55d0de33f1a8be9ec884c7a28a2cb5d4.ppt
- Количество слайдов: 45

PROJECT Web-based Database Applications Lecture 3: Client/Server Databases Environment 1

CLIENT/SERVER ARCHITECTURE 2
Evolution of DBMSs - Modeling Flat-file system Ø Often text files for sequential access q Relational Database Management System (RDBMS) Ø Informix, Oracle, Sybase, DB 2, etc. q Object-oriented Database Management System (OODBMS) Ø Gemstone, O 2, Object. Store, Matisse, Jasmine, Versant, etc. q Object-relational Database Management System (ORDBMS) Ø Informix, Oracle, DB 2, Illustra, Uni. SQL, Matisse, etc. q © H. Afsarmansesh, 2003 3
Evolution of DB system - Architecture q Stand-alone Ø Centralized to Network-based DBs § Stand-alone, on a mainframe or workstations u e. g. Manufacturing industry, SMEs Ø Distributed DBs § Network-based § Supporting geographic dispersion of sites u e. g. Banking, Service provision industry Ø Federated DBs § Network-based § Supporting heterogeneity & autonomy of sites u © H. Afsarmansesh, 2003 e. g. Virtual organizations, Virtual Laboratories 4
Evolution of multi-user DB environment Mainframe-based environment Ø All applications run directly on the main system q Client/Server environment Ø Operates in networked environments Ø Splits the processing of an application between: q § A Front-end Client § A Back-end Processor (server) Client process requires some resources that the server provides Ø Clients and servers can reside on the same computer, or locate on different computers in the network Ø Client and Server are intelligent and programmable Ø © H. Afsarmansesh, 2003 5
Designing the DB architecture and environment q Good balance between Centralization & Distribution q Mainframe-based or Client/Server based databases q Client/Server architectures 1 - File Server architecture 2 - Database Server (two-tier) architecture 3 - three-tier architecture 6 Hoffer © Prentice Hall, 2002
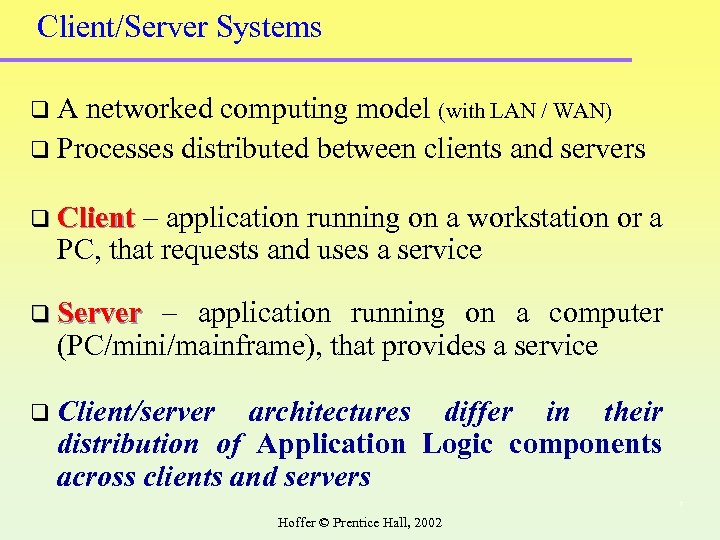
Client/Server Systems q. A networked computing model (with LAN / WAN) q Processes distributed between clients and servers q Client – application running on a workstation or a PC, that requests and uses a service q Server – application running on a computer (PC/mini/mainframe), that provides a service q Client/server architectures differ in their distribution of Application Logic components across clients and servers 7 Hoffer © Prentice Hall, 2002
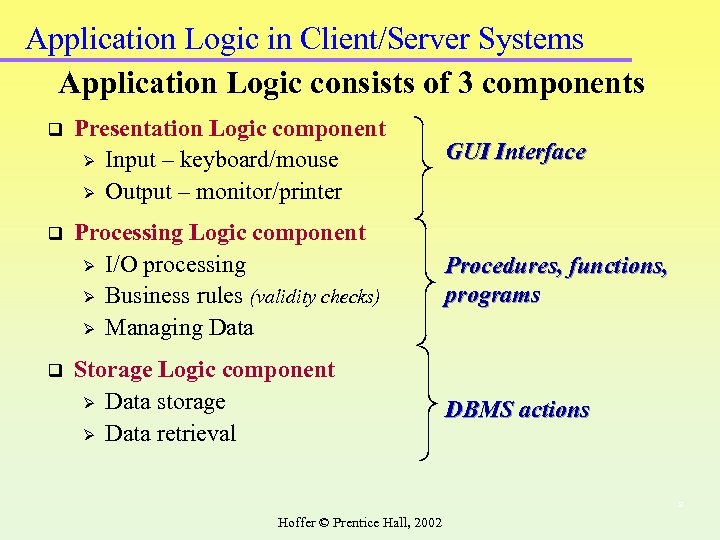
Application Logic in Client/Server Systems Application Logic consists of 3 components q Presentation Logic component Ø Input – keyboard/mouse Ø Output – monitor/printer GUI Interface q Processing Logic component Ø I/O processing Ø Business rules (validity checks) Ø Managing Data Procedures, functions, programs Storage Logic component Ø Data storage Ø Data retrieval DBMS actions q 8 Hoffer © Prentice Hall, 2002
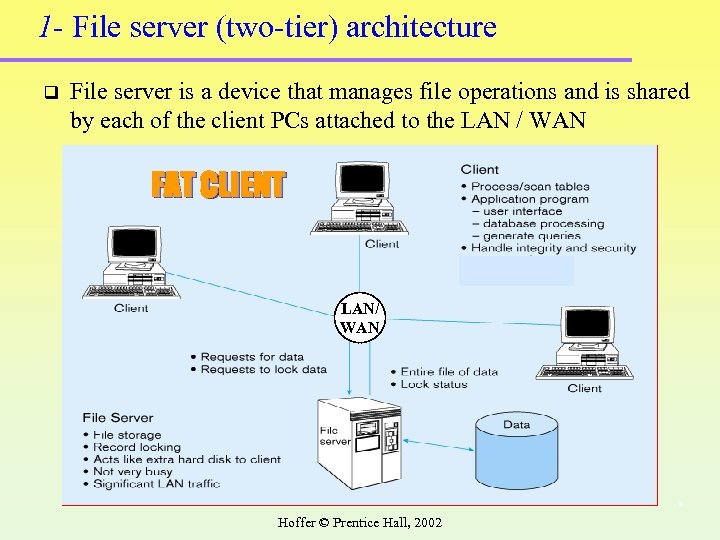
1 - File server (two-tier) architecture q File server is a device that manages file operations and is shared by each of the client PCs attached to the LAN / WAN FAT CLIENT LAN/ WAN 9 Hoffer © Prentice Hall, 2002
Limitations of file server architecture q q q Network is a bottleneck – high traffic load Tight-coupling among the application and the data Considerable processing burden on the client PC Large memory for the client PC (full DBMS transferred!) For multi-user environments - Expert application programmers are needed Ø Request to set locks for shared data(base) integrity Ø Understand consider how their application affects the concurrency, recovery and security of the shared data(base) v Handling shared data(base) problems becomes the responsibility of the application program © H. Afsarmansesh, 2003 10
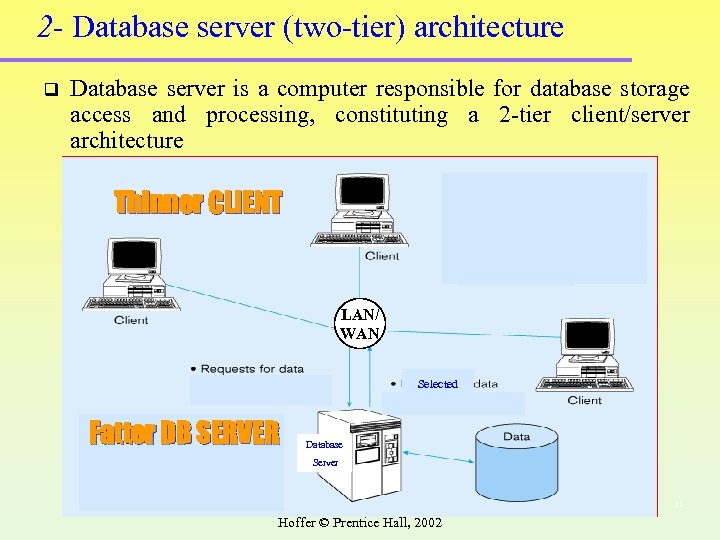
2 - Database server (two-tier) architecture q Database server is a computer responsible for database storage access and processing, constituting a 2 -tier client/server architecture Thinner CLIENT LAN/ WAN Selected Fatter DB SERVER Database Server 11 Hoffer © Prentice Hall, 2002
Advantages of two-tier database architecture q Data traffic load is reduced q Thinner Client: Ø Ø q Processing power only required at the Database server Authorization, integrity, query/update only at Database server Fatter Server: Ø Ø Processing power and larger memory in one location Stored procedures can be defined and run at Database server § A piece of code in the DBMS language (e. g. Oracle’s PL/SQL) § Creates DBMS dependency § Decreased performance © H. Afsarmansesh, 2003 12
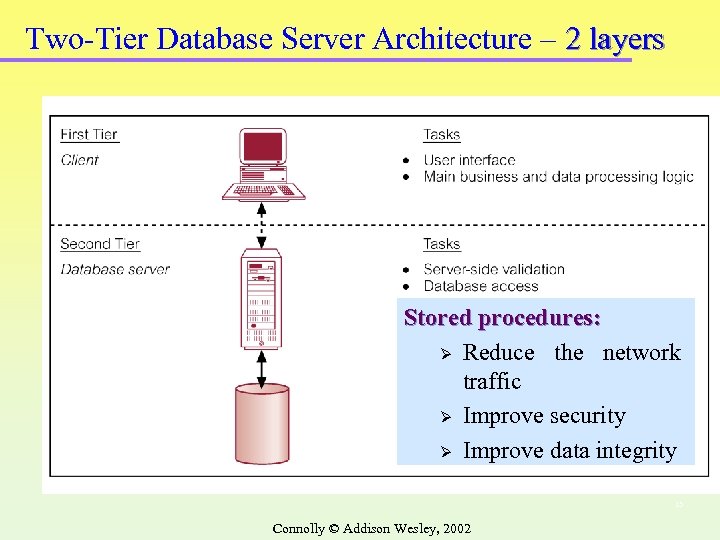
Two-Tier Database Server Architecture – 2 layers Stored procedures: Ø Reduce the network traffic Ø Improve security Ø Improve data integrity 13 Connolly © Addison Wesley, 2002
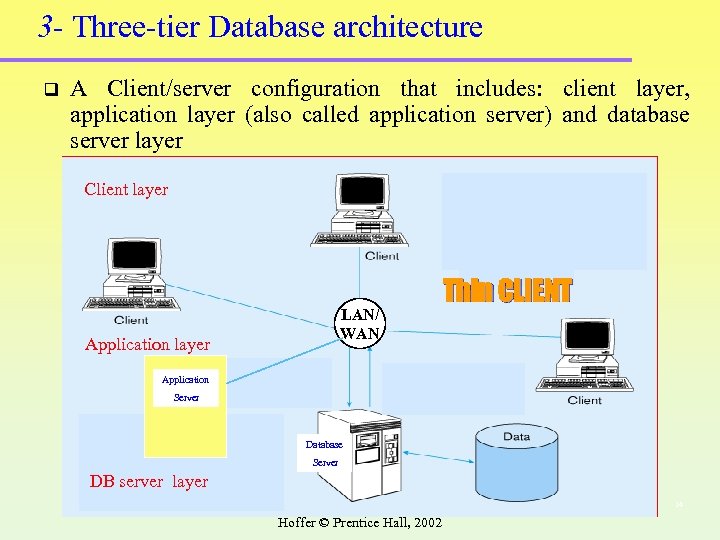
3 - Three-tier Database architecture q A Client/server configuration that includes: client layer, application layer (also called application server) and database server layer Client layer LAN/ WAN Application layer Thin CLIENT Application Server Database Server DB server layer 14 Hoffer © Prentice Hall, 2002
Three-Tier Database Architecture - 3 layers Client only performs a little processing with limited or no data storage l Application server performs the data processing and applies the business rules l Database server performs the data validation & data access l l Database connectivity provides a link between the application logic and the DBMS 15 A. Benabdelkader ©Uv. A, 2002/2003
Advantages of 3 -tier compared to 2 -tier 3 -tier architecture is a popular choice for Internet applications and Net-centric information systems q The architecture provides an increased level of: Ø Scalability § The load between layers can be measured and adjusted Ø Flexibility /Reusability § Loose coupling among the data and application § Less reliance on proprietary DBMS languages § Easier to change the DBMS Ø Performance / Reduced risks § Lower load on client and division of load between the application layer and the server layer Ø Lower long term costs § For maintenance and changes in the configuration © H. Afsarmansesh, 2003 16
Client/Server Architecture - Types of Clients q Fat clients Client does most of the work Ø Relatively large and complex Ø Responsible for user interfaces, application logic and many of the DBMS functions Ø q Thin clients Client is simple and light Ø A PC configured for handling user interfaces Ø Limited storage Ø © H. Afsarmansesh, 2003 17
Client/Server Architecture – Application partitioning q Partitioning a Database application Ø There is no one optimal client/server architecture solution for all database applications Ø A main goal is to reach better performance and interoperability Ø Decisions must be made about the placement of the processing logic Ø How to partition the environment into two-, three-, or n-tier architecture v In each case, storage logic is always handled by the DB server, and the presentation logic by the Client © H. Afsarmansesh, 2003 18

WEB-DATABASES 19
Data on the Web sites Many Web sites are file-based, where each Web document is stored in a separate file q For large sites, this can lead to significant data management problems q Also many Web sites now contain more dynamic information, e. g. products and pricing data q Maintaining updated data in both a database and separate static HTML files is problematic q Accessing database directly from Web would be a better approach q 20 Connolly © Addison Wesley, 2002
Management of data at Web servers Static Web page is an HTML documents stored in a file q Content of a dynamic Web page is generated each time it is accessed Ø Can respond to user input from browser Ø Can be customized for each user Ø Hypertext formatting of the page is used by the server to generate it Ø Needs scripts that perform conversions from different data formats (of the databse) into the HTML ‘on-the-fly’ q 21 Connolly © Addison Wesley, 2002
Web-Databases (or Web-based databases) q Web-databases are structured information repositories that can dynamically interact with a Web Server Ø Web-databases allow for storing data content, in a Web-structured format and let user publish information on the web Ø Web-databases provide a set of high-level functionality tools that support the development, maintenance, and deployment of applications with relative ease and speed 22 A. Benabdelkader ©Uv. A, 2002 /2003
Advantages of Web-Databases DBMS support Ø data structure, security for access, query languages, etc. q Platform independence q Standardization Ø through standard database connectivity layers q Open-architecture that allows interoperability with a variety of systems and technologies. q Cost-effective solution that allows for scalability, growth, and changes in strategic directions, and helps reduce applications development costs q… q 23 Connolly © Addison Wesley, 2002
Disadvantages of Web-Databases Reliability / Availability q Web Security q Immaturity of development tools q Performance / load balancing q Statelessness q Ø Ø Statelessness - no information about transactions is maintained on the server (cookies can be used if necessary) Maintaining State - server tracks the state, e. g. location, selections made, user information © H. Afsarmansesh, 2003 24

Web-Databases Applications Catalogs q Directories (e. g. Yellow pages) q Online-Shopping q Online Auctions q Training courses q Resource libraries q Surveys q Financial Analysis q… q © H. Afsarmansesh, 2003 25
Approaches to Integrate Web and DBMSs Client/server architecture development, using: Java, JDBC, SQLJ, Servlets, and JSP q Common Gateway Interface (CGI) q Extending the Web Server Ø e. g. database request handling middleware q Microsoft Web Solution Platform Ø ASP and ADO q… q 26 Connolly © Addison Wesley, 2002
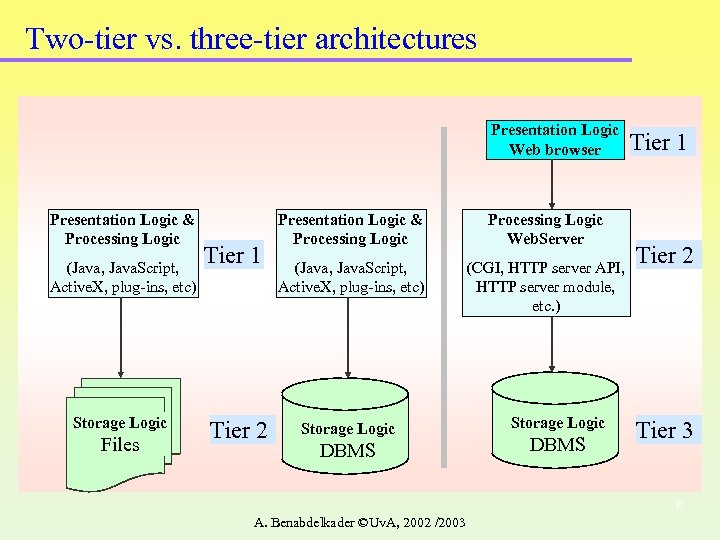
Two-tier vs. three-tier architectures Presentation Logic Web browser Presentation Logic & Processing Logic (Java, Java. Script, Active. X, plug-ins, etc) Storage Logic Files Tier 1 Tier 2 Presentation Logic & Processing Logic Web. Server (Java, Java. Script, Active. X, plug-ins, etc) (CGI, HTTP server API, HTTP server module, etc. ) Storage Logic DBMS Tier 1 Tier 2 Tier 3 27 A. Benabdelkader ©Uv. A, 2002 /2003
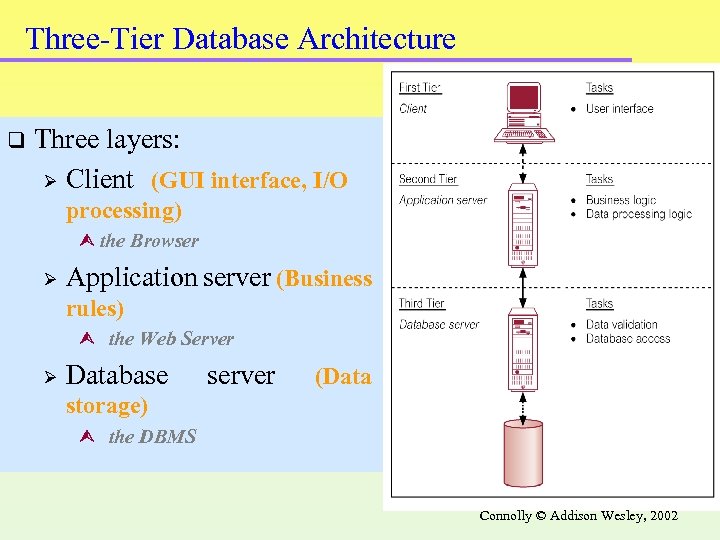
Three-Tier Database Architecture q Three layers: Ø Client (GUI interface, I/O processing) the Browser Ø Application server (Business rules) the Web Server Ø Database server (Data storage) the DBMS 28 Connolly © Addison Wesley, 2002
Client/Server Database Environment ‘Thin’ client, requires less power/cost hardware at the client side q Application maintenance is centralized q Easier to modify or replace one tier without affecting the others q Separating business logic from database functions, makes it easier to implement load balancing q Maps quite naturally to the Web environment q… q 29 Connolly © Addison Wesley, 2002
C/S Database Environment – advantages/disadvantages Advantages: q q q Scalability Technological flexibility Long-term cost reduction Better match of systems to business needs Reduced risk Challenges: q q High short-term costs Tools and training Incompatible standards Interaction with Legacy databases 30 Hoffer © Prentice Hall, 2002
C/S Database Environment - Middleware Software which allows an application to interoperate with other software q No need for programmer/user to understand code low-level operations for interoperability and internal processing q Accomplished via Application Program Interface (API) utilities q The “glue” that holds different layers of the client/server applications together 31 Hoffer © Prentice Hall, 2002
Classification of base tools/approaches to build Middleware q Remote Procedure Calls (RPC) - synchronous / asynchronous Ø Ø q Message-Oriented Middleware (MOM) Ø q Push technology server publishes information, to subscribed clients, when available Object Request Broker (ORB) Ø q Asynchronous calls between the client via message queues Publish/Subscribe Ø q Client makes calls to procedures running on remote computers Similar to Remote Method Invocation (RMI) Object-oriented management of communications between clients and servers SQL-oriented Data Access Ø SQL-based Middleware between applications and database servers 32 Hoffer © Prentice Hall, 2002
Types of Middleware access to Databases q Application Program Interface (API) for Native database Ø A set of operations to access/manipulate the data Ø Efficient Ø Application developers use APIs, and so do not need to develop low level DB operations q ODBC & JDBC Ø Provide database connectivity standards supported by most popular databases Ø Fast and have high flexibility Ø Complexity in learning © H. Afsarmansesh, 2003 33

MANAGING WEBSITES AND WEB-DATABASE SECURITY 34
Challenges in Managing Websites q Web-based systems Security Issues Ø q User’s Privacy Issues Ø q Prevent unauthorized access and malicious data destruction Protect users’ privacy rights Coping with the Rate-of-Change of Internet Technology Ø Deal with rapid advances in technology 35 Hoffer © Prentice Hall, 2002
Security in Client/Server Database Environment An important inhibitor to the growth of e-commerce: lack of user’s confidence in the security of webtransactions q q Protection of sensitive information and preservation of user’s access rights, through the web-related database access q Risk assessment and regular monitoring & testing for intrusion q Even new software tools/techniques may break the security of the site 36 A. Benabdelkader ©Uv. A, 2002 /2003
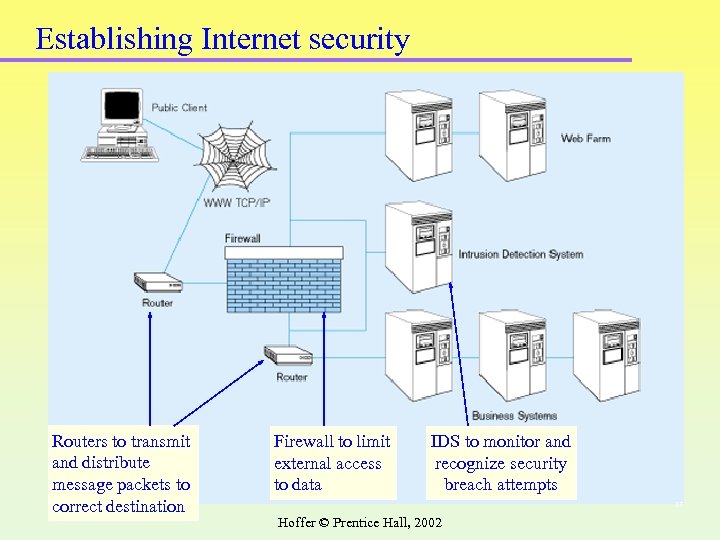
Establishing Internet security Routers to transmit and distribute message packets to correct destination Firewall to limit external access to data IDS to monitor and recognize security breach attempts 37 Hoffer © Prentice Hall, 2002
Website Security enablers q Firewall – hardware/software security component that limits the external access to company’s data q Proxy server – firewall component that manages Internet traffic to and from a LAN q Router – intermediate device that transmits message packets to correct destination over most efficient pathway q Intrusion detection system (IDS) – system that identifies attempt to hack or break into a system 38 Hoffer © Prentice Hall, 2002
Variety of Security levels for C/S Environment -1 Network environments create multi-layer security issues (Network, OS, Web-server, Database, Communication) q 1 - Network-level security § create an account with a user name and password § Web server and DB server on separate LAN away from other business systems § Minimize sharing of hard disks among servers § Regular monitoring of network and firewall logs § Install probe (attack)-monitor software © H. Afsarmansesh, 2003 39
Variety of Security levels for C/S Environment -2 2 - Operating system-level security § Patch (fix) all known OS vulnerabilities and look for new ones § Install anti-virus software for: the system boottime, file download time, and the email reception time, for virus detection § Monitor server logs for unauthorized activity, e. g using IDS Intrusion detective system § Disable non-required services to reduce risk of unauthorized access, e. g. sending automatic emails during an Internet access, that is allowed by the OS, should be disabled © H. Afsarmansesh, 2003 40
Variety of Security levels for C/S Environment - 3 3 - Web-server-level security § Restrict number of users on Web server - Give as few as possible “super users” and administrator rights § Restrict the access (minimize number of open ports) - http and https only, if possible § Remove unneeded programs that load automatically when setting up the server - Delete demo programs that give hackers the access details desired - Restrict CGI scripts (have security problems) to one subdirectory § For Unix, only install minimum software for Web server - Do not boot the default OS that provides a lot of added functionality § Compilers should not be accessible through the path for internal access © H. Afsarmansesh, 2003 41
Variety of Security levels for C/S Environment - 4 4 - Database level security To restrict access/manipulations rights of users to the DBs. § Login/Password check § Creating user roles and privileges assigned to user roles § Views § Access, authorization, rights preservation § Other measures: - Extra check when executing user-defined procedures - Asking extra information (Mother’s maiden name) © H. Afsarmansesh, 2003 42
Variety of Security levels for C/S Environment -5 5 - Data communication level security § TCP/IP is not a very secure protocol § Encryption/decryption processes - transforming readable (plain text) data into unreadable (ciphertext) § A standard encryption method is the Secure Socket Layer (SSL), that is used by the “https” (not with the http) §Public key / Private key §Authentication / bio-metric devices (finger-print, eye pictures, voice recognition) §Digital signature § the Virtual Private Network (VPN) © H. Afsarmansesh, 2003 43
Anonymity vs. Security of Internet communication q q Internet communication must be secure & Internet communication must remain anonymous Ø Ø Ø q q Chat rooms E-mail Access to public data (web-pages) Tracking devices installed on the servers for National security reasons (e. g. FBI’s email monitoring devices installed on email servers, Carnivor and DCS 1000) Advertisement agencies tracking down users access for their data collection purposes © H. Afsarmansesh, 2003 44

References to books q DATABASE SYSTEMS - A practical Approach to Design, Implementation, and Management, T. Connolly, C. Begg, Third Edition, Addison Wesley, 2002. q MODERN DATABASE MANAGEMENT, J. A. Hoffer, M. B. Prescott, F. R. Mc. Fadden, Sixth Edition, Prentice Hall, 2002. q Core SERVLETS and JAVASERVER PAGES, M. Hall, Java 2 Platform, Enterprise Edition Series, Prentice Hall 2002. 45
55d0de33f1a8be9ec884c7a28a2cb5d4.ppt