v Strongly connected graph (unprotected guards) 6
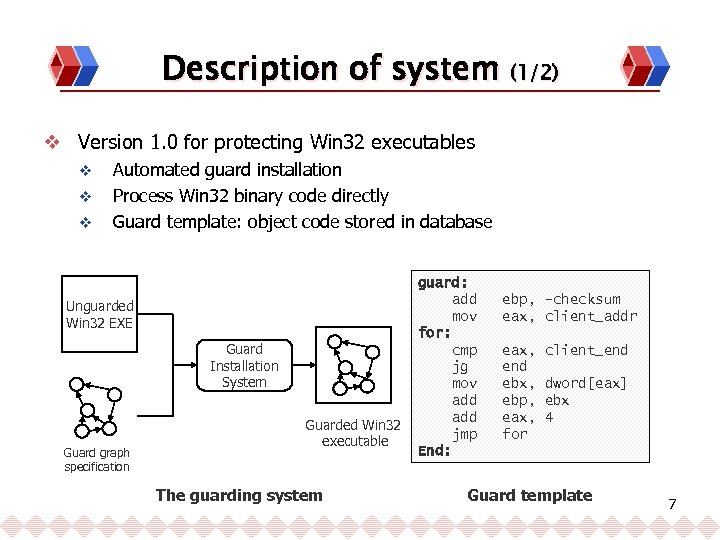
Description of system (1/2) v Version 1. 0 for protecting Win 32 executables v v v Automated guard installation Process Win 32 binary code directly Guard template: object code stored in database Unguarded Win 32 EXE Guard Installation System Guard graph specification Guarded Win 32 executable The guarding system guard: add mov for: cmp jg mov add jmp End: ebp, -checksum eax, client_addr eax, end ebx, ebp, eax, for client_end dword[eax] ebx 4 Guard template 7
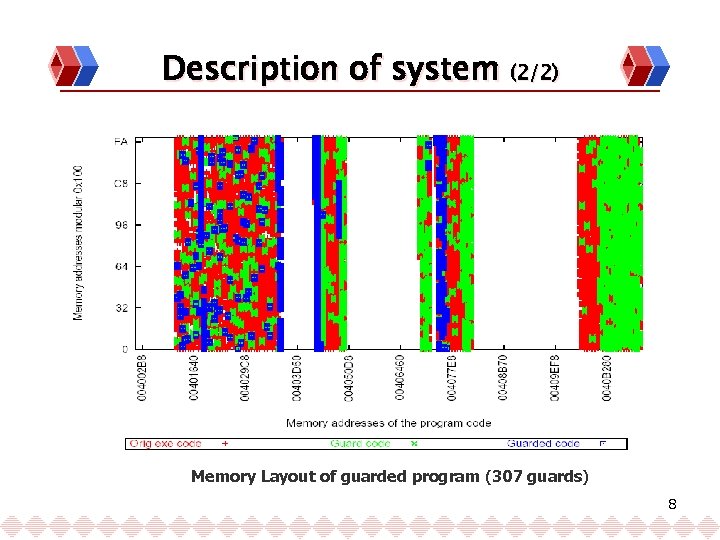
Description of system (2/2) Memory Layout of guarded program (307 guards) 8
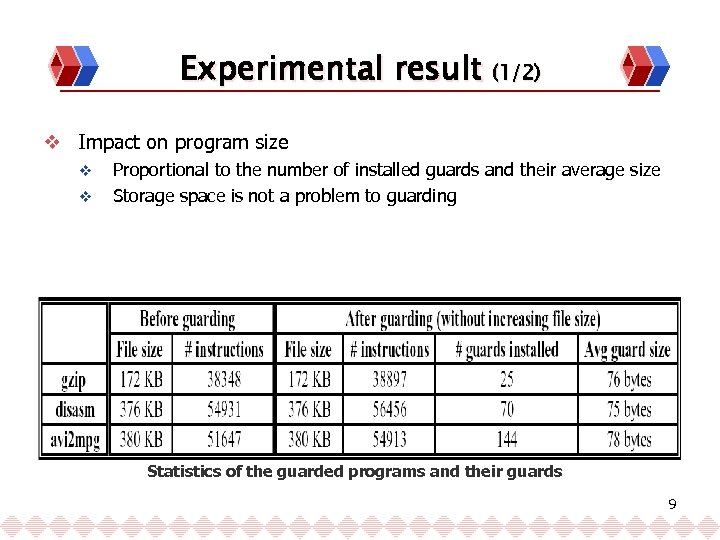
Experimental result (1/2) v Impact on program size v v Proportional to the number of installed guards and their average size Storage space is not a problem to guarding Statistics of the guarded programs and their guards 9
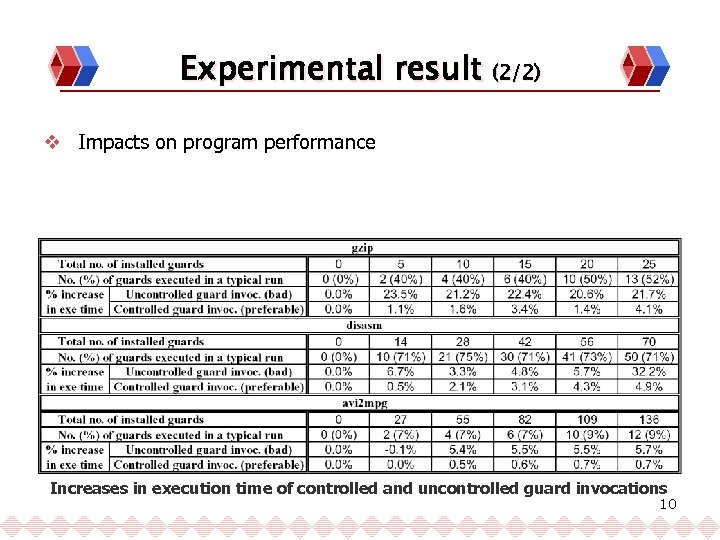
Experimental result (2/2) v Impacts on program performance Increases in execution time of controlled and uncontrolled guard invocations 10
Conclusion v Software based TRS by Guards Distributed protection v Variety of protection schemes v Configurable tamper-resistance v v Our TRS provides. . . Automated guard installation in Win 32 executables v With configurable manner v Graphical user interface v 11
f76f948f2130d9b5ad28350f26e2ee02.ppt