c5bd1da5aec9ef54d477e1128a4545d5.ppt
- Количество слайдов: 23
 Privilege Management in X. 509(2000) David W Chadwick BSc Ph. D 14 May 2002 © 2000 -02 True. Trust Ltd 1
Privilege Management in X. 509(2000) David W Chadwick BSc Ph. D 14 May 2002 © 2000 -02 True. Trust Ltd 1
 X. 509 Evolution • X. 509 (1988) - V 1 PKCertificates and CRLs • X. 509 (1993) - V 2 PKCertificates and revised V 1 CRLs • X. 509 (1997) - V 3 PKCertificates, V 2 CRLs and V 1 Attribute Certificates • X. 509 (2000] - V 3 PKCertificates and V 2 CRLs with additional extensions, plus V 2 Attribute Certificates and PMI 14 May 2002 © 2000 -02 True. Trust Ltd 2
X. 509 Evolution • X. 509 (1988) - V 1 PKCertificates and CRLs • X. 509 (1993) - V 2 PKCertificates and revised V 1 CRLs • X. 509 (1997) - V 3 PKCertificates, V 2 CRLs and V 1 Attribute Certificates • X. 509 (2000] - V 3 PKCertificates and V 2 CRLs with additional extensions, plus V 2 Attribute Certificates and PMI 14 May 2002 © 2000 -02 True. Trust Ltd 2
 Assigning and Delegating Privileges Resource Owner Assigns privilege Privilege Holder 14 May 2002 “I authorise this Privilege Holder to use this resource in the following ways” signed The Resource Owner “I delegate authority to this End User to use this resource in this limited way” signed The Privilege Holder End User (Privilege Holder) Delegates privilege © 2000 -02 True. Trust Ltd 3
Assigning and Delegating Privileges Resource Owner Assigns privilege Privilege Holder 14 May 2002 “I authorise this Privilege Holder to use this resource in the following ways” signed The Resource Owner “I delegate authority to this End User to use this resource in this limited way” signed The Privilege Holder End User (Privilege Holder) Delegates privilege © 2000 -02 True. Trust Ltd 3
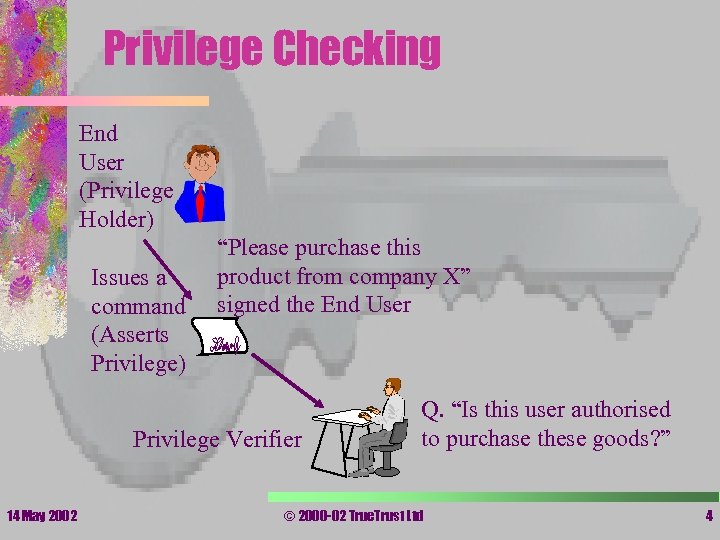 Privilege Checking End User (Privilege Holder) Issues a command (Asserts Privilege) “Please purchase this product from company X” signed the End User Privilege Verifier 14 May 2002 Q. “Is this user authorised to purchase these goods? ” © 2000 -02 True. Trust Ltd 4
Privilege Checking End User (Privilege Holder) Issues a command (Asserts Privilege) “Please purchase this product from company X” signed the End User Privilege Verifier 14 May 2002 Q. “Is this user authorised to purchase these goods? ” © 2000 -02 True. Trust Ltd 4
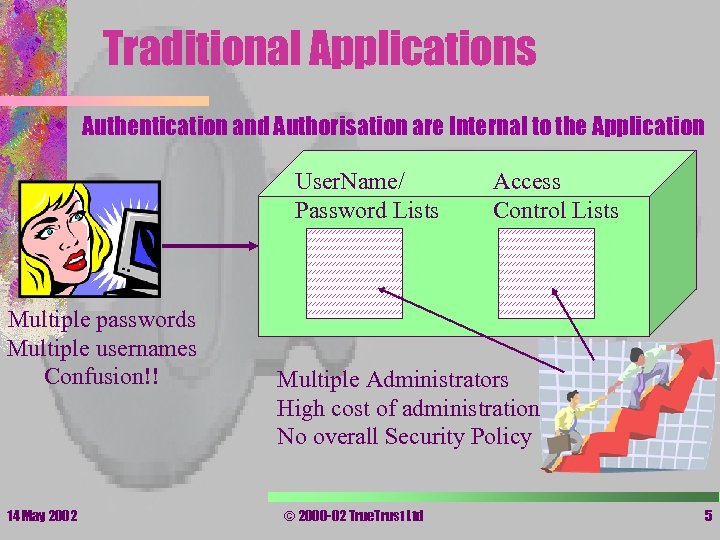 Traditional Applications • Authentication and Authorisation are Internal to the Application User. Name/ Password Lists Multiple passwords Multiple usernames Confusion!! 14 May 2002 Access Control Lists Multiple Administrators High cost of administration No overall Security Policy © 2000 -02 True. Trust Ltd 5
Traditional Applications • Authentication and Authorisation are Internal to the Application User. Name/ Password Lists Multiple passwords Multiple usernames Confusion!! 14 May 2002 Access Control Lists Multiple Administrators High cost of administration No overall Security Policy © 2000 -02 True. Trust Ltd 5
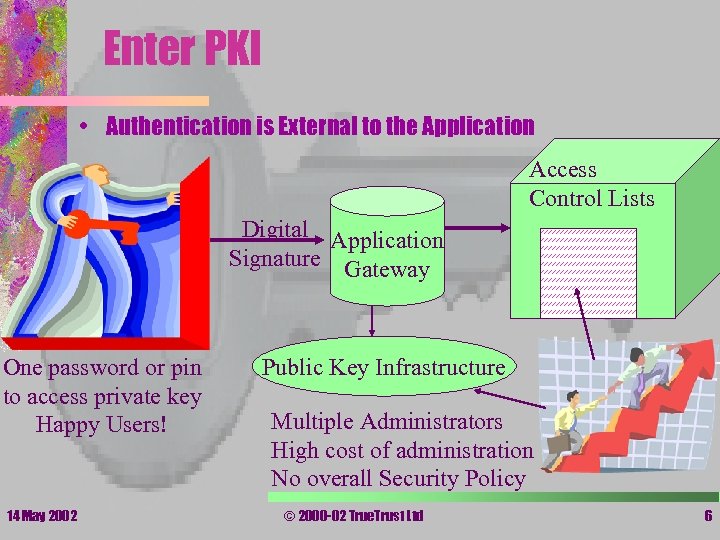 Enter PKI • Authentication is External to the Application Access Control Lists Digital Application Signature Gateway One password or pin to access private key Happy Users! 14 May 2002 Public Key Infrastructure Multiple Administrators High cost of administration No overall Security Policy © 2000 -02 True. Trust Ltd 6
Enter PKI • Authentication is External to the Application Access Control Lists Digital Application Signature Gateway One password or pin to access private key Happy Users! 14 May 2002 Public Key Infrastructure Multiple Administrators High cost of administration No overall Security Policy © 2000 -02 True. Trust Ltd 6
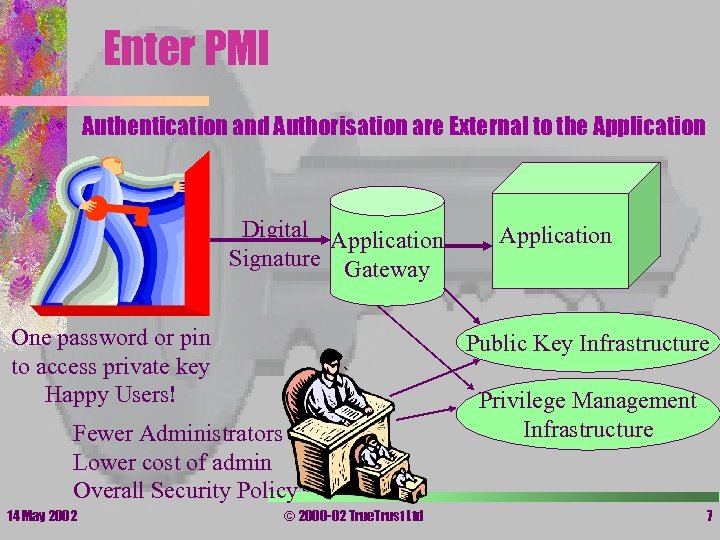 Enter PMI • Authentication and Authorisation are External to the Application Digital Application Signature Gateway One password or pin to access private key Happy Users! Public Key Infrastructure Fewer Administrators Lower cost of admin Overall Security Policy 14 May 2002 Application © 2000 -02 True. Trust Ltd Privilege Management Infrastructure 7
Enter PMI • Authentication and Authorisation are External to the Application Digital Application Signature Gateway One password or pin to access private key Happy Users! Public Key Infrastructure Fewer Administrators Lower cost of admin Overall Security Policy 14 May 2002 Application © 2000 -02 True. Trust Ltd Privilege Management Infrastructure 7
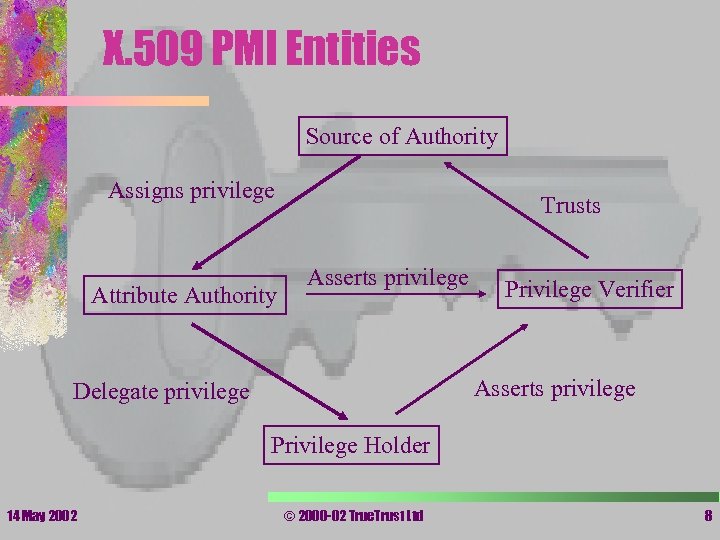 X. 509 PMI Entities Source of Authority Assigns privilege Attribute Authority Trusts Asserts privilege Privilege Verifier Asserts privilege Delegate privilege Privilege Holder 14 May 2002 © 2000 -02 True. Trust Ltd 8
X. 509 PMI Entities Source of Authority Assigns privilege Attribute Authority Trusts Asserts privilege Privilege Verifier Asserts privilege Delegate privilege Privilege Holder 14 May 2002 © 2000 -02 True. Trust Ltd 8
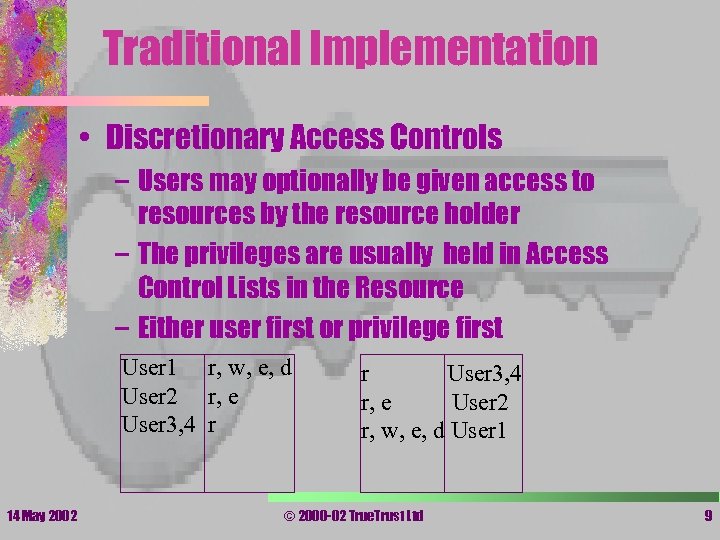 Traditional Implementation • Discretionary Access Controls – Users may optionally be given access to resources by the resource holder – The privileges are usually held in Access Control Lists in the Resource – Either user first or privilege first User 1 r, w, e, d User 2 r, e User 3, 4 r 14 May 2002 r User 3, 4 r, e User 2 r, w, e, d User 1 © 2000 -02 True. Trust Ltd 9
Traditional Implementation • Discretionary Access Controls – Users may optionally be given access to resources by the resource holder – The privileges are usually held in Access Control Lists in the Resource – Either user first or privilege first User 1 r, w, e, d User 2 r, e User 3, 4 r 14 May 2002 r User 3, 4 r, e User 2 r, w, e, d User 1 © 2000 -02 True. Trust Ltd 9
 DAC with X. 509 Attribute Certificates • The user (holder) is given an Attribute Certificate which strongly binds his/her name to the privileges being given to him/her • The AC is signed by the Attribute Authority (Resource Owner or his delegate) • Similar to X. 509 v 3 certificate, only holds a sequence of attributes rather than a public key • An attribute certificate can be stored anywhere since it is secure and self contained 14 May 2002 © 2000 -02 True. Trust Ltd 10
DAC with X. 509 Attribute Certificates • The user (holder) is given an Attribute Certificate which strongly binds his/her name to the privileges being given to him/her • The AC is signed by the Attribute Authority (Resource Owner or his delegate) • Similar to X. 509 v 3 certificate, only holds a sequence of attributes rather than a public key • An attribute certificate can be stored anywhere since it is secure and self contained 14 May 2002 © 2000 -02 True. Trust Ltd 10
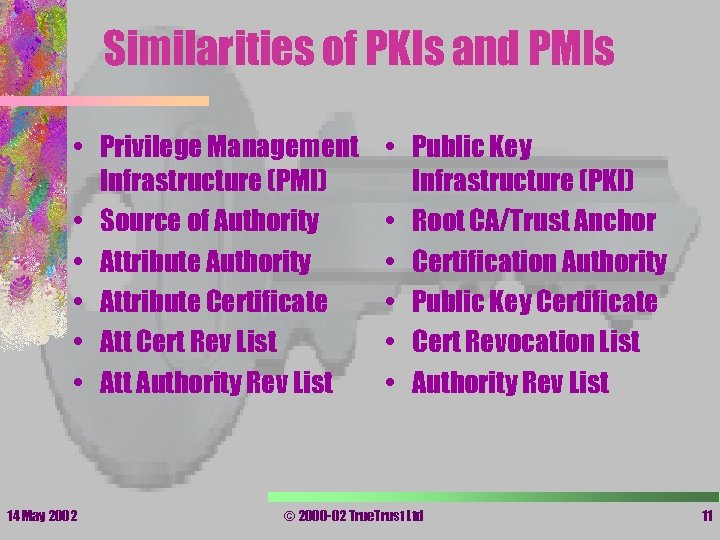 Similarities of PKIs and PMIs • Privilege Management Infrastructure (PMI) • Source of Authority • Attribute Certificate • Att Cert Rev List • Att Authority Rev List 14 May 2002 • Public Key Infrastructure (PKI) • Root CA/Trust Anchor • Certification Authority • Public Key Certificate • Cert Revocation List • Authority Rev List © 2000 -02 True. Trust Ltd 11
Similarities of PKIs and PMIs • Privilege Management Infrastructure (PMI) • Source of Authority • Attribute Certificate • Att Cert Rev List • Att Authority Rev List 14 May 2002 • Public Key Infrastructure (PKI) • Root CA/Trust Anchor • Certification Authority • Public Key Certificate • Cert Revocation List • Authority Rev List © 2000 -02 True. Trust Ltd 11
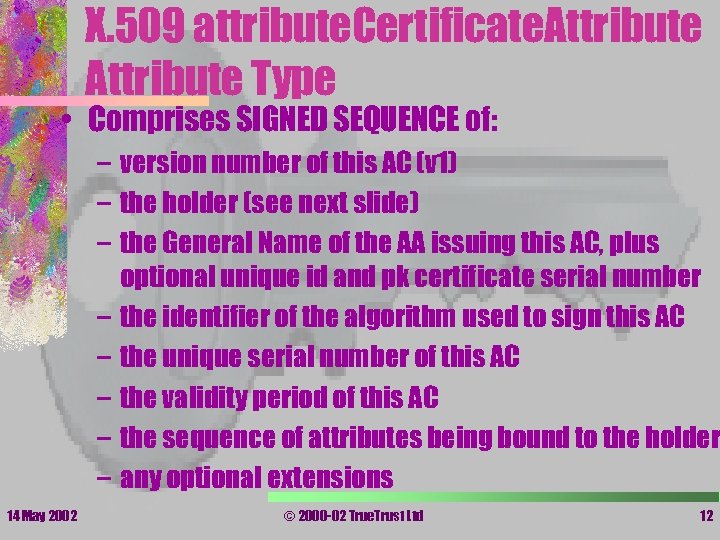 X. 509 attribute. Certificate. Attribute Type • Comprises SIGNED SEQUENCE of: – version number of this AC (v 1) – the holder (see next slide) – the General Name of the AA issuing this AC, plus optional unique id and pk certificate serial number – the identifier of the algorithm used to sign this AC – the unique serial number of this AC – the validity period of this AC – the sequence of attributes being bound to the holder – any optional extensions 14 May 2002 © 2000 -02 True. Trust Ltd 12
X. 509 attribute. Certificate. Attribute Type • Comprises SIGNED SEQUENCE of: – version number of this AC (v 1) – the holder (see next slide) – the General Name of the AA issuing this AC, plus optional unique id and pk certificate serial number – the identifier of the algorithm used to sign this AC – the unique serial number of this AC – the validity period of this AC – the sequence of attributes being bound to the holder – any optional extensions 14 May 2002 © 2000 -02 True. Trust Ltd 12
 Attribute Certificate Holder • Either General. Name of the holder, or • The holder of a private signing key, pointed to via the corresponding public key (X. 509) certificate: – the General Name of the CA issuing the PK certificate – Certificate Serial Number 14 May 2002 © 2000 -02 True. Trust Ltd 13
Attribute Certificate Holder • Either General. Name of the holder, or • The holder of a private signing key, pointed to via the corresponding public key (X. 509) certificate: – the General Name of the CA issuing the PK certificate – Certificate Serial Number 14 May 2002 © 2000 -02 True. Trust Ltd 13
 General Names • • • other. Name - any name of any form rfc 822 Name - e-mail address as per RFC 822 d. NSName - Internet domain name as per RFC 1035 x 400 Address - O/R address as per X. 411 directory. Name - directory name as per X. 501 edi. Party. Name - format agreed between EDI partners, consists of name of EDI naming authority and name of edi party • uniform. Resource. Identifier - for the WWW as per RFC 1630 • i. PAddress - Internet Protocol address as per RFC 791 • registered. ID - any OID registered as per X. 660|ISO 9834 -1 14 May 2002 © 2000 -02 True. Trust Ltd 14
General Names • • • other. Name - any name of any form rfc 822 Name - e-mail address as per RFC 822 d. NSName - Internet domain name as per RFC 1035 x 400 Address - O/R address as per X. 411 directory. Name - directory name as per X. 501 edi. Party. Name - format agreed between EDI partners, consists of name of EDI naming authority and name of edi party • uniform. Resource. Identifier - for the WWW as per RFC 1630 • i. PAddress - Internet Protocol address as per RFC 791 • registered. ID - any OID registered as per X. 660|ISO 9834 -1 14 May 2002 © 2000 -02 True. Trust Ltd 14
 Version 2 Attribute Certificates • The holder and/or the issuer can be identified by a hash value – of their public key certificate, or – if the holder or issuer is a software object e. g. applet, of the object itself • The relying party will directly re-calculate the hash in order to authenticate the holder and/or the issuer 14 May 2002 © 2000 -02 True. Trust Ltd 15
Version 2 Attribute Certificates • The holder and/or the issuer can be identified by a hash value – of their public key certificate, or – if the holder or issuer is a software object e. g. applet, of the object itself • The relying party will directly re-calculate the hash in order to authenticate the holder and/or the issuer 14 May 2002 © 2000 -02 True. Trust Ltd 15
 Role based Privilege Management • Can simplify the management of privileges • People are given a role, and they inherit the privileges assigned to the role • Many people can hold the same role e. g. member of project team A • Implemented as Role Based Access Controls 14 May 2002 © 2000 -02 True. Trust Ltd 16
Role based Privilege Management • Can simplify the management of privileges • People are given a role, and they inherit the privileges assigned to the role • Many people can hold the same role e. g. member of project team A • Implemented as Role Based Access Controls 14 May 2002 © 2000 -02 True. Trust Ltd 16
 Assigning Privileges to Roles in X. 509 • Have a Role Specification Attribute Certificate that assigns privileges to a role (the holder is a role name) • Then assign roles to people, using the role attribute, either – Add a role to the PK certificate of the subject, in the subject. Directory. Attributes extension, or – Give the person a Role Assignment Certificate (assigns a role to a AC holder) • The role membership and role privileges can be separately administered if wanted 14 May 2002 © 2000 -02 True. Trust Ltd 17
Assigning Privileges to Roles in X. 509 • Have a Role Specification Attribute Certificate that assigns privileges to a role (the holder is a role name) • Then assign roles to people, using the role attribute, either – Add a role to the PK certificate of the subject, in the subject. Directory. Attributes extension, or – Give the person a Role Assignment Certificate (assigns a role to a AC holder) • The role membership and role privileges can be separately administered if wanted 14 May 2002 © 2000 -02 True. Trust Ltd 17
 Extensions to Attribute Certificates • Basic privilege management - information about the privilege being asserted • Privilege revocation - location of revocation information • Roles - location of role specification certificates • Source of Authority - information about the SOA • Delegation - place constraints on the delegation of the privileges 14 May 2002 © 2000 -02 True. Trust Ltd 18
Extensions to Attribute Certificates • Basic privilege management - information about the privilege being asserted • Privilege revocation - location of revocation information • Roles - location of role specification certificates • Source of Authority - information about the SOA • Delegation - place constraints on the delegation of the privileges 14 May 2002 © 2000 -02 True. Trust Ltd 18
 Privilege Revocation Extensions • CRL distribution points extension points to where ACRL(s) for this AC will be found – different ACs can be posted to different lists, or – ACs can be posted to different lists according to the reasons for their revocation • No revocation extension – for short lived privilege that will not be revoked during their validity. Can only be present in privilege holder certificates, and not AA certificates 14 May 2002 © 2000 -02 True. Trust Ltd 19
Privilege Revocation Extensions • CRL distribution points extension points to where ACRL(s) for this AC will be found – different ACs can be posted to different lists, or – ACs can be posted to different lists according to the reasons for their revocation • No revocation extension – for short lived privilege that will not be revoked during their validity. Can only be present in privilege holder certificates, and not AA certificates 14 May 2002 © 2000 -02 True. Trust Ltd 19
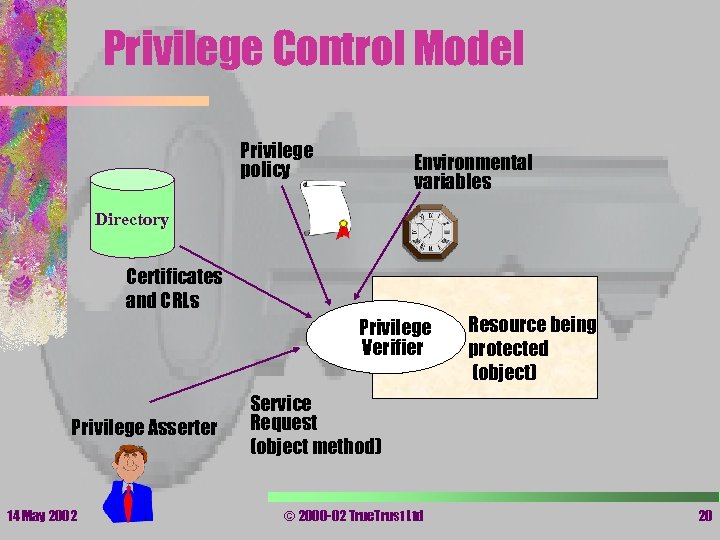 Privilege Control Model Privilege policy Environmental variables Directory Certificates and CRLs Privilege Verifier Privilege Asserter 14 May 2002 Resource being protected (object) Service Request (object method) © 2000 -02 True. Trust Ltd 20
Privilege Control Model Privilege policy Environmental variables Directory Certificates and CRLs Privilege Verifier Privilege Asserter 14 May 2002 Resource being protected (object) Service Request (object method) © 2000 -02 True. Trust Ltd 20
 Bootstrapping the Privilege Verifier • The resource (privilege verifier) must have available to it 14 May 2002 – the root of trust of the PKI (public key of root CA) – the root of trust of the PMI (public key of Source of Authority or a valid PK certificate) – privilege policy (rules for handling privileges) – local variables e. g. time of day, account balances – access to revocation information and certificate chains © 2000 -02 True. Trust Ltd 21
Bootstrapping the Privilege Verifier • The resource (privilege verifier) must have available to it 14 May 2002 – the root of trust of the PKI (public key of root CA) – the root of trust of the PMI (public key of Source of Authority or a valid PK certificate) – privilege policy (rules for handling privileges) – local variables e. g. time of day, account balances – access to revocation information and certificate chains © 2000 -02 True. Trust Ltd 21
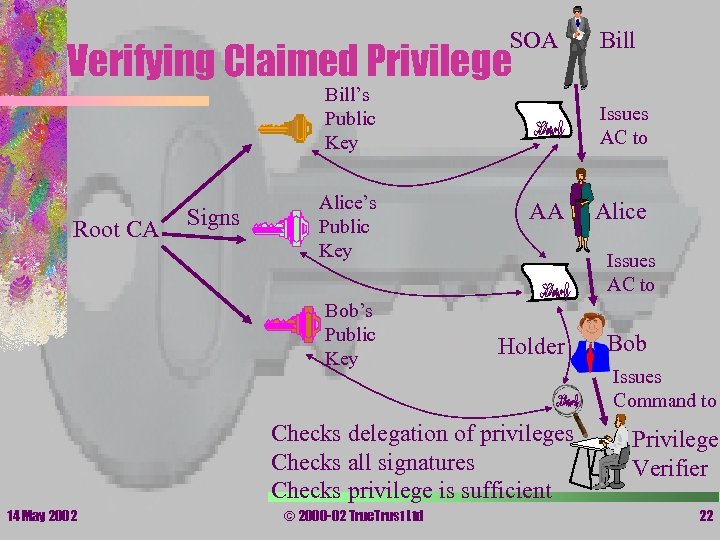 SOA Verifying Claimed Privilege Bill’s Public Key Root CA Signs Alice’s Public Key Bob’s Public Key Issues AC to AA © 2000 -02 True. Trust Ltd Alice Issues AC to Holder Checks delegation of privileges Checks all signatures Checks privilege is sufficient 14 May 2002 Bill Bob Issues Command to Privilege Verifier 22
SOA Verifying Claimed Privilege Bill’s Public Key Root CA Signs Alice’s Public Key Bob’s Public Key Issues AC to AA © 2000 -02 True. Trust Ltd Alice Issues AC to Holder Checks delegation of privileges Checks all signatures Checks privilege is sufficient 14 May 2002 Bill Bob Issues Command to Privilege Verifier 22
 Further Standardisation Work of SG 17 Q. 9 • • • 14 May 2002 Friends attributes in X. 501, X. 511 Distributed page results service in X. 518 Related Entries in X. 501, X. 518 Alignment with IETF LDAP standards Defect reports in entire X. 500 -series © 2000 -02 True. Trust Ltd 23
Further Standardisation Work of SG 17 Q. 9 • • • 14 May 2002 Friends attributes in X. 501, X. 511 Distributed page results service in X. 518 Related Entries in X. 501, X. 518 Alignment with IETF LDAP standards Defect reports in entire X. 500 -series © 2000 -02 True. Trust Ltd 23


