5d8e6fb4554e6edaaaad8787ad510cb5.ppt
- Количество слайдов: 17
Profile-based Web Application Security System 2006 -2 -20 Kyungtae Kim High Performance Computing Lab at Postech 2 nd Joint Workshop between Security Research Labs in Korea and Japan 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Contents Introduction p Related Works p n n Application-Level Web Security Policies Anomaly Detection of Web-based Attacks Problem Definition p Proposed Idea p n n n p Dynamic Model Organization Detection Models Applying Methods Conclusion & Future Works 2 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA

Introduction p Application-level web attack n n p Uses vulnerabilities in the code of a web application. Can’t be covered by traditional method. Unvalidated input : Most critical vulnerability n n n Cross Site Scripting (XSS) : Attacker uses trusted application/company to reflect malicious code to end-user. Buffer Overflows : Attacker attempts to store more data in a buffer than there is memory allocated for it Injection Attacks : Attacker relays malicious code in form variables or URL. 3 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
![Related Works (1/3) [1] Policy-based Web Application Firewall* p Policy : defining validation rules Related Works (1/3) [1] Policy-based Web Application Firewall* p Policy : defining validation rules](https://present5.com/presentation/5d8e6fb4554e6edaaaad8787ad510cb5/image-4.jpg)
Related Works (1/3) [1] Policy-based Web Application Firewall* p Policy : defining validation rules (length, type, etc. ) Filters the HTTP messages between the web-server and client Translates the SPDL into server-side code Automates the policy creation (not fully automated) Specifies the policy * David Scott and Richard Sharp, “Specifying and Enforcing Application. Level Web Security Policies”, 2003 IEEE 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA 4
![[2] Multi-model Approach* (1/2) p Related Works (2/3) Anomaly detection method n n p [2] Multi-model Approach* (1/2) p Related Works (2/3) Anomaly detection method n n p](https://present5.com/presentation/5d8e6fb4554e6edaaaad8787ad510cb5/image-5.jpg)
[2] Multi-model Approach* (1/2) p Related Works (2/3) Anomaly detection method n n p profile-based using positive models (models for normal behavior) Operation of positive models n Training phase : determining the characteristics of normal events n Detection phase : assessing the anomaly of a event, reporting anomalous events * Christopher Kruegel, Giovanni Vigna , “A multi-model approach to the detection of web-based attacks”, 2005 5 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
![[2] Multi-model Approach p Related Works (3/3) (2/2) Multi-model n n p Widening the [2] Multi-model Approach p Related Works (3/3) (2/2) Multi-model n n p Widening the](https://present5.com/presentation/5d8e6fb4554e6edaaaad8787ad510cb5/image-6.jpg)
[2] Multi-model Approach p Related Works (3/3) (2/2) Multi-model n n p Widening the coverage of detection Preventing attacker’s manipulation avoiding specific model Detection models n n Attribute Character Distribution n Structural Inference n Token Finder n Attribute Presence or Absence n p Attribute Length Attribute Order Anomaly score (for each attribute) n Derived from the probability values returned by the models 6 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
![Problem Definition p Shortcomings of Related Works n [1]Policy-based Not automated method p Too Problem Definition p Shortcomings of Related Works n [1]Policy-based Not automated method p Too](https://present5.com/presentation/5d8e6fb4554e6edaaaad8787ad510cb5/image-7.jpg)
Problem Definition p Shortcomings of Related Works n [1]Policy-based Not automated method p Too simple policy p n [2] Multi-model Approach Applying all models to all attributes Low speed p Ignoring each attribute’s characteristics p p Problem Definition n Proposing new application-level web security system that uses automated method and operates on real time. 7 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
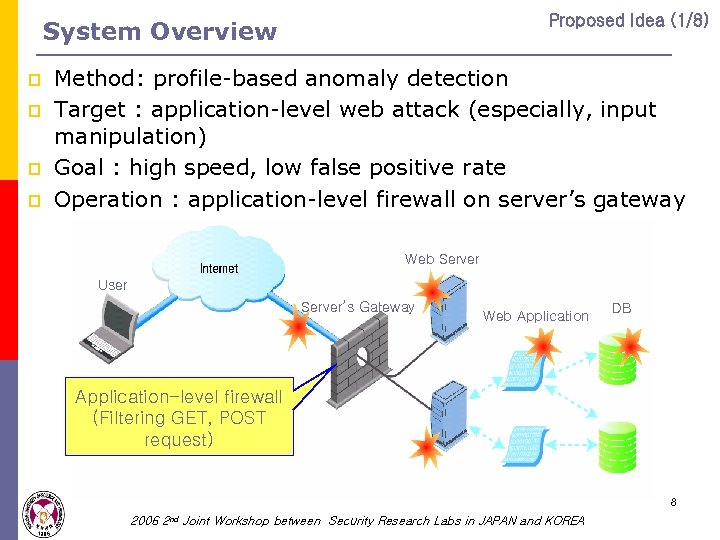
Proposed Idea (1/8) System Overview p p Method: profile-based anomaly detection Target : application-level web attack (especially, input manipulation) Goal : high speed, low false positive rate Operation : application-level firewall on server’s gateway Web Server User Server’s Gateway Web Application DB Application-level firewall (Filtering GET, POST request) 8 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Dynamic Model Organization - Necessity Proposed Idea (2/8) p Each attribute has its own characteristics. p Some model can disturb the division of normal/ abnormal value of specific attribute. n ex> User ID has dynamic character distribution, and some normal values are misjudged to anomaly. (‘aaaa’ vs ‘<script>’) p On most of the attributes, small set of models are important for detection. n Deciding set of models in advance Faster detection 9 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
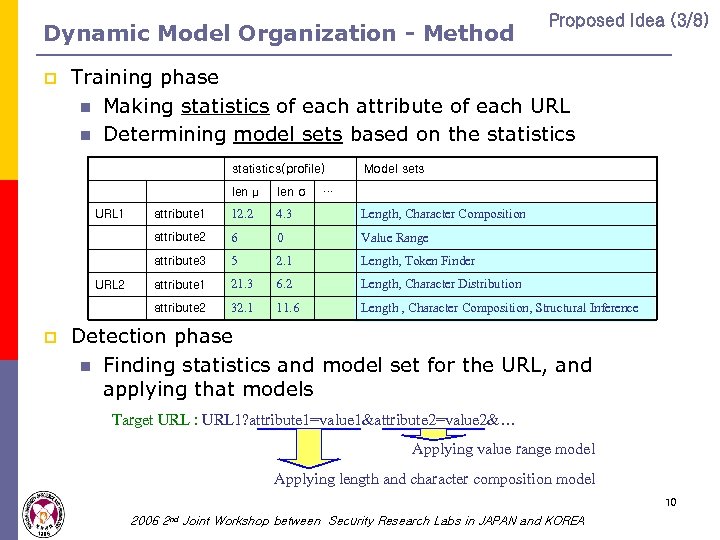
Dynamic Model Organization - Method p Proposed Idea (3/8) Training phase n Making statistics of each attribute of each URL n Determining model sets based on the statistics(profile) Model sets len μ 4. 3 Length, Character Composition 6 0 Value Range 5 2. 1 Length, Token Finder attribute 1 21. 3 6. 2 Length, Character Distribution attribute 2 p 12. 2 attribute 3 URL 2 attribute 1 attribute 2 URL 1 len σ … 32. 1 11. 6 Length , Character Composition, Structural Inference Detection phase n Finding statistics and model set for the URL, and applying that models Target URL : URL 1? attribute 1=value 1&attribute 2=value 2&… Applying value range model Applying length and character composition model 10 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
![Detection Models (1/2) Proposed Idea (4/8) Length (similar with [2]) p Character Distribution (similar Detection Models (1/2) Proposed Idea (4/8) Length (similar with [2]) p Character Distribution (similar](https://present5.com/presentation/5d8e6fb4554e6edaaaad8787ad510cb5/image-11.jpg)
Detection Models (1/2) Proposed Idea (4/8) Length (similar with [2]) p Character Distribution (similar with [2]) p Structural Inference (similar with [2]) p Token Finder (similar with [2]) p Character Composition p Value Range p 11 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
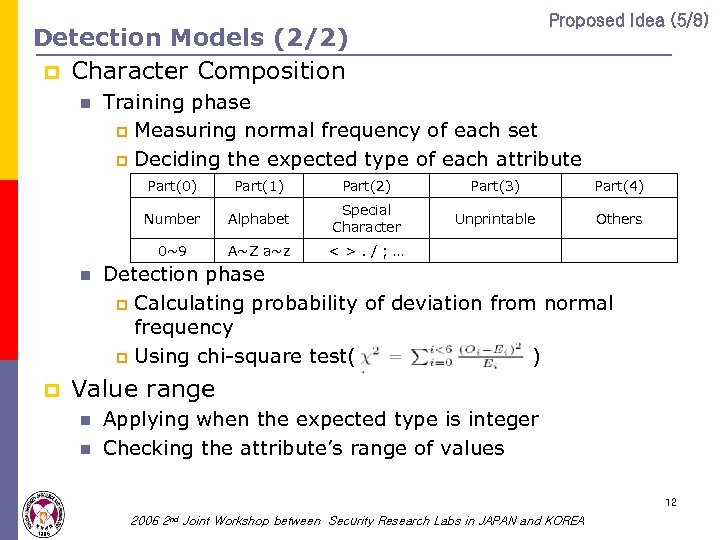
Proposed Idea (5/8) Detection Models (2/2) p Character Composition n Training phase p Measuring normal frequency of each set p Deciding the expected type of each attribute Part(0) Part(3) Part(4) Alphabet Special Character Unprintable Others 0~9 p Part(2) Number n Part(1) A~Z a~z <>. /; … Detection phase p Calculating probability of deviation from normal frequency p Using chi-square test( ) Value range n n Applying when the expected type is integer Checking the attribute’s range of values 12 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA

Applying Methods (1/3) p Length n p Enabled to all string attribute. Token Finder n p Proposed Idea (6/8) Enabled when the attribute is composed with small set of tokens. Character Composition n Disabled when token finder model is enabled or there are too many special characters and unprintable characters. 13 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
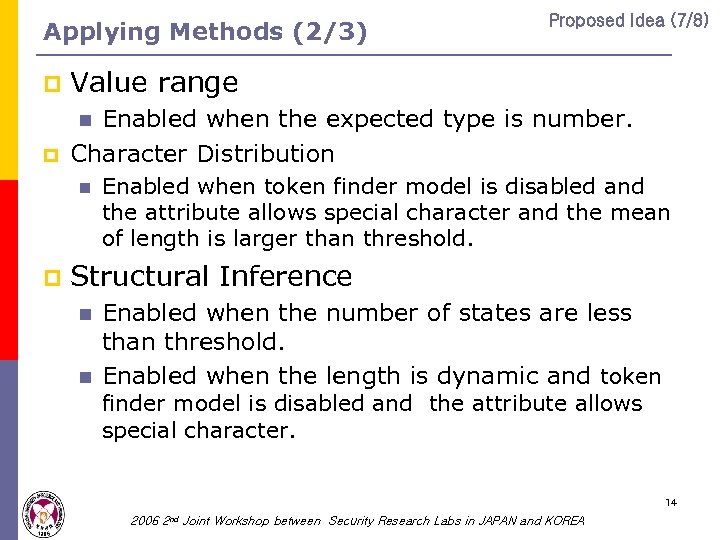
Applying Methods (2/3) Proposed Idea (7/8) p Value range p Enabled when the expected type is number. Character Distribution n n p Enabled when token finder model is disabled and the attribute allows special character and the mean of length is larger than threshold. Structural Inference n n Enabled when the number of states are less than threshold. Enabled when the length is dynamic and token finder model is disabled and the attribute allows special character. 14 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA

Applying Methods (3/3) p Training phase n n p Proposed Idea (8/8) Profiling value of each attribute of each URL Determining each attribute’s model set Detection phase n n n Calculating each model’s probability of abnormality Multiplying the probability and making anomaly score Filtering, modifying or passing the request according to anomaly score 15 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Conclusion & Future Works Unvalidated input is web application’s most critical vulnerability. p Policy-based or signature-based systems are not automated methods, and multimodel based anomaly detection can’t operate on real time. p I introduced profile-based web application security system that gets high speed with dynamic model organization. p Future works are optimizing and evaluating my system. p 16 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA

Thank you! Q&A 17 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
5d8e6fb4554e6edaaaad8787ad510cb5.ppt