88659fd9e914d372c6a7feab43b4658c.ppt
- Количество слайдов: 36
 Products Overview 2013. 4. Ⓒ Copyright XNsystems 2013
Products Overview 2013. 4. Ⓒ Copyright XNsystems 2013
 Company Intro Conpany Xnsystems’ Growth Driving Force 1
Company Intro Conpany Xnsystems’ Growth Driving Force 1
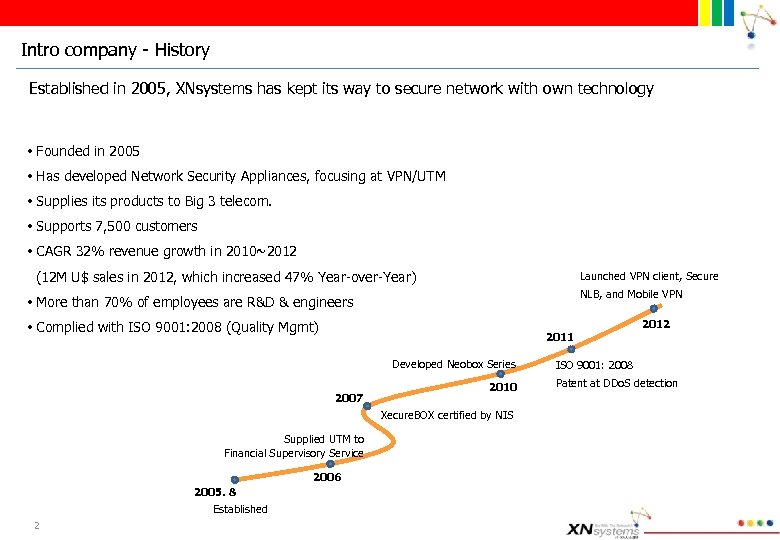 Intro company - History Established in 2005, XNsystems has kept its way to secure network with own technology • Founded in 2005 • Has developed Network Security Appliances, focusing at VPN/UTM • Supplies its products to Big 3 telecom. • Supports 7, 500 customers • CAGR 32% revenue growth in 2010~2012 (12 M U$ sales in 2012, which increased 47% Year-over-Year) Launched VPN client, Secure NLB, and Mobile VPN • More than 70% of employees are R&D & engineers • Complied with ISO 9001: 2008 (Quality Mgmt) 2011 Developed Neobox Series 2007 2010 Xecure. BOX certified by NIS Supplied UTM to Financial Supervisory Service 2006 2005. 8 Established 2 2012 ISO 9001: 2008 Patent at DDo. S detection
Intro company - History Established in 2005, XNsystems has kept its way to secure network with own technology • Founded in 2005 • Has developed Network Security Appliances, focusing at VPN/UTM • Supplies its products to Big 3 telecom. • Supports 7, 500 customers • CAGR 32% revenue growth in 2010~2012 (12 M U$ sales in 2012, which increased 47% Year-over-Year) Launched VPN client, Secure NLB, and Mobile VPN • More than 70% of employees are R&D & engineers • Complied with ISO 9001: 2008 (Quality Mgmt) 2011 Developed Neobox Series 2007 2010 Xecure. BOX certified by NIS Supplied UTM to Financial Supervisory Service 2006 2005. 8 Established 2 2012 ISO 9001: 2008 Patent at DDo. S detection
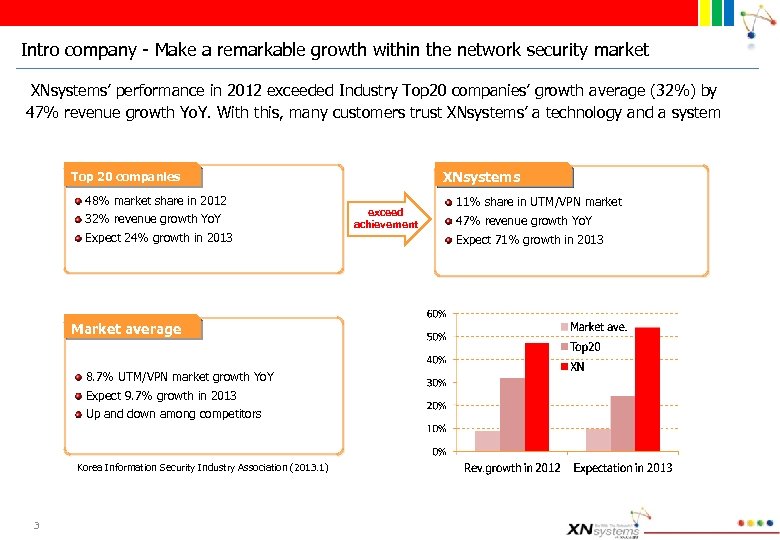 Intro company - Make a remarkable growth within the network security market XNsystems’ performance in 2012 exceeded Industry Top 20 companies’ growth average (32%) by 47% revenue growth Yo. Y. With this, many customers trust XNsystems’ a technology and a system XNsystems Top 20 companies 48% market share in 2012 32% revenue growth Yo. Y Expect 24% growth in 2013 Market average 8. 7% UTM/VPN market growth Yo. Y Expect 9. 7% growth in 2013 Up and down among competitors Korea Information Security Industry Association (2013. 1) 3 exceed achievement 11% share in UTM/VPN market 47% revenue growth Yo. Y Expect 71% growth in 2013
Intro company - Make a remarkable growth within the network security market XNsystems’ performance in 2012 exceeded Industry Top 20 companies’ growth average (32%) by 47% revenue growth Yo. Y. With this, many customers trust XNsystems’ a technology and a system XNsystems Top 20 companies 48% market share in 2012 32% revenue growth Yo. Y Expect 24% growth in 2013 Market average 8. 7% UTM/VPN market growth Yo. Y Expect 9. 7% growth in 2013 Up and down among competitors Korea Information Security Industry Association (2013. 1) 3 exceed achievement 11% share in UTM/VPN market 47% revenue growth Yo. Y Expect 71% growth in 2013
 Intro company - Customers XNsystems is supporting private companies, public institutions, schools and about 10, 000 customers in Korea Public institution Educational institution elementary, middle and high school … Private company Financial Institutions 4 40 universities
Intro company - Customers XNsystems is supporting private companies, public institutions, schools and about 10, 000 customers in Korea Public institution Educational institution elementary, middle and high school … Private company Financial Institutions 4 40 universities
 Growth driving force 1. Customer-driven process The waterfall process for product design is the key to success of XNsystems at target market. We have pursued the cycle from customer’s requirements to customer’s feedback. Focusing at customer requirements at a specific market Proposal and design for optimized tech/services Waterfall process • Proven and awarded by Big 3 Telecom. for more than 10 years • Approach and resolve by its own R&D differently • Customized maintenance and support from expert groups Communication with applicable solutions from QA to R&D Develop new algorithm / products for requirements Continuous improvement of function/performance 5 Feedback from endusers at the market
Growth driving force 1. Customer-driven process The waterfall process for product design is the key to success of XNsystems at target market. We have pursued the cycle from customer’s requirements to customer’s feedback. Focusing at customer requirements at a specific market Proposal and design for optimized tech/services Waterfall process • Proven and awarded by Big 3 Telecom. for more than 10 years • Approach and resolve by its own R&D differently • Customized maintenance and support from expert groups Communication with applicable solutions from QA to R&D Develop new algorithm / products for requirements Continuous improvement of function/performance 5 Feedback from endusers at the market
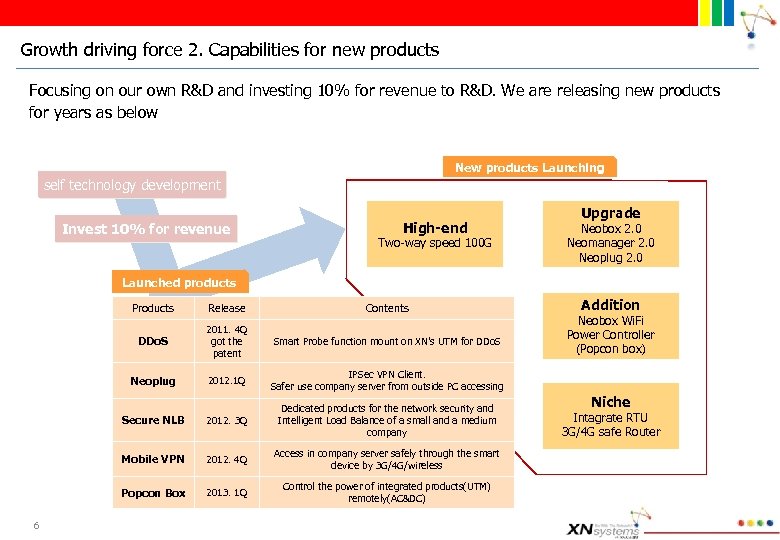 Growth driving force 2. Capabilities for new products Focusing on our own R&D and investing 10% for revenue to R&D. We are releasing new products for years as below New products Launching self technology development Invest 10% for revenue High-end Two-way speed 100 G Upgrade Neobox 2. 0 Neomanager 2. 0 Neoplug 2. 0 Launched products Products Contents DDo. S 2011. 4 Q got the patent Smart Probe function mount on XN’s UTM for DDo. S Neoplug 2012. 1 Q 2012. 3 Q Dedicated products for the network security and Intelligent Load Balance of a small and a medium company Mobile VPN 2012. 4 Q Access in company server safely through the smart device by 3 G/4 G/wireless Popcon Box 2013. 1 Q Control the power of integrated products(UTM) remotely(AC&DC) Addition IPSec VPN Client. Safer use company server from outside PC accessing Secure NLB 6 Release Neobox Wi. Fi Power Controller (Popcon box) Niche Intagrate RTU 3 G/4 G safe Router
Growth driving force 2. Capabilities for new products Focusing on our own R&D and investing 10% for revenue to R&D. We are releasing new products for years as below New products Launching self technology development Invest 10% for revenue High-end Two-way speed 100 G Upgrade Neobox 2. 0 Neomanager 2. 0 Neoplug 2. 0 Launched products Products Contents DDo. S 2011. 4 Q got the patent Smart Probe function mount on XN’s UTM for DDo. S Neoplug 2012. 1 Q 2012. 3 Q Dedicated products for the network security and Intelligent Load Balance of a small and a medium company Mobile VPN 2012. 4 Q Access in company server safely through the smart device by 3 G/4 G/wireless Popcon Box 2013. 1 Q Control the power of integrated products(UTM) remotely(AC&DC) Addition IPSec VPN Client. Safer use company server from outside PC accessing Secure NLB 6 Release Neobox Wi. Fi Power Controller (Popcon box) Niche Intagrate RTU 3 G/4 G safe Router
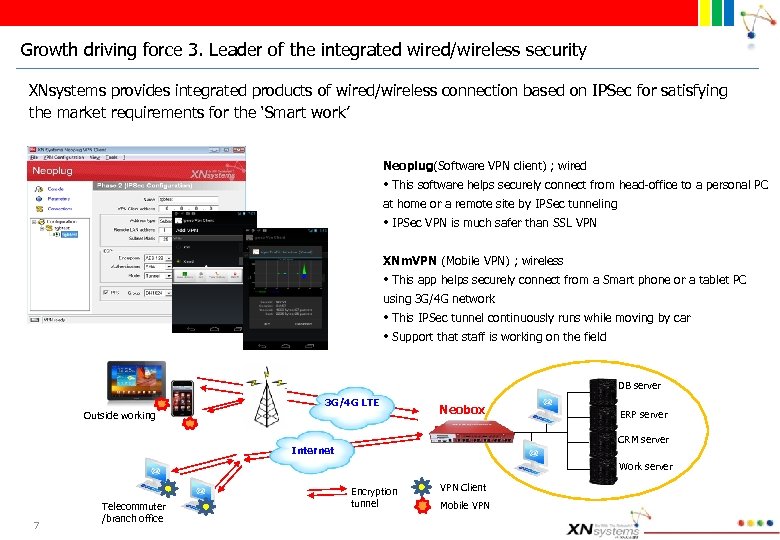 Growth driving force 3. Leader of the integrated wired/wireless security XNsystems provides integrated products of wired/wireless connection based on IPSec for satisfying the market requirements for the ‘Smart work’ Neoplug(Software VPN client) ; wired • This software helps securely connect from head-office to a personal PC at home or a remote site by IPSec tunneling • IPSec VPN is much safer than SSL VPN XNm. VPN (Mobile VPN) ; wireless • This app helps securely connect from a Smart phone or a tablet PC using 3 G/4 G network • This IPSec tunnel continuously runs while moving by car • Support that staff is working on the field DB server 3 G/4 G LTE Outside working Neobox ERP server CRM server Internet Work server 7 Telecommuter /branch office Encryption tunnel VPN Client Mobile VPN
Growth driving force 3. Leader of the integrated wired/wireless security XNsystems provides integrated products of wired/wireless connection based on IPSec for satisfying the market requirements for the ‘Smart work’ Neoplug(Software VPN client) ; wired • This software helps securely connect from head-office to a personal PC at home or a remote site by IPSec tunneling • IPSec VPN is much safer than SSL VPN XNm. VPN (Mobile VPN) ; wireless • This app helps securely connect from a Smart phone or a tablet PC using 3 G/4 G network • This IPSec tunnel continuously runs while moving by car • Support that staff is working on the field DB server 3 G/4 G LTE Outside working Neobox ERP server CRM server Internet Work server 7 Telecommuter /branch office Encryption tunnel VPN Client Mobile VPN
 Market Circumstance change of network security market XN’s action 8
Market Circumstance change of network security market XN’s action 8
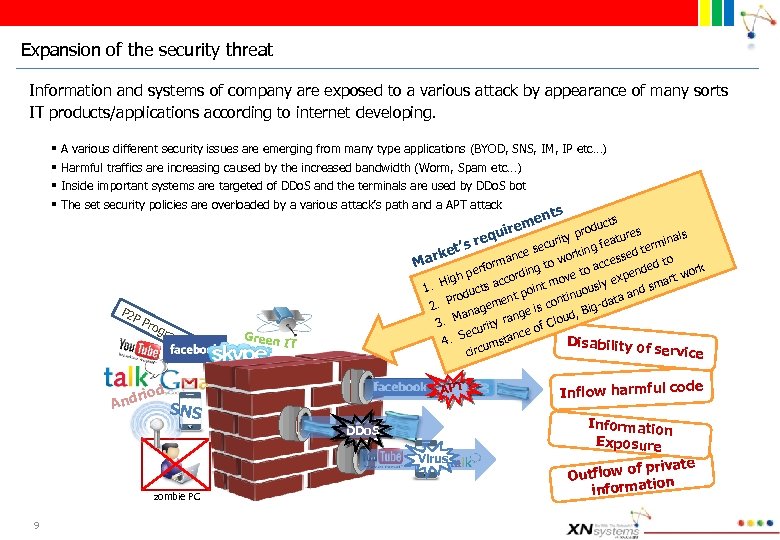 Expansion of the security threat Information and systems of company are exposed to a various attack by appearance of many sorts IT products/applications according to internet developing. § § A various different security issues are emerging from many type applications (BYOD, SNS, IM, IP etc…) Harmful traffics are increasing caused by the increased bandwidth (Worm, Spam etc…) Inside important systems are targeted of DDo. S and the terminals are used by DDo. S bot The set security policies are overloaded by a various attack’s path and a APT attack P 2 P Pro g ram d rio And Green ucts prod res y als re eatu urit f rmin ’s ec e ng et ce s ed t orki ark o man cess ow M or ac ed t k gt perf end wor e to rdin p art High ts acco int mov usly ex m 1. c o o nd s tinu rodu ment p ta a n a 2. P nage s co ig-d ge i a d, B n Clou 3. M urity ra c e of e c 4. S umstan Disability of service circ IT APT SNS DDo. S Virus zombie PC 9 s ent rem qui Inflow harmful code Information Exposure f private Outflow o n informatio
Expansion of the security threat Information and systems of company are exposed to a various attack by appearance of many sorts IT products/applications according to internet developing. § § A various different security issues are emerging from many type applications (BYOD, SNS, IM, IP etc…) Harmful traffics are increasing caused by the increased bandwidth (Worm, Spam etc…) Inside important systems are targeted of DDo. S and the terminals are used by DDo. S bot The set security policies are overloaded by a various attack’s path and a APT attack P 2 P Pro g ram d rio And Green ucts prod res y als re eatu urit f rmin ’s ec e ng et ce s ed t orki ark o man cess ow M or ac ed t k gt perf end wor e to rdin p art High ts acco int mov usly ex m 1. c o o nd s tinu rodu ment p ta a n a 2. P nage s co ig-d ge i a d, B n Clou 3. M urity ra c e of e c 4. S umstan Disability of service circ IT APT SNS DDo. S Virus zombie PC 9 s ent rem qui Inflow harmful code Information Exposure f private Outflow o n informatio
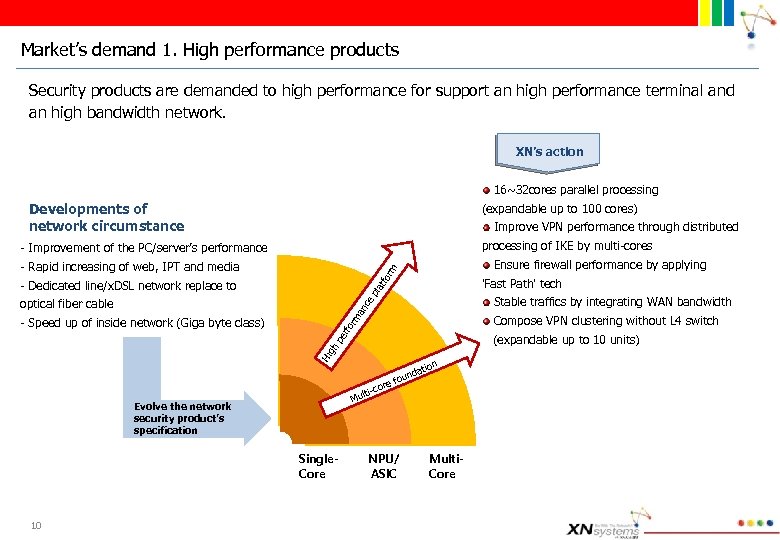 Market’s demand 1. High performance products Security products are demanded to high performance for support an high performance terminal and an high bandwidth network. XN’s action 16~32 cores parallel processing Developments of network circumstance Improve VPN performance through distributed processing of IKE by multi-cores rm Ensure firewall performance by applying pla tfo 'Fast Path' tech an ce Stable traffics by integrating WAN bandwidth pe rfo rm Compose VPN clustering without L 4 switch (expandable up to 10 units) Hi gh - Improvement of the PC/server’s performance - Rapid increasing of web, IPT and media - Dedicated line/x. DSL network replace to optical fiber cable - Speed up of inside network (Giga byte class) (expandable up to 100 cores) Evolve the network security product’s specification Single. Core 10 ion dat or lti-c Mu un e fo NPU/ ASIC Multi. Core
Market’s demand 1. High performance products Security products are demanded to high performance for support an high performance terminal and an high bandwidth network. XN’s action 16~32 cores parallel processing Developments of network circumstance Improve VPN performance through distributed processing of IKE by multi-cores rm Ensure firewall performance by applying pla tfo 'Fast Path' tech an ce Stable traffics by integrating WAN bandwidth pe rfo rm Compose VPN clustering without L 4 switch (expandable up to 10 units) Hi gh - Improvement of the PC/server’s performance - Rapid increasing of web, IPT and media - Dedicated line/x. DSL network replace to optical fiber cable - Speed up of inside network (Giga byte class) (expandable up to 100 cores) Evolve the network security product’s specification Single. Core 10 ion dat or lti-c Mu un e fo NPU/ ASIC Multi. Core
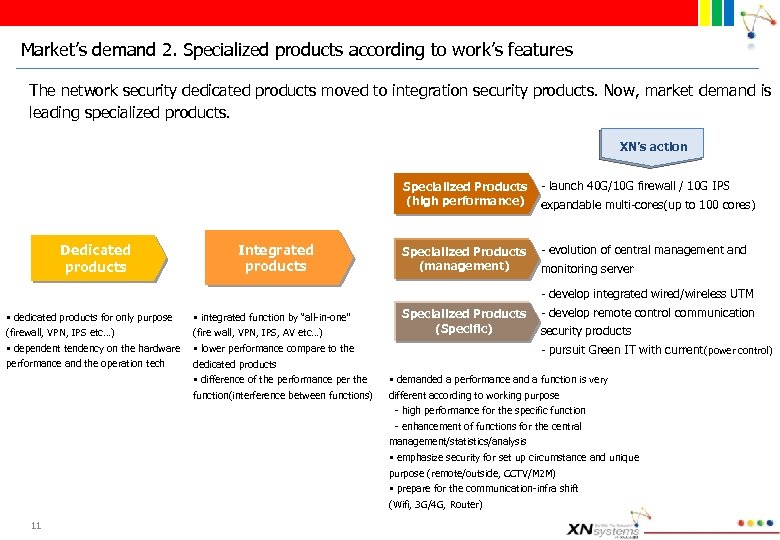 Market’s demand 2. Specialized products according to work’s features The network security dedicated products moved to integration security products. Now, market demand is leading specialized products. XN’s action Specialized Products (high performance) Dedicated products Integrated products - launch 40 G/10 G firewall / 10 G IPS Specialized Products (management) - evolution of central management and expandable multi-cores(up to 100 cores) monitoring server - develop integrated wired/wireless UTM § dedicated products for only purpose (firewall, VPN, IPS etc…) § dependent tendency on the hardware performance and the operation tech 11 § integrated function by “all-in-one” (fire wall, VPN, IPS, AV etc…) § lower performance compare to the dedicated products § difference of the performance per the function(interference between functions) Specialized Products (Specific) - develop remote control communication security products - pursuit Green IT with current (power control) § demanded a performance and a function is very different according to working purpose - high performance for the specific function - enhancement of functions for the central management/statistics/analysis § emphasize security for set up circumstance and unique purpose (remote/outside, CCTV/M 2 M) § prepare for the communication-infra shift (Wifi, 3 G/4 G, Router)
Market’s demand 2. Specialized products according to work’s features The network security dedicated products moved to integration security products. Now, market demand is leading specialized products. XN’s action Specialized Products (high performance) Dedicated products Integrated products - launch 40 G/10 G firewall / 10 G IPS Specialized Products (management) - evolution of central management and expandable multi-cores(up to 100 cores) monitoring server - develop integrated wired/wireless UTM § dedicated products for only purpose (firewall, VPN, IPS etc…) § dependent tendency on the hardware performance and the operation tech 11 § integrated function by “all-in-one” (fire wall, VPN, IPS, AV etc…) § lower performance compare to the dedicated products § difference of the performance per the function(interference between functions) Specialized Products (Specific) - develop remote control communication security products - pursuit Green IT with current (power control) § demanded a performance and a function is very different according to working purpose - high performance for the specific function - enhancement of functions for the central management/statistics/analysis § emphasize security for set up circumstance and unique purpose (remote/outside, CCTV/M 2 M) § prepare for the communication-infra shift (Wifi, 3 G/4 G, Router)
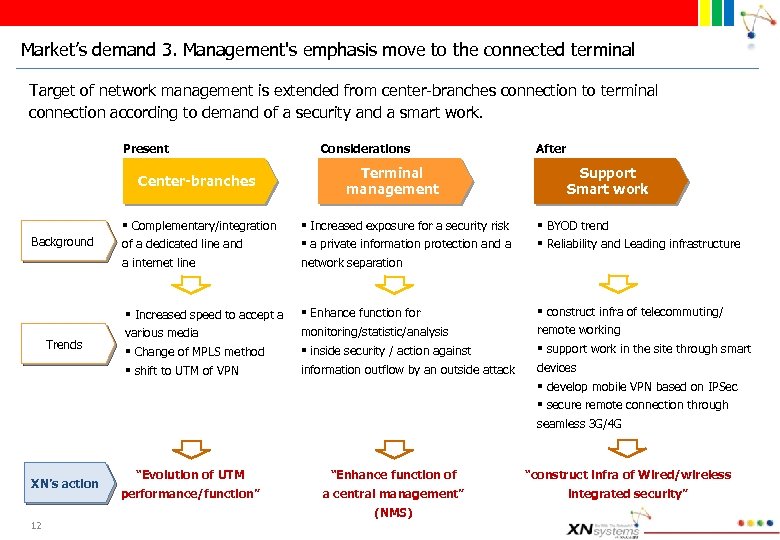 Market’s demand 3. Management's emphasis move to the connected terminal Target of network management is extended from center-branches connection to terminal connection according to demand of a security and a smart work. Present Center-branches Background Trends XN’s action 12 Considerations Terminal management After Support Smart work § Complementary/integration of a dedicated line and a internet line § Increased exposure for a security risk § a private information protection and a network separation § BYOD trend § Reliability and Leading infrastructure § Increased speed to accept a various media § Change of MPLS method § shift to UTM of VPN § Enhance function for monitoring/statistic/analysis § inside security / action against information outflow by an outside attack § construct infra of telecommuting/ remote working § support work in the site through smart devices § develop mobile VPN based on IPSec § secure remote connection through seamless 3 G/4 G “Evolution of UTM “Enhance function of “construct infra of Wired/wireless performance/function” a central management” integrated security” (NMS)
Market’s demand 3. Management's emphasis move to the connected terminal Target of network management is extended from center-branches connection to terminal connection according to demand of a security and a smart work. Present Center-branches Background Trends XN’s action 12 Considerations Terminal management After Support Smart work § Complementary/integration of a dedicated line and a internet line § Increased exposure for a security risk § a private information protection and a network separation § BYOD trend § Reliability and Leading infrastructure § Increased speed to accept a various media § Change of MPLS method § shift to UTM of VPN § Enhance function for monitoring/statistic/analysis § inside security / action against information outflow by an outside attack § construct infra of telecommuting/ remote working § support work in the site through smart devices § develop mobile VPN based on IPSec § secure remote connection through seamless 3 G/4 G “Evolution of UTM “Enhance function of “construct infra of Wired/wireless performance/function” a central management” integrated security” (NMS)
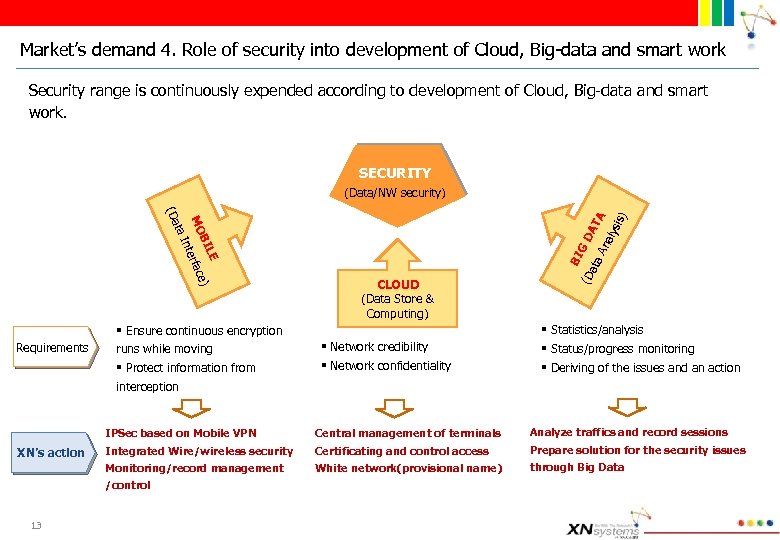 Market’s demand 4. Role of security into development of Cloud, Big-data and smart work Security range is continuously expended according to development of Cloud, Big-data and smart work. SECURITY (Data/NW security) BI G ata DAT A An aly sis ) § Network credibility § Network confidentiality (D E BIL e) MO erfac nt ta I (Da Requirements § Ensure continuous encryption runs while moving § Protect information from interception CLOUD (Data Store & Computing) § Statistics/analysis § Status/progress monitoring § Deriving of the issues and an action IPSec based on Mobile VPN Analyze traffics and record sessions Integrated Wire/wireless security Certificating and control access Prepare solution for the security issues Monitoring/record management XN’s action Central management of terminals White network(provisional name) through Big Data /control 13
Market’s demand 4. Role of security into development of Cloud, Big-data and smart work Security range is continuously expended according to development of Cloud, Big-data and smart work. SECURITY (Data/NW security) BI G ata DAT A An aly sis ) § Network credibility § Network confidentiality (D E BIL e) MO erfac nt ta I (Da Requirements § Ensure continuous encryption runs while moving § Protect information from interception CLOUD (Data Store & Computing) § Statistics/analysis § Status/progress monitoring § Deriving of the issues and an action IPSec based on Mobile VPN Analyze traffics and record sessions Integrated Wire/wireless security Certificating and control access Prepare solution for the security issues Monitoring/record management XN’s action Central management of terminals White network(provisional name) through Big Data /control 13
 Products XN’s differentiated points - Engine - Connection - Wireless UTM - Management - Analysis Products line up 14
Products XN’s differentiated points - Engine - Connection - Wireless UTM - Management - Analysis Products line up 14
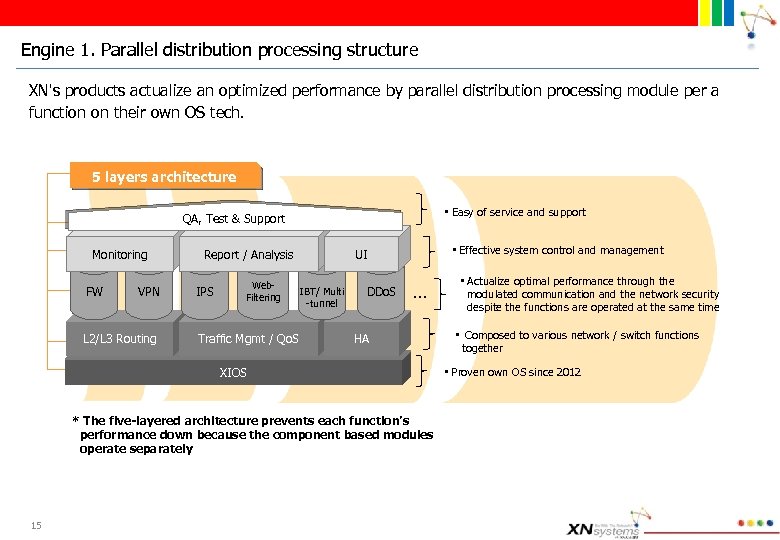 Engine 1. Parallel distribution processing structure XN's products actualize an optimized performance by parallel distribution processing module per a function on their own OS tech. 5 layers architecture • Easy of service and support QA, Test & Support Monitoring FW VPN L 2/L 3 Routing Report / Analysis IPS Web. Filtering Traffic Mgmt / Qo. S • Effective system control and management UI IBT/ Multi -tunnel DDo. S … HA XIOS * The five-layered architecture prevents each function’s performance down because the component based modules operate separately 15 • Actualize optimal performance through the modulated communication and the network security despite the functions are operated at the same time • Composed to various network / switch functions together • Proven own OS since 2012
Engine 1. Parallel distribution processing structure XN's products actualize an optimized performance by parallel distribution processing module per a function on their own OS tech. 5 layers architecture • Easy of service and support QA, Test & Support Monitoring FW VPN L 2/L 3 Routing Report / Analysis IPS Web. Filtering Traffic Mgmt / Qo. S • Effective system control and management UI IBT/ Multi -tunnel DDo. S … HA XIOS * The five-layered architecture prevents each function’s performance down because the component based modules operate separately 15 • Actualize optimal performance through the modulated communication and the network security despite the functions are operated at the same time • Composed to various network / switch functions together • Proven own OS since 2012
 Engine 2. Clustering of Block-building composed Clustering composition is interlocked by Block-building method without a L 4 switch when the center's security device is extended and the branch‘s security devices are connected by NMS's automatic setting system. After (XN) Before NMS R L 2 L 2 L 4 C 1 C 2 L 2 L 2 2 L 4 C 1 C 3 L 4 NMS R L 4 C 2 L 2 R C 3 … L 2 R 3 B 1 … Bn § Extension of Load Balancing/Clustering is a difficult structure to extend without L 4 switch 16 C 10 1 B 1 … Bn 1. easy extension without L 4 switch 2. automatic setting system of the branches 3. all devices of the center support Active-Active function to the branch's devices
Engine 2. Clustering of Block-building composed Clustering composition is interlocked by Block-building method without a L 4 switch when the center's security device is extended and the branch‘s security devices are connected by NMS's automatic setting system. After (XN) Before NMS R L 2 L 2 L 4 C 1 C 2 L 2 L 2 2 L 4 C 1 C 3 L 4 NMS R L 4 C 2 L 2 R C 3 … L 2 R 3 B 1 … Bn § Extension of Load Balancing/Clustering is a difficult structure to extend without L 4 switch 16 C 10 1 B 1 … Bn 1. easy extension without L 4 switch 2. automatic setting system of the branches 3. all devices of the center support Active-Active function to the branch's devices
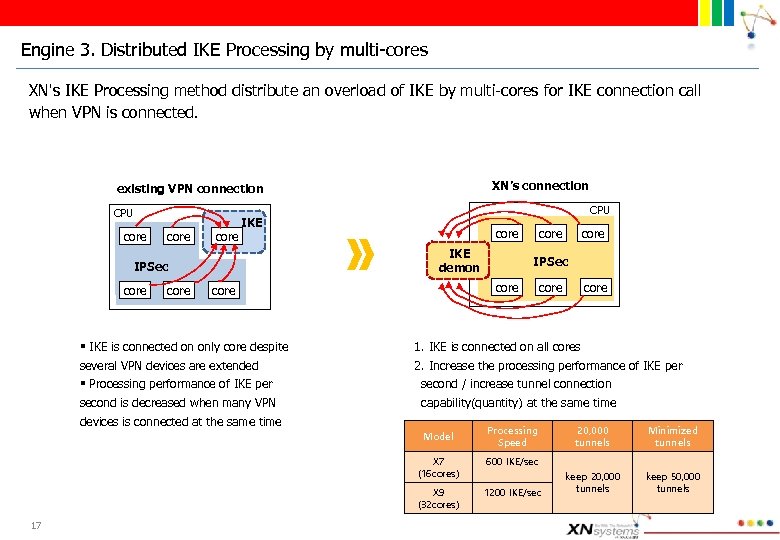 Engine 3. Distributed IKE Processing by multi-cores XN's IKE Processing method distribute an overload of IKE by multi-cores for IKE connection call when VPN is connected. XN’s connection existing VPN connection CPU core core IKE demon IPSec core CPU IKE core 1. IKE is connected on all cores 2. Increase the processing performance of IKE per second / increase tunnel connection capability(quantity) at the same time Model Processing Speed X 7 (16 cores) 1200 IKE/sec 20, 000 tunnels Minimized tunnels keep 20, 000 tunnels keep 50, 000 tunnels 600 IKE/sec X 9 (32 cores) 17 core IPSec core § IKE is connected on only core despite several VPN devices are extended § Processing performance of IKE per second is decreased when many VPN devices is connected at the same time core
Engine 3. Distributed IKE Processing by multi-cores XN's IKE Processing method distribute an overload of IKE by multi-cores for IKE connection call when VPN is connected. XN’s connection existing VPN connection CPU core core IKE demon IPSec core CPU IKE core 1. IKE is connected on all cores 2. Increase the processing performance of IKE per second / increase tunnel connection capability(quantity) at the same time Model Processing Speed X 7 (16 cores) 1200 IKE/sec 20, 000 tunnels Minimized tunnels keep 20, 000 tunnels keep 50, 000 tunnels 600 IKE/sec X 9 (32 cores) 17 core IPSec core § IKE is connected on only core despite several VPN devices are extended § Processing performance of IKE per second is decreased when many VPN devices is connected at the same time core
 Engine 4. Detection and Protection for DDo. S Smart probe function in UTM(Neobox) protect customer network / detect DDo. S as XN's own technology in stead of an expensive dedicated device. Smart Probe function • Improve a monitoring functions of sessions and a detection by applying set-values of sessions per site with control of PPS/BPS (registered patent) • XN's UTM(Neobox) include Smart Probe function detect DDo. S also prevent the DDo. S attack (include firewall/VPN/IPS functions) • This product prevent a failure of router/high cost In-line device caused by the mass-capacity attack in advance. It is a efficient compare to high-cost dedicated In-line DDo. S devices (DDo. S monitoring) • Provides monitoring/reporting 18
Engine 4. Detection and Protection for DDo. S Smart probe function in UTM(Neobox) protect customer network / detect DDo. S as XN's own technology in stead of an expensive dedicated device. Smart Probe function • Improve a monitoring functions of sessions and a detection by applying set-values of sessions per site with control of PPS/BPS (registered patent) • XN's UTM(Neobox) include Smart Probe function detect DDo. S also prevent the DDo. S attack (include firewall/VPN/IPS functions) • This product prevent a failure of router/high cost In-line device caused by the mass-capacity attack in advance. It is a efficient compare to high-cost dedicated In-line DDo. S devices (DDo. S monitoring) • Provides monitoring/reporting 18
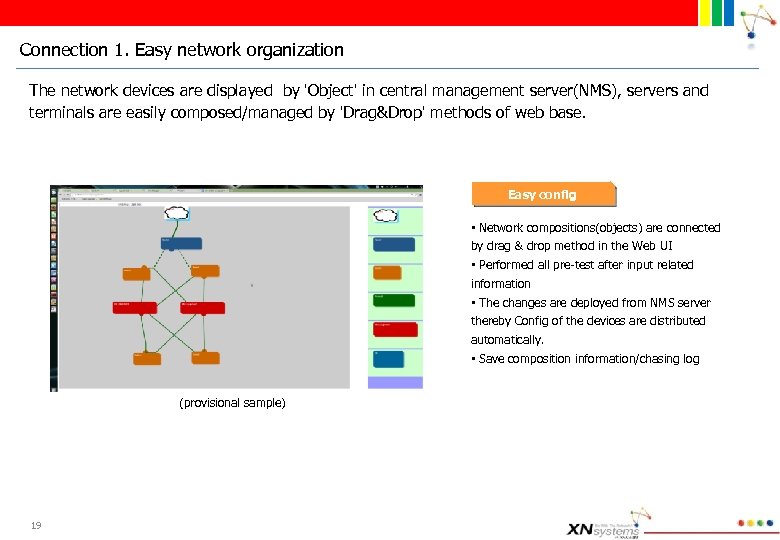 Connection 1. Easy network organization The network devices are displayed by 'Object' in central management server(NMS), servers and terminals are easily composed/managed by 'Drag&Drop' methods of web base. Easy config • Network compositions(objects) are connected by drag & drop method in the Web UI • Performed all pre-test after input related information • The changes are deployed from NMS server thereby Config of the devices are distributed automatically. • Save composition information/chasing log (provisional sample) 19
Connection 1. Easy network organization The network devices are displayed by 'Object' in central management server(NMS), servers and terminals are easily composed/managed by 'Drag&Drop' methods of web base. Easy config • Network compositions(objects) are connected by drag & drop method in the Web UI • Performed all pre-test after input related information • The changes are deployed from NMS server thereby Config of the devices are distributed automatically. • Save composition information/chasing log (provisional sample) 19
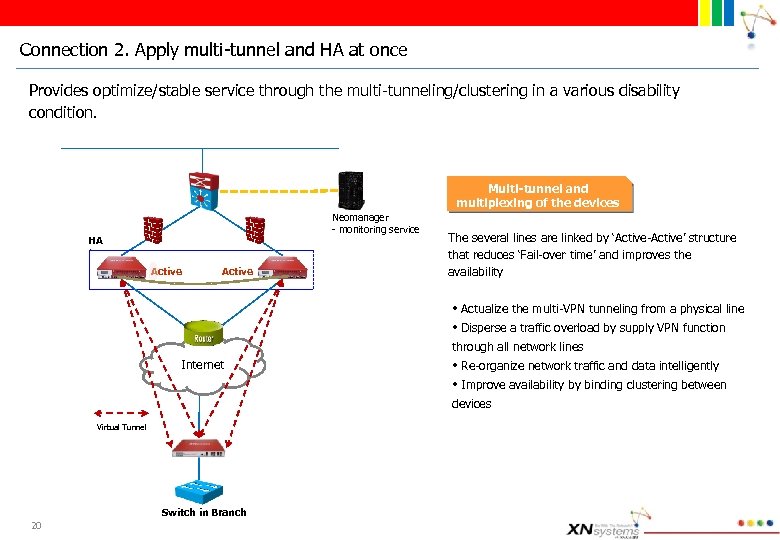 Connection 2. Apply multi-tunnel and HA at once Provides optimize/stable service through the multi-tunneling/clustering in a various disability condition. Multi-tunnel and multiplexing of the devices Neomanager - monitoring service HA Active The several lines are linked by ‘Active-Active’ structure that reduces ‘Fail-over time’ and improves the availability • Actualize the multi-VPN tunneling from a physical line • Disperse a traffic overload by supply VPN function through all network lines Internet • Re-organize network traffic and data intelligently • Improve availability by binding clustering between devices Virtual Tunnel Switch in Branch 20
Connection 2. Apply multi-tunnel and HA at once Provides optimize/stable service through the multi-tunneling/clustering in a various disability condition. Multi-tunnel and multiplexing of the devices Neomanager - monitoring service HA Active The several lines are linked by ‘Active-Active’ structure that reduces ‘Fail-over time’ and improves the availability • Actualize the multi-VPN tunneling from a physical line • Disperse a traffic overload by supply VPN function through all network lines Internet • Re-organize network traffic and data intelligently • Improve availability by binding clustering between devices Virtual Tunnel Switch in Branch 20
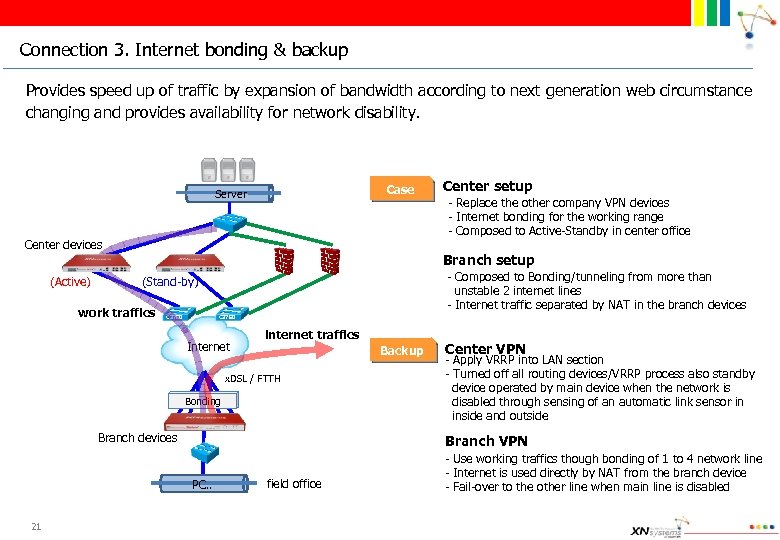 Connection 3. Internet bonding & backup Provides speed up of traffic by expansion of bandwidth according to next generation web circumstance changing and provides availability for network disability. Case Server Center devices (Active) - Replace the other company VPN devices - Internet bonding for the working range - Composed to Active-Standby in center office Branch setup - Composed to Bonding/tunneling from more than unstable 2 internet lines - Internet traffic separated by NAT in the branch devices (Stand-by) work traffics C 3750 Internet internet traffics Backup x. DSL / FTTH Bonding Branch devices Center VPN - Apply VRRP into LAN section - Turned off all routing devices/VRRP process also standby device operated by main device when the network is disabled through sensing of an automatic link sensor in inside and outside Branch VPN PC. . 21 Center setup field office - Use working traffics though bonding of 1 to 4 network line - Internet is used directly by NAT from the branch device - Fail-over to the other line when main line is disabled
Connection 3. Internet bonding & backup Provides speed up of traffic by expansion of bandwidth according to next generation web circumstance changing and provides availability for network disability. Case Server Center devices (Active) - Replace the other company VPN devices - Internet bonding for the working range - Composed to Active-Standby in center office Branch setup - Composed to Bonding/tunneling from more than unstable 2 internet lines - Internet traffic separated by NAT in the branch devices (Stand-by) work traffics C 3750 Internet internet traffics Backup x. DSL / FTTH Bonding Branch devices Center VPN - Apply VRRP into LAN section - Turned off all routing devices/VRRP process also standby device operated by main device when the network is disabled through sensing of an automatic link sensor in inside and outside Branch VPN PC. . 21 Center setup field office - Use working traffics though bonding of 1 to 4 network line - Internet is used directly by NAT from the branch device - Fail-over to the other line when main line is disabled
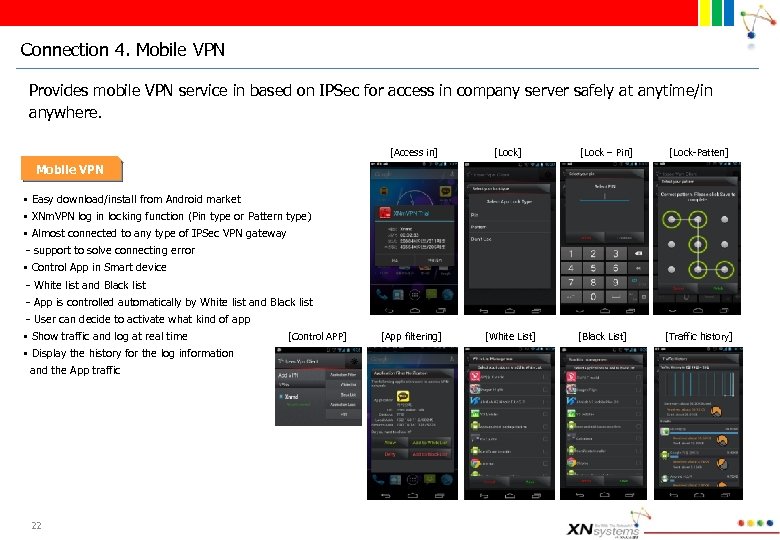 Connection 4. Mobile VPN Provides mobile VPN service in based on IPSec for access in company server safely at anytime/in anywhere. [Access in] [Lock] [App filtering] [White List] [Lock – Pin] [Lock-Patten] Mobile VPN § Easy download/install from Android market § XNm. VPN log in locking function (Pin type or Pattern type) § Almost connected to any type of IPSec VPN gateway - support to solve connecting error § Control App in Smart device - White list and Black list - App is controlled automatically by White list and Black list - User can decide to activate what kind of app § Show traffic and log at real time [Control APP] § Display the history for the log information and the App traffic 22 [Black List] [Traffic history]
Connection 4. Mobile VPN Provides mobile VPN service in based on IPSec for access in company server safely at anytime/in anywhere. [Access in] [Lock] [App filtering] [White List] [Lock – Pin] [Lock-Patten] Mobile VPN § Easy download/install from Android market § XNm. VPN log in locking function (Pin type or Pattern type) § Almost connected to any type of IPSec VPN gateway - support to solve connecting error § Control App in Smart device - White list and Black list - App is controlled automatically by White list and Black list - User can decide to activate what kind of app § Show traffic and log at real time [Control APP] § Display the history for the log information and the App traffic 22 [Black List] [Traffic history]
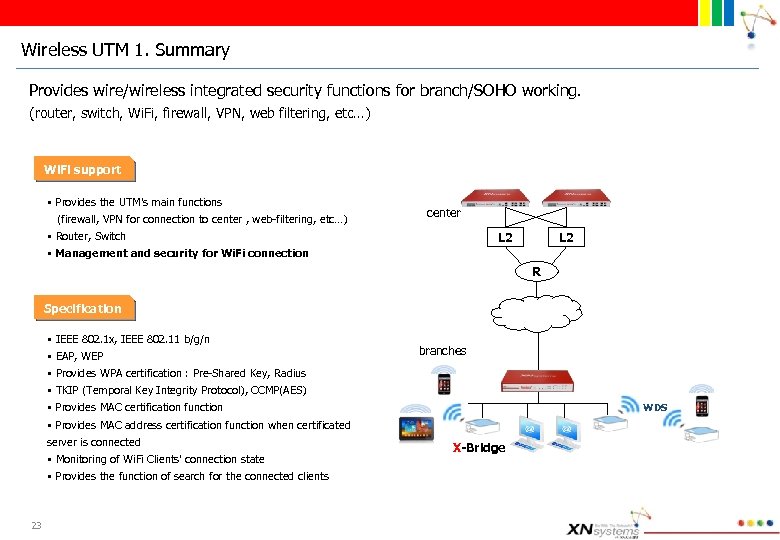 Wireless UTM 1. Summary Provides wire/wireless integrated security functions for branch/SOHO working. (router, switch, Wi. Fi, firewall, VPN, web filtering, etc…) Wi. Fi support § Provides the UTM's main functions (firewall, VPN for connection to center , web-filtering, etc…) § Router, Switch § Management and security for Wi. Fi connection center L 2 R Specification § IEEE 802. 1 x, IEEE 802. 11 b/g/n § EAP, WEP § Provides WPA certification : Pre-Shared Key, Radius § TKIP (Temporal Key Integrity Protocol), CCMP(AES) § Provides MAC certification function § Provides MAC address certification function when certificated server is connected § Monitoring of Wi. Fi Clients’ connection state § Provides the function of search for the connected clients 23 branches WDS X-Bridge
Wireless UTM 1. Summary Provides wire/wireless integrated security functions for branch/SOHO working. (router, switch, Wi. Fi, firewall, VPN, web filtering, etc…) Wi. Fi support § Provides the UTM's main functions (firewall, VPN for connection to center , web-filtering, etc…) § Router, Switch § Management and security for Wi. Fi connection center L 2 R Specification § IEEE 802. 1 x, IEEE 802. 11 b/g/n § EAP, WEP § Provides WPA certification : Pre-Shared Key, Radius § TKIP (Temporal Key Integrity Protocol), CCMP(AES) § Provides MAC certification function § Provides MAC address certification function when certificated server is connected § Monitoring of Wi. Fi Clients’ connection state § Provides the function of search for the connected clients 23 branches WDS X-Bridge
 Wireless UTM 2. Connection device for wireless security Provides a security access and a management condition same as an wired network condition through XN's own the wireless security connection devices(X-bridge ; provisional name) RS 232 Optional UART 2 SDRAM 16 MB SPI Flash 4 MB HW spec 32 Bit BUS CPU RT 3052 MIPs 384 MHz 10/100 WAN /LAN x 1 USB 2. 0 BUS Wi. Fi 2. 4 GHz Mi. Mo 2 T 2 R 24 USB 2. 0 Host Popcon Box Optional RJ 45 WAN LAN • CPU: MIPs 384 MHz RT 3052 • DRAM : SDRAM 16 MB x 2 , 32 Bit BUS • FLASH : SPI FLASH 4 MB • Ethernet : 10/100 LAN/WAN X 1 • WIFI : 2. 4 GHz b/g/n Mi. Mo 300 Mbps • outside interface : USB 2. 0 HOST • Optional : RS 232 x 1 port • Popcon Optional connect USB or RS 232 • IEEE 802. 11 b, g, n 2 T 2 R 300 Mbps • 2. 4 GHz Wi. Fi Mi. Mo
Wireless UTM 2. Connection device for wireless security Provides a security access and a management condition same as an wired network condition through XN's own the wireless security connection devices(X-bridge ; provisional name) RS 232 Optional UART 2 SDRAM 16 MB SPI Flash 4 MB HW spec 32 Bit BUS CPU RT 3052 MIPs 384 MHz 10/100 WAN /LAN x 1 USB 2. 0 BUS Wi. Fi 2. 4 GHz Mi. Mo 2 T 2 R 24 USB 2. 0 Host Popcon Box Optional RJ 45 WAN LAN • CPU: MIPs 384 MHz RT 3052 • DRAM : SDRAM 16 MB x 2 , 32 Bit BUS • FLASH : SPI FLASH 4 MB • Ethernet : 10/100 LAN/WAN X 1 • WIFI : 2. 4 GHz b/g/n Mi. Mo 300 Mbps • outside interface : USB 2. 0 HOST • Optional : RS 232 x 1 port • Popcon Optional connect USB or RS 232 • IEEE 802. 11 b, g, n 2 T 2 R 300 Mbps • 2. 4 GHz Wi. Fi Mi. Mo
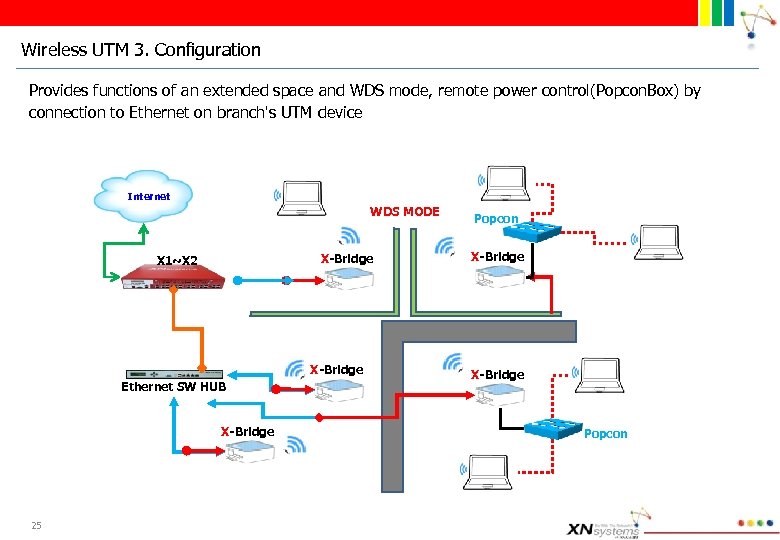 Wireless UTM 3. Configuration Provides functions of an extended space and WDS mode, remote power control(Popcon. Box) by connection to Ethernet on branch's UTM device Internet WDS MODE X-Bridge X 1~X 2 X-Bridge Ethernet SW HUB X-Bridge 25 Popcon X-Bridge Popcon
Wireless UTM 3. Configuration Provides functions of an extended space and WDS mode, remote power control(Popcon. Box) by connection to Ethernet on branch's UTM device Internet WDS MODE X-Bridge X 1~X 2 X-Bridge Ethernet SW HUB X-Bridge 25 Popcon X-Bridge Popcon
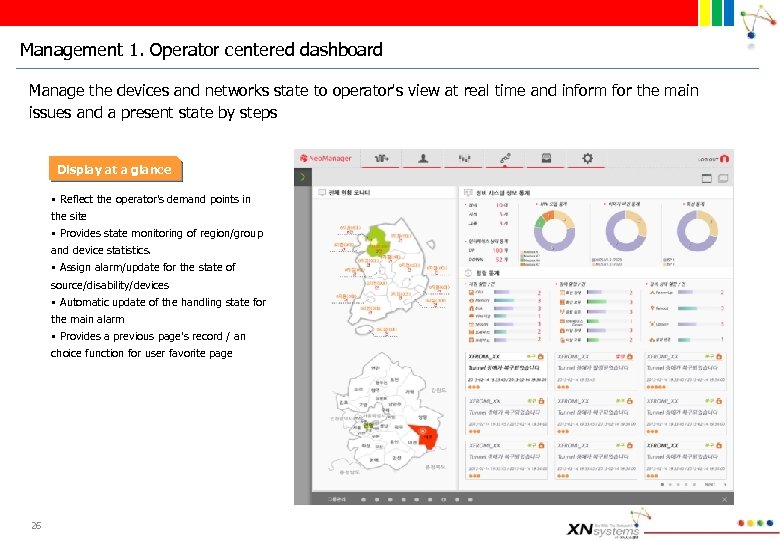 Management 1. Operator centered dashboard Manage the devices and networks state to operator's view at real time and inform for the main issues and a present state by steps Display at a glance § Reflect the operator's demand points in the site § Provides state monitoring of region/group and device statistics. § Assign alarm/update for the state of source/disability/devices § Automatic update of the handling state for the main alarm § Provides a previous page's record / an choice function for user favorite page 26
Management 1. Operator centered dashboard Manage the devices and networks state to operator's view at real time and inform for the main issues and a present state by steps Display at a glance § Reflect the operator's demand points in the site § Provides state monitoring of region/group and device statistics. § Assign alarm/update for the state of source/disability/devices § Automatic update of the handling state for the main alarm § Provides a previous page's record / an choice function for user favorite page 26
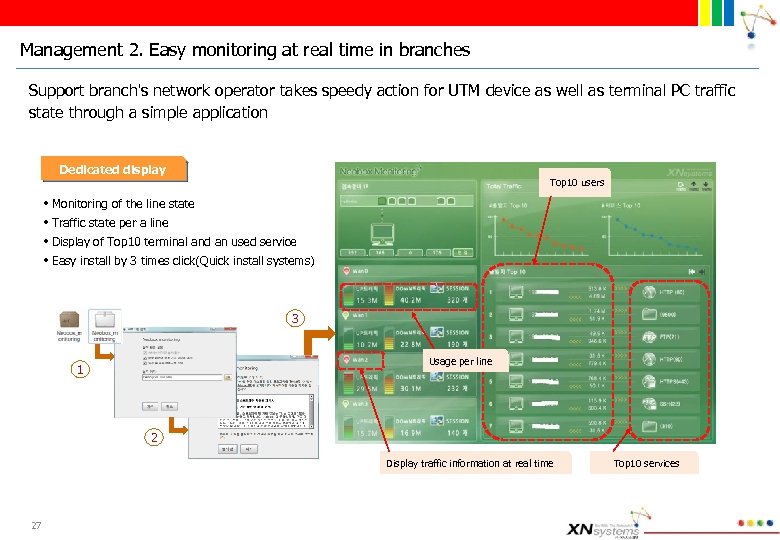 Management 2. Easy monitoring at real time in branches Support branch's network operator takes speedy action for UTM device as well as terminal PC traffic state through a simple application Dedicated display Top 10 users • Monitoring of the line state • Traffic state per a line • Display of Top 10 terminal and an used service • Easy install by 3 times click(Quick install systems) 3 Usage per line 1 2 Display traffic information at real time 27 Top 10 services
Management 2. Easy monitoring at real time in branches Support branch's network operator takes speedy action for UTM device as well as terminal PC traffic state through a simple application Dedicated display Top 10 users • Monitoring of the line state • Traffic state per a line • Display of Top 10 terminal and an used service • Easy install by 3 times click(Quick install systems) 3 Usage per line 1 2 Display traffic information at real time 27 Top 10 services
 Management 3. Enhance the connected terminals management and the branches devices Limit access for the lost/unlicensed devices and perceive the unusual traffics by monitoring traffics on the center devices as well as the branch devices Powerful devices management • Display the branches' network line and the devices • Display the log generating per session and the traffic amount(per total/group/device/terminal) • Provides Top 10 information of traffics per start point address (perceive unusual traffics) • Interlocking to SNMP for VPN tunnel/state information • Lost prevention function for the branch's devices (alarm and limit VPN functions) 28
Management 3. Enhance the connected terminals management and the branches devices Limit access for the lost/unlicensed devices and perceive the unusual traffics by monitoring traffics on the center devices as well as the branch devices Powerful devices management • Display the branches' network line and the devices • Display the log generating per session and the traffic amount(per total/group/device/terminal) • Provides Top 10 information of traffics per start point address (perceive unusual traffics) • Interlocking to SNMP for VPN tunnel/state information • Lost prevention function for the branch's devices (alarm and limit VPN functions) 28
 Management 4. Evolved management for batch distribution and certification Easy distribution after set a firewall policy/NAT rule as well as easy management for a certification/a configuration. Preferences through an interactive window • Processing firewall policy / NAT rules / VPN set up at once • Firmware/DB update & patch • Set up devices and configuration by remote (Web based) • Support CA server - Automatic Issued from Neomanager by using SCEP - Interlocked to CA server of the other company • Provides alarm function when the certification is expired 29
Management 4. Evolved management for batch distribution and certification Easy distribution after set a firewall policy/NAT rule as well as easy management for a certification/a configuration. Preferences through an interactive window • Processing firewall policy / NAT rules / VPN set up at once • Firmware/DB update & patch • Set up devices and configuration by remote (Web based) • Support CA server - Automatic Issued from Neomanager by using SCEP - Interlocked to CA server of the other company • Provides alarm function when the certification is expired 29
 Management 5. Management through remote power control Power control of branches through the remote control device or, takes action through console connection. Popcon. Box • Support a various management mode (management reservation/log/per device) • Provides remote power control/auto power control through connecting of web, SSH and telnet • Duplex of power supply and Bypass (support AC and DC up to 8 devices) • Operation of connected devices are maintained when the remote power control is disabled/rebooting • Integrated management in NMS Popcon. Tab • Power control in NMS or Web • Power control by a dedicated app in the personal computer • Maintain a power for 8 hours when power is failure (charge by USB) • Support AC, DC (4 devices or 8 devices) • Auto power down / auto power recovery for an over-current • Provides real time sensing function for an output power control 30
Management 5. Management through remote power control Power control of branches through the remote control device or, takes action through console connection. Popcon. Box • Support a various management mode (management reservation/log/per device) • Provides remote power control/auto power control through connecting of web, SSH and telnet • Duplex of power supply and Bypass (support AC and DC up to 8 devices) • Operation of connected devices are maintained when the remote power control is disabled/rebooting • Integrated management in NMS Popcon. Tab • Power control in NMS or Web • Power control by a dedicated app in the personal computer • Maintain a power for 8 hours when power is failure (charge by USB) • Support AC, DC (4 devices or 8 devices) • Auto power down / auto power recovery for an over-current • Provides real time sensing function for an output power control 30
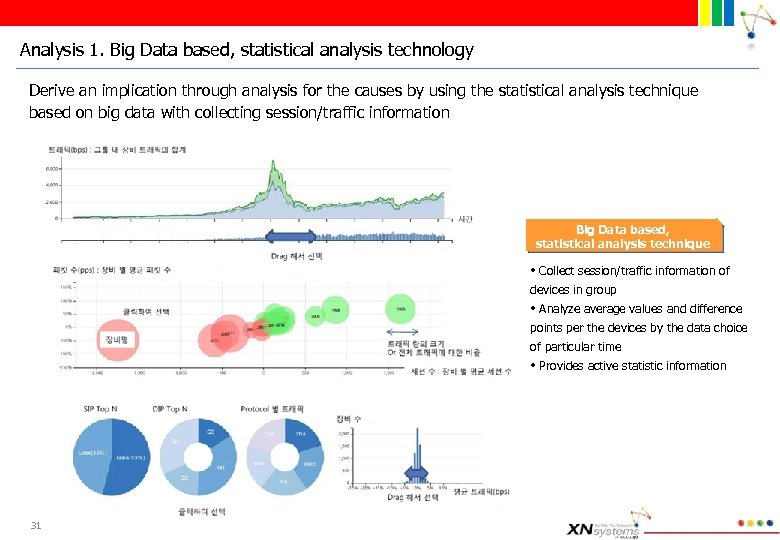 Analysis 1. Big Data based, statistical analysis technology Derive an implication through analysis for the causes by using the statistical analysis technique based on big data with collecting session/traffic information Big Data based, statistical analysis technique • Collect session/traffic information of devices in group • Analyze average values and difference points per the devices by the data choice of particular time • Provides active statistic information 31
Analysis 1. Big Data based, statistical analysis technology Derive an implication through analysis for the causes by using the statistical analysis technique based on big data with collecting session/traffic information Big Data based, statistical analysis technique • Collect session/traffic information of devices in group • Analyze average values and difference points per the devices by the data choice of particular time • Provides active statistic information 31
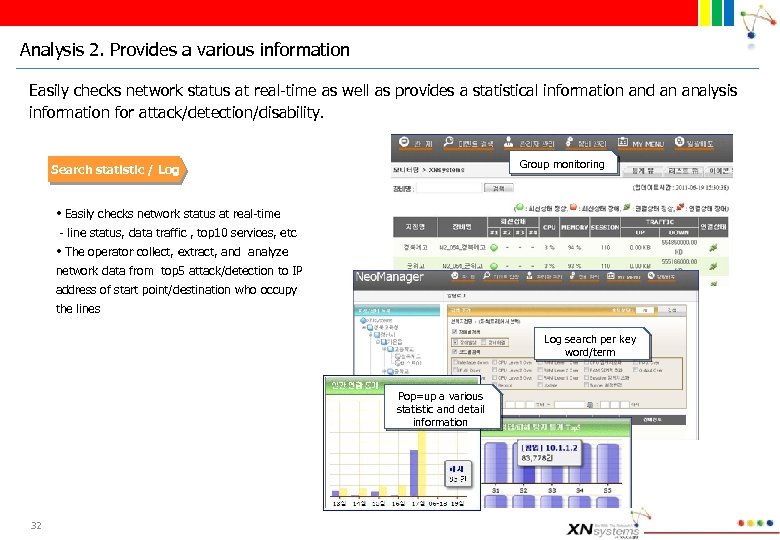 Analysis 2. Provides a various information Easily checks network status at real-time as well as provides a statistical information and an analysis information for attack/detection/disability. Group monitoring Search statistic / Log • Easily checks network status at real-time - line status, data traffic , top 10 services, etc • The operator collect, extract, and analyze network data from top 5 attack/detection to IP address of start point/destination who occupy the lines Log search per key word/term Pop=up a various statistic and detail information 32
Analysis 2. Provides a various information Easily checks network status at real-time as well as provides a statistical information and an analysis information for attack/detection/disability. Group monitoring Search statistic / Log • Easily checks network status at real-time - line status, data traffic , top 10 services, etc • The operator collect, extract, and analyze network data from top 5 attack/detection to IP address of start point/destination who occupy the lines Log search per key word/term Pop=up a various statistic and detail information 32
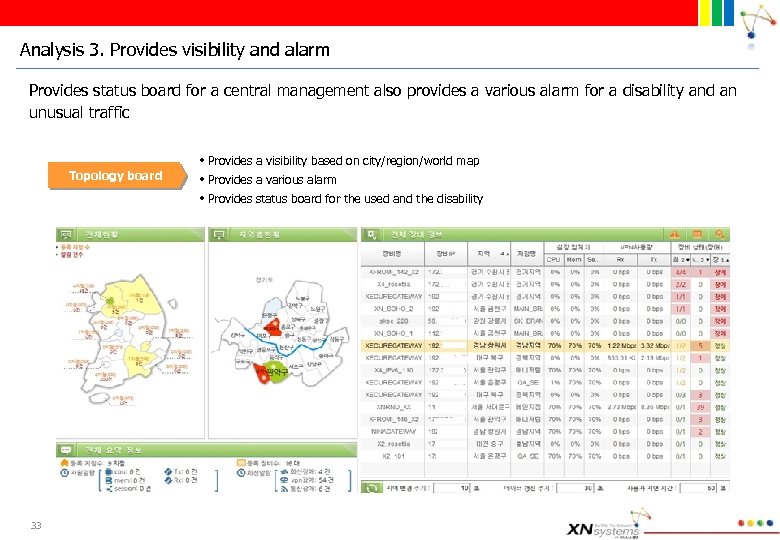 Analysis 3. Provides visibility and alarm Provides status board for a central management also provides a various alarm for a disability and an unusual traffic Topology board 33 • Provides a visibility based on city/region/world map • Provides a various alarm • Provides status board for the used and the disability
Analysis 3. Provides visibility and alarm Provides status board for a central management also provides a various alarm for a disability and an unusual traffic Topology board 33 • Provides a visibility based on city/region/world map • Provides a various alarm • Provides status board for the used and the disability
 Products Line-up : Neobox Series Enterprise/Center Medium SOHO/Branches Neobox series Model X 1 X 2 X 4 X 7 X 9 Client(standard) 50 200 1, 000+ 2, 000+ NPU core / Mem 1 Core / 512 MB 2 Core / 1 GB 4 Core / 4 G 16 Core / 8 GB 32 Core / 16 GB Concurrent Session 250, 000 600, 000 1, 500, 000+ 4, 700, 000+ Firewall Throughput* 1 G / 420 M 2 G / 900 M 4 G / 2. 5 G 13 G / 8 G 40 G IPS Throughput* 20 M / 11 M 260 M / 170 M 540 M / 380 M 2. 7 G / 2. 1 G 10 G VPN Throughput* 200 M / 90 M 400 M / 180 M 1 G / 460 M 3. 7 G / 1. 8 G 10 G Function VPN, Firewall, UTM, IDS/IPS, URL Filtering, Qo. S, Network Load Balancer, DDo. S Detect & Report * Throughput (one way) : Max(1400 Byte) / 512 Byte 34
Products Line-up : Neobox Series Enterprise/Center Medium SOHO/Branches Neobox series Model X 1 X 2 X 4 X 7 X 9 Client(standard) 50 200 1, 000+ 2, 000+ NPU core / Mem 1 Core / 512 MB 2 Core / 1 GB 4 Core / 4 G 16 Core / 8 GB 32 Core / 16 GB Concurrent Session 250, 000 600, 000 1, 500, 000+ 4, 700, 000+ Firewall Throughput* 1 G / 420 M 2 G / 900 M 4 G / 2. 5 G 13 G / 8 G 40 G IPS Throughput* 20 M / 11 M 260 M / 170 M 540 M / 380 M 2. 7 G / 2. 1 G 10 G VPN Throughput* 200 M / 90 M 400 M / 180 M 1 G / 460 M 3. 7 G / 1. 8 G 10 G Function VPN, Firewall, UTM, IDS/IPS, URL Filtering, Qo. S, Network Load Balancer, DDo. S Detect & Report * Throughput (one way) : Max(1400 Byte) / 512 Byte 34
 “Our mission is to provide excellent network security products and services for more people, more convenient, and more safe“ Thanks you
“Our mission is to provide excellent network security products and services for more people, more convenient, and more safe“ Thanks you


