644ce345982d510b8bccef73e16dda65.ppt
- Количество слайдов: 21
 Process Standards (and Process Improvement) Secure Systems Research Group - FAU
Process Standards (and Process Improvement) Secure Systems Research Group - FAU
 Wireless Security Survey Update Standard Format for all Protocols • • Identity Authentication Session key Message/data encryption Do. S, Location detection Discussion of strengths & vulnerabilities Discussion of planned enhancements Secure Systems Research Group - FAU
Wireless Security Survey Update Standard Format for all Protocols • • Identity Authentication Session key Message/data encryption Do. S, Location detection Discussion of strengths & vulnerabilities Discussion of planned enhancements Secure Systems Research Group - FAU
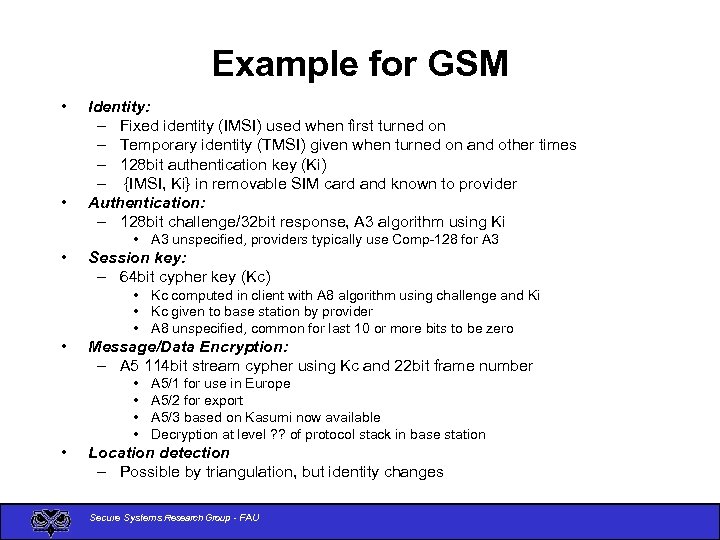 Example for GSM • • Identity: – Fixed identity (IMSI) used when first turned on – Temporary identity (TMSI) given when turned on and other times – 128 bit authentication key (Ki) – {IMSI, Ki} in removable SIM card and known to provider Authentication: – 128 bit challenge/32 bit response, A 3 algorithm using Ki • A 3 unspecified, providers typically use Comp-128 for A 3 • Session key: – 64 bit cypher key (Kc) • Kc computed in client with A 8 algorithm using challenge and Ki • Kc given to base station by provider • A 8 unspecified, common for last 10 or more bits to be zero • Message/Data Encryption: – A 5 114 bit stream cypher using Kc and 22 bit frame number • • • A 5/1 for use in Europe A 5/2 for export A 5/3 based on Kasumi now available Decryption at level ? ? of protocol stack in base station Location detection – Possible by triangulation, but identity changes Secure Systems Research Group - FAU
Example for GSM • • Identity: – Fixed identity (IMSI) used when first turned on – Temporary identity (TMSI) given when turned on and other times – 128 bit authentication key (Ki) – {IMSI, Ki} in removable SIM card and known to provider Authentication: – 128 bit challenge/32 bit response, A 3 algorithm using Ki • A 3 unspecified, providers typically use Comp-128 for A 3 • Session key: – 64 bit cypher key (Kc) • Kc computed in client with A 8 algorithm using challenge and Ki • Kc given to base station by provider • A 8 unspecified, common for last 10 or more bits to be zero • Message/Data Encryption: – A 5 114 bit stream cypher using Kc and 22 bit frame number • • • A 5/1 for use in Europe A 5/2 for export A 5/3 based on Kasumi now available Decryption at level ? ? of protocol stack in base station Location detection – Possible by triangulation, but identity changes Secure Systems Research Group - FAU
 Additions • New Protocols – Wi. Max and Mobile Wi. Max – EV-DO – New military wireless protocols • New domains – Vehicle system wireless (as a variant of shopfloor) • Map of spectrum usage • Updates (i. e. , wrt. advances in cryptography) Secure Systems Research Group - FAU
Additions • New Protocols – Wi. Max and Mobile Wi. Max – EV-DO – New military wireless protocols • New domains – Vehicle system wireless (as a variant of shopfloor) • Map of spectrum usage • Updates (i. e. , wrt. advances in cryptography) Secure Systems Research Group - FAU
 ISO/IEC 17799: 2005(E) Information technology — Security techniques — Code of practice for information security management Second edition 2005 -06 -15 Secure Systems Research Group - FAU
ISO/IEC 17799: 2005(E) Information technology — Security techniques — Code of practice for information security management Second edition 2005 -06 -15 Secure Systems Research Group - FAU
 Intent of the Standard “This International Standard establishes guidelines and general principles for initiating, implementing, maintaining, and improving information security management in an organization. ” “The control objectives and controls of this International Standard are intended to be implemented to meet the requirements identified by a risk assessment. This International Standard may serve as a practical guideline for developing organizational security standards and effective security management practices and to help build confidence in inter-organizational activities. ” Secure Systems Research Group - FAU
Intent of the Standard “This International Standard establishes guidelines and general principles for initiating, implementing, maintaining, and improving information security management in an organization. ” “The control objectives and controls of this International Standard are intended to be implemented to meet the requirements identified by a risk assessment. This International Standard may serve as a practical guideline for developing organizational security standards and effective security management practices and to help build confidence in inter-organizational activities. ” Secure Systems Research Group - FAU
 39 Categories in 11 Clauses 5. Security Policy (1) 6. Organizing Information Security (2) 7. Asset Management (2) 8. Human Resources Security (3) 9. Physical and Environmental Security (2) 10. Communications and Operations Management (10) 11. Access Control (7) 12. Information Systems Acquisition, Development and Maintenance (6) 13. Information Security Incident Management (2) 14. Business Continuity Management (1) 15. Compliance (3) Secure Systems Research Group - FAU
39 Categories in 11 Clauses 5. Security Policy (1) 6. Organizing Information Security (2) 7. Asset Management (2) 8. Human Resources Security (3) 9. Physical and Environmental Security (2) 10. Communications and Operations Management (10) 11. Access Control (7) 12. Information Systems Acquisition, Development and Maintenance (6) 13. Information Security Incident Management (2) 14. Business Continuity Management (1) 15. Compliance (3) Secure Systems Research Group - FAU
 Structure of a Category • a control objective stating what is to be achieved; • one or more controls that can be applied to achieve the control objective. Control descriptions are structured as follows: a. Control: Defines the specific control statement to satisfy the control objective. b. Implementation guidance: Provides more detailed information to support the implementation of the control and meeting the control objective. c. Other information: Provides further information that may need to be considered, for example legal considerations and references to other standards. Secure Systems Research Group - FAU
Structure of a Category • a control objective stating what is to be achieved; • one or more controls that can be applied to achieve the control objective. Control descriptions are structured as follows: a. Control: Defines the specific control statement to satisfy the control objective. b. Implementation guidance: Provides more detailed information to support the implementation of the control and meeting the control objective. c. Other information: Provides further information that may need to be considered, for example legal considerations and references to other standards. Secure Systems Research Group - FAU
 Applicable to development? (Section #: topic covered) 5: Security policy 8: Human resources security 10: Communications and operations management 11: Access control (i. e. , to source code) 13. 2: Management of information security incidents and improvements Secure Systems Research Group - FAU
Applicable to development? (Section #: topic covered) 5: Security policy 8: Human resources security 10: Communications and operations management 11: Access control (i. e. , to source code) 13. 2: Management of information security incidents and improvements Secure Systems Research Group - FAU
 12. Information systems acquisition, development and maintenance 12. 1 Security requirements of information systems 12. 2 Correct processing in applications 12. 3 Cryptographic controls 12. 4 Security of system files 12. 5 Security in development and support processes 12. 6 Technical Vulnerability Management Secure Systems Research Group - FAU
12. Information systems acquisition, development and maintenance 12. 1 Security requirements of information systems 12. 2 Correct processing in applications 12. 3 Cryptographic controls 12. 4 Security of system files 12. 5 Security in development and support processes 12. 6 Technical Vulnerability Management Secure Systems Research Group - FAU
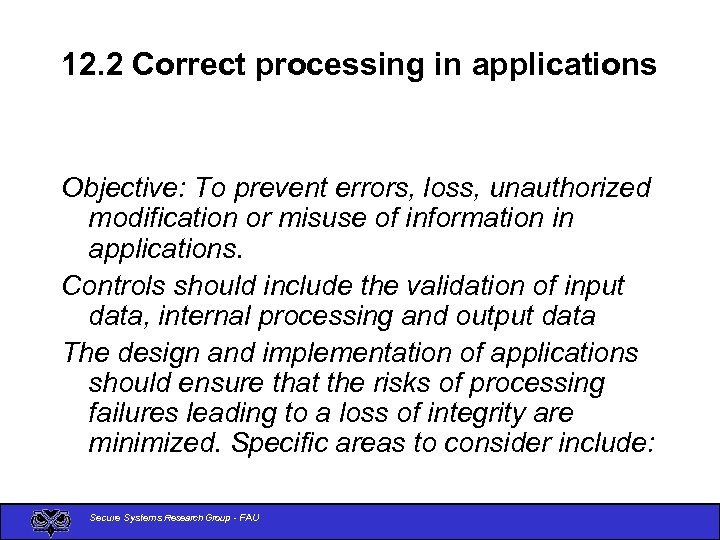 12. 2 Correct processing in applications Objective: To prevent errors, loss, unauthorized modification or misuse of information in applications. Controls should include the validation of input data, internal processing and output data The design and implementation of applications should ensure that the risks of processing failures leading to a loss of integrity are minimized. Specific areas to consider include: Secure Systems Research Group - FAU
12. 2 Correct processing in applications Objective: To prevent errors, loss, unauthorized modification or misuse of information in applications. Controls should include the validation of input data, internal processing and output data The design and implementation of applications should ensure that the risks of processing failures leading to a loss of integrity are minimized. Specific areas to consider include: Secure Systems Research Group - FAU
 12. 5 Security in development and support processes Objective: To maintain the security of application system software and information. 12. 5. 1 Change control procedures 12. 5. 2 Technical review of applications after operating system changes 12. 5. 3 Restrictions on changes to software packages 12. 5. 4 Information leakage 12. 5. 5 Outsourced software development Secure Systems Research Group - FAU
12. 5 Security in development and support processes Objective: To maintain the security of application system software and information. 12. 5. 1 Change control procedures 12. 5. 2 Technical review of applications after operating system changes 12. 5. 3 Restrictions on changes to software packages 12. 5. 4 Information leakage 12. 5. 5 Outsourced software development Secure Systems Research Group - FAU
 12. 5. 1 Change control procedures The implementation of changes should be controlled by the use of formal change control procedures. Introduction of new systems and major changes to existing systems should follow a formal process of documentation, specification, testing, quality control, and managed implementation. Secure Systems Research Group - FAU
12. 5. 1 Change control procedures The implementation of changes should be controlled by the use of formal change control procedures. Introduction of new systems and major changes to existing systems should follow a formal process of documentation, specification, testing, quality control, and managed implementation. Secure Systems Research Group - FAU
 12. 5. 1 Change control procedures c) reviewing controls and integrity procedures to ensure that they will not be compromised by the changes; d) identifying all software, information, database entities, and hardware that require amendment; e) obtaining formal approval for detailed proposals before work commences; Secure Systems Research Group - FAU
12. 5. 1 Change control procedures c) reviewing controls and integrity procedures to ensure that they will not be compromised by the changes; d) identifying all software, information, database entities, and hardware that require amendment; e) obtaining formal approval for detailed proposals before work commences; Secure Systems Research Group - FAU
 12. 5. 2 Technical review of applications after operating system changes When operating systems are changed, business critical applications should be reviewed and tested to ensure there is no adverse impact on organizational operations or security. Secure Systems Research Group - FAU
12. 5. 2 Technical review of applications after operating system changes When operating systems are changed, business critical applications should be reviewed and tested to ensure there is no adverse impact on organizational operations or security. Secure Systems Research Group - FAU
 12. 5. 3 Restrictions on changes to software packages Modifications to software packages should be discouraged, limited to necessary changes, and all changes should be strictly controlled. As far as possible, and practicable, vendorsupplied software packages should be used without modification. Secure Systems Research Group - FAU
12. 5. 3 Restrictions on changes to software packages Modifications to software packages should be discouraged, limited to necessary changes, and all changes should be strictly controlled. As far as possible, and practicable, vendorsupplied software packages should be used without modification. Secure Systems Research Group - FAU
 12. 5. 4 Information leakage Opportunities for information leakage should be prevented. (includes preventing trojan code) a) scanning of outbound media and communications for hidden information; b) masking and modulating system and communications behaviour to reduce the likelihood of a third party being able to deduce information from such behaviour; c) making use of systems and software that are considered to be of high integrity, e. g. using evaluated products (see ISO/IEC 15408); Secure Systems Research Group - FAU
12. 5. 4 Information leakage Opportunities for information leakage should be prevented. (includes preventing trojan code) a) scanning of outbound media and communications for hidden information; b) masking and modulating system and communications behaviour to reduce the likelihood of a third party being able to deduce information from such behaviour; c) making use of systems and software that are considered to be of high integrity, e. g. using evaluated products (see ISO/IEC 15408); Secure Systems Research Group - FAU
 12. 5. 5 Outsourced software development should be supervised and monitored by the organization. a) licensing arrangements, code ownership, and intellectual property rights (see 15. 1. 2); b) certification of the quality and accuracy of the work carried out; c) escrow arrangements in the event of failure of the third party; d) rights of access for audit of the quality and accuracy of work done; e) contractual requirements for quality and security functionality of code; f) testing before installation to detect malicious and Trojan code. Secure Systems Research Group - FAU
12. 5. 5 Outsourced software development should be supervised and monitored by the organization. a) licensing arrangements, code ownership, and intellectual property rights (see 15. 1. 2); b) certification of the quality and accuracy of the work carried out; c) escrow arrangements in the event of failure of the third party; d) rights of access for audit of the quality and accuracy of work done; e) contractual requirements for quality and security functionality of code; f) testing before installation to detect malicious and Trojan code. Secure Systems Research Group - FAU
 12. 6 Technical Vulnerability Management Objective: To reduce risks resulting from exploitation of published technical vulnerabilities. These considerations should include operating systems, and any other applications in use. Timely information about technical vulnerabilities of information systems being used should be obtained, the organization's exposure to such vulnerabilities evaluated, and appropriate measures taken to address the associated risk. A current and complete inventory of assets … Appropriate, timely action should be taken … Secure Systems Research Group - FAU
12. 6 Technical Vulnerability Management Objective: To reduce risks resulting from exploitation of published technical vulnerabilities. These considerations should include operating systems, and any other applications in use. Timely information about technical vulnerabilities of information systems being used should be obtained, the organization's exposure to such vulnerabilities evaluated, and appropriate measures taken to address the associated risk. A current and complete inventory of assets … Appropriate, timely action should be taken … Secure Systems Research Group - FAU
 Observations and Analysis • Some wireless stuff • Focus is on in-house IS/IT support group • Does not address development activities (some items can apply to development team) • Has category for OS evolution. Less attention to impact of emerging networking options • Addresses only 2 nd of Leveson’s 4 levels Secure Systems Research Group - FAU
Observations and Analysis • Some wireless stuff • Focus is on in-house IS/IT support group • Does not address development activities (some items can apply to development team) • Has category for OS evolution. Less attention to impact of emerging networking options • Addresses only 2 nd of Leveson’s 4 levels Secure Systems Research Group - FAU
 Leveson’s Types of Causes • Technical • Human • Organizational • Regulatory Secure Systems Research Group - FAU
Leveson’s Types of Causes • Technical • Human • Organizational • Regulatory Secure Systems Research Group - FAU


