acfc7c9b276be04b2141934a434a0f07.ppt
- Количество слайдов: 52

Product & Services Overview September 2006 CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR
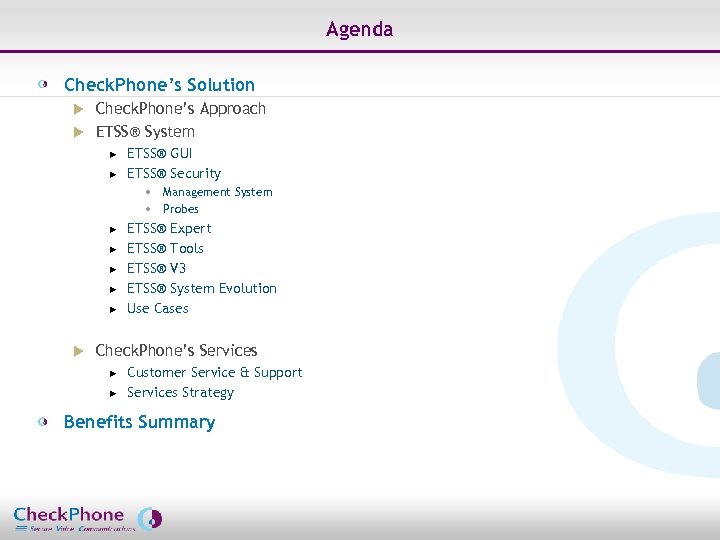
Agenda Check. Phone’s Solution Check. Phone’s Approach u ETSS® System u u u ETSS® GUI ETSS® Security • Management System • Probes u u u ETSS® Expert ETSS® Tools ETSS® V 3 ETSS® System Evolution Use Cases Check. Phone’s Services u u Customer Service & Support Services Strategy Benefits Summary Page 2 CHECKPHONE_PPT_131205_FR. ppt
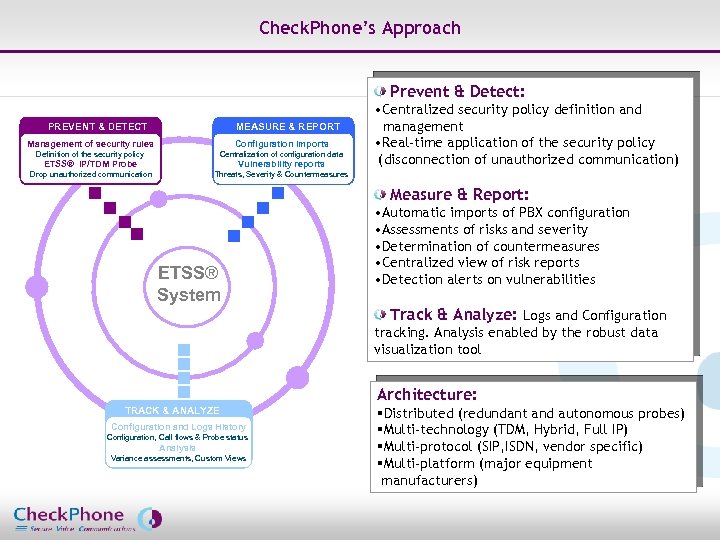
Check. Phone’s Approach Prevent & Detect: PREVENT & DETECT MEASURE & REPORT Management of security rules Configuration imports Definition of the security policy Centralization of configuration data ETSS® IP/TDM Probe Vulnerability reports Drop unauthorized communication • Centralized security policy definition and management • Real-time application of the security policy (disconnection of unauthorized communication) Threats, Severity & Countermeasures Measure & Report: ETSS® System • Automatic imports of PBX configuration • Assessments of risks and severity • Determination of countermeasures • Centralized view of risk reports • Detection alerts on vulnerabilities Track & Analyze: Logs and Configuration tracking. Analysis enabled by the robust data visualization tool Architecture: TRACK & ANALYZE Configuration and Logs History Configuration, Call flows & Probe status Analysis Variance assessments, Custom Views Page 3 §Distributed (redundant and autonomous probes) §Multi-technology (TDM, Hybrid, Full IP) §Multi-protocol (SIP, ISDN, vendor specific) §Multi-platform (major equipment manufacturers) CHECKPHONE_PPT_131205_FR. ppt
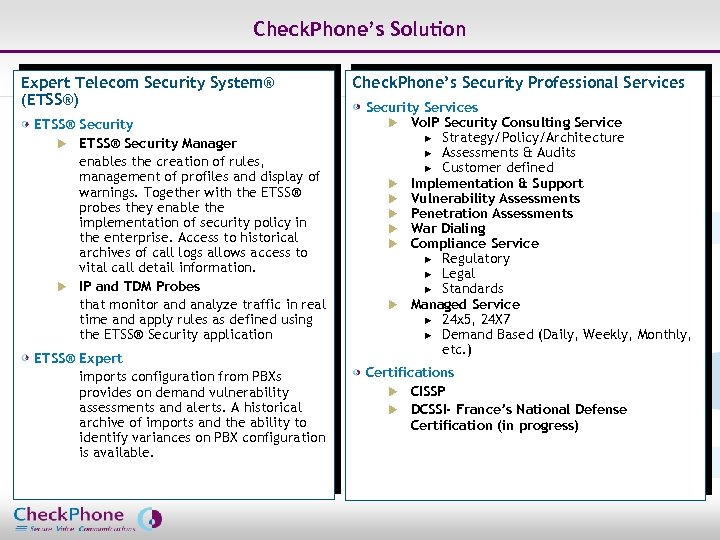
Check. Phone’s Solution Expert Telecom Security System® (ETSS®) ETSS® Security u ETSS® Security Manager enables the creation of rules, management of profiles and display of warnings. Together with the ETSS® probes they enable the implementation of security policy in the enterprise. Access to historical archives of call logs allows access to vital call detail information. u IP and TDM Probes that monitor and analyze traffic in real time and apply rules as defined using the ETSS® Security application ETSS® Expert imports configuration from PBXs provides on demand vulnerability assessments and alerts. A historical archive of imports and the ability to identify variances on PBX configuration is available. Page 4 Check. Phone’s Security Professional Services Security Services u Vo. IP Security Consulting Service u Strategy/Policy/Architecture u Assessments & Audits u Customer defined u Implementation & Support u Vulnerability Assessments u Penetration Assessments u War Dialing u Compliance Service u Regulatory u Legal u Standards u Managed Service u 24 x 5, 24 X 7 u Demand Based (Daily, Weekly, Monthly, etc. ) Certifications u CISSP u DCSSI- France’s National Defense Certification (in progress) CHECKPHONE_PPT_131205_FR. ppt
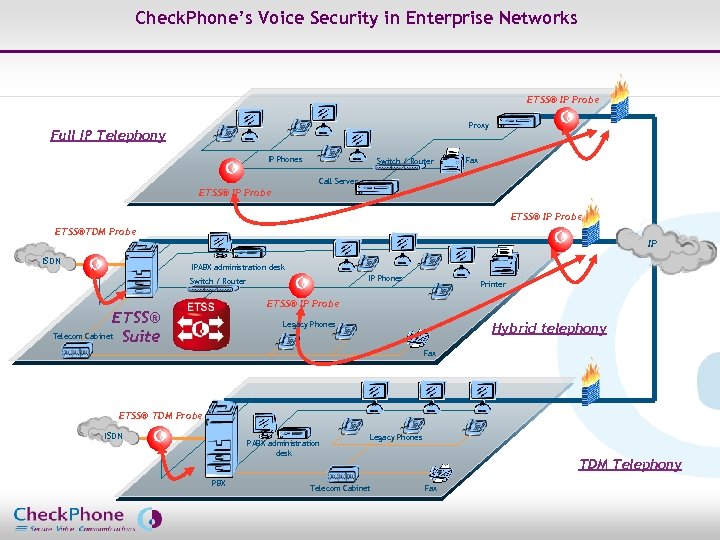
Check. Phone’s Voice Security in Enterprise Networks ETSS® IP Probe Proxy Full IP Telephony IP Phones Switch / Router Fax Call Server ETSS® IP Probe ETSS®TDM Probe IP ISDN IPABX administration desk IP Phones Switch / Router Printer ETSS® IP Probe ETSS® Telecom Cabinet Suite Legacy Phones Hybrid telephony Fax ETSS® TDM Probe ISDN PABX administration desk PBX Page 5 Legacy Phones Telecom Cabinet TDM Telephony Fax CHECKPHONE_PPT_131205_FR. ppt
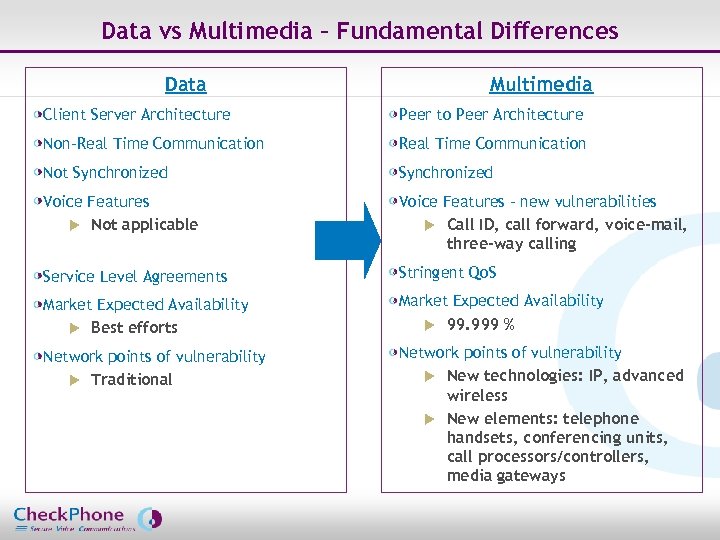
Data vs Multimedia – Fundamental Differences Data Multimedia Client Server Architecture Peer to Peer Architecture Non-Real Time Communication Not Synchronized Voice Features u Not applicable Voice Features – new vulnerabilities u Call ID, call forward, voice-mail, three-way calling Service Level Agreements Stringent Qo. S Market Expected Availability u Best efforts Market Expected Availability u 99. 999 % Network points of vulnerability u Traditional Network points of vulnerability u New technologies: IP, advanced wireless u New elements: telephone handsets, conferencing units, call processors/controllers, media gateways Page 6 CHECKPHONE_PPT_131205_FR. ppt
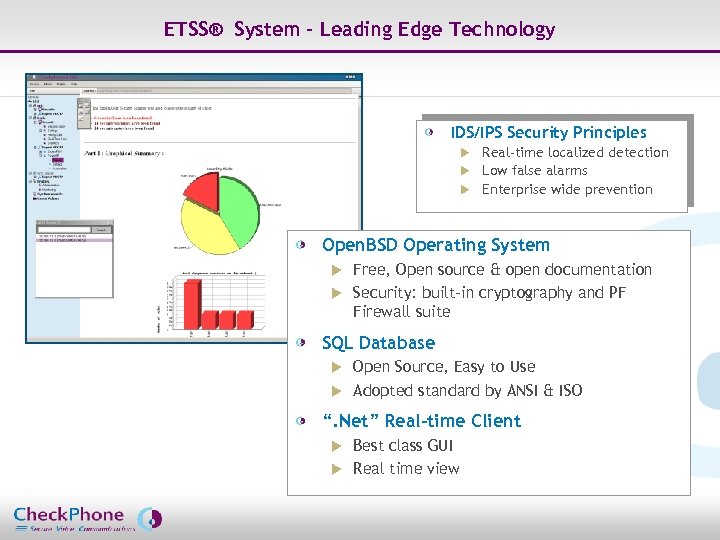
ETSS® System – Leading Edge Technology IDS/IPS Security Principles Real-time localized detection u Low false alarms u Enterprise wide prevention u Open. BSD Operating System Free, Open source & open documentation u Security: built-in cryptography and PF Firewall suite u SQL Database Open Source, Easy to Use u Adopted standard by ANSI & ISO u “. Net” Real-time Client Best class GUI u Real time view u Page 7 CHECKPHONE_PPT_131205_FR. ppt
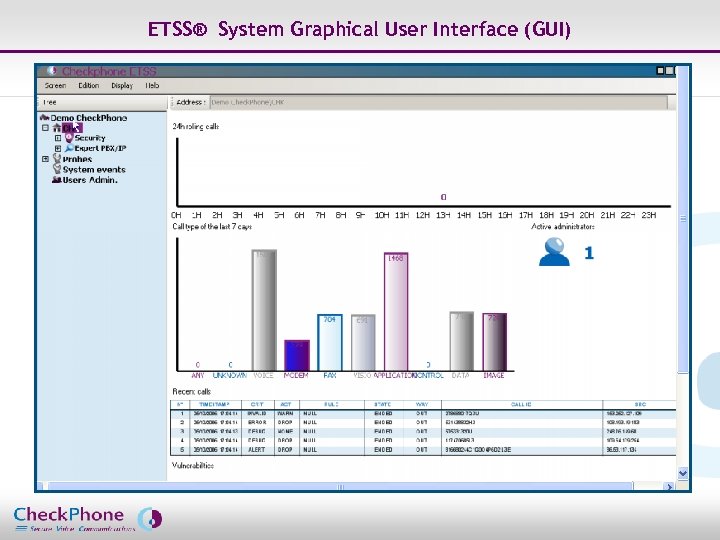
ETSS® System Graphical User Interface (GUI) Page 8 CHECKPHONE_PPT_131205_FR. ppt
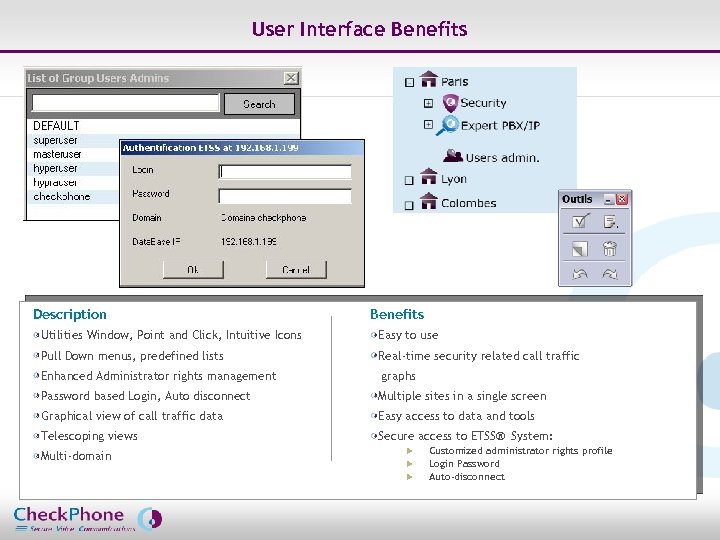
User Interface Benefits Description Benefits Utilities Window, Point and Click, Intuitive Icons Easy to use Pull Down menus, predefined lists Real-time security related call traffic Enhanced Administrator rights management graphs Password based Login, Auto disconnect Multiple sites in a single screen Graphical view of call traffic data Easy access to data and tools Telescoping views Secure access to ETSS® System: Multi-domain u u u Page 9 CHECKPHONE_PPT_131205_FR. ppt Customized administrator rights profile Login Password Auto-disconnect
ETSS® Security CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR
ETSS® Security Overview Security Policy u u u Rule definition Rule filters Implement button Settings u u u Lists Automation Schedules Actions Antifuzz protection Real-time Calls u u 24 hours rolling, by call type view Last 5 calls History Calls Statistics Key Administrator capabilities: Add/Delete Rules Manage Settings View Warnings, call history, real time calls Antifuzz profiles Automate email alerts Page 11 CHECKPHONE_PPT_131205_FR. ppt
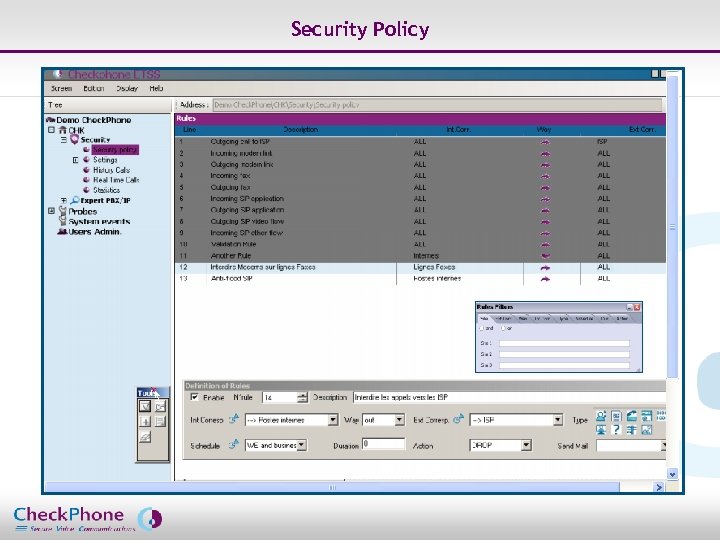
Security Policy Page 12 CHECKPHONE_PPT_131205_FR. ppt

Rule Application ACTIONS u u u Page 13 Each rule entails an action, either directly or after a settable timeout Ban: disconnection of the communication or temporary banishment Authorization Special tagging that flags these calls within the logs for external analysis Analysis: tracking of calls to qualify them with regard to occurrence over time CHECKPHONE_PPT_131205_FR. ppt
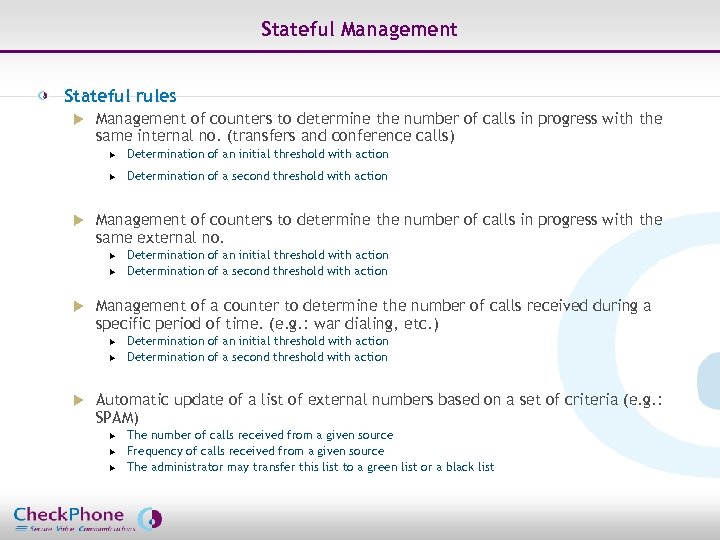
Stateful Management Stateful rules u Management of counters to determine the number of calls in progress with the same internal no. (transfers and conference calls) u u u Determination of an initial threshold with action Determination of a second threshold with action Management of counters to determine the number of calls in progress with the same external no. u u u Management of a counter to determine the number of calls received during a specific period of time. (e. g. : war dialing, etc. ) u u u Determination of an initial threshold with action Determination of a second threshold with action Automatic update of a list of external numbers based on a set of criteria (e. g. : SPAM) u u u Page 14 Determination of an initial threshold with action Determination of a second threshold with action The number of calls received from a given source Frequency of calls received from a given source The administrator may transfer this list to a green list or a black list CHECKPHONE_PPT_131205_FR. ppt
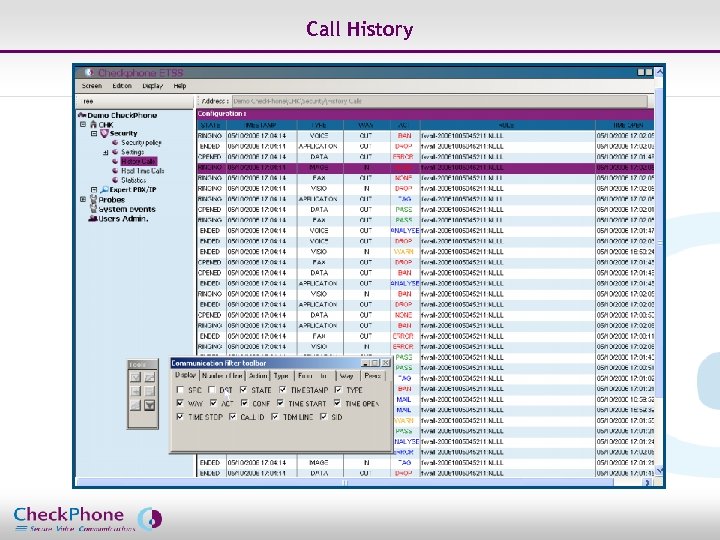
Call History Page 15 CHECKPHONE_PPT_131205_FR. ppt
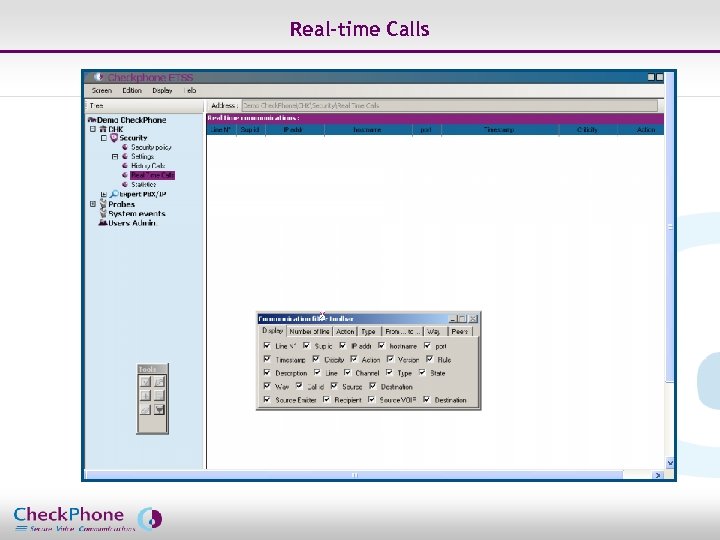
Real-time Calls Page 16 CHECKPHONE_PPT_131205_FR. ppt
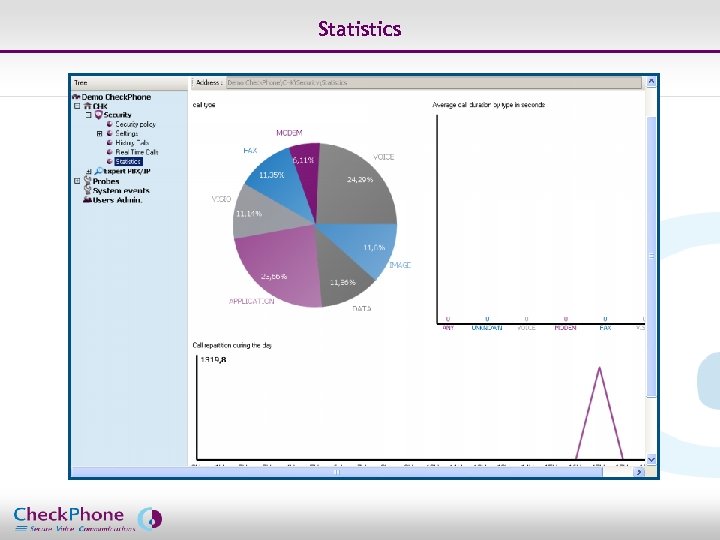
Statistics Include V 3 Screen Page 17 CHECKPHONE_PPT_131205_FR. ppt

ETSS® TDM Probe Page 18 CHECKPHONE_PPT_131205_FR. ppt
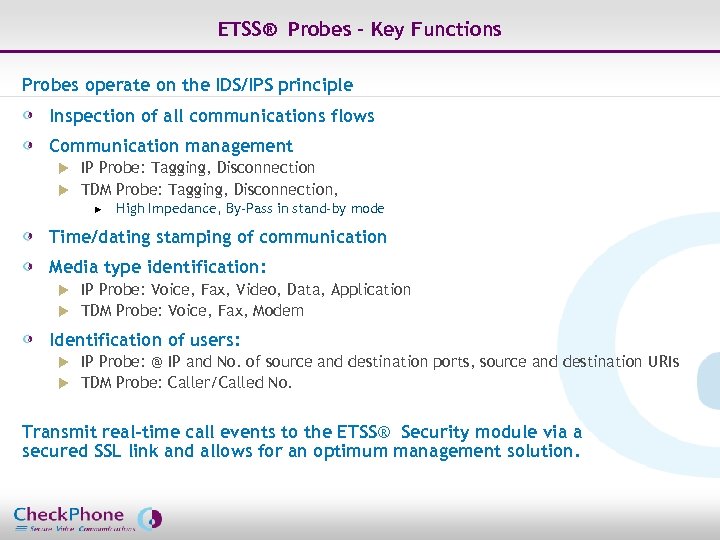
ETSS® Probes – Key Functions Probes operate on the IDS/IPS principle Inspection of all communications flows Communication management IP Probe: Tagging, Disconnection u TDM Probe: Tagging, Disconnection, u u High Impedance, By-Pass in stand-by mode Time/dating stamping of communication Media type identification: IP Probe: Voice, Fax, Video, Data, Application u TDM Probe: Voice, Fax, Modem u Identification of users: IP Probe: @ IP and No. of source and destination ports, source and destination URIs u TDM Probe: Caller/Called No. u Transmit real-time call events to the ETSS® Security module via a secured SSL link and allows for an optimum management solution. Page 19 CHECKPHONE_PPT_131205_FR. ppt
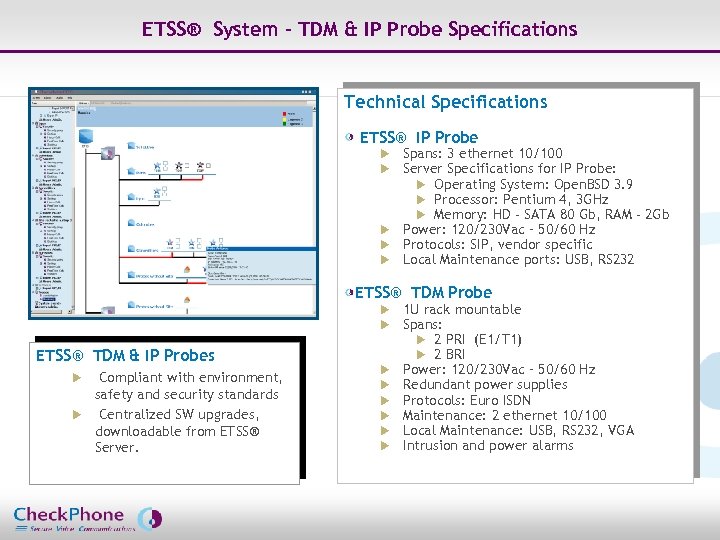
ETSS® System – TDM & IP Probe Specifications Technical Specifications ETSS® IP Probe Spans: 3 ethernet 10/100 Server Specifications for IP Probe: u Operating System: Open. BSD 3. 9 u Processor: Pentium 4, 3 GHz u Memory: HD - SATA 80 Gb, RAM - 2 Gb u Power: 120/230 Vac – 50/60 Hz u Protocols: SIP, vendor specific u Local Maintenance ports: USB, RS 232 u u ETSS® TDM Probe u u ETSS® TDM & IP Probes Compliant with environment, safety and security standards u Centralized SW upgrades, downloadable from ETSS® Server. u Page 20 u u u 1 U rack mountable Spans: u 2 PRI (E 1/T 1) u 2 BRI Power: 120/230 Vac – 50/60 Hz Redundant power supplies Protocols: Euro ISDN Maintenance: 2 ethernet 10/100 Local Maintenance: USB, RS 232, VGA Intrusion and power alarms CHECKPHONE_PPT_131205_FR. ppt
ETSS® Security Key Benefits Centralized management of security in the enterprise: u Centralized enterprise perimeter-wide views of security warnings u Centralized definition of enterprise perimeter-wide security policy rules u Centralized download of rules to probes, upload of logs from the probes Easy to use graphical user interface u Pull-down menus for defined profiles, Scroll bars, action buttons u Call Type Icons u Select/Deselect boxes Choice of operating modes u Block Mode: all calls not authorized by a specific rule are blocked u Authorization Mode: all calls not blocked by a specific rule are allowed Minimizes risk of disruptive security implementation with flexibility to monitor, tag and block calls. Enhanced SIP security management – Antifuzz profiler Automation of key security tool functions Page 21 CHECKPHONE_PPT_131205_FR. ppt

ETSS® Expert CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR
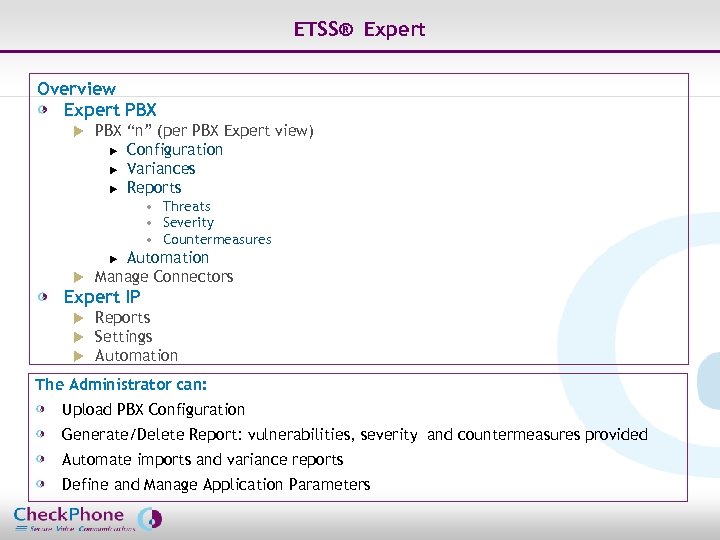
ETSS® Expert Overview Expert PBX u PBX “n” (per PBX Expert view) u Configuration u Variances u Reports • Threats • Severity • Countermeasures Automation u Manage Connectors u Expert IP u u u Reports Settings Automation The Administrator can: Upload PBX Configuration Generate/Delete Report: vulnerabilities, severity and countermeasures provided Automate imports and variance reports Define and Manage Application Parameters Page 23 CHECKPHONE_PPT_131205_FR. ppt
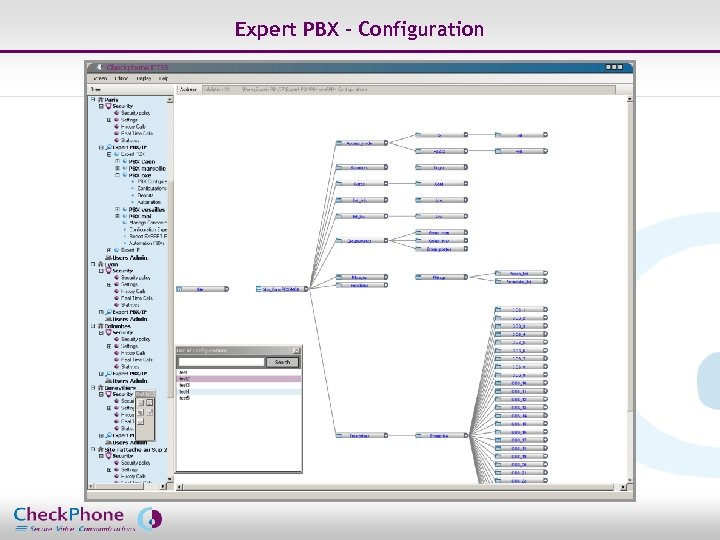
Expert PBX - Configuration Page 24 CHECKPHONE_PPT_131205_FR. ppt
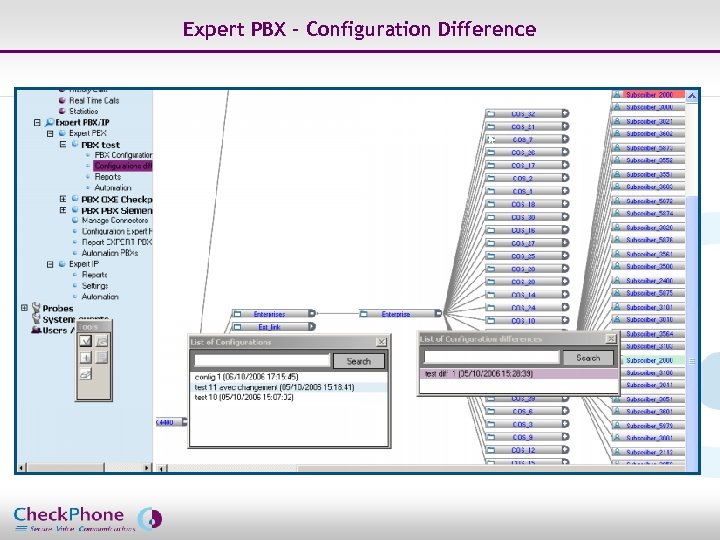
Expert PBX – Configuration Difference Page 25 CHECKPHONE_PPT_131205_FR. ppt
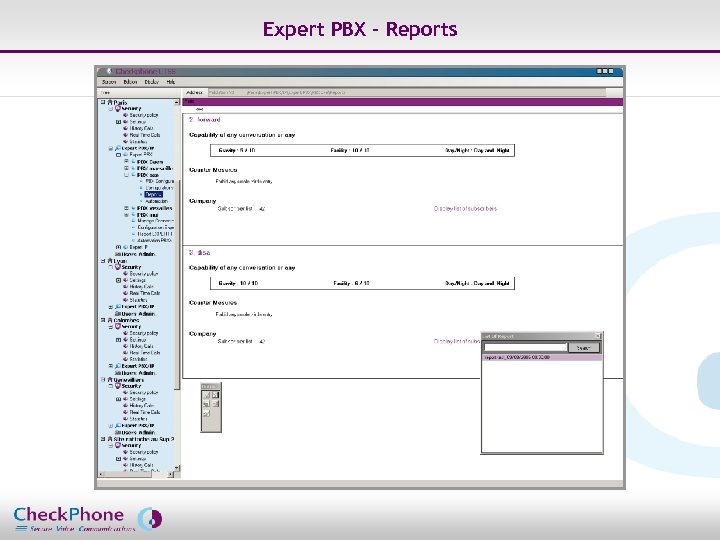
Expert PBX - Reports Page 26 CHECKPHONE_PPT_131205_FR. ppt
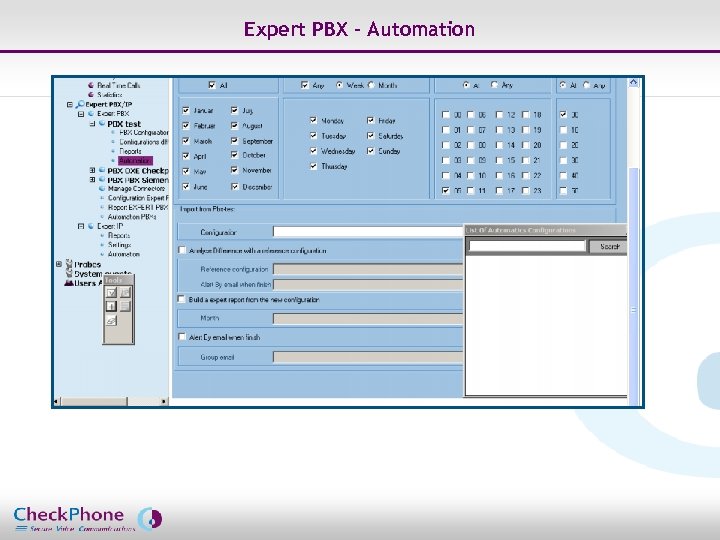
Expert PBX - Automation Page 27 CHECKPHONE_PPT_131205_FR. ppt
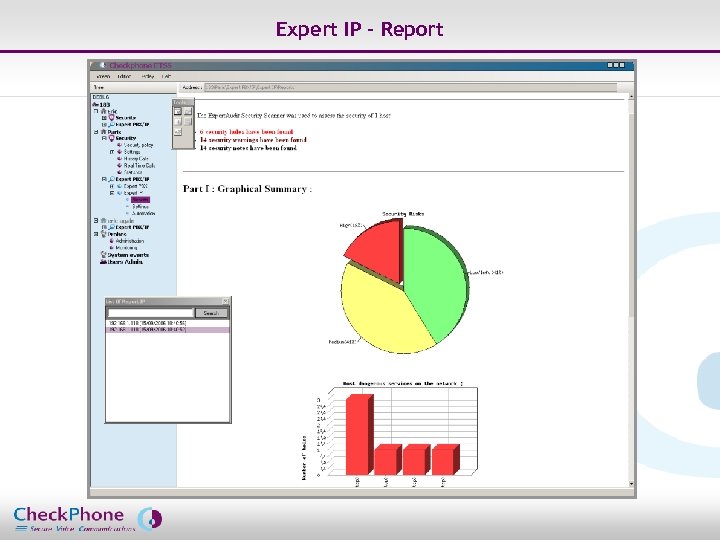
Expert IP - Report Page 28 CHECKPHONE_PPT_131205_FR. ppt
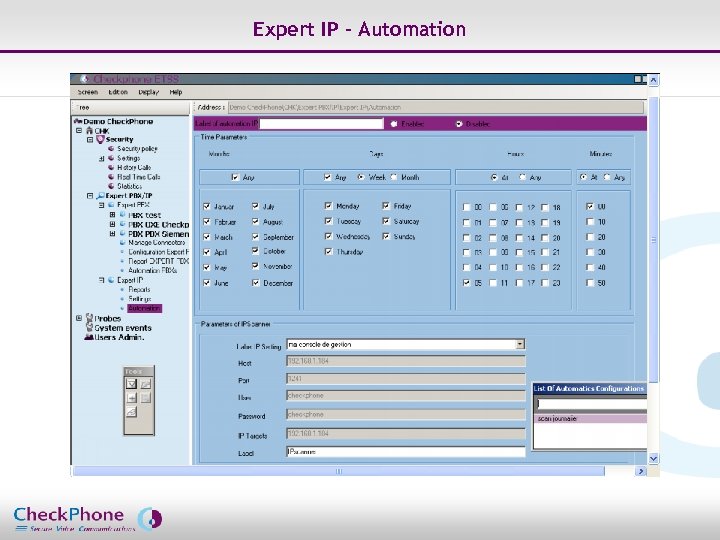
Expert IP - Automation Page 29 CHECKPHONE_PPT_131205_FR. ppt
ETSS® Expert Key Benefits Centralized : u Centralized import of PBX configurations. Key industry PBX types supported. u Centralized view of Reports: threats, severity and countermeasures u Centralized history of PBX configurations & variances Easy to use graphical user interface u Scroll bars to explore lists u Tree based hierarchical views of the file system u Point and Click to select tree elements Automation u Uploads of configurations u Creation of threat reports Knowledge base of more than 3, 000 vulnerabilities and more than 300 scenarios IP Security Scanner Page 30 CHECKPHONE_PPT_131205_FR. ppt
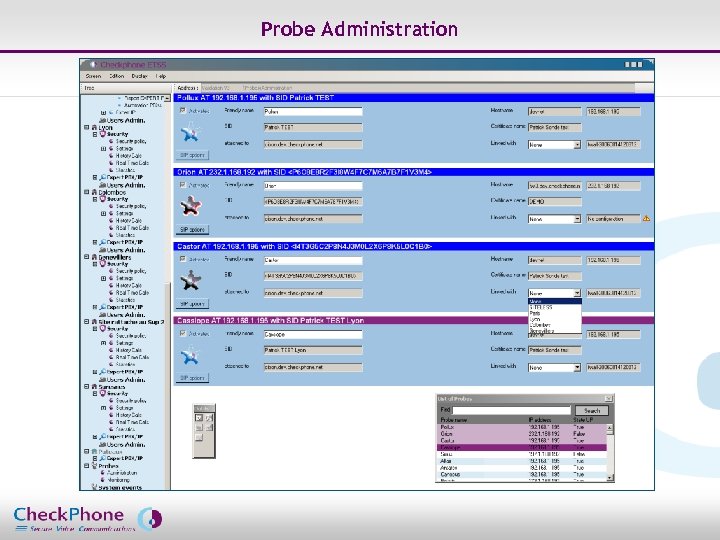
Probe Administration Page 31 CHECKPHONE_PPT_131205_FR. ppt
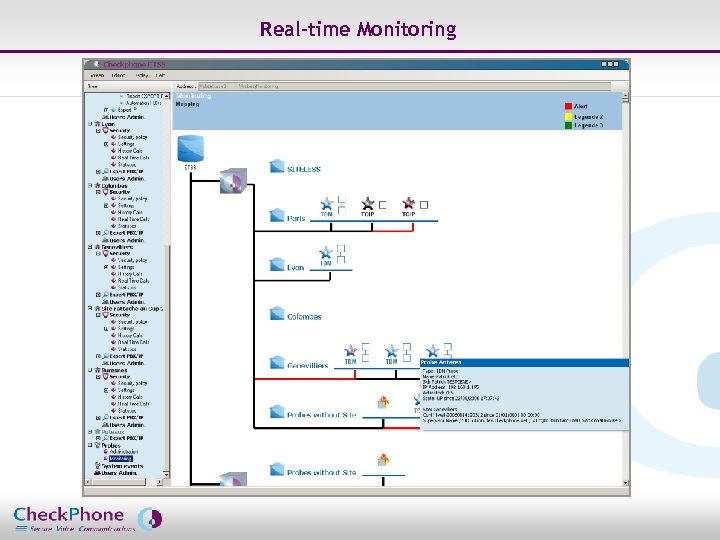
Real-time Monitoring Page 32 CHECKPHONE_PPT_131205_FR. ppt
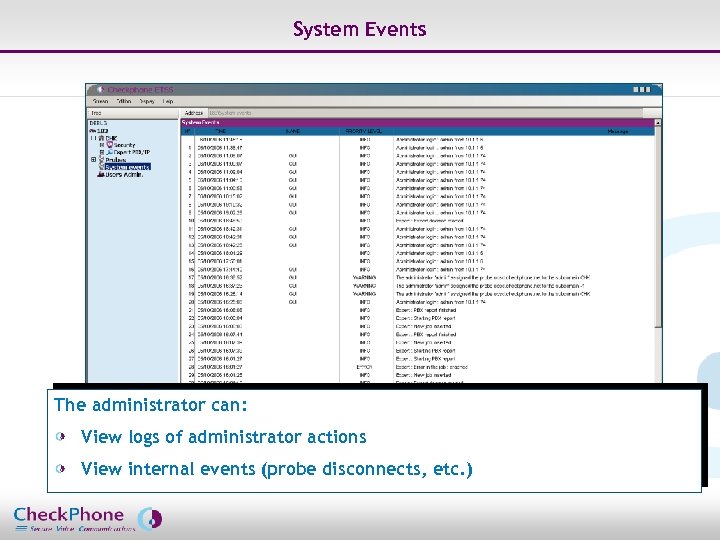
System Events The administrator can: View logs of administrator actions View internal events (probe disconnects, etc. ) Page 33 CHECKPHONE_PPT_131205_FR. ppt
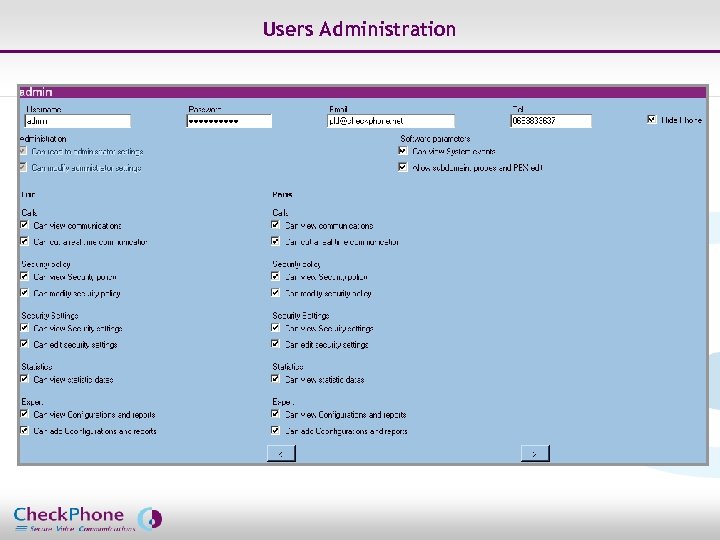
Users Administration Page 34 CHECKPHONE_PPT_131205_FR. ppt
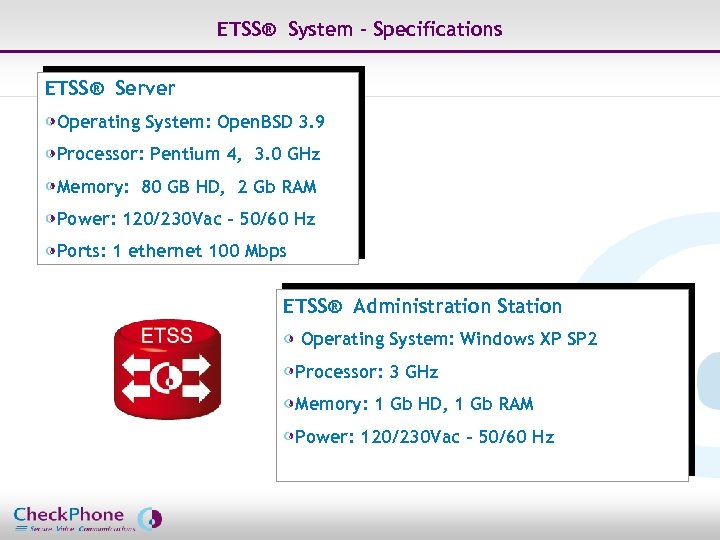
ETSS® System – Specifications ETSS® Server Operating System: Open. BSD 3. 9 Processor: Pentium 4, 3. 0 GHz Memory: 80 GB HD, 2 Gb RAM Power: 120/230 Vac – 50/60 Hz Ports: 1 ethernet 100 Mbps ETSS® Administration Station Operating System: Windows XP SP 2 Processor: 3 GHz Memory: 1 Gb HD, 1 Gb RAM Power: 120/230 Vac – 50/60 Hz Page 35 CHECKPHONE_PPT_131205_FR. ppt

Version 3. 0 Update CHECPHONE_POT_061205_FR. pot CHECKPHONE_PPT_061205_FR
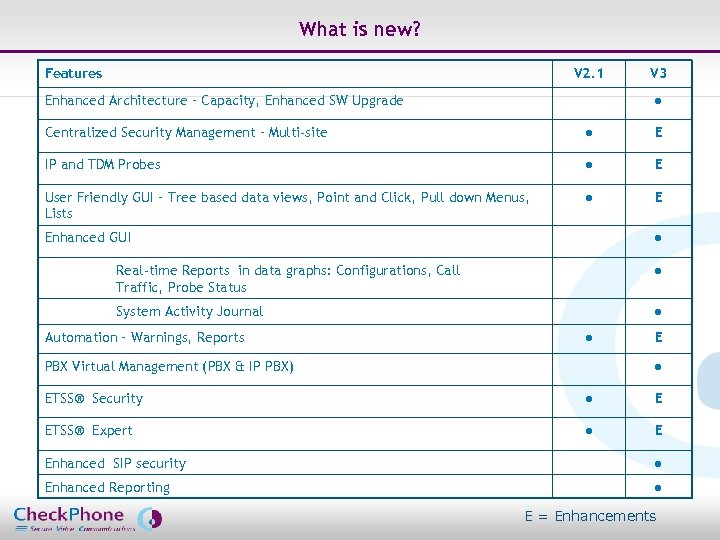
What is new? Features V 2. 1 Enhanced Architecture – Capacity, Enhanced SW Upgrade V 3 ● Centralized Security Management – Multi-site ● E IP and TDM Probes ● E User Friendly GUI – Tree based data views, Point and Click, Pull down Menus, Lists ● E Enhanced GUI ● Real-time Reports in data graphs: Configurations, Call Traffic, Probe Status ● System Activity Journal ● Automation – Warnings, Reports ● PBX Virtual Management (PBX & IP PBX) E ● ETSS® Security ● E ETSS® Expert ● E Enhanced SIP security ● Enhanced Reporting ● Page 37 CHECKPHONE_PPT_131205_FR. ppt E = Enhancements
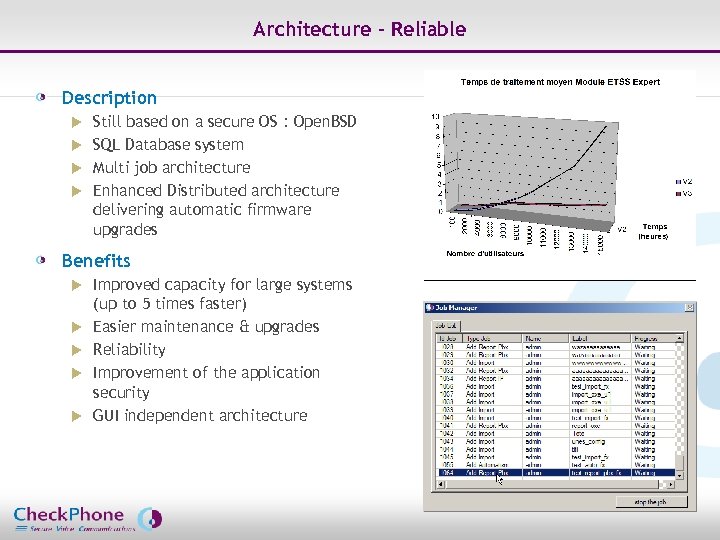
Architecture – Reliable Description Still based on a secure OS : Open. BSD u SQL Database system u Multi job architecture u Enhanced Distributed architecture delivering automatic firmware upgrades u Benefits u u u Page 38 Improved capacity for large systems (up to 5 times faster) Easier maintenance & upgrades Reliability Improvement of the application security GUI independent architecture CHECKPHONE_PPT_131205_FR. ppt

Centralized View & Element Status Description Benefits Multi- domain, single system Optimal use of resources: people, tools Centralized Real-time data access Seamless migration to Vo. IP Centralized tools: Security & Expert Ease of Security management in an evolving/growing Centralized: Probes status, Call logs, SW Updates Centralized: Configurations, Variances System Event Journals Page 39 network Reduced response time CHECKPHONE_PPT_131205_FR. ppt
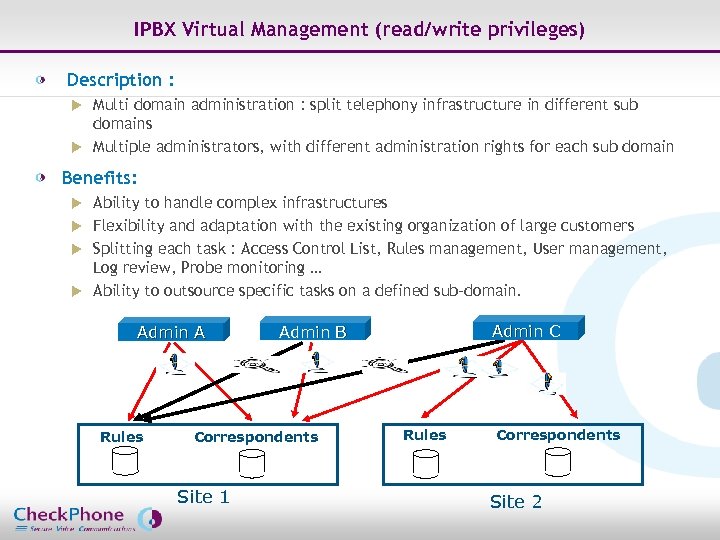
IPBX Virtual Management (read/write privileges) Description : Multi domain administration : split telephony infrastructure in different sub domains u Multiple administrators, with different administration rights for each sub domain u Benefits: Ability to handle complex infrastructures u Flexibility and adaptation with the existing organization of large customers u Splitting each task : Access Control List, Rules management, User management, Log review, Probe monitoring … u Ability to outsource specific tasks on a defined sub-domain. u Admin A Rules Admin C Admin B Correspondents Rules Site 1 Page 40 Correspondents Site 2 CHECKPHONE_PPT_131205_FR. ppt
IPBX Virtual Management (read/write privileges) Page 41 CHECKPHONE_PPT_131205_FR. ppt
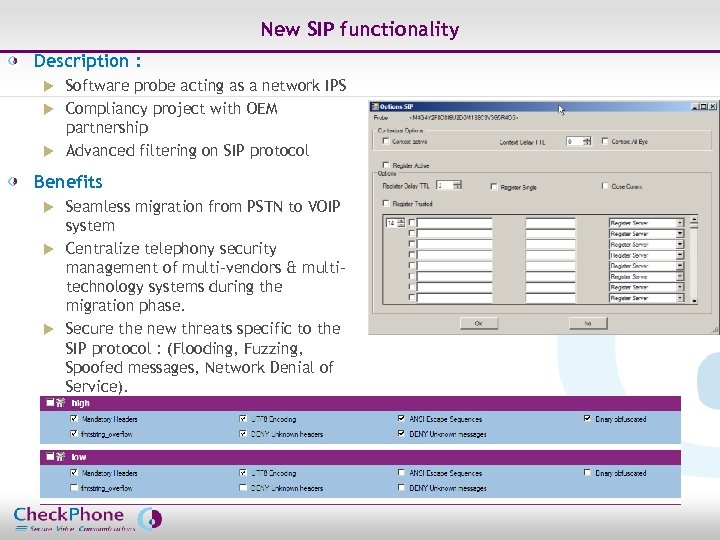
New SIP functionality Description : Software probe acting as a network IPS u Compliancy project with OEM partnership u Advanced filtering on SIP protocol u Benefits Seamless migration from PSTN to VOIP system u Centralize telephony security management of multi-vendors & multitechnology systems during the migration phase. u Secure the new threats specific to the SIP protocol : (Flooding, Fuzzing, Spoofed messages, Network Denial of Service). u Page 42 CHECKPHONE_PPT_131205_FR. ppt
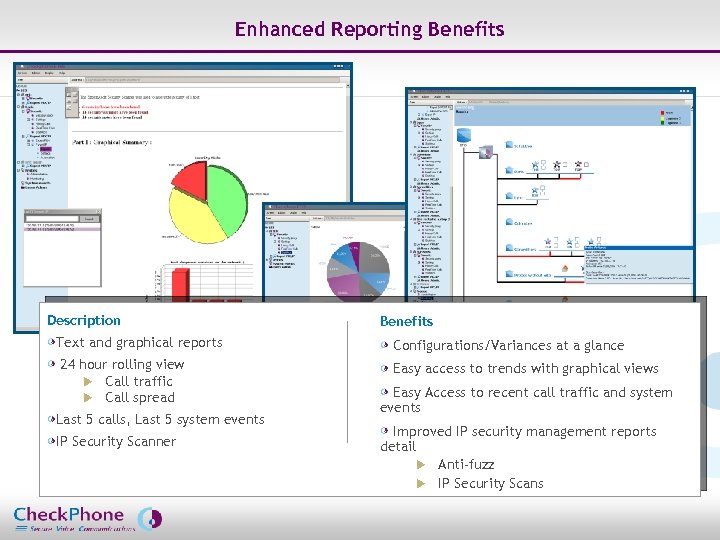
Enhanced Reporting Benefits Description Text and graphical reports 24 hour rolling view u Call traffic u Call spread Last 5 calls, Last 5 system events IP Security Scanner Page 43 Benefits Configurations/Variances at a glance Easy access to trends with graphical views Easy Access to recent call traffic and system events Improved IP security management reports detail u Anti-fuzz u IP Security Scans CHECKPHONE_PPT_131205_FR. ppt
ETSS® System Evolution CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR

ETSS® (Expert Telecom Security Solution®) Evolution 1. Short Term Deliver ETSS® V 3 with: Mature GUI Enhanced Features Fully Commercialized Define New Market Requirements – North America and Western Europe V 4/V 5 Customer, Market and Technology Requirements and Implementation 2. Strategic Create “Best in Class” UI – Simplification Performance and Protection Improvements Complete the Tool Suite Product Integration – UTM/Call Managers Extend the Security Suite IM & Multimedia Small Business and Consumer Wireless Page 45 CHECKPHONE_PPT_131205_FR. ppt
Use Cases CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR
Finance Industry Retail banking business continuity not covered while migrating u. Isolate and be protected against Do. S attacks u. Call centers are crucial and are not secured Investment Banking business integrity not covered while migrating u. Against worms and intrusions u. Against spy and fraudulent attacks Enforce Basel II compliance (traceability, due diligence, …) u. Track changes and assess the security rules u Audit and Report against policies in place Return on Investment is critical u. Centralized management u. Automated processes u. Alerting and forensics u. Risk Management Security is an integral part of service continuity and media integrity. Need to address vulnerabilities in IP and «unique attributes » of voice. Page 47 CHECKPHONE_PPT_131205_FR. ppt

Checkphone Services CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR
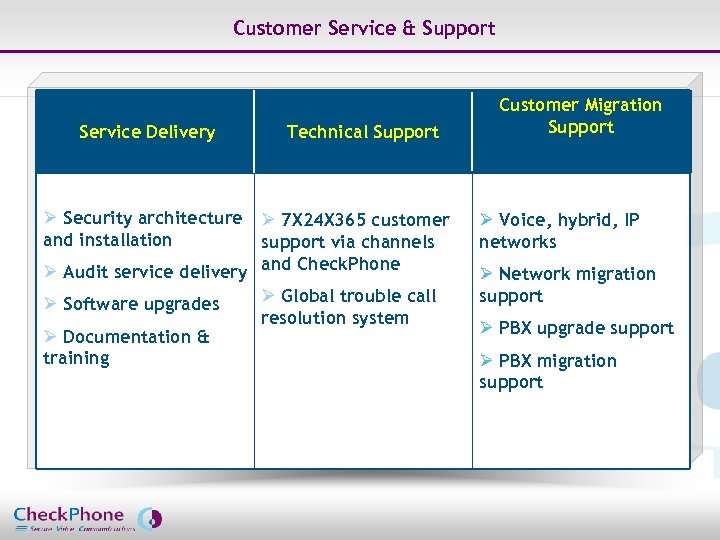
Customer Service & Support Service Delivery Technical Support Ø Security architecture Ø 7 X 24 X 365 customer and installation support via channels Ø Audit service delivery and Check. Phone Ø Software upgrades Ø Documentation & training Page 49 Ø Global trouble call resolution system Customer Migration Support Ø Voice, hybrid, IP networks Ø Network migration support Ø PBX upgrade support Ø PBX migration support CHECKPHONE_PPT_131205_FR. ppt
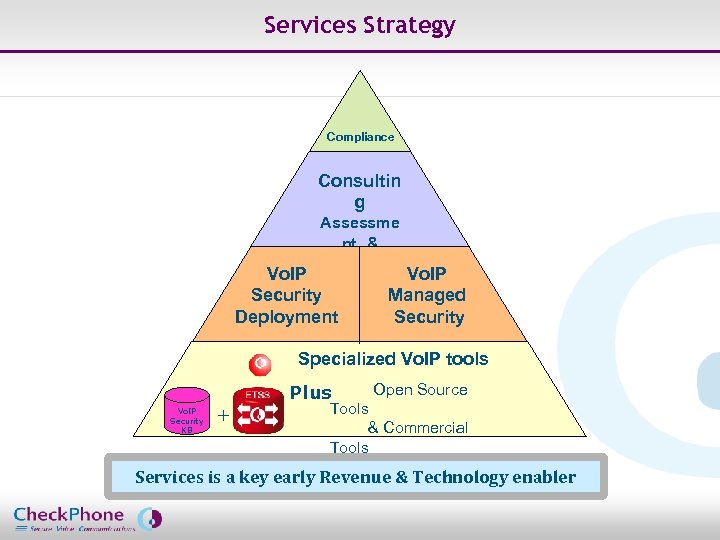
Services Strategy Compliance Consultin g Assessme nt & Audit Vo. IP Security Deployment Vo. IP Managed Security Specialized Vo. IP tools Vo. IP Security KB + Plus Open Source Tools & Commercial Tools Services is a key early Revenue & Technology enabler Page 50 CHECKPHONE_PPT_131205_FR. ppt
Key Benefits Check. Phone meets voice security needs in the enterprise: u u u Real-time monitoring and localized protection against security breaches in the voice network Seamless integration into the existing network infrastructure and migration to Vo. IP Optimal use of security resources with centralization of security management Advanced vulnerability audit and reporting on PBX configuration Ease of use Effective voice security technology Check. Phone addresses major security threats in the voice network u u u Integrity Eavesdropping Interception and modification Service abuse Denial of service Check. Phone a trust worthy Security Solution supplier u u u Page 51 300+ years of Security, IP and telephony experience Proven track record for products and services – a note worthy customer base A future proof approach – Open Source OS and SQL Database, video and voice security, “. Net” connectivity CHECKPHONE_PPT_131205_FR. ppt

Thank You CHECPHONE_POT_061205_FR. pot Analyze, control, and secure your telephone applications CHECKPHONE_PPT_061205_FR
acfc7c9b276be04b2141934a434a0f07.ppt