52da9726201ce43b0cbc534c9a5edf7e.ppt
- Количество слайдов: 24

Progress Report on resource certification February 2007 Geoff Huston Chief Scientist APNIC

Objective • To create a robust framework that allows validation of assertions relating to IP addresses and ASNs and their use and • To make it easier for anyone to see if someone is lying about actual control over addresses and/or routing!

Uses • Signing of IRR entries “Yes, I am the right-of-use holder and that’s precisely the information I entered into the IRR. ” • Signing of Routing Origination “Yes, I am the right-of-use holder for this address prefix and I am permitting ASx to originate a route to this address prefix. ” • Signing of Route Requests “Please route address prefix a. b. c. d/x through customer interface xxx. ”

Resources for this work • APNIC’s allocation database • Public / private key technology • X. 509 v 3 certificate technology • IP resource extensions to X. 509 v 3 certificates • PKI models and trust relationships

The overall objective • To support a PKI that mirrors the existing resource allocation state – Every resource allocation can be attested by a matching certificate that binds the allocated resource with the resource issuer and recipient • To use these resource certificates to make signed assertions that can be validated through this PKI
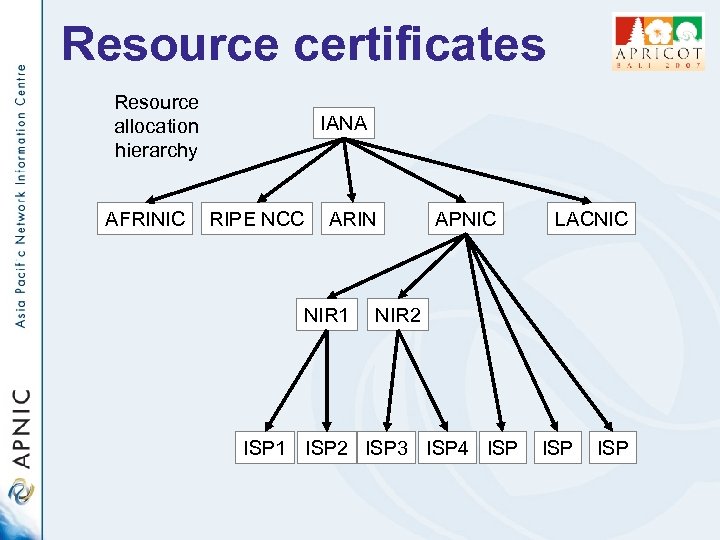
Resource certificates Resource allocation hierarchy AFRINIC IANA RIPE NCC ARIN NIR 1 APNIC LACNIC NIR 2 ISP 1 ISP 2 ISP 3 ISP 4 ISP ISP
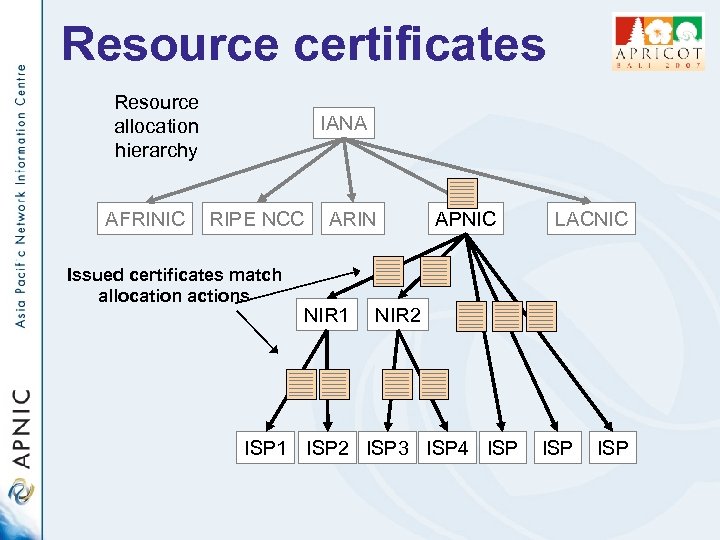
Resource certificates Resource allocation hierarchy AFRINIC IANA RIPE NCC Issued certificates match allocation actions ARIN NIR 1 APNIC LACNIC NIR 2 ISP 1 ISP 2 ISP 3 ISP 4 ISP ISP
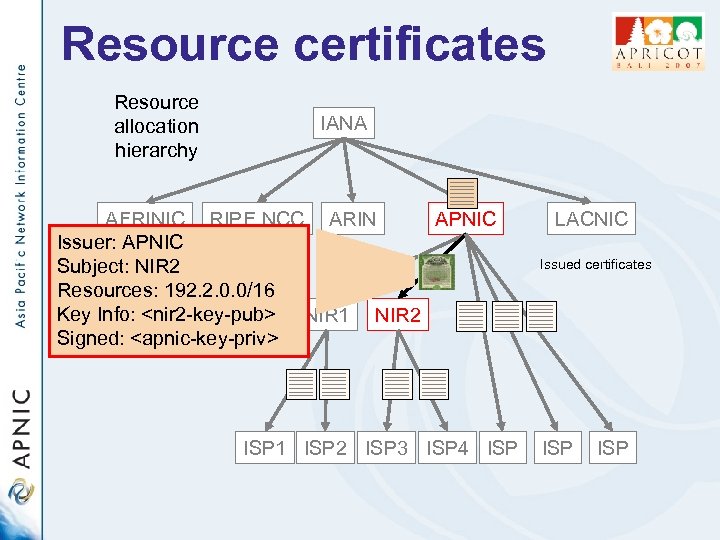
Resource certificates Resource allocation hierarchy IANA AFRINIC RIPE NCC ARIN APNIC Issuer: APNIC Subject: NIR 2 Resources: 192. 2. 0. 0/16 Key Info: <nir 2 -key-pub> NIR 1 NIR 2 Signed: <apnic-key-priv> ISP 1 ISP 2 ISP 3 ISP 4 ISP LACNIC Issued certificates ISP
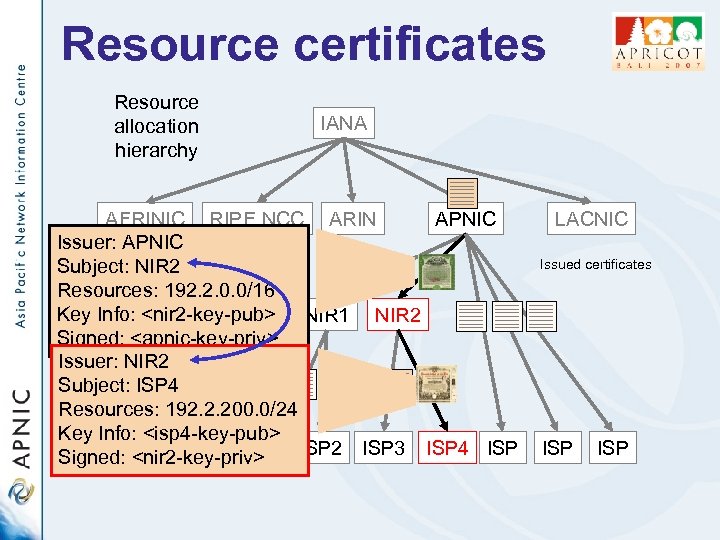
Resource certificates Resource allocation hierarchy IANA AFRINIC RIPE NCC ARIN APNIC Issuer: APNIC Subject: NIR 2 Resources: 192. 2. 0. 0/16 Key Info: <nir 2 -key-pub> NIR 1 NIR 2 Signed: <apnic-key-priv> Issuer: NIR 2 Subject: ISP 4 Resources: 192. 2. 200. 0/24 Key Info: <isp 4 -key-pub> Signed: <nir 2 -key-priv> ISPISP 2 ISP 3 ISP 4 ISP LACNIC Issued certificates ISP
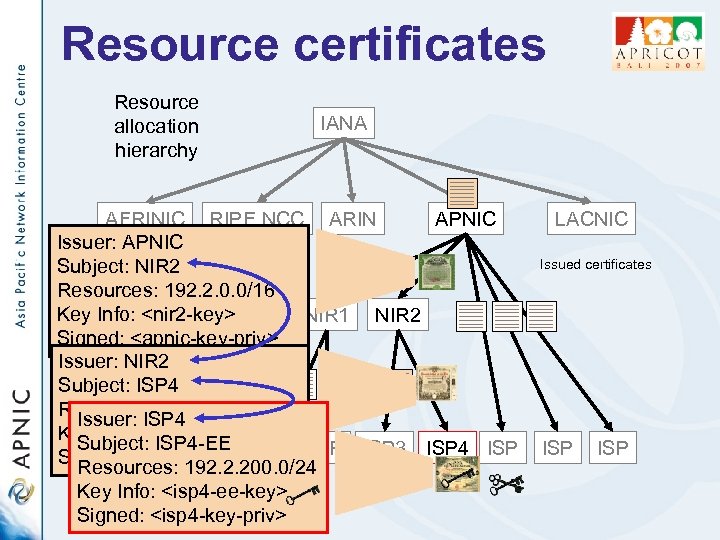
Resource certificates Resource allocation hierarchy IANA AFRINIC RIPE NCC ARIN APNIC Issuer: APNIC Subject: NIR 2 Resources: 192. 2. 0. 0/16 Key Info: <nir 2 -key> NIR 1 NIR 2 Signed: <apnic-key-priv> Issuer: NIR 2 Subject: ISP 4 Resources: 192. 2. 200. 0/22 Issuer: ISP 4 Key Info: <isp 4 -key> Subject: ISP 4 -EE Signed: <nir 2 -key-priv> ISP ISP 3 ISP 4 ISP Resources: 192. 2. 200. 0/24 Key Info: <isp 4 -ee-key> Signed: <isp 4 -key-priv> LACNIC Issued certificates ISP
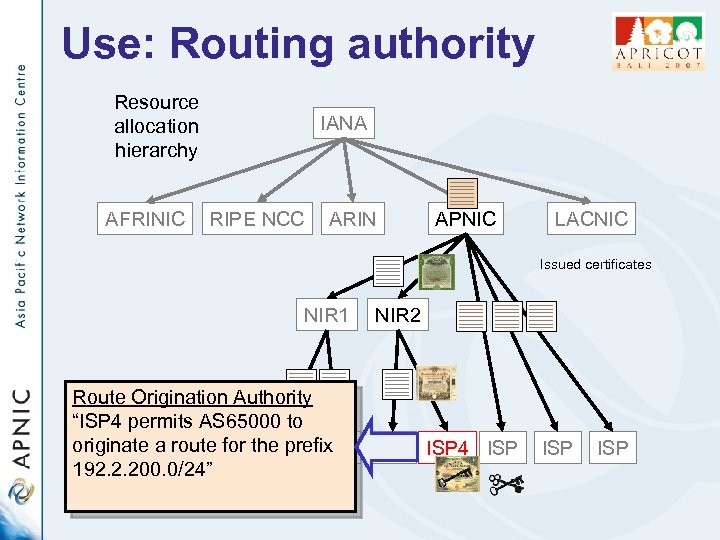
Use: Routing authority Resource allocation hierarchy AFRINIC IANA RIPE NCC ARIN APNIC LACNIC Issued certificates NIR 1 Route Origination Authority “ISP 4 permits AS 65000 to originate a route for the prefix ISP 192. 2. 200. 0/24” NIR 2 ISP 4 ISP ISP
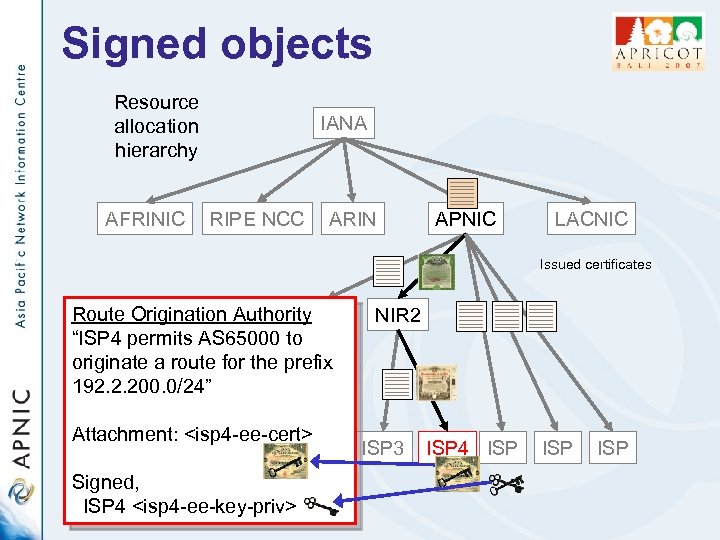
Signed objects Resource allocation hierarchy AFRINIC IANA RIPE NCC ARIN APNIC LACNIC Issued certificates Route Origination Authority LIR 1 “ISP 4 permits AS 65000 to originate a route for the prefix 192. 2. 200. 0/24” NIR 2 Attachment: <isp 4 -ee-cert> ISP ISP 3 Signed, ISP 4 <isp 4 -ee-key-priv> ISP 4 ISP ISP
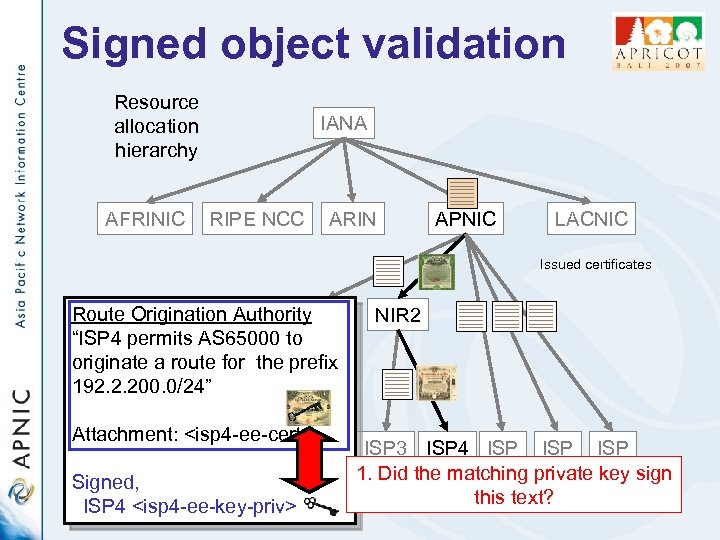
Signed object validation Resource allocation hierarchy AFRINIC IANA RIPE NCC ARIN APNIC LACNIC Issued certificates Route Origination Authority LIR 1 “ISP 4 permits AS 65000 to originate a route for the prefix 192. 2. 200. 0/24” NIR 2 Attachment: <isp 4 -ee-cert> ISP ISP 3 ISP 4 ISP ISP 1. Did the matching private key sign Signed, this text? ISP 4 <isp 4 -ee-key-priv>
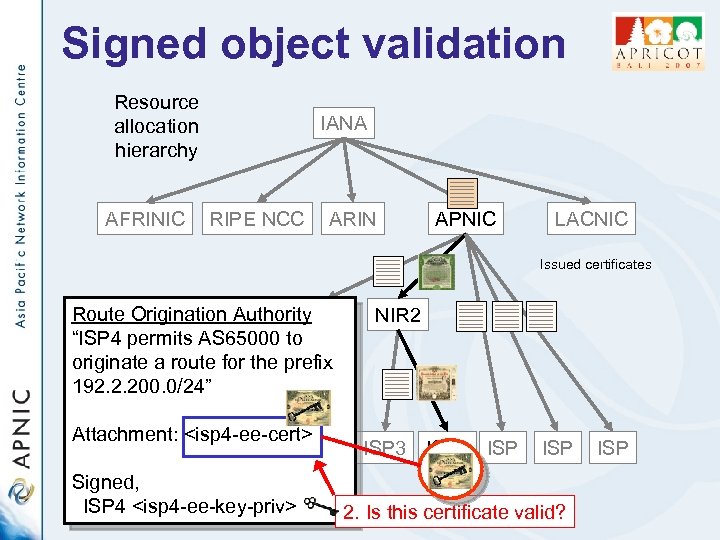
Signed object validation Resource allocation hierarchy AFRINIC IANA RIPE NCC ARIN APNIC LACNIC Issued certificates Route Origination Authority LIR 1 “ISP 4 permits AS 65000 to originate a route for the prefix 192. 2. 200. 0/24” NIR 2 Attachment: <isp 4 -ee-cert> ISP ISP 3 ISP 4 ISP Signed, ISP 4 <isp 4 -ee-key-priv> ISP 2. Is this certificate valid? ISP
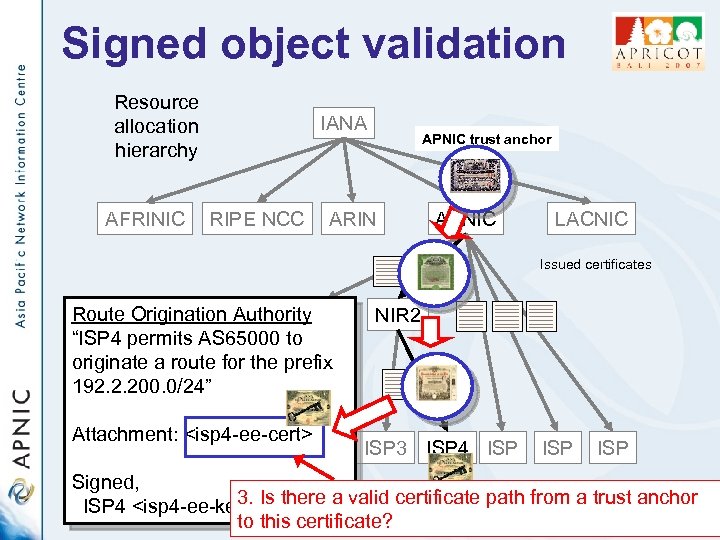
Signed object validation Resource allocation hierarchy AFRINIC IANA RIPE NCC APNIC trust anchor ARIN APNIC LACNIC Issued certificates Route Origination Authority LIR 1 “ISP 4 permits AS 65000 to originate a route for the prefix 192. 2. 200. 0/24” NIR 2 Attachment: <isp 4 -ee-cert> ISP ISP 3 ISP 4 ISP ISP Signed, 3. Is there a valid certificate path from a trust anchor ISP 4 <isp 4 -ee-key-priv> to this certificate?
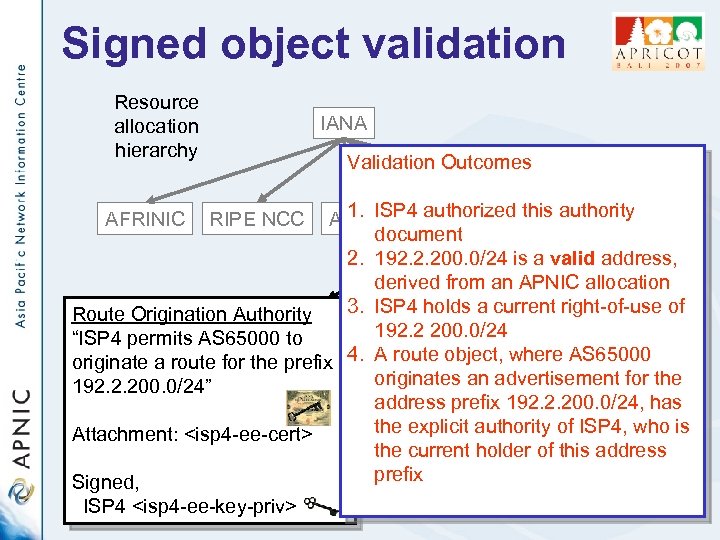
Signed object validation Resource allocation hierarchy IANA RIPE NCC Trust Anchor Validation Outcomes 1. authorized authority ARINISP 4 RIPE NCC this LACNIC document 2. 192. 2. 200. 0/24 is a valid address, Issued Certificates derived from an APNIC allocation Route Origination Authority LIR 13. ISP 4 holds a current right-of-use of LIR 2 192. 2 200. 0/24 “ISP 4 permits AS 65000 to originate a route for the prefix 4. A route object, where AS 65000 originates an advertisement for the 192. 2. 200. 0/24” address prefix 192. 2. 200. 0/24, has the explicit authority of ISP 4, who is Attachment: <isp 4 -ee-cert> ISP the current holder of this address ISP 4 ISP ISP prefix Signed, AFRINIC RIPE NCC ISP 4 <isp 4 -ee-key-priv>
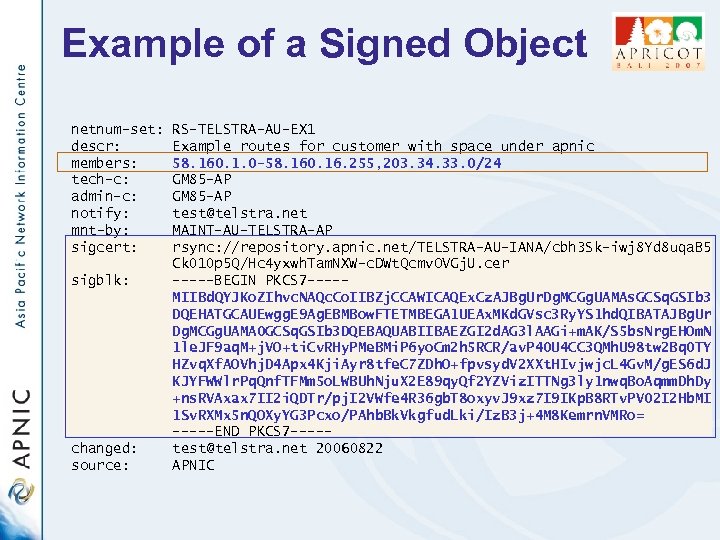
Example of a Signed Object netnum-set: descr: members: tech-c: admin-c: notify: mnt-by: sigcert: sigblk: changed: source: RS-TELSTRA-AU-EX 1 Example routes for customer with space under apnic 58. 160. 1. 0 -58. 160. 16. 255, 203. 34. 33. 0/24 GM 85 -AP test@telstra. net MAINT-AU-TELSTRA-AP rsync: //repository. apnic. net/TELSTRA-AU-IANA/cbh 3 Sk-iwj 8 Yd 8 uqa. B 5 Ck 010 p 5 Q/Hc 4 yxwh. Tam. NXW-c. DWt. Qcmv. OVGj. U. cer -----BEGIN PKCS 7 ----MIIBd. QYJKo. ZIhvc. NAQc. Co. IIBZj. CCAWICAQEx. Cz. AJBg. Ur. Dg. MCGg. UAMAs. GCSq. GSIb 3 DQEHATGCAUEwgg. E 9 Ag. EBMBow. FTETMBEGA 1 UEAx. MKd. GVsc 3 Ry. YS 1 hd. QIBATAJBg. Ur Dg. MCGg. UAMA 0 GCSq. GSIb 3 DQEBAQUABIIBAEZGI 2 d. AG 3 l. AAGi+m. AK/S 5 bs. Nrg. EHOm. N 1 le. JF 9 aq. M+j. VO+ti. Cv. RHy. PMe. BMi. P 6 yo. Cm 2 h 5 RCR/av. P 40 U 4 CC 3 QMh. U 98 tw 2 Bq 0 TY HZvq. Xf. AOVhj. D 4 Apx 4 Kji. Ayr 8 tfe. C 7 ZDh. O+fpvsyd. V 2 XXt. HIvjwjc. L 4 Gv. M/g. ES 6 d. J KJYFWWlr. Pq. Qnf. TFMm 5 o. LWBUh. Nju. X 2 E 89 qy. Qf 2 YZViz. ITTNg 3 ly 1 nwq. Bo. Aqmm. Dh. Dy +ns. RVAxax 7 II 2 i. QDTr/pj. I 2 VWfe 4 R 36 gb. T 8 oxyv. J 9 xz 7 I 9 IKp. B 8 RTv. PV 02 I 2 Hb. MI 1 Sv. RXMx 5 n. QOXy. YG 3 Pcxo/PAhb. Bk. Vkgfud. Lki/Iz. B 3 j+4 M 8 Kemrn. VMRo= -----END PKCS 7 ----test@telstra. net 20060822 APNIC
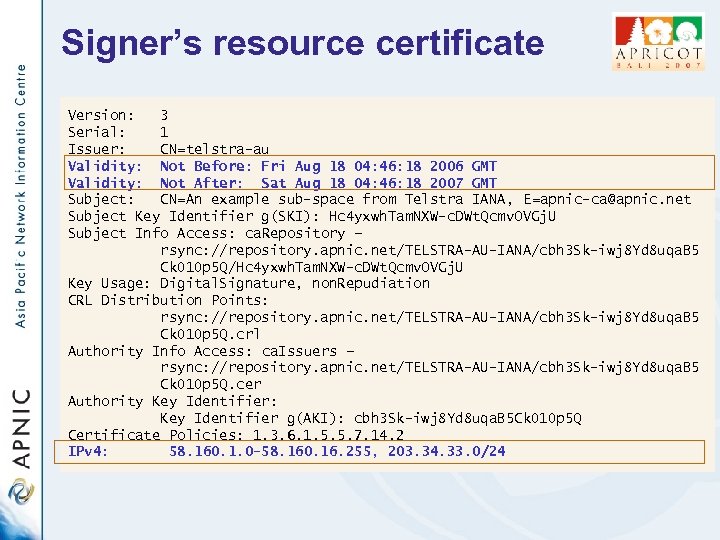
Signer’s resource certificate Version: 3 Serial: 1 Issuer: CN=telstra-au Validity: Not Before: Fri Aug 18 04: 46: 18 2006 GMT Validity: Not After: Sat Aug 18 04: 46: 18 2007 GMT Subject: CN=An example sub-space from Telstra IANA, E=apnic-ca@apnic. net Subject Key Identifier g(SKI): Hc 4 yxwh. Tam. NXW-c. DWt. Qcmv. OVGj. U Subject Info Access: ca. Repository – rsync: //repository. apnic. net/TELSTRA-AU-IANA/cbh 3 Sk-iwj 8 Yd 8 uqa. B 5 Ck 010 p 5 Q/Hc 4 yxwh. Tam. NXW-c. DWt. Qcmv. OVGj. U Key Usage: Digital. Signature, non. Repudiation CRL Distribution Points: rsync: //repository. apnic. net/TELSTRA-AU-IANA/cbh 3 Sk-iwj 8 Yd 8 uqa. B 5 Ck 010 p 5 Q. crl Authority Info Access: ca. Issuers – rsync: //repository. apnic. net/TELSTRA-AU-IANA/cbh 3 Sk-iwj 8 Yd 8 uqa. B 5 Ck 010 p 5 Q. cer Authority Key Identifier: Key Identifier g(AKI): cbh 3 Sk-iwj 8 Yd 8 uqa. B 5 Ck 010 p 5 Q Certificate Policies: 1. 3. 6. 1. 5. 5. 7. 14. 2 IPv 4: 58. 160. 1. 0 -58. 160. 16. 255, 203. 34. 33. 0/24

Trial activity status ü ü Specification of X. 509 resource certificates Generation of resource certificate repositories aligned with existing resource allocations and assignments Tools for registration authority / certificate authority interaction (undertaken by RIPE NCC) Tools to perform validation of resource certificate extensions to Open. SSL for Resource Certificates (open source development activity, supported by ARIN) Current activities Tools for resource collection management, object signing and signed object validation (APNIC, and also open source development activity, supported by ARIN) LIR / ISP Tools for certificate management Testing, testing Operational service profile specification Working notes and related material we’ve been working on in this trial activity: http: //mirin. apnic. net/resourcecerts

Focus points for Q 1 2007 • Can we design the certificate management subsystem to be an largely automated “slave” of the resource allocation function? • Provide a toolset to allow IRs to manage certificate issuance • Use the same toolset to provide ‘hosted’ certificate services
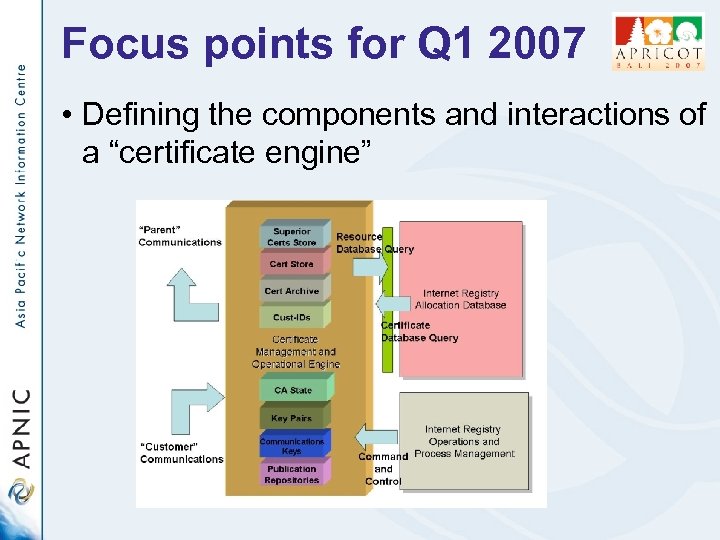
Focus points for Q 1 2007 • Defining the components and interactions of a “certificate engine”

Focus points for Q 1 2007 • Automated certificate issuance – Query / response interaction between registry and registry clients: • List: What resources have been allocated to me and what’s the corresponding state of issued certificates? • Issue: Here is a certificate request – please issue me with a certificate that matches my allocated resource set • Remove: Please revoke certificates issued with this public key

Next steps • Development of the Certificate Engine • End entity Certificates • Tools for relying parties • Evaluation of progress

Thank you http: //mirin. apnic. net/resourcecerts Questions?
52da9726201ce43b0cbc534c9a5edf7e.ppt